Computer Networks & internet protocols.pptx
- 1. 1 COMPUTER NETWORKS AND INTERNET PROTOCOLS Application Layer – I I (DNS) SOUMYA K GHOSH COMPUTER SCIENCE AND ENGINEERING I I T KHARAGPUR SANDIP CHAKRABORTY COMPUTER SCIENCE AND ENGINEERING I I T KHARAGPUR
- 2. TCP/IP - Application Layer
- 3. Application Layer Examples • Domain Name System (DNS) • File Transfer Protocol (FTP) • Hypertext Transfer Protocol (HTTP) • Simple Mail Transport Protocol (SMTP) • Simple Network Management Protocol (SNMP) • Telnet • ….
- 4. What is DNS? • The global database system for Internet addressing, mail and other information. – Much easier to use and memorize. • Concept of domains and sub-domains. – Domain management is distributed. – DNS servers translate domain names to IP addresses.
- 5. Top Level Domains • com – Commercial • org – Non-profit • net – Network service provider • gov – US govt. • mil – military • edu – Education • au – Australian • at – Austrian • ca – Canadian • dk – Dutch • fr – French • de – German • in – Indian • it – Italian • jp – Japanese • kr – Korean • nz – New Zealand • es – Spanish • tw – Taiwanese • uk – British or Irish • us – U.S.
- 7. Domain Names and Labels
- 8. Domains
- 9. Domain Name Structure • Domain names are arranged in a hierarchical tree-like structure. in ac iitkgp iitb math cse cse ece mech nic Eg: cse.iitkgp.ac.in
- 10. Fully qualified domain names (FQDNs) • If a domain name ends in a dot it is assumed to be complete. This is called a fully qualified domain name (FQDN) or an absolute domain name. • If a domain name does not end in a dot, it is incomplete and the DNS resolver may complete this by appending a suffix to the domain name. The rules for doing this are implementation-dependent and locally configurable.
- 11. Generic TLDs • The top-level names are called the generic top-level domains (gTLDs), and can be three characters or more in length. the Internet • These names are registered withand maintained by Corporation for Assigned Names and Numbers (ICANN). http://www.icann.org
- 13. Country Domains • Top-level domains named for the each of the ISO 3166 international 2- character country codes (from ae for the United Arab Emirates to zw for Zimbabwe). These are called the country domains or the geographical domains. • Many countries have their own second-level domains underneath which parallel the generic top-level domains.
- 14. Distribution of Name Space
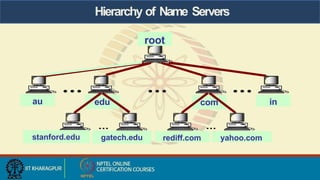
- 15. Hierarchy of Name Servers
- 17. What is a Zone? • Domains are broken into zones for which individual DNS servers are responsible. – A domain represents the entire set of names/machines that are contained under an organizational domain name. – A zone is a domain minus any sub-domains delegated to other DNS servers.
- 18. The Concept • Each domain name is typically served by 2 or more DNS servers for redundancy. – Referred to as primary and secondary. • Only one DNS server should be configured as primary for a zone. – Several secondary DNS servers possible. – The primary server contains master copy of the data for a zone. – Secondary servers get copies of this data through zone transfers.
- 19. Zone Transfer • A primary server loads all information from the disk file. • The secondary server loads all information from the primary server . • When the primary downloads information from the secondary, it is called zone transfer.
- 20. DNS in the Internet
- 21. DNS in the Internet
- 22. Generic Domains
- 23. Country Domains
- 24. Inverse Domain
- 25. Name Resolution
- 26. Name Resolution Process • The commonly used server is BIND (Berkeley Internal NameDomain). – Runs under UNIX as a process called named. • When an application needs some information from the server , it invokes the DNS name resolver. – DNS translates a fully qualified domain name into the corresponding IP address. – Using the command nslookup.
- 27. Name Resolution Process (contd…) – If the name server does not have the information locally, it asks its primary server , and so on. – For redundancy, each host may also have one or more secondary name servers which may be queried when the primary fails. • “nslookup” command
- 28. Hierarchy of Name Servers root stanford.edu com edu rediff.com au in yahoo.com gatech.edu
- 30. Iterative Name Resolution • Client sequentially sends queries to DNS servers and receives response. – If response is negative, the DNS serverto query next is also returned. – Unlike recursive name resolution, where only one response is finally returned back to the client.
