CodeOne SF 2018 "Are you deploying and operating with security in mind?"
Download as pptx, pdf0 likes255 views
So, you’ve fully embraced the container revolution and are now deploying all the Java applications packaged in Docker containers, but are you exercising appropriate caution with the new security issues container technology can bring? This session presents an overview of the current threat landscape, with a focus on container technology and Java applications, and shows how to mitigate the risks. Hear about the impact of security throughout the software creation and delivery lifecycle and how container technology changes and adds to the security requirements of modern software. Also learn about the important open source tools for code scanning, dependency verification, and so on—and guidelines on when to use them.
1 of 60
Download to read offline











![TrustManager[] trustAllCerts = new TrustManager[]{
new X509TrustManager() {
public X509Certificate[] getAcceptedIssuers() {
return null;
}
public void checkClientTrusted(
X509Certificate[] certs, String authType) {
}
public void checkServerTrusted(
X509Certificate[] certs, String authType) {
}
public boolean isClientTrusted( X509Certificate[] cert) {
return true;
}
public boolean isServerTrusted( X509Certificate[] cert) {
return true;
}
}}
Ever written
something
like this?
@spoole167](https://image.slidesharecdn.com/codeonesf-areyoudeployingandoperatingwithsecurityinmindfinal-181022222907/85/CodeOne-SF-2018-Are-you-deploying-and-operating-with-security-in-mind-12-320.jpg)















































Recommended
Security in serverless world



Security in serverless worldYan Cui AWS has taken over the responsibilities of patching the OS and securing the underlying physical infrastructure that runs your serverless application, so what’s left for you to secure? Quite a bit it turns out.
The OWASP top 10 is as relevant to you as ever; DOS attacks are still a threat even if you can probably brute force your way through it as AWS auto-scales Lambda functions automatically; and did you know attackers can easily steal your AWS credentials via your application dependencies?
In addition to the traditional threats, serverless applications have more granular deployment units and therefore there are more things to configure and secure, and the tools and practices are still catching up with this fast changing world.
The Unexpected Attack Vector: Software Updaters



The Unexpected Attack Vector: Software UpdatersPriyanka Aash Every day millions of computers perform silently a simple task with great risk exposure: download and execute code through a software updater. An updater introduces a dangerous attack surface represented by unsafe code practice, unsecure protocols or server infrastructure not adequately protected. This talk will dive into incidents like CCleaner, ShadowPad and Medoc, and tools used to hijack updaters.Every day millions of computers perform silently a simple task with great risk exposure: download and execute code through a software updater. An updater introduces a dangerous attack surface represented by unsafe code practice, unsecure protocols or server infrastructure not adequately protected. This talk will dive into incidents like CCleaner, ShadowPad and Medoc, and tools used to hijack updaters.
Learning Objectives:
1: Learn about a new emerging attack vector (software supply chain and updaters).
2: Investigate findings from recent incidents involving software updates.
3: Rethink update distribution and mitigate the problem.
(Source: RSA Conference USA 2018)
10 Mistakes Hackers Want You to Make



10 Mistakes Hackers Want You to MakeJoe Kutner The document outlines 10 mistakes hackers want developers to make when building applications. The mistakes include: 1) Using dependencies with known vulnerabilities; 2) Unsanitized user input which can enable injection attacks; 3) Unsafe regex patterns that can allow denial of service attacks; 4) Failure to implement rate limiting and prevent abusive requests. The document provides examples and solutions for avoiding each mistake to help developers build more secure applications.
Persistant Cookies and LDAP Injection



Persistant Cookies and LDAP InjectionMaulikLakhani The presentation is on Persistent Cookies and LDAP Injection. Persistent cookies stay on your hard drive (one of your browser's subfolders) until they expire or get deleted. The session will cover introduction to Persistent Cookies and applicable test-cases with respect to Web Application Penetration Testing. In LDAP Injection section, the presentation will cover: Understanding Active Directory, Understanding LDAP and How does LDAP Injection work.
[Wroclaw #9] The purge - dealing with secrets in Opera Software![[Wroclaw #9] The purge - dealing with secrets in Opera Software](https://cdn.slidesharecdn.com/ss_thumbnails/presentation3-181117173825-thumbnail.jpg?width=560&fit=bounds)
![[Wroclaw #9] The purge - dealing with secrets in Opera Software](https://cdn.slidesharecdn.com/ss_thumbnails/presentation3-181117173825-thumbnail.jpg?width=560&fit=bounds)
![[Wroclaw #9] The purge - dealing with secrets in Opera Software](https://cdn.slidesharecdn.com/ss_thumbnails/presentation3-181117173825-thumbnail.jpg?width=560&fit=bounds)
![[Wroclaw #9] The purge - dealing with secrets in Opera Software](https://cdn.slidesharecdn.com/ss_thumbnails/presentation3-181117173825-thumbnail.jpg?width=560&fit=bounds)
[Wroclaw #9] The purge - dealing with secrets in Opera SoftwareOWASP This document discusses Opera Software's process for preventing secrets and sensitive information from being committed to code repositories. It describes the problem of secrets in codebases, various tools for identifying and managing secrets like HashiCorp Vault and detect-secrets, and Opera's implementation which uses Vault for secret storage and detect-secrets for identifying secrets in code. The process involves creating a secrets baseline, enabling detect-secrets hooks to prevent pushes with new secrets, auditing the codebase history, and updating the baseline over time.
DevSecCon Boston 2018: Building a practical DevSecOps pipeline for free by Je...



DevSecCon Boston 2018: Building a practical DevSecOps pipeline for free by Je...DevSecCon The document discusses building a practical DevSecOps pipeline for free. It promotes using Interactive Application Security Testing (IAST) and Runtime Application Self-Protection (RASP) tools to shift security left and implement security throughout the development, integration and operations phases. IAST can detect vulnerabilities during normal application use while RASP can prevent vulnerabilities from being exploited at runtime. The document advocates establishing a security workflow, ensuring instant security feedback, and building a security culture as part of DevSecOps. It also recommends the free and open source Contrast Community Edition as an IAST and RASP tool that can integrate with development tools and provide security testing without slowing down builds or developers.
How to get the best out of DevSecOps - an operations perspective



How to get the best out of DevSecOps - an operations perspectiveColin Domoney This document discusses DevSecOps and the impact on operations. It describes how DevSecOps utilizes collaboration, flexibility, and automation through practices like infrastructure as code. This allows operations to focus on critical tasks rather than manual changes. Best practices for securing operations in a DevSecOps model include controlling source code repositories, protecting deployment pipelines, integrating security testing into the pipeline, and using security telemetry in applications and environments. Automated dashboards can measure security metrics.
WebGoat.SDWAN.Net in Depth: SD-WAN Security Assessment 



WebGoat.SDWAN.Net in Depth: SD-WAN Security Assessment Sergey Gordeychik Denis Kolegov, Oleg Broslavsky, Power of Community 2018, Seoul, Korea
Today, «SD-WAN» is a very hot and attractive topic. Software-defined WAN (SD-WAN) is a technology based on software-defined network (SDN) approach applied to wide area networks (WAN) in enterprise networks. According to Gartner’s predictions study, more than 50% of routers will be replaced with SD-WAN solutions by 2020.
In this presentation, we disclose a set of vulnerabilities in widespread and most popular SD-WAN products including Citrix NetScaler and Silver Peak EdgeConnect. We present the new results of our research, consider some technical details of the insecure design and found vulnerabilities, and describe different attack scenarios that may allow an attacker to compromise SD-WAN control and data planes.
[OPD 2019] Attacking JWT tokens![[OPD 2019] Attacking JWT tokens](https://cdn.slidesharecdn.com/ss_thumbnails/attackingjwttokens-191021171156-thumbnail.jpg?width=560&fit=bounds)
![[OPD 2019] Attacking JWT tokens](https://cdn.slidesharecdn.com/ss_thumbnails/attackingjwttokens-191021171156-thumbnail.jpg?width=560&fit=bounds)
![[OPD 2019] Attacking JWT tokens](https://cdn.slidesharecdn.com/ss_thumbnails/attackingjwttokens-191021171156-thumbnail.jpg?width=560&fit=bounds)
![[OPD 2019] Attacking JWT tokens](https://cdn.slidesharecdn.com/ss_thumbnails/attackingjwttokens-191021171156-thumbnail.jpg?width=560&fit=bounds)
[OPD 2019] Attacking JWT tokensOWASP - JWT tokens can be attacked by exploiting vulnerabilities in how they are validated and used. Common attacks include modifying token properties like the signing algorithm, injection of header parameters like kid and x5u, and cracking weak HS256 keys.
- Tools like jwtbrute and libraries that don't properly validate tokens can aid exploitation. Attackers aim to have their tampered tokens treated as authentic by compromising validation processes.
- Developers must carefully validate all token properties, use strong signing keys, and avoid deserialization that doesn't verify signatures to prevent exploitation of JWT tokens.
DevSecCon London 2018: Open DevSecOps



DevSecCon London 2018: Open DevSecOpsDevSecCon PETKO D. PETKOV
Thanks to the DevSecOps philosophy a growing number of organisations around the world are ensuring their businesses are set up with the security in mind from the get-go. DevSecOps is taking the world by storm. This talk is about how to introduce DevSecOps in your organisation with ready-made, zero-cost, open source templates accessible to everyone. The talk will introduce the OpenDevSecOps project and show many practical examples of how to easily deploy security testing infrastructure on top of existing and well-established development tools.
DevSecCon SG 2018 Fabian Presentation Slides



DevSecCon SG 2018 Fabian Presentation SlidesFab L This document provides instructions for a DevSecCon workshop on securing secrets in development pipelines. The workshop aims to help developers and managers address the problem of hardcoded secrets being checked into code repositories by demonstrating how to remove and rotate secrets using a secret management server integrated with Jenkins. Participants will carry out hands-on labs to find hardcoded secrets, replace them with environment variables stored in a secret server, and prevent secrets from being exposed in builds.
Why Web Security Matters!



Why Web Security Matters!Philippe De Ryck A talk about the importance of Web security, tailored towards IT people of local municipalities.
This was an invited talk at the information day on online security for the municipalities of Flemish Brabant (Belgium).
Building layers of defense for your application



Building layers of defense for your applicationVMware Tanzu This document discusses building layers of defense for applications using the Spring Security framework. It begins with an introduction to authentication and authorization. It then discusses the layers of defense for a web application and provides an overview of Spring Security, how it works, and how to integrate it. The document outlines common security threats and how Spring Security protects against them. It also covers topics like basic authentication, JWT, OAuth, OpenID Connect, and content security policy. Code examples are provided to demonstrate concepts like CSRF protection, HTTP verb tampering prevention, and session fixation.
CSW2017 Enrico branca What if encrypted communications are not as secure as w...



