Computer Security Lecture 2: Classical Encryption Techniques 1
13 likes2,467 views
https://mloey.github.io/courses/security2017.html https://www.youtube.com/watch?v=td_8AM80DUA&list=PLKYmvyjH53q13_6aS4VwgXU0Nb_4sjwuf&index=2&t=37s We will discuss the following: Symmetric Encryption, Substitution Techniques, Caesar Cipher, Monoalphabetic Cipher, Playfair Cipher, Hill Cipher
1 of 72
Downloaded 265 times


































































Ad
Recommended
Feistel cipher



Feistel cipherMDKAWSARAHMEDSAGAR This presentation introduces Feistel encryption and decryption. It discusses the Feistel cipher structure which partitions the input block into two halves and processes them through multiple rounds of substitution and permutation. It shows diagrams of the Feistel encryption and decryption processes. It also covers the design features of Feistel networks such as block size, key size, number of rounds, and sub-key generation. Finally, it provides an example of the round function that performs a bitwise XOR of the left half and output of a function applied to the right half and sub-key.
Computer Security Lecture 3: Classical Encryption Techniques 2



Computer Security Lecture 3: Classical Encryption Techniques 2Mohamed Loey https://mloey.github.io/courses/security2017.html
https://www.youtube.com/watch?v=eGGnjwpaOIo&list=PLKYmvyjH53q13_6aS4VwgXU0Nb_4sjwuf&index=3&t=584s
We will discuss the following: Polyalphabetic Ciphers, Vigenère Cipher, Autokey Cipher, Vernam Cipher, Transposition Techniques, Rail Fence Cipher, Row Transposition Cipher
Cryptography



CryptographyTushar Swami A detailed description about Cryptography explaining the topic from the very basics. Explaining how it all started, and how is it currently being applied in the real world. Mostly useful for students in engineering and mathematics.
What is AES? Advanced Encryption Standards



What is AES? Advanced Encryption StandardsFaisal Shahzad Khan AES (Advanced Encryption Standard) is a symmetric block cipher encryption method that uses a block size of 128 bits and key sizes of 128, 192, or 256 bits. It is an iterative cipher based on substitutions and permutations that performs all computations on bytes rather than bits. The encryption process consists of initial round, main rounds, and final round, with the number of main rounds varying based on key size. Decryption undoes the encryption process in reverse order using inverse operations. AES-256 is considered the most secure variant due to its 256-bit key size.
Topic20 The RC4 Algorithm.pptx



Topic20 The RC4 Algorithm.pptxUrjaDhabarde power point presentation on RC4 encryption decryption algorithm in cryptography and network security
Substitution cipher and Its Cryptanalysis



Substitution cipher and Its CryptanalysisSunil Meena Substitution Cipher
classical cipher and monoalphabetic and polyalphabetic cipher and its cryptanalysis . Correctness and security and learning analysis
Cryptographic algorithms



Cryptographic algorithmsAnamika Singh The document summarizes cryptographic algorithms DES and AES. It describes the basic concepts of encryption, the history and workings of DES including key generation and encryption/decryption processes. It then explains the AES cipher which was selected to replace DES, including the cipher structure involving substitution, shifting, mixing and adding round keys in multiple rounds of processing. The key expansion process is also summarized, which derives the round keys from the main encryption key.
Introduction to Cryptography



Introduction to CryptographySeema Goel The presentation covers the following:
Basic Terms
Cryptography
The General Goals of Cryptography
Common Types of Attacks
Substitution Ciphers
Transposition Cipher
Steganography- “Concealed Writing”
Symmetric Secret Key Encryption
Types of Symmetric Algorithms
Common Symmetric Algorithms
Asymmetric Secret Key Encryption
Common Asymmetric Algorithms
Public Key Cryptography
Hashing Techniques
Hashing Algorithms
Digital Signatures
Transport Layer Security
Public key infrastructure (PKI)
symmetric key encryption algorithms



symmetric key encryption algorithmsRashmi Burugupalli Symmetric Key Encryption Algorithms can be categorized as stream ciphers or block ciphers. Block ciphers like the Data Encryption Standard (DES) operate on fixed-length blocks of bits, while stream ciphers process messages bit-by-bit. DES is an example of a block cipher that encrypts 64-bit blocks using a 56-bit key. International Data Encryption Algorithm (IDEA) is another block cipher that uses a 128-bit key and 64-bit blocks, employing addition and multiplication instead of XOR like DES. IDEA consists of 8 encryption rounds followed by an output transformation to generate the ciphertext from the plaintext and key.
block ciphers



block ciphersAsad Ali In cryptography, a block cipher is a deterministic algorithm operating on ... Systems as a means to effectively improve security by combining simple operations such as .... Finally, the cipher should be easily cryptanalyzable, such that it can be ...
Public Key Cryptography



Public Key CryptographyGopal Sakarkar Public key cryptography uses two keys, a public key that can encrypt messages and a private key that decrypts messages. It has six components: plain text, encryption algorithm, public and private keys, ciphertext, and decryption algorithm. Some key characteristics are that it is computationally infeasible to determine the private key from the public key alone, and encryption/decryption is easy when the relevant key is known. The requirements of public key cryptography are that it is easy to generate a public-private key pair, easy to encrypt with the public key, easy for the recipient to decrypt with the private key, and infeasible to determine the private key from the public key or recover the plaintext from the ciphertext and public key alone
Cryptanalysis



CryptanalysisSou Jana This document provides an overview of the course CS8792 - Cryptography and Network Security. It discusses foundational topics in cryptography including classical encryption techniques, modern cryptography foundations, and cryptanalysis. Cryptanalysis techniques covered include brute force attacks, dictionary attacks, rainbow table attacks, known-plaintext analysis, chosen-plaintext analysis, ciphertext-only analysis, and man-in-the-middle attacks. The success of cryptanalysis depends on the time, computing power, and storage available to attackers.
DES (Data Encryption Standard) pressentation



DES (Data Encryption Standard) pressentationsarhadisoftengg This document discusses data encryption methods. It defines encryption as hiding information so it can only be accessed by those with the key. There are two main types: symmetric encryption uses one key, while asymmetric encryption uses two different but related keys. Encryption works by scrambling data using techniques like transposition, which rearranges the order, and substitution, which replaces parts with other values. The document specifically describes the Data Encryption Standard (DES) algorithm and the public key cryptosystem, which introduced the innovative approach of using different keys for encryption and decryption.
Data Encryption Standard (DES)



Data Encryption Standard (DES)Haris Ahmed - DES (Data Encryption Standard) is a symmetric block cipher algorithm that encrypts data in 64-bit blocks using a 56-bit key. It was the first encryption standard adopted by the U.S. government for protecting sensitive unclassified federal government information.
- DES works by performing 16 rounds of complex substitutions and permutations on each data block, encrypting it using the key. It has various modes of operation like ECB, CBC, CFB, OFB, and CTR that specify how it operates on data.
- In 1998, DES was broken using a brute force attack by the Electronic Frontier Foundation in just 3 days, showing the need for stronger algorithms like AES which replaced DES as the encryption standard
Hash Function 



Hash Function ssuserdfb2da This document discusses cryptographic hash functions including their applications in message authentication and digital signatures. It describes the requirements for hash functions to be secure including resistance to brute force attacks and cryptanalysis. The document outlines some simple hash functions and provides details on the Secure Hash Algorithm (SHA) family of cryptographic hash functions used in standards like SHA-512 which operates on 1024-bit blocks through 80 rounds. It also mentions NIST's selection of the Keccak algorithm as the new SHA-3 standard.
Aes



AesMuhammad Asif The document summarizes the Advanced Encryption Standard (AES). It describes how AES was selected by NIST as a replacement for DES. AES (Rijndael cipher) uses a block size of 128 bits, with key sizes of 128, 192, or 256 bits. It operates on data in rounds that include byte substitution, shifting rows, mixing columns, and adding the round key. The key is expanded into an array of words used for each round.
Block ciphers & public key cryptography



Block ciphers & public key cryptographyRAMPRAKASHT1 This document provides an overview of block ciphers and public key cryptography. It discusses the principles of block ciphers, including block cipher modes of operation. Popular block ciphers like DES, AES, Triple DES and Blowfish are described. The document also covers public key cryptography principles and algorithms like RSA and Diffie-Hellman key exchange. It provides details on elliptic curve cryptography and the arithmetic behind it.
Diffie hellman key exchange algorithm



Diffie hellman key exchange algorithmSunita Kharayat The presentation include:
-Diffie hellman key exchange algorithm
-Primitive roots
-Discrete logarithm and discrete logarithm problem
-Attacks on diffie hellman and their possible solution
-Key distribution center
Symmetric encryption



Symmetric encryptionDR RICHMOND ADEBIAYE Modern block ciphers are widely used to provide encryption of quantities of information, and/or a cryptographic checksum to ensure the contents have not been altered. We continue to use block ciphers because they are comparatively fast, and because we know a fair amount about how to design them.
Cryptography and Network Security William Stallings Lawrie Brown



