Ad
Cloud security, Cloud security Access broker, CSAB's 4 pillar, deployment mode
- 1. Device to cloud: Cloud security, Cloud Security Access Brokers, CASB’s four pillars, deployment mode comparison Himani Singh Sept 2016
- 2. Agenda • An overview of cloud ecosystem • Security in the cloud • Cloud security solutions • What is CASB • CASB’s responsibility and use cases • Deployment modes • Benefit of deployment mode • Cloud glossary
- 3. An overview of cloud ecosystem • The cloud is a metaphor for the internet, It can simply be defined as the distributed infrastructure that is made up with bare metal, virtual machines, storage, network and is always available • Cloud computing refers to applications, services or IT resources delivered from the cloud (via internet) with pay-as-you- go model XaaS IaaS PaaS DRaaS
- 4. Cloud layers • Infrastructure as a Service (IaaS) • When you want to host • Hardware, network resources as service • Dynamic scaling, virtualization • Multiple users with single piece of hardware • Examples: AWS, Azure, Rack space • Platform as a Service (PaaS) • When you want to build • Develop, test, deploy, host and maintain applications • Multi-tenant architecture, include load balancer and failover • Heroku, Google App Engine, IBM Red Hat’s OpenShift, Salesforce as a cloud • Software as a Service • When you want to consume • Pay-as-you-go, APIs • User don’t do patch management • Box, O365, Salesforce, Google apps On-premise Software as a Service Platform as a Service Infrastructure as a Service
- 5. Types of cloud Private, public, community and hybrid • Public cloud • SaaS, PaaS and IaaS is delivered by the external vendor • Multiple unknown user s • No visibility about the user and Multi tenancy • Example – Box, O365 email • Private cloud • Dedicated to only one organization( not shared with other organizations) • More expensive and more secure in comparison of public clouds • On-premise private clouds, those are exclusively used by one organization on the premises. For example AWS hosting the cloud for any military organization. • Externally hosted private clouds. This is hosted by a third party in cloud infrastructure for one organization. • Hybrid cloud • Some critical part of data is hosted in the organization and some are hosted in public. In most of the cased, there will be tunnel or connection between public and private cloud. • Community cloud • A form of public cloud that is reserved for the member of community • Multi tenancy • Example all government in state using the same cloud
- 6. What about security control points ? With IT, HR, Productivity software, infrastructure, build platforms moving to or delivering through the cloud, Security Control Points (SCPs) are distributed in the cloud. In this case, when SCP’s are not on perimeter, the traditional security devices such as IPS, NGFW, SWGs’ are inadequate. Cloud Security is a perfect storm
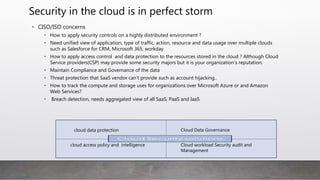
- 7. Security in the cloud is in perfect storm • CISO/ISO concerns • How to apply security controls on a highly distributed environment ? • Need unified view of application, type of traffic, action, resource and data usage over multiple clouds such as Salesforce for CRM, Microsoft 365, workday • How to apply access control and data protection to the resources stored in the cloud ? Although Cloud Service providers(CSP) may provide some security majors but it is your organization’s reputation. • Maintain Compliance and Governance of the data • Threat protection that SaaS vendor can’t provide such as account hijacking.. • How to track the compute and storage uses for organizations over Microsoft Azure or and Amazon Web Services? • Breach detection, needs aggregated view of all SaaS, PaaS and IaaS cloud data protection Cloud Data Governance cloud access policy and intelligence Cloud workload Security audit and Management
- 8. Cloud Security solutions: cloud data protection • Sensitive Data protection • Largest of any security category • Protection of employee and customer PII and intellectual property • Encryption/Decryption for sensitive data • Key management outside the cloud service provider • Protection when Data-in-transit( from Device to cloud) Data-at-rest ( in cloud or at device) • Protect all data type, structured and unstructured • Vendors • CipherCloud, CloudLock(Cisco), Perspecsys(Bluecoat), Vaultive, Netskope
