Cisco CCNA- NAT Configuration
- 1. CISCO CCNA NAT CONFIGURATION TO WATCH OUR CISCO CCNA VIDEO TRAININGS PLEASE CHECK OUT THE LINK BELOW: WWW.ASMED.COM/C1 ASM EDUCATIONAL CENTER INC. (ASM) WHERE TRAINING, TECHNOLOGY & SERVICE CONVERGE PHONE: (301) 984-7400 ROCKVILLE,MD
- 2. CISCO CCNA NAT CONFIGURATION
- 3. CISCO CCNA NAT CONFIGURATION NAT = NETWORK ADDRESS TRANSLATION REMEMBER THE PRIVATE IP ADDRESS 10.0.0.0 — 10.255.255.255 172.16.0.0 —-172.31.255.255 192.168.0.0.—– 192.168.255.255 THE GOAL IS TO CONVERT YOUR PRIVATE IP ADDRESS TO PUBLIC ADDRESS SO THAT YOUR INTERNAL PEOPLE CAN ACCESS THE INTERNET
- 4. CISCO CCNA NAT CONFIGURATION I HAVE 2 KIND: 1) DYNAMIC NAT – USE IT WHEN YOU NEED YOUR PRIVATE NETWORK GO OUT TO INTERNET – IT HAS TWO KIND SUPPOSE I HAVE 6 PRIVATE AND THEN ISP GIVE YOU 6 PUBLIC THEN ALL SIX PEOPLE GO TO INTERNET SUPPOSE I HAVE 62 PRIVATE AND ISP ONLY GIVE YOU 6 PUBLIC IN THIS CASE ; YOU MUST USE THE KEY WORD “OVERLOAD” ; THIS CONCEPT IS CALL PAT (PORT ADDRESS TRANSLATION) 2) STATIC NAT – USE IT WHEN YOU NEED THE INTERNET PEOPLE COME TO YOUR WEBSERVER; THAT IS LOCATED IN PRIVATE LAN =10.10.10.1; IN THIS CASE YOU NEED TO USE STATIC NAT
- 5. CISCO CCNA NAT CONFIGURATION HERE IS MY LAB ON NAT/PAT: GIVEN BY ISP 6 PUBLIC ADDRESS 198.18.151.97 .98, .99,100,101,102 WITH SUBNET MASK /29 /29=255.255.255.248 .11111000 AND I HAVE 62 INTERNAL IP ADDRESS THAT NEED TO GO TO INTERNET 192.168.91.65—192.168.91.126 WITH MASK /26 255.255.255.192 .11000000
- 6. CISCO CCNA NAT CONFIGURATION STEP 1) DEFINE THE POOL OF INSIDE GLOBAL ADDRESS (PUBLIC ADDRESS) THAT INSIDE LOCAL ADDRESS WILL BE TRANSLATED TO: HINT: ALWAYS ALWAYS START WITH IP NAT? R1# R1#CONFIG T ENTER CONFIGURATION COMMANDS, ONE PER LINE. END WITH CNTL/Z. R1(CONFIG)#IP NAT ? INSIDE INSIDE ADDRESS TRANSLATION OUTSIDE OUTSIDE ADDRESS TRANSLATION POOL DEFINE POOL OF ADDRESSES R1(CONFIG)#IP NAT POO R1(CONFIG)#IP NAT POOL ? WORD POOL NAME R1(CONFIG)#IP NAT POOL CCNA ?