CSW2017 Enrico branca What if encrypted communications are not as secure as w...CanSecWest The document discusses analyzing over 73 million encryption certificates to test their security. It finds that over 25 million certificates share the same public key, over 2.5 million share the same modulus, and over 750,000 share divisors, indicating weak key generation. It also finds some certificates with invalid exponents, moduli divisible by small primes, and a few with an exponent of 1, all of which make the keys insecure. The analysis shows many keys assumed to be secure may actually be vulnerable to attacks due to flaws in key generation.
How to 2FA-enable Open Source Applications



How to 2FA-enable Open Source ApplicationsAll Things Open How to 2FA-enable Open Source Applications (Extended Session)
Presented at: Open Source 101 at Home 2020
Presented by: Mike Schwartz, Gluu
Abstract: Your organization loves open source tools like Wordpress, SuiteCRM, NextCloud, RocketChat, and OnlyOffice... but most of these tools are protected with plain old passwords. You want to use two-factor authentication... but how? In this workshop, you'll learn:
- Which 2FA technologies can be used without paying a license;
- How to enable users to enroll and delete 2FA credentials;
- How to configure open source applications to act as a federated relying party--delegating authentication to a central service
- How custom applications can act as a federated relying party
The Log4Shell Vulnerability – explained: how to stay secure



The Log4Shell Vulnerability – explained: how to stay secureKaspersky On December 9th, researchers uncovered a zero-day critical vulnerability in the Apache Log4j library used by millions of Java applications. CVE-2021-44228 or “Log4Shell” is a RCE vulnerability that allows attackers to execute arbitrary code and potentially take full control over an infected system. The vulnerability has been ranked a 10/10 on the CVSSv3 severity scale.
While the Apache Foundation has already released a patch for this CVE, it can take weeks or months for vendors to update their software, and there are already widespread scans being conducted by malicious attackers to exploit Log4Shell.
What should companies or organizations do?
Join Marco Preuss, Head of Europe’s Global Research and Analysis (GReAT) team, Marc Rivero and Dan Demeter, Senior Security Researchers with GReAT, for an in-depth discussion on Log4Shell and a live Q&A session.
To see the full webinar, please visit: https://securelist.com/webinars/log4shell-vulnerability-how-to-stay-secure/?utm_source=Slideshare&utm_medium=partner&utm_campaign=gl_jespo_je0066&utm_content=link&utm_term=gl_Slideshare_organic_s966w1tou5a0snh
From Zero to DevSecOps in 60 Minutes - DevTalks Romania - Cluj-Napoca



From Zero to DevSecOps in 60 Minutes - DevTalks Romania - Cluj-Napocajerryhargrove Whether you’re building an application in a DevOps + Security culture, or have already bridged the gap with DevSecOps, the task remains the same: How do you ensure that security best practices are understood, architected for and integrated into your application from day 1 AND remain relevant year 1. During this talk I’ll focus on how to achieve these goals amidst the ever changing landscape of people, process, and technology in the cloud, in the context of various compute environments like instances, containers and serverless functions. and how to do so using off-the-shelf AWS services and features. I’ll complete the story by accompanying this discussion with a reference application architecture and examples. Attendees of this talk will receive actionable best practices and guidance, with specific implementation details for AWS
DevSecOps: Finding the Adversaries in our Midst



DevSecOps: Finding the Adversaries in our MidstDevOps.com Security’s function is to keep the bad guys out. Better development and testing practices have led to improved attack prevention, but too often breaches occur from attacks outside industry standard top ten lists.
Well, what if we could find out the top ten vectors that bad guys actually attack rather than the ones we presume they do?
Join Shannon Lietz, DevSecOps Leader at Intuit and James Wickett, Head of Research at Signal Sciences, as they discuss how you can get greater visibility into both how and where you’re being attacked, then use that visibility to build, create, secure, and deploy sites that protect what your business actually cares about.
You’ll learn how:
DevOps and security can identify where attacks are actually happening
To remove information silos between security, development, and operations
Using this new information and collaboration can help you build more secure software
Building a DevSecOps Pipeline Around Your Spring Boot Application



Building a DevSecOps Pipeline Around Your Spring Boot ApplicationVMware Tanzu SpringOne Platform 2019
Building a DevSecOps Pipeline Around Your Spring Boot Application
Speaker: Hayley Denbraver, Developer Advocate, Snyk
YouTube: https://youtu.be/CtQ2KZ4aMnQ
30+ Nexus Integrations to Accelerate DevOps



30+ Nexus Integrations to Accelerate DevOpsSonatype This document provides descriptions of 30+ integrations for Nexus Repository that can accelerate DevOps. It lists the integrations alphabetically by name, with a brief 1-2 sentence description of each integration and its author. The integrations cover a wide range of technologies and platforms, including Docker, Maven, npm, VSTS, Jenkins, Puppet, and more. The integrations are meant to extend the capabilities of Nexus Repository and provide connections to other tools in the development pipeline. Users can find these integrations on the Nexus Exchange website.
DevSecCon London 2017: Their-problems-are-your-problems-devseccon by Tim Kadlec



DevSecCon London 2017: Their-problems-are-your-problems-devseccon by Tim KadlecDevSecCon The document discusses security issues that arise from dependencies on third-party code and libraries. It notes that the web is powered by other people's code and outlines responsibilities for ensuring security across layers of an application. Specific vulnerabilities discussed include those in Struts and exposed servers, as well as mitigations like content security policy, subresource integrity, and developing with security in mind from the start.
Wtf is happening_inside_my_android_phone_public



Wtf is happening_inside_my_android_phone_publicJaime Blasco The document discusses the architecture and analysis of Android malware called Red Bunny or ADRD. It was discovered in 2011 sending device information like IMEI and IMSI to command and control servers. The malware uses encryption, sets an HTTP proxy, and sends specially crafted headers. It decrypts responses and executes commands depending on the decrypted value.
SecPod: A Framework for Virtualization-based Security Systems



SecPod: A Framework for Virtualization-based Security SystemsYue Chen The OS kernel is critical to the security of a computer system. Many systems have been proposed to improve its security. A fundamental weakness of those systems is that page tables, the data structures that control the memory protection, are not isolated from the vulnerable kernel, and thus subject to tampering. To address that, researchers have relied on virtualization for reliable kernel memory protection. Unfortunately, such memory protection requires to monitor every update to the guest’s page tables. This fundamentally conflicts with the recent advances in the hardware virtualization support. In this paper, we propose SecPod, an extensible framework for virtualization-based security systems that can provide both strong isolation and the compatibility with modern hardware. SecPod has two key techniques: paging delegation delegates and audits the kernel’s paging operations to a secure space; execution trapping intercepts the (compromised) kernel’s attempts to subvert SecPod by misusing privileged instructions. We have implemented a prototype of SecPod based on KVM. Our experiments show that SecPod is both effective and efficient.
[OWASP Poland Day] A study of Electron security![[OWASP Poland Day] A study of Electron security](https://cdn.slidesharecdn.com/ss_thumbnails/lucacarettonia-study-of-electron-security-171003211450-thumbnail.jpg?width=560&fit=bounds)
![[OWASP Poland Day] A study of Electron security](https://cdn.slidesharecdn.com/ss_thumbnails/lucacarettonia-study-of-electron-security-171003211450-thumbnail.jpg?width=560&fit=bounds)
![[OWASP Poland Day] A study of Electron security](https://cdn.slidesharecdn.com/ss_thumbnails/lucacarettonia-study-of-electron-security-171003211450-thumbnail.jpg?width=560&fit=bounds)
![[OWASP Poland Day] A study of Electron security](https://cdn.slidesharecdn.com/ss_thumbnails/lucacarettonia-study-of-electron-security-171003211450-thumbnail.jpg?width=560&fit=bounds)
[OWASP Poland Day] A study of Electron securityOWASP Electron is an open-source framework for building desktop applications using HTML, CSS and JavaScript. It has a large attack surface including outdated dependencies, insecure default configurations, and deviations from browser security models. The document outlines security issues in Electron's core framework, such as nodeIntegration bypasses allowing remote code execution, and weaknesses in "glorified" APIs. It provides a checklist for developing secure Electron apps and introduces Electronegativity, a tool to help with security testing.
[Wroclaw #7] Why So Serial?![[Wroclaw #7] Why So Serial?](https://cdn.slidesharecdn.com/ss_thumbnails/whysoserialv1-171206133328-thumbnail.jpg?width=560&fit=bounds)
![[Wroclaw #7] Why So Serial?](https://cdn.slidesharecdn.com/ss_thumbnails/whysoserialv1-171206133328-thumbnail.jpg?width=560&fit=bounds)
![[Wroclaw #7] Why So Serial?](https://cdn.slidesharecdn.com/ss_thumbnails/whysoserialv1-171206133328-thumbnail.jpg?width=560&fit=bounds)
![[Wroclaw #7] Why So Serial?](https://cdn.slidesharecdn.com/ss_thumbnails/whysoserialv1-171206133328-thumbnail.jpg?width=560&fit=bounds)
[Wroclaw #7] Why So Serial?OWASP Serialization vulnerabilities are very dangerous and can enable remote code execution and other attacks. They are difficult to fix due to issues with blacklisting, whitelisting, and the lack of a "silver bullet" solution. Serialization problems are common in Java libraries and formats like JSON/XML. Developers must think carefully before applying fixes and avoid playing "gadget whack-a-mole" since the vulnerabilities are language and format agnostic.
DevSecCon London 2017: Hands-on secure software development from design to de...



DevSecCon London 2017: Hands-on secure software development from design to de...DevSecCon This document promotes secure software development practices and advertises an upcoming security conference. It discusses the speaker's background in security research and hacking competitions. It then outlines some common security issues like weak passwords, SQL injection, and open redirects. To demonstrate secure development, it proposes a hands-on exercise of attacking, fixing, and rewriting the codebase of a sample legacy online spaceflight booking application. The document emphasizes the importance of considering security throughout the entire software development lifecycle from design to deployment. It invites the reader to join the security conference conversation.
[OPD 2019] Threat modeling at scale![[OPD 2019] Threat modeling at scale](https://cdn.slidesharecdn.com/ss_thumbnails/letsgetevil-threatmodellingatscale-191022195630-thumbnail.jpg?width=560&fit=bounds)
![[OPD 2019] Threat modeling at scale](https://cdn.slidesharecdn.com/ss_thumbnails/letsgetevil-threatmodellingatscale-191022195630-thumbnail.jpg?width=560&fit=bounds)
![[OPD 2019] Threat modeling at scale](https://cdn.slidesharecdn.com/ss_thumbnails/letsgetevil-threatmodellingatscale-191022195630-thumbnail.jpg?width=560&fit=bounds)
![[OPD 2019] Threat modeling at scale](https://cdn.slidesharecdn.com/ss_thumbnails/letsgetevil-threatmodellingatscale-191022195630-thumbnail.jpg?width=560&fit=bounds)
[OPD 2019] Threat modeling at scaleOWASP This document discusses using threat modeling at scale in agile development to improve security. It proposes identifying security requirements and test cases for each user story by considering potential "abuser stories". This would involve breaking down high-level user stories, assigning security champions to identify abuser stories, and having the security team maintain base threat models and own testing. Examples of threat modeling user stories around password resets and money withdrawals are provided. The goal is to shift security left in the SDLC by introducing it earlier through systematic threat modeling of user stories.
Tw noche geek quito webappsec



Tw noche geek quito webappsecThoughtworks The document discusses common web application security vulnerabilities and tools for testing them. It begins with an introduction to common classes of security flaws like injection, cross-site scripting, and broken authentication. The document then outlines a testing methodology including information gathering, analysis, automated scanning, and testing authentication, access controls, and input validation. It demonstrates several tools like Burp Suite, ZAP, sqlmap, and shows examples of vulnerabilities like SQL injection and cross-site scripting. The goal is to help developers and testers harden web applications against attacks.
Java application security the hard way - a workshop for the serious developer



