Ad
computer-security-and-cryptography-a-simple-presentation
- 1. 10/01/10 Technical presentation - Alex.C.P 1 Computer Security and Cryptography A very simple presentation : ) Alex.C.P
- 2. 10/01/10 Technical presentation - Alex.C.P 2 Computer Security Virus ? Firewalls ? Hacker ?
- 3. 10/01/10 Technical presentation - Alex.C.P 3 Computer Security Ensuring that information is accessible only to those authorized to have access" (ISO definition excerpt) It is the accuracy, consistency and reliability of the information content Means that the information, the computing systems used to process the information, and the security controls used to protect the information are all available and functioning correctly when the information is needed. ● Confidentiality ● Integrity ● Availability Concerns itself with
- 4. 10/01/10 Technical presentation - Alex.C.P 4 The Role of Cryptography in Computer Security Confidentiality Availability Integrity Cryptographic Techniques
- 5. 10/01/10 Technical presentation - Alex.C.P 5 Cryptography The Basics A two step process Simple? Yes! but I am in the details
- 6. 10/01/10 Technical presentation - Alex.C.P 6 Cryptography History Cryptography or cryptology; derived from Greek kryptós "hidden," and the verb gráfo "write" or λεγειν legein "to speak") An ancient greek scytale (3rd BC) This device was used around 3rd century BC This machine, used in World War II, uses as its base the XOR cipher For example, the string "Wiki" (01010111 01101001 01101011 01101001 in 8-bit ASCII) can be encrypted with the key 11110011 using this method as follows: The German Lorenz cipher machine (1940’s)
- 7. 10/01/10 Technical presentation - Alex.C.P 7 Cryptography - Types of algorithms
- 8. 10/01/10 Technical presentation - Alex.C.P 8 Cryptography – Secret Key Cryptography Symmetric-key algorithms can be divided into stream ciphers and block ciphers. Stream ciphers encrypt the bits of the message one at a time, and block ciphers take a number of bits Popular SKC schemes Data Encryption Standard (DES): The most common SKC scheme used today, DES was designed by IBM in the 1970s and adopted by the National Bureau of Standards (NBS) in 1977 for commercial and unclassified government applications. DES is a block-cipher employing a 56-bit key that operates on 64-bit blocks. Advanced Encryption Standard (AES): This is the next version of DES and is a 128-bit block cipher employing a 128-, 192-, or 256-bit key Other schemes -Twofish, Serpent, AES (aka Rijndael), Blowfish, CAST5, RC4, TDES, and IDEA. encrypt decrypt
- 9. 10/01/10 Technical presentation - Alex.C.P 9 encrypt Cryptography – Public Key Cryptography decrypt PKC depends upon the existence of so-called one-way functions •Multiplication vs. Factorization 9*16= 144 (can be calculated extremely fast) But from 144 (2*2*2*2*3*9) it takes more time and effort to guess the correct key (9&16) •Exponentiation vs. logarithms 3^6 (3 raised to 6) = 729 But the solution to logx 729 = y is non trivial ( note x= 3, y =6) Note - The mathematical "trick" in PKC is to find a trap door in the one-way function so that the inverse calculation becomes easy given knowledge of some item of information.
- 10. 10/01/10 Technical presentation - Alex.C.P 10 Cryptography – Public Key Cryptography Contd Bob’s Private key (9,16) Bob’s Public key (144) Alice writes secret message to Bob & encrypts with Bob’s public key and gives to mutual friend Dave to deliver to Bob Curious boy Dave tries to read the letter using Bobs public key – He can’t Bob decrypts the letter using his private key
- 11. 10/01/10 Technical presentation - Alex.C.P 11 Cryptography: Ensuring Identity -Digital Signature Bob’s Private key Bob’s Public key Bob writes message to Alice & encrypts with Bob’s private key Alice uses Bob’s public key to decrypt it. If it gets decrypted it means message is from Bob
- 12. 10/01/10 Technical presentation - Alex.C.P 12 Role of Trust Secure use of cryptography requires trust. Bob ? Can you give me your public key 177 Impersonator Dave tricks Alice into believing that she has Bob Key – Read on to see what Dave can do next -- Hi ! Hi Bob Hi ! Contd… Then Dave sends a message to Alice “Hi Alice – Our Date is off, too busy – Bob” Then Dave meets Alice and asks her for a date
- 13. 10/01/10 Technical presentation - Alex.C.P 13 Role of Trust Digital Certificate Hi , Here is my Public Key and my name is Bob can you certify it pls 4 Ok, Can you prove your ID Verisign Certified by Verisign + Verisign Private Key = 1 2 3 Bob Shows his Driving License
- 14. 10/01/10 Technical presentation - Alex.C.P 14 Cryptography against Hackers SSL, the e-commerce trust engine SSL does two things: • First, it encrypts the communication between client and server, so there is no use in tapping the line and wait for the user to type in his secret password. But - how can the user know that the web site, which asks him to type in his secret password actually belongs to you and isn't an imitation meant to seduce him to disclose his password? That's where the other purpose of SSL comes into play. • The certificate, which is installed on the server in order to enable SSL is supposed to be signed by a neutral 3rd party who vouches for your identity More details at How SSL Works also see browser settings for safe browsing
