CNIT 128 3. Attacking iOS Applications (Part 1)
0 likes351 views
For a college class: Hacking Mobile Devices at CCSF Based on "The Mobile Application Hacker's Handbook 1st Edition", by Dominic Chell Instructor: Sam Bowne More info: https://samsclass.info/128/128_S19.shtml
1 of 44
Download to read offline











































Ad
Recommended
CNIT 141: 13. TLS



CNIT 141: 13. TLSSam Bowne For a college course -- CNIT 141: Cryptography for Computer Networks, at City College San Francisco
Based on "Serious Cryptography: A Practical Introduction to Modern Encryption", by Jean-Philippe Aumasson, No Starch Press (November 6, 2017), ISBN-10: 1593278268 ISBN-13: 978-1593278267
Instructor: Sam Bowne
More info: https://samsclass.info/141/141_S19.shtml
CNIT 129S Ch 7: Attacking Session Management



CNIT 129S Ch 7: Attacking Session ManagementSam Bowne This document provides an overview of securing session management and discusses vulnerabilities in session tokens. It describes how session tokens can be attacked by predicting, modifying, or stealing them. It also discusses weaknesses related to how tokens are generated, transmitted, handled by applications, and terminated. The document recommends generating strong, unpredictable tokens and protecting them throughout their lifecycle to help secure session management.
CNIT 141: 13. TLS



CNIT 141: 13. TLSSam Bowne This document discusses Transport Layer Security (TLS), a cryptographic protocol that provides secure communication over the internet. It summarizes TLS 1.3 improvements such as removing weak algorithms, removing insecure features like compression, adding downgrade protection and enabling a single round-trip handshake. The document also outlines how TLS authenticates servers with certificates and certificate authorities, provides forward secrecy to protect past and current sessions, and how things can still go wrong with compromised certificate authorities or implementation bugs.
CNIT 126: Ch 2 & 3



CNIT 126: Ch 2 & 3Sam Bowne Practical Malware Analysis
2: Malware Analysis in Virtual Machines
3: Basic Dynamic Analysis
More info: https://samsclass.info/126/126_S21.shtml#schedule
Ch 6: Attacking Authentication



Ch 6: Attacking AuthenticationSam Bowne This document provides a summary of authentication techniques and common vulnerabilities. It discusses how over 90% of applications use usernames and passwords for authentication. More secure authentication methods like two-factor authentication are also described. The document outlines various authentication protocols like HTTP, SAML, and JWT. It then details common design flaws such as weak passwords, password change vulnerabilities, account recovery issues, and information leakage. Specific attacks like brute force, credential stuffing, and session hijacking are examined. The summary recommends approaches to secure authentication like strong credentials, hashing passwords, multi-factor authentication, and logging authentication events.
CNIT 141: 1. Encryption



CNIT 141: 1. EncryptionSam Bowne This document provides an overview of cryptography topics for computer networks, including the basics of encryption with keys and ciphertexts. It discusses classical ciphers like the Caesar cipher and the Vigenere cipher. It also covers modern symmetric ciphers, the one-time pad, encryption security models, asymmetric encryption, and ways encryption can be used beyond just encrypting data, as well as how implementations can potentially go wrong.
penetration test using Kali linux ppt



penetration test using Kali linux pptAbhayNaik8 This document discusses penetration testing using Kali Linux. It introduces Kali Linux as a Debian-based Linux distribution for penetration testing and security auditing. It describes penetration testing as simulating attacks on systems to identify vulnerabilities. The document then outlines the methodology for penetration testing using Kali Linux, including information gathering, scanning, exploitation, and post-exploitation maintenance of access. It concludes that Kali Linux is a useful free tool for penetration testers to identify security issues.
Practical Malware Analysis Ch 14: Malware-Focused Network Signatures



Practical Malware Analysis Ch 14: Malware-Focused Network SignaturesSam Bowne This document discusses techniques for analyzing malware network signatures and developing effective network countermeasures. It describes using firewalls, proxies, and intrusion detection systems to filter malicious traffic. Deep packet inspection can detect malware beacons hidden in layers like HTTP user-agents. The document advises passively monitoring real infected networks to understand malware without tipping off attackers. It also provides methods for safely investigating attackers online anonymously. Analyzing how malware generates domain names and URLs can reveal signatures to detect similar strains. The goal is to create general signatures that still work if the malware evolves while avoiding false positives.
Ch 7: Attacking Session Management



Ch 7: Attacking Session ManagementSam Bowne This document provides a summary of session management vulnerabilities. It discusses how session management enables identifying users across multiple requests and is thus a prime target for attackers. Potential consequences of session management attacks include impersonating other users or escalating privileges. The document then covers specific weaknesses like predictable or encrypted tokens, time-dependent values, and weak random number generation that can be exploited. It also addresses issues like tokens being transmitted without encryption, stolen via network sniffing, or exposed by not fully using HTTPS. Overall, the summary highlights how session management is critical to security and important to attack.
Hack Attack! An Introduction to Penetration Testing



Hack Attack! An Introduction to Penetration TestingSteve Phillips This document provides an introduction to penetration testing and ethical hacking. It discusses how hacking can be done ethically through penetration testing with permission. It outlines the stages of a hacker's skills from script kiddie to uberhacker. Popular programming languages for creating hacking tools like C, Python, and Ruby are also mentioned. The document demonstrates some hacking tools in BackTrack Linux like sniffing passwords with Ettercap and bruteforcing FTP passwords with Hydra. It emphasizes how virtualization allows one to practice hacking legally and provides further learning resources.
BSIDES-PR Keynote Hunting for Bad Guys



BSIDES-PR Keynote Hunting for Bad GuysJoff Thyer This document discusses techniques for hunting bad guys on networks, including identifying client-side attacks, malware command and control channels, post-exploitation activities, and hunting artifacts. It provides examples of using DNS logs, firewall logs, HTTP logs, registry keys, installed software inventories, and the AMCache registry hive to look for anomalous behaviors that could indicate security compromises. The goal is to actively hunt for threats rather than just detecting known bad behaviors.
Kali presentation



Kali presentationZain Ul abadin kali operating system LINUX UNIX MAC Window presentation ubanto MAC KAli features compare of kali and unix in hindi easy present ppt slideshare tolls hacking penetration ethical hacking KALI top ten feature best hacking tool
BlueHat v17 || Disrupting the Mirai Botnet 



BlueHat v17 || Disrupting the Mirai Botnet BlueHat Security Conference Chuck McAuley, Ixia Communications
The Mirai botnet has brought public awareness to the danger of poorly secured embedded devices. Its ability to propagate is fast and reliable. Its impact can be devastating and variants of it will be around for a long time. You need to identify it, stop it, and prevent its spread. I had the opportunity to become familiar with the structure, design, and weaknesses of Mirai and its variants. At this talk you'll learn how to detect members of the botnet, mess with them through various means and setup a safe live fire lab environment for your own amusement. I will demonstrate how to join a C2 server, how to collect new samples for study, and some changes that have occurred since release of the source code. By the end you'll be armed and ready to take the fight to these jerks. Unless you're a botnet operator. Then you'll learn about some of the mistakes you made.
CNIT 125 Ch 4. Security Engineering (Part 2)



CNIT 125 Ch 4. Security Engineering (Part 2)Sam Bowne This document provides a summary of key topics covered in Chapter 4, Part 2 of the CNIT 125 course on information security and CISSP preparation. It discusses cornerstone cryptographic concepts like encryption, decryption, and cryptanalysis. It then covers the history of cryptography, from early techniques like the Caesar cipher and Vigenere square to modern algorithms like AES and RSA. The document also examines types of cryptography like symmetric, asymmetric, hashing and steganography. It analyzes cryptographic attacks such as brute force, social engineering and side-channel attacks. Finally, it discusses implementing cryptography through techniques including digital signatures, SSL/TLS, IPSec and steganography.
BlueHat v17 || Dyre to Trickbot: An Inside Look at TLS-Encrypted Command-And-...



