CLÍNICA DE RESPUESTAS A INCIDENTES Y THREAT HUNTING - WORKSHOP DAY TÉCNICO DE CISCO
- 1. #CLUS Del enfoque reactivo al enfoque proactivo, aprendiendo a cazar al enemigo! Miguel Garro CISM, CEH, SFCP Cybersecurity Consulting Systems Engineer Perú, Ecuador, Bolivia.
- 2. © 2018 Cisco and/or its affiliates. All rights reserved. Cisco Public#CLUS • Severity & Frequency of Cyber Threats • Building Threat Hunting Program • Threat Response Platform • Architecture & Components • Uses cases Agenda 2
- 3. Severity & Frequency of Cyber Threats 2:05
- 4. © 2018 Cisco and/or its affiliates. All rights reserved. Cisco Public#CLUS 4BRKSEC-2109 Threat Hunting Goals
- 5. © 2018 Cisco and/or its affiliates. All rights reserved. Cisco Public#CLUS 5BRKSEC-2109 Many solutions claim to block 99% of threats But what about the of threats they’re missing?
- 6. © 2018 Cisco and/or its affiliates. All rights reserved. Cisco Public#CLUS 6BRKSEC-2109 Visibility Proactivity Response What to consider
- 7. © 2018 Cisco and/or its affiliates. All rights reserved. Cisco Public#CLUS 7BRKSEC-2109 “[Threat hunting is] the process of proactively and iteratively searching … to detect and isolate advanced threats that evade existing security solutions.” - SQRRL DATA INC., “A FRAMEWORK FOR THREAT HUNTING”, 2016
- 8. © 2018 Cisco and/or its affiliates. All rights reserved. Cisco Public#CLUS 8BRKSEC-2109 ThreatHuntMaturity
- 9. © 2018 Cisco and/or its affiliates. All rights reserved. Cisco Public#CLUS 9BRKSEC-2109 ThreatHuntLifeCycle ThreatHuntLifeCycle
- 10. © 2018 Cisco and/or its affiliates. All rights reserved. Cisco Public#CLUS 10BRKSEC-2109 Determining what to hunt for and how often 1Choose your favorite attack model
- 11. © 2018 Cisco and/or its affiliates. All rights reserved. Cisco Public#CLUS 11BRKSEC-2109 Determining what to hunt for and how often 2Identify most concerning activities
- 12. © 2018 Cisco and/or its affiliates. All rights reserved. Cisco Public#CLUS 12BRKSEC-2109 Determining what to hunt for and how often 3 Build your threat hunting calendar
- 13. Threat Hunting: Case Study
- 14. © 2018 Cisco and/or its affiliates. All rights reserved. Cisco Public#CLUS 14BRKSEC-2109 Creating a Hypothesis You have found activity in reports from your SEIM showing FCAJMVXRD.COM as a location accessed by hosts on your network. You need to understand • What is this domain • What is the risk to your environment • What other sites may be related to this domain.
- 15. © 2018 Cisco and/or its affiliates. All rights reserved. Cisco Public#CLUS 15BRKSEC-2109 Investigate
- 16. © 2018 Cisco and/or its affiliates. All rights reserved. Cisco Public#CLUS 16BRKSEC-2109 WHOIS databases store the registered users or assignees of an Internet resou rce, such as a domain name, IP address block, or autonomous system Investigate with raw data & intelligence
- 17. © 2018 Cisco and/or its affiliates. All rights reserved. Cisco Public#CLUS 17BRKSEC-2109 Uncover TTP’s (Tactics, Techniques & Procedures) Threat Grid integration provides a deep understanding of all malware samples that are associated with this domain and how the malware was identified as malicious
- 18. © 2018 Cisco and/or its affiliates. All rights reserved. Cisco Public#CLUS 18BRKSEC-2109 Determining activity to identify this domain as malicious. Each of these items are a ranking mechanism used by Investigate and the TALOS team to identify the domain as a bad actor. Enrich & Harden
- 19. © 2018 Cisco and/or its affiliates. All rights reserved. Cisco Public Recon Weapon Delivery Exploitation Installation C&C Action ThreatHunt
