CIS14: Working with OAuth and OpenID Connect
7 likes3,217 views
The document provides an overview of OAuth 2.0 and OpenID Connect, detailing how OAuth 2.0 enables limited access to HTTP services through various authorization flows. It describes the differences between OAuth and OpenID Connect, highlighting the additional identity layer and the processes for provider discovery and client registration. Key components such as authorization requests, access tokens, and ID tokens are also elaborated, emphasizing the importance of authentication and information claims.
1 of 54
Downloaded 143 times

























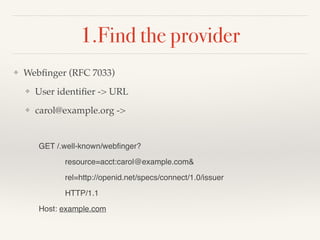
![Webfinger response
HTTP/1.1 200 OK!
Access-Control-Allow-Origin: *!
Content-Type: application/jrd+json!
!
{!
"subject" : "acct:carol@example.com",!
"links" :!
[ {!
"rel" : "http://openid.net/specs/connect/1.0/issuer",!
"href" : "https://openid.example.com"!
} ]!
}](https://image.slidesharecdn.com/cisopenidconnectintro-140811131050-phpapp02/85/CIS14-Working-with-OAuth-and-OpenID-Connect-27-320.jpg)



























Ad
Recommended
OAuth 2.0 and OpenId Connect
OAuth 2.0 and OpenId ConnectSaran Doraiswamy This document discusses authentication and authorization frameworks like OAuth and OpenID Connect. It provides an overview of key concepts like authentication, authorization, roles in OAuth like resource owner, client, authorization server and resource server. It explains the authorization code grant flow in OAuth and how OpenID Connect builds upon OAuth to provide identity features. It also compares OpenID Connect to SAML and discusses Microsoft and TechCello implementations of these specifications.
OpenID Connect - An Emperor or Just New Cloths?
OpenID Connect - An Emperor or Just New Cloths?Oliver Pfaff OpenID Connect is a specification that defines an identity layer on top of the OAuth 2.0 authorization framework. It allows clients to verify user identity and obtain basic profile information about the user. OpenID Connect supports common identity use cases like single sign-on and identity federation through the use of ID tokens and user info endpoints. While it is not a complete replacement for SAML, OpenID Connect provides a simpler approach that is better suited for mobile and REST-based applications compared to the XML-based SAML standard.
CIS14: OAuth and OpenID Connect in Action
CIS14: OAuth and OpenID Connect in ActionCloudIDSummit The document outlines the steps for implementing OAuth and OpenID Connect with Salesforce Identity, highlighting client registration, metadata retrieval, client initialization, and token usage. It also covers the use of social sign-on and just-in-time provisioning for improved federation, along with advanced features like enterprise policies and two-factor authentication. Additionally, it emphasizes the importance of refresh tokens for single sign-on (SSO) capabilities.
Single Sign On with OAuth and OpenID
Single Sign On with OAuth and OpenIDGasperi Jerome The document discusses the implementation of single sign-on (SSO) using OpenID and OAuth standards for authentication and authorization. It outlines the process of accessing Kalideos data through a secured WMS server, highlighting how user information and rights are managed through OAuth tokens and identity servers. Additionally, it mentions the planned use of OpenID Connect within the Theia project, which focuses on land surface thematic research in France.
Understanding OpenID
Understanding OpenIDPrabath Siriwardena OpenID is a decentralized protocol that allows users to log in to multiple websites using a single digital identity. It allows users to maintain a single username and password that can be used to access any website that accepts OpenID logins. When a user logs in to a website using OpenID, they are redirected to their OpenID provider to authenticate, and then sent back to the website. This allows for single sign-on across multiple sites without needing separate credentials for each site.
Securing your APIs with OAuth, OpenID, and OpenID Connect
Securing your APIs with OAuth, OpenID, and OpenID ConnectManish Pandit The document discusses securing APIs using OAuth, OpenID, and OpenID Connect, explaining how these protocols facilitate authentication and authorization across various platforms. It outlines the roles of different entities, such as resource owners, resource servers, and authorization servers, and emphasizes the importance of delegated authentication to enhance security. The piece also contrasts traditional authentication methods with the benefits of modern approaches provided by OpenID Connect and OAuth 2.0.
Full stack security
Full stack securityDPC Consulting Ltd The document covers the topics of OAuth 2.0, OpenID Connect, and JSON Web Tokens (JWT), outlining their functionalities in authorizing and authenticating users. OAuth 2.0 presents methods for secure resource access via tokens while addressing common security issues. OpenID Connect builds on OAuth 2.0 to provide user identity verification through an ID token, and the document also includes flow diagrams and practical implementation details.
Protecting web APIs with OAuth 2.0
Protecting web APIs with OAuth 2.0Vladimir Dzhuvinov The document provides an overview of protecting web APIs using OAuth 2.0, focusing on the use of bearer tokens to authenticate requests. It details the handling of token statuses such as missing, invalid, or insufficient privileges, and outlines two types of token encodings. Additionally, it covers the OAuth 2.0 grant types, the role of authorization servers in issuing tokens, and introduces OpenID Connect as an identity layer on top of OAuth 2.0.
OpenID Connect 1.0 Explained
OpenID Connect 1.0 ExplainedEugene Siow The document details the process of OpenID Connect involving a relying party (RP) and an OpenID provider (OP) for user authentication. It outlines the steps from the initial request by the client to user consent, followed by the OP sending an ID token and access token back to the RP, which can then access user information via a userinfo endpoint. The document also references specific protocols and specifications related to OpenID Connect and JWT.
Mit 2014 introduction to open id connect and o-auth 2
Mit 2014 introduction to open id connect and o-auth 2Justin Richer The document provides an overview of OAuth 2.0 and OpenID Connect (OIDC) protocols. It discusses how OAuth limits information sharing between parties in a protocol to improve security. It presents a diagram showing the separation of username, codes, tokens, sessions, and other credentials between the user agent, authorization server, client, and protected resource in the OAuth authorization code flow. The document emphasizes that OAuth and OIDC aim to avoid password proliferation, enable authentication and authorization across different systems, and provide a standardized user identity API.
OpenID vs OAuth - Identity on the Web
OpenID vs OAuth - Identity on the WebRichard Metzler The document discusses identity management protocols OpenID and OAuth. OpenID allows users to use a single digital identity across multiple websites, while OAuth allows websites to grant third party applications access to user data without sharing passwords. The document outlines the roles, flows, and differences between the two protocols, and proposes a project to implement an OAuth service provider and consumer as an example.
OpenID Connect: An Overview
OpenID Connect: An OverviewPat Patterson OpenID Connect is a simple identity layer that allows clients like mobile or web apps to verify user identities based on an authentication performed by an authorization server, as well as obtain basic profile information about users. It is built on OAuth 2.0 and defined by the OpenID Foundation. The specification defines core features as well as optional discovery, dynamic registration, session management, and OAuth 2.0 response types. Major companies like Google, Salesforce, and Microsoft have implemented or are deploying OpenID Connect to provide single sign-on for web and mobile clients.
ConFoo 2015 - Securing RESTful resources with OAuth2
ConFoo 2015 - Securing RESTful resources with OAuth2Rodrigo Cândido da Silva The document discusses securing RESTful resources using OAuth 2.0, highlighting its importance, concepts, and implementation strategies. It covers the evolution of OAuth, its grant types, and Java implementations, emphasizing the benefits and complexities associated with using OAuth 2.0 for authentication and authorization of APIs. Additionally, it provides practical insights and references for further exploration of OAuth 2.0 security practices.
Spring security oauth2
Spring security oauth2axykim00 OAuth2 is a protocol for authorization that allows clients limited access to user accounts and specifies four methods for obtaining an access token, including the authorization code flow. The authorization code flow involves a client redirecting a user to an authorization server, the user authorizing access, and the authorization server issuing an authorization code to the client, which can then request an access token to access a resource server on the user's behalf, while avoiding exposing the user's credentials directly.
OpenID Connect: The new standard for connecting to your Customers, Partners, ...
OpenID Connect: The new standard for connecting to your Customers, Partners, ...Salesforce Developers The document provides an overview of OpenID Connect, a new standard for identity that is based on OAuth 2.0. It discusses how OpenID Connect allows clients to authenticate users through an authorization server without having to handle usernames and passwords. The document outlines the basic OpenID Connect workflow which involves the client obtaining an ID token from the authorization server after the user authenticates. This ID token contains claims about the user that are verified by the authorization server's signature. The document encourages developers to leverage OpenID Connect to build applications that can acquire customers through social sign-on and to rapidly develop secure mobile apps.
OpenID Connect vs. OpenID 1 & 2
OpenID Connect vs. OpenID 1 & 2Mike Schwartz OpenID Connect introduces key enhancements over OpenID 1 and 2, including easier user authentication with email as the identifier, dynamic client registration, and scalable discovery for any provider. It addresses previous issues such as difficult URI identifiers and lack of support for modern signing techniques. Additionally, OpenID Connect is widely supported by major identity providers and is becoming a standard for social logins.
OpenID Connect and Single Sign-On for Beginners
OpenID Connect and Single Sign-On for BeginnersSalesforce Developers The document discusses OpenID Connect and its application in single sign-on (SSO) for Salesforce environments. It highlights problems faced by Universal Containers around user management and employee productivity, proposing solutions like implementing OpenID Connect for SSO. The presentation also outlines practical implementation steps and key takeaways on how Salesforce can function as both an OpenID Connect client and provider.