BlueHat v17 || Dyre to Trickbot: An Inside Look at TLS-Encrypted Command-And-...BlueHat Security Conference Andrew Brandt, Symantec
Back in 2014 and 2015, the Dyre (sometimes called Dyreza) Trojan was a distinctive crimeware tool for the simple reason that it appeared to employ, and experiment with, a whole range of sophisticated tactics, techniques and procedures: It was the first Trojan which exclusively employed HTTPS for its C2 traffic; It operated on a modular basis with a small cadre of other malware families, such as the Upatre downloader, which seemed to support it exclusively, as well as email address scraping tools and spam mail relayers; and it was at least as interested in profiling the environment it had infected as it was in exfiltrating any data it could find on the victim's machine. Then it disappeared suddenly, but re-emerged this year in the form of a Trojan now called Trickbot (aka Trickybot), completely rewritten but with many of the same features. In the lab, we permit Trickbot samples to persist on infected machines for days to weeks in order to perform man-in-the-middle SSL decryption on their C2 traffic. In this session, attendees will get a detailed forensic analysis of the content of some of this C2 traffic and the endpoint behavior of various machines (virtual and bare-metal) when left infected for an extended period of time. Finally, we will share what we know about the botnet's C2 infrastructure and its historical reputation. By understanding how Trickbot functions, and to where it communicates, we hope we can help identify infections more rapidly and, maybe, interpret the motives of whoever is operating this shadowy botnet to predict its next course of action.
Anatomy of a Cloud Hack



Anatomy of a Cloud HackNotSoSecure Global Services This document discusses anatomy of cloud hacks by analyzing past data breaches and vulnerabilities. It begins by looking at known attacks where compromised infrastructure was based in the cloud. Specific case studies of attacks on Code Spaces, Olindata, and Tesla are described. The document then covers techniques for enumerating cloud services and resources like storage containers. Methods for gaining an initial foothold like leaked credential hunting and exploiting server-side request forgery are also outlined.
Sullivan white boxcrypto-baythreat-2013



Sullivan white boxcrypto-baythreat-2013Cloudflare In this talk, we discuss white box cryptography, a technique used to protect cryptographic keys from a local attacker. In keeping with the theme of building and breaking security, we will discuss the challenges involved in building a white-box crypto system.
Kali linux and some features [view in Full screen mode]![Kali linux and some features [view in Full screen mode]](https://cdn.slidesharecdn.com/ss_thumbnails/kali-171205224458-thumbnail.jpg?width=560&fit=bounds)
![Kali linux and some features [view in Full screen mode]](https://cdn.slidesharecdn.com/ss_thumbnails/kali-171205224458-thumbnail.jpg?width=560&fit=bounds)
![Kali linux and some features [view in Full screen mode]](https://cdn.slidesharecdn.com/ss_thumbnails/kali-171205224458-thumbnail.jpg?width=560&fit=bounds)
![Kali linux and some features [view in Full screen mode]](https://cdn.slidesharecdn.com/ss_thumbnails/kali-171205224458-thumbnail.jpg?width=560&fit=bounds)
Kali linux and some features [view in Full screen mode]abdou Bahassou This is a short presentation about Kali Linux and some of it's features , some reasons why i should use Linux in general and more ...
Kali Linux



Kali LinuxChanchal Dabriya Kali Linux is a Debian-derived Linux distribution designed for digital forensics and penetration testing. It contains over 300 security tools and can run on various hardware architectures. Kali is an updated version of BackTrack, which it replaced in 2013 to address dependency issues. Some key tools included are nmap, Wireshark, John the Ripper, and Aircrack-ng. It is maintained by Offensive Security and intended to perform tests from an attacker's perspective to evaluate system vulnerabilities.
Learn Ethical Hacking With Kali Linux | Ethical Hacking Tutorial | Kali Linux...



Learn Ethical Hacking With Kali Linux | Ethical Hacking Tutorial | Kali Linux...Edureka! ( ** Edureka Online Training: https://www.edureka.co/cybersecurity-certification-training ** )
This Edureka "Ethical Hacking using Kali Linux" video will give you an introduction to Ethical Hacking and Kali Linux. This video will give you an exhaustive video on the fundamentals of Kali Linux and teach how to use the operating system along with its various tools. Below are the topics in this video:
What is ethical hacking?
What is Kali Linux?
Why use Kali Linux?
Command Line Essentials
Proxychains
Macchanger
Wireless Penetration Testing
Cracking WPA2 using Aircrack-ng & Crunch
Instagram: https://www.instagram.com/edureka_lea...
Facebook: https://www.facebook.com/edurekaIN/
Twitter: https://twitter.com/edurekain
LinkedIn: https://www.linkedin.com/company/edureka
Cryptography



CryptographySri Manakula Vinayagar Engineering College This document provides an overview of cryptography concepts including:
- Cryptography is the science of securing communication by encrypting information into an unreadable format.
- The main goals of cryptography are confidentiality, integrity, availability, non-repudiation, authentication, and digital signatures.
- There are two main types of cryptosystems - symmetric cryptography which uses the same key for encryption and decryption, and asymmetric cryptography which uses public/private key pairs.
- Popular symmetric algorithms include AES and RSA is an example of an asymmetric algorithm. Tools for encrypting data include BitLocker, LastPass, VeraCrypt and FileVault2. End-to-end encryption provides the most secure communication by
Path of Cyber Security



Path of Cyber SecuritySatria Ady Pradana The document discusses the path of cyber security and how to become a hacker or security professional. It outlines the typical steps of penetration testing: reconnaissance and analysis, vulnerability mapping, gaining access, privilege escalation, maintaining access, and covering tracks. It recommends starting with networking and programming skills, focusing on an area of expertise like web security, participating in competitions and creating a practice lab to learn. The presenter gives demonstrations on vulnerable VMs and recommends courses, CTF competitions, and building your own lab to advance your skills in security research, tool development, and operations.
Bypass Security Checking with Frida



Bypass Security Checking with FridaSatria Ady Pradana Small discussion on Echo's Hack In The Zoo (HITZ) 2017
Ragunan Zoo Jakarta
Jakarta, 2017-09-09
Frida? It's a Dynamic Binary Instrumentation. DBI.
Let's see what frida can do for us, reverse engineer.
Parrot Security OS | Introduction to Parrot Security OS | Cybersecurity Train...



Parrot Security OS | Introduction to Parrot Security OS | Cybersecurity Train...Edureka! (** Cyber Security Course: https://www.edureka.co/cybersecurity-certification-training **)
This ‘Parrot Security OS’ PPT by Edureka will help you learn all about one of the topmost Linux distribution for ethical hacking – Parrot Security OS.
Below is the list of topics covered in this session:
Linux Distributions for Ethical Hacking
Parrot Security OS
Kali Linux vs Parrot Security OS
How to install Parrot Security?
Parrot Security OS Tools
Cyber Security Playlist: https://bit.ly/2N2jlNN
Cyber Security Blog Series: https://bit.ly/2AuULkP
Instagram: https://www.instagram.com/edureka_lea...
Facebook: https://www.facebook.com/edurekaIN/
Twitter: https://twitter.com/edurekain
LinkedIn: https://www.linkedin.com/company/edureka
Sullivan randomness-infiltrate 2014



Sullivan randomness-infiltrate 2014Cloudflare Many information security systems rely on cryptographic schemes that need truly random numbers be secure. In recent months there have been several high profile news stories about weaknesses or potential compromises in both software and hardware random number generators. A compromised random number generator is difficult to catch because it can output random looking data that is predictable to an attacker only. In this talk I describe how to go from knowledge of a weakness in a random number generator to a full security compromise.
We will look at examples including how to fully decrypt a TLS stream, how to compromise a bitcoin wallet by looking at the ECDSA signatures on the public block chain, how to factor improperly generated RSA keys, and more. There will be live demos and discussions of interesting ways to pull off these attacks.
CNIT 121: 14 Investigating Applications



CNIT 121: 14 Investigating ApplicationsSam Bowne Slides for a college course based on "Incident Response & Computer Forensics, Third Edition" by by Jason Luttgens, Matthew Pepe, and Kevin Mandia.
Teacher: Sam Bowne
Twitter: @sambowne
Website: https://samsclass.info/121/121_F16.shtml
Practical Malware Analysis: Ch 2 Malware Analysis in Virtual Machines & 3: Ba...