- 22. © 2018 Cisco and/or its affiliates. All rights reserved. Cisco Public#CLUS 22BRKSEC-2109 “How did it happen and what more do I need to know?” Goals Age: 32 Work: Biography: Security events requiring deeper investigation come to me. I focus on finding the proper security data and determine what happened: Why, When, and then come up with recommendations for future prevention. The Incident Responder 0 9 Challenges SOC Data Center Desk Security Investigator Experience (Years): 10
- 23. © 2018 Cisco and/or its affiliates. All rights reserved. Cisco Public#CLUS 23BRKSEC-2109 Incident Responder Internal Monitoring Threat Intelligence How do I fix it ? What happened ? Method Repair
- 24. © 2018 Cisco and/or its affiliates. All rights reserved. Cisco Public#CLUS 24BRKSEC-2109 Internal Monitoring Threat Intelligence Incident Responder
- 25. © 2018 Cisco and/or its affiliates. All rights reserved. Cisco Public#CLUS 25BRKSEC-2109 Internal Monitoring Threat Intelligence Incident Responder Open Source Feeds Curated Feeds Aggregation From Vendors Alienvault, ThreatQ, Recorded Future, *CERT, Bulletins, Etc. Etc Identification Phases – “I see a potential threat”
- 26. © 2018 Cisco and/or its affiliates. All rights reserved. Cisco Public#CLUS 26BRKSEC-2109 Internal Monitoring Threat Intelligence Incident Responder Open Source Feeds Curated Feeds Aggregation From Vendors Alienvault, ThreatQ, Recorded Future, *CERT, Bulletins, Etc. Etc Server Logs Flow Data Firewall Events Proxy Logs WAF Logs IDS Logs Identification Phases – “Did it affect us?”
- 27. © 2018 Cisco and/or its affiliates. All rights reserved. Cisco Public#CLUS 27BRKSEC-2109 Me Policy and Enforcement Incident Responder Identification Phases – “Lets’ Block it, or Triage it.”
- 28. © 2018 Cisco and/or its affiliates. All rights reserved. Cisco Public#CLUS 28BRKSEC-2109 Policy and Enforcement Incident Responder Identification Phases – “Lets’ Block it, or Triage it.” How many Changes need to happen in this phase? How will those changes work together?
- 29. © 2018 Cisco and/or its affiliates. All rights reserved. Cisco Public#CLUS 29BRKSEC-2109 IR Team EPP NGIPS DNS Security Etc File Analysis Domain reputation IP reputation Etc EPP logs NGIPS logs DNS logs Etc Threat Response Platform
- 30. © 2018 Cisco and/or its affiliates. All rights reserved. Cisco Public#CLUS 30BRKSEC-2109 IR Team File Analysis Domain reputation IP reputation Etc EPP logs NGIPS logs DNS logs Etc EPP NGIPS DNS Security Etc
- 31. © 2018 Cisco and/or its affiliates. All rights reserved. Cisco Public#CLUS 31BRKSEC-2109 Threat Response Platform Integrating security for faster defense Open APIs · Developer Environment · Services Best of Breed Portfolio EndpointNetwork Cloud Leading Threat Intelligence Cisco Threat Response Deploy Policy InvestigateDetect Remediate 3rd Parties+280 security tech partners
- 32. © 2018 Cisco and/or its affiliates. All rights reserved. Cisco Public#CLUS 32BRKSEC-2109 Threat Response Platform Module-driven integration platform to orchestrate threat research and response. Intuitive relationship graphs built based on event telemetry from multiple 3rd party modules
- 33. © 2018 Cisco and/or its affiliates. All rights reserved. Cisco Public#CLUS 33BRKSEC-2109 Advanced Malware Protection Cloud-managed endpoint security combining prevention, detection, and response in a single agent. Deep endpoint visibility to aid investigations. Robust remediation capabilities.
- 34. © 2018 Cisco and/or its affiliates. All rights reserved. Cisco Public#CLUS 34BRKSEC-2109 Next Generation Sandboxing Global Malware Threat Intelligence platform (wikipedia of malware). Automated sample analysis platform and 3rd party integrations. API driven, streamlined User Interface.
- 35. © 2018 Cisco and/or its affiliates. All rights reserved. Cisco Public#CLUS 35BRKSEC-2109 DNS Security Cloud-delivered DNS security with millions of classified domains. Adversary infrastructure and relationship maps between domains, IPs, and ASNs. Custom domain blocking/whitelisting.