- 33. Domain name stub resolver • Stub resolver, a routine linked with the user program, that forwards the queries to a name server for processing. • On most platforms, the stub resolver is implemented by two library routines (or by some variation of these routines): gethostbyname() and gethostbyaddr().
- 34. DNS Messages
- 35. DNS Resource Records (RR) • Domain Name System's distributed database is composed of resource records (RRs), which are divided into classes for different kinds of networks. • Resource records provide a mapping between domain names and network objects. • The most common network objects are the addresses of Internet hosts, but the Domain Name System is designed to accommodate a wide range of different objects. • A zone consists of a group of resource records, beginning with a Start of Authority (SOA) record. • The SOA record identifies the domain name of the zone. • There will be a name server (NS) record for the primary name server for this zone. There might also be NS records for the secondary name servers. • The NS records are used to identify which of the name servers are authoritative.
- 37. DNS RR Message Format
- 38. DNS Messages
- 39. Query and Response Messages
- 40. Header Format
- 41. QR: Query/Response OpCode:0 standard, 1 inverse, 2 server status AA: Authoritative TC: Truncated RD: Recursion Desired RA: Recursion Available rCode: Status of the error Flag Fields
- 42. Types of Records
- 46. Example 1 • A resolver sends a query message to a local server to find the IP address for the host “chal.fhda.edu”. We discuss the query and response messages separately.
- 47. Example 1: The Query Message
- 48. Example 1: The Response Message
- 49. Example 2 • An FTP server has received a packet from an FTP client with IP address 153.2.7.9. The FTP server wants to verify that the FTP client is anauthorized client.
- 50. Example 2: Inverse Query Message
- 51. Example 2: Inverse Response Message
- 52. 52
- 53. 1 COMPUTER NETWORKS AND INTERNET PROTOCOLS Application Layer – I I [Cli-Srv, FTP] SOUMYA K GHOSH COMPUTER SCIENCE AND ENGINEERING I I T KHARAGPUR SANDIP CHAKRABORTY COMPUTER SCIENCE AND ENGINEERING I I T KHARAGPUR
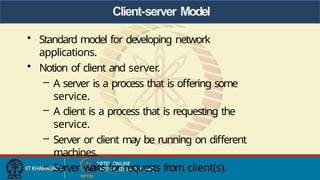
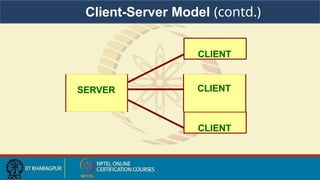
- 55. Client-server Model • Standard model for developing network applications. • Notion of client and server. – A server is a process that is offering some service. – A client is a process that is requesting the service. – Server or client may be running on different machines. – Server waits for requests from client(s).
- 56. CLIENT CLIENT SERVER CLIENT Client-Server Model (contd.)
- 57. Client-Server Model (contd.) • Typical scenario: – The server process starts on some computer system. • Initializes itself, then goes to sleep waiting for a client request. – A client process starts, either on the same system or on some other system. • Sends a request to the server.
- 58. Client-Server Model (contd.) – When the server process has finished providing its service to the client, the server goes back to sleep, waiting for the next client request to arrive. • The process repeats.
- 59. Client-Server Model (contd.) • Roles of the client and the server processes are asymmetric. • Two types of servers: – Iterative servers. – Concurrent servers.
- 60. Iterative Servers • Used when the server process knows in advance how long it takes to handle each request and it handles each request itself. – Single copy of server runs at all times. – A client may have to wait if the server is busy.
- 61. Concurrent Servers • Used when the amount of work required to handle a request is unknown; the server starts another process to handle each request. – A copy of the server caters to a client’s request in a dedicated fashion. – As many copies of server as there are client requests.
- 62. Using TCP or UDP • Before start of communication, a connection has to be established between the two hosts. • Five components in a connection: – Protocol used – Source IP address – Source port number – Destination IP address – Destination port number
- 63. Develop a Network Application • The best way is to use some standard and well-accepted protocol. – At the data link layer level, use Ethernet. – At the network layer level, use IP. – At the transport layer level, use TCP. – At the application layer level, use a standardAPI like the Berkeley Socket Interface.
- 64. What is a Socket? • The socket is the method for achieving inter-process communication (IPC). • It is used to allow one process to speak to another (on same or different machine). – Analogy: Like the telephone is used to allow one person to speak to another.