Stateless Auth using OAuth2 & JWT
Stateless Auth using OAuth2 & JWTGaurav Roy The document discusses stateless authorization using OAuth2 and JSON Web Tokens (JWT). It begins with an introduction to authentication, authorization, and single sign-on (SSO). It then provides an in-depth explanation of OAuth2 actors, flows, and grant types. The Authorization Code Grant flow and Implicit Grant flow are explained in detail. Finally, it introduces JWT and why it is a suitable standard for representing OAuth2 access tokens since it meets the requirements and libraries are available.
Stateless Auth using OAUTH2 & JWT
Stateless Auth using OAUTH2 & JWTMobiliya The document discusses stateless authentication using OAuth2 and JWT, explaining the concepts of authentication, authorization, and single sign-on (SSO). It provides an in-depth look at OAuth2, detailing its actors, various grant flows, and the implementation of JWT as a token standard for secure authorization. Additionally, it outlines how to implement OAuth2 services, the differences between grant types, and the necessary setup for stateless authorization.
CIS14: Consolidating Authorization for API and Web SSO using OpenID Connect
CIS14: Consolidating Authorization for API and Web SSO using OpenID ConnectCloudIDSummit The document discusses the advantages of using OpenID Connect over traditional SAML for authentication and API authorization, highlighting its single flow that allows both identity assertion and security tokens to be returned together. It outlines the processes for authorization requests, token responses, and key components such as access tokens and refresh tokens, emphasizing enhanced mobile and REST compatibility. Additionally, it contrasts OAuth 2 with OpenID Connect by noting the extra request for the 'openid' scope and the inclusion of an ID token.
OAuth 2.0 and Mobile Devices: Is that a token in your phone in your pocket or...
OAuth 2.0 and Mobile Devices: Is that a token in your phone in your pocket or...Brian Campbell This document provides an overview of OAuth 2.0 and how it can be used to securely authorize access to APIs from mobile applications. It begins with an introduction to OAuth and discusses how it addresses issues with directly sharing passwords between applications. The document then outlines the basic OAuth flow, including key concepts like access tokens, authorization codes, and refresh tokens. It provides code snippets demonstrating an example OAuth flow for both Android and iOS, showing the HTTP requests and responses at each step.
#5 WSO2 Masterclassitalia - WSO2 Identity Server, un approccio OAUTH2
#5 WSO2 Masterclassitalia - WSO2 Identity Server, un approccio OAUTH2Profesia Srl, Lynx Group The document promotes joining the WSO2 Italy LinkedIn group to engage with the community on WSO2 technology and integration strategies. It details various OAuth2 client grant types, token validation methods, and the functionality for OAuth2 token revocation, along with different client types (confidential and public). Additionally, the document outlines both back-channel and front-channel authentication flows, discussing their advantages and disadvantages.
Single-Page-Application & REST security
Single-Page-Application & REST securityIgor Bossenko The document discusses various authentication and authorization methods for REST APIs, including API keys, signatures, OAuth 1.0, and OAuth 2.0. It provides details on implementing authentication with an API key, secret key, or signature for identity and authorization. The document contrasts OAuth 1.0 and 2.0, covering their concepts, authentication flows, and differences. It also discusses using OAuth for SSO, refreshing tokens, and consuming secured RSS/ATOM feeds, as well as validating state, data consistency, and enforcing authorization with REST services.
An introduction to OAuth 2
An introduction to OAuth 2Sanjoy Kumar Roy This document provides an introduction and overview of OAuth 2.0. It discusses the key components and actors in the OAuth framework, including clients, protected resources, resource owners, and authorization servers. It describes the major steps of an OAuth transaction, issuing and using tokens. Specifically, it outlines the authorization code grant flow, how clients request and receive access tokens from authorization servers to access protected resources on behalf of resource owners. It also defines common OAuth concepts like scopes, refresh tokens, and authorization grants.
JWT SSO Inbound Authenticator
JWT SSO Inbound AuthenticatorMifrazMurthaja The document introduces JWT SSO as an authentication protocol that utilizes JWT tokens for user authentication in single sign-on flows. It outlines the basic working mechanism, the necessary parameters for the application, and provides a configuration guide for enabling JWT SSO. The conclusion highlights security considerations for validating JWT tokens and the support from miniorange.
Mixing OAuth 2.0,
Jersey and
Guice to
Build an Ecosystem of Apps - JavaOne...
Mixing OAuth 2.0,
Jersey and
Guice to
Build an Ecosystem of Apps - JavaOne...Hermann Burgmeier The document discusses building an ecosystem of applications using OAuth 2.0, Jersey, and Guice. It describes how to implement OAuth 2.0 authentication and authorization in a REST API built with JAX-RS and Jersey. Specifically, it shows how to enable the Implicit Grant flow to allow access from JavaScript clients, and integrates an external identity provider. The presentation includes a demonstration of these techniques using a coffee price service.
OpenID Connect Explained
OpenID Connect ExplainedVladimir Dzhuvinov OpenID Connect is a new standard for single sign-on (SSO) that allows for identity provision across web, mobile, and enterprise applications. It uses JSON Web Tokens (JWT) to assert user identity and provides a framework for authenticating users through various flows, including authorization code flow and implicit flow. The protocol, built on OAuth 2.0, supports user information retrieval and client registration, making it extensible and adaptable to various use cases.
CIS 2012 - Going Mobile with PingFederate and OAuth 2
CIS 2012 - Going Mobile with PingFederate and OAuth 2scotttomilson Scott Tomilson discusses integrating mobile applications with PingFederate using OAuth 2. He covers OAuth 2 terminology, common grant types for mobile including authorization code, implicit, and resource owner password credentials. The presentation includes demonstrations of obtaining authorization codes and access tokens on mobile devices. Topics like secure token handling, single sign-on approaches, and challenges of combining native apps with browsers are also covered.
[LDAPCon 2015] The OpenID Connect Protocol
[LDAPCon 2015] The OpenID Connect ProtocolClément OUDOT The document outlines the OAuth 2.0 protocol, detailing its framework, roles, authorization methods, and token usage. It also introduces the OpenID Connect protocol, which builds on OAuth 2.0 to provide identity verification alongside access delegation. Key differences between OpenID Connect and SAML, as well as client types and security aspects, are also discussed.
More Related Content
What's hot (20)
OpenID Connect 1.0 Explained
OpenID Connect 1.0 ExplainedEugene Siow The document details the process of OpenID Connect involving a relying party (RP) and an OpenID provider (OP) for user authentication. It outlines the steps from the initial request by the client to user consent, followed by the OP sending an ID token and access token back to the RP, which can then access user information via a userinfo endpoint. The document also references specific protocols and specifications related to OpenID Connect and JWT.
Mit 2014 introduction to open id connect and o-auth 2
Mit 2014 introduction to open id connect and o-auth 2Justin Richer The document provides an overview of OAuth 2.0 and OpenID Connect (OIDC) protocols. It discusses how OAuth limits information sharing between parties in a protocol to improve security. It presents a diagram showing the separation of username, codes, tokens, sessions, and other credentials between the user agent, authorization server, client, and protected resource in the OAuth authorization code flow. The document emphasizes that OAuth and OIDC aim to avoid password proliferation, enable authentication and authorization across different systems, and provide a standardized user identity API.
OpenID vs OAuth - Identity on the Web
OpenID vs OAuth - Identity on the WebRichard Metzler The document discusses identity management protocols OpenID and OAuth. OpenID allows users to use a single digital identity across multiple websites, while OAuth allows websites to grant third party applications access to user data without sharing passwords. The document outlines the roles, flows, and differences between the two protocols, and proposes a project to implement an OAuth service provider and consumer as an example.
OpenID Connect: An Overview
OpenID Connect: An OverviewPat Patterson OpenID Connect is a simple identity layer that allows clients like mobile or web apps to verify user identities based on an authentication performed by an authorization server, as well as obtain basic profile information about users. It is built on OAuth 2.0 and defined by the OpenID Foundation. The specification defines core features as well as optional discovery, dynamic registration, session management, and OAuth 2.0 response types. Major companies like Google, Salesforce, and Microsoft have implemented or are deploying OpenID Connect to provide single sign-on for web and mobile clients.
ConFoo 2015 - Securing RESTful resources with OAuth2
ConFoo 2015 - Securing RESTful resources with OAuth2Rodrigo Cândido da Silva The document discusses securing RESTful resources using OAuth 2.0, highlighting its importance, concepts, and implementation strategies. It covers the evolution of OAuth, its grant types, and Java implementations, emphasizing the benefits and complexities associated with using OAuth 2.0 for authentication and authorization of APIs. Additionally, it provides practical insights and references for further exploration of OAuth 2.0 security practices.
Spring security oauth2
Spring security oauth2axykim00 OAuth2 is a protocol for authorization that allows clients limited access to user accounts and specifies four methods for obtaining an access token, including the authorization code flow. The authorization code flow involves a client redirecting a user to an authorization server, the user authorizing access, and the authorization server issuing an authorization code to the client, which can then request an access token to access a resource server on the user's behalf, while avoiding exposing the user's credentials directly.
OpenID Connect: The new standard for connecting to your Customers, Partners, ...
OpenID Connect: The new standard for connecting to your Customers, Partners, ...Salesforce Developers The document provides an overview of OpenID Connect, a new standard for identity that is based on OAuth 2.0. It discusses how OpenID Connect allows clients to authenticate users through an authorization server without having to handle usernames and passwords. The document outlines the basic OpenID Connect workflow which involves the client obtaining an ID token from the authorization server after the user authenticates. This ID token contains claims about the user that are verified by the authorization server's signature. The document encourages developers to leverage OpenID Connect to build applications that can acquire customers through social sign-on and to rapidly develop secure mobile apps.