- 36. © 2018 Cisco and/or its affiliates. All rights reserved. Cisco Public#CLUS 36BRKSEC-2109 Threat Response Platform • Need to be an integrated architecture. • Brings together threat intelligence and localized security context • Reduces complexity by • enriching observables automatically across multiple sources • collating results into an intuitive format in one location • Help identify malicious observables and speed up incident response. • Helps incident responders understand threats on their network by gathering and combining threat intelligence available from 3rd parties.
- 37. © 2018 Cisco and/or its affiliates. All rights reserved. Cisco Public#CLUS 37 Can investigate & mitigate from Threat Response Platform.
- 39. © 2018 Cisco and/or its affiliates. All rights reserved. Cisco Public#CLUS 39BRKSEC-2109 Core Threat Response Terminology and Concepts • Modules • Observables • Investigate UI • Judgements • Verdicts • Sightings • Indicators • Targets • Snapshots • Casebooks
- 40. © 2018 Cisco and/or its affiliates. All rights reserved. Cisco Public#CLUS 40BRKSEC-2109 Modules Cisco Threat Response uses integration modules to integrate with Cisco security products and 3rd party tools. Integration modules can provide enrichment and response capabilities.
- 41. © 2018 Cisco and/or its affiliates. All rights reserved. Cisco Public#CLUS 41BRKSEC-2109 Observables Cisco Threat Response supports the quick investigation of cyber Observables, which might be domain names, IP addresses, file hashes, PKI certificate serial numbers, and even specific devices or users. The first thing that Cisco Threat Response does with an observable is determine its disposition, by aggregating what is known about that observable from the various enrichment modules configured. The disposition tells the Incident Responder whether the observable is: Clean (explicitly whitelisted) Malicious (explicitly blacklisted) Suspicious (potentially harmful) Unknown (not currently associated with a known disposition) Unknown observables are not enriched.
- 42. © 2018 Cisco and/or its affiliates. All rights reserved. Cisco Public#CLUS 42BRKSEC-2109 It is designed to allow an incident responder to copy and paste the contents of an email, or a log message, or an incident ticket into its main search form. Cisco Threat Response will then extract all of the Observables from the supplied text. Investigate UI Once the investigation is begun, either via the form shown above or via a pivot into Cisco Threat Response from another product, the UI will show the results of that investigation.
- 43. © 2018 Cisco and/or its affiliates. All rights reserved. Cisco Public#CLUS 43BRKSEC-2109 Judgments A Judgment associates a disposition with a cyber observable at a point in time, and is valid for an explicit span of time. Judgments can optionally be related to Indicators, providing further insight as to why a specific disposition was associated with that observable. Judgments are given by configured data source modules, and are shown associated with those data sources, along with more information including the reason.
- 44. © 2018 Cisco and/or its affiliates. All rights reserved. Cisco Public#CLUS 44BRKSEC-2109 Verdicts A Verdict indicates the most recent and most relevant disposition for a given cyber observable, as well as the Judgement from which the verdict was derived. Cisco Threat Response considers a clean verdict to be more reliable than a malicious verdict. The order of precedence for verdicts is as follows: • Clean • Malicious • Suspicious • Common • Unknown When an observable has multiple dispositions, Cisco Threat Response shows the one that appears first in the above list.
- 45. © 2018 Cisco and/or its affiliates. All rights reserved. Cisco Public#CLUS 45BRKSEC-2109 Sightings A Sighting is a record of the appearance of a cyber observable at a given date and time. Sightings can optionally be related to Indicators, providing threat intelligence context about the observable.
- 46. © 2018 Cisco and/or its affiliates. All rights reserved. Cisco Public#CLUS 46BRKSEC-2109 Indicators An Indicator describes a pattern of behavior or a set of conditions which indicate malicious behavior. Some indicators are more indicative than others of malicious behavior, so knowing exactly which bad behaviors an observable are exhibiting can help an incident responder decide what to do next. Cisco Threat Response uses a large collection of malware indicators from the AMP Global Intelligence threat archive, Threat Grid, and other sources.
