Computer security module 4
- 2. Network Security Kerberos trusted key server system from MIT Symmetric encryption using no public keys provides centralised private-key third-party authentication in a distributed network allows users access to services distributed through network without needing to trust all workstations rather all trust a central authentication server two versions in use: 4 & 5
- 3. Kerberos Requirements Secure: should be strong enough that a potential opponent does not find it to be the weak link. Reliable: should be highly reliable and should employ a distributed server architecture with one system able to back up another. Transparent: the user should not be aware that authentication is taking place beyond the requirement to enter a password. Scalable: should be capable of supporting large numbers of clients and servers.
- 4. Kerberos v4 Overview a basic third-party authentication scheme have an Authentication Server (AS) that knows the passwords of all users and stores these in a centralized database. shares a unique secret key with each server. creates a ticket that contains the user’s ID and network address and the server’s ID. have a Ticket Granting server (TGS) issues tickets to users who have been authenticated to AS
- 5. Kerberos v4 Dialogue 1. The client requests a ticket-granting ticket by sending its user’s ID to the AS, together with the TGS ID, indicating a request to use the TGS service. 2. The AS responds with a ticket that is encrypted with a key that is derived from the user’s password (Kc ), which is already stored at the AS. When this response arrives at the client, the client users his password, generates the key, and attempts to decrypt the incoming message. If the password is correct, the ticket is successfully recovered. 3. The client requests a service-granting ticket by transmitting a message to the TGS containing the user’s ID, the ID of the desired service, and the ticket- granting ticket.
- 6. 4. The TGS decrypts the incoming ticket using a key shared only by the AS and the TGS ( Ktgs) and it checks to make sure that the lifetime has not expired. Then it compares the user ID and network address with the incoming information to authenticate the user. If the user is permitted access to the server V, the TGS issues a ticket to grant access to the requested service. 5. The client requests access to a service by transmitting a message to the server containing the user’s ID and the service-granting ticket. The server authenticates by using the contents of the ticket.
- 8. Kerberos Version 4 Simplified approach Client asks authentication server for ticket AS grants ticket Client sends ticket to server Weaknesses Big load on AS (Provide secondary ticket-granting servers) Repeated password entry (Password to AS seldom, tickets from TGS when needed, based on AS authentication)
- 9. Kerberos Realms a Kerberos environment consists of: a Kerberos server a number of clients, all registered with server application servers, sharing keys with server this is termed a realm typically a single administrative domain if have multiple realms, their Kerberos servers must share keys and trust
- 10. Difference Between Version 4 and 5 Encryption system dependence (V.4 DES) Internet protocol dependence Message byte ordering Ticket lifetime Authentication forwarding Interrealm authentication
- 11. X.509 Authentication Service Distributed set of servers that maintains a database about users. Provides a certificate that contains the public key of a user and is signed with the private key of a CA defines framework for authentication services directory may store public-key certificates with public key of user signed by certification authority also defines authentication protocols uses public-key crypto & digital signatures Available versions are 1,2,and 3
- 12. version (1, 2, or 3) certificate serial number (unique within CA) signature algorithm identifier issuer name (CA) period of validity (from - to dates) subject name (name of owner) subject public-key info (algorithm, parameters, key) issuer unique identifier subject unique identifier extension fields signature (of hash of all fields in certificate)
- 13. Obtaining a Certificate any user with access to CA can get any certificate from it only the CA can modify a certificate The standard uses the following notation to define a certificate CA<<A>> = CA {V, SN, AI, CA, UCA, A, UA, Ap, TA} notation CA<<A>> denotes certificate for A signed by CA V=version of the certificate SN=serial number of the certificate AI =identifier of the algorithm used to sign the certificate CA =name of certificate authority UCA =optional unique identifier of the CA A=name of user A UA=optional unique identifier of the user A Ap=public key of user A TA=period of validity of the certificate
- 14. CA Hierarchy if both users share a common CA then they are assumed to know its public key each CA has certificates for clients (forward) and parent (backward) each client trusts parents certificates enable verification of any certificate from one CA by users of all other CAs in hierarchy
- 15. Certificate Revocation certificates have a period of validity may need to revoke before expiry, CA’s maintain list of revoked certificates the Certificate Revocation List (CRL) users should check certificates with CA’s CRL