OpenID Connect vs. OpenID 1 & 2
OpenID Connect vs. OpenID 1 & 2Mike Schwartz OpenID Connect introduces key enhancements over OpenID 1 and 2, including easier user authentication with email as the identifier, dynamic client registration, and scalable discovery for any provider. It addresses previous issues such as difficult URI identifiers and lack of support for modern signing techniques. Additionally, OpenID Connect is widely supported by major identity providers and is becoming a standard for social logins.
OpenID Connect and Single Sign-On for Beginners
OpenID Connect and Single Sign-On for BeginnersSalesforce Developers The document discusses OpenID Connect and its application in single sign-on (SSO) for Salesforce environments. It highlights problems faced by Universal Containers around user management and employee productivity, proposing solutions like implementing OpenID Connect for SSO. The presentation also outlines practical implementation steps and key takeaways on how Salesforce can function as both an OpenID Connect client and provider.
Stateless Auth using OAuth2 & JWT
Stateless Auth using OAuth2 & JWTGaurav Roy The document discusses stateless authorization using OAuth2 and JSON Web Tokens (JWT). It begins with an introduction to authentication, authorization, and single sign-on (SSO). It then provides an in-depth explanation of OAuth2 actors, flows, and grant types. The Authorization Code Grant flow and Implicit Grant flow are explained in detail. Finally, it introduces JWT and why it is a suitable standard for representing OAuth2 access tokens since it meets the requirements and libraries are available.
Stateless Auth using OAUTH2 & JWT
Stateless Auth using OAUTH2 & JWTMobiliya The document discusses stateless authentication using OAuth2 and JWT, explaining the concepts of authentication, authorization, and single sign-on (SSO). It provides an in-depth look at OAuth2, detailing its actors, various grant flows, and the implementation of JWT as a token standard for secure authorization. Additionally, it outlines how to implement OAuth2 services, the differences between grant types, and the necessary setup for stateless authorization.
CIS14: Consolidating Authorization for API and Web SSO using OpenID Connect
CIS14: Consolidating Authorization for API and Web SSO using OpenID ConnectCloudIDSummit The document discusses the advantages of using OpenID Connect over traditional SAML for authentication and API authorization, highlighting its single flow that allows both identity assertion and security tokens to be returned together. It outlines the processes for authorization requests, token responses, and key components such as access tokens and refresh tokens, emphasizing enhanced mobile and REST compatibility. Additionally, it contrasts OAuth 2 with OpenID Connect by noting the extra request for the 'openid' scope and the inclusion of an ID token.
OAuth 2.0 and Mobile Devices: Is that a token in your phone in your pocket or...
OAuth 2.0 and Mobile Devices: Is that a token in your phone in your pocket or...Brian Campbell This document provides an overview of OAuth 2.0 and how it can be used to securely authorize access to APIs from mobile applications. It begins with an introduction to OAuth and discusses how it addresses issues with directly sharing passwords between applications. The document then outlines the basic OAuth flow, including key concepts like access tokens, authorization codes, and refresh tokens. It provides code snippets demonstrating an example OAuth flow for both Android and iOS, showing the HTTP requests and responses at each step.
#5 WSO2 Masterclassitalia - WSO2 Identity Server, un approccio OAUTH2
#5 WSO2 Masterclassitalia - WSO2 Identity Server, un approccio OAUTH2Profesia Srl, Lynx Group The document promotes joining the WSO2 Italy LinkedIn group to engage with the community on WSO2 technology and integration strategies. It details various OAuth2 client grant types, token validation methods, and the functionality for OAuth2 token revocation, along with different client types (confidential and public). Additionally, the document outlines both back-channel and front-channel authentication flows, discussing their advantages and disadvantages.
Single-Page-Application & REST security
Single-Page-Application & REST securityIgor Bossenko The document discusses various authentication and authorization methods for REST APIs, including API keys, signatures, OAuth 1.0, and OAuth 2.0. It provides details on implementing authentication with an API key, secret key, or signature for identity and authorization. The document contrasts OAuth 1.0 and 2.0, covering their concepts, authentication flows, and differences. It also discusses using OAuth for SSO, refreshing tokens, and consuming secured RSS/ATOM feeds, as well as validating state, data consistency, and enforcing authorization with REST services.
An introduction to OAuth 2
An introduction to OAuth 2Sanjoy Kumar Roy This document provides an introduction and overview of OAuth 2.0. It discusses the key components and actors in the OAuth framework, including clients, protected resources, resource owners, and authorization servers. It describes the major steps of an OAuth transaction, issuing and using tokens. Specifically, it outlines the authorization code grant flow, how clients request and receive access tokens from authorization servers to access protected resources on behalf of resource owners. It also defines common OAuth concepts like scopes, refresh tokens, and authorization grants.
JWT SSO Inbound Authenticator
JWT SSO Inbound AuthenticatorMifrazMurthaja The document introduces JWT SSO as an authentication protocol that utilizes JWT tokens for user authentication in single sign-on flows. It outlines the basic working mechanism, the necessary parameters for the application, and provides a configuration guide for enabling JWT SSO. The conclusion highlights security considerations for validating JWT tokens and the support from miniorange.
Mixing OAuth 2.0,
Jersey and
Guice to
Build an Ecosystem of Apps - JavaOne...
Mixing OAuth 2.0,
Jersey and
Guice to
Build an Ecosystem of Apps - JavaOne...Hermann Burgmeier The document discusses building an ecosystem of applications using OAuth 2.0, Jersey, and Guice. It describes how to implement OAuth 2.0 authentication and authorization in a REST API built with JAX-RS and Jersey. Specifically, it shows how to enable the Implicit Grant flow to allow access from JavaScript clients, and integrates an external identity provider. The presentation includes a demonstration of these techniques using a coffee price service.
OpenID Connect Explained
OpenID Connect ExplainedVladimir Dzhuvinov OpenID Connect is a new standard for single sign-on (SSO) that allows for identity provision across web, mobile, and enterprise applications. It uses JSON Web Tokens (JWT) to assert user identity and provides a framework for authenticating users through various flows, including authorization code flow and implicit flow. The protocol, built on OAuth 2.0, supports user information retrieval and client registration, making it extensible and adaptable to various use cases.
CIS 2012 - Going Mobile with PingFederate and OAuth 2
CIS 2012 - Going Mobile with PingFederate and OAuth 2scotttomilson Scott Tomilson discusses integrating mobile applications with PingFederate using OAuth 2. He covers OAuth 2 terminology, common grant types for mobile including authorization code, implicit, and resource owner password credentials. The presentation includes demonstrations of obtaining authorization codes and access tokens on mobile devices. Topics like secure token handling, single sign-on approaches, and challenges of combining native apps with browsers are also covered.
OpenID Connect: The new standard for connecting to your Customers, Partners, ...
OpenID Connect: The new standard for connecting to your Customers, Partners, ...Salesforce Developers
Viewers also liked (12)
[LDAPCon 2015] The OpenID Connect Protocol
[LDAPCon 2015] The OpenID Connect ProtocolClément OUDOT The document outlines the OAuth 2.0 protocol, detailing its framework, roles, authorization methods, and token usage. It also introduces the OpenID Connect protocol, which builds on OAuth 2.0 to provide identity verification alongside access delegation. Key differences between OpenID Connect and SAML, as well as client types and security aspects, are also discussed.
An Introduction to the Emerging JSON-Based Identity and Security Protocols (O...
An Introduction to the Emerging JSON-Based Identity and Security Protocols (O...Brian Campbell The document provides an introduction to JSON-based identity and security protocols, highlighting new frameworks like JSON Web Token (JWT), JSON Web Signature (JWS), and JSON Web Encryption (JWE). It discusses their components, benefits for improving interoperability, and security enhancements over older XML-based methods like SAML. The speaker, Brian Campbell, shares his professional background and contributions to the field of identity and security standards.
Introducing SAML 2.0 Protocol: Security and Performance
Introducing SAML 2.0 Protocol: Security and PerformanceAmin Saqi SAML 2.0 is an OASIS standard for exchanging authentication and authorization data between online services. It defines XML frameworks to securely share this information. The document discusses SAML's security components and profiles, analyzing how they work and potential vulnerabilities like CSRF, replay, and man-in-the-middle attacks if not using secure communication or PKI. It outlines the IdP-initiated and SP-initiated flows of the Web Browser SSO profile to illustrate normal SAML usage and points where security could be compromised without additional protections.
CIS14: An Overview of FIDO's Universal Factor (UAF) Specifications
CIS14: An Overview of FIDO's Universal Factor (UAF) SpecificationsCloudIDSummit This document provides an overview of the FIDO UAF (Universal Authentication Framework) protocol. It describes common password and one-time password issues like phishing, theft, and inconvenience. It then explains how FIDO UAF works by using a cryptographic authenticator device to verify the user and sign authentication responses. The document outlines the registration and authentication flows and describes how metadata is used to understand the authenticator's security characteristics. It also discusses various implementation options for the authenticator including hardware-based devices, software authenticators, and leveraging trusted execution environments.