Cryptography and Network Security William Stallings Lawrie BrownInformation Security Awareness Group Block ciphers like DES encrypt data in blocks and are based on the Feistel cipher structure. DES encrypts 64-bit blocks using a 56-bit key and 16 rounds of encryption. Modern cryptanalysis techniques like differential and linear cryptanalysis use statistical analysis to reveal weaknesses in block ciphers, though DES remains relatively secure against these attacks. Careful design of block ciphers, including aspects like non-linear substitution boxes and complex key scheduling, aims to provide security against cryptanalysis.
Double DES & Triple DES



Double DES & Triple DESHemant Sharma Double Data Encryption Standard (2DES) and Triple Data Encryption Standard (3DES) with 2 key and 3 key.
Encryption algorithms



Encryption algorithmstrilokchandra prakash In this PPT we are discuss about the cryptography and what are the encryption algorithms are used for the cryptography.
CNIT 141: 6. Hash Functions



CNIT 141: 6. Hash FunctionsSam Bowne For a college course -- CNIT 141: Cryptography for Computer Networks, at City College San Francisco
Based on "Serious Cryptography: A Practical Introduction to Modern Encryption", by Jean-Philippe Aumasson, No Starch Press (November 6, 2017), ISBN-10: 1593278268 ISBN-13: 978-1593278267
Instructor: Sam Bowne
More info: https://samsclass.info/141/141_S19.shtml
Information and data security advanced encryption standard (aes)



Information and data security advanced encryption standard (aes)Mazin Alwaaly Information And Data Security Advanced Encryption Standard (AES) seminar
Mustansiriya University
Department of Education
Computer Science
Classical Encryption Techniques in Network Security



Classical Encryption Techniques in Network Securitybabak danyal The document provides an overview of classical encryption techniques, including: symmetric ciphers that use the same key for encryption and decryption (such as the Caesar cipher, monoalphabetic ciphers like the Playfair cipher, and polyalphabetic ciphers like the Vigenère cipher) as well as transposition techniques that rearrange plaintext; rotor machines like the Enigma that implemented complex polyalphabetic substitution; and steganography that hides messages within other files or messages. The goal is to introduce basic concepts and terminology of encryption to prepare for studying modern cryptography.
Cryptography and network security



Cryptography and network securitypatisa This document provides an overview of cryptography including:
1. Cryptography is the process of encoding messages to protect information and ensure confidentiality, integrity, authentication and other security goals.
2. There are symmetric and asymmetric encryption algorithms that use the same or different keys for encryption and decryption. Examples include AES, RSA, and DES.
3. Other techniques discussed include digital signatures, visual cryptography, and ways to implement cryptography like error diffusion and halftone visual cryptography.
Symmetric & Asymmetric Cryptography



Symmetric & Asymmetric Cryptographychauhankapil This document summarizes symmetric and asymmetric cryptography. Symmetric cryptography involves both parties agreeing on an encryption algorithm and key beforehand to encrypt and decrypt messages. Asymmetric cryptography uses public and private key pairs, where the public key encrypts messages and the private key decrypts them, allowing encryption without pre-sharing keys. It also discusses digital signatures, where messages are signed with a private key and verified with the corresponding public key. Common attacks on public-key cryptography like man-in-the-middle attacks are addressed. The document is intended for a computer science course on cryptography fundamentals and security mechanisms.
Cs8792 cns - unit v



Cs8792 cns - unit vArthyR3 The document discusses intrusion detection and various types of intruders and intrusion techniques. It covers password capture methods like watching someone enter their password or using a Trojan horse. It also discusses different types of intrusion detection approaches like statistical anomaly detection, rule-based detection, and honeypots. The document then covers password management, viruses, worms, and distributed denial of service attacks. It concludes by discussing firewall design principles and characteristics like packet filtering routers.
Computer Security Lecture 1: Overview



Computer Security Lecture 1: OverviewMohamed Loey https://mloey.github.io/courses/security2017.html
We will discuss the following: Cryptography, Computer Security, OSI Security Architecture, Security Structure Scheme, Key Properties, Symmetric Encryption, Asymmetric Encryption, finally Our Book
Computer Security Lecture 4: Block Ciphers and the Data Encryption Standard



Computer Security Lecture 4: Block Ciphers and the Data Encryption StandardMohamed Loey We will discuss the following: Stream Ciphers and Block Ciphers, Data Encryption Standard, DES Algorithm, DES Key Creation, DES Encryption, The Strength Of DES.
https://www.youtube.com/watch?v=1-lF4dePpts&list=PLKYmvyjH53q13_6aS4VwgXU0Nb_4sjwuf
More Related Content
What's hot (20)
symmetric key encryption algorithms



symmetric key encryption algorithmsRashmi Burugupalli Symmetric Key Encryption Algorithms can be categorized as stream ciphers or block ciphers. Block ciphers like the Data Encryption Standard (DES) operate on fixed-length blocks of bits, while stream ciphers process messages bit-by-bit. DES is an example of a block cipher that encrypts 64-bit blocks using a 56-bit key. International Data Encryption Algorithm (IDEA) is another block cipher that uses a 128-bit key and 64-bit blocks, employing addition and multiplication instead of XOR like DES. IDEA consists of 8 encryption rounds followed by an output transformation to generate the ciphertext from the plaintext and key.
block ciphers



block ciphersAsad Ali In cryptography, a block cipher is a deterministic algorithm operating on ... Systems as a means to effectively improve security by combining simple operations such as .... Finally, the cipher should be easily cryptanalyzable, such that it can be ...
Public Key Cryptography



Public Key CryptographyGopal Sakarkar Public key cryptography uses two keys, a public key that can encrypt messages and a private key that decrypts messages. It has six components: plain text, encryption algorithm, public and private keys, ciphertext, and decryption algorithm. Some key characteristics are that it is computationally infeasible to determine the private key from the public key alone, and encryption/decryption is easy when the relevant key is known. The requirements of public key cryptography are that it is easy to generate a public-private key pair, easy to encrypt with the public key, easy for the recipient to decrypt with the private key, and infeasible to determine the private key from the public key or recover the plaintext from the ciphertext and public key alone
Cryptanalysis



CryptanalysisSou Jana This document provides an overview of the course CS8792 - Cryptography and Network Security. It discusses foundational topics in cryptography including classical encryption techniques, modern cryptography foundations, and cryptanalysis. Cryptanalysis techniques covered include brute force attacks, dictionary attacks, rainbow table attacks, known-plaintext analysis, chosen-plaintext analysis, ciphertext-only analysis, and man-in-the-middle attacks. The success of cryptanalysis depends on the time, computing power, and storage available to attackers.
DES (Data Encryption Standard) pressentation



DES (Data Encryption Standard) pressentationsarhadisoftengg This document discusses data encryption methods. It defines encryption as hiding information so it can only be accessed by those with the key. There are two main types: symmetric encryption uses one key, while asymmetric encryption uses two different but related keys. Encryption works by scrambling data using techniques like transposition, which rearranges the order, and substitution, which replaces parts with other values. The document specifically describes the Data Encryption Standard (DES) algorithm and the public key cryptosystem, which introduced the innovative approach of using different keys for encryption and decryption.
Data Encryption Standard (DES)



Data Encryption Standard (DES)Haris Ahmed - DES (Data Encryption Standard) is a symmetric block cipher algorithm that encrypts data in 64-bit blocks using a 56-bit key. It was the first encryption standard adopted by the U.S. government for protecting sensitive unclassified federal government information.
- DES works by performing 16 rounds of complex substitutions and permutations on each data block, encrypting it using the key. It has various modes of operation like ECB, CBC, CFB, OFB, and CTR that specify how it operates on data.
- In 1998, DES was broken using a brute force attack by the Electronic Frontier Foundation in just 3 days, showing the need for stronger algorithms like AES which replaced DES as the encryption standard
Hash Function 



Hash Function ssuserdfb2da This document discusses cryptographic hash functions including their applications in message authentication and digital signatures. It describes the requirements for hash functions to be secure including resistance to brute force attacks and cryptanalysis. The document outlines some simple hash functions and provides details on the Secure Hash Algorithm (SHA) family of cryptographic hash functions used in standards like SHA-512 which operates on 1024-bit blocks through 80 rounds. It also mentions NIST's selection of the Keccak algorithm as the new SHA-3 standard.
Aes



AesMuhammad Asif The document summarizes the Advanced Encryption Standard (AES). It describes how AES was selected by NIST as a replacement for DES. AES (Rijndael cipher) uses a block size of 128 bits, with key sizes of 128, 192, or 256 bits. It operates on data in rounds that include byte substitution, shifting rows, mixing columns, and adding the round key. The key is expanded into an array of words used for each round.
Block ciphers & public key cryptography



Block ciphers & public key cryptographyRAMPRAKASHT1 This document provides an overview of block ciphers and public key cryptography. It discusses the principles of block ciphers, including block cipher modes of operation. Popular block ciphers like DES, AES, Triple DES and Blowfish are described. The document also covers public key cryptography principles and algorithms like RSA and Diffie-Hellman key exchange. It provides details on elliptic curve cryptography and the arithmetic behind it.
Diffie hellman key exchange algorithm