- 16. Authentication Procedures X.509 includes three alternative authentication procedures: i. One-Way Authentication ii. Two-Way Authentication iii. Three-Way Authentication all use public-key signatures
- 17. One-Way Authentication 1 message ( A->B) used to establish the identity of A and that message is from A message was intended for B integrity & originality of message message must include timestamp, nonce, B's identity and is signed by A may include additional info for B eg session key
- 18. Two-Way Authentication 2 messages (A->B, B->A) which also establishes in addition: the identity of B and that reply is from B that reply is intended for A integrity & originality of reply reply includes original nonce from A, also timestamp and nonce from B may include additional info for A
- 19. Three-Way Authentication 3 messages (A->B, B->A, A->B) has reply from A back to B containing signed copy of nonce from B means that timestamps need not be checked or relied upon
- 20. X.509 Version 3 has been recognised that additional information is needed in a certificate email/URL, policy details, usage constraints rather than explicitly naming new fields defined a general extension method extensions consist of: extension identifier criticality indicator extension value
- 21. Certificate Extensions key and policy information convey info about subject & issuer keys, plus indicators of certificate policy certificate subject and issuer attributes support alternative names, in alternative formats for certificate subject and/or issuer certificate path constraints allow constraints on use of certificates by other CA’s
- 22. Public Key Infrastructure as the set of hardware, software, people, policies, and procedures needed to create, manage, store, distribute, and revoke digital certificates based on asymmetric cryptography. enable secure, convenient, and efficient acquisition of public keys.
- 24. End entity: used to denote end users, devices (e.g., servers, routers), or any other entity that can be identified in the subject field of a public key certificate. End entities typically consume and/or support PKI-related services. Certificate authority (CA): The issuer of certificates and (usually) certificate revocation lists (CRLs). Registration authority (RA): An optional component that can assume a number of administrative functions from the CA. Then RA is often associated with the End Entity registration process. CRL issuer: An optional component that a CA can delegate to publish CRLs. Repository: A generic term used to denote any method for storing certificates and CRLs so that they can be retrieved by End Entities.
- 25. Email Security email is one of the most widely used and regarded network services Email Security Enhancements 1. confidentiality protection from disclosure 2. authentication of sender of message 3. message integrity protection from modification 4. non-repudiation of origin protection from denial by sender
- 26. Pretty Good Privacy (PGP) provides a confidentiality and authentication service that can be used for e-mail and file storage applications. developed by Phil Zimmermann Based on known algorithms such as RSA integrated into a single program It is availiable free on a variety of platforms.(Unix, PC, Macintosh and other systems ) originally free, now also have commercial versions available For personal email security
- 27. Operational Description Consist of four services: Authentication Confidentiality Compression E-mail compatibility
- 28. Authentication 1. sender creates message 2. use SHA-1 to generate 160-bit hash of message 3. signed hash with RSA using sender's private key is attached to message 4. receiver uses RSA with sender's public key to decrypt and recover hash code 5. receiver verifies received message using hash of it and compares with decrypted hash code
- 29. Confidentiality 1. sender generates message and 128-bit random number as session key for it 2. encrypt message using 3DES or other methods in CBC mode with session key 3. session key encrypted using RSA with recipient's public key, & attached to message 4. receiver uses RSA with private key to decrypt and recover session key 5. session key is used to decrypt message
- 30. Compression by default PGP compresses message after signing but before encrypting so can store uncompressed message & signature for later verification Message encryption is after compression To strengthen cryptographic security uses ZIP compression algorithm
- 31. Email Compatibility when using PGP will have binary data to send (encrypted message etc) however email was designed only for text hence PGP must encode raw binary data into printable ASCII characters uses radix-64 algorithm maps 3 bytes to 4 printable characters also appends a CRC PGP also segments messages if too big
- 33. Cryptographic Keys PGP uses four types of keys Session keys Public keys Private Keys Passphrase keys
- 34. Session Keys need a session key for each message of varying sizes: 56-bit DES, 168-bit Triple-DES uses random inputs taken from previous uses and from keystroke timing of user Public & Private Keys PGP use: public keys for encrypting session keys / verifying signatures. private keys for decrypting session keys / creating signatures. Passphrase Keys A passphrase is a longer version of a password, and in theory, a more secure one. Typically composed of multiple words,