OAuth 2.0 & OpenID Connect #MA7
OAuth 2.0 & OpenID Connect #MA7Nov Matake This document discusses OAuth 2.0 and OpenID Connect for accessing APIs. It provides an overview of how OAuth 2.0 allows clients to obtain access tokens to access protected resources from an authorization server, including the steps to obtain an authorization code and exchange it for an access token. It then introduces OpenID Connect as an identity layer on top of OAuth 2.0 that provides authentication as well as authorization and allows clients to verify the identity of the resource owner. The document promotes OpenID Connect as an improvement over traditional OpenID that supports API access and a better user experience.
Introduction to FIDO Authentication
Introduction to FIDO AuthenticationFIDO Alliance The document discusses the rise of data breaches and the inadequacy of traditional authentication methods, highlighting the need for a more secure and user-friendly approach. It introduces the FIDO (Fast Identity Online) Alliance, which aims to develop standards for authentication using public key cryptography, reducing reliance on shared secrets. The FIDO ecosystem promotes better security for online services, easier user experience, and collaboration among industry partners.
Google Case Study: Becoming Unphisable: Towards Simpler, Stronger Authenticat...
Google Case Study: Becoming Unphisable: Towards Simpler, Stronger Authenticat...FIDO Alliance This document discusses stronger authentication methods and the transition away from passwords. It introduces FIDO U2F as a passwordless authentication standard that uses public key cryptography between a user's security key and account data on a server. Google has implemented FIDO U2F internally and as an opt-in for consumers, finding it more secure than one-time passwords. While progress has been made, challenges remain in deploying FIDO U2F at large scale across different devices and providing support if users lose their key. The presentation provides resources for implementing FIDO U2F and recommends it for internal enterprise authentication as well as high-value external customers.
Fido U2F Protocol by Ather Ali
Fido U2F Protocol by Ather Ali OWASP Delhi The document discusses U2F (Universal 2nd Factor) authentication. It describes the FIDO Alliance, an organization that aims to develop open authentication standards to replace passwords. The FIDO Alliance has two specifications, UAF and U2F, that allow websites to interface with a variety of security devices. U2F provides a simple and secure authentication method where the user inserts and presses a button on their security key device for authentication across multiple services. This method is resistant to phishing and man-in-the-middle attacks since each device has unique cryptographic keys.
Introduction to SAML 2.0
Introduction to SAML 2.0Mika Koivisto This document provides an introduction to Security Assertion Markup Language (SAML) 2.0, including:
- SAML is an XML-based standard for exchanging authentication and authorization data between parties like an identity provider and service provider.
- It defines roles like identity providers, service providers, and users.
- SAML supports single sign-on, attribute sharing, identity federation, and other use cases through protocols, bindings, and profiles.
- Liferay supports acting as an identity provider or service provider using SAML through an enterprise edition plugin, allowing configuration as an IdP or SP through properties and metadata files.
- The presentation demonstrates SAML single sign-on flows and configurations using examples
Ad
Similar to CIS14: Working with OAuth and OpenID Connect (20)
OAuth 2
OAuth 2ChrisWood262 OAuth 2 is an authorization framework that allows applications to access user data and perform actions on their behalf. It defines flows for applications to request access, and provides short-lived credentials in response. The main roles in OAuth are the resource owner (user), client (application), resource server (API), and authorization server (issues tokens). Common grant types include authorization code, implicit, and client credentials flows. Tokens returned include access and refresh tokens, and OpenID Connect adds optional ID tokens containing user information.
Protecting your APIs with Doorkeeper and OAuth 2.0
Protecting your APIs with Doorkeeper and OAuth 2.0Mads Toustrup-Lønne This document discusses using Doorkeeper and OAuth 2.0 to protect APIs. It provides an overview of OAuth concepts like access tokens, scopes, applications, roles, and grant types. It then covers setting up Doorkeeper, including defining scopes, protecting controllers, handling user groups, password resets, and testing. Real-world uses of OAuth like email logins, first-party apps, third-party apps, native apps, and API documentation are also mentioned.
Learn with WSO2 - API Security
Learn with WSO2 - API Security WSO2 The document discusses OAuth and its core concepts including authorization grants, client types, authentication methods, and the OAuth handshake process. It describes the key components of OAuth including the resource owner, resource server, client, and authorization server. It also covers the different authorization grant types (authorization code, implicit, resource owner password credentials, client credentials), scopes, and the steps involved in the OAuth authorization code grant flow and implicit grant flow.
OAuth2 and OpenID with Spring Boot
OAuth2 and OpenID with Spring BootGeert Pante This document discusses OAuth2 and OpenID Connect for authentication. It begins by outlining goals of understanding OAuth, OpenID Connect concepts, and integrating them with Spring Security. It then explains key OAuth2 concepts like tokens, scopes, and flows. It describes OpenID Connect and how it builds on OAuth2 to provide authentication. It provides examples of configuring Spring Security for OAuth2 and OpenID Connect login, including registering a client and configuring the application.
Best Practices in Building an API Security Ecosystem
Best Practices in Building an API Security EcosystemPrabath Siriwardena The document outlines best practices for building an API security ecosystem, emphasizing the importance of decoupling clients from API implementations and centralizing security enforcement. It discusses issues with traditional password-based authentication and suggests the use of OAuth for managing access tokens while detailing various OAuth flows, scopes, and authorization mechanisms. Additionally, it highlights the need for strong auditing, monitoring, and fine-grained access control to secure API interactions effectively.
OAuth2 + API Security
OAuth2 + API SecurityAmila Paranawithana The document discusses OAuth 2.0 and how it provides a method for third party applications to access private resources from an API, while allowing the resource owners to authorize access without sharing credentials. It describes the four main roles in OAuth 2.0 - resource owner, client, authorization server, and resource server. It also summarizes the three main authorization flows - authorization code, implicit, and client credentials flows. The document provides details on how each flow works, including the request and response parameters.
What the Heck is OAuth and OIDC - UberConf 2018
What the Heck is OAuth and OIDC - UberConf 2018Matt Raible The document provides an in-depth overview of OAuth 2.0 and OpenID Connect (OIDC), exploring their different flows and terminologies used in the context of web authentication and delegated authorization. It highlights OAuth 2.0 as an authorization framework, noting its use cases and emphasizing that it is not an authentication protocol, while OpenID Connect extends OAuth 2.0 to include user authentication capabilities. Additionally, security considerations and common issues associated with OAuth 2.0 are discussed, alongside various grant types and examples of how these technologies integrate with identity management solutions.
What the Heck is OAuth and OIDC - Denver Developer Identity Workshop 2020
What the Heck is OAuth and OIDC - Denver Developer Identity Workshop 2020Matt Raible The document provides an overview of OAuth 2.0 and OpenID Connect (OIDC), focusing on the differences between authorization and authentication. It discusses the terminology, flow types, security considerations, and use cases for OAuth 2.0, along with the enhancements brought by OIDC. The content also touches on the complexities of implementing these protocols in modern web applications.
Demystifying OAuth 2.0
Demystifying OAuth 2.0Karl McGuinness The document explains OAuth 2.0 as a delegated authorization framework designed for REST and APIs, enabling apps to access user data without sharing passwords. It discusses various OAuth flows, security considerations, and modern use cases, emphasizing the distinction between authorization and authentication. Additionally, it covers the integration of OpenID Connect, extending OAuth 2.0 for user identity and session management.
2019 - Tech Talk DC - Token-based security for web applications using OAuth2 ...
2019 - Tech Talk DC - Token-based security for web applications using OAuth2 ...Vladimir Bychkov The document provides an overview of token-based security for web applications using OAuth 2.0 and OpenID Connect, presented by Vladimir Bychkov. It explains the architecture, protocols, and flows involved in delegated authorization and includes details on various grant types and security concerns for web applications. A demo section illustrates the practical applications of these concepts, showcasing different authorization flows and endpoints.
O Auth 2.0 The Path to Heaven from Hell
O Auth 2.0 The Path to Heaven from HellWSO2 The document discusses security issues with the traditional method of third-party applications accessing user resources using resource owner passwords. Specifically, it notes that passwords must be stored insecurely, access cannot be restricted or revoked for individual third parties, and compromise of a third party results in compromise of the user's password and all protected data. The document introduces OAuth as a solution to address these issues using mechanisms such as access tokens and authorization codes to control third party access.
OAuth 2.0 with Pet Care House
OAuth 2.0 with Pet Care HousePrabath Siriwardena The document discusses security issues with the traditional method of third-party applications accessing user resources using resource owner passwords. Specifically, it notes that passwords must be stored insecurely, access cannot be restricted or revoked for individual third parties, and compromise of a third party results in compromise of the user's password and all protected data. The document proposes using OAuth as a solution to address these issues.
O auth with facebook and google using .net
O auth with facebook and google using .netSathyaish Chakravarthy This document discusses OAuth and how it allows third-party applications to access a user's resources like contacts or photos from services like Google or Facebook without sharing the user's passwords. It describes registering clients, the authorization code flow, and demonstrates OAuth with Google and Facebook using .NET. Key points are that OAuth is not about authentication but permission, and allows resources to be shared securely without giving passwords to third parties.
Securing APIs with OAuth 2.0
Securing APIs with OAuth 2.0Kai Hofstetter The document discusses securing APIs with OAuth 2.0. It introduces the key players in OAuth 2.0 - the resource owner, resource server, client, and authorization server. It then summarizes three OAuth 2.0 grant types: the client credentials grant, which allows a client to obtain an access token to access public resources without a resource owner; the authorization code grant, which exchanges an authorization code for an access token after the resource owner authorizes the client; and the implicit grant, which returns an access token directly to the client without exchanging an authorization code. Refresh tokens are also discussed, which allow clients to obtain new access tokens once the initial access token expires.