Java application security the hard way - a workshop for the serious developerSteve Poole Cybercrime is rising at an alarming rate. As a Java developer you know you need to be better informed about security matters but it’s hard to know where to start. This workshop will help you understand how to improve the security of your application through a series of demonstration hacks and related hands on exercises. Serious though the topic is, this practical session will be fun and will leaving you more informed and better prepared. Start building your security memory muscle here
DevSecCon London 2017: when good containers go bad by Tim Mackey



DevSecCon London 2017: when good containers go bad by Tim MackeyDevSecCon This document summarizes Tim Mackey's presentation at DevSecCon. It discusses the importance of security driven development practices like using trusted components, continuous integration processes that include security testing, and digitally signing container images. It warns that while infrastructure teams aim to provide security, vulnerabilities can still exist, and advocates continually evaluating the trust of components used. The document predicts disclosure of security issues will increase and outlines penalties for data breaches under new regulations like GDPR. It emphasizes automating awareness of open source dependencies to keep pace with DevOps.
More Related Content
What's hot (20)
[OPD 2019] Attacking JWT tokens![[OPD 2019] Attacking JWT tokens](https://cdn.slidesharecdn.com/ss_thumbnails/attackingjwttokens-191021171156-thumbnail.jpg?width=560&fit=bounds)
![[OPD 2019] Attacking JWT tokens](https://cdn.slidesharecdn.com/ss_thumbnails/attackingjwttokens-191021171156-thumbnail.jpg?width=560&fit=bounds)
![[OPD 2019] Attacking JWT tokens](https://cdn.slidesharecdn.com/ss_thumbnails/attackingjwttokens-191021171156-thumbnail.jpg?width=560&fit=bounds)
![[OPD 2019] Attacking JWT tokens](https://cdn.slidesharecdn.com/ss_thumbnails/attackingjwttokens-191021171156-thumbnail.jpg?width=560&fit=bounds)
[OPD 2019] Attacking JWT tokensOWASP - JWT tokens can be attacked by exploiting vulnerabilities in how they are validated and used. Common attacks include modifying token properties like the signing algorithm, injection of header parameters like kid and x5u, and cracking weak HS256 keys.
- Tools like jwtbrute and libraries that don't properly validate tokens can aid exploitation. Attackers aim to have their tampered tokens treated as authentic by compromising validation processes.
- Developers must carefully validate all token properties, use strong signing keys, and avoid deserialization that doesn't verify signatures to prevent exploitation of JWT tokens.
DevSecCon London 2018: Open DevSecOps



DevSecCon London 2018: Open DevSecOpsDevSecCon PETKO D. PETKOV
Thanks to the DevSecOps philosophy a growing number of organisations around the world are ensuring their businesses are set up with the security in mind from the get-go. DevSecOps is taking the world by storm. This talk is about how to introduce DevSecOps in your organisation with ready-made, zero-cost, open source templates accessible to everyone. The talk will introduce the OpenDevSecOps project and show many practical examples of how to easily deploy security testing infrastructure on top of existing and well-established development tools.
DevSecCon SG 2018 Fabian Presentation Slides



DevSecCon SG 2018 Fabian Presentation SlidesFab L This document provides instructions for a DevSecCon workshop on securing secrets in development pipelines. The workshop aims to help developers and managers address the problem of hardcoded secrets being checked into code repositories by demonstrating how to remove and rotate secrets using a secret management server integrated with Jenkins. Participants will carry out hands-on labs to find hardcoded secrets, replace them with environment variables stored in a secret server, and prevent secrets from being exposed in builds.
Why Web Security Matters!



Why Web Security Matters!Philippe De Ryck A talk about the importance of Web security, tailored towards IT people of local municipalities.
This was an invited talk at the information day on online security for the municipalities of Flemish Brabant (Belgium).
Building layers of defense for your application



Building layers of defense for your applicationVMware Tanzu This document discusses building layers of defense for applications using the Spring Security framework. It begins with an introduction to authentication and authorization. It then discusses the layers of defense for a web application and provides an overview of Spring Security, how it works, and how to integrate it. The document outlines common security threats and how Spring Security protects against them. It also covers topics like basic authentication, JWT, OAuth, OpenID Connect, and content security policy. Code examples are provided to demonstrate concepts like CSRF protection, HTTP verb tampering prevention, and session fixation.
CSW2017 Enrico branca What if encrypted communications are not as secure as w...



CSW2017 Enrico branca What if encrypted communications are not as secure as w...CanSecWest The document discusses analyzing over 73 million encryption certificates to test their security. It finds that over 25 million certificates share the same public key, over 2.5 million share the same modulus, and over 750,000 share divisors, indicating weak key generation. It also finds some certificates with invalid exponents, moduli divisible by small primes, and a few with an exponent of 1, all of which make the keys insecure. The analysis shows many keys assumed to be secure may actually be vulnerable to attacks due to flaws in key generation.
How to 2FA-enable Open Source Applications



How to 2FA-enable Open Source ApplicationsAll Things Open How to 2FA-enable Open Source Applications (Extended Session)
Presented at: Open Source 101 at Home 2020
Presented by: Mike Schwartz, Gluu
Abstract: Your organization loves open source tools like Wordpress, SuiteCRM, NextCloud, RocketChat, and OnlyOffice... but most of these tools are protected with plain old passwords. You want to use two-factor authentication... but how? In this workshop, you'll learn:
- Which 2FA technologies can be used without paying a license;
- How to enable users to enroll and delete 2FA credentials;
- How to configure open source applications to act as a federated relying party--delegating authentication to a central service
- How custom applications can act as a federated relying party
The Log4Shell Vulnerability – explained: how to stay secure



The Log4Shell Vulnerability – explained: how to stay secureKaspersky On December 9th, researchers uncovered a zero-day critical vulnerability in the Apache Log4j library used by millions of Java applications. CVE-2021-44228 or “Log4Shell” is a RCE vulnerability that allows attackers to execute arbitrary code and potentially take full control over an infected system. The vulnerability has been ranked a 10/10 on the CVSSv3 severity scale.
While the Apache Foundation has already released a patch for this CVE, it can take weeks or months for vendors to update their software, and there are already widespread scans being conducted by malicious attackers to exploit Log4Shell.
What should companies or organizations do?
Join Marco Preuss, Head of Europe’s Global Research and Analysis (GReAT) team, Marc Rivero and Dan Demeter, Senior Security Researchers with GReAT, for an in-depth discussion on Log4Shell and a live Q&A session.
To see the full webinar, please visit: https://securelist.com/webinars/log4shell-vulnerability-how-to-stay-secure/?utm_source=Slideshare&utm_medium=partner&utm_campaign=gl_jespo_je0066&utm_content=link&utm_term=gl_Slideshare_organic_s966w1tou5a0snh
From Zero to DevSecOps in 60 Minutes - DevTalks Romania - Cluj-Napoca



From Zero to DevSecOps in 60 Minutes - DevTalks Romania - Cluj-Napocajerryhargrove Whether you’re building an application in a DevOps + Security culture, or have already bridged the gap with DevSecOps, the task remains the same: How do you ensure that security best practices are understood, architected for and integrated into your application from day 1 AND remain relevant year 1. During this talk I’ll focus on how to achieve these goals amidst the ever changing landscape of people, process, and technology in the cloud, in the context of various compute environments like instances, containers and serverless functions. and how to do so using off-the-shelf AWS services and features. I’ll complete the story by accompanying this discussion with a reference application architecture and examples. Attendees of this talk will receive actionable best practices and guidance, with specific implementation details for AWS
DevSecOps: Finding the Adversaries in our Midst



DevSecOps: Finding the Adversaries in our MidstDevOps.com Security’s function is to keep the bad guys out. Better development and testing practices have led to improved attack prevention, but too often breaches occur from attacks outside industry standard top ten lists.
Well, what if we could find out the top ten vectors that bad guys actually attack rather than the ones we presume they do?
Join Shannon Lietz, DevSecOps Leader at Intuit and James Wickett, Head of Research at Signal Sciences, as they discuss how you can get greater visibility into both how and where you’re being attacked, then use that visibility to build, create, secure, and deploy sites that protect what your business actually cares about.
You’ll learn how:
DevOps and security can identify where attacks are actually happening
To remove information silos between security, development, and operations
Using this new information and collaboration can help you build more secure software
Building a DevSecOps Pipeline Around Your Spring Boot Application



Building a DevSecOps Pipeline Around Your Spring Boot ApplicationVMware Tanzu SpringOne Platform 2019
Building a DevSecOps Pipeline Around Your Spring Boot Application
Speaker: Hayley Denbraver, Developer Advocate, Snyk
YouTube: https://youtu.be/CtQ2KZ4aMnQ
30+ Nexus Integrations to Accelerate DevOps



30+ Nexus Integrations to Accelerate DevOpsSonatype This document provides descriptions of 30+ integrations for Nexus Repository that can accelerate DevOps. It lists the integrations alphabetically by name, with a brief 1-2 sentence description of each integration and its author. The integrations cover a wide range of technologies and platforms, including Docker, Maven, npm, VSTS, Jenkins, Puppet, and more. The integrations are meant to extend the capabilities of Nexus Repository and provide connections to other tools in the development pipeline. Users can find these integrations on the Nexus Exchange website.
DevSecCon London 2017: Their-problems-are-your-problems-devseccon by Tim Kadlec



DevSecCon London 2017: Their-problems-are-your-problems-devseccon by Tim KadlecDevSecCon The document discusses security issues that arise from dependencies on third-party code and libraries. It notes that the web is powered by other people's code and outlines responsibilities for ensuring security across layers of an application. Specific vulnerabilities discussed include those in Struts and exposed servers, as well as mitigations like content security policy, subresource integrity, and developing with security in mind from the start.
Wtf is happening_inside_my_android_phone_public



Wtf is happening_inside_my_android_phone_publicJaime Blasco The document discusses the architecture and analysis of Android malware called Red Bunny or ADRD. It was discovered in 2011 sending device information like IMEI and IMSI to command and control servers. The malware uses encryption, sets an HTTP proxy, and sends specially crafted headers. It decrypts responses and executes commands depending on the decrypted value.
SecPod: A Framework for Virtualization-based Security Systems