- 65. Socket - Basic Idea • When two processes located on two machines communicate, we define association and socket. – Association: basically a 5-tuple • Protocol • Local IP address • Local port number • Remote IP address • Remote port number
- 66. Socket - Basic Idea – Socket: also called half-association (a 3- tuple) • Protocol, local IP address, local port number • Protocol, remote IP address, remote port number
- 67. File Transfer Protocol (FTP)
- 68. FTP • Facilitates transfer of files over network • Server/Client model • FTP often works with • Transmission Control Protocol (TCP) • Telnet Protocol • Defined as RFC959
- 69. Overview of FTP • FTP uses TCP as a transport protocol to provide reliable end-to-end connections and implements two types of connections in managing data transfers. • The FTP client initiates the first connection, referred to as the control connection, to well-known port 21 (the client’s port is typically ephemeral). It is on this port that an FTP server listens for and accepts new connections. • The control connection is used for all of the control commands a client user uses to log on to the server , manipulate files, and terminate a session. This is also the connection across which the FTP server will send messages to the client in response to these control commands. Ref: IBM Redbools
- 70. Overview of FTP (contd.) • The second connection used by FTP is referred to as the data connection. • Typically, the data connection is established on server port 20. However , depending on how the data connection is established, both the client and server might use ephemeral ports. • FTP transfers the data over data connection. FTP only opens a data connection when a client issues a command requiring a data transfer , such as a request to retrieve a file, or to view a list of the files available. It is possible for an entire FTP session to open and close without a data connection ever having been opened. • The data connection is unidirectional. FTP can transfer data only from the client to the server , or from the server to the client, but not both. • The data connection can be initiated from either the client or the server . Data connections initiated by the server are active, while those initiated by the client are passive.
- 71. FTP – Basic working ⚫ FTP has to be on both server and client computers to work ⚫ Connection ⚫ Control connection (port 21) ⚫ Used to send and receive FTP commands ⚫ Data connection (port 20) ⚫ Used to upload and download files ⚫ Processes ⚫ Data Transfer Process (DTP) ⚫ Establishing the connection and managing the data channel ⚫ Protocol Interpreter (PI) ⚫ Interprets the protocol ⚫ let DTP be controlled using commands received over the control channel
- 72. FTP – Basic working (contd.) ⚫ Transferring mode between server and client ⚫ Active mode ⚫ Control connection port: Client: Large port (N>1023); Server: 21 ⚫ Data connection port: Client: N+1; Server: 20 ⚫ Passive mode ⚫ Control connection port: Client: Large port (N>1023); Server: 21 ⚫ Data connection port: Client: N+1; Server: large port (P>1023) ⚫ File Transferring mode ⚫ ASCII mode ⚫ .txt, .html, .asp, .vbs,.js ⚫ Binary ⚫ .doc, .pdf, .mp3/mp4
- 73. FTP – Basic working (contd.) • The client FTP application is built with a protocol interpreter (PI), a data transfer process (DTP), and a user interface. • The server FTP application typically only consists of a PI and DTP Ref: IBM Redbools
- 74. FTP – Basic working (contd.) • FTP client’s user interface communicates with the protocol interpreter (PI), which manages the control connection. • PI translates any application-specific commands to the RFC architected FTP commands, and then communicates these control commands to the FTP server. • The FTP server’s PI receives these commands, and then initiates the appropriate processes to service the client’s requests. If the requests require the transfer of data, data management is performed by the DTPs on both the client and server applications. • After the completion of the data transfer , the data connection is closed, and control is returned to the PIs of the client and server applications. • Only one data transfer can occur for each data connection. If multiple data transfers are required for a single FTP session, one distinct control connection will be opened for each transfer. Ref: IBM Redbools
- 75. FTP Operation – User’s Perspective When using FTP , the user performs some or all of the following operations: • Connect to a remote host. • Navigate and manipulate the directory structure. • List files available for transfer. • Define the transfer mode, transfer type, and data structure. • Transfer data to or from the remote host. • Disconnect from the remote host. Ref: IBM Redbools
- 76. A Typical FTP scenario Ref: IBM Redbools
- 77. Trivial File Transfer Protocol (TFTP) • TFTP file transfer is a disk-to-disk data transfer , and is an simple protocol used to transfer files. The simplicity of the architecture is deliberate in order to facilitate ease of implementation. • This simplistic approach has many benefits over traditional FTP , including: – Use by diskless devices to download firmware at boot time – Use by any automated process for which the assignment of a user ID or password is not feasible – Small application size, allowing it to be implemented inexpensively and in environments where resources are constricted • TFTP is implemented on top of the User Datagram Protocol. • The TFTP client initially sends read/write request through well-known port 69. The server and the client then determine the port that they will use for the rest of the connection. • TFTP lacks most of the features of FTP , and instead is limited to only reading a file from a server or writing a file to a server. • TFTP has no provisions for user authentication; in that respect, it is an insecure protocol. Ref: IBM Redbools