Microservice security with spring security 5.1,Oauth 2.0 and open id connect
Microservice security with spring security 5.1,Oauth 2.0 and open id connect Nilanjan Roy This document provides an overview of microservice security using Spring Security 5.1, OAuth 2.0, and OpenID Connect. It defines OAuth 2.0 and its authorization framework, describing how applications can be authorized to access user data. It outlines the authorization code grant flow and other grant types, including how applications register and use client IDs and secrets. JSON Web Tokens are discussed as an access token format. OpenID Connect is described as extending OAuth 2.0 to provide authentication via ID tokens. Key components like access tokens, refresh tokens, and the client credentials flow are also summarized.
The OAuth 2.0 Authorization Framework
The OAuth 2.0 Authorization FrameworkSamuele Cozzi The document provides an overview of the OAuth 2.0 authorization framework, including definitions of key actors (resource owner, resource server, authorization server, client), grant types (authorization code, implicit, resource owner password credentials, client credentials), and protocol flows. It describes the authorization endpoint, token endpoint, common request/response parameters, and how to obtain and refresh access tokens.
Keeping Pace with OAuth’s Evolving Security Practices.pdf
Keeping Pace with OAuth’s Evolving Security Practices.pdfSirris The document provides an overview of OAuth 2.0 security practices, focusing on different grant types such as client credentials, password, implicit, and authorization code grants. It discusses the advantages and threats associated with each grant type, emphasizing the importance of using secure methods like the authorization code with PKCE for user authorization. Best practices and recommendations for secure token handling and implementation are also outlined, highlighting the need to adhere to updated standards for enhanced security.
Intro to API Security with Oauth 2.0
Intro to API Security with Oauth 2.0Functional Imperative The document provides an introduction to API security with OAUTH 2.0, describing the basics of authentication and authorization, the four primary grant types including the authorization code grant process and actors. It also discusses criticisms of OAUTH including a lack of interoperability and being designed for hosted applications in 2006. Alternative security approaches like Oz are presented that build on the lessons learned from OAUTH.
Configuring Single Sign-On (SSO) via Identity Management | MuleSoft Mysore Me...
Configuring Single Sign-On (SSO) via Identity Management | MuleSoft Mysore Me...MysoreMuleSoftMeetup The document outlines the agenda and key topics for the 'Mysore Mulesoft Meetup' held on July 6, 2024, focusing on configuring Single Sign-On (SSO) via identity management. It discusses the advantages and disadvantages of SSO, compares OpenID Connect and SAML 2.0 protocols, and details their respective architectures. Additionally, it emphasizes the importance of mapping identity provider groups with Anypoint teams to ensure appropriate permissions for users within the Anypoint platform.
Y U No OAuth, Using Common Patterns to Secure Your Web Applications
Y U No OAuth, Using Common Patterns to Secure Your Web ApplicationsJason Robert The document discusses user management and authentication methods for web applications, highlighting the evolution from traditional identity management to utilizing OAuth 2.0 and OpenID Connect with JSON Web Tokens (JWTs). It covers various authentication flows, including client credentials, password, and implicit flows, emphasizing the importance of choosing the right identity provider based on the application's infrastructure. The document concludes with recommendations for modern authentication practices, particularly for single-page applications (SPAs), advocating for the use of authorization code with Proof Key for Code Exchange (PKCE).
Configuring Single Sign-On (SSO) via Identity Management | MuleSoft Mysore Me...
Configuring Single Sign-On (SSO) via Identity Management | MuleSoft Mysore Me...MysoreMuleSoftMeetup
Ad
More from CloudIDSummit (20)
CIS 2016 Content Highlights
CIS 2016 Content HighlightsCloudIDSummit The document outlines the upcoming Cloud Identity Summit, featuring over 160 presenters, 20 keynote speakers, and 117 sessions across 22 tracks. Notable speakers include General David H. Petraeus and industry leaders like Alex Simons and Frank Abagnale, alongside various master classes and industry body summits. Key topics will cover new innovations such as blockchain and privacy, as well as traditional themes like authentication and IoT.
Top 6 Reasons You Should Attend Cloud Identity Summit 2016
Top 6 Reasons You Should Attend Cloud Identity Summit 2016CloudIDSummit The Cloud Identity Summit was founded by Ping Identity with support from industry leaders in 2010 to bring together the brightest minds across the identity and security industry. Today the event is recognized as the world’s premier identity industry conference and includes tracks from industry thought leaders, CIOs and practitioners. Cloud Identity Summit serves as a multi-year roadmap to deploy solutions that are here today but built for the future. For more info, go to www.cloudidentitysummit.com.
Be apart of the convo on Twitter: @CloudIDSummit + #CISNOLA
CIS 2015 Security Without Borders: Taming the Cloud and Mobile Frontier - And...
CIS 2015 Security Without Borders: Taming the Cloud and Mobile Frontier - And...CloudIDSummit This document introduces a new identity security system called Sierra Border Security V1.0. It discusses how the assumptions around internet and enterprise security have changed over time as the perimeter has expanded with new technologies. The key challenges mentioned are that identity is now too weak and disconnected to protect organizations at scale. The proposed new system aims to evolve authentication beyond single-factor to continuous multi-factor authentication using standards-based interactions. It will leverage big data and intelligence for dynamic access control and move to identity-based security definitions.
Mobile security, identity & authentication reasons for optimism 20150607 v2
Mobile security, identity & authentication reasons for optimism 20150607 v2CloudIDSummit This document discusses authentication and security across devices, operating systems, applications, and networks. It covers a variety of authentication mechanisms like fingerprints, facial recognition, PINs, and security hardware. It also discusses the FIDO protocol for passwordless authentication and its ability to securely authenticate users across different devices and applications. The growing number of connected devices makes scalable authentication a challenge, but solutions like FIDO aim to simplify authentication without compromising security.
CIS 2015 Mobile Security, Identity & Authentication: Reasons for Optimism - R...
CIS 2015 Mobile Security, Identity & Authentication: Reasons for Optimism - R...CloudIDSummit The document discusses advancements in security and authentication, highlighting the inadequacies of traditional passwords and the increasing prevalence of identity theft. It introduces FIDO (Fast Identity Online) protocols as a solution for secure authentication across devices, focusing on user and data integrity. The content emphasizes the need for a hardware-based trust chain in authentication efforts to enhance security measures.
CIS 2015 Virtual Identity: The Vision, Challenges and Experiences in Driving ...
CIS 2015 Virtual Identity: The Vision, Challenges and Experiences in Driving ...CloudIDSummit This document discusses building an enterprise identity provider (IdP) to address security, scalability, and governance of federated identity and access management. It describes what an enterprise IdP is and its benefits, including being a federated identity service, security token service, providing a 360 degree view of identity, and more. It outlines considerations for building an enterprise IdP such as for scalability, ROI, durability, and longevity. Potential pitfalls are also discussed like responsibility issues, skills gaps, lack of time and sponsorship. Planning recommendations include committing to a strategic IAM view, formalizing an IAM program, selling the idea of an enterprise IdP, and leveraging strategic partners.
CIS 2015 Deploying Strong Authentication to a Global Enterprise: A Comedy in ...
CIS 2015 Deploying Strong Authentication to a Global Enterprise: A Comedy in ...CloudIDSummit The document humorously details the challenges faced during the deployment of strong authentication (MFA) at Microsoft, highlighting the lengthy pilot phases and issues with user experience. It narrates a conversation where executive sponsorship helped facilitate the rollout despite the obstacles. The latter sections reflect on policy exceptions and the common misinformation that arose post-deployment regarding authentication-related issues.
CIS 2015 Without Great Security, Digital Identity is Not Worth the Electrons ...
CIS 2015 Without Great Security, Digital Identity is Not Worth the Electrons ...CloudIDSummit The document discusses the critical importance of security in digital identity management, highlighting that without robust security measures, digital identity is essentially worthless. It outlines alarming statistics regarding the frequency of cyber attacks, the significant costs associated with data breaches, and various strategies and technologies being employed to enhance security. Additionally, it emphasizes the risks posed by weak protocols and malicious attacks, underscoring the need for constant vigilance and advanced detection techniques.
CIS 2015 Mergers & Acquisitions in a Cloud Enabled World - Brian Puhl
CIS 2015 Mergers & Acquisitions in a Cloud Enabled World - Brian PuhlCloudIDSummit The document discusses the merger and acquisition strategy of a company that conducts 10-15 acquisitions annually, primarily involving small firms. Key focus areas include ensuring identity management, maintaining business processes, and facilitating seamless integration of employees and applications. It emphasizes the importance of identity management as a central theme in successful integration efforts.
CIS 2015 IoT and IDM in your Mobile Enterprise - Brian Katz
CIS 2015 IoT and IDM in your Mobile Enterprise - Brian KatzCloudIDSummit Brian Katz discusses how IoT and identity management are important for mobile enterprises. He notes that IoT strategies must include connectivity APIs, sensors to collect data, and tools to manage identity across endpoints. Effective IoT implementation generates large amounts of data from connected devices that companies need to properly manage and secure. There are also challenges around data ownership, privacy, lack of standards, and security that businesses must address when incorporating IoT technologies.
CIS 2015 Practical Deployments Enterprise Cloud Access Management Platform - ...
CIS 2015 Practical Deployments Enterprise Cloud Access Management Platform - ...CloudIDSummit The document outlines a strategy for transitioning to a cloud access management platform, focusing on migrating from legacy systems while enhancing self-service and automation capabilities. Key components include cross-platform federation using OpenID Connect, API gateways for resource access, and a shift in responsibility to business app teams. The approach aims to create a standards-based, network-independent system that supports modern applications, including mobile and SaaS use cases.
