Control Freak: Risk and Control in Azure DevOps
Download as pptx, pdf1 like1,686 views
This document discusses controls for audit and risk management in Azure DevOps. It covers controls for environments, code, data at rest, and data in motion. For environments, it recommends using ARM templates, VSTS branch policies, and deployment pipelines. For code, it suggests using GitFlow, branch policies, and deployment pipelines with approvals. For data at rest, it proposes encryption with TDE, Always Encrypted, and Storage Service Encryption. For data in motion, it advises using TLS and virtual networks. The document also outlines logging, monitoring, and response controls using tools like Application Insights, Azure Policy, and Security Center.
1 of 29
Downloaded 18 times




























Ad
Recommended
강성훈, 실버바인 대기열 서버 설계 리뷰, NDC2019
강성훈, 실버바인 대기열 서버 설계 리뷰, NDC2019devCAT Studio, NEXON Le document semble contenir des informations variées et des discussions sur des outils technologiques et des systèmes de communication, incluant des références à Redis et à des techniques de sécurité comme les attaques par rejeu. Il présente également des éléments visuels tels que des émoticônes et un certain degré d'ambiguïté dans le texte. De plus, des dates et des indications sur des mises à jour technologiques sont mentionnées, mais le contenu exact demeure peu clair en raison de sa nature fragmentaire.
Introduction to jira
Introduction to jiraKhubaib Ahmed Dan Chuparkoff is a group manager at Atlassian who uses JIRA. The document provides an introduction to using JIRA for agile planning, work tracking, and dashboards. It discusses challenges in defining and estimating tasks and using story points. It also contrasts Scrum and Kanban methods for organizing work in JIRA and explains plan and work modes.
Azure Infrastructure as Code and Hashicorp Terraform
Azure Infrastructure as Code and Hashicorp TerraformAlex Mags This document discusses using Infrastructure as Code with Terraform and Azure. It begins with an introduction to Terraform and how it can be used to manage Azure infrastructure in a declarative way. The document then covers the Terraform workflow including editing configuration files, running a plan, and deploying infrastructure. It demonstrates Terraform through a live demo and discusses how it can benefit operations, security, and development teams. It concludes by discussing the partnership between Microsoft and HashiCorp to further integrate Terraform with Azure.
Final terraform
Final terraformGourav Varma This document provides an overview of Terraform including its key features and how to install, configure, and use Terraform to deploy infrastructure on AWS. It covers topics such as creating EC2 instances and other AWS resources with Terraform, using variables, outputs, and provisioners, implementing modules and workspaces, and managing the Terraform state.
Platform as a Product: How to Delight Your Developers and Deliver Value for Y...
Platform as a Product: How to Delight Your Developers and Deliver Value for Y...VMware Tanzu The document discusses the principles of treating a platform as a product within the context of DevOps and software development. It emphasizes the importance of user-centered design and value addition while also highlighting the need for a dedicated product team to manage the platform effectively. Internal consulting and training are suggested to enhance collaboration and success in implementing microservices and DevOps practices.
Lightening Talk: definition of ready
Lightening Talk: definition of readyAgileee This document discusses the concept of "READY" in agile development. It defines READY as having clear goals and criteria, understanding how to complete the work, having the ability to complete it in the sprint, and managing risks and dependencies. Work that is not READY causes problems like missed deadlines and unclear acceptance criteria. The document recommends using READY as a quality gate to prevent unprepared work from being committed to sprints. It provides examples of how to structure product backlogs and incrementally prepare stories to become READY. The results section notes low adoption rates for READY compared to definitions of done.
Agile Reporting in JIRA
Agile Reporting in JIRACprime The document presents a webinar by Monte Montoya from cprime on Jira agile reporting, highlighting the importance of effective reporting in scaled agile environments. Key topics include project metrics for burnup, sprints, and cross-team dependencies, as well as the roles involved in release planning. It emphasizes the need for alignment between business and delivery teams to ensure successful project execution and reporting.
How to test infrastructure code: automated testing for Terraform, Kubernetes,...