SecPod: A Framework for Virtualization-based Security SystemsYue Chen The OS kernel is critical to the security of a computer system. Many systems have been proposed to improve its security. A fundamental weakness of those systems is that page tables, the data structures that control the memory protection, are not isolated from the vulnerable kernel, and thus subject to tampering. To address that, researchers have relied on virtualization for reliable kernel memory protection. Unfortunately, such memory protection requires to monitor every update to the guest’s page tables. This fundamentally conflicts with the recent advances in the hardware virtualization support. In this paper, we propose SecPod, an extensible framework for virtualization-based security systems that can provide both strong isolation and the compatibility with modern hardware. SecPod has two key techniques: paging delegation delegates and audits the kernel’s paging operations to a secure space; execution trapping intercepts the (compromised) kernel’s attempts to subvert SecPod by misusing privileged instructions. We have implemented a prototype of SecPod based on KVM. Our experiments show that SecPod is both effective and efficient.
[OWASP Poland Day] A study of Electron security![[OWASP Poland Day] A study of Electron security](https://cdn.slidesharecdn.com/ss_thumbnails/lucacarettonia-study-of-electron-security-171003211450-thumbnail.jpg?width=560&fit=bounds)
![[OWASP Poland Day] A study of Electron security](https://cdn.slidesharecdn.com/ss_thumbnails/lucacarettonia-study-of-electron-security-171003211450-thumbnail.jpg?width=560&fit=bounds)
![[OWASP Poland Day] A study of Electron security](https://cdn.slidesharecdn.com/ss_thumbnails/lucacarettonia-study-of-electron-security-171003211450-thumbnail.jpg?width=560&fit=bounds)
![[OWASP Poland Day] A study of Electron security](https://cdn.slidesharecdn.com/ss_thumbnails/lucacarettonia-study-of-electron-security-171003211450-thumbnail.jpg?width=560&fit=bounds)
[OWASP Poland Day] A study of Electron securityOWASP Electron is an open-source framework for building desktop applications using HTML, CSS and JavaScript. It has a large attack surface including outdated dependencies, insecure default configurations, and deviations from browser security models. The document outlines security issues in Electron's core framework, such as nodeIntegration bypasses allowing remote code execution, and weaknesses in "glorified" APIs. It provides a checklist for developing secure Electron apps and introduces Electronegativity, a tool to help with security testing.
[Wroclaw #7] Why So Serial?![[Wroclaw #7] Why So Serial?](https://cdn.slidesharecdn.com/ss_thumbnails/whysoserialv1-171206133328-thumbnail.jpg?width=560&fit=bounds)
![[Wroclaw #7] Why So Serial?](https://cdn.slidesharecdn.com/ss_thumbnails/whysoserialv1-171206133328-thumbnail.jpg?width=560&fit=bounds)
![[Wroclaw #7] Why So Serial?](https://cdn.slidesharecdn.com/ss_thumbnails/whysoserialv1-171206133328-thumbnail.jpg?width=560&fit=bounds)
![[Wroclaw #7] Why So Serial?](https://cdn.slidesharecdn.com/ss_thumbnails/whysoserialv1-171206133328-thumbnail.jpg?width=560&fit=bounds)
[Wroclaw #7] Why So Serial?OWASP Serialization vulnerabilities are very dangerous and can enable remote code execution and other attacks. They are difficult to fix due to issues with blacklisting, whitelisting, and the lack of a "silver bullet" solution. Serialization problems are common in Java libraries and formats like JSON/XML. Developers must think carefully before applying fixes and avoid playing "gadget whack-a-mole" since the vulnerabilities are language and format agnostic.
DevSecCon London 2017: Hands-on secure software development from design to de...



DevSecCon London 2017: Hands-on secure software development from design to de...DevSecCon This document promotes secure software development practices and advertises an upcoming security conference. It discusses the speaker's background in security research and hacking competitions. It then outlines some common security issues like weak passwords, SQL injection, and open redirects. To demonstrate secure development, it proposes a hands-on exercise of attacking, fixing, and rewriting the codebase of a sample legacy online spaceflight booking application. The document emphasizes the importance of considering security throughout the entire software development lifecycle from design to deployment. It invites the reader to join the security conference conversation.
[OPD 2019] Threat modeling at scale![[OPD 2019] Threat modeling at scale](https://cdn.slidesharecdn.com/ss_thumbnails/letsgetevil-threatmodellingatscale-191022195630-thumbnail.jpg?width=560&fit=bounds)
![[OPD 2019] Threat modeling at scale](https://cdn.slidesharecdn.com/ss_thumbnails/letsgetevil-threatmodellingatscale-191022195630-thumbnail.jpg?width=560&fit=bounds)
![[OPD 2019] Threat modeling at scale](https://cdn.slidesharecdn.com/ss_thumbnails/letsgetevil-threatmodellingatscale-191022195630-thumbnail.jpg?width=560&fit=bounds)
![[OPD 2019] Threat modeling at scale](https://cdn.slidesharecdn.com/ss_thumbnails/letsgetevil-threatmodellingatscale-191022195630-thumbnail.jpg?width=560&fit=bounds)
[OPD 2019] Threat modeling at scaleOWASP This document discusses using threat modeling at scale in agile development to improve security. It proposes identifying security requirements and test cases for each user story by considering potential "abuser stories". This would involve breaking down high-level user stories, assigning security champions to identify abuser stories, and having the security team maintain base threat models and own testing. Examples of threat modeling user stories around password resets and money withdrawals are provided. The goal is to shift security left in the SDLC by introducing it earlier through systematic threat modeling of user stories.
Tw noche geek quito webappsec



Tw noche geek quito webappsecThoughtworks The document discusses common web application security vulnerabilities and tools for testing them. It begins with an introduction to common classes of security flaws like injection, cross-site scripting, and broken authentication. The document then outlines a testing methodology including information gathering, analysis, automated scanning, and testing authentication, access controls, and input validation. It demonstrates several tools like Burp Suite, ZAP, sqlmap, and shows examples of vulnerabilities like SQL injection and cross-site scripting. The goal is to help developers and testers harden web applications against attacks.
Similar to CodeOne SF 2018 "Are you deploying and operating with security in mind?" (20)
Java application security the hard way - a workshop for the serious developer



Java application security the hard way - a workshop for the serious developerSteve Poole Cybercrime is rising at an alarming rate. As a Java developer you know you need to be better informed about security matters but it’s hard to know where to start. This workshop will help you understand how to improve the security of your application through a series of demonstration hacks and related hands on exercises. Serious though the topic is, this practical session will be fun and will leaving you more informed and better prepared. Start building your security memory muscle here
DevSecCon London 2017: when good containers go bad by Tim Mackey



DevSecCon London 2017: when good containers go bad by Tim MackeyDevSecCon This document summarizes Tim Mackey's presentation at DevSecCon. It discusses the importance of security driven development practices like using trusted components, continuous integration processes that include security testing, and digitally signing container images. It warns that while infrastructure teams aim to provide security, vulnerabilities can still exist, and advocates continually evaluating the trust of components used. The document predicts disclosure of security issues will increase and outlines penalties for data breaches under new regulations like GDPR. It emphasizes automating awareness of open source dependencies to keep pace with DevOps.
How to get along with HATEOAS without letting the bad guys steal your lunch?



How to get along with HATEOAS without letting the bad guys steal your lunch?Graham Charters This document discusses how hackers may attempt to exploit APIs and outlines strategies for using HATEOAS to improve API security. It notes that hackers will automatically fuzz APIs using tools to find vulnerabilities. It recommends using HATEOAS to enforce state-based navigation through the API, adding tracking data to links, and having a "front door" endpoint to validate requests and limit guessable paths, reducing opportunities for exploitation. Overall, the document argues that while HATEOAS aims to help clients, naively implementing it does not improve security, and the engine of application state concept should be used thoughtfully to enforce valid request flows and detect unexpected behavior.
Hacking mobile apps



Hacking mobile appskunwaratul hax0r This presentation contains android and iOS pentesting resources and methods to test the applications.
Anatomy of Java Vulnerabilities - NLJug 2018



Anatomy of Java Vulnerabilities - NLJug 2018Steve Poole Java is everywhere. According to Oracle it’s on 3 billion devices and counting.
We also know that Java is one of the most popular vehicles for delivering malware. But that’s just the plugin right? Well maybe not. Java on the server can be just at risk as the client.
In this talk we’ll cover all aspects of Java Vulnerabilities. We’ll explain why Java has this dubious reputation, what’s being done to address the issues and what you have to do to reduce your exposure. You’ll learn about Java vulnerabilities in general: how they are reported, managed and fixed as well as learning about the specifics of attack vectors and just what a ‘vulnerability’ actually is. With the continuing increase in cybercrime it’s time you knew how to defend your code. With examples and code this talk will help you become more effective in reducing security issues in Java.
DevSecOps: The Open Source Way



DevSecOps: The Open Source WayBlack Duck by Synopsys DevOps purists may chafe at the DevSecOps term given that security and other important practices are supposed to already be an integral part of routine DevOps workflows. But the reality is that security often gets more lip service than thoughtful and systematic integration into open source software sourcing, development pipelines, and operations processes--in spite of an increasing number of threats.
In this session, we’ll look at successful practices that distributed and diverse teams use to iterate rapidly. We’ll discuss how a container platform can serve as the foundation for DevSecOps in your organization. We'll also consider the risk management associated with integrating components from a variety of sources--a consideration that open source software has had to deal with since the beginning. Finally, we'll show ways by which automation and repeatable trusted delivery of code can be built directly into a DevOps pipeline.
DevOps and the cloud: all hail the (developer) king - Daniel Bryant, Steve Poole



DevOps and the cloud: all hail the (developer) king - Daniel Bryant, Steve PooleJAXLondon_Conference 1) The document discusses the rise of microservices and DevOps approaches in application development and deployment. It notes both the promises and challenges of these approaches, including increased complexity and the need for new tooling.
2) It describes lessons learned from early adoption of microservices, such as the problems that can arise from shared data stores and monolithic upgrades.
3) The document advocates for a "safety first" mindset with DevOps, emphasizing the importance of security, compliance, and understanding where data is located in cloud environments.
The Anatomy of Java Vulnerabilities



The Anatomy of Java VulnerabilitiesSteve Poole In this talk we’ll cover all aspects of Java Vulnerabilities. We’ll explain why Java has this dubious reputation, what’s being done to address the issues and what you have to do to reduce your exposure. You’ll learn about Java vulnerabilities in general: how they are reported, managed and fixed as well as learning about the specifics of attack vectors and just what a ‘vulnerability’ actually is.
JAXLondon 2015 "DevOps and the Cloud: All Hail the (Developer) King"



JAXLondon 2015 "DevOps and the Cloud: All Hail the (Developer) King"Daniel Bryant Last year we talked about DevOps, what it was, why it was important and how to get started. Boy, was it scary. Now we’re wiser. More battle-scarred. The scale of the challenge for application writers exploiting cloud and DevOps is clearer, but so is the path forward. Understanding the DevOps approach is important but equally you must understand specific deployment technologies. How to exploit them and how they effect the design of applications. Whether creating simple applications or sophisticated microservice architectures many of the challenges are the same.
Presented at JAXLondon 2015 with Steve Poole
Css sf azure_8-9-17-protecting_web_apps_stephen coty_al



Css sf azure_8-9-17-protecting_web_apps_stephen coty_alAlert Logic The document discusses strategies for protecting web applications from security threats. It begins by examining the types of attacks organizations face, including application attacks, brute force attacks, and suspicious activity. It then covers hacker reconnaissance methods such as crawling websites, using vulnerability scanners, and searching open forums and the dark web. The document outlines how attacks can escalate from exploiting web applications to gaining privileged access. It concludes by providing recommendations for developing a secure code, access management policies, patch management, monitoring strategies, and staying informed of the latest vulnerabilities.
CSS17: Houston - Protecting Web Apps



CSS17: Houston - Protecting Web AppsAlert Logic Presentation from Stephen Coty, Chief Security Evangelist, Alert Logic, at the Cloud Security Summit in Houston, Texas on June 14, 2017.
Securing TodoMVC Using the Web Cryptography API



Securing TodoMVC Using the Web Cryptography APIKevin Hakanson The open source TodoMVC project implements a Todo application using popular JavaScript MV* frameworks. Some of the implementations add support for compile to JavaScript languages, module loaders and real time backends. This presentation will demonstrate a TodoMVC implementation which adds support for the forthcoming W3C Web Cryptography API, as well as review some key cryptographic concepts and definitions.
Instead of storing the Todo list as plaintext in localStorage, this "secure" TodoMVC implementation encrypts Todos using a password derived key. The PBKDF2 algorithm is used for the deriveKey operation, with getRandomValues generating a cryptographically random salt. The importKey method sets up usage of AES-CBC for both encrypt and decrypt operations. The final solution helps address item "A6-Sensitive Data Exposure" from the OWASP Top 10.
With the Web Cryptography API being a recommendation in 2014, any Q&A time will likely include browser implementations and limitations, and whether JavaScript cryptography adds any value.
Here Be Dragons: Security Maps of the Container New World



Here Be Dragons: Security Maps of the Container New WorldC4Media Video and slides synchronized, mp3 and slide download available at URL http://bit.ly/1KjxPiO.
Josh Bregman explores some of the unique security challenges created by both the development workflow and application runtime, explains why and how the current approaches in SecDevOps 1.0 are insufficient, and how SecDevOps 2.0 techniques including Software Defined Firewalls (SDF) provide a promising path forward for all parties involved. Filmed at qconnewyork.com.
Josh Bregman is Information Security Architect and Executive Vice President for Technical Sales at Conjur Inc.
Java script and web cryptography (cf.objective)



Java script and web cryptography (cf.objective)ColdFusionConference This document provides an overview of a session on JavaScript and web cryptography. It will explore the current state of JavaScript and web cryptography, reviewing basic concepts and definitions. It will discuss the role of TLS/SSL and provide working examples applying cryptography to real-world use cases. It will also preview the upcoming W3C WebCryptoAPI. Code samples will demonstrate CryptoJS in the browser and Node.js Crypto on the server. An extended example will secure the popular TodoMVC project using PBKDF2 for key generation, HMAC for integrity and AES for encryption.
DevoxxUK 2016: "DevOps: Microservices, containers, platforms, tooling... Oh y...