Diffie hellman key exchange algorithmSunita Kharayat The presentation include:
-Diffie hellman key exchange algorithm
-Primitive roots
-Discrete logarithm and discrete logarithm problem
-Attacks on diffie hellman and their possible solution
-Key distribution center
Symmetric encryption



Symmetric encryptionDR RICHMOND ADEBIAYE Modern block ciphers are widely used to provide encryption of quantities of information, and/or a cryptographic checksum to ensure the contents have not been altered. We continue to use block ciphers because they are comparatively fast, and because we know a fair amount about how to design them.
Cryptography and Network Security William Stallings Lawrie Brown



Cryptography and Network Security William Stallings Lawrie BrownInformation Security Awareness Group Block ciphers like DES encrypt data in blocks and are based on the Feistel cipher structure. DES encrypts 64-bit blocks using a 56-bit key and 16 rounds of encryption. Modern cryptanalysis techniques like differential and linear cryptanalysis use statistical analysis to reveal weaknesses in block ciphers, though DES remains relatively secure against these attacks. Careful design of block ciphers, including aspects like non-linear substitution boxes and complex key scheduling, aims to provide security against cryptanalysis.
Double DES & Triple DES



Double DES & Triple DESHemant Sharma Double Data Encryption Standard (2DES) and Triple Data Encryption Standard (3DES) with 2 key and 3 key.
Encryption algorithms



Encryption algorithmstrilokchandra prakash In this PPT we are discuss about the cryptography and what are the encryption algorithms are used for the cryptography.
CNIT 141: 6. Hash Functions



CNIT 141: 6. Hash FunctionsSam Bowne For a college course -- CNIT 141: Cryptography for Computer Networks, at City College San Francisco
Based on "Serious Cryptography: A Practical Introduction to Modern Encryption", by Jean-Philippe Aumasson, No Starch Press (November 6, 2017), ISBN-10: 1593278268 ISBN-13: 978-1593278267
Instructor: Sam Bowne
More info: https://samsclass.info/141/141_S19.shtml
Information and data security advanced encryption standard (aes)



Information and data security advanced encryption standard (aes)Mazin Alwaaly Information And Data Security Advanced Encryption Standard (AES) seminar
Mustansiriya University
Department of Education
Computer Science
Classical Encryption Techniques in Network Security



Classical Encryption Techniques in Network Securitybabak danyal The document provides an overview of classical encryption techniques, including: symmetric ciphers that use the same key for encryption and decryption (such as the Caesar cipher, monoalphabetic ciphers like the Playfair cipher, and polyalphabetic ciphers like the Vigenère cipher) as well as transposition techniques that rearrange plaintext; rotor machines like the Enigma that implemented complex polyalphabetic substitution; and steganography that hides messages within other files or messages. The goal is to introduce basic concepts and terminology of encryption to prepare for studying modern cryptography.
Cryptography and network security



Cryptography and network securitypatisa This document provides an overview of cryptography including:
1. Cryptography is the process of encoding messages to protect information and ensure confidentiality, integrity, authentication and other security goals.
2. There are symmetric and asymmetric encryption algorithms that use the same or different keys for encryption and decryption. Examples include AES, RSA, and DES.
3. Other techniques discussed include digital signatures, visual cryptography, and ways to implement cryptography like error diffusion and halftone visual cryptography.
Symmetric & Asymmetric Cryptography



Symmetric & Asymmetric Cryptographychauhankapil This document summarizes symmetric and asymmetric cryptography. Symmetric cryptography involves both parties agreeing on an encryption algorithm and key beforehand to encrypt and decrypt messages. Asymmetric cryptography uses public and private key pairs, where the public key encrypts messages and the private key decrypts them, allowing encryption without pre-sharing keys. It also discusses digital signatures, where messages are signed with a private key and verified with the corresponding public key. Common attacks on public-key cryptography like man-in-the-middle attacks are addressed. The document is intended for a computer science course on cryptography fundamentals and security mechanisms.
Cs8792 cns - unit v



Cs8792 cns - unit vArthyR3 The document discusses intrusion detection and various types of intruders and intrusion techniques. It covers password capture methods like watching someone enter their password or using a Trojan horse. It also discusses different types of intrusion detection approaches like statistical anomaly detection, rule-based detection, and honeypots. The document then covers password management, viruses, worms, and distributed denial of service attacks. It concludes by discussing firewall design principles and characteristics like packet filtering routers.
Cryptography and Network Security William Stallings Lawrie Brown



Cryptography and Network Security William Stallings Lawrie BrownInformation Security Awareness Group
Viewers also liked (20)
Computer Security Lecture 1: Overview



Computer Security Lecture 1: OverviewMohamed Loey https://mloey.github.io/courses/security2017.html
We will discuss the following: Cryptography, Computer Security, OSI Security Architecture, Security Structure Scheme, Key Properties, Symmetric Encryption, Asymmetric Encryption, finally Our Book
Computer Security Lecture 4: Block Ciphers and the Data Encryption Standard



Computer Security Lecture 4: Block Ciphers and the Data Encryption StandardMohamed Loey We will discuss the following: Stream Ciphers and Block Ciphers, Data Encryption Standard, DES Algorithm, DES Key Creation, DES Encryption, The Strength Of DES.
https://www.youtube.com/watch?v=1-lF4dePpts&list=PLKYmvyjH53q13_6aS4VwgXU0Nb_4sjwuf
Cryptography.ppt



Cryptography.pptkusum sharma This document provides an overview of cryptography. It defines cryptography as the science of securing messages from attacks. It discusses basic cryptography terms like plain text, cipher text, encryption, decryption, and keys. It describes symmetric key cryptography, where the same key is used for encryption and decryption, and asymmetric key cryptography, which uses different public and private keys. It also covers traditional cipher techniques like substitution and transposition ciphers. The document concludes by listing some applications of cryptography like e-commerce, secure data, and access control.
Computer Security Lecture 4.1: DES Supplementary Material



Computer Security Lecture 4.1: DES Supplementary MaterialMohamed Loey We will discuss the following: Data Encryption Standard, DES Algorithm, DES Key Creation
https://www.youtube.com/watch?v=1-lF4dePpts&list=PLKYmvyjH53q13_6aS4VwgXU0Nb_4sjwuf
2 classical cryptosystems



2 classical cryptosystemsdmc5abdulla Shift ciphers are substitution ciphers where each letter is shifted a fixed number of positions in the alphabet. Substitution ciphers replace each letter with another letter or symbol according to a key. Frequency analysis involves analyzing letter frequencies in ciphertext to break substitution ciphers. The Vigenère cipher uses multiple substitution ciphers with different keys, making it harder to break using frequency analysis alone.
D-Cipher 1.0 (Strong Passwords)



D-Cipher 1.0 (Strong Passwords)Venkat Sandeep Manthi The document discusses common passwords and password security. It reports that the most common passwords are "123456", "password", and "12345678". Nearly 3,000 users chose "123456" as their password. The document provides tips for choosing more secure passwords such as using random letters, numbers, and symbols; avoiding common words and personal information; and not reusing the same password across accounts. It also warns about the risks of password cracking and accessing saved password information from browsers.
Introductory Lecture Information Systems 2011.12



Introductory Lecture Information Systems 2011.12Dr Mariann Hardey This document provides an overview of an information systems lecture that will explore emerging technologies, developing business cases, and evaluating benefits-driven portfolios through project-based group assignments. The lecture will ask students to critically think about life cycle models, development issues, systematic and exploratory powers, and frameworks for action. It recommends readings on agile project management, benefits management, and outlines learning outcomes related to understanding value from information systems, applying approaches to identify opportunities, setting investment priorities, and appreciating implementation skills.
Tx 3 hill shuman_oliver



Tx 3 hill shuman_oliverOPUNITE This document summarizes two presentations on treatment of opioid use disorders given at the National Prescription Drug Abuse Summit in 2014.
The first presentation outlines the risks of current inpatient opioid detoxification methods and benefits of evidence-based alternatives. It also examines opportunities for stakeholders to impact opioid addiction education.
The second presentation discusses innovations in buprenorphine treatment, including collaborative care models, group practice models, and strategies to address high-risk patients prescribed buprenorphine in office-based opioid treatment settings. Buprenorphine prescriber shortages, standards, retention challenges, and predictors of positive outcomes are also reviewed.
Shannon and 5 good criteria of a good cipher 



Shannon and 5 good criteria of a good cipher Sina Manavi The document discusses Claude Shannon and his 5 criteria for a good cipher. The criteria are that the amount of encryption should match the needed security level, the keys and encryption algorithm should be simple to implement and use, implementation should be as simple as possible without undermining security, errors shouldn't propagate, and the encrypted text shouldn't be longer than the original text. However, some of Shannon's concerns about complexity may no longer apply due to modern computers. The overall message is that ciphers should provide security without unnecessary complexity or expansion of the encrypted text.
Applications of-linear-algebra-hill-cipher



