Computer memory management
Download as ppt, pdf1 like3,184 views
This document discusses memory management techniques including basic memory management, swapping, virtual memory, page replacement algorithms, segmentation, and the implementation of paging systems. Key concepts covered include memory hierarchies with fast cache, slower main memory, and disk storage; fixed partitioning and multiprogramming; page tables; translation lookaside buffers; page replacement with FIFO, LRU, and clock algorithms; and segmentation combined with paging in systems like MULTICS and the Pentium.
1 of 63
Downloaded 173 times



























































Ad
Recommended
Memory management
Memory managementCHANDERPRABHU JAIN COLLEGE OF HIGHER STUDIES & SCHOOL OF LAW The document provides an extensive overview of memory management techniques, including swapping, contiguous memory allocation, paging, and segmentation. It covers key concepts such as logical vs. physical address spaces, address binding methods, dynamic loading, and linking, along with hardware implementation like the memory-management unit (MMU) and page tables. The Intel Pentium's architecture, which supports both segmentation and paging, is highlighted as an example of these principles in action.
17. Recovery System in DBMS
17. Recovery System in DBMSkoolkampus The document discusses various database recovery techniques including log-based recovery, shadow paging recovery, and recovery with concurrent transactions. Log-based recovery uses a log to record transactions and supports either deferred or immediate database modification. Shadow paging maintains a shadow page table to allow recovery to a previous state. Checkpointing improves recovery performance. Recovery for concurrent transactions uses undo and redo lists constructed during the recovery process.
Computer architecture control unit
Computer architecture control unitMazin Alwaaly The document outlines the architecture and functionality of a computer's control unit, detailing its role in executing instructions through control signals and cycles. It discusses different types of control unit implementations, such as hardwired and microprogrammed control, and compares their characteristics. Additionally, it covers the control registers, the fetch sequence, and various cycles like indirect and interrupt cycles that are integral to program execution.
Disk scheduling
Disk schedulingJ.T.A.JONES The document discusses different disk scheduling policies and RAID levels. It describes FIFO, SSTF, SCAN, C-SCAN, and FSCAN scheduling policies and how they differ in terms of seek time optimization. It also explains RAID levels 0, 1, and 5 and their tradeoffs between performance, reliability, and cost. An example trace compares the average seek lengths for different scheduling policies.
File Allocation Methods.ppt
File Allocation Methods.pptBharathiLakshmiAAssi This document summarizes different file system structures and allocation methods. It describes the logical layers of a file system from the application to the physical devices. It then explains three common allocation methods: contiguous allocation, linked allocation, and indexed allocation. Contiguous allocation stores files in contiguous disk blocks but can lead to fragmentation. Linked allocation uses pointers but is unreliable and wastes space. Indexed allocation uses an index block to point to other data blocks, reducing fragmentation and pointer space waste. It analyzes the performance of reading a block from each type of allocation.
Kernel I/O subsystem
Kernel I/O subsystemAtiKa Bhatti The document defines the kernel as the core of an operating system that provides basic services for I/O. It discusses I/O services provided by the kernel like scheduling, buffering, caching, spooling, device reservation, error handling, and I/O protection. The document also describes data structures like open file tables that the kernel uses to track the state of I/O components and activities.
Chapter 10 - File System Interface
Chapter 10 - File System InterfaceWayne Jones Jnr This chapter discusses file systems and their interfaces. It covers key concepts like files, directories, access methods, mounting file systems, file sharing, and protection. Directories provide structure and organization for files on a file system using tree or graph structures. File systems support operations like creating/deleting files, searching directories, and opening/closing files. They also implement features like file sharing across networks and access control using permissions.
Disk structure
Disk structureShareb Ismaeel The document discusses the physical and logical structures of disk storage, including hard disks, floppy disks, and other storage technologies. Key concepts include disk geometry, tracks, sectors, clusters, and the logical organization of disks into components like the Master Boot Record (MBR), DOS Boot Record (DBR), File Allocation Table (FAT), root directory, and data area. Understanding these structures is essential for describing how information is stored and managed on hard drives.
Contiguous Memory Allocation.ppt
Contiguous Memory Allocation.pptinfomerlin Contiguous allocation is an early method for allocating main memory between the operating system and user processes. Each process is contained within a single contiguous section of memory. Relocation and limit registers are used to protect processes from each other and allow transient changes to the operating system. Multiple-partition allocation allocates variable sized partitions to processes out of memory holes. Storage allocation approaches like first-fit and best-fit are used to allocate partitions from the holes. Fragmentation can occur both externally and internally, taking up space that cannot be used.
System calls
System callsBernard Senam This presentation discusses system calls and provides an overview of their key aspects:
System calls provide an interface between processes and the operating system. They allow programs to request services from the OS like reading/writing files. There are different methods of passing parameters to the OS, such as via registers, parameter blocks, or pushing to the stack. System calls fall into categories including process control, file management, device management, information maintenance, and communication. An example is given of how system calls would be used in a program to copy data between two files.
contiguous memory allocation.pptx
contiguous memory allocation.pptxRajapriya82 The document discusses various methods for managing contiguous memory allocation, focusing on logical and physical addresses, and the use of relocation and limit registers for memory protection. It outlines memory partitioning strategies, including fixed-sized partitions and different allocation strategies like first-fit, best-fit, and worst-fit, along with issues of fragmentation. Compaction techniques and noncontiguous memory allocation are suggested as solutions to external fragmentation challenges.
Conditional branches
Conditional branchesDilip Mathuria The document presents a detailed overview of conditional branches in pipelined computers, discussing instruction pipelining, stages, and the impacts of conditional branches on performance. It explains different types of conditional instructions, techniques for dealing with branches, and various approaches such as branch prediction and loop buffers. Additionally, it covers internal forwarding of instructions to improve CPU efficiency by reducing unnecessary memory accesses.
Interrupts
Interruptsguest2e9811e Interrupts allow external events to suspend and later resume processes running on a computer. They improve processor utilization by allowing the operating system to interrupt running processes to respond to external events like user input or I/O device completion. There are different types of interrupts including program-generated, timer, I/O, and hardware failure interrupts. When an interrupt occurs, the CPU saves its context and executes an interrupt handling routine that calls the appropriate interrupt service routine to handle the interrupt before resuming the original process.
Paging and segmentation
Paging and segmentationPiyush Rochwani This document summarizes and compares paging and segmentation, two common memory management techniques. Paging divides physical memory into fixed-size frames and logical memory into same-sized pages. It maps pages to frames using a page table. Segmentation divides logical memory into variable-sized segments and uses a segment table to map segment numbers to physical addresses. Paging avoids external fragmentation but can cause internal fragmentation, while segmentation avoids internal fragmentation but can cause external fragmentation. Both approaches separate logical and physical address spaces but represent different models of how a process views memory.
Memory Management in OS
Memory Management in OSvampugani This document discusses different memory management techniques used in operating systems. It begins by describing the basic components and functions of memory. It then explains various memory management algorithms like overlays, swapping, paging and segmentation. Overlays divide a program into instruction sets that are loaded and unloaded as needed. Swapping loads entire processes into memory for execution then writes them back to disk. Paging and segmentation are used to map logical addresses to physical addresses through page tables and segment tables respectively. The document compares advantages and limitations of these approaches.
Unix Memory Management - Operating Systems
Unix Memory Management - Operating SystemsDrishti Bhalla The document discusses memory management techniques in UNIX, including swapping, demand paging, and how they are implemented in Intel Pentium hardware. Swapping involves copying processes from memory to disk swap space to free up memory. Demand paging only loads pages into memory when accessed. The Pentium supports segmentation and paging, where logical addresses are translated to linear then physical addresses using segment descriptors, page directories and tables.
Operating system memory management
Operating system memory managementrprajat007 Memory management is an operating system function that handles primary memory allocation and tracks both used and free memory. It incorporates mechanisms like dynamic loading and linking, logical vs. physical address spaces, and techniques such as swapping and fragmentation. Various allocation strategies, including single-partition and multiple-partition allocation, along with paging and segmentation, are employed to optimize memory usage and mitigate fragmentation.
Chapter 11 - File System Implementation
Chapter 11 - File System ImplementationWayne Jones Jnr Chapter 11 focuses on file system implementation, covering local and remote file system structures, allocation methods, free-space management, and recovery processes. It discusses virtual file systems (VFS), various allocation strategies (contiguous, linked, indexed), and the efficiency and performance factors related to these systems. Additionally, it explores the NFS (Network File System) architecture, emphasizing its interoperability across heterogeneous systems and detailing remote file operations.