DevoxxUK 2016: "DevOps: Microservices, containers, platforms, tooling... Oh y...Daniel Bryant Two years ago at Devoxx UK we talked about DevOps, what it was, why it was important and how to get started. Boy, was it scary. Now we’re wiser. More battle-scarred. The large scale of the challenge for application writers exploiting cloud and DevOps is clearer, but so is the path forward. Understanding the DevOps approach is important, but equally you must understand specific deployment technologies, security issues, operational reliability, and how to drive organisational transformation. Whether creating simple applications or sophisticated microservice architectures many of the challenges are the same. Join us to learn how you can apply this within your team and company.
Security Testing ModernApps_v1.0



Security Testing ModernApps_v1.0Neelu Tripathy In the recent years, the traditional application monolith has broken down into a hefty chunk of micro-services thereby increasing the attack surface. We will look at how this increases the entry points into the complex modern day application ecosystem. The modern security tester needs various skills to pen-test such apps including the understanding of containers to successfully break or defend such applications.
When we tie this with the fast paced devOps life cycles for applications and explore the challenges when scaling security for such applications across the organization.
Hence, this webinar discusses traditional and relatively newer methods of Pen-testing web applications. Thereby illustrating how the changing business requirements and Agile life cycles for applications affect Security testing for modern applications.
Key Takeaways:
- what do the traditional Pen testing/Security testing Techniques entail?
- How is the landscape for Applications changing and how it affects security testing?
- What are the key essentials for testing modern applications?
- what can be done to scaling Security Assessments(Testing) for Modern & Agile life cycles?
Protect Your Payloads: Modern Keying Techniques



Protect Your Payloads: Modern Keying TechniquesLeo Loobeek The document discusses keying techniques for encrypting payloads in a way that only allows decryption on specific target systems. It covers using local system resources like environment variables or file paths to derive encryption keys. It also introduces using remote resources like web pages or DNS records hosted by the attacker to control when payloads execute. Tools like Ebowla, KeyRing, and KeyServer are presented as ways to implement these keying techniques for various scripting languages and to automate controlling remote keys. The goal is to make payloads only executable on intended targets and to maintain control over payload execution.
SCS DevSecOps Seminar - State of DevSecOps



SCS DevSecOps Seminar - State of DevSecOpsStefan Streichsbier - Stefan Streichsbier is the CEO of GuardRails and a professional white-hat hacker who has identified severe shortcomings in security processes and technologies, leading him to create GuardRails.
- The document discusses the evolution of DevOps and increasing complexity, the state of security and how it needs to fit within modern development workflows, and introduces the concept of DevSecOps to address shortcomings and better integrate security.
- Key aspects of DevSecOps discussed include how to create, test, and monitor secure applications and empower development teams to build security in from the start rather than see it as a separate function. Automated security tools and the need to reduce noise and improve usability for developers is also
Solnet dev secops meetup



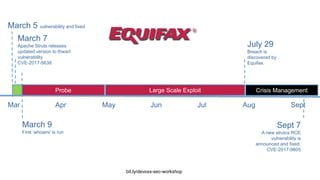
Solnet dev secops meetuppbink DevSecOps aims to integrate security practices into DevOps workflows to deliver value faster and safer. It addresses challenges like keeping security practices aligned with continuous delivery models and empowered DevOps teams. DevSecOps incorporates security checks and tools into development pipelines to find and fix issues early. This helps prevent breaches like the 2017 Equifax hack, which exploited a known vulnerability. DevSecOps promotes a culture of collaboration, shared responsibility, and proactive security monitoring throughout the software development lifecycle.
Stranger Danger: Your Java Attack Surface Just Got Bigger | JBCNConf 2022



Stranger Danger: Your Java Attack Surface Just Got Bigger | JBCNConf 2022Brian Vermeer The document discusses the security challenges of modern applications that rely heavily on open source code and containers. It notes that 80-90% of application codebases are open source, and 80% of vulnerabilities are found in indirect dependencies. It also discusses how applications are built, deployed, and scaled rapidly through containers and infrastructure as code. The document argues that this new application profile requires a DevSecOps approach that integrates security throughout the development lifecycle rather than a "shift left" approach. It presents the tooling offered by Snyk to help developers securely use open source, containers, and infrastructure as code.
DevOps and the cloud: all hail the (developer) king - Daniel Bryant, Steve Poole



DevOps and the cloud: all hail the (developer) king - Daniel Bryant, Steve PooleJAXLondon_Conference
More from Daniel Bryant (20)
ITKonekt 2023: The Busy Platform Engineers Guide to API Gateways



ITKonekt 2023: The Busy Platform Engineers Guide to API GatewaysDaniel Bryant API Gateways are certainly not a new technology, but the way in which they are being deployed, configured, and operated within modern platforms is forcing many of us to rethink our approach. Can we simply lift and shift our existing gateway into the cloud? Is our API gateway GitOps friendly (and does it need to be)? And what about service meshes, CNI, eBPF, and...
Join this talk for a whistle stop tour of modern API gateways, which a focus on deploying and managing this technology within Kubernetes (on which many modern platforms are built):
- Understand why platform engineers should care about API Gateways today
- Learn about API gateways, options, and requirements for modern platforms
- Identify key considerations for migrating to the cloud or building a new platform on Kubernetes
- Understand how cloud native workflows impact the user/developer experience (UX/DX) of an API gateway
- Explore the components of a complete "edge stack" that supports end-to-end development flows
CraftConf 2023 "Microservice Testing Techniques: Mocks vs Service Virtualizat...



CraftConf 2023 "Microservice Testing Techniques: Mocks vs Service Virtualizat...Daniel Bryant When enterprise organizations adopt microservices, containers, and cloud native development, the technologies and architectures may change, but the fact remains that we all still add the occasional bug to our code. The main challenge you now face is how to perform integration or end-to-end testing without spinning up all of your microservices locally and driving your laptop fans into high speed!
Join me for a tour of your microservices testing options using a series of Java-friendly tools.
- Explore challenges with scaling container-based application development (you can only run so many microservices locally before minikube melts your laptop)
- Learn about effective unit testing with mocks, using TestContainers for dependency testing, and using Telepresence to extend your local testing environment into the cloud
- Understand when to use each type of test and tooling based on your use case and requirements for realism, speed, and practicality
- See how Telepresence can "intercept" or reroute traffic from a specified service in a remote K8s cluster to your local dev machine
PlatformCon 23: "The Busy Platform Engineers Guide to API Gateways"



PlatformCon 23: "The Busy Platform Engineers Guide to API Gateways"Daniel Bryant API Gateways are certainly not a new technology, but the way in which they are being deployed, configured, and operated within modern platforms is forcing many of us to rethink our approach. Can we simply lift and shift our existing gateway into the cloud? Is our API gateway GitOps friendly (and does it need to be)? And what about service meshes, CNI, eBPF, and...
Join this talk for a whistle stop tour of modern API gateways, which a focus on deploying and managing this technology within Kubernetes (on which many modern platforms are built):
- Understand why platform engineers should care about API Gateways today
- Learn about API gateways, options, and requirements for modern platforms
- Identify key considerations for migrating to the cloud or building a new platform on Kubernetes
- Understand how cloud native workflows impact the user/developer experience (UX/DX) of an API gateway
- Explore the components of a complete "edge stack" that supports end-to-end development flows
Java Meetup 23: 'Debugging Microservices "Remocally" in Kubernetes with Telep...



Java Meetup 23: 'Debugging Microservices "Remocally" in Kubernetes with Telep...Daniel Bryant When enterprise organizations adopt microservices, containers, and cloud native development, the technologies and architectures may change, but the fact remains that we all still add the occasional bug to our code. The main challenge you now face is how to perform integration or end-to-end testing without spinning up all of your microservices locally and driving your laptop fans into high speed!
Join me for a tour of your microservices testing options using a series of Java-friendly tools.
- Explore challenges with scaling container-based application development (you can only run so many microservices locally before minikube melts your laptop)
- Learn about effective unit testing with mocks, using TestContainers for dependency testing, and using Telepresence to extend your local testing environment into the cloud
- Understand when to use each type of test and tooling based on your use case and requirements for realism, speed, and practicality
- See how Telepresence can "intercept" or reroute traffic from a specified service in a remote K8s cluster to your local dev machine
DevRelCon 2022: "Is Product Led Growth (PLG) the “DevOps” of the DevRel World"



DevRelCon 2022: "Is Product Led Growth (PLG) the “DevOps” of the DevRel World"Daniel Bryant Over the last year, the Ambassador Labs team has doubled down on their adoption of Product Led Growth (PLG), a growth model where product usage drives customer acquisition, retention, and expansion. It’s been an interesting journey for the DevRel team, who have found themselves working more closely with both the sales and growth engineering teams.
In their quest to reduce the friction of product adoption, they’re thinking more and more about the end-to-end experiences, experimentation, instrumentation, data analysis, and handoffs — much like we saw in the software development world with the adoption of DevOps breaking down barriers between engineering and operations.
The Ambassador Labs team have learned more about the value of creating hypotheses and analyzing quantitative data, but have also been reminded that there is no substitute for qualitative data and engaging human-to-human. Join Daniel for a whistle-stop tour of PLG through the DevRel lens:
– Understand how moving to PLG can impact devrel teams and the work they do: for better and worse!
– Explore how DevRel tooling and community platforms are increasingly overlapping with PLG marketer tooling
– Learn how to structure your goals, common languages, and teams for successfully adopting PLG
Fall 22: "From Kubernetes to PaaS to... err, what's next"



Fall 22: "From Kubernetes to PaaS to... err, what's next"Daniel Bryant Developers building applications on Kubernetes today are being asked to not just code applications -- they are also responsible for shipping and running their applications, too. We often talk about needing a Kubernetes platform, but are we really looking for a PaaS? Or instead, are we looking for some kind of developer control plane with a Goldilock-sized collection of tools that provides just the right amount of platform? This talk will look back on my experience of building platforms, both as an end-user and now as part of an organization helping our customers do the same. We’ll wrap this talk with a walk-through of the CNCF ecosystem through the developer control plane lens, and look at what’s next in the future of this important emerging category.
Building Microservice Systems Without Cooking Your Laptop: Going “Remocal” wi...



