Cloud design patterns - Federated Identity & Gatekeeper
- 1. Presented by: Roger Chien Mar 2014 Content is from “Cloud design patterns – perspective architecture guidance for cloud applications”, by Microsoft. Cloud Design Patterns Federated Identity & Gatekeeper Pattern
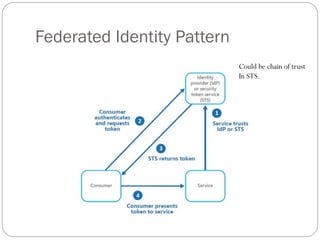
- 2. Federated Identity Pattern Delegate authentication to external identity provider LDAP inAAA. Eliminates the need of multiple login credentials for every service. (e.g. Open-ID) More easily for privilege management. (people leave and fine grain control) Application and services can save the overhead of identity management.
- 3. Federated Identity Pattern Could be chain of trust In STS.
- 4. Federated Identity Pattern - Issues Can be single point of failure. Need fine grain control for features & resources via Role based access control (RBAC). Need to maintain user information for claim based authentication (thru registration) If there is multiple STS, have to deal with sign-in redirection.
- 5. Federated Identity Pattern - Example User in large enterprise to use SaaS application onWindowsAzure.
- 6. Gatekeeper Pattern Using a dedicated host instance that acts as a broker between clients and applications/services, validates and sanitizes requests and passes requests and data between them. Add another layer of security and reduce attack surface. Fit for: Applications that handle sensitive information, expose services that must have high a degree of protection from malicious attacks, or perform mission-critical operations that must not be disrupted. Distributed applications where it is necessary to perform request validation separately from the main tasks, or to centralize this validation to simplify maintenance and administration.
- 8. Gatekeeper Pattern Controlled validation: validates all requests and rejects those didn’t meet requirement. Limited risk and exposure: Gatekeeper itself is not access to credentials and keys. If gatekeeper is compromised, those information are not exposed. Appropriate security: Run gatekeeper in a limited privilege mode. Gatekeeper is actually an application firewall.
- 9. Gatekeeper Pattern - Issues The trusted nodes only expose necessary interfaces to Gatekeeper. Run in limited privilege mode (Gatekeeper and trusted nodes are in separated hosted services orVM) Gatekeeper only do validation and sanitization, not touch any processing related to services/applications. Secure channel (SSL/TLS/HTTPS) is required for communication between Gatekeeper & trusted nodes. Performance impact. Could be single point of failure.
- 10. Gatekeeper Pattern - Example