Applications of-linear-algebra-hill-cipherAashirwad Kashyap The document discusses the Hill cipher, a polygraphic cipher technique based on linear algebra. The Hill cipher operates on blocks of letters, using a secret key matrix to encrypt plaintext letters into ciphertext. It encrypts by multiplying blocks of plaintext letters by the key matrix, taking the result modulo 26. The corresponding decryption matrix is calculated from the encryption matrix and is used to decrypt by reversing the process. An example demonstrates encrypting and then decrypting the message "HELLO WORLD" using a 2x2 matrix.
Crypto tools



Crypto toolsNaga Srimanyu Timmaraju This document discusses several symmetric and asymmetric ciphers. It describes Caesar cipher, Vigenere cipher, transposition cipher, one-time pad, and RSA cipher. For each cipher it provides a brief overview of the encryption process and includes examples to demonstrate how the cipher works. It aims to educate the reader about common cryptographic tools and techniques.
Deconstructing Columnar Transposition Ciphers



Deconstructing Columnar Transposition CiphersRobert Talbert Examining the cycle structure and order of columnar transposition ciphers as elements of the symmetric group on L elements (L = length of message). Talk given at Ball State University Faculty Mathematics Colloquium, 2 April 2009.
Chap 05 ip addresses classfless



Chap 05 ip addresses classflessNoctorous Jamal - An organization was granted a block of IP addresses with the beginning address 14.24.74.0/24, containing 256 addresses total.
- The organization needs to create 11 subnets within this block to meet its networking needs.
- To create 11 subnets, the subnet prefix length would need to increase by 4 bits to /28, dividing the block into 16-address subnets (2^4 = 16 subnets).
Civilian OPSEC in cyberspace



Civilian OPSEC in cyberspacezapp0 Methods and techniques for monitoring, surveillance and profiling of cyberspace activities are available to state actors and criminal operators as well as to skilled individuals.
Civilian individuals without extensive knowledge and exposure to counter-intelligence techniques and Operations Security (OPSEC) protocols are vulnerable and helpless against these privacy breaches. This represents significant gap between actors and their victims – gap that can be bridged only through education.
The primary objective of this workshop oriented activity is to educate people operating in above-average risk situations in cyberspace and to bridge the unfair gap between them and malicious actors. Secondary objective aims at understanding how cyber security can be taught to non-security minded people in efficient way.
Semantech: IT Architecture in the Enterprise



Semantech: IT Architecture in the EnterpriseStephen Lahanas This presentation provides a high-level overview for the practice of IT Architecture in today's enterprise. It is the first in several IT Architecture presentations we will be providing.
Excel Lecture



Excel Lecturedeborah canning This document provides an overview and lessons for a Microsoft Excel 2003 training course on creating a workbook. It covers topics such as creating and navigating workbooks and worksheets, entering different types of data into cells including text, numbers, dates and times, and editing data. It also discusses formatting cells and removing formatting. The lessons include objectives, instructions, examples and practice questions.
Decoding QR codes



Decoding QR codesMaria Vassilopoulou Greek students worked on an eTwinning project called LEGENDS from 2015 to 2016 where they learned how to decode QR codes. The students worked in their classroom on this project to learn about decoding quick response barcodes. Their project involved figuring out how to read QR codes.
Secret key cryptography



Secret key cryptographyPrabhat Goel This document summarizes classical encryption techniques such as secret key cryptography, stream ciphers, block ciphers, substitution techniques like the Caesar cipher and Playfair cipher, polyalphabetic ciphers like the Vigenère cipher, and the theoretically unbreakable one-time pad cipher. It explains the basic components and workings of these classical encryption schemes.
Navigating Electronic Signature Law In Florida



Navigating Electronic Signature Law In FloridaClientSide In this presentation you will learn "The 4 General Principles of ESIGN" and the difference between UETA and Electronic Signatures in Global and National Commerce Act (ESIGN).
Firms that have adopted E-Sign Law and Technology in their practice typically have faster client-engagement times, lower overhead costs, a happier staff, and, most importantly, happier clients.
This E-Signatures Laws and Technology CLE addresses the authentication of scanned and emailed signatures, including scenarios specific to the practice of law. The seminar will give you a survey understanding of laws behind electronic signature laws, including the Federal Electronic Signatures in Global and National Commerce Act (ESIGN Act; 15 U.S.C. 96) and Georgia’s adoption of the Uniform Electronic Transactions Act (UETA; O.C.G.A. Sec. 10-12-1 et. seq). The seminar further discusses the audit technology you should have in place for digitally received signed documents.
Ad
Similar to Computer Security Lecture 2: Classical Encryption Techniques 1 (20)
Classic Information encryption techniques



Classic Information encryption techniquesJay Nagar (All Cipher Technic )
Symmetric Cipher
Basic Terminology
Brute Force
Classical Substitution Ciphers
Playfair Cipher
Cryptography
Network security CS2



Network security CS2Infinity Tech Solutions Cryptography, Classical Encryption
Breaking the Cryptosystem
Review the Simple attack to break the cryptosystem
Modular Arithmetic, Groups and Rings
One example each in classical substitutive and transposition ciphering.
Caesar/Affine Cipher –Worksheet and Lab Program
SYMMETRIC CYPHER MODELS WITH SUITABLE DIAGRAM.pptx



SYMMETRIC CYPHER MODELS WITH SUITABLE DIAGRAM.pptxajajkhan16 SYMMETRIC CYPHER MODELS WITH SUITABLE DIAGRAMSYMMETRIC CYPHER MODELS WITH SUITABLE DIAGRAM
Classical Encryption Techniques



Classical Encryption TechniquesJeevananthamArumugam The document discusses classical encryption techniques used in cryptography. It begins with an overview of symmetric encryption and the basic concepts of plaintext, ciphertext, encryption, and decryption. It then covers various classical encryption techniques like the Caesar cipher, monoalphabetic cipher, Playfair cipher, polyalphabetic ciphers including the Vigenère cipher, Vernam cipher, and the theoretically unbreakable one-time pad cipher. It also discusses transposition techniques like the rail fence cipher and row transposition cipher.
Classical encryption techniques



Classical encryption techniquesDr.Florence Dayana Symmetric Encryption,Cryptographic Systems,Encryption Scheme Security,Substitution Technique,Transposition Techniques ,Rotor Machines
Classical encryption techniques



Classical encryption techniquesJanani S The document discusses classical encryption techniques such as substitution ciphers like the Caesar cipher and monoalphabetic cipher, transposition ciphers like the rail fence cipher and row transposition cipher, and polyalphabetic ciphers like the Vigenere cipher. It introduces basic concepts and terminology in cryptography such as plaintext, ciphertext, encryption, decryption, and secret keys. The goals are to introduce basic concepts and terminology of encryption and to prepare for studying modern cryptography.
Classical encryption techniques



Classical encryption techniquesramya marichamy This document provides an overview of classical encryption techniques. It begins with definitions of key terms like plaintext, ciphertext, encryption, and decryption. It then describes the symmetric cipher model and simplifies it. The document outlines areas of cryptography and cryptanalysis. It explains techniques like substitution ciphers, the Caesar cipher, monoalphabetic ciphers, the Playfair cipher, the Hill cipher, polyalphabetic ciphers, and the one-time pad cipher. For each technique, it provides a brief description and encryption algorithm.
Classical encryption techniques



Classical encryption techniquesdhivyakesavan3 This ppt explains about the different types of classical encryption techniques. It also includes steganography and rotor machines.
EncryptionTechChap2.ppt



EncryptionTechChap2.pptrajirajesh8 Classical encryption techniques include symmetric ciphers that use the same key for encryption and decryption, such as substitution ciphers that replace plaintext letters and transposition ciphers that rearrange the order of letters. More complex techniques include the Playfair cipher which encrypts digrams and the Vigenère cipher that applies a series of Caesar ciphers controlled by a keyword. Product ciphers combine substitution and transposition layers to strengthen security.
Module 1.pptx



Module 1.pptxShilpaShettyA1 This document provides an overview of cryptography concepts and techniques. It defines cryptography and its principles such as symmetric and asymmetric ciphers. It then describes various classical encryption techniques like the Caesar cipher, monoalphabetic and polyalphabetic ciphers, the Playfair cipher, Hill cipher, and the Vernam cipher. For each technique, it explains the encryption and decryption algorithms and provides examples to illustrate how they work. The document also discusses cryptanalysis techniques like brute force attacks that can be used to break certain ciphers.
Symmetric Cipher Model, Substitution techniques, Transposition techniques, St...