How to test infrastructure code: automated testing for Terraform, Kubernetes,...Yevgeniy Brikman This document discusses the importance of automated testing for infrastructure code in DevOps, highlighting various testing strategies such as static analysis, unit tests, and integration tests. It emphasizes that confidence in infrastructure changes can be achieved through these automated tests, using tools like Terraform and Kubernetes. The author also outlines practical examples and tools for implementing these tests effectively.
Azure devops
Azure devopsMohit Chhabra This document discusses using Azure DevOps for open source projects. It mentions Mohit Chhabra as the author and includes his email and Twitter handle. It also includes links to the Puppet Labs and IT Pro Guy websites, which contain articles about DevOps practices such as testing in production, fault injection, and usage monitoring. The document promotes a happy DevOps cycle between development and operations.
Are we done yet?
Are we done yet?Richard Cheng This document discusses the importance of team charters and definitions of ready and done in Agile development. It defines key elements of a team charter such as goals, success criteria, constraints, and team rules/working agreements. It also explains what a definition of ready and definition of done are, providing examples of criteria that could be included in each. The document emphasizes that definitions of ready and done are not static and should be informed by the team's experience. It poses questions about why teams should create charters and who is accountable for ensuring teams follow their charters.
JİRA'ya Giriş / Atlassian
JİRA'ya Giriş / AtlassianCansu Kaya IT- Project Management dersi için hazırladığımız tanıtım çalışması
Cloud Migration, Application Modernization, and Security
Cloud Migration, Application Modernization, and Security Tom Laszewski The document outlines Amazon Web Services' (AWS) cloud migration methodology, detailing processes for application modernization, security, and infrastructure assessment. It discusses various migration approaches, including lift-and-shift and re-platforming, along with best practices for ensuring security and compliance during migration. Additionally, it provides a case study on Condé Nast's successful data center migration, highlighting key migration criteria and lessons learned.
B2B EDI Formats and MuleSoft X12 Connector
B2B EDI Formats and MuleSoft X12 ConnectorVikalp Bhalia The document discusses a meetup on B2B EDI formats and MuleSoft's X12 connector. It provides an overview of different EDI formats including X12, UN/EDIFACT, and TRADACOM. It then explains what X12 is, how different transactions are represented, and how the MuleSoft X12 connector works, allowing conversion between X12 and DataWeave and supporting validation and acknowledgments. The presenter concludes with a demonstration of the connector and a Q&A.
Jira Agile
Jira AgilePeter Perger This document discusses Agile project management tools and methodologies. It covers JIRA Agile for tracking work in an Agile workflow, the Scrum framework, and its events and artifacts like sprints, product backlogs, and burn down charts. It also mentions the Agile manifesto and its values of prioritizing working software and customer collaboration over documentation and contracts.
NDC17 장창완(최종)
NDC17 장창완(최종)창완 장 <마비노기 영웅전>의 사례에 기반하여 다음의 내용을 설명합니다.
1. 국내 및 해외에서 라이브 서비스 중에 발생하는 작업장 이슈에 대응하기 위해서 실시간 로그 수집 프로세스를 구축하면서 고민하였던 내용과
2. 수집한 로그 데이터를 활용하여 온라인 액션 게임에서 캐릭터 애니메이션 패턴간의 유사도(TF-IDF, Cosine Similarity)를 분석하여 현업 실무의 어뷰징 탐지에 활용한 사례를 공유합니다.
라이브 서비스 환경에서 국내 및 해외의 실시간 로그 수집에 대해서 고민하시는 개발자나 온라인 게임에서의 봇탐지에 관심있는 분석가들에게 유용한 사례를 소개해드릴 수 있을 것으로 생각합니다.
VMware Tanzu Kubernetes Connect
VMware Tanzu Kubernetes ConnectVMware Tanzu This document provides an agenda and materials for a workshop on VMware Tanzu for Kubernetes Operations. The agenda includes an introduction to challenges faced by platform teams maintaining Kubernetes platforms, an overview of Tanzu for Kubernetes Operations and how it can help address those challenges, and a hands-on lab session. Tanzu for Kubernetes Operations is a collection of products that provide capabilities for common customer needs around managing containerized platforms at scale, including simplified management of Kubernetes clusters across clouds, centralized visibility and security policies, and developer self-service access.