Practical Malware Analysis: Ch 2 Malware Analysis in Virtual Machines & 3: Ba...Sam Bowne This document discusses using virtual machines for safe dynamic malware analysis. It recommends using a virtual machine to run malware in a protected environment isolated from the host system. Specific virtualization software discussed includes VMware Player, Workstation and Fusion along with VirtualBox and Hyper-V. The document outlines techniques for configuring networking and taking snapshots in virtual machines for malware analysis. It also introduces tools for dynamic analysis within virtual machines like Process Monitor, Process Explorer, Regshot, INetSim and Wireshark that can monitor the behavior and network activity of malware samples.
External to DA, the OS X Way



External to DA, the OS X WayStephan Borosh The document provides an overview of techniques for penetrating OS X environments externally, including using the EmPyre remote access Trojan, phishing with OS X payloads, privilege escalation, persistence mechanisms like login hooks and crontab, host and network reconnaissance tools, and lateral movement options like SSH. The challenges of operating in an OS X environment and adapting typical Windows tactics are also discussed.
Owasp Mobile Risk Series : M3 : Insufficient Transport Layer Protection



Owasp Mobile Risk Series : M3 : Insufficient Transport Layer ProtectionAnant Shrivastava This Session will focus on Mobile Top 10 2014-M3 : Insufficient Transport Layer protection. We will try to understand Transport Layer, Transport layer security (TLS), insecurities in TLS/SSL, and how this affects the overall security of Mobile Devices as well as what kind of protection can be applied and how this can be identified..
Shifting security left simplifying security for k8s open shift environments



Shifting security left simplifying security for k8s open shift environmentsLibbySchulze This document discusses securing secrets in Kubernetes. It describes how attackers were able to hijack cloud resources by accessing unprotected credentials stored in a Kubernetes console. It then provides recommendations for securely managing secrets, including using Conjur to establish identity for applications and enforce authorization. It outlines best practices like regularly rotating secrets and removing hard-coded credentials. The document also describes how Conjur can integrate with Kubernetes to verify application identities and issue credentials without exposing secrets.
More Related Content
What's hot (20)
Ch 7: Attacking Session Management



Ch 7: Attacking Session ManagementSam Bowne This document provides a summary of session management vulnerabilities. It discusses how session management enables identifying users across multiple requests and is thus a prime target for attackers. Potential consequences of session management attacks include impersonating other users or escalating privileges. The document then covers specific weaknesses like predictable or encrypted tokens, time-dependent values, and weak random number generation that can be exploited. It also addresses issues like tokens being transmitted without encryption, stolen via network sniffing, or exposed by not fully using HTTPS. Overall, the summary highlights how session management is critical to security and important to attack.
Hack Attack! An Introduction to Penetration Testing



Hack Attack! An Introduction to Penetration TestingSteve Phillips This document provides an introduction to penetration testing and ethical hacking. It discusses how hacking can be done ethically through penetration testing with permission. It outlines the stages of a hacker's skills from script kiddie to uberhacker. Popular programming languages for creating hacking tools like C, Python, and Ruby are also mentioned. The document demonstrates some hacking tools in BackTrack Linux like sniffing passwords with Ettercap and bruteforcing FTP passwords with Hydra. It emphasizes how virtualization allows one to practice hacking legally and provides further learning resources.
BSIDES-PR Keynote Hunting for Bad Guys



BSIDES-PR Keynote Hunting for Bad GuysJoff Thyer This document discusses techniques for hunting bad guys on networks, including identifying client-side attacks, malware command and control channels, post-exploitation activities, and hunting artifacts. It provides examples of using DNS logs, firewall logs, HTTP logs, registry keys, installed software inventories, and the AMCache registry hive to look for anomalous behaviors that could indicate security compromises. The goal is to actively hunt for threats rather than just detecting known bad behaviors.
Kali presentation



Kali presentationZain Ul abadin kali operating system LINUX UNIX MAC Window presentation ubanto MAC KAli features compare of kali and unix in hindi easy present ppt slideshare tolls hacking penetration ethical hacking KALI top ten feature best hacking tool
BlueHat v17 || Disrupting the Mirai Botnet 



BlueHat v17 || Disrupting the Mirai Botnet BlueHat Security Conference Chuck McAuley, Ixia Communications
The Mirai botnet has brought public awareness to the danger of poorly secured embedded devices. Its ability to propagate is fast and reliable. Its impact can be devastating and variants of it will be around for a long time. You need to identify it, stop it, and prevent its spread. I had the opportunity to become familiar with the structure, design, and weaknesses of Mirai and its variants. At this talk you'll learn how to detect members of the botnet, mess with them through various means and setup a safe live fire lab environment for your own amusement. I will demonstrate how to join a C2 server, how to collect new samples for study, and some changes that have occurred since release of the source code. By the end you'll be armed and ready to take the fight to these jerks. Unless you're a botnet operator. Then you'll learn about some of the mistakes you made.
CNIT 125 Ch 4. Security Engineering (Part 2)



CNIT 125 Ch 4. Security Engineering (Part 2)Sam Bowne This document provides a summary of key topics covered in Chapter 4, Part 2 of the CNIT 125 course on information security and CISSP preparation. It discusses cornerstone cryptographic concepts like encryption, decryption, and cryptanalysis. It then covers the history of cryptography, from early techniques like the Caesar cipher and Vigenere square to modern algorithms like AES and RSA. The document also examines types of cryptography like symmetric, asymmetric, hashing and steganography. It analyzes cryptographic attacks such as brute force, social engineering and side-channel attacks. Finally, it discusses implementing cryptography through techniques including digital signatures, SSL/TLS, IPSec and steganography.
BlueHat v17 || Dyre to Trickbot: An Inside Look at TLS-Encrypted Command-And-...



BlueHat v17 || Dyre to Trickbot: An Inside Look at TLS-Encrypted Command-And-...BlueHat Security Conference Andrew Brandt, Symantec
Back in 2014 and 2015, the Dyre (sometimes called Dyreza) Trojan was a distinctive crimeware tool for the simple reason that it appeared to employ, and experiment with, a whole range of sophisticated tactics, techniques and procedures: It was the first Trojan which exclusively employed HTTPS for its C2 traffic; It operated on a modular basis with a small cadre of other malware families, such as the Upatre downloader, which seemed to support it exclusively, as well as email address scraping tools and spam mail relayers; and it was at least as interested in profiling the environment it had infected as it was in exfiltrating any data it could find on the victim's machine. Then it disappeared suddenly, but re-emerged this year in the form of a Trojan now called Trickbot (aka Trickybot), completely rewritten but with many of the same features. In the lab, we permit Trickbot samples to persist on infected machines for days to weeks in order to perform man-in-the-middle SSL decryption on their C2 traffic. In this session, attendees will get a detailed forensic analysis of the content of some of this C2 traffic and the endpoint behavior of various machines (virtual and bare-metal) when left infected for an extended period of time. Finally, we will share what we know about the botnet's C2 infrastructure and its historical reputation. By understanding how Trickbot functions, and to where it communicates, we hope we can help identify infections more rapidly and, maybe, interpret the motives of whoever is operating this shadowy botnet to predict its next course of action.
Anatomy of a Cloud Hack



Anatomy of a Cloud HackNotSoSecure Global Services This document discusses anatomy of cloud hacks by analyzing past data breaches and vulnerabilities. It begins by looking at known attacks where compromised infrastructure was based in the cloud. Specific case studies of attacks on Code Spaces, Olindata, and Tesla are described. The document then covers techniques for enumerating cloud services and resources like storage containers. Methods for gaining an initial foothold like leaked credential hunting and exploiting server-side request forgery are also outlined.
Sullivan white boxcrypto-baythreat-2013



Sullivan white boxcrypto-baythreat-2013Cloudflare In this talk, we discuss white box cryptography, a technique used to protect cryptographic keys from a local attacker. In keeping with the theme of building and breaking security, we will discuss the challenges involved in building a white-box crypto system.
Kali linux and some features [view in Full screen mode]![Kali linux and some features [view in Full screen mode]](https://cdn.slidesharecdn.com/ss_thumbnails/kali-171205224458-thumbnail.jpg?width=560&fit=bounds)
![Kali linux and some features [view in Full screen mode]](https://cdn.slidesharecdn.com/ss_thumbnails/kali-171205224458-thumbnail.jpg?width=560&fit=bounds)
![Kali linux and some features [view in Full screen mode]](https://cdn.slidesharecdn.com/ss_thumbnails/kali-171205224458-thumbnail.jpg?width=560&fit=bounds)
![Kali linux and some features [view in Full screen mode]](https://cdn.slidesharecdn.com/ss_thumbnails/kali-171205224458-thumbnail.jpg?width=560&fit=bounds)
Kali linux and some features [view in Full screen mode]abdou Bahassou This is a short presentation about Kali Linux and some of it's features , some reasons why i should use Linux in general and more ...
Kali Linux



Kali LinuxChanchal Dabriya Kali Linux is a Debian-derived Linux distribution designed for digital forensics and penetration testing. It contains over 300 security tools and can run on various hardware architectures. Kali is an updated version of BackTrack, which it replaced in 2013 to address dependency issues. Some key tools included are nmap, Wireshark, John the Ripper, and Aircrack-ng. It is maintained by Offensive Security and intended to perform tests from an attacker's perspective to evaluate system vulnerabilities.
Learn Ethical Hacking With Kali Linux | Ethical Hacking Tutorial | Kali Linux...