Symmetric Cipher Model, Substitution techniques, Transposition techniques, St...JAINAM KAPADIYA 1) The document discusses symmetric encryption techniques including the symmetric cipher model, substitution techniques like the Caesar cipher and transposition techniques like the rail fence cipher.
2) It also covers the one-time pad cipher and its requirements for security as well as steganography techniques for hiding messages.
3) Cryptanalysis methods like brute force attacks and cryptanalytic attacks are explained for analyzing encryption algorithms.
ch02.ppt



ch02.pptShailendraPardeshi4 This document summarizes classical encryption techniques discussed in Chapter 2. Symmetric encryption uses a shared secret key between the sender and receiver. Techniques discussed include the Caesar cipher, which shifts letters by a fixed number; the monoalphabetic cipher, which maps each plaintext letter to a ciphertext letter; the Playfair cipher, which encrypts digrams; and the polyalphabetic Vigenère cipher, which uses multiple Caesar ciphers with a keyword as the key. The document also discusses cryptanalysis techniques like frequency analysis and the Kasiski method to help break these classical ciphers.
Classical Encryption Techniques



Classical Encryption Techniquesuniversity of education,Lahore The document discusses classical encryption techniques, including symmetric encryption which uses the same key for encryption and decryption. It describes ciphers like the Caesar cipher which substitutes letters by shifting the alphabet, the monoalphabetic cipher with one substitution table, and the polyalphabetic Vigenère cipher which uses multiple substitution alphabets. The document also covers the Playfair cipher which encrypts letters in pairs using a 5x5 keyword matrix, and discusses cryptanalysis techniques for breaking classical ciphers.
Elementary cryptography



Elementary cryptographyPrachi Gulihar The document provides an overview of elementary cryptography concepts including:
- Substitution and transposition ciphers such as Caesar cipher, Playfair cipher and Vigenère cipher. Frequency analysis and other cryptanalysis techniques are also discussed.
- The Data Encryption Standard (DES) which encrypts data in 64-bit blocks using a 56-bit key and 16 rounds of processing.
- Triple DES and issues with DES key length that led to it being broken. Linear cryptanalysis is also introduced.
- Public key encryption techniques that use asymmetric keys allowing encryption and decryption with different keys.
Ad
More from Mohamed Loey (20)
Lecture 6: Deep Learning Applications



Lecture 6: Deep Learning ApplicationsMohamed Loey We will discuss the following: Deep Learning Applications, Image Processing, Video Processing, Medical, Computer Network, Big Data, Bioinformatics.
Lecture 5: Convolutional Neural Network Models



Lecture 5: Convolutional Neural Network ModelsMohamed Loey We will discuss the following: Convolutional Neural Network, AlexNet, ZFNet, VGGNet, GoogleNet, ResNet, DenseNet.
Lecture 4: Deep Learning Frameworks



Lecture 4: Deep Learning FrameworksMohamed Loey The document provides information on several popular deep learning frameworks: TensorFlow, Caffe, Theano, Torch, CNTK, and Keras. It describes each framework's creator, license, programming languages supported, and brief purpose or use. TensorFlow is noted as the most popular framework, created by Google for machine learning research. Caffe is described as the fastest, Theano as most efficient, Torch is used by Facebook AI, CNTK for high scalability, and Keras for easy experimentation across frameworks. The document also provides examples of building and running computational graphs in TensorFlow.
Lecture 4: How it Works: Convolutional Neural Networks



Lecture 4: How it Works: Convolutional Neural NetworksMohamed Loey We will discuss the following: Filtering, Convolution, Convolution layer, Normalization, Rectified Linear Units, Pooling, Pooling layer, ReLU layer, Deep stacking, Fully connected layer.
Lecture 3: Convolutional Neural Networks



Lecture 3: Convolutional Neural NetworksMohamed Loey We will discuss the following: Deep vs Machine Learning, Superstar Researchers, Superstar Companies, Deep Learning, Deep Learning Requirements, Deep Learning Architectures, Convolution Neural Network, Case studies, LeNet,AlexNet, ZFNet, GoogLeNet, VGGNet, ResNet, ILSVRC, MNIST, CIFAR-10, CNN Optimization , NVIDIA TITAN X.
Lecture 2: Artificial Neural Network



Lecture 2: Artificial Neural NetworkMohamed Loey We will discuss the following: Artificial Neural Network, Perceptron Learning Example, Artificial Neural Network Training Process, Forward propagation, Backpropagation, Classification of Handwritten Digits, Neural Network Zoo.
Lecture 1: Deep Learning for Computer Vision



Lecture 1: Deep Learning for Computer VisionMohamed Loey This document discusses how deep learning has helped advance computer vision capabilities. It notes that deep learning can help bridge the gap between pixels and meaning by allowing computers to recognize complex patterns in images. It provides an overview of related fields like image processing, machine learning, artificial intelligence, and computer graphics. It also lists some specific applications of deep learning like object detection, image classification, and generating descriptive text. Students are then assigned a task to research how deep learning has improved one particular topic and submit a two-page summary.
Design of an Intelligent System for Improving Classification of Cancer Diseases



Design of an Intelligent System for Improving Classification of Cancer DiseasesMohamed Loey The methodologies that depend on gene expression profile have been able to detect cancer since its inception. The previous works have spent great efforts to reach the best results. Some researchers have achieved excellent results in the classification process of cancer based on the gene expression profile using different gene selection approaches and different classifiers
Early detection of cancer increases the probability of recovery. This thesis presents an intelligent decision support system (IDSS) for early diagnosis of cancer-based on the microarray of gene expression profiles. The problem of this dataset is the little number of examples (not exceed hundreds) comparing to a large number of genes (in thousands). So, it became necessary to find out a method for reducing the features (genes) that are not relevant to the investigated disease to avoid overfitting. The proposed methodology used information gain (IG) for selecting the most important features from the input patterns. Then, the selected features (genes) are reduced by applying the Gray Wolf Optimization algorithm (GWO). Finally, the methodology exercises support vector machine (SVM) for cancer type classification. The proposed methodology was applied to three data sets (breast, colon, and CNS) and was evaluated by the classification accuracy performance measurement, which is most important in the diagnosis of diseases. The best results were gotten when integrating IG with GWO and SVM rating accuracy improved to 96.67% and the number of features was reduced to 32 feature of the CNS dataset.
This thesis investigates several classification algorithms and their suitability to the biological domain. For applications that suffer from high dimensionality, different feature selection methods are considered for illustration and analysis. Moreover, an effective system is proposed. In addition, Experiments were conducted on three benchmark gene expression datasets. The proposed system is assessed and compared with related work performance.
Computer Security - CCNA Security - Lecture 2



Computer Security - CCNA Security - Lecture 2Mohamed Loey We will discuss the following: Classical Security Methods, AAA, Authentication, Authorization, Accounting, AAA Characteristic, Local Based AAA, Server Based AAA, TACACS+ and RADIUS.
Computer Security - CCNA Security - Lecture 1



Computer Security - CCNA Security - Lecture 1Mohamed Loey We will discuss the following: CCNAS Overview, Threats Landscape, Hackers Tools, Tools. Kali Linux Parrot Linux Cisco Packet Tracer Wireshark Denial of Service
Distributed DoS
Man In The Middle
Phishing
Vishing
Smishing
Pharming
Sniffer
Password Attack
Algorithms Lecture 8: Pattern Algorithms



Algorithms Lecture 8: Pattern AlgorithmsMohamed Loey We will discuss the following: Pattern searching, Naive Pattern Searching, Regular Expression.
Regular Expression Regular Expression Regular Expression Regular Expression Regular Expression Regular Expression Regular Expression Regular Expression Regular Expression Regular Expression Regular Expression
Algorithms Lecture 7: Graph Algorithms



Algorithms Lecture 7: Graph AlgorithmsMohamed Loey We will discuss the following: Graph, Directed vs Undirected Graph, Acyclic vs Cyclic Graph, Backedge, Search vs Traversal, Breadth First Traversal, Depth First Traversal, Detect Cycle in a Directed Graph.
Algorithms Lecture 6: Searching Algorithms



Algorithms Lecture 6: Searching AlgorithmsMohamed Loey We will discuss the following: Search Algorithms, Linear Search, Binary Search, Jump Search, and Interpolation Search
Algorithms Lecture 5: Sorting Algorithms II



Algorithms Lecture 5: Sorting Algorithms IIMohamed Loey We will discuss the following: Sorting Algorithms, Counting Sort, Radix Sort, Merge Sort.Algorithms, Time Complexity & Space Complexity, Algorithm vs Pseudocode, Some Algorithm Types, Programming Languages, Python, Anaconda.
Algorithms Lecture 4: Sorting Algorithms I



Algorithms Lecture 4: Sorting Algorithms IMohamed Loey The document discusses three sorting algorithms: bubble sort, selection sort, and insertion sort. Bubble sort works by repeatedly swapping adjacent elements that are in the wrong order. Selection sort finds the minimum element and swaps it into the sorted portion of the array. Insertion sort inserts elements into the sorted portion of the array, swapping as needed to put the element in the correct position. Both selection sort and insertion sort have a time complexity of O(n^2) in the worst case.
Algorithms Lecture 3: Analysis of Algorithms II



Algorithms Lecture 3: Analysis of Algorithms IIMohamed Loey We will discuss the following: Maximum Pairwise Product, Fibonacci, Greatest Common Divisors, Naive algorithm is too slow. The Efficient algorithm is much better. Finding the correct algorithm requires knowing something interesting about the problem
Algorithms Lecture 2: Analysis of Algorithms I