- 15. 10/01/10 Technical presentation - Alex.C.P 15 Trust Models used by cryptographic schemes Public Key Certificates and Certificate Authorities Widely used in e-commerce applications. For purposes of electronic transactions, certificates are digital documents. The specific functions of the certificate include: ▪ Establish identity: Associate, or bind, a public key to an individual, organization, corporate position, or other entity. ▪ Assign authority: Establish what actions the holder may or may not take based upon this certificate. ▪ Secure confidential information (e.g., encrypting the session's symmetric key for data confidentiality). Typically, a certificate contains a public key, a name, an expiration date, the name of the authority that issued the certificate The public key is transmitted as part of a certificate. The digital certificate is used to ensure that the submitted public key is, in fact, the public key that belongs to the submitter. The client checks that the certificate has been digitally signed by a certification authority (CA) that the client explicitly trusts. A CA is a trusted authority that verifies the validity of the combination of entity name and public key in a certificate. PGP Web of Trust Is a widely used private e-mail scheme based on public key methods. A PGP user maintains a local key ring of all their known and trusted public keys. The user makes their own determination about the trustworthiness of a key using what is called a "web of trust.“ If Alice needs Bob's public key, Alice can ask Bob for it in another e-mail or, in many cases, download the public key from an advertised server; this server might be a well-known PGP key repository or a site that Bob maintains himself. Alice is prepared to believe that Bob's public key, as stored at these locations, is valid. Kerberos Kerberos is a commonly used authentication scheme on the Internet . Kerberos employs a client/server architecture and provides user-to-server authentication rather than host-to-host authentication. In this model, security and authentication will be based on secret key technology where every host on the network has its own secret key.
- 16. 10/01/10 Technical presentation - Alex.C.P 16 Cryptography – Enabling Confidentiality Confidentiality is the most common use of cryptographic algorithms – protecting data from prying eyes while in transit over an insecure communications channel like the Internet. Once the sender has encrypted the message with the recipient's public key no one (not even the sender) can decrypt it without access to the recipient's private key. Confidentiality Popular PKA Algorithms RSA: Invented by Ronald Rivest, Adi Shamir, and Leonard Adleman of MIT. RSA uses a variable size encryption block and a variable size key The key-pair is derived from a very large number, n, that is the product of two prime numbers chosen according to special rules; these primes may be 100 or more digits in length each, yielding an n with roughly twice as many digits as the prime factors. The public key information includes n and a derivative of one of the factors of n; an attacker cannot determine the prime factors of n (and, therefore, the private key) from this information alone and that is what makes the RSA algorithm so secure. Diffie-Hellman: After the RSA algorithm was published, Diffie and Hellman came up with their own algorithm. D-H is used for secret-key key exchange only, and not for authentication or digital signatures.
- 17. 10/01/10 Technical presentation - Alex.C.P 17 Cryptography- Ensuring Integrity Popular Algorithms Message Digest (MD) algorithms:MD2, MD4, MD5 A series of byte-oriented algorithms that produce a 128-bit hash value from an arbitrary-length message. Secure Hash Algorithm (SHA):. SHA-1 produces a 160-bit hash value Integrity Ensuring Integrity is the second most common use of cryptographic algorithms – ensuring that the data transmitted between two parties is not tampered with intentionally or unintentionally.
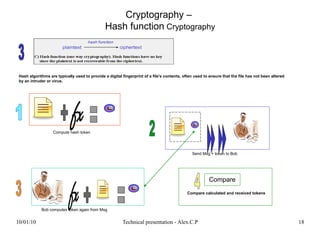
- 18. 10/01/10 Technical presentation - Alex.C.P 18 Cryptography – Hash function Cryptography Hash algorithms are typically used to provide a digital fingerprint of a file's contents, often used to ensure that the file has not been altered by an intruder or virus. Compare Compute hash token Bob computes token again from Msg Send Msg + token to Bob Compare calculated and received tokens
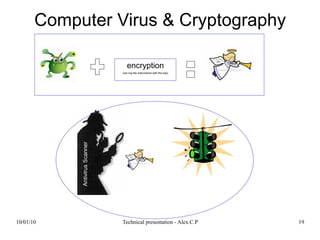
- 19. 10/01/10 Technical presentation - Alex.C.P 19 AntivirusScanner Computer Virus & Cryptography encryption (xor-ing the instructions with the key)
- 20. 10/01/10 Technical presentation - Alex.C.P 20 Cryptography against Virus Technology of granular execution control, backed by strong cryptographic digital signatures, will go a long way toward increasing the security of our systems in general. LoveLetter virus (LOVE-LETTER-FOR-YOU.vbs) A functioning granular execution control the LoveLetter virus would not have spread, because a piece of code would not have been allowed to send out hundreds of copies of itself in electronic mail. Similarly, a Win32 Trojan horse arriving at a victim's system would fail to install, since a random program signed by a stranger, or not signed at all, would not be allowed to alter the registry, or install itself in the TCP/IP stack. Downloading programs and comparing it with the MD5 values also helps in safeguarding.