System call
System callSumant Diwakar System calls provide an interface between processes and the operating system. They allow programs to request services like reading/writing files or communicating over a network. Common system calls include opening/closing files, reading/writing data, process creation/termination, and requesting the current time/date. System calls are grouped into categories like process control, file management, device management, information maintenance, and communications.
Ch02 early system memory management
Ch02 early system memory managementJacob Cadeliña This chapter discusses early memory management techniques including fixed partitions, dynamic partitions, and relocatable dynamic partitions. It describes how these systems allocate and deallocate memory using concepts like first-fit and best-fit allocation, and how they utilize compaction to optimize memory usage. Special registers are used to track memory locations as programs are relocated during compaction.
External memory - Computer Architecture
External memory - Computer ArchitectureBretz Harllynne Moltio Magnetic disks remain the most important component of external memory. Data is recorded on disks through magnetic read and write heads. Disks are organized into tracks and sectors for efficient data access. RAID systems provide data redundancy or higher performance through striping and mirroring across multiple disks. Optical disks like CDs and DVDs store data through microscopic pits and lands read by lasers, and use constant linear velocity to increase storage capacity toward the disk edge.
Memory mapping
Memory mappingSnehalataAgasti Cache memory is located between the processor and main memory. It is smaller and faster than main memory. There are two types of cache memory policies - write-back and write-through. Mapping is a technique that maps CPU-generated memory addresses to cache lines. There are three types of mapping - direct, associative, and set associative. Direct mapping maps each main memory block to a single cache line using the formula: cache line number = main memory block number % number of cache lines. This can cause conflict misses.
12 processor structure and function
12 processor structure and functionSher Shah Merkhel This chapter discusses processor structure and function. It covers the basic components of a CPU including registers, instruction cycles, and data flow. Key points include:
- A CPU must fetch, interpret, fetch operands for, process, and write data from instructions. It uses registers for temporary storage and a program counter to keep track of instructions.
- Common registers include general purpose, data, address, condition code, control/status, and program status registers. General purpose registers can vary in number, size, and whether they are general or specialized use.
- An instruction cycle involves fetching an instruction from memory, decoding it, fetching operands, executing the instruction, and writing results. Pipelining and branch prediction are
File system structure
File system structuresangrampatil81 The document discusses the structure of file systems. It explains that a file system provides mechanisms for storing and accessing files and data. It uses a layered approach, with each layer responsible for specific tasks related to file management. The logical file system contains metadata and verifies permissions and paths. It maps logical file blocks to physical disk blocks using a file organization module, which also manages free space. The basic file system then issues I/O commands to access those physical blocks via device drivers, with I/O controls handling interrupts.
Memory Organization
Memory OrganizationKamal Acharya The document discusses the different types of memory in digital computers, including main memory, associative memory, cache memory, and virtual memory, detailing their organization, functions, and access methods. It explains the memory hierarchy, the role of auxiliary memory, and various mapping techniques for cache memory, such as associative, direct, and set-associative mapping. Additionally, the document covers memory addressing, data storage, and mechanisms like page replacement in virtual memory systems.
Scheduling algorithms
Scheduling algorithmsChankey Pathak The document discusses various scheduling algorithms used in operating systems including:
- First Come First Serve (FCFS) scheduling which services processes in the order of arrival but can lead to long waiting times.
- Shortest Job First (SJF) scheduling which prioritizes the shortest processes first to minimize waiting times. It can be preemptive or non-preemptive.
- Priority scheduling assigns priorities to processes and services the highest priority process first, which can potentially cause starvation of low priority processes.
- Round Robin scheduling allows equal CPU access to all processes by allowing each a small time quantum or slice before preempting to the next process.
Memory Hierarchy
Memory Hierarchychauhankapil The document discusses the memory hierarchy in computers. It describes the different levels of memory from fastest to slowest as register memory, cache memory, main memory (RAM and ROM), and auxiliary memory (magnetic tapes, hard disks, etc.). The main memory directly communicates with the CPU while the auxiliary memory provides backup storage and needs to transfer data to main memory to be accessed by the CPU. A cache memory is also used to increase processing speed.
Interrupt
InterruptSiddique Ibrahim Interrupts allow input/output devices to alert the processor when they are ready. When an interrupt request occurs, the processor saves its context and jumps to an interrupt service routine. It then acknowledges the interrupt and restores its context before returning to the original instruction. Processors have mechanisms for prioritizing interrupts and enabling/disabling them to avoid infinite loops or unintended requests.
Memory Management | Computer Science
Memory Management | Computer ScienceTransweb Global Inc The document provides an introduction to memory management in operating systems, detailing its functions like swapping processes between primary memory and disk. It describes logical and physical address spaces, types of memory management, cache memory, and virtual memory. Additionally, it mentions the '0x0000001a' error related to memory malfunctions and offers a link for further information.
Memory management
Memory managementRajni Sirohi The document discusses memory management in operating systems. It covers key concepts like logical versus physical addresses, binding logical addresses to physical addresses, and different approaches to allocating memory like contiguous allocation. It also discusses dynamic storage allocation using a buddy system to merge adjacent free spaces, as well as compaction techniques to reduce external fragmentation by moving free memory blocks together. Memory management aims to efficiently share physical memory between processes using mechanisms like partitioning memory and enforcing protection boundaries.
More Related Content
What's hot (20)
Contiguous Memory Allocation.ppt
Contiguous Memory Allocation.pptinfomerlin Contiguous allocation is an early method for allocating main memory between the operating system and user processes. Each process is contained within a single contiguous section of memory. Relocation and limit registers are used to protect processes from each other and allow transient changes to the operating system. Multiple-partition allocation allocates variable sized partitions to processes out of memory holes. Storage allocation approaches like first-fit and best-fit are used to allocate partitions from the holes. Fragmentation can occur both externally and internally, taking up space that cannot be used.
System calls
System callsBernard Senam This presentation discusses system calls and provides an overview of their key aspects:
System calls provide an interface between processes and the operating system. They allow programs to request services from the OS like reading/writing files. There are different methods of passing parameters to the OS, such as via registers, parameter blocks, or pushing to the stack. System calls fall into categories including process control, file management, device management, information maintenance, and communication. An example is given of how system calls would be used in a program to copy data between two files.
contiguous memory allocation.pptx
contiguous memory allocation.pptxRajapriya82 The document discusses various methods for managing contiguous memory allocation, focusing on logical and physical addresses, and the use of relocation and limit registers for memory protection. It outlines memory partitioning strategies, including fixed-sized partitions and different allocation strategies like first-fit, best-fit, and worst-fit, along with issues of fragmentation. Compaction techniques and noncontiguous memory allocation are suggested as solutions to external fragmentation challenges.
Conditional branches
Conditional branchesDilip Mathuria The document presents a detailed overview of conditional branches in pipelined computers, discussing instruction pipelining, stages, and the impacts of conditional branches on performance. It explains different types of conditional instructions, techniques for dealing with branches, and various approaches such as branch prediction and loop buffers. Additionally, it covers internal forwarding of instructions to improve CPU efficiency by reducing unnecessary memory accesses.
Interrupts
Interruptsguest2e9811e Interrupts allow external events to suspend and later resume processes running on a computer. They improve processor utilization by allowing the operating system to interrupt running processes to respond to external events like user input or I/O device completion. There are different types of interrupts including program-generated, timer, I/O, and hardware failure interrupts. When an interrupt occurs, the CPU saves its context and executes an interrupt handling routine that calls the appropriate interrupt service routine to handle the interrupt before resuming the original process.
Paging and segmentation
Paging and segmentationPiyush Rochwani This document summarizes and compares paging and segmentation, two common memory management techniques. Paging divides physical memory into fixed-size frames and logical memory into same-sized pages. It maps pages to frames using a page table. Segmentation divides logical memory into variable-sized segments and uses a segment table to map segment numbers to physical addresses. Paging avoids external fragmentation but can cause internal fragmentation, while segmentation avoids internal fragmentation but can cause external fragmentation. Both approaches separate logical and physical address spaces but represent different models of how a process views memory.
Memory Management in OS
Memory Management in OSvampugani This document discusses different memory management techniques used in operating systems. It begins by describing the basic components and functions of memory. It then explains various memory management algorithms like overlays, swapping, paging and segmentation. Overlays divide a program into instruction sets that are loaded and unloaded as needed. Swapping loads entire processes into memory for execution then writes them back to disk. Paging and segmentation are used to map logical addresses to physical addresses through page tables and segment tables respectively. The document compares advantages and limitations of these approaches.