Learn Ethical Hacking With Kali Linux | Ethical Hacking Tutorial | Kali Linux...Edureka! ( ** Edureka Online Training: https://www.edureka.co/cybersecurity-certification-training ** )
This Edureka "Ethical Hacking using Kali Linux" video will give you an introduction to Ethical Hacking and Kali Linux. This video will give you an exhaustive video on the fundamentals of Kali Linux and teach how to use the operating system along with its various tools. Below are the topics in this video:
What is ethical hacking?
What is Kali Linux?
Why use Kali Linux?
Command Line Essentials
Proxychains
Macchanger
Wireless Penetration Testing
Cracking WPA2 using Aircrack-ng & Crunch
Instagram: https://www.instagram.com/edureka_lea...
Facebook: https://www.facebook.com/edurekaIN/
Twitter: https://twitter.com/edurekain
LinkedIn: https://www.linkedin.com/company/edureka
Cryptography



CryptographySri Manakula Vinayagar Engineering College This document provides an overview of cryptography concepts including:
- Cryptography is the science of securing communication by encrypting information into an unreadable format.
- The main goals of cryptography are confidentiality, integrity, availability, non-repudiation, authentication, and digital signatures.
- There are two main types of cryptosystems - symmetric cryptography which uses the same key for encryption and decryption, and asymmetric cryptography which uses public/private key pairs.
- Popular symmetric algorithms include AES and RSA is an example of an asymmetric algorithm. Tools for encrypting data include BitLocker, LastPass, VeraCrypt and FileVault2. End-to-end encryption provides the most secure communication by
Path of Cyber Security



Path of Cyber SecuritySatria Ady Pradana The document discusses the path of cyber security and how to become a hacker or security professional. It outlines the typical steps of penetration testing: reconnaissance and analysis, vulnerability mapping, gaining access, privilege escalation, maintaining access, and covering tracks. It recommends starting with networking and programming skills, focusing on an area of expertise like web security, participating in competitions and creating a practice lab to learn. The presenter gives demonstrations on vulnerable VMs and recommends courses, CTF competitions, and building your own lab to advance your skills in security research, tool development, and operations.
Bypass Security Checking with Frida



Bypass Security Checking with FridaSatria Ady Pradana Small discussion on Echo's Hack In The Zoo (HITZ) 2017
Ragunan Zoo Jakarta
Jakarta, 2017-09-09
Frida? It's a Dynamic Binary Instrumentation. DBI.
Let's see what frida can do for us, reverse engineer.
Parrot Security OS | Introduction to Parrot Security OS | Cybersecurity Train...



Parrot Security OS | Introduction to Parrot Security OS | Cybersecurity Train...Edureka! (** Cyber Security Course: https://www.edureka.co/cybersecurity-certification-training **)
This ‘Parrot Security OS’ PPT by Edureka will help you learn all about one of the topmost Linux distribution for ethical hacking – Parrot Security OS.
Below is the list of topics covered in this session:
Linux Distributions for Ethical Hacking
Parrot Security OS
Kali Linux vs Parrot Security OS
How to install Parrot Security?
Parrot Security OS Tools
Cyber Security Playlist: https://bit.ly/2N2jlNN
Cyber Security Blog Series: https://bit.ly/2AuULkP
Instagram: https://www.instagram.com/edureka_lea...
Facebook: https://www.facebook.com/edurekaIN/
Twitter: https://twitter.com/edurekain
LinkedIn: https://www.linkedin.com/company/edureka
Sullivan randomness-infiltrate 2014



Sullivan randomness-infiltrate 2014Cloudflare Many information security systems rely on cryptographic schemes that need truly random numbers be secure. In recent months there have been several high profile news stories about weaknesses or potential compromises in both software and hardware random number generators. A compromised random number generator is difficult to catch because it can output random looking data that is predictable to an attacker only. In this talk I describe how to go from knowledge of a weakness in a random number generator to a full security compromise.
We will look at examples including how to fully decrypt a TLS stream, how to compromise a bitcoin wallet by looking at the ECDSA signatures on the public block chain, how to factor improperly generated RSA keys, and more. There will be live demos and discussions of interesting ways to pull off these attacks.
CNIT 121: 14 Investigating Applications



CNIT 121: 14 Investigating ApplicationsSam Bowne Slides for a college course based on "Incident Response & Computer Forensics, Third Edition" by by Jason Luttgens, Matthew Pepe, and Kevin Mandia.
Teacher: Sam Bowne
Twitter: @sambowne
Website: https://samsclass.info/121/121_F16.shtml
Practical Malware Analysis: Ch 2 Malware Analysis in Virtual Machines & 3: Ba...



Practical Malware Analysis: Ch 2 Malware Analysis in Virtual Machines & 3: Ba...Sam Bowne This document discusses using virtual machines for safe dynamic malware analysis. It recommends using a virtual machine to run malware in a protected environment isolated from the host system. Specific virtualization software discussed includes VMware Player, Workstation and Fusion along with VirtualBox and Hyper-V. The document outlines techniques for configuring networking and taking snapshots in virtual machines for malware analysis. It also introduces tools for dynamic analysis within virtual machines like Process Monitor, Process Explorer, Regshot, INetSim and Wireshark that can monitor the behavior and network activity of malware samples.
External to DA, the OS X Way



External to DA, the OS X WayStephan Borosh The document provides an overview of techniques for penetrating OS X environments externally, including using the EmPyre remote access Trojan, phishing with OS X payloads, privilege escalation, persistence mechanisms like login hooks and crontab, host and network reconnaissance tools, and lateral movement options like SSH. The challenges of operating in an OS X environment and adapting typical Windows tactics are also discussed.
BlueHat v17 || Dyre to Trickbot: An Inside Look at TLS-Encrypted Command-And-...



BlueHat v17 || Dyre to Trickbot: An Inside Look at TLS-Encrypted Command-And-...BlueHat Security Conference
Similar to CNIT 128 3. Attacking iOS Applications (Part 1) (20)
Owasp Mobile Risk Series : M3 : Insufficient Transport Layer Protection



Owasp Mobile Risk Series : M3 : Insufficient Transport Layer ProtectionAnant Shrivastava This Session will focus on Mobile Top 10 2014-M3 : Insufficient Transport Layer protection. We will try to understand Transport Layer, Transport layer security (TLS), insecurities in TLS/SSL, and how this affects the overall security of Mobile Devices as well as what kind of protection can be applied and how this can be identified..
Shifting security left simplifying security for k8s open shift environments



Shifting security left simplifying security for k8s open shift environmentsLibbySchulze This document discusses securing secrets in Kubernetes. It describes how attackers were able to hijack cloud resources by accessing unprotected credentials stored in a Kubernetes console. It then provides recommendations for securely managing secrets, including using Conjur to establish identity for applications and enforce authorization. It outlines best practices like regularly rotating secrets and removing hard-coded credentials. The document also describes how Conjur can integrate with Kubernetes to verify application identities and issue credentials without exposing secrets.
Hacking mobile apps



Hacking mobile appskunwaratul hax0r This presentation contains android and iOS pentesting resources and methods to test the applications.
CNIT 128 7. Attacking Android Applications (Part 2)



CNIT 128 7. Attacking Android Applications (Part 2)Sam Bowne This document discusses attacking Android application components and exploiting insecure communications. It describes how application components like activities, services, and content providers can be vulnerable if not properly secured. Specific vulnerabilities discussed include insecure content providers exposing private data, SQL injection in content provider queries, abusing started services, exploiting insecure bound services, and intent sniffing from unprotected broadcast receivers. Examples are provided of exploiting these vulnerabilities in the Open Sieve Android app.
KKBOX WWDC17 Security - Antony