- 21. 10/01/10 Technical presentation - Alex.C.P 21 Wrap up of popular algorithmsIP Security Protocol (IPsec) (Psec was first proposed for use with IP version 6 (IPv6), but can also be employed with the current IP version, IPv4. ) This is actually a bunch of RFC’s written in order to overcome the security limitations of IPv4 Kerberos -A secret-key encryption and authentication system, designed to authenticate requests for network resources within a user domain rather than to authenticate messages. Kerberos also uses a trusted third-party approach; a client communications with the Kerberos server to obtain "credentials" so that it may access services at the application server uses DES to generate keys and encrypt message Message Digest Cipher (MDC) uses a one-way hash function into a block cipher. Pretty Good Privacy (PGP) PGP 5.x uses Diffie-Hellman for key management and digital signatures; IDEA, CAST, or 3DES for message encryption; and MD5 or SHA for computing the message's hash value. Secure Hypertext Transfer Protocol (S-HTTP) An extension to HTTP to provide secure exchange of documents over the World Wide Web. Supported algorithms include RSA and Kerberos for key exchange, DES for encryption Secure Sockets Layer (SSL) -Developed by Netscape Communications to provide application-independent security and privacy over the Internet. SSL is designed so that protocols such as HTTP, FTP (File Transfer Protocol), and Telnet can operate over it transparently. RSA is used during negotiation to exchange keys and identify the actual cryptographic algorithm (DES, IDEA, RC2, RC4, or 3DES) to use for the session. SSL also uses MD5 for message digests and X.509 public-key certificates. (Found to be breakable soon after the IETF announced formation of group to work on TLS.) Transport Layer Security (TLS) -IETF specification (RFC 2246) intended to replace SSL. Employs Triple-DES (secret key cryptography), SHA (hash), Diffie-Hellman (key exchange), and DSS (digital signatures). X.509 TU-T recommendation for the format of certificates for the public key infrastructure. Certificates map (bind) a user identity to a public key. The IETF application of X.509 certificates is documented in RFC 2459. Secure Shell or SSH is a network protocol that allows data to be exchanged over a secure channel between two computers. Encryption provides confidentiality and integrity of data. SSH uses public-key cryptography to authenticate the remote computer and allow the remote computer to authenticate the user, if necessary. Uses Diffie-Hellman key exchange and strong integrity checking via message authentication codes. (something like a hash function)
- 22. 10/01/10 Technical presentation - Alex.C.P 22 References 1. An Overview of Cryptography-http://www.garykessler.net/library/crypto.html#dhmath 2. Wikipedia -http://en.wikipedia.org/wiki/Main_Page 3. Cryptography basics for infosecurity managers-http://searchsecurity.techtarget.com/tip/1,289483,sid14_gci936670,00.html 4. DAME -http://ftp.fortunaty.net/text/textfiles/virus/datut006.txt 5. Can Cryptography Prevent Computer Viruses? -http://www.research.ibm.com/antivirus/SciPapers/VB2000JFM.htm 6. The History of Computer Viruses -http://www.virus-scan-software.com/virus-scan-help/answers/the-history-of-computer-viruses.shtml 7. Linux vs. Windows Viruses -http://www.theregister.co.uk/2003/10/06/linux_vs_windows_viruses/ 8. How SSL works -https://www.securetrust.com/resources/how-ssl-works 9. How SSL works - http://www.askdavetaylor.com/how_does_ssl_work.html 10. Cryptography Law Survey (in difft countries)- http://rechten.uvt.nl/koops/cryptolaw/ 11. Digital Signature Law Survey -https://dsls.rechten.uvt.nl/ 12. Practical Quantum Cryptography - http://www.youtube.com/watch?v=CKkqUR7FY0o&feature=related 13. Emerging Security Vulnerabilities & the Impact to Business -http://www.youtube.com/watch?v=QTfFCr4G0qA


























































![[Cluj] Turn SSL ON](https://cdn.slidesharecdn.com/ss_thumbnails/owaspeee8oct2015-ovidiucical-turnsslon-letsencrypt-151026112724-lva1-app6892-thumbnail.jpg?width=560&fit=bounds)


