Unix Memory Management - Operating Systems
Unix Memory Management - Operating SystemsDrishti Bhalla The document discusses memory management techniques in UNIX, including swapping, demand paging, and how they are implemented in Intel Pentium hardware. Swapping involves copying processes from memory to disk swap space to free up memory. Demand paging only loads pages into memory when accessed. The Pentium supports segmentation and paging, where logical addresses are translated to linear then physical addresses using segment descriptors, page directories and tables.
Operating system memory management
Operating system memory managementrprajat007 Memory management is an operating system function that handles primary memory allocation and tracks both used and free memory. It incorporates mechanisms like dynamic loading and linking, logical vs. physical address spaces, and techniques such as swapping and fragmentation. Various allocation strategies, including single-partition and multiple-partition allocation, along with paging and segmentation, are employed to optimize memory usage and mitigate fragmentation.
Chapter 11 - File System Implementation
Chapter 11 - File System ImplementationWayne Jones Jnr Chapter 11 focuses on file system implementation, covering local and remote file system structures, allocation methods, free-space management, and recovery processes. It discusses virtual file systems (VFS), various allocation strategies (contiguous, linked, indexed), and the efficiency and performance factors related to these systems. Additionally, it explores the NFS (Network File System) architecture, emphasizing its interoperability across heterogeneous systems and detailing remote file operations.
System call
System callSumant Diwakar System calls provide an interface between processes and the operating system. They allow programs to request services like reading/writing files or communicating over a network. Common system calls include opening/closing files, reading/writing data, process creation/termination, and requesting the current time/date. System calls are grouped into categories like process control, file management, device management, information maintenance, and communications.
Ch02 early system memory management
Ch02 early system memory managementJacob Cadeliña This chapter discusses early memory management techniques including fixed partitions, dynamic partitions, and relocatable dynamic partitions. It describes how these systems allocate and deallocate memory using concepts like first-fit and best-fit allocation, and how they utilize compaction to optimize memory usage. Special registers are used to track memory locations as programs are relocated during compaction.
External memory - Computer Architecture
External memory - Computer ArchitectureBretz Harllynne Moltio Magnetic disks remain the most important component of external memory. Data is recorded on disks through magnetic read and write heads. Disks are organized into tracks and sectors for efficient data access. RAID systems provide data redundancy or higher performance through striping and mirroring across multiple disks. Optical disks like CDs and DVDs store data through microscopic pits and lands read by lasers, and use constant linear velocity to increase storage capacity toward the disk edge.
Memory mapping
Memory mappingSnehalataAgasti Cache memory is located between the processor and main memory. It is smaller and faster than main memory. There are two types of cache memory policies - write-back and write-through. Mapping is a technique that maps CPU-generated memory addresses to cache lines. There are three types of mapping - direct, associative, and set associative. Direct mapping maps each main memory block to a single cache line using the formula: cache line number = main memory block number % number of cache lines. This can cause conflict misses.
12 processor structure and function
12 processor structure and functionSher Shah Merkhel This chapter discusses processor structure and function. It covers the basic components of a CPU including registers, instruction cycles, and data flow. Key points include:
- A CPU must fetch, interpret, fetch operands for, process, and write data from instructions. It uses registers for temporary storage and a program counter to keep track of instructions.
- Common registers include general purpose, data, address, condition code, control/status, and program status registers. General purpose registers can vary in number, size, and whether they are general or specialized use.
- An instruction cycle involves fetching an instruction from memory, decoding it, fetching operands, executing the instruction, and writing results. Pipelining and branch prediction are
File system structure
File system structuresangrampatil81 The document discusses the structure of file systems. It explains that a file system provides mechanisms for storing and accessing files and data. It uses a layered approach, with each layer responsible for specific tasks related to file management. The logical file system contains metadata and verifies permissions and paths. It maps logical file blocks to physical disk blocks using a file organization module, which also manages free space. The basic file system then issues I/O commands to access those physical blocks via device drivers, with I/O controls handling interrupts.
Memory Organization
Memory OrganizationKamal Acharya The document discusses the different types of memory in digital computers, including main memory, associative memory, cache memory, and virtual memory, detailing their organization, functions, and access methods. It explains the memory hierarchy, the role of auxiliary memory, and various mapping techniques for cache memory, such as associative, direct, and set-associative mapping. Additionally, the document covers memory addressing, data storage, and mechanisms like page replacement in virtual memory systems.
Scheduling algorithms
Scheduling algorithmsChankey Pathak The document discusses various scheduling algorithms used in operating systems including:
- First Come First Serve (FCFS) scheduling which services processes in the order of arrival but can lead to long waiting times.
- Shortest Job First (SJF) scheduling which prioritizes the shortest processes first to minimize waiting times. It can be preemptive or non-preemptive.
- Priority scheduling assigns priorities to processes and services the highest priority process first, which can potentially cause starvation of low priority processes.
- Round Robin scheduling allows equal CPU access to all processes by allowing each a small time quantum or slice before preempting to the next process.
Memory Hierarchy
Memory Hierarchychauhankapil The document discusses the memory hierarchy in computers. It describes the different levels of memory from fastest to slowest as register memory, cache memory, main memory (RAM and ROM), and auxiliary memory (magnetic tapes, hard disks, etc.). The main memory directly communicates with the CPU while the auxiliary memory provides backup storage and needs to transfer data to main memory to be accessed by the CPU. A cache memory is also used to increase processing speed.
Interrupt
InterruptSiddique Ibrahim Interrupts allow input/output devices to alert the processor when they are ready. When an interrupt request occurs, the processor saves its context and jumps to an interrupt service routine. It then acknowledges the interrupt and restores its context before returning to the original instruction. Processors have mechanisms for prioritizing interrupts and enabling/disabling them to avoid infinite loops or unintended requests.
Viewers also liked (20)
Memory Management | Computer Science
Memory Management | Computer ScienceTransweb Global Inc The document provides an introduction to memory management in operating systems, detailing its functions like swapping processes between primary memory and disk. It describes logical and physical address spaces, types of memory management, cache memory, and virtual memory. Additionally, it mentions the '0x0000001a' error related to memory malfunctions and offers a link for further information.
Memory management
Memory managementRajni Sirohi The document discusses memory management in operating systems. It covers key concepts like logical versus physical addresses, binding logical addresses to physical addresses, and different approaches to allocating memory like contiguous allocation. It also discusses dynamic storage allocation using a buddy system to merge adjacent free spaces, as well as compaction techniques to reduce external fragmentation by moving free memory blocks together. Memory management aims to efficiently share physical memory between processes using mechanisms like partitioning memory and enforcing protection boundaries.
Memory management
Memory managementVishal Singh The document discusses memory management techniques used in operating systems. It describes logical vs physical addresses and how relocation registers map logical addresses to physical addresses. It covers contiguous and non-contiguous storage allocation, including paging and segmentation. Paging divides memory into fixed-size frames and pages, using a page table and translation lookaside buffer (TLB) for address translation. Segmentation divides memory into variable-sized segments based on a program's logical structure. Virtual memory and demand paging are also covered, along with page replacement algorithms like FIFO, LRU and optimal replacement.
Storage management
Storage managementAtul Sharma This document discusses different approaches to memory management in computer systems. It explains that memory plays a central role, with the CPU and I/O system interacting with memory. It then describes four approaches to memory allocation and management: contiguous storage allocation, non-contiguous storage allocation, virtual storage using paging, and virtual storage using segmentation. Paging divides memory into fixed-size frames and logical memory into same-sized pages, using a page table to map logical to physical addresses. Segmentation divides a program into variable-sized segments and uses a segment table to map two-dimensional physical addresses. The most efficient approach sometimes combines paging and segmentation.
Design and development of autotransformer motor starter for induced draft fan...
Design and development of autotransformer motor starter for induced draft fan...Alexander Decker This document summarizes a study on designing and developing an autotransformer motor starter prototype for an induced draft fan (IDF) at Batangas Sugar Central Inc. (BSCI). The existing wye-delta starting method was found to cause high inrush currents of over 5 times the rated current during switching, tripping safety devices and causing operational issues. The study aims to evaluate alternative starting methods, consider electrical code design requirements, design and fabricate an autotransformer prototype, and test its performance in terms of starting voltage, current and torque. Computed prototype parameter values closely matched measured values, demonstrating it can reliably start the IDF motor while avoiding high transient currents of the existing method.