KKBOX WWDC17 Security - AntonyLiyao Chen This document summarizes the WWDC 2017 reading session. It discusses topics around network security standards, privacy and apps, advances in networking technology, and new features for Apple Pay Wallet. Specific areas covered include app transport security, privacy prompts, location services, device check, multipath TCP, URL session updates, and enhanced support for donations and error handling in Apple Pay.
CNIT 128 7. Attacking Android Applications (Part 2)



CNIT 128 7. Attacking Android Applications (Part 2)Sam Bowne For a college class: Hacking Mobile Devices at CCSF
Instructor: Sam Bowne
More info: https://samsclass.info/128/128_S19.shtml
Webservice security considerations and measures



Webservice security considerations and measuresMaarten Smeets Security is a hot topic, especially with new laws concerning how to deal with personally identifiable information (PII) and the journey to the cloud many organisations are making. When implemented correctly, security measures can protect your company from people trying to spy on you or manipulate your systems. Security can be implemented at different layers. In this presentation I'll zoom in on webservices and which choices there are to make on the application layer and transport layer. This spans area's like authentication, keys/keystores, OWSM policy choices, WebLogic SSL configuration and cipher suite choices. Security measures are even more relevant in cloud integration scenario's since services might not just be accessible from your internal network. After this presentation, architects and developers will have a good idea on how to quickly get started with taking security measures.
Jenkins Terraform Vault



Jenkins Terraform VaultShrivatsa Upadhye The 3 Muskeeters: Jenkins Terraform Vault:
Deploying applications securely in multi-cloud environments can get overwhelming very quickly. This is where Infrastructure as code comes to your rescue. You might be already looking at Terraform or better yet, using it.
In this talk, we will learn how to secure your Cloud and application keys with "Vault" and extend that to integrate with Jenkins and Terraform. This would allow the DevOps engineer to truly "build, test, deploy, manage and secure" the infrastructure from one place.
We will look at a quick demo of these 3 tools working together and understand some of the best practices around them.
CNIT 129S: 10: Attacking Back-End Components



CNIT 129S: 10: Attacking Back-End ComponentsSam Bowne This document discusses various attacks against backend components in web applications, including command injection, path traversal, file inclusion, XML external entity injection (XXE), SOAP injection, HTTP parameter injection, SMTP injection, and more. It provides examples of each attack and recommendations for prevention, such as input validation, output encoding, and restricting file system and network access.
Hybrid - Seguridad en Contenedores v3.pptx



Hybrid - Seguridad en Contenedores v3.pptxHansFarroCastillo1 The document discusses security considerations for containers in cloud platforms. It covers several areas:
1. Cloud security categorization including access control, network security, platform security, application security, and data security.
2. Application platform security layers including physical, virtual private cloud, public cloud, container runtime layer, image registry, cluster layer, and code layer.
3. Container security workflow including CI/CD, cluster security, container security, node security, operating system, container runtime, and code security.
"Mobile security: iOS", Yaroslav Vorontsov, DataArt



"Mobile security: iOS", Yaroslav Vorontsov, DataArtDataArt Yaroslav talks more about Mobile Security and his experience doing it on iOS platforms.
You can see his full lecture here: https://www.youtube.com/watch?v=_f7pmwi0yfs
Yaroslav Vorontsov works as a software architect at DataArt. Over the course of his professional career, he has taken part in many projects from different industrial domains, managed to grow from an intern to a tech lead quickly. He has also won two major prizes at two consecutive THacks in Berlin as a member of DataArt teams, participated in local developers’ communities and taught about 100 students in total for 3 years at the university. When he's not working, Yaroslav enjoys playing and watching football, and exploring new countries with his wife.
IT talk is an open community, where anyone interested in technologies can participate. It is a real opportunity for IT professionals, teachers, students and even novice developers to share knowledge, network & discuss technical solutions and even present them at the next IT Talk seminars!
Website: http://dataart.bg/
Facebook: https://www.facebook.com/dataartbulgaria/
YouTube: https://www.youtube.com/channel/UCFYE6-NmhDFhFtx4gGkHXGQ
9 Writing Secure Android Applications



9 Writing Secure Android ApplicationsSam Bowne This document discusses various techniques for writing secure Android apps, including minimizing unnecessary permissions and exposure, securing data storage and communication, and making apps difficult to reverse engineer. It provides examples of implementing essential security mechanisms like permission protection and securing activities, content providers, and web views. It also covers more advanced techniques such as protection level downgrades, obfuscation, and tamper detection.
7. Attacking Android Applications (Part 2)



7. Attacking Android Applications (Part 2)Sam Bowne This document summarizes part 2 of a course on attacking Android applications. It discusses how application components like activities and services can be exploited if not properly protected. Specific vulnerabilities in the Sieve password manager application are demonstrated, including insecure content providers, SQL injection, and an insecure file-backed content provider. The document also covers how services and broadcast receivers can be abused if not protected correctly.
Certificate pinning in android applications



Certificate pinning in android applicationsArash Ramez Certificate pinning is a security mechanism where an app specifies certificates from trusted authorities and only accepts connections signed by those certificates. This prevents man-in-the-middle attacks. The document discusses implementing certificate pinning in Android apps by configuring the network security configuration file or using third party libraries like OkHttp that have CertificatePinner classes to restrict which certificates an app will accept. It also describes how to retrieve a server's public key hashes to include in the pinning configuration.
Security Considerations for Microservices and Multi cloud



Security Considerations for Microservices and Multi cloudNeelkamal Gaharwar These slides contains my notes on what are the security consideration w.r.t Micro services and Multi Cloud. I am still working on this part. It is just a comprehension of whatever I have studied so far.
Breaking Secure Mobile Applications - Hack In The Box 2014 KL



Breaking Secure Mobile Applications - Hack In The Box 2014 KLiphonepentest Dominic Chell presents "Breaking Secure Mobile Applications" at Hack In The Box 2014.
This presentation details common vulnerabilities that can be found in supposedly secure applications, including BYOD and MDM apps. It also provides an overview of the binary protections that can be implemented to complicate these types of attacks.
#ALSummit: Architecting Security into your AWS Environment



#ALSummit: Architecting Security into your AWS EnvironmentAlert Logic Ryan Holland (Cloud Platform Solutions Director, Alert Logic)'s presentation on securing your AWS environment at the NYC Alert Logic Cloud Security Summit on June 14, 2016.
Spa Secure Coding Guide



Spa Secure Coding GuideGeoffrey Vandiest Here you can find the slides that accompany my “SPA Secure Coding Guide”, this presentation go through a set of security best practices specially targeted towards developing Angular applications with ASP.Net Web Api backends.
It comes with a WebApi example project available on GitHub that provides several code examples of how to defend yourself. The example app is based on the famous "Tour of Heroes" Angular app used throughout the Angular documentation.
It first introduce general threat modelling before explaining the most current type of attacks Asp.Net Web API are vulnerable to .
It is designed to serve as a secure coding reference guide, to help development teams quickly understand Asp.Net Core secure coding practices.
Mobile code mining for discovery and exploits nullcongoa2013



Mobile code mining for discovery and exploits nullcongoa2013Blueinfy Solutions This document discusses mobile code mining for discovery and exploits. It introduces the speaker, Hemil Shah, and provides an overview of mobile infrastructure, apps, and changes in the mobile environment compared to web. It then discusses several mobile attacks including insecure storage, insecure network communication, UI impersonation, activity monitoring, and system modification. It also covers decompiling Android apps and analyzing app code for security issues.
Ad
More from Sam Bowne (20)
Introduction to the Class & CISSP Certification



Introduction to the Class & CISSP CertificationSam Bowne For a college class. See:
https://samsclass.info/125/125_F24.shtml
Cyberwar



CyberwarSam Bowne The document discusses various topics related to cyberwar including Mastodon, Lockheed-Martin's kill chain model, and Mitre's ATT&CK framework. It notes that China, Russia, Iran, and North Korea pose major cyber threats according to the FBI and CISA. China is described as the broadest cyber espionage threat. Russia conducts destructive malware and ransomware operations. Iran's growing cyber expertise makes it a threat. North Korea's program poses an espionage, cybercrime, and attack threat and continues cryptocurrency heists.
3: DNS vulnerabilities 