- 36. PGP Key Rings each PGP user has a pair of key rings: public-key ring contains all the public-keys of other PGP users known to this user, indexed by key ID private-key ring contains the public/private key pair(s) for this user, indexed by key ID & encrypted keyed from a hashed passphrase
- 37. EP=public-key encryption DP=public-key decryption EC=symmetric encryption DC = symmetric decryption H=hash function ||=concatenation Z=compression using ZIP algorithm PGP Message Generation
- 39. The sending PGP entity performs the following steps: Signs the message: PGP gets sender’s private key from key ring using its user id as an index. PGP prompts user for passphrase to decrypt private key. PGP constructs the signature component of the message. Encrypts the message: PGP generates a session key and encrypts the message. PGP retrieves the receiver public key from the key ring using its user id as an index. PGP constructs session component of message
- 41. The receiving PGP entity performs the following steps: Decrypting the message: PGP get private key from private-key ring using Key ID field in session key component of message as an index. PGP prompts user for passphrase to decrypt private key. PGP recovers the session key and decrypts the message. Authenticating the message: PGP retrieves the sender’s public key from the public-key ring using the Key ID field in the signature key component as index. PGP recovers the transmitted message digest. PGP computes the message for the received message and compares it to the transmitted version for authentication.
- 42. PGP Key Management in PGP every user is own CA can sign keys for users they know directly PGP adopts a trust model called the web of trust. No centralised authority means Individuals sign one another’s public keys, these “certificates” are stored along with keys in key rings. PGP computes a trust level for each public key in key ring. Trust levels for public keys dependent on: Number of signatures on the key; Trust level assigned to each of those signatures. Trust levels recomputed from time to time.
- 43. S/MIME (Secure/Multipurpose Internet Mail Extensions) security enhancement to MIME email emerged as the industry standard original Internet RFC822 email was text only MIME provided support for varying content types and multi-part messages with encoding of binary data to textual form S/MIME added security enhancements have S/MIME support in many mail agents eg MS Outlook, Mozilla, Mac Mail etc
- 44. S/MIME Functions Enveloped Data: Encrypted content and encrypted session keys for recipients. Signed Data: Message Digest encrypted with private key of “signer.” Clear-Signed Data: Signed but not encrypted. Signed and Enveloped Data: Various orderings for encrypting and signing
- 45. Header fields in MIME MIME-Version: identifies the version Content-Type: Describes the data contained in the body (application/word) Content-Transfer-Encoding: How message has been encoded (radix-64) Content-ID: Unique identifying character string. Content Description: Needed when content is not readable text (e.g.mpeg)
- 46. S/MIME Cryptographic Algorithms digital signatures: DSS & RSA hash functions: SHA-1 & MD5 session key encryption: RSA message encryption: AES, Triple-DES and others MAC: HMAC with SHA-1
- 47. S/MIME Certificate Processing S/MIME uses X.509 v3 certificates uses a hybrid of X.509 CA hierarchy & PGP’s web of trust for key management each client has a list of trusted CA’s certificates and own public/private key pairs & certificates certificates must be signed by trusted CA’s
- 48. S/MIME – User Agent Role Key generation Generating key with RSA Registration Register a user’s public key with a certification authority Certificate storage and retrieval Access to a local list of certificates in order to verify incoming signatures and encrypt outgoing
- 49. Enhanced Security Services Signed receipts: the recipient signs the entire original message plus original (sender's) signature and appends the new signature to form a new S/MIME message. Security labels: used for access control, by indicating which users are permitted access to an object. Secure mailing lists
- 50. IP Security Internet Protocol security (IPSec) is a suite of cryptography based protection services and security protocols. provides authentication confidentiality key management applicable to use over LANs, WANs, & Internet
- 51. Applications of IPSec Secure branch office connectivity over the Internet Secure remote access over the Internet Establishing extranet and intranet connectivity with partners Enhancing electronic commerce security Benefits of IPSec in a firewall/router provides strong security to all traffic in a firewall/router is resistant to bypass transparent to applications and end users provide security for individual users
- 52. IP Security Architecture Architecture RFC4301 Security Architecture for Internet Protocol have two security header extensions: Authentication Header (AH) Encapsulating Security Payload (ESP) Contains 1. documents that define IPSec. 2. IPSec services 3. concept of security association.