Virtual memory
Virtual memoryIshwar Dhumal Virtual memory is a technique that allows processes to execute as if they have more memory than is physically installed. It works by swapping pages of memory between RAM and disk as needed. With demand paging, only pages actively being used are loaded into memory, avoiding loading unnecessary pages. This allows programs to be larger than physical memory and improves efficiency by not loading parts that may never be used.
Pentium
PentiumAkshay Nagpurkar The document provides an overview of the evolution of Intel processors from early 16-bit processors like the 8086 and 8088 through to the Pentium processor. It describes the key features and architectural changes introduced at each generation, including protected mode and segmentation in the 286, 32-bit registers and virtual memory support in the 386, pipelining and caching in the 486, and superscalar processing and branch prediction in the Pentium.
Vm
VmAparna Bhadran This document discusses virtual memory and how it works. Virtual memory allows multiple processors to each have their own virtual address space even if there is not enough physical memory for each processor to have a full address space allocated. It does this by dividing physical memory into blocks that are allocated to different processors. A protection scheme restricts each process to only accessing blocks belonging to that process. Virtual memory reduces the time needed to start programs by not requiring all code and data to be loaded into physical memory. Memory is mapped so that virtual addresses are translated to physical addresses to access main memory.
Virtual memory
Virtual memoryaaina_katyal Virtual memory is a technique that allows a computer to use parts of the hard disk as if they were memory. This allows processes to have more memory than the physical RAM alone. When physical memory is full, pages are written to disk. Page replacement algorithms like FIFO, LRU, and OPT determine which pages to remove from RAM and write to disk when new pages are needed. Virtual memory improves performance by allowing swapping of infrequently used pages to disk.
computer memory ,., .
computer memory ,., .santokh00700 This document provides an overview of different storage types and devices in computer systems, including hard drives, floppy disks, and optical storage like CD/DVD. It categorizes storage by their operations, access methods, technologies, and hierarchies, explaining concepts such as online, near-online, and offline storage. Additionally, it discusses the performance metrics of storage devices, including capacity and access times.
8259 Programmable Interrupt Controller by vijay
8259 Programmable Interrupt Controller by vijayVijay Kumar The 8259A Programmable Interrupt Controller (PIC) is used to simplify the interrupt interface of 8088/8086 microprocessor systems. It can accept up to 8 interrupt requests and expand to 64 requests by cascading additional PICs. The PIC is programmable through initialization command words to configure operating modes and interrupt vector assignments. It also has operation command words to control interrupt masking, priorities, and acknowledgement.
COMPUTER MEMORY
COMPUTER MEMORYElisha Kharel The document provides an overview of various types of computer memory, including RAM, ROM, and cache memory, and explains their functions. RAM, both dynamic and static, is highlighted for its importance in running programs quickly but is limited by its volatile nature. Cache memory is described as a fast storage area that improves data retrieval speeds, with registers further enhancing CPU operations by holding frequently used values.
Operating System (Scheduling, Input and Output Management, Memory Management,...
Operating System (Scheduling, Input and Output Management, Memory Management,...Project Student The document provides an overview of operating systems, which are essential software for managing computer operations and acting as an interface between users and hardware. It details tasks performed by the OS, including scheduling, memory management, and file management, highlighting the roles of virtual memory and device drivers. The text also discusses how the OS optimizes performance and manages input/output devices while ensuring efficient resource allocation.
Computer Memory
Computer Memorysumeshkumarsheoran The document discusses computer memory, detailing its types, including primary (volatile) and secondary (non-volatile) memory. It further explains RAM and ROM, highlighting their differences, types, and characteristics, such as static RAM (SRAM) and dynamic RAM (DRAM). Additionally, it covers cache memory's role in enhancing CPU performance by acting as a buffer for frequently accessed data.
VIRTUAL MEMORY
VIRTUAL MEMORYKamran Ashraf Virtual memory allows programs to execute without requiring their entire address space to be resident in physical memory. It uses virtual addresses that are translated to physical addresses by the hardware. This translation occurs via page tables managed by the operating system. When a virtual address is accessed, its virtual page number is used as an index into the page table to obtain the corresponding physical page frame number. If the page is not in memory, a page fault occurs and the OS handles loading it from disk. Paging partitions both physical and virtual memory into fixed-sized pages to address fragmentation issues. Segmentation further partitions the virtual address space into logical segments. Hardware support for segmentation involves a segment table containing base/limit pairs for each segment. Translation lookaside buffers
three phase induction machine starter
three phase induction machine starterAditya More This document discusses different types of starters for 3-phase induction motors, including their operation and advantages/disadvantages. It describes stator resistance, auto-transformer, star-delta, rotor resistance, and direct online starters. The star-delta starter connects the motor in a star configuration at start to reduce voltage and current by 1/3, then switches to delta for run. The direct online starter connects the motor directly to full voltage, providing maximum torque but also maximum starting current of 6-8 times full load current. Variable frequency drives control motor speed by varying supply frequency and voltage.
Chapter 9 - Virtual Memory
Chapter 9 - Virtual MemoryWayne Jones Jnr Chapter 9 discusses virtual memory, detailing its benefits such as separating logical and physical memory, and methods including demand paging and page replacement algorithms. It explains concepts like copy-on-write and thrashing, and various algorithms for managing memory efficiently, including FIFO and LRU. Additionally, it touches on kernel memory allocation, memory-mapped files, and real-world operating system implementations like Windows XP and Solaris.
Operating Systems: Virtual Memory
Operating Systems: Virtual MemoryDamian T. Gordon The document discusses how modern operating systems use paging to manage memory. Programs are divided into chunks called pages which are loaded into frames of main memory as needed. This allows more programs to reside partially in memory than would fit entirely, through demand paging which loads only currently used parts of a program. This creates the illusion of larger memory usage via virtual memory.
Motor starter
Motor starterBHAGWAN PRASAD This document discusses different types of motor starters used for AC and DC motors. It describes the necessity of starters to limit inrush current and protect motors. The main types covered are DOL, star-delta, and autotransformer starters. It provides information on their wiring diagrams, motor starting characteristics, advantages and disadvantages, suitable motor sizes and applications. Current ratings for motors used with different starters are also included.
Virtual memory
Virtual memoryAnuj Modi The document discusses the concept of virtual memory. Virtual memory allows a program to access more memory than what is physically available in RAM by storing unused portions of the program on disk. When a program requests data that is not currently in RAM, it triggers a page fault that causes the needed page to be swapped from disk into RAM. This allows the illusion of more memory than physically available through swapping pages between RAM and disk as needed by the program during execution.
Ad
Similar to Computer memory management (20)
chap.4.memory.manag.ppt
chap.4.memory.manag.pptamadayshwan The document covers various aspects of memory management, including basic memory management techniques, swapping, virtual memory, and page replacement algorithms. It explains how memory hierarchies function, discusses multiple page replacement strategies, and highlights the importance of design and implementation issues. Additionally, it touches upon segmentation and the integration of paging systems within operating systems.
4 (1)
4 (1)Mothi R This document discusses memory management techniques including paging, segmentation, and page replacement algorithms. It begins with an overview of memory hierarchy and basic memory management. It then covers topics such as swapping, virtual memory, page tables, TLBs, page replacement algorithms like FIFO, LRU and clock, and design issues for paging systems including page size and locality. The document also discusses segmentation, its implementation, and examples like MULTICS and the Pentium that use both paging and segmentation.
Chapter 04
Chapter 04 Google This document discusses various memory management techniques including basic memory management, swapping, virtual memory, page replacement algorithms, segmentation, and the implementation of paging systems. It covers topics such as fixed and variable memory partitioning, page tables, segmentation, page replacement algorithms like FIFO, LRU and working set, and the role of the operating system in memory management.
Memory Management
Memory ManagementRamasubbu .P The document discusses various techniques for memory management including basic memory management without swapping or paging, multiprogramming with fixed partitions, swapping, paging, segmentation, page replacement algorithms like FIFO, LRU, and working set, and design issues for paging systems like page size, separate instruction and data spaces, and implementation issues like page fault handling.
Memory Management-Muhammad Ahmad.ppt
Memory Management-Muhammad Ahmad.pptAliyanAbbas1 The document discusses memory management techniques used in operating systems. It covers basic memory management, swapping, virtual memory, page replacement algorithms like FIFO, LRU and clock algorithms. It also discusses segmentation, paging, page tables, virtual memory, page replacement policies and implementation issues in memory management. The document provides an overview of key concepts in memory management with examples.