- 78. FTP – Access Commands Ref: TCP/IP Protocol Suite
- 79. FTP – File Management Commands Ref: TCP/IP Protocol Suite
- 80. FTP – Data Formatting Commands Ref: TCP/IP Protocol Suite
- 81. FTP – File Transfer Commands Ref: TCP/IP Protocol Suite
- 82. 30
- 83. 1 COMPUTER NETWORKS AND INTERNET PROTOCOLS Application Layer – IV [HTTP , HTML, TELNET] SOUMYA K GHOSH COMPUTER SCIENCE AND ENGINEERING I I T KHARAGPUR SANDIP CHAKRABORTY COMPUTER SCIENCE AND ENGINEERING I I T KHARAGPUR
- 84. HyperText Transfer Protocol (HTTP) • HTTP is the protocol that supports communication between webbrowsers and web servers. • A “Web Server” is a HTTP server • A “Web Browser” is a HTTP client • Most clients/servers run version 1.1, but 1.0 is also in use. – RFC 1945 (HTTP 1.0) – RFC 2616 (HTTP 1.1) • HTTP version 1.1 specifies a persistent connection by default.
- 85. HTTP – Overview • “HTTP is an application-level protocol with the lightness and speed necessary for distributed, hypermedia information systems.” • Transport Independence – HTTP protocol generally takes place over a TCP connection, – However , the protocol itself is not dependent on a specific transport layer.
- 86. Request - Response • HTTP has a simple structure: – client sends a request – server returns a reply. • HTTP can support multiple request-reply exchanges over a single TCP connection. • The “well known” TCP port for HTTP servers is port 80. – Other ports also can be used
- 87. ARCHITECTURE WWW is a distributed client/server service, in which a HTTP client (browser) can access a service from a HTTP server. • Client (Browser) • Server • Uniform Resource Locator • Cookies
- 88. Operation Ref: Data Communication and Networking, Forouzan
- 89. HTTP Client (Browser) Ref: Data Communication and Networking, Forouzan
- 90. URL
- 91. WEB DOCUMENTS Web documents can be grouped into three broad categories: • Static • Dynamic • Active
- 92. Static document Ref: Data Communication and Networking, Forouzan
- 93. Dynamic document using CGI (Common Gateway Interface)
- 94. Dynamic document using Server-site script Ref: Data Communication and Networking, Forouzan
- 95. Active document using Java applet
- 96. Active document using Client-site script
- 97. HTTP transaction
- 98. HTTP: Request and Response messages Ref: Data Communication and Networking, Forouzan
- 99. HTTP Request and Status lines
- 100. HTTP Methods Ref: Data Communication and Networking, Forouzan
- 101. HTTP Status Codes
- 102. HTTP Status Codes (contd…)
- 103. HTTP Header
- 104. Request Headers
- 105. Response Headers
- 106. HTTP: Entity headers
- 107. This example retrieves a document. We use the GET method to retrieve an image with the path /usr/bin/image1. The request line shows the method (GET), the URL, and the HTTP version (1.1). The header has two lines that show that the client can accept images in the GIF or JPEG format. The request does not have a body. The response message contains the status line and four lines of header. The header lines define the date, server, MIME version, and length of the document. The body of the document follows the header. Example 1
- 108. Clien t Request (GET method) GET /usr/bin/image1 HTTP/1.1 Accept: image/gif Accept: image/jpeg HTTP/1.1 200 OK Date: Mon, 07-Jan-05 13:15:14 GMT Server: Challenger MIME-version: 1.0 Content-length: 2048 (Body of the document) Respons e Serve r
- 109. In this example, the client wants to send data to the server. Use the POST method. The request line shows the method (POST), URL, and HTTP version (1.1). There are four lines of headers. The request body contains the input information. The response message contains the status line and four lines of headers. The created document, which is a CGI document, is included as the body Example 2
- 110. Example 2
- 111. Connecting HTTP server using TELNET
- 113. HTML
- 114. What is HTML? • Stands for Hyper Text Markup Language • Computer language used to create web pages • HTML file = text file containing markup tags such <p> • T ags tell Web browser how to display a page • Can have either *.htm or *.html file extension
- 115. HTML Elements • T ags are the elements that create the components of a page • T ags surrounded by angle brackets < > • Usually come in pairs – Example: Start tag <p> and end tag </p> • Stuff between is called “element content” • T ags are not case sensitive – New standard is to use lower case
- 116. Y our created HTML document <html> <head> <title> …document title… </title> </head> <body> …your page content… </body> </html>
- 117. Page Components • <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1- transitional.dtd"> – First line of code – Declaration of version of HTML • <html>…</html> – Container for the document • <head>…</head> – <title> Title of page </title> • <body>…</body> – Content of page <html> <head> <title> …document title… </title> </head> <body> …your page content… </body> </html>
- 119. Basic T ags to <h6>…</ h6> • Headings – <h1>… </h1> – Like in Word • Paragraph – <p>… </p> – Inserts a line space before and after a paragraph
- 120. Example of use of Heading
- 121. Link T ag • Link – Anchor tag <a>…</a> – 3 kinds • Link to page in same folder • Link to page in different folder • Link to outside webpage on the Internet.