- 7. CISCO CCNA NAT CONFIGURATION A.B.C.D START IP ADDRESS R1(CONFIG)#IP NAT POOL CCNA 198.18.151.97 ? A.B.C.D END IP ADDRESS R1(CONFIG)#IP NAT POOL CCNA 198.18.151.97 198.18.151.102 ? NETMASK SPECIFY THE NETWORK MASK R1(CONFIG)#IP NAT POOL CCNA 198.18.151.97 198.18.151.102 NET R1(CONFIG)#IP NAT POOL CCNA 198.18.151.97 198.18.151.102 NETMASK ? A.B.C.D NETWORK MASK R1(CONFIG)#IP NAT POOL CCNA 198.18.151.97 198.18.151.102 NETMASK 255.255.255.248 ? <CR> R1(CONFIG)#IP NAT POOL CCNA 198.18.151.97 198.18.151.102 NETMASK 255.255.255.248 R1(CONFIG)#
- 8. CISCO CCNA NAT CONFIGURATION HERE IS MY SHOW RUN: IP NAT POOL CCNA 198.18.151.97 198.18.151.102 NETMASK 255.255.255.248 HINT: ANY TIME YOU SEE THE WORD POOL IT WILL TELL YOU; THAT IS PUBLIC IP ADDRESS STEP 2) DEFINE THE SOURCE OF THE INSIDE LOCAL ADDRESS AND BIND IT TO CCNA DEFINED IN PART 1 HINT: IP NAT? R1# R1# R1#CONFIG T ENTER CONFIGURATION COMMANDS, ONE PER LINE. END WITH CNTL/Z. R1(CONFIG)#IP NAT ? INSIDE INSIDE ADDRESS TRANSLATION OUTSIDE OUTSIDE ADDRESS TRANSLATION POOL DEFINE POOL OF ADDRESSES R1(CONFIG)#IP NAT % INCOMPLETE COMMAND. R1(CONFIG)#IP NAT INS R1(CONFIG)#IP NAT INSIDE ? SOURCE SOURCE ADDRESS TRANSLATION
- 9. CISCO CCNA NAT CONFIGURATION R1(CONFIG)#IP NAT INSIDE SOU R1(CONFIG)#IP NAT INSIDE SOURCE ? LIST SPECIFY ACCESS LIST DESCRIBING LOCAL ADDRESSES STATIC SPECIFY STATIC LOCAL->GLOBAL MAPPING R1(CONFIG)#IP NAT INSIDE SOURCE LIST ? <1-199> ACCESS LIST NUMBER FOR LOCAL ADDRESSES WORD ACCESS LIST NAME FOR LOCAL ADDRESSES R1(CONFIG)#IP NAT INSIDE SOURCE LIST 1 ? INTERFACE SPECIFY INTERFACE FOR GLOBAL ADDRESS POOL NAME POOL OF GLOBAL ADDRESSES R1(CONFIG)#IP NAT INSIDE SOURCE LIST 1 POO R1(CONFIG)#IP NAT INSIDE SOURCE LIST 1 POOL ? WORD NAME POOL OF GLOBAL ADDRESSES R1(CONFIG)#IP NAT INSIDE SOURCE LIST 1 POOL CCNA ? OVERLOAD OVERLOAD AN ADDRESS TRANSLATION <CR> R1(CONFIG)#IP NAT INSIDE SOURCE LIST 1 POOL CCNA OVE R1(CONFIG)#IP NAT INSIDE SOURCE LIST 1 POOL CCNA OVERLOAD ? <CR> R1(CONFIG)#IP NAT INSIDE SOURCE LIST 1 POOL CCNA OVERLOAD
- 10. CISCO CCNA NAT CONFIGURATION HINT: IF ISP HAS GIVEN YOU A SINGLE IP ADDRESS AFTER LIST 1 ? I WILL USE INTERFACE S0/0 HINT: WHEN YOU SEE THE WORD LIST THAT SHOULD TELL YOU ; I NEED TO HAVE ACL 1 THAT WILL DEFINE MY LOCAL ADDRESS STEP 3) NOW DEFINE YOU ACL 1 HINT: I HAVE /26 255.255.255.255- 255.255.255.192 ————– 0.0.0.63 AS WILD CARDS R1(CONFIG )# ACCESS-LIST 1 PERMIT 192.168.91.64 0.0.0.63 SUBNET ID WILD CARDS
- 11. CISCO CCNA NAT CONFIGURATION R1(CONFIG)# R1(CONFIG)#ACC R1(CONFIG)#ACCESS-LIST ? <1-99> IP STANDARD ACCESS LIST <100-199> IP EXTENDED ACCESS LIST R1(CONFIG)#ACCESS-LIST 1 ? DENY SPECIFY PACKETS TO REJECT PERMIT SPECIFY PACKETS TO FORWARD REMARK ACCESS LIST ENTRY COMMENT R1(CONFIG)#ACCESS-LIST 1 PERMI R1(CONFIG)#ACCESS-LIST 1 PERMIT ? A.B.C.D ADDRESS TO MATCH ANY ANY SOURCE HOST HOST A SINGLE HOST ADDRESS R1(CONFIG)#ACCESS-LIST 1 PERMIT 192.168.91.69 0.0.0.63