- 53. IPSec Documents The IPSec specification consists of numerous documents and is divided into seven groups, 1. Architecture: Covers the general concepts, security requirements, definitions, and mechanisms defining IPSec technology. 2. Encapsulating Security Payload (ESP): Covers the packet format and general issues related to the use of the ESP for packet encryption and authentication. 3. Authentication Header (AH): Covers the packet format and general issues related to the use of AH for packet authentication. 4. Encryption Algorithm: A set of documents that describe how various encryption algorithms are used for ESP.
- 54. 5. Authentication Algorithm: A set of documents that describe how various authentication algorithms are used 6. Key Management: Documents that describe key management schemes. 7. Domain of Interpretation (DOI): include identifiers for approved encryption and authentication algorithms, as well as operational parameters such as key lifetime
- 55. IPSec Services Access control Data origin authentication Rejection of replayed packets Confidentiality (encryption) Limited traffic flow confidentiality
- 56. Security Associations a one-way relationship between sender & receiver that affords security for traffic flow defined by 3 parameters: i. Security Parameters Index (SPI): A bit string assigned to SA to enable the receiving system to select the SA under which a received packet will be processed. ii. IP Destination Address:unicast addresses are allowed iii. Security Protocol Identifier:indicates whether the association is an AH or ESP security association. has a number of other parameters seq no,lifetime etc
- 57. Authentication Header (AH) provides support for data integrity & authentication of IP packets Authentication based on use of a MAC(HMAC)
- 58. Next Header (8 bits): Identifies the type of header immediately following this header Payload Length (8 bits): Length of Authentication Header Reserved (16 bits): For future use Security Parameters Index (32 bits): Identifies a security association Sequence Number (32 bits): A monotonically increasing counter value for preventing attacks Authentication Data (variable): A variable-length field
- 59. Encapsulating Security Payload (ESP) provides message content confidentiality & limited traffic flow confidentiality can use a variety of encryption & authentication algorithms
- 60. • Security Parameters Index (32 bits): Identifies a security association • Sequence Number (32 bits): A monotonically increasing counter value; this provides an anti-replay function • Payload Data (variable): This is a transport-level segment (transport mode) or IP packet (tunnel mode) that is protected by encryption • Padding (0–255 bytes): for various reasons • Pad Length (8 bits): Indicates the number of pad bytes • Next Header (8 bits): Identifies the type of data contained in the payload data field by identifying the first header in that payload • Authentication Data (variable): A variable-length field that contains the Integrity Check Value
- 61. Transport and Tunnel Modes Transport Mode(end-to-end) • Provides protection primarily for upper-layer protocol payloads • used for end-to-end communication between two hosts. Tunnel Mode(end-to-intermediate) • provides protection to the entire IP packet • add new header for next hop • no routers on way can examine inner IP header • is used when one or both ends of an SA are a security gateway, such as a firewall or router that implements IPSec
- 63. Combining Security Associations SA’s can implement either AH or ESP to implement both need to combine SA’s form a security association bundle combined by transport adjacency: more than one security protocol on same IP packet, without invoking tunneling iterated tunneling: application of multiple layers of security protocols effected through IP tunneling Mainly four cases of SA association
- 64. The cases are: i. Case 1 security is provided between end systems that implement IPSec. ii. Case 2 security is provided only between gateways (routers, firewalls , etc.) and no hosts implement IPSec. iii. Case 3 builds on Case 2 by adding end-to-end security . iv. Case 4 provides support for a remote host that uses the Internet to reach an organization’s firewall and then to gain access to some server or workstation behind the firewall. Only tunnel mode is required between the remote host and the firewall.