CIS 2015 What I Learned From Pitching IAM To My CIO - Steve Tout
CIS 2015 What I Learned From Pitching IAM To My CIO - Steve ToutCloudIDSummit The document discusses lessons learned from pitching an identity and access management (IAM) initiative to a Chief Information Officer (CIO). It emphasizes the importance of having a clear vision, gaining support, and adapting presentations to fit the audience's understanding. Notably, it highlights the CIO's key priorities, which include compliance, security, innovation, and customer experience.
CIS 2015 How to secure the Internet of Things? Hannes Tschofenig
CIS 2015 How to secure the Internet of Things? Hannes TschofenigCloudIDSummit The document discusses securing the Internet of Things. It begins by describing common constraints of IoT devices like limited RAM, flash, and CPU capabilities. It then summarizes lessons learned from real-world attacks on IoT systems, including limited software update mechanisms, missing key management, inappropriate access control, lack of communication security, and vulnerability to physical attacks. The document advocates following security best practices like integrating software updates, using modern OS concepts, automated key management, and considering physical attacks in threat analyses. It also describes ARM's contributions to improving IoT security through its mbed platform, libraries, and involvement in standards organizations.
CIS 2015 The IDaaS Dating Game - Sean Deuby
CIS 2015 The IDaaS Dating Game - Sean DeubyCloudIDSummit The document discusses the appeal and adoption of Identity-as-a-Service (IDaaS), highlighting its benefits like rapid deployment, enhanced security, and suitability for various business sizes. It outlines use cases for IDaaS, particularly in environments with high turnover and security-oriented firms, while also pointing out challenges like complex on-premises environments and the low adoption of identity standards. The conclusion emphasizes the growing mainstream acceptance of IDaaS, driven by factors such as cloud migration and major SaaS applications like Office 365.
CIS 2015 SSO for Mobile and Web Apps Ashish Jain
CIS 2015 SSO for Mobile and Web Apps Ashish JainCloudIDSummit The document discusses Single Sign-On (SSO) solutions for mobile and web applications, outlining the current and desired user experiences. It introduces various options for implementing SSO, such as using system browsers, enrolling devices, and leveraging different authentication methods. Additionally, it highlights challenges faced in mobile SSO and suggests potential strategies to enhance user access and security.
The Industrial Internet, the Identity of Everything and the Industrial Enterp...
The Industrial Internet, the Identity of Everything and the Industrial Enterp...CloudIDSummit The document discusses the Industrial Internet of Things (IoT), emphasizing its components such as unique identities, network connections, data access, and security. It highlights the importance of accurately defining identities and the challenges associated with integrating numerous devices into enterprises. Additionally, it stresses the need for secure design practices and risk management in the Industrial Enterprise context.
CIS 2015 SAML-IN / SAML-OUT - Scott Tomilson & John Dasilva
CIS 2015 SAML-IN / SAML-OUT - Scott Tomilson & John DasilvaCloudIDSummit The document discusses building federated relationships for Single Sign-On (SSO) capabilities using protocols like SAML and WS-FED among partners. It emphasizes the importance of extending federation capabilities and provides examples related to SharePoint and OpenID Connect. The content is framed within the context of the Cloud Identity Summit, highlighting the significance of SSO in modern applications.
CIS 2015 Session Management at Scale - Scott Tomilson & Jamshid Khosravian
CIS 2015 Session Management at Scale - Scott Tomilson & Jamshid KhosravianCloudIDSummit The document discusses session management using PingAccess within a web application environment, detailing session initiation and token management. It covers topics such as session attributes, timeouts, single logout, and scalability options for PingAccess. The presentation concludes with explanations of session token structure, storage, and security considerations.
CIS 2015 So you want to SSO … Scott Tomilson & John Dasilva
CIS 2015 So you want to SSO … Scott Tomilson & John DasilvaCloudIDSummit The document discusses Single Sign-On (SSO) and its integration with various applications, emphasizing the need for a unified username and password approach. It outlines the challenges and steps related to 'first mile' and 'last mile' integration, including the necessity of conforming to web SSO standards such as SAML and OpenID Connect. Additionally, it addresses the options available for mobile application SSO and the importance of user experience in managing multiple logins.
CIS 2015 Identity Relationship Management in the Internet of Things
CIS 2015 Identity Relationship Management in the Internet of ThingsCloudIDSummit The document discusses identity relationship management (IRM) in the context of the Internet of Things (IoT), emphasizing the need for selective data sharing that balances privacy and usability. It highlights existing limitations of current consent tools and proposes federated authorization as a solution for enabling centralized authorization-as-a-service for managing data sharing. The author provides a connected-car scenario to illustrate the implementation of these concepts while stressing the importance of security and control in this evolving landscape.
Recently uploaded (20)
Cluster-Based Multi-Objective Metamorphic Test Case Pair Selection for Deep N...
Cluster-Based Multi-Objective Metamorphic Test Case Pair Selection for Deep N...janeliewang985 the slides of the MP selection approach CMPS
AI Agents and FME: A How-to Guide on Generating Synthetic Metadata
AI Agents and FME: A How-to Guide on Generating Synthetic MetadataSafe Software In the world of AI agents, semantics is king. Good metadata is thus essential in an organization's AI readiness checklist. But how do we keep up with the massive influx of new data? In this talk we go over the tips and tricks in generating synthetic metadata for the consumption of human users and AI agents alike.
9-1-1 Addressing: End-to-End Automation Using FME
9-1-1 Addressing: End-to-End Automation Using FMESafe Software This session will cover a common use case for local and state/provincial governments who create and/or maintain their 9-1-1 addressing data, particularly address points and road centerlines. In this session, you'll learn how FME has helped Shelby County 9-1-1 (TN) automate the 9-1-1 addressing process; including automatically assigning attributes from disparate sources, on-the-fly QAQC of said data, and reporting. The FME logic that this presentation will cover includes: Table joins using attributes and geometry, Looping in custom transformers, Working with lists and Change detection.
Connecting Data and Intelligence: The Role of FME in Machine Learning
Connecting Data and Intelligence: The Role of FME in Machine LearningSafe Software In this presentation, we want to explore powerful data integration and preparation for Machine Learning. FME is known for its ability to manipulate and transform geospatial data, connecting diverse data sources into efficient and automated workflows. By integrating FME with Machine Learning techniques, it is possible to transform raw data into valuable insights faster and more accurately, enabling intelligent analysis and data-driven decision making.
Curietech AI in action - Accelerate MuleSoft development
Curietech AI in action - Accelerate MuleSoft developmentshyamraj55 CurieTech AI in Action – Accelerate MuleSoft Development
Overview:
This presentation demonstrates how CurieTech AI’s purpose-built agents empower MuleSoft developers to create integration workflows faster, more accurately, and with less manual effort
linkedin.com
+12
curietech.ai
+12
meetups.mulesoft.com
+12
.
Key Highlights:
Dedicated AI agents for every stage: Coding, Testing (MUnit), Documentation, Code Review, and Migration
curietech.ai
+7
curietech.ai
+7
medium.com
+7
DataWeave automation: Generate mappings from tables or samples—95%+ complete within minutes
linkedin.com
+7
curietech.ai
+7
medium.com
+7
Integration flow generation: Auto-create Mule flows based on specifications—speeds up boilerplate development
curietech.ai
+1
medium.com
+1
Efficient code reviews: Gain intelligent feedback on flows, patterns, and error handling
youtube.com
+8
curietech.ai
+8
curietech.ai
+8
Test & documentation automation: Auto-generate MUnit test cases, sample data, and detailed docs from code
curietech.ai
+5
curietech.ai
+5
medium.com
+5
Why Now?
Achieve 10× productivity gains, slashing development time from hours to minutes
curietech.ai
+3
curietech.ai
+3
medium.com
+3
Maintain high accuracy with code quality matching or exceeding manual efforts
curietech.ai
+2
curietech.ai
+2
curietech.ai
+2
Ideal for developers, architects, and teams wanting to scale MuleSoft projects with AI efficiency
Conclusion:
CurieTech AI transforms MuleSoft development into an AI-accelerated workflow—letting you focus on innovation, not repetition.
AI VIDEO MAGAZINE - June 2025 - r/aivideo
AI VIDEO MAGAZINE - June 2025 - r/aivideo1pcity Studios, Inc AI VIDEO MAGAZINE - r/aivideo community newsletter – Exclusive Tutorials: How to make an AI VIDEO from scratch, PLUS: How to make AI MUSIC, Hottest ai videos of 2025, Exclusive Interviews, New Tools, Previews, and MORE - JUNE 2025 ISSUE -
Smarter Aviation Data Management: Lessons from Swedavia Airports and Sweco
Smarter Aviation Data Management: Lessons from Swedavia Airports and SwecoSafe Software Managing airport and airspace data is no small task, especially when you’re expected to deliver it in AIXM format without spending a fortune on specialized tools. But what if there was a smarter, more affordable way?
Join us for a behind-the-scenes look at how Sweco partnered with Swedavia, the Swedish airport operator, to solve this challenge using FME and Esri.
Learn how they built automated workflows to manage periodic updates, merge airspace data, and support data extracts – all while meeting strict government reporting requirements to the Civil Aviation Administration of Sweden.
Even better? Swedavia built custom services and applications that use the FME Flow REST API to trigger jobs and retrieve results – streamlining tasks like securing the quality of new surveyor data, creating permdelta and baseline representations in the AIS schema, and generating AIXM extracts from their AIS data.