- 122. Example of Anchor T ag <a href="http://www.iitkgp.ac.in">Go to the IITKgp home page</a> address text in page – Two components • Address • Text or description – this is what you see on the page
- 123. Image Source T ag • Empty tag – no closing tag • Components of Img tag <img src="url“ alt = “description of image” /> – url = points to location of the image file – alt = describes image for screen readers
- 124. File location • Same folder: “samplePic.gif” – Document-relative link – Look for image in same folder • Different folder named images: “/images/samplePic.gif”
- 125. Division T ag • <div>…</div> – Division or section of document – Use to group elements to apply formatting or style – Example: <div style="color: #1F00FF"> <h1> Title of section</h1> <p> Computer Networks</p> </div> <html> <head> <title> Sample - Page</title> </head> <body> Hello from NPTEL! <div style="color: #1F00FF"> <h1> Title of section</h1> <p> Computer Networks </p> </div> </body> </html>
- 127. Examples of use of Links
- 128. Typical HTML document <html> <head> <title> …document title… </title> </head> <body> …your page content… </body> </html>
- 129. End Product • <html> • <head> • <title>Author’s Page</title> • </head> • <body> • <div> • <a href="index.html>Home</a><br /> • <a href="courses.html">Courses</a><br /> • <a href="personal.html">Personal</a><br /> • </div> • <p>Hello my name is XYZ and I am writing about myself. Contact info: <a href="http://www.hawaii.edu/slis/webteam">Web Team</a> <div> <img src="palmtree.jpg"alt=”a picture of a palm tree”/> </div> • • • • • • </ div> • </ body> • </ html>
- 130. Next Mission • Choose colors for your page – Text color – Link color – Background color • Choose font size – Type of font – Font size
- 131. TELNET
- 132. TELNET
- 133. TELNET vs. telnet • TELNET is a protocol that provides “a general, bi- directional, eight-bit byte oriented communications facility”. • telnet is a program that supports the TELNET protocol over TCP . • Many application protocols are built upon the TELNET protocol.
- 134. The TELNET Protocol Reference: RFC 854 • TCP connection (Popular port: 23) • Data and control over the same connection. • Network Virtual Terminal – intermediate representation of a generic terminal. – provides a standard language for communication of terminal control functions.
- 135. Network Virtual Terminal (NVT) NVT TCP Server Process NVT TCP
- 136. TELNET
- 137. Negotiated Options • All NVTs support a minimal set of capabilities. – Some terminals have more capabilities than the minimal set. • The set of options is not part of the TELNET protocol, – so that new terminal features can be incorporated without changing the TELNET protocol. • Two endpoints negotiate a set of mutually acceptable options – Line mode vs. character mode – echo modes – character set (EBCDIC vs. ASCII)
- 138. Control Functions • TELNET includes support for a series of control functions commonly supported by servers. • This provides a uniform mechanism for communication of (the supported) control functions.
- 139. Control Functions • Interrupt Process (IP) – suspend/abort process. • Abort Output (AO) – send no more output to user’s terminal. • Are Y ou There (AYT) – check to see if system is still running. • Erase Character (EC) – delete last character sent • Erase Line (EL) – delete all input in current line.