- 66. Key Management handles key generation & distribution of secret keys typically need 2 pairs of keys 2 per direction(Transmit and Receive) for AH & ESP Two types of key management i. manual key management System admin manually configures every system ii. automated key management automated system for on demand creation of keys for large systems
- 67. Web Security SSL (Secure Socket Layer) is a method for providing security for web based applications transport layer security service subsequently became Internet standard known as TLS (Transport Layer Security) uses TCP to provide a reliable end-to-end service SSL has two layers of protocols
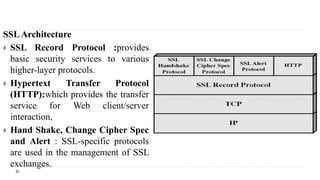
- 68. SSLArchitecture SSL Record Protocol :provides basic security services to various higher-layer protocols. Hypertext Transfer Protocol (HTTP):which provides the transfer service for Web client/server interaction, Hand Shake, Change Cipher Spec and Alert : SSL-specific protocols are used in the management of SSL exchanges.
- 69. Two important SSL concepts 1. SSL connection peer-to-peer, communications link associated with one SSL session 2. SSL session an association between client & server created by the Handshake Protocol may be shared by multiple SSL connections
- 70. SSL Record Protocol Services This protocol provides two services for SSL connections: 1. Confidentiality - using conventional encryption. 2. Message Integrity - using a Message Authentication Code (MAC). It takes an application message to be transmitted and fragments it into manageable blocks. These blocks are then optionally compressed which must be lossless and may not increase the content length by more than 1024 bytes. A message authentication code is then computed over the compressed data using a shared secret key. This is then appended to the compressed (or plaintext) block.
- 71. SSL Record Protocol Operation The compressed message plus MAC are then encrypted using symmetric encryption. The final step is to prepend a header
- 72. SSL Change Cipher Spec Protocol This consists of a single message which consists of a single byte with the value 1. This is used to cause the pending state to be copied into the current state which updates the cipher suite to be used on this connection. SSLAlert Protocol conveys SSL-related alerts to peer entity Consists of two bytes fatal or warning If the level is fatal SSL immediately terminates the connection. The second byte contains a code that indicates the specific alert
- 73. SSL Handshake Protocol This protocol is used before any application data is sent. allows server & client to: authenticate each other to negotiate encryption & MAC algorithms to negotiate cryptographic keys to be used Uses a series of messages exchanged by the client and server during 4 phases, 1. Establish Security Capabilities 2. Server Authentication and Key Exchange 3. Client Authentication and Key Exchange 4. Finish
- 75. System Security Intruders can identify classes of intruders: Masquerader: An individual who is not authorized to use the computer Misfeasor: A legitimate user who accesses unauthorized data, programs, or resources clandestine user: An individual who seizes supervisory control of the system and uses this control to evade auditing and access controls or to suppress audit collection (either) Intruder attacks range from the benign (simply exploring net to see what is there); to the serious (who attempt to read privileged data, perform unauthorized modifications, or disrupt system)
- 76. Intrusion Techniques aim to gain access and/or increase privileges on a system basic attack methodology target acquisition and information gathering initial access privilege escalation covering tracks key goal often is to acquire passwords so then exercise access rights of owner
- 77. Password Guessing one of the most common attacks attacker knows a login (from email/web page etc) then attempts to guess password for it defaults, short passwords, common word searches user info (variations on names, birthday, phone, common words/interests) exhaustively searching all possible passwords
- 78. Password Capture another attack involves password capture watching over shoulder as password is entered using a trojan horse program to collect monitoring an insecure network login eg. telnet, FTP, web, email extracting recorded info after successful login (web history/cache, last number dialed etc)
- 79. Intrusion Detection intrusion detection is the one method of system defense which aims to detect intrusions so can: i. block access & minimize damage if detected quickly; ii. act as deterrent given chance of being caught; iii. can collect info on intruders to improve future security.