Memory management
Memory managementRasi123 Memory management handles allocating and deallocating memory for processes. It tracks which parts of memory are in use and frees memory when processes are done. It may use swapping between main memory and disk when disk storage is too small. Memory is organized in a hierarchy from fast expensive cache to slower cheaper disk storage. The memory management unit handles this hierarchy. Basic techniques include fixed partitions and relocation and protection using base and limit registers. More advanced techniques include swapping, bitmaps, linked lists, paging and segmentation. Paging and segmentation allow non-contiguous virtual address spaces. Page replacement algorithms select pages to remove to make space for new pages.
Virtual Memory Management
Virtual Memory ManagementRahul Jamwal The document discusses virtual memory management. It describes key concepts like virtual memory, virtual address spaces, demand paging, and page replacement. Virtual memory allows processes to have a logical address space that is larger than physical memory by mapping portions of virtual memory to physical memory frames as needed. When a process accesses a page not in memory, a page fault occurs which is resolved through demand paging by loading the missing page from secondary storage. If no physical frame is available during a page fault, an existing page must be replaced using an algorithm like least recently used.
Os unit 2
Os unit 2Arnav Chowdhury This document discusses memory management techniques in operating systems including paging, segmentation, and virtual memory. It defines key concepts such as logical versus physical addresses, page tables, frames, and how memory management units map between these spaces. Advantages and disadvantages of different algorithms like FIFO, LRU and clock are presented. The goals of memory management are to allow for more efficient use of limited memory and enable running multiple processes simultaneously.
ikh311-06
ikh311-06Anung Ariwibowo The document discusses various techniques for managing memory in an operating system. It covers memory hierarchies, motivations for memory management, basic approaches like fixed partitions and multiprogramming, and more advanced techniques like relocation, protection, swapping, paging using page tables and translation look-up buffers, and page replacement algorithms like FIFO, LRU, and working set. It also discusses design issues like local vs global allocation policies, page size selection, instruction/data separation, shared pages, and cleaning policies.
Virtual memory Chapter 9 simple and easy
Virtual memory Chapter 9 simple and easy1415lv54 The document provides an overview of virtual memory, including its definition, implementation through demand paging and segmentation, and how it allows for more efficient process management by enabling processes to occupy non-contiguous memory. It discusses key components like page tables, the translation lookaside buffer (TLB), and page replacement algorithms, emphasizing the necessity of efficient management to prevent issues such as thrashing. Additionally, it covers various memory allocation strategies and the impact of page size on performance and page faults.
08 virtual memory
08 virtual memoryKamal Singh Virtual memory allows processes to be larger than physical memory by storing portions of processes that don't fit in RAM on disk. When a process attempts to access memory not currently in RAM, a page fault occurs, swapping the needed page in from disk while another process runs. Hardware and software mechanisms like page tables, TLBs, and replacement algorithms efficiently manage mapping virtual addresses to physical locations and swapping pages between disk and RAM. This improves system utilization by allowing many processes to reside partially in memory simultaneously.
memory allocation techniques in operating systems
memory allocation techniques in operating systemsVivekananda Gn The document discusses the concepts of virtual memory and memory management in operating systems, specifically focusing on page replacement algorithms and their performance implications. It explains how virtual memory allows logical address spaces to exceed physical memory limits, and details various page replacement strategies like FIFO, LRU, and enhancements such as second-chance and working set models. Additionally, it touches on issues like thrashing, prepaging, and the performance of demand paging across different operating systems.
CH09.pdf
CH09.pdfImranKhan880955 Virtual memory allows a process to have a logical address space that is larger than physical memory by paging portions of memory to disk as needed. When a process accesses a page that is not in memory, a page fault occurs which brings the needed page into memory from disk. If no free frames are available, a page replacement algorithm must select a page to remove from memory and write to disk to make space for the new page. Common page replacement algorithms aim to minimize page faults by selecting pages that are least recently used.
Distributed Operating System_3
Distributed Operating System_3Dr Sandeep Kumar Poonia The document discusses distributed operating systems, focusing on virtual memory concepts such as demand paging, page replacement, and process creation benefits. It elaborates on mechanisms like copy-on-write and memory-mapped file I/O, as well as various page replacement algorithms aimed at optimizing performance and managing memory allocation effectively. Additionally, it highlights issues like thrashing and provides insights into operating system implementations like Windows NT and Solaris 2 that utilize these concepts.
Virtual Memory.pdf
Virtual Memory.pdfSujanTimalsina5 Virtual memory allows processes to have a logical address space that is larger than physical memory by paging portions of processes into and out of RAM as needed. When a process attempts to access a memory page that is not currently in RAM, a page fault occurs which brings the required page into memory from disk. Page replacement algorithms like FIFO and LRU are used to determine which page to remove from RAM to make room for the new page. If page faults occur too frequently due to insufficient free memory, it can cause thrashing which degrades system performance.
OS_Ch10
OS_Ch10Supriya Shrivastava Virtual memory allows processes to access memory addresses that exceed the amount of physical memory available. When a process references a memory page that is not in RAM, a page fault occurs which brings the missing page into memory from disk. Page replacement algorithms are used to determine which page to remove from RAM to make room for the new page. Factors like page fault rate, locality of reference, and thrashing are important considerations for virtual memory performance.
Ch10 OS
Ch10 OSC.U Virtual memory allows processes to have a logical address space larger than physical memory by paging portions of memory to disk as needed. When a process accesses a page not in memory, a page fault occurs which the operating system handles by finding a free frame, loading the needed page, and updating data structures. Page replacement algorithms aim to select pages least likely to be used soon when a free frame is unavailable. Thrashing can occur if working set sizes exceed available memory, continuously triggering page faults.
OSCh10
OSCh10Joe Christensen Virtual memory allows processes to access memory addresses that exceed the amount of physical memory available. When a process references a memory page that is not in RAM, a page fault occurs which brings the missing page into memory from disk. Page replacement algorithms are used to determine which page to remove from RAM to make room for the faulting page. The working set model aims to keep the active pages used by each process in memory to reduce thrashing, which occurs when the total memory demand exceeds the available RAM.
Demand paging
Demand pagingTrinity Dwarka The document discusses virtual memory systems, focusing on concepts like demand paging, page replacement, and allocation of page frames to optimize memory usage. It explains various algorithms for page replacement, such as FIFO, LRU, and their performance implications, as well as frame allocation strategies. Additionally, it highlights the issue of thrashing when there are inadequate pages and introduces the working-set model to manage page faults effectively.
Paging +Algorithem+Segmentation+memory management
Paging +Algorithem+Segmentation+memory managementkazim Hussain The document discusses memory management techniques used in computer systems, including memory partitioning, paging, segmentation, and virtual memory. It provides details on:
1) How memory is divided between the operating system and currently running program.
2) The use of fixed and variable size partitions and their tradeoffs.
3) How paging divides programs and memory into pages to more efficiently allocate memory.
4) How segmentation further subdivides memory to simplify programming and enable access controls.
5) How virtual memory uses paging, disk storage, and demand paging to make programs appear larger than physical memory.
Ad
More from Kumar (20)
Graphics devices
Graphics devicesKumar This document discusses graphics hardware components. It describes various graphics input devices like the mouse, joystick, light pen etc. and how they are either analog or digital. It then covers common graphics output devices such as CRT displays, plasma displays, LCDs and 3D viewing systems. It provides details on the internal components and working of CRT displays. It also discusses graphics storage formats and the architecture of raster and random graphics systems.
Fill area algorithms
Fill area algorithmsKumar The document describes different algorithms for filling polygon and area shapes, including scanline fill, boundary fill, and flood fill algorithms. The scanline fill algorithm works by determining intersections of boundaries with scanlines and filling color between intersections. Boundary fill works by starting from an interior point and recursively "painting" neighboring points until the boundary is reached. Flood fill replaces a specified interior color. Both can be 4-connected or 8-connected. The document also discusses problems that can occur and more efficient span-based approaches.
region-filling
region-fillingKumar This document discusses techniques for filling 2D shapes and regions in raster graphics. It covers seed fill algorithms that start with an interior seed point and grow outward, filling neighboring pixels. Boundary fill and flood fill are described as variations. The document also discusses raster-based filling that processes shapes one scanline at a time. Methods for filling polygons are presented, including using the even-odd rule or winding number rule to determine if a point is inside the polygon boundary.
Bresenham derivation
Bresenham derivationKumar The document derives Bresenham's line algorithm for drawing lines on a discrete grid. It starts with the line equation and defines variables for the slope and intercept. It then calculates the distance d1 and d2 from the line to two possible pixel locations and expresses their difference in terms of the slope and intercept. By multiplying this difference by the change in x, it removes the floating point slope value, resulting in an integer comparison expression. This is defined recursively to draw each subsequent pixel, using pre-computed constants. The initial p0 value is also derived from the line endpoint coordinates.