3: DNS vulnerabilities Sam Bowne - DNS vulnerabilities can arise from configuration errors, architecture mistakes, vulnerable software implementations, protocol weaknesses, and failure to use security extensions.
- Common mistakes include single points of failure, exposure of internal information, leakage of internal queries, unnecessary recursiveness, failure to restrict access, and unprotected zone transfers.
- Software vulnerabilities have included buffer overflows and flaws in randomization of source ports, transaction IDs, and domain name ordering that enable cache poisoning and man-in-the-middle attacks.
8. Software Development Security



8. Software Development SecuritySam Bowne This chapter discusses software development security. It covers topics like programming concepts, compilers and interpreters, procedural vs object-oriented languages, application development methods like waterfall vs agile models, databases, object-oriented design, assessing software vulnerabilities, and artificial intelligence techniques. The key aspects are securing the entire software development lifecycle from initial planning through operation and disposal, using secure coding practices, testing for vulnerabilities, and continually improving processes.
4 Mapping the Application



4 Mapping the ApplicationSam Bowne For a Securing Web Applications class at college.
More info: https://samsclass.info/129S/129S_S23.shtml
3. Attacking iOS Applications (Part 2)



3. Attacking iOS Applications (Part 2)Sam Bowne This document discusses attacking iOS applications by exploiting vulnerabilities in the iOS runtime, interprocess communication, and through injection attacks. Specifically, it covers instrumenting the iOS runtime using method swizzling, attacking applications using interprocess communication techniques like application extensions, and exploiting entry points like UIWebViews, client-side data stores, and file handling routines to perform injection attacks on iOS apps.
12 Elliptic Curves



12 Elliptic CurvesSam Bowne This document provides an overview of elliptic curve cryptography including what an elliptic curve is, the elliptic curve discrete logarithm problem (ECDLP), Diffie-Hellman key agreement and digital signatures using elliptic curves. It discusses NIST standard curves like P-256 and Curve25519 as well as choosing appropriate curves and potential issues like attacks if randomness is not properly implemented or an invalid curve is used.
11. Diffie-Hellman



11. Diffie-HellmanSam Bowne The document discusses the Diffie-Hellman key exchange protocol. It describes how Diffie-Hellman works by having two parties agree on a shared secret over an insecure channel without transmitting the secret itself. It also covers potential issues like using proper cryptographic techniques to derive keys from the shared secret and using safe prime numbers to prevent attacks.
2a Analyzing iOS Apps Part 1



2a Analyzing iOS Apps Part 1Sam Bowne This document provides an overview of analyzing iOS apps, including jailbreaking mobile devices. It discusses iOS security features like code signing and sandboxing. It explains how to set up a test environment for analyzing apps by jailbreaking a device and using Unix tools. Key files like property lists and databases that can be explored are also outlined.
12 Investigating Windows Systems (Part 2 of 3)



12 Investigating Windows Systems (Part 2 of 3)Sam Bowne The document discusses investigating Windows systems by analyzing the Windows Registry. It describes the purpose and structure of the Registry, including the main hive files and user-specific hives. It provides an overview of important Registry keys that can contain forensic artifacts, such as system configuration keys, network information keys, user and security information keys, and auto-run keys that can indicate malware persistence. Specific Registry keys and values are highlighted that are most useful for analyzing evidence on a compromised system, including ShellBags, UserAssist, MRU lists, and Internet Explorer TypedURLs and TypedPaths. Tools for Registry analysis like RegRipper, AutoRuns, and Nirsoft utilities are also mentioned.
10 RSA



10 RSASam Bowne This document provides an overview of the RSA cryptosystem. It begins with the mathematical foundations of RSA, including the group ZN* and Euler's totient function. It then covers the RSA trapdoor permutation using modular exponentiation and key generation. The document discusses encrypting and signing with RSA, as well as implementations using libraries and algorithms like square-and-multiply. It concludes with topics like side-channel attacks, optimizations for speed, and ways implementations can fail like the Bellcore attack on RSA-CRT.
12 Investigating Windows Systems (Part 1 of 3



12 Investigating Windows Systems (Part 1 of 3Sam Bowne This document provides an overview of analyzing the Windows file system, NTFS metadata, and logs to investigate security incidents and recover deleted files. It discusses the Master File Table (MFT) structure, timestamps, alternate data streams, prefetch files, event logs, and scheduled tasks. The MFT stores file metadata including attributes, timestamps, and data runs. File deletion only marks the MFT entry inactive, allowing recovery of deleted file contents and metadata. Event and security logs can reveal lateral movement and suspicious processes. Prefetch files indicate program execution history. Scheduled tasks configure automated programs through .job files logged by Task Scheduler.
9. Hard Problems



9. Hard ProblemsSam Bowne This document discusses computational hardness and complexity classes related to cryptography. It covers the computational complexity of problems like factoring large numbers and the discrete logarithm problem. These problems are assumed to be hard, even for quantum computers, and form the basis for cryptographic techniques. The document also discusses how cryptography could be broken if faster algorithms were found for these problems or if the key sizes used were too small.
8 Android Implementation Issues (Part 1)



8 Android Implementation Issues (Part 1)Sam Bowne This document discusses exploiting vulnerabilities in Android devices. It covers identifying pre-installed apps that could provide access, techniques for remotely or locally exploiting devices, and the different privilege levels an attacker may obtain including non-system app access, installed package access, ADB shell access, system user access, and root user access. Specific exploitation techniques mentioned include exploiting update mechanisms, remote code loading, webviews, listening services, and messaging apps. Tools discussed include Drozer, Ettercap, and Burp.
11 Analysis Methodology



11 Analysis MethodologySam Bowne This document provides an overview of the incident response analysis methodology process. It discusses defining objectives, understanding the situation and available resources, identifying leadership, avoiding impossible tasks like proving a negative, asking why to define scope, knowing where data is stored, accessing raw data, selecting analysis methods like searching for malware or using tools like VirusTotal, manual review, filtering data, statistical analysis using tools like Sawmill, string searching, analyzing unallocated space, and file carving. It stresses periodically evaluating results to ensure progress and only making definitive statements if supported by evidence.
8. Authenticated Encryption



8. Authenticated EncryptionSam Bowne This document discusses authenticated encryption, which both encrypts messages and authenticates them with a tag. It covers several authenticated encryption schemes:
1. Authenticated Encryption with Associated Data (AEAD) which encrypts a plaintext and authenticates additional associated data with a tag.
2. AES-GCM, the standard authenticated cipher, which uses AES in Galois/Counter Mode. It has two layers - encryption then authentication.
3. OCB, faster than GCM but limited by licensing. It blends encryption and authentication into one layer.
4. SIV, considered the safest as it is secure even if nonces are reused, but it is not streamable.
7. Attacking Android Applications (Part 1)



7. Attacking Android Applications (Part 1)Sam Bowne This document discusses attacking Android applications through their components. It covers exploiting vulnerabilities in an app's security model, intercepting communications, and compromising application containers or internet servers that apps rely on. Specific attacks examined include bypassing the lock screen, tapjacking, accessing private app data through recently used screenshots, and changing a PIN without knowing the old one using fragment injection. The document provides examples of how to interact with an app's activities, services, content providers and permissions through intents and other techniques.
5. Stream Ciphers



5. Stream CiphersSam Bowne The document discusses stream ciphers and how they can be implemented in either hardware or software. It describes how stream ciphers work by generating a pseudorandom bitstream from a key and nonce that is XOR'd with the plaintext. Hardware-oriented stream ciphers were initially more efficient to implement than block ciphers using dedicated circuits like LFSRs. However, LFSR-based designs are insecure and modern software-oriented stream ciphers like Salsa20 are more efficient on CPUs. The document cautions that stream ciphers can be broken if the key and nonce are reused or if there are flaws in the implementation.
6 Scope & 7 Live Data Collection



6 Scope & 7 Live Data CollectionSam Bowne Live data collection on Windows systems can be done using prebuilt kits like Mandiant Redline or Velociraptor, by creating your own scripted toolkit using built-in and free tools to collect processes, network connections, system logs and other volatile data, while following best practices like testing your methods first and being cautious of malware on investigated systems.
4. Block Ciphers 



4. Block Ciphers Sam Bowne Block ciphers like AES encrypt data in fixed-size blocks and use cryptographic keys and rounds of processing to encrypt the data securely. AES is the current standard, using 128-bit blocks and keys of 128, 192, or 256 bits. Modes of operation like ECB, CBC, CTR are used to handle full messages. ECB is insecure as identical plaintext blocks produce identical ciphertext, while CBC and CTR provide security if nonces and IVs are not reused. Implementation details like padding and side channels must be handled carefully to prevent attacks.
Ad
Recently uploaded (20)
Strengthened Senior High School - Landas Tool Kit.pptx



Strengthened Senior High School - Landas Tool Kit.pptxSteffMusniQuiballo Landas Tool Kit is a very helpful guide in guiding the Senior High School students on their SHS academic journey. It will pave the way on what curriculum exits will they choose and fit in.
THERAPEUTIC COMMUNICATION included definition, characteristics, nurse patient...