- 80. Approaches to Intrusion Detection 1. Statistical anomaly detection 2. Rule based detection 1. Statistical anomaly detection: collect data relating to the behavior of legitimate users, then use statistical tests to determine whether new behavior is legitimate user behavior or not. a. Threshold detection: b. Profile based:
- 81. threshold detection define thresholds, independent of user, for the frequency of occurrence of events. count occurrences of specific event over time if exceed reasonable value assume intrusion profile based develop profile of activity of each user and use to detect changes in the behavior characterize past behavior of users detect significant deviations from this profile usually multi-parameter
- 82. 2. Rule-based detection: attempt to define a set of rules used to decide if given behavior is an intruder a. Anomaly detection: analyze historical audit records to identify usage patterns & auto-generate rules for them then observe current behavior & match against rules to see if conforms like statistical anomaly detection does not require prior knowledge of security flaws
- 83. b. Penetration identification: expert system approach that searches for suspicious behavior uses expert systems technology with rules identifying known penetration, weakness patterns, or suspicious behavior compare audit records or states against rules rules usually machine & O/S specific rules are generated by experts who interview & codify knowledge of security admins quality depends on how well this is done
- 84. Audit Records fundamental tool for intrusion detection Basically, two plans are used: • Native audit records: Virtually all main O/S’s include accounting software that collects information on user activity, • Detection-specific audit records: implement collection facility to generates custom audit records with desired info, advantage is it can be vendor independent and portable, disadvantage is extra overhead involved
- 85. Distributed Intrusion Detection may need to deal with different audit record formats One or more nodes in the network will serve as collection and analysis points for the data, which must be securely transmitted to them Either a centralized (single point, easier but bottleneck) or decentralized (multiple centers must coordinate) architecture can be used.
- 86. Host agent module: audit collection module operating as a background process on a monitored system LAN monitor agent module: like a host agent module except it analyzes LAN traffic Central manager module: Receives reports from LAN monitor and host agents and processes and correlates these reports to detect intrusion
- 87. Agent Implementation The agent captures each native O/S audit record, & applies a filter that retains only records of security interest. These records are then reformatted into a standardized format (HAR). Then a template-driven logic module analyzes the records for suspicious activity. When suspicious activity is detected, an alert is sent to the central manager. The central manager includes an expert system that can draw inferences from received data. The manager may also query individual systems for copies of HARs to correlate with those from other agents.
- 89. Password Management front-line defense against intruders users supply both: login – determines privileges of that user password – to identify them passwords often stored encrypted Unix uses multiple DES (variant with salt) more recent systems use crypto hash function should protect password file on system
- 90. Managing Passwords - Education can use policies and good user education educate on importance of good passwords give guidelines for good passwords minimum length (>6) require a mix of upper & lower case letters, numbers, punctuation not dictionary words
- 91. Computer Generated let computer create passwords if random likely not memorisable, so will be written down have history of poor user acceptance FIPS PUB 181 one of best generators has both description & sample code generates words from concatenating random pronounceable syllables
- 92. Reactive Checking reactively run password guessing tools cracked passwords are disabled but is resource intensive bad passwords are vulnerable till found
- 93. Proactive Checking most promising approach to improving password security allow users to select own password but have system verify it is acceptable simple rule enforcement compare against dictionary of bad passwords use algorithmic (markov model or bloom filter) to detect poor choices
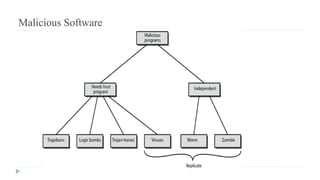
- 95. Backdoor or Trapdoor Uses secret entry point into a program allows those who know access bypassing usual security procedures have been commonly used by developers a threat when left in production programs allowing exploited by attackers very hard to block in O/S requires good s/w development & update
- 96. Logic Bomb one of oldest types of malicious software code embedded in legitimate program activated when specified conditions met eg presence/absence of some file particular date/time particular user when triggered typically damage system modify/delete files/disks, halt machine, etc
- 97. Trojan Horse A Trojan horse is a useful, or apparently useful, program or command procedure (eg game, utility, s/w upgrade etc) containing hidden code that performs some unwanted or harmful function that an unauthorized user could not accomplish directly. Commonly used to make files readable, propagate a virus or worm, or simply to destroy data.