- 9. Cloud Security Solutions: Cloud Data Governance • Cloud data governance • Compliance • Regulations • HIPPA • Policy • Companies: CloudLock (Cisco), Better Cloud, JumpCloud
- 10. Cloud security solutions: cloud access policy and intelligence • Cloud access policy and intelligence • Who can access the data in cloud • What device, frequency and quantity of the data • Build the good behavior • Detect the anomaly with the variation from the good behavior. • Companies : Adallom(Microsoft) , Skyfence, Elastica ( Bluecoat), Netskope, Threatstack
- 11. Cloud security solutions : cloud workload security audit and monitoring • IaaS protection solution • Works on AWS, Azure or rack space • Malware protection, IDS, IPS, FW, virtualization support, File integrity monitoring and log management • This is an emerging category • Vendors can either support (1) Cloud only solution that security workload in IaaS and PaaS, Analyze the access and security logs and (2) Securing, analysis the on-premises solution virtualization and bare-metal • Companies • HyTrust, Trend Micro, Illumio, Dome9, Symantec , FortyCloud, Palerra, Cloud Passage
- 12. Cloud Security Access Broker (CASB) Cloud access security brokers (CASBs) are a software (and technology ) that provide the cloud-based security control points that provides the visibility, access control, security intelligence, and protection for cloud based resources and users. CASB can be inline( that is, between cloud resource and consumer) or can be out-of- the band (API based) CASB vendors ensure the secure access to recourse from any device (corporate, private, managed, unmanaged), any location( office, home, airport), for any user (admin, non- admin) to any resource ( file, db) in any cloud-app(box, O365). .
- 13. The need for CASB • With highly distributed IT Infrastructure, when everything is derived as service, CEO/CISO/CIO needs the cloud-based security-policy enforcement points (SPEPs) • CASBs address three out of four main cloud security concerns • Cloud data protection • Cloud data Governance • Cloud access policy and intelligence • By using all security intelligence, Also provide • Visibility • Threat protection • Breach detection • User behavior analytic
- 14. CASB conceptual overview Corporate office, Servers, desktop, mobile phone and tablet Unmanaged mobile or personal devices Remote users IaaS AWS, Azure, Soft layer PaaS Oracle cloud, Google API, Bluemix SaaS Box, workday, O365 salesforce CASB Visibility Data Protection Continuous Monitoring Data Governance Compliance Threat Protection FW or SWG Proxy
- 15. CASB Technology overview-visibility • Visibility • Organizations are suffering from unsanctioned app(shadow IT) used in the organization. Visibility is one way to look inside your network. • CASB gives the detailed view of organization’s traffic as six W’s : • Which user, • What device(mac, mobile, chrome book), • Which app(box, one drive), • When (time), • What activity ( view, download), • What resource (file) • Visibility is achieved by either logs from NGFW/web proxies(web sense, Bluecoat) or all traffic passing through CASB. CASB NGFW Web proxies LDAP, Enterprise integration Internet
- 16. CASB technology overview – visibility A dashboard will provide the graphic and searchable view of following- • Unsanctioned and sanctioned app list • Application risk-based-score • Single User behavior over multiple cloud apps and single app with multiple users • Pass through traffic and policy based alerts • API based logs These logs can be used for defining the baseline for entity(user, app, devise)behavior. Application risk-based-score • Many CASB vendor calculate the risk-score for an application( or an vendor) • Risk is calculated the risk on many data points such as CAS, who owns the data, review Service Organization controls (SOC ) reports, research, CSA Trust, Physical data center location • CASB vendors use this data-points and put in complex matrix to calculate the App-risk score
- 17. CASB technology overview – Data protection • Cloud services make it easy to inappropriately( intentionally or by mistake) share the data • CASB offers the Data protection on file, field or object level based on the policy • Following are the technique used for data protection • Data loss protection • Encryption/decryption • Tokenization • DRM • Cover all grounds in policy ( can be very complex polices) • User centric – user, location, user action(share, view, download ), application, • Device centric- device, native client vs browser, managed or unmanaged device • Data centric -type of data, time, app, data-at-rest or data-at-move,