- 47. © 2018 Cisco and/or its affiliates. All rights reserved. Cisco Public#CLUS 47BRKSEC-2109 Targets A Target represents the device, identity, or resource that a threat has targeted. A Target is identified by one or more Observables. When known, a type, operating system, and other metadata is recorded as well. Targets are always part of a local Sighting.
- 48. © 2018 Cisco and/or its affiliates. All rights reserved. Cisco Public#CLUS 48BRKSEC-2109 Snapshots A snapshot saves the current investigation and graph for subsequent retrieval and analysis. A unique identifier is created upon snapshot creation. Users can provide a name for the snapshot as well as a description. Snapshots can be shared among users in the same organization, to communicate the state of an investigation at a point in time.
- 49. © 2018 Cisco and/or its affiliates. All rights reserved. Cisco Public#CLUS 49BRKSEC-2109 Casebooks Built with APIs hosted in and data stored in Cisco Threat Response. Available via • Cisco Threat Response Investigate UI • Other integrated Cisco products and tools • Any web page at all via browser plugin, including • other Cisco products, integrated or not • existing external Threat Intel sources • existing 3rd party tools Allow you to: • gather observables in groups (aka cases). • assign the case a name and a description • take and save notes on the case • add other observables at any time • immediately see verdicts and take actions • Seamlessly work a case across multiple tools § even from different vendors • Share cases between staff
- 50. How to use
- 51. © 2018 Cisco and/or its affiliates. All rights reserved. Cisco Public#CLUS 51BRKSEC-2109 My team can • answer questions faster about observables. • block and unblock domains from Cisco Threat Response. • block and unblock file executions from Cisco Threat Response. • hunt for an observable associated with a known actor and immediately see organizational impact. • save a point in time snapshot of our investigations for further analysis. • document our analysis in a cloud casebook from all integrated or web-accessible tools, via an API. • Integrate Cisco Threat Response easily into existing processes and custom tools
- 52. © 2018 Cisco and/or its affiliates. All rights reserved. Cisco Public#CLUS 52 Answer questions faster about observables. • Unknown disposition. • See how it affects organization. • Get details of program executing.
- 53. © 2018 Cisco and/or its affiliates. All rights reserved. Cisco Public#CLUS 53 Can block and unblock domains from Cisco Threat Response. • Execute block from Cisco Threat Response. • Block is effected in Cisco Umbrella. • API integration to block and unblock.
- 54. © 2018 Cisco and/or its affiliates. All rights reserved. Cisco Public#CLUS 54BRKSEC-2109 Can integrate Cisco Threat Response easily into existing processes and custom tools Cisco Threat Response is designed to integrate with other security products through URLs that enable you to build powerful security workflows. The examples below assume a Cisco Threat Response install located at https://visibility.amp.cisco.com You can perform an Investigation by passing a search string to the q parameter that comes after the #/investigate part of the URL. Multiple search items are allowed, just separate them with a space character. Be sure to properly URL encode this argument. https://visibility.amp.cisco.com/#/investigate?q=domain.com https://visibility.amp.cisco.com/#/investigate?q=google.com%0A8.8.8.8%0A6732417baa49b873d72747c0ef46f8d1 You can search for Indicators, Judgements, and Sightings on the Explore pages. Similar to the Investigate page, pass a search query to the q parameter to search these threat objects. https://visibility.amp.cisco.com/#/explore/indicators?q=rat https://visibility.amp.cisco.com/#/explore/judgements?q=rat%20ip https://visibility.amp.cisco.com/#/explore/sightings?q=662472b8378274eda5cc848536cba2db1d27f8ad
- 55. See in action