- 98. Zombie program which secretly takes over another networked computer then uses it to indirectly launch attacks used in denial-of-service attacks, Typically zombies exploit known flaws in networked computer
- 99. Viruses a piece of self-replicating code attached to some other code both propagates itself & carries a payload (code to make copies of itself) Once a virus is executing, it can perform any function, such as erasing files and programs.
- 100. Virus Operation virus phases: dormant – virus is idle, waiting for trigger event. Not all viruses have this stage propagation – virus places a copy of itself into other programs / system areas triggering – virus is activated by some trigger event to perform intended function execution – desired function (which may be harmless or destructive) is performed
- 101. Virus Structure components: infection mechanism - enables replication trigger - event that makes payload activate payload - what it does, malicious or benign Virus can be prepended / postpended / embedded when infected program invoked, executes virus code then original program code can block initial infection (difficult) or propagation (with access controls)
- 103. The virus code (V) is prepended to infected programs (assuming the entry point is the first line of the program). The first line of code jumps to the main virus program. The second line is a special marker for infected programs. The main virus program first seeks out uninfected executable files and infects them. Then it may perform some action, Finally, the virus transfers control to the original program. If the infection phase of the program is reasonably rapid, a user is unlikely to notice any difference between the execution of an infected and uninfected program. This type of virus can be detected because the length of the program changes. More sophisticated variants attempt to hide their presence better, by for example, compressing the original program.
- 104. Types of Viruses can classify on basis of how they attack i. parasitic virus : traditional and still most common form of virus, it attaches itself to executable files and replicates when the infected program is executed ii. memory-resident virus: Lodges in main memory as part of a resident system program, and infects every program that executes iii. boot sector virus:Infects a master boot record and spreads when a system is booted from the disk containing the virus iv. Stealth: a virus explicitly designed to hide itself from detection by antivirus software
- 105. v. polymorphic virus : mutates with every infection, making detection by the “signature "of the virus impossible. vi. metamorphic virus : mutates with every infection, rewriting itself completely at each iteration changing behavior and/or appearance, increasing the difficulty of detection.
- 106. Macro Virus macro code attached to some data file platform independent infect documents easily spread exploit macro capability of office apps executable program embedded in office doc is a major source of new viral infection
- 107. Email Virus spread using email with attachment containing a macro virus e.g. Melissa exploits MS Word macro in attached doc if attachment opened, macro activates sends email to all on users address list and does local damage usually targeted at Microsoft Outlook mail agent & Word/Excel documents
- 108. Worms replicating but not infecting program typically spreads over a network by using users distributed privileges or by exploiting system vulnerabilities widely used by hackers to create zombie PC's, subsequently used for further attacks, esp DoS major issue is lack of security
- 109. Worm Operation worm phases like those of viruses: dormant propagation search for other systems to infect establish connection to target remote system replicate self onto remote system triggering execution
- 110. Virus Countermeasures prevention - ideal solution but difficult realistically need: detection identification removal if detect but can’t identify or remove, must discard and replace infected program
- 111. Anti-Virus Software first-generation scanner uses virus signature to identify virus or change in length of programs second-generation uses heuristic rules to spot viral infection or uses crypto hash of program to spot changes third-generation memory-resident programs identify virus by actions fourth-generation packages with a variety of antivirus techniques eg scanning & activity traps, access-controls
- 112. Advanced Anti-Virus Techniques generic decryption use CPU simulator to check program signature & behavior before actually running it Ex: behavior blocking software digital immune system (IBM) general purpose emulation & virus detection any virus entering is captured, analyzed, detection/shielding created for it, removed
- 113. Behavior-Blocking Software integrated with host O/S monitors program behavior in real-time eg file access, disk format, executable mods, system settings changes, network access for possibly malicious actions if detected can block, terminate, or seek ok has advantage over scanners but malicious code runs before detection
- 116. 1. A monitoring program on each PC uses a variety of heuristics based on system behavior, suspicious changes to programs, or family signature to infer that a virus may be present, & forwards infected programs to an administrative machine 2. The administrative machine encrypts the sample and sends it to a central virus analysis machine 3. This machine creates an environment in which the infected program can be safely run for analysis to produces a prescription for identifying and removing the virus 4. The resulting prescription is sent back to the administrative machine 5. The administrative machine forwards the prescription to the infected client 6. The prescription is also forwarded to other clients in the organization 7. Subscribers around the world receive regular antivirus updates that protect them from the new virus.