Algorithms Lecture 2: Analysis of Algorithms IMohamed Loey This document discusses analysis of algorithms and time complexity. It explains that analysis of algorithms determines the resources needed to execute algorithms. The time complexity of an algorithm quantifies how long it takes. There are three cases to analyze - worst case, average case, and best case. Common notations for time complexity include O(1), O(n), O(n^2), O(log n), and O(n!). The document provides examples of algorithms and determines their time complexity in different cases. It also discusses how to combine complexities of nested loops and loops in algorithms.
Algorithms Lecture 1: Introduction to Algorithms



Algorithms Lecture 1: Introduction to AlgorithmsMohamed Loey We will discuss the following: Algorithms, Time Complexity & Space Complexity, Algorithm vs Pseudo code, Some Algorithm Types, Programming Languages, Python, Anaconda.
Convolutional Neural Network Models - Deep Learning



Convolutional Neural Network Models - Deep LearningMohamed Loey Convolutional Neural Network Models - Deep Learning
Convolutional Neural Network
ILSVRC
AlexNet (2012)
ZFNet (2013)
VGGNet (2014)
GoogleNet 2014)
ResNet (2015)
Conclusion
Convolutional Neural Network (CNN) is a multi-layer neural network
Deep Learning - Overview of my work II



Deep Learning - Overview of my work IIMohamed Loey Deep Learning Machine Learning MNIST CIFAR 10 Residual Network AlexNet VGGNet GoogleNet Nvidia Deep learning (DL) is a hierarchical structure network which through simulates the human brain’s structure to extract the internal and external input data’s features
Recently uploaded (20)
How to Create a Rainbow Man Effect in Odoo 18



How to Create a Rainbow Man Effect in Odoo 18Celine George In Odoo 18, the Rainbow Man animation adds a playful and motivating touch to task completion. This cheerful effect appears after specific user actions, like marking a CRM opportunity as won. It’s designed to enhance user experience by making routine tasks more engaging.
Gibson "Secrets to Changing Behaviour in Scholarly Communication: A 2025 NISO...



Gibson "Secrets to Changing Behaviour in Scholarly Communication: A 2025 NISO...National Information Standards Organization (NISO) This presentation was provided by Jennifer Gibson of Dryad, during the first session of our 2025 NISO training series "Secrets to Changing Behavior in Scholarly Communications." Session One was held June 5, 2025.
LDMMIA Free Reiki Yoga S9 Grad Level Intuition II



LDMMIA Free Reiki Yoga S9 Grad Level Intuition IILDM & Mia eStudios Completed Sunday 6/8. For Weekend 6/14 & 15th. (Fathers Day Weekend US.) These workshops are also timeless for future students TY. No admissions needed.
A 9th FREE WORKSHOP
Reiki - Yoga
“Intuition-II, The Chakras”
Your Attendance is valued.
We hit over 5k views for Spring Workshops and Updates-TY.
Thank you for attending our workshops.
If you are new, do welcome.
Grad Students: I am planning a Reiki-Yoga Master Course (As a package). I’m Fusing both together.
This will include the foundation of each practice. Our Free Workshops can be used with any Reiki Yoga training package. Traditional Reiki does host rules and ethics. Its silent and within the JP Culture/Area/Training/Word of Mouth. It allows remote healing but there’s limits As practitioners and masters, we are not allowed to share certain secrets/tools. Some content is designed only for “Masters”. Some yoga are similar like the Kriya Yoga-Church (Vowed Lessons). We will review both Reiki and Yoga (Master tools) in the Course upcoming.
S9/This Week’s Focus:
* A continuation of Intuition-2 Development. We will review the Chakra System - Our temple. A misguided, misused situation lol. This will also serve Attunement later.
Thx for tuning in. Your time investment is valued. I do select topics related to our timeline and community. For those seeking upgrades or Reiki Levels. Stay tuned for our June packages. It’s for self employed/Practitioners/Coaches…
Review & Topics:
* Reiki Is Japanese Energy Healing used Globally.
* Yoga is over 5k years old from India. It hosts many styles, teacher versions, and it’s Mainstream now vs decades ago.
* Anything of the Holistic, Wellness Department can be fused together. My origins are Alternative, Complementary Medicine. In short, I call this ND. I am also a metaphysician. I learnt during the 90s New Age Era. I forget we just hit another wavy. It’s GenZ word of Mouth, their New Age Era. WHOA, History Repeats lol. We are fusing together.
* So, most of you have experienced your Spiritual Awakening. However; The journey wont be perfect. There will be some roller coaster events. The perks are: We are in a faster Spiritual Zone than the 90s. There’s more support and information available.
(See Presentation for all sections, THX AGAIN.)
SEXUALITY , UNWANTED PREGANCY AND SEXUAL ASSAULT .pptx



SEXUALITY , UNWANTED PREGANCY AND SEXUAL ASSAULT .pptxPoojaSen20 SEXUALITY AND ITS TYPES , UNWANTED PREGANCY AND SEXUAL ASSAULT
Capitol Doctoral Presentation -June 2025.pptx



Capitol Doctoral Presentation -June 2025.pptxCapitolTechU Slides from a Capitol Technology University presentation covering doctoral programs offered by the university. All programs are online, and regionally accredited. The presentation covers degree program details, tuition, financial aid and the application process.
Black and White Illustrative Group Project Presentation.pdf (1).pdf



Black and White Illustrative Group Project Presentation.pdf (1).pdfAnnasofiaUrsini mmmmmmmmmmmmmmmmmmmmmmmmmmmmmmmmmm
Ray Dalio How Countries go Broke the Big Cycle



Ray Dalio How Countries go Broke the Big CycleDadang Solihin A complete and practical understanding of the Big Debt Cycle. A much more practical understanding of how supply and demand really work compared to the conventional economic thinking. A complete and practical understanding of the Overall Big Cycle, which is driven by the Big Debt Cycle and the other major cycles, including the big political cycle within countries that changes political orders and the big geopolitical cycle that changes world orders.
Different pricelists for different shops in odoo Point of Sale in Odoo 17



Different pricelists for different shops in odoo Point of Sale in Odoo 17Celine George Price lists are a useful tool for managing the costs of your goods and services. This can assist you in working with other businesses effectively and maximizing your revenues. Additionally, you can provide your customers discounts by using price lists.
Parenting Teens: Supporting Trust, resilience and independence



Parenting Teens: Supporting Trust, resilience and independencePooky Knightsmith For more information about my speaking and training work, visit: https://www.pookyknightsmith.com/speaking/
SESSION OVERVIEW:
Parenting Teens: Supporting Trust, Resilience & Independence
The teenage years bring new challenges—for teens and for you. In this practical session, we’ll explore how to support your teen through emotional ups and downs, growing independence, and the pressures of school and social life.
You’ll gain insights into the teenage brain and why boundary-pushing is part of healthy development, along with tools to keep communication open, build trust, and support emotional resilience. Expect honest ideas, relatable examples, and space to connect with other parents.
By the end of this session, you will:
• Understand how teenage brain development affects behaviour and emotions
• Learn ways to keep communication open and supportive
• Explore tools to help your teen manage stress and bounce back from setbacks
• Reflect on how to encourage independence while staying connected
• Discover simple strategies to support emotional wellbeing
• Share experiences and ideas with other parents
How to Manage & Create a New Department in Odoo 18 Employee



How to Manage & Create a New Department in Odoo 18 EmployeeCeline George In Odoo 18's Employee module, organizing your workforce into departments enhances management and reporting efficiency. Departments are a crucial organizational unit within the Employee module.
Optimization technique in pharmaceutical product development.pptx



Optimization technique in pharmaceutical product development.pptxUrmiPrajapati3 Optimization techniques in pharmaceutical product development
How to Manage Upselling of Subscriptions in Odoo 18



How to Manage Upselling of Subscriptions in Odoo 18Celine George Subscriptions in Odoo 18 are designed to auto-renew indefinitely, ensuring continuous service for customers. However, businesses often need flexibility to adjust pricing or quantities based on evolving customer needs.
Hemiptera & Neuroptera: Insect Diversity.pptx



Hemiptera & Neuroptera: Insect Diversity.pptxArshad Shaikh *Order Hemiptera:*
Hemiptera, commonly known as true bugs, is a large and diverse order of insects that includes cicadas, aphids, leafhoppers, and shield bugs. Characterized by their piercing-sucking mouthparts, Hemiptera feed on plant sap, other insects, or small animals. Many species are significant pests, while others are beneficial predators.
*Order Neuroptera:*
Neuroptera, also known as net-winged insects, is an order of insects that includes lacewings, antlions, and owlflies. Characterized by their delicate, net-like wing venation and large, often prominent eyes, Neuroptera are predators that feed on other insects, playing an important role in biological control. Many species have aquatic larvae, adding to their ecological diversity.
Energy Balances Of Oecd Countries 2011 Iea Statistics 1st Edition Oecd



Energy Balances Of Oecd Countries 2011 Iea Statistics 1st Edition Oecdrazelitouali Energy Balances Of Oecd Countries 2011 Iea Statistics 1st Edition Oecd
Energy Balances Of Oecd Countries 2011 Iea Statistics 1st Edition Oecd
Energy Balances Of Oecd Countries 2011 Iea Statistics 1st Edition Oecd
Module 4 Presentation - Enhancing Competencies and Engagement Strategies in Y...