- 18. CASB technology overview – Data protection use case • Data loss prevention(DLP) • Both unstructured data and structured data should be searched • Pattern matches are done either • Inline when data is flowing through the CASB • Through APIs when data is at rest • Many methods to match content • Regular expression evaluation • Pre-defined library for PII, CC, SSN, medical conditions and more • Document fingerprinting • Keyword matching • Directory match • Action after policy match • Action can be encryption, block, contain, quarantine, watermark, DRM, block user, compress with password or alert
- 19. CASB technology overview – Data protection use case • Enterprise data could be tagged as “ top confidential” • If CASB vendor can read the tag, policies can be configured as data can’t be stored without encryption or can’t be copied or can’t be shared
- 20. CASB technology overview – Data protection – Encryption and tokenization • Encryption • File level • Protect data at rest ( cloud or mobile device) • Encryption done when data is upload and decrypt when downloaded. • Keys can be managed by third party or CASB itself • Same keys can be used for multiple cloud • Tokenization • Field level data obfuscation • Fields in the can be replace by the some random data ( or with some pattern depending on Tokenization scheme) • Token is stored in token vault, and it is retrieve to read the data
- 21. CASB technology overview – compliance and data Governance • Compliance and Governance is when external legislation and internal rules are applied from. Example are following • Some data can’t leave the regional boundary, such as EULA • Regulations like PCI, HIPPA • Most CASB vendors will provide the DB of attributes tracked for a cloud service, the attributes may be • The number of attribute tracked for each cloud application • Encryption strength • Two-factor authentication • A cloud risk scoring system • Detailed auditing that have five W’s (who, when, what, where, why)
- 22. CASB technology overview – Threat Protection • Malware has new playground in cloud • Since CABSs are “single point of control “ in cloud, it has an added responsibility to detect and prevent the threat. • Threat detection included scanning of traffic and checking the IP, URL, location, files, hash of the files against the know-bad-database. • Once threat is detected, the object can be blocked, quarantined or send an alert • Block traffic based on geo-locations • On the application level • Account hijacking • Stale accounts • Selective wipe
- 23. CASB technology overview – Threat Protection • User behavior analysis on multiple clouds • One user login at saleforce.com from San Jose, CA and within 30 minutes it login box.com from Huston, TX. • Some other user downloading 10 times of his usual files on his personal device. • Action could be • Block, selective wipe, alert • Ask for 2F authentication • Account lockout
- 24. CASB log based discovery • What is Discovery • An organization can understand the traffic pattern by analyzing the logs • No agent needed but Enterprise integration can help to identify users • Logs • These logs are provided by FWs, NGFW, SWG • Logs can be uploaded • Manually , using syslog or received the logs in tap mode • Can be uploaded as zip and compress mode • Most CASBs have inbuilt log parsers for popular FWs • What is discovered • Any or unknown apps can be identified • Provide the baseline for your network as cloud apps used, traffic per app, users files and more CASB NGFW Web proxies LDAP, Enterprise Integration Internet Logs
- 25. CASB deployment modes • CASB can be divided into two deployment mode • API mode (non-intrusive mode) • This is out-of-band mode • Agent-less and known as cloud application integration • Proxy mode ( inline) • Two modes of proxy • Reverse proxy • Forward proxy • CASB (software) is installed in the public cloud or some vendors own data center • Traffic is redirected to the Proxy before it goes to SaaS Server • While passing through, traffic is being scanned and all attributes such as app, IP, user- name, action (and more) are being collected and analyzed for session data • Decision can be made and Polices can be applied.