Bresenham circles and polygons derication
Bresenham circles and polygons dericationKumar The document discusses algorithms for drawing lines and circles on a discrete pixel display. It begins by describing what characteristics an "ideal line" would have on such a display. It then introduces several algorithms for drawing lines, including the simple line algorithm, digital differential analyzer (DDA) algorithm, and Bresenham's line algorithm. The Bresenham algorithm is described in detail, as it uses only integer calculations. Next, a simple potential circle drawing algorithm is presented and its shortcomings discussed. Finally, the more accurate and efficient mid-point circle algorithm is described. This algorithm exploits the eight-way symmetry of circles and uses incremental calculations to determine the next pixel point.
Introductionto xslt
Introductionto xsltKumar The document provides an introduction to XSLT (Extensible Stylesheet Language Transformations), including:
1) It discusses XSLT basics like using templates to extract values from XML and output them, using for-each loops to process multiple elements, and if/choose for decisions.
2) It covers XPath for addressing parts of an XML document, and functions like contains() and position().
3) The document gives examples of transforming sample XML data using XSLT templates, value-of, and apply-templates.
Extracting data from xml
Extracting data from xmlKumar XML documents can be represented and stored in memory as tree structures using models like DOM and XDM. XPath is an expression language used to navigate and select parts of an XML tree. It allows traversing elements and their attributes, filtering nodes by properties or position, and evaluating paths relative to a context node. While XPath expressions cannot modify the document, they are commonly used with languages like XSLT and XQuery which can transform or extract data from XML trees.
Xml basics
Xml basicsKumar This document provides an overview of XML programming and XML documents. It discusses the physical and logical views of an XML document, document structure including the root element, and how XML documents are commonly stored as text files. It also summarizes how an XML parser reads and validates an XML document by checking its syntax and structure. The document then covers various XML components in more detail, such as elements, attributes, character encoding, entities, processing instructions, well-formedness, validation via DTDs, and document modeling.
XML Schema
XML SchemaKumar XML Schema provides a way to formally define and validate the structure and content of XML documents. It allows defining elements, attributes, and data types, as well as restrictions like length, pattern, and value ranges. DTD is more limited and cannot validate data types. XML Schema is written in XML syntax, uses XML namespaces, and provides stronger typing capabilities compared to DTD. It allows defining simple and complex element types, attributes, and restrictions to precisely describe the expected structure and values within XML documents.
Publishing xml
Publishing xmlKumar This document discusses style sheet languages like CSS that are used to control the presentation of XML documents. CSS allows one to specify things like fonts, colors, spacing etc. for different elements in an XML file. A single XML file can then be formatted in multiple ways just by changing the associated CSS stylesheet without modifying the XML content. The document provides examples of using CSS selectors, rules and properties to style elements in an XML file and controlling presentation aspects like layout of elements on a page. It also discusses how to link the CSS stylesheet to an XML file using processing instructions.
DTD
DTDKumar An attribute declaration specifies attributes for elements in a DTD. It defines the attribute name, data type or permissible values, and required behavior. For example, an attribute may have a default value if not provided, be optional, or require a value. Notations can label non-XML data types and unparsed entities can import binary files. Together DTDs and entities provide a schema to describe document structure and relationships.
Applying xml
Applying xmlKumar This document discusses XML web services and their components. It defines XML web services as software services exposed on the web through the SOAP protocol and described with WSDL and registered in UDDI. It describes how SOAP is used for communication, WSDL describes service interfaces, and UDDI allows for service discovery. Examples of web services are provided. The architecture of web services is shown involving clients, services, and standards. Finally, it discusses how XML data can be transformed to HTML for display in web pages using XSLT transformation rules.
Introduction to XML
Introduction to XMLKumar This document provides an introduction and overview of XML. It explains that XML stands for Extensible Markup Language and is used for data transportation and storage in a platform and language neutral way. XML plays an important role in data exchange on the web. The document discusses the history of XML and how it was developed as an improvement over SGML and HTML by allowing users to define their own tags to structure data for storage and interchange. It also provides details on the pros and cons of XML compared to other markup languages.
How to deploy a j2ee application
How to deploy a j2ee applicationKumar This document provides instructions for packaging and deploying a J2EE application that was developed in IBM Rational Application Developer. It describes resetting the database to its original state, exporting the application as an EAR file, using the WebSphere administrative console to install the EAR file on the application server, and testing the application in a web browser. The goal is to simulate taking an application developed in a development environment and deploying it to a production server.
JNDI, JMS, JPA, XML
JNDI, JMS, JPA, XMLKumar This document provides an overview of key Java enterprise technologies including JNDI, JMS, JPA and XML. It discusses the architecture and usage of JNDI for accessing naming and directory services. It also covers the point-to-point and publish/subscribe messaging models of JMS, the core JMS programming elements like connection factories, connections and destinations, and how applications use these elements to send and receive messages. Finally, it briefly introduces JPA for object-relational mapping and the role of XML.
EJB Fundmentals
EJB FundmentalsKumar The document discusses the benefits of using Enterprise JavaBeans (EJBs) for developing Java EE applications. It explains that EJBs provide infrastructure for developing and deploying mission-critical, enterprise applications by handling common tasks like database connectivity and transaction management. The three types of EJBs - session, entity, and message-driven beans - are described as well as how they are contained in EJB containers.
JSP and struts programming
JSP and struts programmingKumar This document provides an overview of JSP and Struts programming. It discusses the advantages of JSP over servlets, the JSP lifecycle, and basic JSP elements like scriptlets, expressions, directives. It also covers creating simple JSP pages, the JSP API, and using scripting elements to include Java code in JSP pages.
java servlet and servlet programming
java servlet and servlet programmingKumar This document provides lecture notes on servlet programming. It covers topics like the introduction to servlets, GET and POST methods, the lifecycle of a servlet, servlet interfaces like Servlet, GenericServlet and HttpServlet. It also discusses request dispatching in servlets, session management techniques and servlet filters. Code examples are provided to demonstrate servlet implementation and request dispatching.
Introduction to JDBC and JDBC Drivers
Introduction to JDBC and JDBC DriversKumar The document discusses Java Database Connectivity (JDBC) and provides details about its core components and usage. It covers:
1) The four core components of JDBC - drivers, connections, statements, and result sets.
2) The four types of JDBC drivers and examples of each.
3) How to use JDBC to connect to a database, execute queries using statements, iterate through result sets, and update data. Prepared statements are also discussed.
Introduction to J2EE
Introduction to J2EEKumar The document is a set of lecture notes on Enterprise Java from January to June 2014 prepared by Mr. Hitesh Kumar Sharma and Mr. Ravi Tomar. It covers core J2EE technologies, enterprise application architectures like 2-tier, 3-tier and n-tier, advantages and disadvantages of architectures, J2EE application servers, web containers and EJB containers. The notes are to be submitted by B.Tech CS VI semester students specializing in MFT, O&G, OSS and CCVT.
Recently uploaded (20)
AI VIDEO MAGAZINE - June 2025 - r/aivideo
AI VIDEO MAGAZINE - June 2025 - r/aivideo1pcity Studios, Inc AI VIDEO MAGAZINE - r/aivideo community newsletter – Exclusive Tutorials: How to make an AI VIDEO from scratch, PLUS: How to make AI MUSIC, Hottest ai videos of 2025, Exclusive Interviews, New Tools, Previews, and MORE - JUNE 2025 ISSUE -
10 Key Challenges for AI within the EU Data Protection Framework.pdf
10 Key Challenges for AI within the EU Data Protection Framework.pdfPriyanka Aash 10 Key Challenges for AI within the EU Data Protection Framework
“MPU+: A Transformative Solution for Next-Gen AI at the Edge,” a Presentation...
“MPU+: A Transformative Solution for Next-Gen AI at the Edge,” a Presentation...Edge AI and Vision Alliance For the full video of this presentation, please visit: https://www.edge-ai-vision.com/2025/06/mpu-a-transformative-solution-for-next-gen-ai-at-the-edge-a-presentation-from-fotonation/
Petronel Bigioi, CEO of FotoNation, presents the “MPU+: A Transformative Solution for Next-Gen AI at the Edge” tutorial at the May 2025 Embedded Vision Summit.
In this talk, Bigioi introduces MPU+, a novel programmable, customizable low-power platform for real-time, localized intelligence at the edge. The platform includes an AI-augmented image signal processor that enables leading image and video quality.