Module 4 Presentation - Enhancing Competencies and Engagement Strategies in Y...GeorgeDiamandis11 Enhancing Competencies and Engagement Strategies in Youth Work
Gibson "Secrets to Changing Behaviour in Scholarly Communication: A 2025 NISO...



Gibson "Secrets to Changing Behaviour in Scholarly Communication: A 2025 NISO...National Information Standards Organization (NISO)
Computer Security Lecture 2: Classical Encryption Techniques 1
- 1. Classical Encryption Techniques 1 Classical Encryption Techniques 1
- 2. Classical Encryption Techniques 1 Symmetric Encryption Substitution Techniques Caesar Cipher Monoalphabetic Cipher Playfair Cipher Hill Cipher
- 3. Classical Encryption Techniques 1 Symmetric Encryption Substitution Techniques Caesar Cipher Monoalphabetic Cipher Playfair Cipher Hill Cipher
- 5. Classical Encryption Techniques 1 Encryption algorithm: The encryption algorithm performs various substitutions and transformations on the plaintext. Secret key: The secret key is also input to the encryption algorithm. The key is a value independent of the plaintext and of the algorithm. The algorithm will produce a different output depending on the specific key being used at the time.
- 6. Classical Encryption Techniques 1 Ciphertext: This is the scrambled message produced as output. It depends on the plaintext and the secret key. Decryption algorithm: This is essentially the encryption algorithm run in reverse. It takes the ciphertext and the secret key and produces the original plaintext.
- 7. Classical Encryption Techniques 1 Symmetric-key algorithms are algorithms for cryptography that use the same cryptographic keys for both encryption of plaintext and decryption of ciphertext.
- 8. Classical Encryption Techniques 1 Symmetric Encryption Substitution Techniques Caesar Cipher Monoalphabetic Cipher Playfair Cipher Hill Cipher
- 9. Classical Encryption Techniques 1 Cipherered text 3 IODQN HDVW DWWDFN DW GDZQ A B C D E F G H I J K L M N O P Q R S T U V W X Y Z A B C A B C D E F G H I J K L M N O P Q R S T U V W X Y Z The clear text message would be encoded using a key of 3. 1 FLANK EAST ATTACK AT DAWN Shift the top scroll over by three characters (key of 3), an A becomes D, B becomes E, and so on. 2 The clear text message would be encrypted as follows using a key of 3. Clear text
- 10. Classical Encryption Techniques 1 Caesar Cipher Monoalphabetic Ciphers Playfair Cipher Hill Cipher Polyalphabetic Ciphers Vigenère Cipher Autokey Cipher Vernam Cipher
- 11. Classical Encryption Techniques 1 Symmetric Encryption Substitution Techniques Caesar Cipher Monoalphabetic Cipher Playfair Cipher Hill Cipher
- 12. Classical Encryption Techniques 1 Caesar Cipher is one of the simplest and most widely known encryption techniques.
- 16. Classical Encryption Techniques 1 PlainText = dcodex K=3 1) P=d 2) P=3 3) C=P+K mod 26=3+3 mod 26=6 mod 26 =6 4) C=g
- 17. Classical Encryption Techniques 1 PlainText = dcodex K=3 1) P=x 2) P=23 3) C=P+K mod 26=23+3 mod 26=26 mod 26= 0 4) C=a
- 18. Classical Encryption Techniques 1 P= dcodex C= gfrgha K=3
- 19. Classical Encryption Techniques 1 CipherText = gfrgha K=3 1) C=g 2) C=6 3) P=C-K mod 26=6-3 mod 26=3 4) P=d
- 20. Classical Encryption Techniques 1 CipherText = gfrgha K=3 1) C=a 2) C=0 3) P=C-K mod 26=0-3 mod 26=-3 mod 26 =23 4) P=x
- 21. Classical Encryption Techniques 1 C= gfrgha P= dcodex K=3
- 22. Classical Encryption Techniques 1 Three important characteristics of this problem enabled us to use a bruteforce cryptanalysis: The encryption and decryption algorithms are known. There are only 25 keys to try. The language of the plaintext is known and easily recognizable.
- 24. Classical Encryption Techniques 1 How to implement Caesar Cipher technique on Arabic letters?
- 25. Classical Encryption Techniques 1 Symmetric Encryption Substitution Techniques Caesar Cipher Monoalphabetic Cipher Playfair Cipher Hill Cipher
- 26. Classical Encryption Techniques 1 A monoalphabetic cipher uses fixed substitution over the entire message Random Key
- 27. Classical Encryption Techniques 1 Example: Plaintext alphabets: ABCDEFGHIJKLMNOPQRSTUVWXYZ Ciphertext alphabet: ZEBRASCDFGHIJKLMNOPQTUVWXY P= ITEMS Encoding C= FQAIP Decoding P= ITEMS
- 28. Classical Encryption Techniques 1 Relative Frequency of Letters in English Text
- 29. Classical Encryption Techniques 1 C=
- 30. Classical Encryption Techniques 1 cipher letters P and Z are the equivalents of plain letters e and t
- 31. Classical Encryption Techniques 1 Finally, The complete plaintext
- 32. Classical Encryption Techniques 1 How to implement Monoalphabetic Cipher technique on Arabic letters?
- 33. Classical Encryption Techniques 1 Symmetric Encryption Substitution Techniques Caesar Cipher Monoalphabetic Cipher Playfair Cipher Hill Cipher
- 34. Classical Encryption Techniques 1 The Playfair system was invented by Charles Wheatstone, who first described it in 1854. Used by many countries during wartime The Playfair algorithm is based on the use of a 5 x 5 matrix of letters constructed using a keyword.
- 35. Classical Encryption Techniques 1 In this case, the keyword is monarchy.
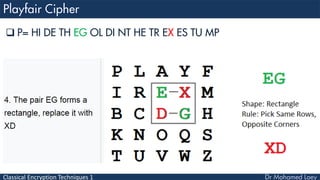
- 36. Classical Encryption Techniques 1 4 Rules: 1) If both letters are the same (or only one letter is left), add an "X" after the first letter. 2) If the letters appear on the same row of your table, replace them with the letters to their immediate right respectively