To conclude, FME expert Dean Hintz will walk through a GeoBorders reading workflow and highlight recent enhancements to FME’s AIXM (Aeronautical Information Exchange Model) processing and interpretation capabilities.
Discover how airports like Swedavia are harnessing the power of FME to simplify aviation data management, and how you can too.
" How to survive with 1 billion vectors and not sell a kidney: our low-cost c...
" How to survive with 1 billion vectors and not sell a kidney: our low-cost c...Fwdays Let's talk about our history. How we started the project with a small vector database of less than 2 million records. Later, we received a request for +100 million records, then another +100... And so gradually we reached almost 1 billion. Standard tools were quickly running out of steam - we were running into performance, index size, and very limited resources. After a long series of trials and errors, we built our own low-cost cluster, which today stably processes thousands of queries to more than 1B vectors.
Mastering AI Workflows with FME by Mark Döring
Mastering AI Workflows with FME by Mark DöringSafe Software Harness the full potential of AI with FME: From creating high-quality training data to optimizing models and utilizing results, FME supports every step of your AI workflow. Seamlessly integrate a wide range of models, including those for data enhancement, forecasting, image and object recognition, and large language models. Customize AI models to meet your exact needs with FME’s powerful tools for training, optimization, and seamless integration
The Future of Product Management in AI ERA.pdf
The Future of Product Management in AI ERA.pdfAlyona Owens Hi, I’m Aly Owens, I have a special pleasure to stand here as over a decade ago I graduated from CityU as an international student with an MBA program. I enjoyed the diversity of the school, ability to work and study, the network that came with being here, and of course the price tag for students here has always been more affordable than most around.
Since then I have worked for major corporations like T-Mobile and Microsoft and many more, and I have founded a startup. I've also been teaching product management to ensure my students save time and money to get to the same level as me faster avoiding popular mistakes. Today as I’ve transitioned to teaching and focusing on the startup, I hear everybody being concerned about Ai stealing their jobs… We’ll talk about it shortly.
But before that, I want to take you back to 1997. One of my favorite movies is “Fifth Element”. It wowed me with futuristic predictions when I was a kid and I’m impressed by the number of these predictions that have already come true. Self-driving cars, video calls and smart TV, personalized ads and identity scanning. Sci-fi movies and books gave us many ideas and some are being implemented as we speak. But we often get ahead of ourselves:
Flying cars,Colonized planets, Human-like AI: not yet, Time travel, Mind-machine neural interfaces for everyone: Only in experimental stages (e.g. Neuralink).
Cyberpunk dystopias: Some vibes (neon signs + inequality + surveillance), but not total dystopia (thankfully).
On the bright side, we predict that the working hours should drop as Ai becomes our helper and there shouldn’t be a need to work 8 hours/day. Nobody knows for sure but we can require that from legislation. Instead of waiting to see what the government and billionaires come up with, I say we should design our own future.
So, we as humans, when we don’t know something - fear takes over. The same thing happened during the industrial revolution. In the Industrial Era, machines didn’t steal jobs—they transformed them but people were scared about their jobs. The AI era is making similar changes except it feels like robots will take the center stage instead of a human. First off, even when it comes to the hottest space in the military - drones, Ai does a fraction of work. AI algorithms enable real-time decision-making, obstacle avoidance, and mission optimization making drones far more autonomous and capable than traditional remote-controlled aircraft. Key technologies include computer vision for object detection, GPS-enhanced navigation, and neural networks for learning and adaptation. But guess what? There are only 2 companies right now that utilize Ai in drones to make autonomous decisions - Skydio and DJI.
The Future of Technology: 2025-2125 by Saikat Basu.pdf
The Future of Technology: 2025-2125 by Saikat Basu.pdfSaikat Basu A peek into the next 100 years of technology. From Generative AI to Global AI networks to Martian Colonisation to Interstellar exploration to Industrial Nanotechnology to Artificial Consciousness, this is a journey you don't want to miss. Which ones excite you the most? Which ones are you apprehensive about? Feel free to comment! Let the conversation begin!
"Scaling in space and time with Temporal", Andriy Lupa.pdf
"Scaling in space and time with Temporal", Andriy Lupa.pdfFwdays Design patterns like Event Sourcing and Event Streaming have long become standards for building real-time analytics systems. However, when the system load becomes nonlinear with fast and often unpredictable spikes, it's crucial to respond quickly in order not to lose real-time operating itself.
In this talk, I’ll share my experience implementing and using a tool like Temporal.io. We'll explore the evolution of our system for maintaining real-time report generation and discuss how we use Temporal both for short-lived pipelines and long-running background tasks.
EIS-Webinar-Engineering-Retail-Infrastructure-06-16-2025.pdf
EIS-Webinar-Engineering-Retail-Infrastructure-06-16-2025.pdfEarley Information Science As AI reshapes expectations in retail and B2B commerce, organizations are recognizing a critical reality: meaningful AI outcomes depend on well-structured, adaptable infrastructure. In this session, Seth Earley is joined by Phil Ryan - AI strategist, search technologist, and founder of Glass Leopard Technologies - for a candid conversation on what it truly means to engineer systems for scale, agility, and intelligence.
Phil draws on more than two decades of experience leading search and AI initiatives for enterprise organizations. Together, he and Seth explore the challenges businesses face when legacy architectures limit personalization, agility, and real-time decisioning - and what needs to change to support agentic technologies and next-best-action capabilities.
Key themes from the webinar include:
Composability as a prerequisite for AI - Why modular, loosely coupled systems are essential for adapting to rapid innovation and evolving business needs
Search and relevance as foundational to AI - How techniques honed-in enterprise search have laid the groundwork for more responsive and intelligent customer experiences
From MDM and CDP to agentic systems - How data platforms are evolving to support richer customer context and dynamic orchestration
Engineering for business alignment - Why successful AI programs require architectural decisions grounded in measurable outcomes
The conversation is practical and forward-looking, connecting deep technical understanding with real-world business needs. Whether you’re modernizing your commerce stack or exploring how AI can enhance product discovery, personalization, or customer journeys, this session provides a clear-eyed view of the capabilities, constraints, and priorities that matter most.
2025_06_18 - OpenMetadata Community Meeting.pdf
2025_06_18 - OpenMetadata Community Meeting.pdfOpenMetadata The community meetup was held Wednesday June 18, 2025 @ 9:00 AM PST.
Catch the next OpenMetadata Community Meetup @ https://www.meetup.com/openmetadata-meetup-group/
In this month's OpenMetadata Community Meetup, "Enforcing Quality & SLAs with OpenMetadata Data Contracts," we covered data contracts, why they matter, and how to implement them in OpenMetadata to increase the quality of your data assets!
Agenda Highlights:
👋 Introducing Data Contracts: An agreement between data producers and consumers
📝 Data Contracts key components: Understanding a contract and its purpose
🧑🎨 Writing your first contract: How to create your own contracts in OpenMetadata
🦾 An OpenMetadata MCP Server update!
➕ And More!
From Manual to Auto Searching- FME in the Driver's Seat
From Manual to Auto Searching- FME in the Driver's SeatSafe Software Finding a specific car online can be a time-consuming task, especially when checking multiple dealer websites. A few years ago, I faced this exact problem while searching for a particular vehicle in New Zealand. The local classified platform, Trade Me (similar to eBay), wasn’t yielding any results, so I expanded my search to second-hand dealer sites—only to realise that periodically checking each one was going to be tedious. That’s when I noticed something interesting: many of these websites used the same platform to manage their inventories. Recognising this, I reverse-engineered the platform’s structure and built an FME workspace that automated the search process for me. By integrating API calls and setting up periodic checks, I received real-time email alerts when matching cars were listed. In this presentation, I’ll walk through how I used FME to save hours of manual searching by creating a custom car-finding automation system. While FME can’t buy a car for you—yet—it can certainly help you find the one you’re after!
Quantum AI Discoveries: Fractal Patterns Consciousness and Cyclical Universes
Quantum AI Discoveries: Fractal Patterns Consciousness and Cyclical UniversesSaikat Basu Embark on a cosmic journey exploring the intersection of quantum
computing, consciousness, and ancient wisdom. Together we'll uncover the
recursive patterns that bind our reality.
Security Tips for Enterprise Azure Solutions
Security Tips for Enterprise Azure SolutionsMichele Leroux Bustamante Delivering solutions to Azure may involve a variety of architecture patterns involving your applications, APIs data and associated Azure resources that comprise the solution. This session will use reference architectures to illustrate the security considerations to protect your Azure resources and data, how to achieve Zero Trust, and why it matters. Topics covered will include specific security recommendations for types Azure resources and related network security practices. The goal is to give you a breadth of understanding as to typical security requirements to meet compliance and security controls in an enterprise solution.
Securing Account Lifecycles in the Age of Deepfakes.pptx
Securing Account Lifecycles in the Age of Deepfakes.pptxFIDO Alliance Securing Account Lifecycles in the Age of Deepfakes
Raman Bhaumik - Passionate Tech Enthusiast
Raman Bhaumik - Passionate Tech EnthusiastRaman Bhaumik A Junior Software Developer with a flair for innovation, Raman Bhaumik excels in delivering scalable web solutions. With three years of experience and a solid foundation in Java, Python, JavaScript, and SQL, she has streamlined task tracking by 20% and improved application stability.
CIS14: Working with OAuth and OpenID Connect
- 1. OAuth 2.0 and OpenID Connect Basics From OAuth2 to OpenID Connect by Roland Hedberg
- 2. Let’s start with OAuth2
- 3. ❖ The OAuth 2.0 authorization framework enables a third-party application to obtain limited access to an HTTP service, ! ❖ either on behalf of a resource owner by orchestrating an approval interaction between the resource owner and the HTTP service, ! ❖ or by allowing the third-party application to obtain access on its own behalf.