- 140. Command Structure • All TELNET commands and data flow through the same TCPconnection. • Commands start with a special character called the Interpret as Command escape character – The IAC code is 255. – If a 255 is sent as data - it must be followed by another 255. • If IAC is found and the next byte is IAC – a single byte is presented to application/terminal • If IAC is followed by any other code – the TELNET layer interprets this as a command.
- 141. TELNET Operations • You can use the telnet program to play with the TELNET protocol. • telnet is a generic TCP client. – Sends whatever you type to the TCP socket. – Prints whatever comes back through the TCP socket – Useful for testing TCP servers (ASCII based protocols). • Many Unix systems have these servers running (by default): – echo port 7 discard – daytime port 13 chargen port 9 port 19
- 142. telnet hostname port > telnet skg.cse.edu 7 Trying 234.197.140.246... Connected to skg.cse.edu (234.197.140.246). Escape character is '^]'. Hi SKG Hi SKG Testing telnet Testing telnet ^] telnet> quit Connection closed.
- 143. TELNET
- 144. 62
- 145. 1 COMPUTER NETWORKS AND INTERNET PROTOCOLS Application Layer – IV [HTTP , HTML, TELNET] SOUMYA K GHOSH COMPUTER SCIENCE AND ENGINEERING I I T KHARAGPUR SANDIP CHAKRABORTY COMPUTER SCIENCE AND ENGINEERING I I T KHARAGPUR
- 146. Simple Mail Transfer Protocol (SMTP)
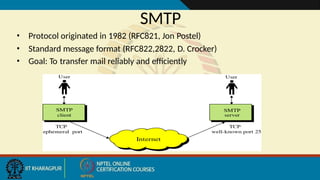
- 147. SMTP • Protocol originated in 1982 (RFC821, Jon Postel) • Standard message format (RFC822,2822, D. Crocker) • Goal: To transfer mail reliably and efficiently
- 148. SMTP • SMTP clients and servers have two main components – User Agents – Prepares the message, encloses it in an envelope. (ex. Thunderbird, Eudora) – Mail Transfer Agent – Transfers the mail across the internet (ex. Sendmail, Exim) – Analogous to the postal system in many ways
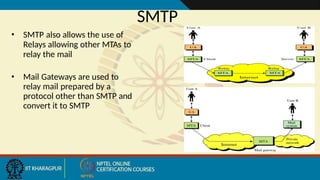
- 149. SMTP • SMTP also allows the use of Relays allowing other MTAs to relay the mail • Mail Gateways are used to relay mail prepared by a protocol other than SMTP and convert it to SMTP
- 150. Typical form of an Email • Mail is a text file • Envelope – – sender address – receiver address – other information • Message – – Mail Header – defines the sender, the receiver, the subject of the message, and other information – Mail Body – Contains the actual information in the message
- 151. SMTP Keywords Keyword Arguments HELO Sender’s Host Domain Name MAIL FROM: Email Address of sender RCPT TO: Email of Intended recipient DATA Body of the message QUIT
- 152. Keyword Arguments RSET VRFY Name to be verified NOOP TURN EXPN Mailing list to expand HELP Command Name SMTP Keywords
- 153. Status Codes • The Server responds with a 3 digit code that may be followed by text info – 2## - Success – 3## - Command can be accepted with more information – 4## - Command was rejected, but error condition is temporary – 5## - Command rejected, Bad User!