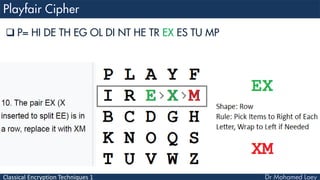
- 37. Classical Encryption Techniques 1 4 Rules: 3) If the letters appear on the same column of your table, replace them with the letters immediately below respectively 4) If the letters are not on the same row or column, replace them with the letters on the same row respectively but at the other pair of corners of the rectangle defined by the original pair.
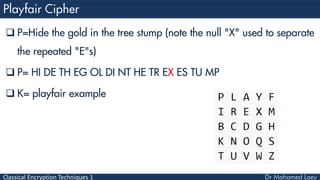
- 38. Classical Encryption Techniques 1 P=Hide the gold in the tree stump (note the null "X" used to separate the repeated "E"s) P= HI DE TH EG OL DI NT HE TR EX ES TU MP K= playfair example
- 39. Classical Encryption Techniques 1 How to build 5x5 Matrix (assuming that I and J are interchangeable), the table becomes (omitted letters in red):
- 40. Classical Encryption Techniques 1 P= HI DE TH EG OL DI NT HE TR EX ES TU MP
- 41. Classical Encryption Techniques 1 P= HI DE TH EG OL DI NT HE TR EX ES TU MP
- 42. Classical Encryption Techniques 1 P= HI DE TH EG OL DI NT HE TR EX ES TU MP
- 43. Classical Encryption Techniques 1 P= HI DE TH EG OL DI NT HE TR EX ES TU MP
- 44. Classical Encryption Techniques 1 P= HI DE TH EG OL DI NT HE TR EX ES TU MP
- 45. Classical Encryption Techniques 1 C= BM OD ZB XD NA BE KU DM UI XM MO UV IF the message "Hide the gold in the tree stump" becomes "BMODZ BXDNA BEKUD MUIXM MOUVI F"
- 46. Classical Encryption Techniques 1 Using Playfair Cipher how to decrepit the following cipher text: C= “BMODZ BXDNA BEKUD MUIXM MOUVI F” K= playfair example
- 47. Classical Encryption Techniques 1 Symmetric Encryption Substitution Techniques Caesar Cipher Monoalphabetic Cipher Playfair Cipher Hill Cipher
- 48. Classical Encryption Techniques 1 The Hill Cipher was invented by Lester S. Hill in 1929 The Hill Cipher based on linear algebra Encryption 2 x 2 Matrix Encryption 3 x 3 Matrix Encryption
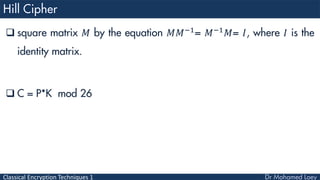
- 49. Classical Encryption Techniques 1 square matrix 𝑀 by the equation 𝑀𝑀−1 = 𝑀−1 𝑀= 𝐼, where 𝐼 is the identity matrix. C = P*K mod 26
- 51. Classical Encryption Techniques 1 Example of Key 2 x 2 𝐾 = 𝐻 𝐼 𝐿 𝐿 = 7 8 11 11 plaintext message "short example“ 𝑃= short example 𝑃 = 𝑆 ℎ 𝑜 𝑟 𝑡 𝑒 𝑥 𝑎 𝑚 𝑝 𝑙 𝑒 = 18 7 14 17 19 4 23 0 12 15 11 4
- 52. Classical Encryption Techniques 1 𝑃 = 𝑆 ℎ 𝑜 𝑟 𝑡 𝑒 𝑥 𝑎 𝑚 𝑝 𝑙 𝑒 = 18 7 14 17 19 4 23 0 12 15 11 4 𝐶 = 𝐾 ∗ 𝑃 𝑚𝑜𝑑 26 𝑘0 𝑘1 𝑘2 𝑘3 ∗ 𝑝0 𝑝1 = 𝑘0 ∗ 𝑝0 + 𝑘1 ∗ 𝑝1 𝑘2 ∗ 𝑝0 + 𝑘3 ∗ 𝑝1 7 8 11 11 ∗ 18 7 = 7 ∗ 18 + 8 ∗ 7 11 ∗ 18 + 11 ∗ 7 = 182 275 𝐶 = 182 275 𝑚𝑜𝑑 26 = 0 15 = 𝑎 𝑝
- 53. Classical Encryption Techniques 1 𝑃 = 𝑆 ℎ 𝑜 𝑟 𝑡 𝑒 𝑥 𝑎 𝑚 𝑝 𝑙 𝑒 = 18 7 14 17 19 4 23 0 12 15 11 4
- 54. Classical Encryption Techniques 1 𝑃 = 𝑆 ℎ 𝑜 𝑟 𝑡 𝑒 𝑥 𝑎 𝑚 𝑝 𝑙 𝑒 = 18 7 14 17 19 4 23 0 12 15 11 4
- 55. Classical Encryption Techniques 1 𝑃 = 𝑆 ℎ 𝑜 𝑟 𝑡 𝑒 𝑥 𝑎 𝑚 𝑝 𝑙 𝑒 = 18 7 14 17 19 4 23 0 12 15 11 4
- 56. Classical Encryption Techniques 1 𝑃 = 𝑆 ℎ 𝑜 𝑟 𝑡 𝑒 𝑥 𝑎 𝑚 𝑝 𝑙 𝑒 = 18 7 14 17 19 4 23 0 12 15 11 4
- 57. Classical Encryption Techniques 1 𝑃 = 𝑆 ℎ 𝑜 𝑟 𝑡 𝑒 𝑥 𝑎 𝑚 𝑝 𝑙 𝑒 = 18 7 14 17 19 4 23 0 12 15 11 4
- 58. Classical Encryption Techniques 1 𝐶 = 𝑎 𝑝 𝑎 𝑑 𝑗 𝑡 𝑓 𝑡 𝑤 𝑙 𝑓 𝑗 This gives us a final ciphertext of "APADJ TFTWLFJ"
- 59. Classical Encryption Techniques 1 𝐶 = 𝑎 𝑝 𝑎 𝑑 𝑗 𝑡 𝑓 𝑡 𝑤 𝑙 𝑓 𝑗 This gives us a final ciphertext of "APADJ TFTWLFJ“ 𝐾 = 𝐻 𝐼 𝐿 𝐿 = 7 8 11 11 We want to find 𝐾−1
- 60. Classical Encryption Techniques 1 𝑆𝑡𝑒𝑝 1 − 𝐹𝑖𝑛𝑑 𝑡ℎ𝑒 𝑀𝑢𝑙𝑡𝑖𝑝𝑙𝑖𝑐𝑎𝑡𝑖𝑣𝑒 𝐼𝑛𝑣𝑒𝑟𝑠𝑒 𝑜𝑓 𝑡ℎ𝑒 𝐷𝑒𝑡𝑒𝑟𝑚𝑖𝑛𝑎𝑛𝑡 𝐷 𝐾 = 7 ∗ 11 − 8 ∗ 11 = −11 𝑚𝑜𝑑 26 = 15 𝐷𝐷−1 = 1 𝑚𝑜𝑑 26 = 15 ∗ 𝐷−1 15 ∗ 𝐷−1 𝑚𝑜𝑑 26 = 1 Try and Test 1 𝑚𝑜𝑑 26 = 105 105 mod 26 =1 𝐷−1 = 7
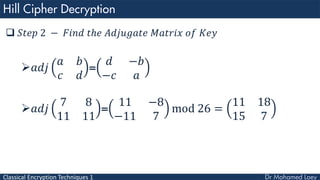
- 61. Classical Encryption Techniques 1 𝑆𝑡𝑒𝑝 2 − 𝐹𝑖𝑛𝑑 𝑡ℎ𝑒 𝐴𝑑𝑗𝑢𝑔𝑎𝑡𝑒 𝑀𝑎𝑡𝑟𝑖𝑥 𝑜𝑓 𝐾𝑒𝑦 𝑎𝑑𝑗 𝑎 𝑏 𝑐 𝑑 = 𝑑 −𝑏 −𝑐 𝑎 𝑎𝑑𝑗 7 8 11 11 = 11 −8 −11 7 mod 26 = 11 18 15 7
- 62. Classical Encryption Techniques 1 𝑆𝑡𝑒𝑝 3 𝑀𝑢𝑙𝑡𝑖𝑝𝑙𝑦 𝑡ℎ𝑒 𝑀𝑢𝑙𝑡𝑖𝑝𝑙𝑖𝑐𝑎𝑡𝑖𝑣𝑒 𝐼𝑛𝑣𝑒𝑟𝑠𝑒 𝑜𝑓 𝑡ℎ𝑒 𝐷𝑒𝑡𝑒𝑟𝑚𝑖𝑛𝑎𝑛𝑡 𝑏𝑦 𝑡ℎ𝑒 𝐴𝑑𝑗𝑢𝑔𝑎𝑡𝑒 𝑀𝑎𝑡𝑟𝑖𝑥 7 ∗ 11 18 15 7 = 77 126 105 49 𝑚𝑜𝑑 26 = 25 22 1 23 = 𝐾−1
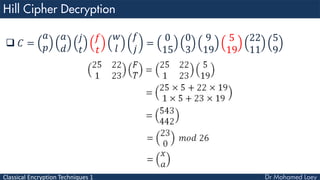
- 63. Classical Encryption Techniques 1 𝐶 = 𝑎 𝑝 𝑎 𝑑 𝑗 𝑡 𝑓 𝑡 𝑤 𝑙 𝑓 𝑗 = 0 15 0 3 9 19 5 19 22 11 5 9
- 64. Classical Encryption Techniques 1 𝐶 = 𝑎 𝑝 𝑎 𝑑 𝑗 𝑡 𝑓 𝑡 𝑤 𝑙 𝑓 𝑗 = 0 15 0 3 9 19 5 19 22 11 5 9
- 65. Classical Encryption Techniques 1 𝐶 = 𝑎 𝑝 𝑎 𝑑 𝑗 𝑡 𝑓 𝑡 𝑤 𝑙 𝑓 𝑗 = 0 15 0 3 9 19 5 19 22 11 5 9
- 66. Classical Encryption Techniques 1 𝐶 = 𝑎 𝑝 𝑎 𝑑 𝑗 𝑡 𝑓 𝑡 𝑤 𝑙 𝑓 𝑗 = 0 15 0 3 9 19 5 19 22 11 5 9
- 67. Classical Encryption Techniques 1 𝐶 = 𝑎 𝑝 𝑎 𝑑 𝑗 𝑡 𝑓 𝑡 𝑤 𝑙 𝑓 𝑗 = 0 15 0 3 9 19 5 19 22 11 5 9
- 68. Classical Encryption Techniques 1 𝐶 = 𝑎 𝑝 𝑎 𝑑 𝑗 𝑡 𝑓 𝑡 𝑤 𝑙 𝑓 𝑗 = 0 15 0 3 9 19 5 19 22 11 5 9
- 69. Classical Encryption Techniques 1 Using Hill Cipher how to implement 3x3 matrix encryption ? The key for a hill cipher is a matrix e.g. 𝒌 = 2 4 5 9 2 1 3 17 7 and message= ATTACK AT DAWN
- 70. Classical Encryption Techniques 1 Use MS Word Send me mail to [email protected] with email subject “ Classical Encryption Techniques 1 “ Put your name on Arabic with department and section on word and email body Finally, press Send Deadline Next Lecture
- 71. Classical Encryption Techniques 1 facebook.com/mloey [email protected] twitter.com/mloey linkedin.com/in/mloey [email protected] mloey.github.io
- 72. Classical Encryption Techniques 1 www.YourCompany.com © 2020 Companyname PowerPoint Business Theme. All Rights Reserved. THANKS FOR YOUR TIME