- 117. Distributed Denial of Service Attacks (DDoS) DDoS Countermeasures three broad lines of defense: 1. attack prevention & preemption (before) 2. attack detection & filtering (during) 3. attack source traceback & ident (after)
- 118. a choke point of control and monitoring interconnects networks with differing trust imposes restrictions on network services only authorized traffic is allowed auditing and controlling access provide NAT & usage monitoring Firewall
- 119. Firewall Limitations cannot protect from attacks bypassing it cannot protect against internal threats cannot protect against transfer of all virus infected programs or files Types Of Firewalls three common types 1. packet filters 2. application-level gateways 3. circuit-level gateways
- 120. Firewalls – Packet Filters A packet-filtering router applies a set of rules to each incoming and outgoing IP packet to forward or discard the packet. Filtering rules are based on information contained in a network packet such as source & destination IP addresses, ports, transport protocol & interface. Some advantages are simplicity, transparency & speed. If there is no match to any rule, then one of two default policies are applied: • discard packet, conservative policy • forward packet, permissive policy
- 122. Firewalls - Application Level Gateway (or Proxy) have application specific gateway / proxy has full access to protocol user requests service from proxy proxy validates request as legal then actions request and returns result to user can log / audit traffic at application level need separate proxies for each service some services naturally support proxying others are more problematic
- 123. Firewalls - Circuit Level Gateway relays two TCP connections, i. between itself and an inside TCP user ii. between itself and a TCP user on an outside host Once the two connections are established, it relays TCP data from one connection to the other without examining its contents. The security function consists of determining which connections will be allowed.
- 124. Bastion Host highly secure host system runs circuit / application level gateways provides externally accessible services may support 2 or more net connections
- 125. Firewall Configurations i. screened host firewall, single-homed bastion ii. screened host firewall, dual-homed bastion iii.screened subnet firewall
- 126. screened host firewall, single- homed bastion the firewall consists of two systems: • a packet-filtering router - allows Internet packets to/from bastion only • a bastion host - performs authentication and proxy functions This configuration has greater security, as it implements both packet-level & application-level filtering
- 127. screened host firewall, dual-homed bastion physically separates the external and internal networks, ensuring two systems must be compromised to breach security. The advantages of dual layers of security are also present here. Again, an information server or other hosts can be allowed direct communication with the router if this is in accord with the security policy, but are now separated from the internal network.
- 128. screened subnet firewall the most secure shown. It has two packet-filtering routers, i. between the bastion host and the Internet ii. between the bastion host and the internal network, creating an isolated subnetwork. May include one or more information servers and modems for dial-in capability. Systems on the inside network cannot construct direct routes to the Internet
- 129. Access Control given system has identified a user determine what resources they can access general model is that of access matrix with subject - active entity (user, process) object - passive entity (file or resource) access right – way object can be accessed can decompose by columns as access control lists rows as capability tickets
- 130. Bell LaPadula (BLP) Model one of the most famous security models implemented as mandatory policies on system has two key policies: no read up (simple security property) a subject can only read/write an object if the current security level of the subject dominates (>=) the classification of the object no write down (*-property) a subject can only append/write to an object if the current security level of the subject is dominated by (<=) the classification of the object