Building Microservice Systems Without Cooking Your Laptop: Going “Remocal” wi...Daniel Bryant Join me for a tour of coding, testing, and shipping microservices using remote-to-local “remocal” tools and techniques. You will:
- Understand the challenges with scaling container-based application development – i.e. you can only run so many microservices locally before minikube melts your laptop.
- Learn when to use various types of development practices and tooling based on your use case and requirements for production realism, speed, and practicality.
- Explore how to utilize containerized dependencies and Docker for testing, including for both apps and services you own and those you don’t.
- Learn how Telepresence can enable “remocal” development, expanding your local machine and Docker Desktop out into a remote Kubernetes cluster.
KubeCrash 22: Debugging Microservices "Remocally" in Kubernetes with Telepres...



KubeCrash 22: Debugging Microservices "Remocally" in Kubernetes with Telepres...Daniel Bryant
Many organizations adopt cloud native development practices with the goal of shipping features faster. The technologies and architectures may change when we move to the cloud, but the fact remains that we all still add the occasional bug to our code.
The challenge here is that many of your existing local debugging tools and practices can’t be used when everything is running in a container or deployed onto Kubernetes running in the cloud. This is where the open source Telepresence tool can help.
Join Daniel to learn about:
- Quick overview of remote-local ("remocal") options and tooling e.g. “kubectl port-forward”, Skaffold, ksync, Telepresence etc.
- An exploration of how Telepresence can “intercept” or reroute traffic from a specified service in a remote K8s cluster to your local dev machine
-- The benefits of getting a “hot reload” fast feedback loop between applications being developed locally and apps running in the remote environment
JAX London 22: Debugging Microservices "Remocally" in Kubernetes with Telepre...



JAX London 22: Debugging Microservices "Remocally" in Kubernetes with Telepre...Daniel Bryant When enterprise organizations adopt microservices, containers, and cloud native development, the technologies and architectures may change, but the fact remains that we all still add the occasional bug to our code. The main challenge you now face is how to perform integration or end-to-end testing without spinning up all of your microservices locally and driving your laptop fans into high speed! Join me for a tour of testing microservices using a series of Java applications as a case study.
You will learn everything about effective unit testing with mocks, using TestContainers for dependency testing, and using Telepresence to extend your local testing environment into the cloud. Learn when to use each type of test and tooling based on your use case and requirements for realism, speed, and practicality. We will discuss how to utilize containerized dependencies and Docker for testing, including both apps and services you own and those you don’t. We’ll also go over the challenges with scaling container-based application development (you can only run so many microservices locally before minikube melts your laptop). Finally, you’ll see how Telepresence can "intercept" or reroute traffic from a specified service in a remote K8s cluster to your local dev machine.
CloudBuilders 2022: "The Past, Present, and Future of Cloud Native API Gateways"



CloudBuilders 2022: "The Past, Present, and Future of Cloud Native API Gateways"Daniel Bryant The document discusses the evolution of API gateways driven by changes in application architecture and technology. It describes how API gateways evolved from hardware load balancers to software load balancers to application delivery controllers to first-generation API management platforms as applications moved to the cloud and adopted microservices. Managing APIs and microservices at the edge with Kubernetes poses new challenges around scaling edge management and supporting diverse requirements. The document outlines three strategies for managing APIs at the edge with Kubernetes and concludes that choosing an API gateway intentionally is important when adopting cloud-native technologies and platforms.
KubeCon EU 2022: From Kubernetes to PaaS to Err What's Next



KubeCon EU 2022: From Kubernetes to PaaS to Err What's NextDaniel Bryant Developers building applications on Kubernetes today are being asked to not just code applications -- they are also responsible for shipping and running their applications, too. We often talk about needing a Kubernetes platform, but are we really looking for a PaaS? Or instead, are we looking for some kind of developer control plane with a Goldilock-sized collection of tools that provides just the right amount of platform? This talk will look back on my experience of building platforms, both as an end-user and now as part of an organization helping our customers do the same. The key takeaways are:
- Treat platform as a product
- Realize that you can’t have good developer experience (DevEx) without good UX
- Focus on workflows and tooling interoperability
We’ll wrap this talk with a walk-through of the CNCF ecosystem through the developer control plane lens, and look at what’s next in the future of this important emerging category.
Devoxx UK 22: Debugging Java Microservices "Remocally" in Kubernetes with Tel...



Devoxx UK 22: Debugging Java Microservices "Remocally" in Kubernetes with Tel...Daniel Bryant Many Java-based organizations adopt cloud native development practices with the goal of shipping features faster. The technologies and architectures may change when we move to the cloud, but the fact remains that we all still add the occasional bug to our code. The challenge here is that many of your existing local debugging tools and practices can’t be used when everything is running in a container or deployed onto Kubernetes running in the cloud. This is where the open source Telepresence tool can help.
Join me to learn about:
– The challenges with scaling Kubernetes-based Java development i.e. you can only run so many microservices locally before minikube melts your laptop
– Quick overview of remote-local ("removal") options and tooling e.g. “kubectl port-forward”, Skaffold, ksync, Telepresence etc
– An exploration of how Telepresence can “intercept” or reroute traffic from a specified service in a remote K8s cluster to your local dev machine
– The benefits of getting a “hot reload” fast feedback loop between applications being developed locally and apps running in the remote environment
DevXDay KubeCon NA 2021: "From Kubernetes to PaaS to Developer Control Planes"



DevXDay KubeCon NA 2021: "From Kubernetes to PaaS to Developer Control Planes"Daniel Bryant Developers building applications on Kubernetes today are being asked to not just develop applications -- they are also responsible for releasing and running their applications, too. In this talk, we’ll discuss the secular shift towards what Netflix calls “Full Cycle Development” or what Google calls “Service Ownership”. With developers managing so much of the cloud-native development loop, a new class of infrastructure has emerged -- the developer control plane. We’ll explore the evolution from Kubernetes to PaaS, to the developer control planes in use today. We’ll draw on our personal experiences and podcast chats with the larger CNCF community, and discuss real-world examples of developer control planes used at New Relic, Spotify, InVision, and Twitter. We’ll wrap this talk with a walk through of the CNCF ecosystem through the developer control plane lens, and look at what’s next in the future of this important emerging category.
JAX London 2021: Jumpstart Your Cloud Native Development: An Overview of Prac...



JAX London 2021: Jumpstart Your Cloud Native Development: An Overview of Prac...Daniel Bryant At a previous JAX event I talked about effective cloud native Java developer workflow. Two years later and many new developer technologies have come and gone, but I still hear daily from cloud developers about the pain and friction associated with building, debugging, and deploying to the cloud. In this talk I’ll share my latest learning on how to bring the fun and productivity back into delivering Kubernetes-based software.
Join this talk to:
Learn why the core tenets of continuous delivery — speed and safety — must be considered in all parts of the cloud native SDLC
Explore how cloud native coding benefits from thinking separately about the inner development loop, continuous integration, continuous deployment, observability, and analysis
Understand how cloud native best practices and tooling fit together. Learn about artifact syncing (e.g. Skaffold), dev environment bridging (e.g. Telepresence), GitOps (e.g. Argo), and observability-focused monitoring (e.g. Prometheus, Jaeger)
Explore the importance of cultivating an effective cloud platform and associated team of experts
Walk away with an overview of tools that can help you develop and debug effectively when using Kubernetes
Container Days: Easy Debugging of Microservices Running on Kubernetes with Te...



Container Days: Easy Debugging of Microservices Running on Kubernetes with Te...Daniel Bryant Many organizations adopt cloud native development practices with the goal of shipping features faster. The technologies and architectures may change when we move to the cloud, but the fact remains that we all still add the occasional bug to our code. The challenge here is that many of your existing local debugging tools and practices can't be used when everything is running in a container or deployed onto Kubernetes running in the cloud. This is where the open source Telepresence tool can help.
Join me to learn about:
- The challenges with scaling Kubernetes-based Java development i.e. you can only run so many microservices locally before minikube melts your laptop
- An exploration of how Telepresence can "intercept" or reroute traffic from a specified service in a remote K8s cluster to your local dev machine
- The benefits of getting a "hot reload" fast feedback loop between applications being developed locally and apps running in the remote environment
- A tour of Telepresence, from the sidecar proxy deployed into the remote K8s cluster to the CLI
- An overview of using "preview URLs" and header-based routing for the sharing, collaboration, and isolation of changes you are making on your local copy of an intercepted service
Canadian CNCF: "Emissary-ingress 101: An introduction to the CNCF incubation-...



Canadian CNCF: "Emissary-ingress 101: An introduction to the CNCF incubation-...Daniel Bryant By Daniel Bryant, Ambassador Labs We all need to be able to get user traffic into our applications, and your requirements for services running on Kubernetes are no different. "But", I hear you say, "what about the K8s Ingress spec? And how do I observe what's happening under the hood? And who should be responsible for configuring the gateway: dev or ops?" These are all good questions! Join me for a whistle-stop tour of all things emissary-ingress, where we will explore how this new edition to the family of CNCF incubation projects can make your life easier when it comes to routing, observability, and integration into the bigger (people and technology) picture.
MJC 2021: "Debugging Java Microservices Running on Kubernetes with Telepresence"



MJC 2021: "Debugging Java Microservices Running on Kubernetes with Telepresence"Daniel Bryant The document discusses using Telepresence to improve the development workflow for Java microservices running on Kubernetes. Telepresence allows developers to run their code locally while still connecting to the Kubernetes cluster, improving the speed of the inner development loop. It supports various workflows from small to large systems. The benefits of Telepresence include using local tools, connecting to cloud resources, and a very fast inner loop. It is an open source project maintained by the CNCF.
LJC 4/21"Easy Debugging of Java Microservices Running on Kubernetes with Tele...



LJC 4/21"Easy Debugging of Java Microservices Running on Kubernetes with Tele...Daniel Bryant Many Java-based organizations adopt cloud native development practices with the goal of shipping features faster. The technologies and architectures may change when we move to the cloud, but the fact remains that we all still add the occasional bug to our code. The challenge here is that many of your existing local debugging tools and practices can't be used when everything is running in a container or deployed onto Kubernetes running in the cloud. This is where the open source Telepresence tool can help.
Join me to learn about:
- The challenges with scaling Kubernetes-based Java development i.e. you can only run so many microservices locally before minikube melts your laptop
- An exploration of how Telepresence can "intercept" or reroute traffic from a specified service in a remote K8s cluster to your local dev machine
- The benefits of getting a "hot reload" fast feedback loop between applications being developed locally and apps running in the remote environment
- A tour of Telepresence, from the sidecar proxy deployed into the remote K8s cluster to the CLI
- An overview of using "preview URLs" and header-based routing for the sharing, collaboration, and isolation of changes you are making on your local copy of an intercepted service
GOTOpia 2/2021 "Cloud Native Development Without the Toil: An Overview of Pra...