Azure API Management
Azure API Managementjeremysbrown This document discusses Azure API Management and how it can help create a successful API program. It outlines key components like developer engagement, analytics, and security. It also describes the logical architecture of API Management and how it can host APIs from any platform or framework. Several demos are included that showcase features like adding the API Management service, creating APIs and products, configuring policies, and using OAuth 2.0 for security.
Docker Swarm 0.2.0
Docker Swarm 0.2.0Docker, Inc. The document introduces Docker Swarm, a clustering system that allows multiple Docker engines to be managed as a single entity, highlighting its functionality, resource management capabilities, and the ease of getting started. It outlines features such as advanced scheduling, node management, and custom constraints, along with its upcoming integration with various backends and high availability options. The document also includes key commands for creating and managing clusters, as well as an invitation for community contributions.
Vault
VaultJean-Philippe Bélanger Vault is a tool for securely accessing secrets. It provides encryption of secrets at rest and controls access through authentication, authorization, and auditing. Keys are rotated automatically and secrets have time-to-live limits. Vault can be used for secrets like API keys, passwords, certificates and more. It supports multiple backends for secret storage including Consul, DynamoDB, and filesystem. Vault has built-in authentication methods and is highly available through replication across multiple nodes.
GitHub Actions in action
GitHub Actions in actionOleksii Holub GitHub Actions is an automation platform for GitHub repositories that allows users to build workflows to automate software tasks. It was introduced in 2019 and is based on Azure Pipelines. Workflows are configured using YAML files and can be triggered by events like push commits, pull requests, or scheduled times. Actions, which are reusable code components, can be used in workflows and are sourced from the GitHub marketplace or created by users. GitHub Actions is free for public repositories and offers paid plans for private repositories.
Continuous Delivery
Continuous DeliveryMike McGarr The document discusses continuous delivery, outlining its principles and core practices aimed at enhancing software development efficiency. It contrasts traditional waterfall methods with agile approaches to highlight the benefits of continuous integration and deployment, emphasizing the importance of automation and collaboration. Key components include build pipelines, testing strategies, and deployment automation to enable faster and more reliable software releases.
Microservices Architecture - Cloud Native Apps
Microservices Architecture - Cloud Native AppsAraf Karsh Hamid This document provides an overview of microservices architecture, including concepts, characteristics, infrastructure patterns, and software design patterns relevant to microservices. It discusses when microservices should be used versus monolithic architectures, considerations for sizing microservices, and examples of pioneers in microservices implementation like Netflix and Spotify. The document also covers domain-driven design concepts like bounded context that are useful for decomposing monolithic applications into microservices.
Kanban in Action Workshop
Kanban in Action WorkshopMark Grove The document provides an overview of the Kanban method, emphasizing its role in improving service delivery, catalyzing business improvements, and managing workflow efficiently. It outlines essential Kanban practices such as visualizing progress, limiting work-in-progress, and implementing feedback loops, while also presenting various scenarios and challenges teams may face when applying the method. Additionally, it offers insights on how to coach teams to navigate issues like bottlenecks, external dependencies, and maintaining a steady flow of work.
SOLID & Design Patterns
SOLID & Design PatternsGrokking VN This document discusses SOLID principles and design patterns. It introduces SOLID, including the single responsibility, open-closed, Liskov substitution, interface segregation, and dependency inversion principles. It then explains three design patterns - decorator, strategy, and visitor patterns - with examples. The document emphasizes that understanding SOLID helps make design patterns more approachable and useful for communication. It concludes with a Q&A section.
How to estimate in scrum
How to estimate in scrumGloria Stoilova - Story points are an arbitrary measure used by Scrum teams to estimate the effort required to implement a user story. Teams typically use a Fibonacci sequence like 1, 2, 3, 5, 8, 13, 20, 40, 100.
- Estimating user stories allows teams to plan how many highest priority stories can be completed in a sprint and helps forecast release schedules. The whole team estimates during backlog refinement.
- Stories are estimated once they are small enough to fit in a sprint and acceptance criteria are agreed upon. Teams commonly use planning poker where each member privately assigns a story point value and the team discusses until consensus is reached.