- 57. © 2018 Cisco and/or its affiliates. All rights reserved. Cisco Public#CLUS 57BRKSEC-2109 Threats Phishing DDoS APT Ransomware Trojan Botnet Wiper Attack Data/IP Theft Monetary Theft Data Manipulation/ Destruction Spyware/Malware Man in the Middle Drive by Download Malvertising Unpatched Software Rogue Software Intelligence that works across the threat lifecycle Cisco IP/Domain/URL Hash/Artifacts Learn Adversary Models Hunt Threats (TTP/Tools) Process Telemetry Develop Engines (ML) Network NGFW/NGIPS Secure SD-WAN WSA/ESA Cloud Umbrella Endpoint AMP for Endpoints Access Policy Segmentation ISE DNA / Trustsec Stealthwatch Revoke App Cloudlock Quarantine File AMP for Endpoints Logs/Syslog AD, Servers Firewall, Proxy Host to Host Communications Stealthwatch App/Workload Usage Cloudlock Tetration System Behavior AMP for Endpoints SIEM Cisco partner Telemetry Intelligence Enforcement Detection Investigation Remediation Incident Response Threat Response Global Internet Analysis Umbrella Investigate Global File Analysis Threat Grid
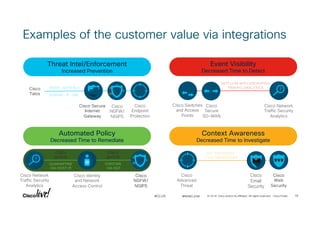
- 58. © 2018 Cisco and/or its affiliates. All rights reserved. Cisco Public#CLUS 58BRKSEC-2109 Examples of the customer value via integrations NETFLOW WITH ENCRYPTED TRAFFIC ANALYTICS Cisco Secure SD-WAN Cisco Switches and Access Points Cisco Network Traffic Security Analytics Event Visibility Decreased Time to Detect HASH • ARTIFACT DOMAIN • IP • URL Cisco Endpoint Protection Cisco Secure Internet Gateway Cisco NGFW/ NGIPS Threat Intel/Enforcement Increased Prevention Cisco Talos QUARANTINE VIA HOST IP CONTAIN VIA SGT Cisco pxGrid Automated Policy Decreased Time to Remediate Cisco Identity and Network Access Control Cisco NGFW/ NGIPS Cisco Network Traffic Security Analytics Cisco pxGrid IOC BEHAVIORS • FILE TRAJECTORY Cisco Web Security Cisco Email Security Context Awareness Decreased Time to Investigate Cisco Advanced Threat
- 59. © 2018 Cisco and/or its affiliates. All rights reserved. Cisco Public#CLUS 59BRKSEC-2109 Integration and automation is a top priority Multiple tools Block IP, URL, Domain, Hash Block Hash Block Domain Network Endpoint Cloud SIEM Umbrella Investigate Investigate Remediate Sightings Sightings Sightings 4 Plays Events from each play Multiple tools • Attack detection across multiple technologies from different vendors • SIEM integration • Manual correlation of threat intelligence with context information • Coordination and collaboration among several responders • Remediation through multiple, inconsistent consoles Difficult Time-Consuming Error-Prone
- 60. © 2018 Cisco and/or its affiliates. All rights reserved. Cisco Public#CLUS 60BRKSEC-2109 Cisco Security Automated Policy Context Awareness Event Visibility Threat Intel/Enforcement Integrated Architecture Enterprise Mobility Management Network Traffic Security Analytics Cloud Workload Protection Web Security Email Security Advanced Threat Secure SD-WAN / Routers Identity and Network Access Control Secure Internet Gateway Switches and Access Points Next-Gen FW/IPS Cloud Access Security Cisco Threat Intelligence Cisco Platform Exchange Cisco Threat Response
- 61. © 2018 Cisco and/or its affiliates. All rights reserved. Cisco Public#CLUS 61BRKSEC-2109 Enterprise Mobility Management Network Traffic Security Analytics Cloud Workload Protection Web Security Email Security Advanced Threat Secure SD-WAN / Routers Identity and Network Access Control Secure Internet Gateway Switches and Access Points Next-Gen FW/IPS Cloud Access Security Threat Response
- 62. Thank you #CLUS







![© 2018 Cisco and/or its affiliates. All rights reserved. Cisco Public#CLUS 7BRKSEC-2109
“[Threat hunting is] the
process of proactively
and iteratively searching
… to detect and isolate
advanced threats that
evade existing security
solutions.”
- SQRRL DATA INC., “A FRAMEWORK FOR THREAT HUNTING”, 2016](https://image.slidesharecdn.com/ciscothreathunting-191108160321/85/CLINICA-DE-RESPUESTAS-A-INCIDENTES-Y-THREAT-HUNTING-WORKSHOP-DAY-TECNICO-DE-CISCO-7-320.jpg)