In addition, it integrates ultra-low-power object and motion detection capabilities to enable always-on computer vision. A programmable neural processor provides flexibility to efficiently implement new neural networks. And additional specialized engines facilitate image stabilization and audio enhancements.
Techniques for Automatic Device Identification and Network Assignment.pdf
Techniques for Automatic Device Identification and Network Assignment.pdfPriyanka Aash Techniques for Automatic Device Identification and Network Assignment
UserCon Belgium: Honey, VMware increased my bill
UserCon Belgium: Honey, VMware increased my billstijn40 VMware’s pricing changes have forced organizations to rethink their datacenter cost management strategies. While FinOps is commonly associated with cloud environments, the FinOps Foundation has recently expanded its framework to include Scopes—and Datacenter is now officially part of the equation. In this session, we’ll map the FinOps Framework to a VMware-based datacenter, focusing on cost visibility, optimization, and automation. You’ll learn how to track costs more effectively, rightsize workloads, optimize licensing, and drive efficiency—all without migrating to the cloud. We’ll also explore how to align IT teams, finance, and leadership around cost-aware decision-making for on-prem environments. If your VMware bill keeps increasing and you need a new approach to cost management, this session is for you!
"Scaling in space and time with Temporal", Andriy Lupa.pdf
"Scaling in space and time with Temporal", Andriy Lupa.pdfFwdays Design patterns like Event Sourcing and Event Streaming have long become standards for building real-time analytics systems. However, when the system load becomes nonlinear with fast and often unpredictable spikes, it's crucial to respond quickly in order not to lose real-time operating itself.
In this talk, I’ll share my experience implementing and using a tool like Temporal.io. We'll explore the evolution of our system for maintaining real-time report generation and discuss how we use Temporal both for short-lived pipelines and long-running background tasks.
Using the SQLExecutor for Data Quality Management: aka One man's love for the...
Using the SQLExecutor for Data Quality Management: aka One man's love for the...Safe Software The SQLExecutor is one of FME’s most powerful and flexible transformers. Pivvot maintains a robust internal metadata hierarchy used to support ingestion and curation of thousands of external data sources that must be managed for quality before entering our platform. By using the SQLExecutor, Pivvot can efficiently detect problems and perform analysis before data is extracted from our staging environment, removing the need for rollbacks or cycles waisted on a failed job. This presentation will walk through three distinct examples of how Pivvot uses the SQLExecutor to engage its metadata hierarchy and integrate with its Data Quality Management workflows efficiently and within the source postgres database. Spatial Validation –Validating spatial prerequisites before entering a production environment. Reference Data Validation - Dynamically validate domain-ed columns across any table and multiple columns per table. Practical De-duplication - Removing identical or near-identical well point locations from two distinct source datasets in the same table.
Quantum AI Discoveries: Fractal Patterns Consciousness and Cyclical Universes
Quantum AI Discoveries: Fractal Patterns Consciousness and Cyclical UniversesSaikat Basu Embark on a cosmic journey exploring the intersection of quantum
computing, consciousness, and ancient wisdom. Together we'll uncover the
recursive patterns that bind our reality.
Lessons Learned from Developing Secure AI Workflows.pdf
Lessons Learned from Developing Secure AI Workflows.pdfPriyanka Aash Lessons Learned from Developing Secure AI Workflows
Quantum AI: Where Impossible Becomes Probable
Quantum AI: Where Impossible Becomes ProbableSaikat Basu Imagine combining the "brains" of Artificial Intelligence (AI) with the "super muscles" of Quantum Computing. That's Quantum AI!
It's a new field that uses the mind-bending rules of quantum physics to make AI even more powerful.
From Manual to Auto Searching- FME in the Driver's Seat
From Manual to Auto Searching- FME in the Driver's SeatSafe Software Finding a specific car online can be a time-consuming task, especially when checking multiple dealer websites. A few years ago, I faced this exact problem while searching for a particular vehicle in New Zealand. The local classified platform, Trade Me (similar to eBay), wasn’t yielding any results, so I expanded my search to second-hand dealer sites—only to realise that periodically checking each one was going to be tedious. That’s when I noticed something interesting: many of these websites used the same platform to manage their inventories. Recognising this, I reverse-engineered the platform’s structure and built an FME workspace that automated the search process for me. By integrating API calls and setting up periodic checks, I received real-time email alerts when matching cars were listed. In this presentation, I’ll walk through how I used FME to save hours of manual searching by creating a custom car-finding automation system. While FME can’t buy a car for you—yet—it can certainly help you find the one you’re after!
Salesforce Summer '25 Release Frenchgathering.pptx.pdf
Salesforce Summer '25 Release Frenchgathering.pptx.pdfyosra Saidani Salesforce Summer '25 Release Frenchgathering.pptx.pdf
9-1-1 Addressing: End-to-End Automation Using FME
9-1-1 Addressing: End-to-End Automation Using FMESafe Software This session will cover a common use case for local and state/provincial governments who create and/or maintain their 9-1-1 addressing data, particularly address points and road centerlines. In this session, you'll learn how FME has helped Shelby County 9-1-1 (TN) automate the 9-1-1 addressing process; including automatically assigning attributes from disparate sources, on-the-fly QAQC of said data, and reporting. The FME logic that this presentation will cover includes: Table joins using attributes and geometry, Looping in custom transformers, Working with lists and Change detection.
Security Tips for Enterprise Azure Solutions
Security Tips for Enterprise Azure SolutionsMichele Leroux Bustamante Delivering solutions to Azure may involve a variety of architecture patterns involving your applications, APIs data and associated Azure resources that comprise the solution. This session will use reference architectures to illustrate the security considerations to protect your Azure resources and data, how to achieve Zero Trust, and why it matters. Topics covered will include specific security recommendations for types Azure resources and related network security practices. The goal is to give you a breadth of understanding as to typical security requirements to meet compliance and security controls in an enterprise solution.
Raman Bhaumik - Passionate Tech Enthusiast
Raman Bhaumik - Passionate Tech EnthusiastRaman Bhaumik A Junior Software Developer with a flair for innovation, Raman Bhaumik excels in delivering scalable web solutions. With three years of experience and a solid foundation in Java, Python, JavaScript, and SQL, she has streamlined task tracking by 20% and improved application stability.
Connecting Data and Intelligence: The Role of FME in Machine Learning
Connecting Data and Intelligence: The Role of FME in Machine LearningSafe Software In this presentation, we want to explore powerful data integration and preparation for Machine Learning. FME is known for its ability to manipulate and transform geospatial data, connecting diverse data sources into efficient and automated workflows. By integrating FME with Machine Learning techniques, it is possible to transform raw data into valuable insights faster and more accurately, enabling intelligent analysis and data-driven decision making.
A Constitutional Quagmire - Ethical Minefields of AI, Cyber, and Privacy.pdf
A Constitutional Quagmire - Ethical Minefields of AI, Cyber, and Privacy.pdfPriyanka Aash A Constitutional Quagmire - Ethical Minefields of AI, Cyber, and Privacy
Wenn alles versagt - IBM Tape schützt, was zählt! Und besonders mit dem neust...
Wenn alles versagt - IBM Tape schützt, was zählt! Und besonders mit dem neust...Josef Weingand IBM LTO10
“MPU+: A Transformative Solution for Next-Gen AI at the Edge,” a Presentation...