- 12. CISCO CCNA NAT CONFIGURATION HERE I INTENTIONALLY PUT WRONG SUBNET ID; BUT IOS WILL FIX IT FOR ME: HERE IS MY SHOW RUN: IP NAT POOL CCNA 198.18.151.97 198.18.151.102 NETMASK 255.255.255.248 IP NAT INSIDE SOURCE LIST 1 POOL CCNA OVERLOAD IP CLASSLESS ! ! ACCESS-LIST 1 PERMIT 192.168.91.64 0.0.0.63 STEP 4) TELL ROUTER WHICH SIDE IS INSIDE AND WHICH SIDE IS OUTSIDE AND MAKE SURE BE UNDER INTERFACE AND GIVE: INT F0/0 IP NAT INSIDE INT S0/0 IP NAT OUTSIDE
- 13. CISCO CCNA NAT CONFIGURATION R1#CONFIG T ENTER CONFIGURATION COMMANDS, ONE PER LINE. END WITH CNTL/Z. R1(CONFIG)#INT F0/0 R1(CONFIG-IF)#IP NAT R1(CONFIG-IF)#IP NAT ? INSIDE INSIDE INTERFACE FOR ADDRESS TRANSLATION OUTSIDE OUTSIDE INTERFACE FOR ADDRESS TRANSLATION R1(CONFIG-IF)#IP NAT INS R1(CONFIG-IF)#IP NAT INSIDE R1(CONFIG-IF)# R1(CONFIG-IF)# R1(CONFIG-IF)#INT S0/0 R1(CONFIG-IF)#IP NAT ? INSIDE INSIDE INTERFACE FOR ADDRESS TRANSLATION OUTSIDE OUTSIDE INTERFACE FOR ADDRESS TRANSLATION R1(CONFIG-IF)#IP NAT OUT R1(CONFIG-IF)#IP NAT OUTSIDE
- 14. CISCO CCNA NAT CONFIGURATION NOW LET’S LOOK AT SHOW RUN: INTERFACE FASTETHERNET0/0 IP ADDRESS 192.168.91.126 255.255.255.192 IP NAT INSIDE DUPLEX AUTO SPEED AUTO ! ! INTERFACE SERIAL0/0 IP ADDRESS 192.0.1.109 255.255.255.252 IP NAT OUTSIDE CLOCK RATE 64000 IP NAT POOL CCNA 198.18.151.97 198.18.151.102 NETMASK 255.255.255.248 IP NAT INSIDE SOURCE LIST 1 POOL CCNA OVERLOAD IP CLASSLESS ! ! ACCESS-LIST 1 PERMIT 192.168.91.64 0.0.0.63 LAST TWO STEPS IS DONE TO CHECK AND MAKE SURE LIFE IS GOOD;
- 15. CISCO CCNA NAT CONFIGURATION STEP 5) MAKE SURE YOUR ROUTER HAS A DEFAULT ROUTE TO ISP. R1#CONFIG T ENTER CONFIGURATION COMMANDS, ONE PER LINE. END WITH CNTL/Z. R1(CONFIG)# R1(CONFIG)#IP ROUTE 0.0.0.0 0.0.0.0 ? A.B.C.D FORWARDING ROUTER’S ADDRESS ETHERNET IEEE 802.3 FASTETHERNET FASTETHERNET IEEE 802.3 GIGABITETHERNET GIGABITETHERNET IEEE 802.3Z LOOPBACK LOOPBACK INTERFACE NULL NULL INTERFACE SERIAL SERIAL R1(CONFIG)#IP ROUTE 0.0.0.0 0.0.0.0 192.0.1.110
- 16. CISCO CCNA NAT CONFIGURATION STEP 6) MAKE SURE ISP KNOWS YOUR NETWORK; SO ISP WILL NEED A STATIC ROUTE BACK TO YOUR NETWORK ISP# ISP#CONFIG T ENTER CONFIGURATION COMMANDS, ONE PER LINE. END WITH CNTL/Z. ISP(CONFIG)#IP ROUTE ? A.B.C.D DESTINATION PREFIX ISP(CONFIG)#IP ROUTE 198.18.151.96 ? A.B.C.D DESTINATION PREFIX MASK ISP(CONFIG)#IP ROUTE 198.18.151.96 255.255.255.248 ? A.B.C.D FORWARDING ROUTER’S ADDRESS ETHERNET IEEE 802.3 FASTETHERNET FASTETHERNET IEEE 802.3 GIGABITETHERNET GIGABITETHERNET IEEE 802.3Z LOOPBACK LOOPBACK INTERFACE NULL NULL INTERFACE SERIAL SERIAL ISP(CONFIG)#IP ROUTE 198.18.151.96 255.255.255.248 S0/0 ISP(CONFIG)#