GOTOpia 2/2021 "Cloud Native Development Without the Toil: An Overview of Pra...Daniel Bryant At GOTO Amsterdam in 2019 I presented how to create an effective cloud native developer workflow. Two years later and many new developer technologies have come and gone, but I still hear daily from cloud developers about the pain and friction associated with building, debugging, and deploying to the cloud. In this talk I'll share my latest learning on how to bring the fun and productivity back into delivering Kubernetes-based software.
Join this talk to:
Learn why the core tenets of continuous delivery -- speed and safety -- must be considered in all parts of the cloud native SDLC
Explore how cloud native coding benefits from thinking separately about the inner development loop, continuous integration, continuous deployment, observability, and analysis
Understand how cloud native best practices and tooling fit together. Learn about artifact syncing (e.g. Skaffold), dev environment bridging (e.g. Telepresence), GitOps (e.g. Argo), and observability-focused monitoring (e.g. Prometheus, Jaeger)
Explore the importance of cultivating an effective cloud platform and associated team of experts
Walk away with an overview of tools that can help you develop and debug effectively when using Kubernetes
HashiCorp Webinar: "Getting started with Ambassador and Consul on Kubernetes ...



HashiCorp Webinar: "Getting started with Ambassador and Consul on Kubernetes ...Daniel Bryant HashiCorp Consul integrates with Ambassador to securely route Ingress traffic to Consul Service Mesh when using Kubernetes. When onboarding applications onto a service mesh or when integrating with existing applications outside of the Mesh, a north south API gateway is typically required for communications with clients outside of the network. Ambassador is a Kubernetes API Gateway that allows you to route incoming traffic to your Consul Service Mesh proxies while also providing the ability to leverage advanced API Gateway functionalities such as rate limiting and authentication.
Recently uploaded (20)
"AI in the browser: predicting user actions in real time with TensorflowJS", ...



"AI in the browser: predicting user actions in real time with TensorflowJS", ...Fwdays With AI becoming increasingly present in our everyday lives, the latest advancements in the field now make it easier than ever to integrate it into our software projects. In this session, we’ll explore how machine learning models can be embedded directly into front-end applications. We'll walk through practical examples, including running basic models such as linear regression and random forest classifiers, all within the browser environment.
Once we grasp the fundamentals of running ML models on the client side, we’ll dive into real-world use cases for web applications—ranging from real-time data classification and interpolation to object tracking in the browser. We'll also introduce a novel approach: dynamically optimizing web applications by predicting user behavior in real time using a machine learning model. This opens the door to smarter, more adaptive user experiences and can significantly improve both performance and engagement.
In addition to the technical insights, we’ll also touch on best practices, potential challenges, and the tools that make browser-based machine learning development more accessible. Whether you're a developer looking to experiment with ML or someone aiming to bring more intelligence into your web apps, this session will offer practical takeaways and inspiration for your next project.
Build your own NES Emulator... with Kotlin



Build your own NES Emulator... with KotlinArtur Skowroński For those who have ever wanted to recreate classic games, this presentation covers my five-year journey to build a NES emulator in Kotlin. Starting from scratch in 2020 (you can probably guess why), I’ll share the challenges posed by the architecture of old hardware, performance optimization (surprise, surprise), and the difficulties of emulating sound. I’ll also highlight which Kotlin features shine (and why concurrency isn’t one of them). This high-level overview will walk through each step of the process—from reading ROM formats to where GPT can help, though it won’t write the code for us just yet. We’ll wrap up by launching Mario on the emulator (hopefully without a call from Nintendo).
Multistream in SIP and NoSIP @ OpenSIPS Summit 2025



Multistream in SIP and NoSIP @ OpenSIPS Summit 2025Lorenzo Miniero Slides for my "Multistream support in the Janus SIP and NoSIP plugins" presentation at the OpenSIPS Summit 2025 event.
They describe my efforts refactoring the Janus SIP and NoSIP plugins to allow for the gatewaying of an arbitrary number of audio/video streams per call (thus breaking the current 1-audio/1-video limitation), plus some additional considerations on what this could mean when dealing with application protocols negotiated via SIP as well.
The fundamental misunderstanding in Team Topologies



The fundamental misunderstanding in Team TopologiesPatricia Aas In this talk I will break down the argument presented in the book and argue that it is fundamentally ill-conceived, building on weak and erroneous assumptions. And that this leads to a "solution" that is not only flawed, but outright wrong, and might cost your organization vast sums of money for far inferior results.
With Claude 4, Anthropic redefines AI capabilities, effectively unleashing a ...



With Claude 4, Anthropic redefines AI capabilities, effectively unleashing a ...SOFTTECHHUB With the introduction of Claude Opus 4 and Sonnet 4, Anthropic's newest generation of AI models is not just an incremental step but a pivotal moment, fundamentally reshaping what's possible in software development, complex problem-solving, and intelligent business automation.
Fully Open-Source Private Clouds: Freedom, Security, and Control



Fully Open-Source Private Clouds: Freedom, Security, and ControlShapeBlue In this presentation, Swen Brüseke introduced proIO's strategy for 100% open-source driven private clouds. proIO leverage the proven technologies of CloudStack and LINBIT, complemented by professional maintenance contracts, to provide you with a secure, flexible, and high-performance IT infrastructure. He highlighted the advantages of private clouds compared to public cloud offerings and explain why CloudStack is in many cases a superior solution to Proxmox.
--
The CloudStack European User Group 2025 took place on May 8th in Vienna, Austria. The event once again brought together open-source cloud professionals, contributors, developers, and users for a day of deep technical insights, knowledge sharing, and community connection.
Wondershare Filmora 14.3.2 Crack + License Key Free for Windows PC



Wondershare Filmora 14.3.2 Crack + License Key Free for Windows PCMudasir COPY & PASTE LINK 👉👉👉
https://pcsoftsfull.org/dl
Wondershare Filmora for Windows PC is an all-in-one home video editor with powerful functionality and a fully stacked feature set. Filmora has a simple drag-and-droptop interface, allowing you to be artistic with the story you want to create.
Droidal: AI Agents Revolutionizing Healthcare



Droidal: AI Agents Revolutionizing HealthcareDroidal LLC Droidal’s AI Agents are transforming healthcare by bringing intelligence, speed, and efficiency to key areas such as Revenue Cycle Management (RCM), clinical operations, and patient engagement. Built specifically for the needs of U.S. hospitals and clinics, Droidal's solutions are designed to improve outcomes and reduce administrative burden.
Through simple visuals and clear examples, the presentation explains how AI Agents can support medical coding, streamline claims processing, manage denials, ensure compliance, and enhance communication between providers and patients. By integrating seamlessly with existing systems, these agents act as digital coworkers that deliver faster reimbursements, reduce errors, and enable teams to focus more on patient care.
Droidal's AI technology is more than just automation — it's a shift toward intelligent healthcare operations that are scalable, secure, and cost-effective. The presentation also offers insights into future developments in AI-driven healthcare, including how continuous learning and agent autonomy will redefine daily workflows.
Whether you're a healthcare administrator, a tech leader, or a provider looking for smarter solutions, this presentation offers a compelling overview of how Droidal’s AI Agents can help your organization achieve operational excellence and better patient outcomes.
A free demo trial is available for those interested in experiencing Droidal’s AI Agents firsthand. Our team will walk you through a live demo tailored to your specific workflows, helping you understand the immediate value and long-term impact of adopting AI in your healthcare environment.
To request a free trial or learn more:
https://droidal.com/
Master tester AI toolbox - Kari Kakkonen at Testaus ja AI 2025 Professio



Master tester AI toolbox - Kari Kakkonen at Testaus ja AI 2025 ProfessioKari Kakkonen My slides at Professio Testaus ja AI 2025 seminar in Espoo, Finland.
Deck in English, even though I talked in Finnish this time, in addition to chairing the event.
I discuss the different motivations for testing to use AI tools to help in testing, and give several examples in each categories, some open source, some commercial.
MCP Dev Summit - Pragmatic Scaling of Enterprise GenAI with MCP



MCP Dev Summit - Pragmatic Scaling of Enterprise GenAI with MCPSambhav Kothari MCP Dev Summit Talk By Sambhav Kothari - Head of AI Productivity at Bloomberg.
From Legacy to Cloud-Native: A Guide to AWS Modernization.pptx



From Legacy to Cloud-Native: A Guide to AWS Modernization.pptxMohammad Jomaa From Legacy to Cloud-Native: A Guide
to AWS Modernization
UiPath Community Berlin: Studio Tips & Tricks and UiPath Insights



UiPath Community Berlin: Studio Tips & Tricks and UiPath InsightsUiPathCommunity Join the UiPath Community Berlin (Virtual) meetup on May 27 to discover handy Studio Tips & Tricks and get introduced to UiPath Insights. Learn how to boost your development workflow, improve efficiency, and gain visibility into your automation performance.
📕 Agenda:
- Welcome & Introductions
- UiPath Studio Tips & Tricks for Efficient Development
- Best Practices for Workflow Design
- Introduction to UiPath Insights
- Creating Dashboards & Tracking KPIs (Demo)
- Q&A and Open Discussion
Perfect for developers, analysts, and automation enthusiasts!
This session streamed live on May 27, 18:00 CET.
Check out all our upcoming UiPath Community sessions at:
👉 https://community.uipath.com/events/
Join our UiPath Community Berlin chapter:
👉 https://community.uipath.com/berlin/
AI in Java - MCP in Action, Langchain4J-CDI, SmallRye-LLM, Spring AI



AI in Java - MCP in Action, Langchain4J-CDI, SmallRye-LLM, Spring AIBuhake Sindi This is the presentation I gave with regards to AI in Java, and the work that I have been working on. I've showcased Model Context Protocol (MCP) in Java, creating server-side MCP server in Java. I've also introduced Langchain4J-CDI, previously known as SmallRye-LLM, a CDI managed too to inject AI services in enterprise Java applications. Also, honourable mention: Spring AI.
European Accessibility Act & Integrated Accessibility Testing



European Accessibility Act & Integrated Accessibility TestingJulia Undeutsch Emma Dawson will guide you through two important topics in this session.
Firstly, she will prepare you for the European Accessibility Act (EAA), which comes into effect on 28 June 2025, and show you how development teams can prepare for it.
In the second part of the webinar, Emma Dawson will explore with you various integrated testing methods and tools that will help you improve accessibility during the development cycle, such as Linters, Storybook, Playwright, just to name a few.
Focus: European Accessibility Act, Integrated Testing tools and methods (e.g. Linters, Storybook, Playwright)
Target audience: Everyone, Developers, Testers
Artificial Intelligence (Kecerdasan Buatan).pdf



Artificial Intelligence (Kecerdasan Buatan).pdfNufiEriKusumawati AI stands for Artificial Intelligence.
It refers to the ability of a computer system or machine to perform tasks that usually require human intelligence, such as:
thinking,
learning from experience,
solving problems, and
making decisions.
John Carmack’s Slides From His Upper Bound 2025 Talk



John Carmack’s Slides From His Upper Bound 2025 TalkRazin Mustafiz Source: https://docs.google.com/presentation/d/1GmGe9ref1nxEX_ekDuJXhildpWGhLEYBMeXCclVECek/edit?usp=sharing
Content and eLearning Standards: Finding the Best Fit for Your-Training



Content and eLearning Standards: Finding the Best Fit for Your-TrainingRustici Software Tammy Rutherford, Managing Director of Rustici Software, walks through the pros and cons of different standards to better understand which standard is best for your content and chosen technologies.
Supercharge Your AI Development with Local LLMs