“MPU+: A Transformative Solution for Next-Gen AI at the Edge,” a Presentation...Edge AI and Vision Alliance
Computer memory management
- 1. 1 Memory Management Chapter 4 4.1 Basic memory management 4.2 Swapping 4.3 Virtual memory 4.4 Page replacement algorithms 4.5 Modeling page replacement algorithms 4.6 Design issues for paging systems 4.7 Implementation issues 4.8 Segmentation
- 2. 2 Memory Management • Ideally programmers want memory that is – large – fast – non volatile • Memory hierarchy – small amount of fast, expensive memory – cache – some medium-speed, medium price main memory – gigabytes of slow, cheap disk storage • Memory manager handles the memory hierarchy
- 3. 3 Basic Memory Management Monoprogramming without Swapping or Paging Three simple ways of organizing memory - an operating system with one user process
- 4. 4 Multiprogramming with Fixed Partitions • Fixed memory partitions – separate input queues for each partition – single input queue
- 5. 5 Modeling Multiprogramming CPU utilization as a function of number of processes in memory Degree of multiprogramming
- 6. 6 Analysis of Multiprogramming System Performance • Arrival and work requirements of 4 jobs • CPU utilization for 1 – 4 jobs with 80% I/O wait • Sequence of events as jobs arrive and finish – note numbers show amout of CPU time jobs get in each interval
- 7. 7 Relocation and Protection • Cannot be sure where program will be loaded in memory – address locations of variables, code routines cannot be absolute – must keep a program out of other processes’ partitions • Use base and limit values – address locations added to base value to map to physical addr – address locations larger than limit value is an error
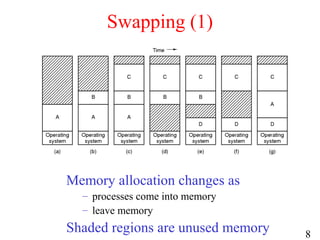
- 8. 8 Swapping (1) Memory allocation changes as – processes come into memory – leave memory Shaded regions are unused memory
- 9. 9 Swapping (2) • Allocating space for growing data segment • Allocating space for growing stack & data segment
- 10. 10 Memory Management with Bit Maps • Part of memory with 5 processes, 3 holes – tick marks show allocation units – shaded regions are free • Corresponding bit map • Same information as a list
- 11. 11 Memory Management with Linked Lists Four neighbor combinations for the terminating process X
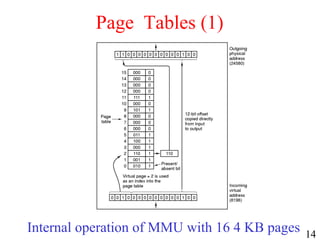
- 12. 12 Virtual Memory Paging (1) The position and function of the MMU
- 13. 13 Paging (2) The relation between virtual addresses and physical memory addres- ses given by page table
- 14. 14 Page Tables (1) Internal operation of MMU with 16 4 KB pages
- 15. 15 Page Tables (2) • 32 bit address with 2 page table fields • Two-level page tables Second-level page tables Top-level page table
- 16. 16 Page Tables (3) Typical page table entry
- 17. 17 TLBs – Translation Lookaside Buffers A TLB to speed up paging
- 18. 18 Inverted Page Tables Comparison of a traditional page table with an inverted page table
- 19. 19 Page Replacement Algorithms • Page fault forces choice – which page must be removed – make room for incoming page • Modified page must first be saved – unmodified just overwritten • Better not to choose an often used page – will probably need to be brought back in soon
- 20. 20 Optimal Page Replacement Algorithm • Replace page needed at the farthest point in future – Optimal but unrealizable • Estimate by … – logging page use on previous runs of process – although this is impractical
- 21. 21 Not Recently Used Page Replacement Algorithm • Each page has Reference bit, Modified bit – bits are set when page is referenced, modified • Pages are classified 1. not referenced, not modified 2. not referenced, modified 3. referenced, not modified 4. referenced, modified • NRU removes page at random – from lowest numbered non empty class
- 22. 22 FIFO Page Replacement Algorithm • Maintain a linked list of all pages – in order they came into memory • Page at beginning of list replaced • Disadvantage – page in memory the longest may be often used
- 23. 23 Second Chance Page Replacement Algorithm • Operation of a second chance – pages sorted in FIFO order – Page list if fault occurs at time 20, A has R bit set (numbers above pages are loading times)
- 24. 24 The Clock Page Replacement Algorithm
- 25. 25 Least Recently Used (LRU) • Assume pages used recently will used again soon – throw out page that has been unused for longest time • Must keep a linked list of pages – most recently used at front, least at rear – update this list every memory reference !! • Alternatively keep counter in each page table entry – choose page with lowest value counter – periodically zero the counter
- 26. 26 Simulating LRU in Software (1) LRU using a matrix – pages referenced in order 0,1,2,3,2,1,0,3,2,3
- 27. 27 Simulating LRU in Software (2) • The aging algorithm simulates LRU in software • Note 6 pages for 5 clock ticks, (a) – (e)
- 28. 28 The Working Set Page Replacement Algorithm (1) • The working set is the set of pages used by the k most recent memory references • w(k,t) is the size of the working set at time, t
- 29. 29 The Working Set Page Replacement Algorithm (2) The working set algorithm
- 30. 30 The WSClock Page Replacement Algorithm Operation of the WSClock algorithm
- 31. 31 Review of Page Replacement Algorithms
- 32. 32 Modeling Page Replacement Algorithms Belady's Anomaly • FIFO with 3 page frames • FIFO with 4 page frames • P's show which page references show page faults
- 33. 33 Stack Algorithms State of memory array, M, after each item in reference string is processed 7 4 6 5
- 34. 34 The Distance String Probability density functions for two hypothetical distance strings
- 35. 35 The Distance String • Computation of page fault rate from distance string – the C vector – the F vector
- 36. 36 Design Issues for Paging Systems Local versus Global Allocation Policies (1) • Original configuration • Local page replacement • Global page replacement
- 37. 37 Local versus Global Allocation Policies (2) Page fault rate as a function of the number of page frames assigned
- 38. 38 Load Control • Despite good designs, system may still thrash • When PFF algorithm indicates – some processes need more memory – but no processes need less • Solution : Reduce number of processes competing for memory – swap one or more to disk, divide up pages they held – reconsider degree of multiprogramming
- 39. 39 Page Size (1) Small page size • Advantages – less internal fragmentation – better fit for various data structures, code sections – less unused program in memory • Disadvantages – programs need many pages, larger page tables
- 40. 40 Page Size (2) • Overhead due to page table and internal fragmentation • Where – s = average process size in bytes – p = page size in bytes – e = page entry 2 s e p overhead p ⋅ = + page table space internal fragmentation Optimized when 2p se=
- 41. 41 Separate Instruction and Data Spaces • One address space • Separate I and D spaces
- 42. 42 Shared Pages Two processes sharing same program sharing its page table
- 43. 43 Cleaning Policy • Need for a background process, paging daemon – periodically inspects state of memory • When too few frames are free – selects pages to evict using a replacement algorithm • It can use same circular list (clock) – as regular page replacement algorithmbut with diff ptr
- 44. 44 Implementation Issues Operating System Involvement with Paging Four times when OS involved with paging 1. Process creation − determine program size − create page table 1. Process execution − MMU reset for new process − TLB flushed 1. Page fault time − determine virtual address causing fault − swap target page out, needed page in 1. Process termination time − release page table, pages
- 45. 45 Page Fault Handling (1) 1. Hardware traps to kernel 2. General registers saved 3. OS determines which virtual page needed 4. OS checks validity of address, seeks page frame 5. If selected frame is dirty, write it to disk
- 46. 46 Page Fault Handling (2) OS brings schedules new page in from disk Page tables updated Faulting instruction backed up to when it began Faulting process scheduled Registers restored Program continues
- 47. 47 Instruction Backup An instruction causing a page fault
- 48. 48 Locking Pages in Memory • Virtual memory and I/O occasionally interact • Proc issues call for read from device into buffer – while waiting for I/O, another processes starts up – has a page fault – buffer for the first proc may be chosen to be paged out • Need to specify some pages locked – exempted from being target pages
- 49. 49 Backing Store (a) Paging to static swap area (b) Backing up pages dynamically
- 50. 50 Separation of Policy and Mechanism Page fault handling with an external pager
- 51. 51 Segmentation (1) • One-dimensional address space with growing tables • One table may bump into another
- 52. 52 Segmentation (2) Allows each table to grow or shrink, independently
- 53. 53 Segmentation (3) Comparison of paging and segmentation
- 54. 54 Implementation of Pure Segmentation (a)-(d) Development of checkerboarding (e) Removal of the checkerboarding by compaction
- 55. 55 Segmentation with Paging: MULTICS (1) • Descriptor segment points to page tables • Segment descriptor – numbers are field lengths
- 56. 56 Segmentation with Paging: MULTICS (2) A 34-bit MULTICS virtual address
- 57. 57 Segmentation with Paging: MULTICS (3) Conversion of a 2-part MULTICS address into a main memory address
- 58. 58 Segmentation with Paging: MULTICS (4) • Simplified version of the MULTICS TLB • Existence of 2 page sizes makes actual TLB more complicated
- 59. 59 Segmentation with Paging: Pentium (1) A Pentium selector
- 60. 60 Segmentation with Paging: Pentium (2) • Pentium code segment descriptor • Data segments differ slightly
- 61. 61 Segmentation with Paging: Pentium (3) Conversion of a (selector, offset) pair to a linear address
- 62. 62 Segmentation with Paging: Pentium (4) Mapping of a linear address onto a physical address
- 63. 63 Segmentation with Paging: Pentium (5) Protection on the Pentium Level