- 17. CISCO CCNA NAT CONFIGURATION AS WE SEE FOR ISP MAKE SURE YOU USE THE PUBLIC ADDRESS NOT PRIVATE; SNICE ISP DOES NOT KNOW YOUR PRIVATE IP ADDRESS NOW I GO AND CHECK THE PING FROM PC TO INTERNET; THEN I GO TO R1#SHOW IP NAT TRANSLATION ! PC> PC>PING 192.0.1.110 PINGING 192.0.1.110 WITH 32 BYTES OF DATA: REPLY FROM 192.0.1.110: BYTES=32 TIME=13MS TTL=254 REPLY FROM 192.0.1.110: BYTES=32 TIME=15MS TTL=254 REPLY FROM 192.0.1.110: BYTES=32 TIME=11MS TTL=254 REPLY FROM 192.0.1.110: BYTES=32 TIME=12MS TTL=254 PING STATISTICS FOR 192.0.1.110: PACKETS: SENT = 4, RECEIVED = 4, LOST = 0 (0% LOSS), APPROXIMATE ROUND TRIP TIMES IN MILLI-SECONDS: MINIMUM = 11MS, MAXIMUM = 15MS, AVERAGE = 12MS
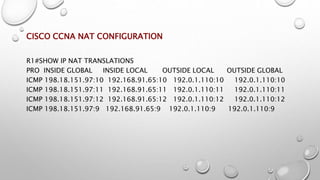
- 18. CISCO CCNA NAT CONFIGURATION R1#SHOW IP NAT TRANSLATIONS PRO INSIDE GLOBAL INSIDE LOCAL OUTSIDE LOCAL OUTSIDE GLOBAL ICMP 198.18.151.97:10 192.168.91.65:10 192.0.1.110:10 192.0.1.110:10 ICMP 198.18.151.97:11 192.168.91.65:11 192.0.1.110:11 192.0.1.110:11 ICMP 198.18.151.97:12 192.168.91.65:12 192.0.1.110:12 192.0.1.110:12 ICMP 198.18.151.97:9 192.168.91.65:9 192.0.1.110:9 192.0.1.110:9
- 19. CISCO CCNA NAT CONFIGURATION HERE IS THE SUMMARY: INTERFACE FASTETHERNET0/0 IP ADDRESS 192.168.91.126 255.255.255.192 IP NAT INSIDE DUPLEX AUTO SPEED AUTO ! INTERFACE SERIAL0/0 IP ADDRESS 192.0.1.109 255.255.255.252 IP NAT OUTSIDE CLOCK RATE 64000 ! IP NAT POOL CCNA 198.18.151.97 198.18.151.102 NETMASK 255.255.255.248 IP NAT INSIDE SOURCE LIST 1 POOL CCNA OVERLOAD IP CLASSLESS IP ROUTE 0.0.0.0 0.0.0.0 192.0.1.110 ! ! ACCESS-LIST 1 PERMIT 192.168.91.64 0.0.0.63 !
- 20. CISCO CCNA NAT CONFIGURATION HINT: IF ISP HAS GIVEN YOU SINGLE IP ADDRESS THEN YOU DO NOT NEED THE POOL STATEMENT ( THE 1ST STATEMENT) ; AND ALSO YOUR 2ND STATMENT WILL BE LIKE THIS IP NAT INSIDE SOURCE LIST 1 INT S0/0 OVERLOAD NOW IF I ADD ANOTHER LAN (10.10.10.0/24) USING MY INT F0/1 MAKE SURE YOU HAVE DEFINE ACL FOR NETWORK 10.10.10.0 /24 TO GO OUT AND MAKE SURE YOUR APPLY TO INT F0/1 WITH COMMAND IP NAT INSIDE INTERFACE FASTETHERNET0/0 IP ADDRESS 192.168.91.126 255.255.255.192 IP NAT INSIDE DUPLEX AUTO SPEED AUTO !
- 21. CISCO CCNA NAT CONFIGURATION INTERFACE FASTETHERNET0/1 IP ADDRESS 10.10.10.100 255.255.255.0 IP NAT INSIDE ( PLEASE ADD THIS) DUPLEX AUTO SPEED AUTO ! INTERFACE SERIAL0/0 IP ADDRESS 192.0.1.109 255.255.255.252 IP NAT OUTSIDE CLOCK RATE 64000 !
- 22. CISCO CCNA NAT CONFIGURATION IP NAT POOL CCNA 198.18.151.97 198.18.151.102 NETMASK 255.255.255.248 IP NAT INSIDE SOURCE LIST 1 POOL CCNA OVERLOAD IP CLASSLESS IP ROUTE 0.0.0.0 0.0.0.0 192.0.1.110 ! ! ACCESS-LIST 1 PERMIT 192.168.91.64 0.0.0.63 ACCESS-LIST 1 PERMIT 10.10.10.0 0.0.0.255 (PLEASE ADD THIS LINE) !
- 23. ASM EDUCATIONAL CENTER INC. (ASM) WHERE TRAINING, TECHNOLOGY & SERVICE CONVERGE TO WATCH OUR CISCO CCNA VIDEO TRAININGS PLEASE CHECK OUT THE LINK BELOW: WWW.ASMED.COM/C1 PHONE: (301) 984-7400 ROCKVILLE,MD