Terraform on Azure
Terraform on AzureMithun Shanbhag The document discusses the use of Terraform for Azure deployments, outlining its advantages such as multi-cloud support and open-source nature, along with some disadvantages. It covers installation steps, key terminology, resources and modules, and provides functionality details for HCL language and provisioners. Additionally, it highlights integration with Azure and offers links for further reading on Terraform and its providers.
Azure DevOps CI/CD For Beginners
Azure DevOps CI/CD For BeginnersRahul Nath The document outlines a guide for beginners on using Azure DevOps for CI/CD pipelines, emphasizing the integration of various agile tools to enhance workflow efficiency. It details features like collaboration through Git providers, testing capabilities, and package management, highlighting the importance of infrastructure as code with Azure Resource Manager templates. Additionally, the content includes practical insights on implementing YAML releases and maintaining developer workflows.
Secure Your Code Implement DevSecOps in Azure
Secure Your Code Implement DevSecOps in Azurekloia The document discusses the integration of DevSecOps practices in Azure, emphasizing the importance of security throughout the development lifecycle. It covers topics such as security automation, vulnerability assessment, and implementing best practices using Azure tools, GitHub, and third-party solutions. Additionally, it provides a step-by-step demo for setting up a secure CI/CD pipeline in Azure DevOps using various integrated services.
Azure Security Check List - Final.pdf
Azure Security Check List - Final.pdfOkan YILDIZ The Azure DevOps Security Guide provides a comprehensive framework for ensuring a secure Azure DevOps environment, covering areas such as access control, authentication, network security, and continuous monitoring. Key recommendations include implementing role-based access control, multi-factor authentication, and regular auditing of user accounts and permissions. The guide emphasizes a culture of continuous improvement and collaboration among developers and security teams to protect organizational assets.
More Related Content
What's hot (20)
How to test infrastructure code: automated testing for Terraform, Kubernetes,...
How to test infrastructure code: automated testing for Terraform, Kubernetes,...Yevgeniy Brikman This document discusses the importance of automated testing for infrastructure code in DevOps, highlighting various testing strategies such as static analysis, unit tests, and integration tests. It emphasizes that confidence in infrastructure changes can be achieved through these automated tests, using tools like Terraform and Kubernetes. The author also outlines practical examples and tools for implementing these tests effectively.
Azure devops
Azure devopsMohit Chhabra This document discusses using Azure DevOps for open source projects. It mentions Mohit Chhabra as the author and includes his email and Twitter handle. It also includes links to the Puppet Labs and IT Pro Guy websites, which contain articles about DevOps practices such as testing in production, fault injection, and usage monitoring. The document promotes a happy DevOps cycle between development and operations.
Are we done yet?
Are we done yet?Richard Cheng This document discusses the importance of team charters and definitions of ready and done in Agile development. It defines key elements of a team charter such as goals, success criteria, constraints, and team rules/working agreements. It also explains what a definition of ready and definition of done are, providing examples of criteria that could be included in each. The document emphasizes that definitions of ready and done are not static and should be informed by the team's experience. It poses questions about why teams should create charters and who is accountable for ensuring teams follow their charters.
JİRA'ya Giriş / Atlassian
JİRA'ya Giriş / AtlassianCansu Kaya IT- Project Management dersi için hazırladığımız tanıtım çalışması
Cloud Migration, Application Modernization, and Security
Cloud Migration, Application Modernization, and Security Tom Laszewski The document outlines Amazon Web Services' (AWS) cloud migration methodology, detailing processes for application modernization, security, and infrastructure assessment. It discusses various migration approaches, including lift-and-shift and re-platforming, along with best practices for ensuring security and compliance during migration. Additionally, it provides a case study on Condé Nast's successful data center migration, highlighting key migration criteria and lessons learned.
B2B EDI Formats and MuleSoft X12 Connector
B2B EDI Formats and MuleSoft X12 ConnectorVikalp Bhalia The document discusses a meetup on B2B EDI formats and MuleSoft's X12 connector. It provides an overview of different EDI formats including X12, UN/EDIFACT, and TRADACOM. It then explains what X12 is, how different transactions are represented, and how the MuleSoft X12 connector works, allowing conversion between X12 and DataWeave and supporting validation and acknowledgments. The presenter concludes with a demonstration of the connector and a Q&A.