THERAPEUTIC COMMUNICATION included definition, characteristics, nurse patient...parmarjuli1412 The document provides an overview of therapeutic communication, emphasizing its importance in nursing to address patient needs and establish effective relationships. THERAPEUTIC COMMUNICATION included some topics like introduction of COMMUNICATION, definition, types, process of communication, definition therapeutic communication, goal, techniques of therapeutic communication, non-therapeutic communication, few ways to improved therapeutic communication, characteristics of therapeutic communication, barrier of THERAPEUTIC RELATIONSHIP, introduction of interpersonal relationship, types of IPR, elements/ dynamics of IPR, introduction of therapeutic nurse patient relationship, definition, purpose, elements/characteristics , and phases of therapeutic communication, definition of Johari window, uses, what actually model represent and its areas, THERAPEUTIC IMPASSES and its management in 5th semester Bsc. nursing and 2nd GNM students
Different pricelists for different shops in odoo Point of Sale in Odoo 17



Different pricelists for different shops in odoo Point of Sale in Odoo 17Celine George Price lists are a useful tool for managing the costs of your goods and services. This can assist you in working with other businesses effectively and maximizing your revenues. Additionally, you can provide your customers discounts by using price lists.
TV Shows and web-series quiz | QUIZ CLUB OF PSGCAS | 13TH MARCH 2025



TV Shows and web-series quiz | QUIZ CLUB OF PSGCAS | 13TH MARCH 2025Quiz Club of PSG College of Arts & Science HOW YOU DOIN'?
Cool, cool, cool...
Because that's what she said after THE QUIZ CLUB OF PSGCAS' TV SHOW quiz.
Grab your popcorn and be seated.
QM: THARUN S A
BCom Accounting and Finance (2023-26)
THE QUIZ CLUB OF PSGCAS.
Final Sketch Designs for poster production.pptx



Final Sketch Designs for poster production.pptxbobby205207 Final Sketch Designs for poster production.
Gibson "Secrets to Changing Behaviour in Scholarly Communication: A 2025 NISO...



Gibson "Secrets to Changing Behaviour in Scholarly Communication: A 2025 NISO...National Information Standards Organization (NISO) This presentation was provided by Jennifer Gibson of the Dryad, during the first session of our 2025 NISO training series "Secrets to Changing Behavior in Scholarly Communications." Session One was held June 5, 2025.
LDMMIA Reiki Yoga Next Week Grad Updates



LDMMIA Reiki Yoga Next Week Grad UpdatesLDM & Mia eStudios A short update and next week. I am writing both Session 9 and Orientation S1.
As a Guest Student,
You are now upgraded to Grad Level.
See Uploads for “Student Checkin” & “S8”. Thx.
Thank you for attending our workshops.
If you are new, do welcome.
Grad Students: I am planning a Reiki-Yoga Master Course (As a package). I’m Fusing both together.
This will include the foundation of each practice. Our Free Workshops can be used with any Reiki Yoga training package. Traditional Reiki does host rules and ethics. Its silent and within the JP Culture/Area/Training/Word of Mouth. It allows remote healing but there’s limits As practitioners and masters. We are not allowed to share certain secrets/tools. Some content is designed only for “Masters”. Some yoga are similar like the Kriya Yoga-Church (Vowed Lessons). We will review both Reiki and Yoga (Master tools) in the Course upcoming.
Session Practice, For Reference:
Before starting a session, Make sure to check your environment. Nothing stressful. Later, You can decorate a space as well.
Check the comfort level, any needed resources (Yoga/Reiki/Spa Props), or Meditation Asst?
Props can be oils, sage, incense, candles, crystals, pillows, blankets, yoga mat, any theme applies.
Select your comfort Pose. This can be standing, sitting, laying down, or a combination.
Monitor your breath. You can add exercises.
Add any mantras or affirmations. This does aid mind and spirit. It helps you to focus.
Also you can set intentions using a candle.
The Yoga-key is balancing mind, body, and spirit.
Finally, The Duration can be long or short.
Its a good session base for any style.
Next Week’s Focus:
A continuation of Intuition Development. We will review the Chakra System - Our temple. A misguided, misused situation lol. This will also serve Attunement later.
For Sponsor,
General updates,
& Donations:
Please visit:
https://ldmchapels.weebly.com
Unit 3 Poster Sketches with annotations.pptx



Unit 3 Poster Sketches with annotations.pptxbobby205207 Unit 3 Poster Sketches with annotations.pptx
Module 4 Presentation - Enhancing Competencies and Engagement Strategies in Y...



Module 4 Presentation - Enhancing Competencies and Engagement Strategies in Y...GeorgeDiamandis11 Enhancing Competencies and Engagement Strategies in Youth Work
Coleoptera: The Largest Insect Order.pptx



Coleoptera: The Largest Insect Order.pptxArshad Shaikh Coleoptera, commonly known as beetles, is the largest order of insects, comprising approximately 400,000 described species. Beetles can be found in almost every habitat on Earth, exhibiting a wide range of morphological, behavioral, and ecological diversity. They have a hardened exoskeleton, with the forewings modified into elytra that protect the hind wings. Beetles play important roles in ecosystems as decomposers, pollinators, and food sources for other animals, while some species are considered pests in agriculture and forestry.
POS Reporting in Odoo 18 - Odoo 18 Slides



POS Reporting in Odoo 18 - Odoo 18 SlidesCeline George To view all the available reports in Point of Sale, navigate to Point of Sale > Reporting. In this section, you will find detailed reports such as the Orders Report, Sales Details Report, and Session Report, as shown below.
How to Manage Maintenance Request in Odoo 18



How to Manage Maintenance Request in Odoo 18Celine George Efficient maintenance management is crucial for keeping equipment and work centers running smoothly in any business. Odoo 18 provides a Maintenance module that helps track, schedule, and manage maintenance requests efficiently.
Pfeiffer "Secrets to Changing Behavior in Scholarly Communication: A 2025 NIS...



Pfeiffer "Secrets to Changing Behavior in Scholarly Communication: A 2025 NIS...National Information Standards Organization (NISO) This presentation was provided by Nicole 'Nici" Pfeiffer of the Center for Open Science (COS), during the first session of our 2025 NISO training series "Secrets to Changing Behavior in Scholarly Communications." Session One was held June 5, 2025.
Analysis of Quantitative Data Parametric and non-parametric tests.pptx



Analysis of Quantitative Data Parametric and non-parametric tests.pptxShrutidhara2 This presentation covers the following points--
Parametric Tests
• Testing the Significance of the Difference between Means
• Analysis of Variance (ANOVA) - One way and Two way
• Analysis of Co-variance (One-way)
Non-Parametric Tests:
• Chi-Square test
• Sign test
• Median test
• Sum of Rank test
• Mann-Whitney U-test
Moreover, it includes a comparison of parametric and non-parametric tests, a comparison of one-way ANOVA, two-way ANOVA, and one-way ANCOVA.
Adam Grant: Transforming Work Culture Through Organizational Psychology



Adam Grant: Transforming Work Culture Through Organizational PsychologyPrachi Shah This presentation explores the groundbreaking work of Adam Grant, renowned organizational psychologist and bestselling author. It highlights his key theories on giving, motivation, leadership, and workplace dynamics that have revolutionized how organizations think about productivity, collaboration, and employee well-being. Ideal for students, HR professionals, and leadership enthusiasts, this deck includes insights from his major works like Give and Take, Originals, and Think Again, along with interactive elements for enhanced engagement.
LDMMIA Free Reiki Yoga S9 Grad Level Intuition II