- 4. The players Authorization Server Resource ServerClient
- 5. Authorization Request Authorization Server Resource Server Client Authorization request
- 6. Authorization Request - details Parameters! client_id! redirect_uri! response_type! scope! state Authorization Server Resource Server Client Authorization request GET! http://example.com/authorization?state=1521671980316802035&! ! redirect_uri=https://example.org/authz_cb&! ! response_type=code&! ! client_id=SFEBuhC7sp3a
- 7. Authorization Server Resource Server Client AUTHENTICATION HAPPENS & End-user consent/authorization
- 8. Authorization Response Authorization Server Resource Server Client Authorization response
- 9. Authorization Response - details Authorization Server Resource Server Client Authorization response GET! https://example.org/authz_cb?state=1521671980316802035&! ! code=s87BT60pp2UbNX2HnkWpZ9YhPVHRZaoTuU9XJul6JMuQaKUidUM6y1Boab6 Parameters code! state access_token! token_type! expires_in! scope! state
- 10. Access Token Request Authorization Server Resource Server Client Access token request
- 11. Access Token Request - details POST! http://example.com/token! ! code=s87BT60pp2UbNX2HnkWpZ9YhPVHRZaoTuU9XJul6JMuQaKUidUM6y1Boab6&! ! grant_type=authorization_code&! ! redirect_uri=https://example.org/authz_cb Authorization Server Resource Server Client Access token request Parameters! client_id! code! grant_type! redirect_uri
- 12. Access Token Response Authorization Server Resource Server Client Access token response
- 13. Access Token Response - details {! ! 'access_token': ’s87BT60pp2UbNX2HnkWpfPfWNo9Gi7chACuWoa2IDND', ! ! 'expires_in': 3600, ! ! 'refresh_token': ’s87BT60pp2U+bNX2HnkWpVCnDYPsy8EOpI’! ! 'state': ’STATE0’,! ! 'token_type': 'Bearer', ! } Authorization Server Resource Server Client Access token response Parameters! access_token! expires_in! refresh_token scope! token_type
- 14. Resource Access Authorization Server Resource Server Client Resource request/response
- 15. Resource Access - details Authorization Server Resource Server Client Resource request/response GET! https://example.com/resource! ! Header:! ! Authorization: ’Bearer s87BT60pp2UbNX2HnkWpfPfWNo9Gi7chACuWoa2IDND’!
- 16. The whole Authorization Server Resource Server Client Authorization request Authorization Server Resource Server Client Authorization response Authorization Server Resource Server Client Access token request Authorization Server Resource Server Client Access token response Authorization Server Resource Server Client Resource request/response Authorization Server Resource Server Client AUTHENTICATION HAPPENS & End-user consent/authorization
- 17. Flows ❖ Authorization Code Grant! ❖ Implicit Grant! ❖ Resource Owner Password Credentials Grant! ❖ Client Credentials Grant
- 18. Implicit grant Authorization Server Resource Server Client Authorization request Authorization Server Resource Server Client Resource request/response Authorization Server Resource Server Client Authorization response Authorization Server Resource Server Client AUTHENTICATION HAPPENS & End-user consent/authorization
- 19. Resource Owner Password Credentials Grant & Client Credentials Grant Authorization Server Resource Server Client Access token request Authorization Server Resource Server Client Access token response Authorization Server Resource Server Client Resource request/response
- 20. From OAuth2 to OpenID Connect
- 21. ❖ OpenID Connect 1.0 is a simple identity layer on top of the OAuth 2.0 protocol. ! ❖ It enables Clients to verify the identity of the End-User based on the authentication performed by an Authorization Server, as well as to obtain basic profile information about the End-User in an interoperable and REST-like manner.
- 22. The differences ❖ Only authorization grant and implicit grant flows! ❖ Dynamic provider discovery and client registration! ❖ ID Token! ❖ Additions/Clarifications/Constrictions! ❖ UserInfo endpoint
- 23. Flows ❖ Authorization code! ❖ Implicit! ❖ Hybrid (authorization code with a twist)! ❖ code id_token! ❖ code token! ❖ code id_token token
- 24. Dynamic provider discovery and client registration
- 25. Dynamic discovery and registration 1. Find the provider! 2. Discover provider info! 3. Register client
- 26. 1.Find the provider ❖ Webfinger (RFC 7033)! ❖ User identifier -> URL! ❖ [email protected] ->! ! GET /.well-known/webfinger?! resource=acct:[email protected]&! rel=http://openid.net/specs/connect/1.0/issuer! HTTP/1.1! Host: example.com
- 27. Webfinger response HTTP/1.1 200 OK! Access-Control-Allow-Origin: *! Content-Type: application/jrd+json! ! {! "subject" : "acct:[email protected]",! "links" :! [ {! "rel" : "http://openid.net/specs/connect/1.0/issuer",! "href" : "https://openid.example.com"! } ]! }
- 28. 2.Discover provider info - query GET /.well-known/openid-configuration HTTP/1.1! Host: openid.example.com
- 29. 2. Discover provider info - response ❖ issuer! ❖ jwks_uri! ❖ endpoints! ❖ functions supported! ❖ support for signing/encrypting algorithms! ❖ policy/tos
- 30. Required information ❖ issuer! ❖ jwks_uri! ❖ authorization_endpoint! ❖ token_endpoint (*)! ❖ response_types_supported! ❖ subject_types_supported! ❖ id_token_signing_alg_supported
- 31. 3. Client registration ❖ uris! ❖ application information! ❖ support for signing/encrypting algorithms! ❖ key material! ❖ server behavior! ❖ client behavior
- 33. Client registration response ❖ client_id! ❖ possibly client_secret and if so client_secret_experies_at! ❖ and the Authorization servers view of things
- 34. An Authorization Server ❖ MAY add fields the client didn’t include.! ❖ MAY reject or replace any of the Client's requested field values and substitute them with suitable values.! ❖ MAY ignore values provided by the client, and MUST ignore any fields sent by the Client that it does not understand.
- 35. A Client can not ❖ modify a registration! ❖ delete a registration
- 36. ID Token
- 37. ID Token ❖ Have to make a detour into JWT/K/A/S/E land
- 38. JWT ❖ Jason Web Token! ❖ a compact URL-safe means of representing claims to be transferred between two parties! ❖ Suggested pronunciation: ’jot’
- 39. JWS represents content secured with digital signatures or Message Authentication Codes (MACs) using JavaScript Object Notation (JSON) based data structures. JWE represents encrypted content using JavaScript Object Notation (JSON) based data structures.
- 40. JWK a JavaScript Object Notation (JSON) data structure that represents a cryptographic key JWA registers cryptographic algorithms and identifiers to be used with the JSON Web Signature(JWS), JSON Web Encryption (JWE), and JSON Web Key (JWK) specifications
- 41. ID Token ❖a security token that contains Claims about the Authentication of an End-User by an Authorization Server when using a Client, and potentially other requested Claims. ! ❖is represented as a JSON Web Token (JWT)
- 42. ID Token claims -required ❖ iss - Issuer Identifier for the Issuer of the response! ❖ sub - Subject Identifier! ❖ aud - Intended audience! ❖ exp - Expiration time! ❖ iat - Issued at! ❖ auth_time - Authentication time! ❖ nonce
- 43. ID Token claims - optional ❖ acr - Authentication Context Class Reference! ❖ amr - Authentication Method References! ❖ azp - Authorized party
- 45. OAuth2 Authorization Request - details Parameters! client_id! redirect_uri! response_type! scope! state Authorization Server Resource Server Client Authorization request GET! http://example.com/authorization?state=1521671980316802035&! ! redirect_uri=https://example.org/authz_cb&! ! response_type=code&! ! client_id=SFEBuhC7sp3a
- 46. Authentication Request - OpenID Connect extensions ❖ response_mode - The mechanism to use for returning parameters! ❖ nonce - Associates client session with ID Token! ❖ Signed/encrypted Authentication Request! ❖ End-user interactions! ❖ Response details
- 47. Signed/encrypted Authentication Request ❖ request - by value! ❖ request_uri - by reference! ! ❖ Single self-contained parameter! ❖ Signed and/or encrypted (JWT)
- 48. End-user interactions ❖ display - How to display pages to End-User! ❖ prompt - If the End-User should be prompted for re-authentication/ consent! ❖ max_age - allowed max time since last authentication! ❖ ui_locales - End-User’s preferred languages and scripts! ❖ id_token_hint - ID Token previously issued ! ❖ login_hint - login identifier the End-User might want to use! ❖ acr_values - requested Authentication Context Class Reference values
- 49. Response details ❖ claims! ❖ user_info! ❖ id_token! ! ❖ claims specification! ❖ null! ❖ essential! ❖ value! ❖ values
- 51. User info ❖ sub! ❖ name! ❖ given_name! ❖ family_name! ❖ middle_name! ❖ nickname! ❖ preferred_username Set of standard claims ❖ profile! ❖ picture! ❖ website! ❖ email! ❖ email_verified! ❖ gender! ❖ birthdate ❖ zoneinfo! ❖ locale! ❖ phone_number! ❖ phone_number_verfied! ❖ address! ❖ updated_at!
- 52. claims types ❖ Normal! ❖ Aggregated! ❖ Distributed
- 53. Summary ❖ OAuth2 is about authorization! ❖ OpenID Connect adds authentication and identity information
- 54. Questions ?