- 155. Message Progress
- 156. Connection Termination TCP Connection Termination
- 157. Solution: SMTP extensions • MIME – Multipurpose Internet Mail Extensions – Transforms non-ASCII data to NVT (Network Virtual Terminal) ASCII data • Text • Application • Image • Audio • Video RFC 1425, 1426, 1521
- 158. MIME Headers • Located between the Email Header and Body – MIME-Version: 1.1 – Content-Type: type/subtype – Content-Transfer-Encoding: encoding type – Content-Id: message id – Content-Description: textual explanation of non- textual contents
- 159. MIME Headers (cont’d) • Content-Type – Type of data used in the Body – Text: plain, unformatted text; HTML – Multipart: Body contains different data types – Message: Body contains a whole, part, or pointer to a message – Image: Message contains a static image (JPEG, GIF) – Video: Message contains an animated image (MPEG) – Audio: Message contains a basic sound sample (8kHz) – Application: Message is of data type not previously defined • Content-Transfer-Encoding – How to encode the message – 7 bit – no encoding needed – 8 bit – Non-ASCII, short lines – Binary – Non-ASCII, unlimited length lines – Base64 – 6 bit blocks encoded into 8-bit ASCII – Quoted-printable – send non-ASCII characters as 3 ASCII characters, =##, ## is the hex representation of the byte
- 160. MT As and Mail Access Protocols • The MT A delivers email to the user’s mailbox • Can be complex with numerous delivery methods, routers, and ACLs • Exim, Postfix, Sendmail • The Mail Access Protocols are used by the users to retrieve the email from the mailbox – POP3 – IMAP4
- 161. POP vs. IMAP All Messages POP3: IMAP : Johnr Internet Friends … Intern . et
- 162. Post Office Protocol v3 • Simple • Allows the user to obtain a list of their Emails • Users can retrieve their emails • Users can either delete or keep the email on their system • Minimizes server resources
- 163. Internet Mail Access Protocol (IMAP) v4 • Has more features than POP3 • User can check the email header before downloading • Emails can be accessed from any location • Can search the email for a specific string of characters before downloading • User can download parts of an email • User can create, delete, or rename mailboxes on a server
- 164. Simple Network Management Protocol (SNMP)
- 165. Network Management The development of SNMP was to be kept simple, facilitating rapid deployment of the protocol throughout the Internet community. After the immediate management needs were met, albeit temporarily, by SNMP, thorough research and development could be performed on CMIS/CMIP. Ultimately, this protocol would then be deployed as a permanent solution, replacing SNMP.
- 166. Simple Network Management Protocol (SNMP) Fundamental objective of Simple Network Management Protocol (SNMP) is to manage all aspects of a network, as well as applications related to that network. Monitor: SNMP implementations allow network administrators to monitor their networks in order to--among other things--ensure the health of the network, forecast usage and capacity, and in problem determination. Manage: SNMP provides the capability for network administrators to affect aspects with the network. Values which regulate network operation can be altered, allowing administrators to quickly respond to network problems, dynamically implement new network changes, and to perform real-time testing on how changes may affect their network.
- 167. Simple Network Management Protocol (SNMP) • SNMP implements a manager/agent/subagent model, which conforms very closely to the client/server model. • RFC 1157 defines the components and interactions involved in an SNMP community, which include: A Management Information Base An SNMP agent An manager SNMP subagents S N M P a ge nt S N M P m a n a g e r S N M P a ge nt S N M P a ge nt S N M P protocol m e s s a g e s
- 168. Simple Network Management Protocol (SNMP) • SNMP agent is software that runs on a piece of network equipment (host, router, printer, or others) and that maintains information about its configuration and current state in a database • Information in the database is described by Management Information Bases (MIBs) • An SNMP manager is an application program that contacts an SNMP agent to query or modify the database at the agent. • SNMP protocol is the application layer protocol used by SNMP agents and managers to send and receive data.
- 169. SNMP - Interactions S N M P M a n a g e r P ro c e s s Replies Queries Traps S N M P U D P IP IP U D P S N M P S N M P A g e n t P ro c e s s Access object s Dat a I P N e t w o r k M a n a g e m e n t Stat io n S N M P m e s s a g e s Trap s M a n a g e d S y s t e m M I B
- 170. Management Information Bases (MIBs) • A MIB specifies the managed objects • MIB is a text file that describes managed objects using the syntax of ASN.1 (Abstract Syntax Notation 1) • ASN.1 is a formal language for describing data and its properties • In Linux, MIB files are in the directory /usr/share/snmp/mibs –Multiple MIB files –MIB-II (defined in RFC 1213) defines the managed objects of TCP/IP networks
- 171. Managed Objects • Each managed object is assigned an object identifier (OID) • OID is specified in a MIB file. • An OID can be represented as a sequence of integers separated by decimal points or by a text string: • When an SNMP manager requests an object, it sends the OID to the SNMP agent.
- 172. SNMP Protocol • SNMP manager and an SNMP agent communicate using the SNMP protocol –Generally: Manager sends queries and agent responds –Exception: Traps are initiated by agent. g e t- r e q u e s t g e t- n ex t - r e q u e s t se t - re q u e s t trap P o r t 1 6 1 P o r t 1 6 1 P o r t 1 6 1 P o r t 1 6 2 S N M P a g e n t S N M P m a n a g e r g e t- r e s p o n s e g e t- r e s p o n s e g e t- r e s p o n s e
- 173. SNMP Protocol • Get-request. Requests the values of one or more objects • Get-next-request. Requests the value of the next object, according to a lexicographical ordering of OIDs. • Set-request. A request to modify the value of one or more objects • Get-response. Sent by SNMP agent in response to a get-request, get-next- request, or set-request message. • Trap. An SNMP trap is a notification sent by an SNMP agent to an SNMP manager, which is triggered by certain events at the agent.