LDMMIA Free Reiki Yoga S9 Grad Level Intuition IILDM & Mia eStudios Completed Sunday 6/8. For Weekend 6/14 & 15th. (Fathers Day Weekend US.) These workshops are also timeless for future students TY. No admissions needed.
A 9th FREE WORKSHOP
Reiki - Yoga
“Intuition-II, The Chakras”
Your Attendance is valued.
We hit over 5k views for Spring Workshops and Updates-TY.
Thank you for attending our workshops.
If you are new, do welcome.
Grad Students: I am planning a Reiki-Yoga Master Course (As a package). I’m Fusing both together.
This will include the foundation of each practice. Our Free Workshops can be used with any Reiki Yoga training package. Traditional Reiki does host rules and ethics. Its silent and within the JP Culture/Area/Training/Word of Mouth. It allows remote healing but there’s limits As practitioners and masters, we are not allowed to share certain secrets/tools. Some content is designed only for “Masters”. Some yoga are similar like the Kriya Yoga-Church (Vowed Lessons). We will review both Reiki and Yoga (Master tools) in the Course upcoming.
S9/This Week’s Focus:
* A continuation of Intuition-2 Development. We will review the Chakra System - Our temple. A misguided, misused situation lol. This will also serve Attunement later.
Thx for tuning in. Your time investment is valued. I do select topics related to our timeline and community. For those seeking upgrades or Reiki Levels. Stay tuned for our June packages. It’s for self employed/Practitioners/Coaches…
Review & Topics:
* Reiki Is Japanese Energy Healing used Globally.
* Yoga is over 5k years old from India. It hosts many styles, teacher versions, and it’s Mainstream now vs decades ago.
* Anything of the Holistic, Wellness Department can be fused together. My origins are Alternative, Complementary Medicine. In short, I call this ND. I am also a metaphysician. I learnt during the 90s New Age Era. I forget we just hit another wavy. It’s GenZ word of Mouth, their New Age Era. WHOA, History Repeats lol. We are fusing together.
* So, most of you have experienced your Spiritual Awakening. However; The journey wont be perfect. There will be some roller coaster events. The perks are: We are in a faster Spiritual Zone than the 90s. There’s more support and information available.
(See Presentation for all sections, THX AGAIN.)
june 10 2025 ppt for madden on art science is over.pptx



june 10 2025 ppt for madden on art science is over.pptxroger malina art science is over -talk by roger malina for jack madden group
Optimization technique in pharmaceutical product development.pptx



Optimization technique in pharmaceutical product development.pptxUrmiPrajapati3 Optimization techniques in pharmaceutical product development
TV Shows and web-series quiz | QUIZ CLUB OF PSGCAS | 13TH MARCH 2025



TV Shows and web-series quiz | QUIZ CLUB OF PSGCAS | 13TH MARCH 2025Quiz Club of PSG College of Arts & Science
Gibson "Secrets to Changing Behaviour in Scholarly Communication: A 2025 NISO...



Gibson "Secrets to Changing Behaviour in Scholarly Communication: A 2025 NISO...National Information Standards Organization (NISO)
Pfeiffer "Secrets to Changing Behavior in Scholarly Communication: A 2025 NIS...



Pfeiffer "Secrets to Changing Behavior in Scholarly Communication: A 2025 NIS...National Information Standards Organization (NISO)
CNIT 128 3. Attacking iOS Applications (Part 1)
- 1. CNIT 128 Hacking Mobile Devices 3. Attacking iOS Apps Part 1
- 2. Topics: Part 1 • Introduction to Transport Security • Identifying Insecure Storage • Patching iOS Applications with Hopper
- 3. Topics: Part 2 • Attacking the iOS Runtime • Understanding Interprocess Communication • Attacking Using Injection
- 4. Attack Scenarios • From the network • Tainted data from server-side applications • Physical access to the phone • Interactive access to the phone • Control of another app on the phone
- 6. Cleartext Channels • Such as HTTP • Never safe • Even if not transmitting sensitive data like passwords • Because an attacker could inject JavaScript
- 7. Finding Cleartext • Examine traffic with Wireshark or Burp
- 8. Three SSL/TLS Implementations • The URL loading system • The Carbon Framework • The Secure Transport API
- 9. The URL Loading System • High-level classes and methods like • NSURLConnection • NSURLSession • Simplest method • Most widely adopted
- 10. Carbon Framework • More granular API than the URL loading system • Gives developers greater control over network requests • Implemented using the CFNetwork class
- 11. Secure Transport API • Low-level API • The foundation of CFNetwork and the URL loading system • Greatest control over the transport • Complex to implement • Rarely used directly
- 12. Certificate Validation • SSL and TLS use certificate-based authentication to • Ensure that you are communicating with the desired server • Prevent eavesdropping and tampering attacks • Unless the validation is weakened
- 13. Trusted CA • Certificates must be signed by a trusted Certificate Authority (CA) • Accepting self-signed or unvalidated certificates undermines TLS and SSL • Allowing MiTM attacks
- 14. NSURLConnection Class • Developer can allow self-signed certificates • By customizing the didReceiveAuthenticationChallenge method
- 15. Carbon Framework • Can allow self-signed certficates by setting up an SSL settings dictionary • That sets the kCFStreamSSLValidatesCertificateChain constant to false
- 16. Secure Transport API • Setting the kSSLSessionOptionBreakOnServerAuth option • Disables the API's certificate validation • But the app might have its own trust evaluation routines, like certificate pinning
- 17. Certificate Problems • Self-signed certificates • Expired certificates • Mismatched hostnames • Expired root CA certificates • Allowing any root certificate
- 18. Dynamic Testing • Route traffic through the Burp proxy • Browser detects the SSL error
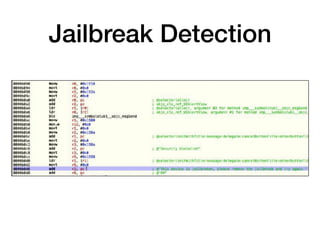
- 19. GOTO Fail
- 22. SSL Session Security • There are other possible SSL errors if an app is using the Carbon framework or the Secure Transport API • But not if it uses the high-level URL loading API • Because there is no way to modify the SSL/TLS session properties
- 23. Protocol Versions • CFNetwork and Secure Transport APIs • Both allow a developer to modify the protocol version • SSLv2 and SSLv3 are vulnerable
- 24. CFNetwork API (Carbon Framework) Protocol Settings • These settings specify vulnerable versions • kCFStreamSocketSecurityLevelSSLv2 • kCFStreamSocketSecurityLevelSSLv3 • kCFStreamSocketSecurityLevelTLSv1 • These settings allow negotiation of insecure versions • kCFStreamSocketSecurityLevelNone • kCFStreamSocketSecurityLevelNegotiatedSSL
- 25. Secure Transport API Protocol Settings • These settings allow vulnerable versions • kSSLProtocolUnknown • kSSLProtocol3 • kTLSProtocol1 • kTLSProtocol11 • kDTLSProtocol1 • This is the preferred setting • kTLSProtocol12
- 27. Specific Cipher Suite • Developer may specify an insecure suite • Secure Transport and CFNetwork APIs allow this
- 28. Intercepting Encrypted Communications • Necessary to test apps • Must install the Burp certificate on the phone
- 29. Bypassing Certificate Pinning • An app has information about the correct certificate embedded in it • And refuses to connect with other certificates • This must be bypassed to view the network traffic
- 30. Substrate Tweaks
- 32. Local Storage • An attacker can steal local data when • The phone is stolen while unlocked • The Touch ID sensor is bypassed • Remote compromise through exploitation • Default credentials on jailbroken phones • There is no passcode • Pairing with a malicious computer • Exploiting the boot chain
- 33. Storage Errors • Stored by app in plaintext • Using custom encryption with insecure key • Stored with wrong data protection class • Inadvertently stored by iOS
- 35. Protection Classes • No Protection • Not encrypted • Unsuitable for sensitive data • Complete Until First User Authentication • Discouraged for sensitive data
- 36. Identifying Data Protection Classes • If data can be backed up • Back up, then use
- 37. Keychain Items • keychain_dump creates plist files • protection_class key inside them
- 38. Dynamic Analysis • Tests stored data that doesn't get backed up • Use Cydia Substrate • The old Snoop-It tool was helpful, but it's gone
- 39. Patching iOS Applications with Hopper
- 40. Get the Binary • Project M 702
- 43. Pseudo Code