- 26. CASB Deployment mode -API • Out of the band deployment • Best used for scrubbing the cloud • The API integration for the known SaaS applications • API crawl the cloud for historic data for an SaaS app and apply the policy for DLP, invalid sharing or malware detection. • Control can be applied for any future action • Polling based • When a worker is watching the cloud and any change will alert the system • Change will be scanned and polices will be applied • Callback mode • Some cloud app support the API, in that case SaaS informs any significant changes Corporate office, Servers, desktop, mobile phone and tablet Unmanaged mobile or personal devices Remote users IaaS AWS, Azure, Soft layer PaaS Oracle cloud, Google API, Bluemix SaaS Box, workday, O365 salesforce CASB Visibility Data Protection Continuous Monitoring Data Governance Compliance Threat Protection FW or SWG Proxy
- 27. CASB API mode – Pros and cons • Advantage • Zero latency introduced by API • Can scrub the cloud • Agentless and cover both managed and unmanaged device • Covers SaaS, PaaS and IaaS traffic • Fast deploy, no need for DNS redirection, proxy chaining, reverse proxy or agent • Disadvantage • Works only for known SaaS • Most of the time it is reporting, in advanced cases decision can be made after the fact
- 28. CASB Deploy mode – forward proxy • Forward Proxy • Traffic, from End-user and admin, is redirected to the forward proxy • Traffic can be forwarded • by agent that is installed on the end devices like laptop, mobile • By DNS redirection, that is change the DNS server address in the end point to a particular DNS server • PAC file or explicit proxy in browser • Once Proxy receives the traffic, decision is made according to policies Corporate office, Servers, desktop, mobile phone and tablet Unmanaged mobile or personal devices Remote users PaaS Oracle cloud, Google API, Bluemix SaaS Box, workday, O365 salesforce CASB Visibility Data Protection Continuous Monitoring Data Governance Compliance Threat Protection Proxy Chaining, Traffic redirection, agent agent Enterprise Integration
- 29. Deploy mode – Forward Proxy Pros and Cons • Advantage • Real time, that is an advantage over API mode • Knows user, devices with enterprise integration(LDAP) • Deep packet inspection • Can work with applications’ client, that is if box or outlook is been installed on the laptop, that traffic can be scanned too • That is an advantage over reverse proxy • Disadvantage • Latency, because of proxy in comparison to API • Single point of failure • Forward proxy can’t support unmanaged devices ( no agent no DNS redirection) • Mostly focus on SaaS traffic
- 30. CASB Deploy mode-reverse proxy • Reverse Proxy • This is inline mode • Traffic, both the end-user and administration, is been redirected to the CASB Proxy • The redirection is been used achieved by URL rewriting • The decision is made when traffic is been analysis URL rewrite, traffic redirection, IDM, IDaaS, SSO, Corporate office, Servers, desktop, mobile phone and tablet Unmanaged mobile or personal devices Remote users PaaS Oracle cloud, Google API, Bluemix SaaS Box, workday, O365 salesforce CASB Visibility Data Protection Continuous Monitoring Data Governance Compliance Threat Protection Enterprise Integration
- 31. CASB Deploy mode-reverse proxy redirection Web client Unmanaged mobile or personal devices PaaS Oracle cloud, Google API, Bluemix SaaS Box, workday, O365 salesforce CASB1 2 Identity Provider 3 4 5 6 Packet flow 1. Web Client makes a connection request to SaaS, for example “abc.box.com” 2. Cloud app redirects the browser to “identity provider”. That is configured as cloud application 3. The ID-Provider retunes to the browser to another redirection with SAML SSO token 4. Using that SSO token, browser automatically connects to the CASB 5. Now CASB is inline
- 32. CASB Deploy mode-reverse proxy advantage and disadvantage • Advantage • Real time (advantage over API mode) • Agentless • Knows user, devices with enterprise integration(LDAP) • Best for unmanaged devices, can work with managed devices • Disadvantage • Latency because of proxy in comparison to API • Single point of failure • Reverse proxy only works with browser • If SaaS’s native client ( like outlook for O365) is used to send the traffic, reverse proxy will not redirect the traffic. • Works with known apps • Mostly focus on SaaS traffic