- 174. SNMP Versions • Three versions are in use today: –SNMPv1 (1990) –SNMPv2c (1996) •Adds “GetBulk” function and some new types •Adds RMON (remote monitoring) capability –SNMPv3 (2002) •SNMPv3 started from SNMPv1 (and not SNMPv2c) •Addresses security • All versions are active • Many SNMP agents and managers support all three versions of the protocol.
- 175. Format of SNMP Packets • SNMPv1 Get/Set messages: Version Community SNMP PDU PDU Type Request ID Error Status Error Index Object 1, Value 1 Object 2, Value 2 ... Cleartext string that is used as a password PDU type, e.g.: 32: SNMPv1 Get 64: SNMPv2 Get Unique ID to match requests with replies Sequence of name-value pairs
- 176. SNMP Security • SNMPv1 uses plain text community strings for authentication as plain text without encryption • SNMPv2 was supposed to fix security problems, but effort de-railed (The “c” in SNMPv2c stands for “community”). • SNMPv3 has numerous security features: – Ensure that a packet has not been tampered with (integrity), – Ensures that a message is from a valid source (authentication) – Ensures that a message cannot be read by unauthorized (privacy).
- 177. References 1. “TCP/IP Tutorial and Technical Overview”, An IBM Redbooks publication, 2006. 2. Data Communications & Networking, Behrouz A. Forouzan 3. TCP/IP Protocol Suite, B. Forouzan 4. SMTP, TCP/IP and Upper Layer Protocols, Ezra Kissel, M. Lacroce and J. Watson 5. Internet resources
- 178. 34



















































![1
COMPUTER NETWORKS AND
INTERNET PROTOCOLS
Application Layer – I
I [Cli-Srv, FTP]
SOUMYA K GHOSH
COMPUTER SCIENCE AND ENGINEERING
I
I
T KHARAGPUR
SANDIP CHAKRABORTY
COMPUTER SCIENCE AND ENGINEERING
I
I
T KHARAGPUR](https://image.slidesharecdn.com/computernetworksinternetprotocols-250625075210-3411524c/85/Computer-Networks-internet-protocols-pptx-53-320.jpg)



























![1
COMPUTER NETWORKS AND
INTERNET PROTOCOLS
Application Layer – IV [HTTP
, HTML, TELNET]
SOUMYA K GHOSH
COMPUTER SCIENCE AND ENGINEERING
I
I
T KHARAGPUR
SANDIP CHAKRABORTY
COMPUTER SCIENCE AND ENGINEERING
I
I
T KHARAGPUR](https://image.slidesharecdn.com/computernetworksinternetprotocols-250625075210-3411524c/85/Computer-Networks-internet-protocols-pptx-83-320.jpg)


























































![telnet hostname port
> telnet skg.cse.edu 7
Trying 234.197.140.246...
Connected to skg.cse.edu
(234.197.140.246).
Escape character is '^]'.
Hi SKG
Hi SKG
Testing telnet
Testing telnet
^]
telnet> quit
Connection closed.](https://image.slidesharecdn.com/computernetworksinternetprotocols-250625075210-3411524c/85/Computer-Networks-internet-protocols-pptx-142-320.jpg)


![1
COMPUTER NETWORKS AND
INTERNET PROTOCOLS
Application Layer – IV [HTTP
, HTML, TELNET]
SOUMYA K GHOSH
COMPUTER SCIENCE AND ENGINEERING
I
I
T KHARAGPUR
SANDIP CHAKRABORTY
COMPUTER SCIENCE AND ENGINEERING
I
I
T KHARAGPUR](https://image.slidesharecdn.com/computernetworksinternetprotocols-250625075210-3411524c/85/Computer-Networks-internet-protocols-pptx-145-320.jpg)