Supercharge Your AI Development with Local LLMsFrancesco Corti In today's AI development landscape, developers face significant challenges when building applications that leverage powerful large language models (LLMs) through SaaS platforms like ChatGPT, Gemini, and others. While these services offer impressive capabilities, they come with substantial costs that can quickly escalate especially during the development lifecycle. Additionally, the inherent latency of web-based APIs creates frustrating bottlenecks during the critical testing and iteration phases of development, slowing down innovation and frustrating developers.
This talk will introduce the transformative approach of integrating local LLMs directly into their development environments. By bringing these models closer to where the code lives, developers can dramatically accelerate development lifecycles while maintaining complete control over model selection and configuration. This methodology effectively reduces costs to zero by eliminating dependency on pay-per-use SaaS services, while opening new possibilities for comprehensive integration testing, rapid prototyping, and specialized use cases.
A Comprehensive Guide on Integrating Monoova Payment Gateway



A Comprehensive Guide on Integrating Monoova Payment Gatewaydanielle hunter Monoova is a merchant-centric platform with integrations for payments, marketing, loyalty programs, and customer insights.
CodeOne SF 2018 "Are you deploying and operating with security in mind?"
- 1. Are You Deploying and Operating with Security in Mind? Steve Poole @spoole167 Daniel Bryant @danielbryantuk
- 2. Containers: Expectations versus reality 22/10/2018 @danielbryantuk “DevOps”
- 3. tl;dr • Using containers does not make you invulnerable from attack. • Practical mitigation of risk needs you to understand how you are open to attack. • Practical mitigation requires you to pay attention to how you develop software –and how you behave • Adding metadata to containers is vital for understanding your software supply chain and current state of the world in production • Testing system quality attributes ("NFRs") within an automated build pipeline is table stakes for today's threat landscape. 22/10/2018 @danielbryantuk
- 4. @danielbryantuk Independent Tech Consultant, Product Architect at Datawire Architecture, DevOps, Java, microservices, cloud, containers 22/10/2018 @danielbryantuk @spoole167 Developer Advocate, IBM Java (pre 1.0), DevOps, security, cloud, containers
- 5. The economics of crime – and why you’re culpable 22/10/2018 @danielbryantuk
- 6. In 2016 Cybercrime was estimated to be worth 450 Billion Dollars @spoole167 Cybercrime is the most profitable type of crime In 2016 The illicit drug trade was estimated to be worth 435 Billion Dollars
- 7. Cybercrime is the most profitable type of crime • Guess which one has the least risk to the criminal ? • Guess which is growing the fastest ? • Guess which one is the hardest to prosecute ? • Guess which one is predicted to reach 2100 Billion Dollars by 2019? • Guess which one is predicted to reach 6000 Billion Dollars by 2021? @spoole167
- 8. 0 1000 2000 3000 4000 5000 6000 2013 2014 2015 2016 2017 2018 2019 2020 2021 Cybercrime Drug trade
- 9. That’s about $600 for every person on the planet In the US it’s about $8000 each
- 10. Don’t agree? “The bad guys prey on the weak, vulnerable and ignorant” That’s you @spoole167
- 11. Ever googled for: “very trusting trust manager” “Getting Java to accept all certs over HTTPS” “How to Trust Any SSL Certificate” “Disable Certificate Validation in Java” @spoole167
- 12. TrustManager[] trustAllCerts = new TrustManager[]{ new X509TrustManager() { public X509Certificate[] getAcceptedIssuers() { return null; } public void checkClientTrusted( X509Certificate[] certs, String authType) { } public void checkServerTrusted( X509Certificate[] certs, String authType) { } public boolean isClientTrusted( X509Certificate[] cert) { return true; } public boolean isServerTrusted( X509Certificate[] cert) { return true; } }} Ever written something like this? @spoole167
- 13. We’ve all done something like that @spoole167
- 14. We’ve all done something like that We do it all the time @spoole167
- 15. We’ve all done something like that We do it all the time The whole world does it How bad can it be? @spoole167
- 16. We’ve all done something like that We do it all the time The whole world does it Github search “implements TrustManager” …. @spoole167
- 17. We’ve found 72,609 code results AlwaysValidTrustManager TrustAllServersWrappingTrustManager A very friendly, accepting trust manager factory. Allows anything through. all kind of certificates are accepted and trusted. A very trusting trust manager that accepts anything // Install the all-trusting trust manager OverTrustingTrustProvider AllTrustingSecurityManagerPlugin.java AcceptingTrustManagerFactory.java AllTrustingCertHttpRequester.java
- 18. And.. given how important using https correctly is…
- 19. Why do we turn it off? curl –insecure wget --no-check-certificate sudo apt-get --allow-unauthenticated
- 20. For reasonable reasons? • “The server I access is self-signed” • “I want to access multiple servers “ Unexpectedly? • “I thought I was using the tool correctly” • “I didn’t realize what the default setting was” • “I trusted the tool to do the right thing” Maliciously? • “Someone changed the script and I don’t know why”
- 22. Attackers use vulnerabilities to get into your system And go through your system to another (and repeat) To steal your data To change your data To crash your systems Use your compute power
- 23. if (multiWrapper.hasErrors()) { if(validation!=null){ validation.addActionError( … ); } } This is a major vulnerability
- 24. So is this. Just two characters
- 25. Vulnerabilities are almost always simple there are no smoking guns Exploits are chaining together vulnerabilities https://www.flickr.com/photos/84744710@N06/
- 26. Apache struts 2 - the Equifax affair Attackers used Remote Code Execution to steal data over a long period CVE-2017-5638 The Jakarta Multipart parser in Apache Struts 2 2.3.x before 2.3.32 and 2.5.x before 2.5.10.1 has incorrect exception handling and error- message generation during file-upload attempts, which allows remote attackers to execute arbitrary commands via a crafted Content-Type, Content-Disposition, or Content-Length HTTP header, as exploited in the wild in March 2017 with a Content-Type header containing a #cmd= string.
- 27. Content-Type: %{(#_='multipart/form-data'). (#[email protected]@DEFAULT_MEMBER_ACCESS) . (@java.lang.Runtime@getRuntime().exec('curl localhost:8000'))} https://dzone.com/articles/will-it-pwn-cve-2017-5638-remote-code- execution-in Apache Struts OGNL If type contains “multipart/form-data’ try to parse it as form data This fails and as part of the building an error message the OGNL is evaluated…
- 28. Large Scale Exploit March 9 First ‘whoami’ is run AprMar May Jun Jul Aug Sept March 7 Apache Struts releases updated version to thwart vulnerability CVE-2017-5638 July 29 Breach is discovered by Equifax. Sept 7 A new strutcs RCE vulnerability is announced and fixed. CVE-2017-9805 Probe Crisis Management March 5 vulnerability and fixed bit.ly/devoxx-sec-workshop
- 29. Time to EXPLOIT?Source: Adapted from IBM X-Force / Analysis by Gartner Research (September 2016) Year of Date Reported 2006 2007 2008 2009 2010 2011 2012 2013 2104 2015 10 20 30 40 50 0 AverageDaystoExploit Average 45 15 2017
- 30. 2 days
- 31. The bad news • Vulnerabilities are the gateway into the server Systems with vulnerabilities are easily found Everyone has vulnerabilities 2 days from publication to attack Exploits are easily found • Developers don’t think about security • Application design thinking suffers • Development processes etc suffer
- 32. The truth is • Most of the time you’re attacked just because your more vulnerable and weak than the next guy • Keeping up to date with vulnerability patches keeps you lower down the list and hence safer • Once they get into your system – they spend a long time looking around and finding all your weaknesses
- 34. Container technology 101 • OS-level virtualisation • Just a bunch of (Linux) processes • cgroups, namespaces, rootfs • Package and execute software 22/10/2018 @danielbryantuk
- 35. How do you view containers? 22/10/2018 @danielbryantuk
- 36. Sorry, it’s more like… 22/10/2018 @danielbryantuk
- 37. Container Runtime Security 22/10/2018 @danielbryantuk
- 38. Container runtime security 101 22/10/2018 @danielbryantuk https://kubernetes.io/docs/tasks/configure-pod-container/security-context/ https://www.infoq.com/news/2016/08/secure-docker-microservices
- 39. Privileges and Capabilities 22/10/2018 @danielbryantuk
- 40. Container Supply Chain 22/10/2018 @danielbryantuk
- 41. Lesson learned: Metadata is valuable • Application metadata • Version / GIT SHA • Build metadata • Build date • Image name • Vendor • Quality metadata • QA control, signed binaries, ephemeral support • Security profiles (AppArmor), Security audited etc 22/10/2018 @danielbryantuk
- 42. Metadata - Adding Labels at build time • Docker Labels • Add key/value data to image 22/10/2018 @danielbryantuk
- 43. Metadata - Adding Labels at build time • Microscaling Systems’ Makefile • Labelling automated builds on DockerHub (h/t Ross Fairbanks) • Create file ‘/hooks/build’ • label-schema.org • microbadger.com 22/10/2018 @danielbryantuk
- 44. Metadata - Adding Labels at runtime 22/10/2018 @danielbryantuk $ docker run -d --label uk.co.danielbryant.lbname=frontdoor nginx • Can ’docker commit’, but creates new image • Not possible to update running container • Docker Proposal: Update labels #21721
- 45. External registry with metadata support 22/10/2018 @danielbryantuk
- 46. Grafeas + Kritis 22/10/2018 @danielbryantuk
- 48. Testing in a Java Build Pipeline 22/10/2018 @danielbryantuk
- 49. Testing security in the build pipeline • PMD /Findsecbugs • OWASP Dependency check • DockerHub Scanner / CoreOS Clair • Bdd-security (OWASP ZAP) / Arachni • Gauntlt / Serverspec • Docker Bench / KubeBench 22/10/2018 @danielbryantuk
- 50. Security Visibility: Basic (Java) Code Scanning 22/10/2018 @danielbryantuk
- 52. Static Image Scanning 22/10/2018 @danielbryantuk github.com/arminc/clair-scanner
- 53. Delaying NFRs to the ‘Last Responsible Moment’ Newsflash! Sometimes the last responsible moment is up-front Modern platforms/architectures don’t necessarily make this easier 22/10/2018 @danielbryantuk
- 54. Bonus: Secure runtime comms 22/10/2018 @danielbryantuk
- 55. Google’s BeyondCorp: Zero Trust Networks 22/10/2018 @danielbryantuk cloud.google.com/beyondcorp/
- 56. Securing communications • Mutial TLS (mTLS) • Intentions • Policy-based controls 22/10/2018 @danielbryantuk
- 57. mTLS: Securing communications 22/10/2018 @danielbryantuk
- 59. In summary • Using containers does not make you invulnerable from attack. Used wisely containers can substantially reduce your exposure. Used poorly containers substantially increase your risk. • Practical mitigation of risk needs you to understand how you are open to attack. Practical mitigation requires you to pay attention to how you develop software –and how you behave • Adding metadata to containers is vital for understanding your software supply chain and current state of the world in production • Testing system quality attributes ("NFRs") within an automated build pipeline is table stakes for today's threat landscape. 22/10/2018 @danielbryantuk
- 60. Thanks for listening… Twitter: @spoole167 Email: Twitter: @danielbryantuk Email: [email protected] 22/10/2018 @danielbryantuk