- 33. Technology Integrations • MDM integration • Can be used to push the CASB agents on the mobile • Agents can be configure to forward particular domain ranges to the CASB • Advantage : traffic redirection • Enterprise secure web gateways • Used for proxy chaining in case of forward proxy • Only selected traffic can be forwarded to CASB and other traffic can pass through • Advantage : traffic redirection • On- premises integration • LDAP or active directory integration with CASB • It can be an IAM solution installed on enterprise • A software can be installed that pulls user, group information for directory services and push to CASB • Advantage : polices can be applied based on user, group, IP to user mapping, Ongoing user addition updating updates the user status, Bulk update on the users, roles
- 34. Technology Integrations • Identity and access management as a Service (IDaaS) • Useful in traffic redirection in the case of reverse proxy • Cloud applications single sign-on(SSO) • Advantage: traffic redirection. Bulk update and ongoing update for user, roles. • SAML and OAuth: Single Sign-on tokens, used in allow user to authenticate at identity provider • Security information and event management (SIEM) integration • Provides visibility • Active Sync proxy
- 35. CASB Deploy mode summary Log based discovery API based (out of band ) Forward proxy( real time) Reverse Proxy( real time) Offline, log is uploaded only sanctioned app those have API support Agent, DNS redirection or chain proxy Web client, sanctioned apps Visibility Yes Yes Yes ( any traffic) Yes Network latency No No yes yes Resource access control No On going and cloud scrubbing (after the fact) yes Yes Compliance No yes Yes Yes Unmanaged device support Yes No No Yes Managed device support Not applicable yes yes yes Data loss prevention and data protection Encryption No Yes, on going and cloud scrubbing yes yes Managed device support No applicable yes yes yes
- 36. CASB Deploy mode summary Log based discovery API based (out of band ) Forward proxy( real time) Reverse Proxy( real time) Enterprise and cloud integration (IAM and IDaaS) yes yes Yes SaaS Native client support Not applicable yes yes No Continuous Monitoring Yes ( tap mode) yes yes Yes Single point of failure Not applicable No Yes Yes Secure IaaS, PaaS and SaaS Yes Yes Focused on SaaS Focused on SaaS
- 37. Choose your CASB for SaaS highway • Every deployment mode has pros and cons • The sequence • Start with log-based discovery • Then chose either API and/or finally proxy based • Multimode CASB • If an organization has NGFW and SWG on premises then add log-based discovery and API-based CASB • If your concern is about many unmanaged devices/mobiles and sanctioned apps, probably reverse proxy based is better. • If it is more of organization and managed devices, forward proxy plus API is best approach. Most organizations will put multimode CASB
- 38. Cloud glossary • Web app: • Only used by web browser and have a combination of server side and client side script. Online shopping, webEx, eBay and more • Cloud app : • Service delivered by cloud that can be deceived by web browser or a native client. In most cases web interface is used as alternative methods. Cloud app example is: outlook on your mac/window or office 365 login, box, Evernote, salesforce and more. • Data can be accessed in offline mode by download is locally and can be synched periodically. • Shadow IT: • A user targeted cloud app or unseasoned app used organization personal without organization IT approval.
- 39. Cloud glossary • Structured and Unstructured data : • Structure data: A data with columns and can be easily searchable by basic algorithms. Examples include spreadsheets and relational databases. • Unstructured data is like human use and searching is hard. Example is emails, binary, word docs, social media posts, images, audio and more • Identity and Access Management (IAM) • It is mission critical security practice that ensure the enables the right individuals to access the right resources at the right times for the right reasons.1 • IAM solution providers are Okta, onelogin, PingIdetity, Centrify • Identity as a service (IDaaS) • An IAM cloud based service, that is used by an organization to authentic a user or service using Single Sign-on(SSO using SAML or OIDC) for multiple software and cloud-based applications. It can be for multi-tenant or dedicated organizations.
- 40. Cloud glossary • XaaS: Anything as a Service • DaaS : Desktop as a Service • IaaS: Infrastructure as a Service • SaaS: Software as a Service • BDaaS: Bigdata as a Service • HDaaS: HaDoop as a Service • BaaS : Backup as a Service • SCaaS : Security as a Service • MaaS : Monitoring as a Service • DRaaS : Disaster recovery as a Service
Editor's Notes
- #40: 1 Garners definition