Jira Agile
Jira AgilePeter Perger This document discusses Agile project management tools and methodologies. It covers JIRA Agile for tracking work in an Agile workflow, the Scrum framework, and its events and artifacts like sprints, product backlogs, and burn down charts. It also mentions the Agile manifesto and its values of prioritizing working software and customer collaboration over documentation and contracts.
NDC17 장창완(최종)
NDC17 장창완(최종)창완 장 <마비노기 영웅전>의 사례에 기반하여 다음의 내용을 설명합니다.
1. 국내 및 해외에서 라이브 서비스 중에 발생하는 작업장 이슈에 대응하기 위해서 실시간 로그 수집 프로세스를 구축하면서 고민하였던 내용과
2. 수집한 로그 데이터를 활용하여 온라인 액션 게임에서 캐릭터 애니메이션 패턴간의 유사도(TF-IDF, Cosine Similarity)를 분석하여 현업 실무의 어뷰징 탐지에 활용한 사례를 공유합니다.
라이브 서비스 환경에서 국내 및 해외의 실시간 로그 수집에 대해서 고민하시는 개발자나 온라인 게임에서의 봇탐지에 관심있는 분석가들에게 유용한 사례를 소개해드릴 수 있을 것으로 생각합니다.
VMware Tanzu Kubernetes Connect
VMware Tanzu Kubernetes ConnectVMware Tanzu This document provides an agenda and materials for a workshop on VMware Tanzu for Kubernetes Operations. The agenda includes an introduction to challenges faced by platform teams maintaining Kubernetes platforms, an overview of Tanzu for Kubernetes Operations and how it can help address those challenges, and a hands-on lab session. Tanzu for Kubernetes Operations is a collection of products that provide capabilities for common customer needs around managing containerized platforms at scale, including simplified management of Kubernetes clusters across clouds, centralized visibility and security policies, and developer self-service access.
Azure API Management
Azure API Managementjeremysbrown This document discusses Azure API Management and how it can help create a successful API program. It outlines key components like developer engagement, analytics, and security. It also describes the logical architecture of API Management and how it can host APIs from any platform or framework. Several demos are included that showcase features like adding the API Management service, creating APIs and products, configuring policies, and using OAuth 2.0 for security.
Docker Swarm 0.2.0
Docker Swarm 0.2.0Docker, Inc. The document introduces Docker Swarm, a clustering system that allows multiple Docker engines to be managed as a single entity, highlighting its functionality, resource management capabilities, and the ease of getting started. It outlines features such as advanced scheduling, node management, and custom constraints, along with its upcoming integration with various backends and high availability options. The document also includes key commands for creating and managing clusters, as well as an invitation for community contributions.
Vault
VaultJean-Philippe Bélanger Vault is a tool for securely accessing secrets. It provides encryption of secrets at rest and controls access through authentication, authorization, and auditing. Keys are rotated automatically and secrets have time-to-live limits. Vault can be used for secrets like API keys, passwords, certificates and more. It supports multiple backends for secret storage including Consul, DynamoDB, and filesystem. Vault has built-in authentication methods and is highly available through replication across multiple nodes.
GitHub Actions in action
GitHub Actions in actionOleksii Holub GitHub Actions is an automation platform for GitHub repositories that allows users to build workflows to automate software tasks. It was introduced in 2019 and is based on Azure Pipelines. Workflows are configured using YAML files and can be triggered by events like push commits, pull requests, or scheduled times. Actions, which are reusable code components, can be used in workflows and are sourced from the GitHub marketplace or created by users. GitHub Actions is free for public repositories and offers paid plans for private repositories.
Continuous Delivery
Continuous DeliveryMike McGarr The document discusses continuous delivery, outlining its principles and core practices aimed at enhancing software development efficiency. It contrasts traditional waterfall methods with agile approaches to highlight the benefits of continuous integration and deployment, emphasizing the importance of automation and collaboration. Key components include build pipelines, testing strategies, and deployment automation to enable faster and more reliable software releases.
Microservices Architecture - Cloud Native Apps
Microservices Architecture - Cloud Native AppsAraf Karsh Hamid This document provides an overview of microservices architecture, including concepts, characteristics, infrastructure patterns, and software design patterns relevant to microservices. It discusses when microservices should be used versus monolithic architectures, considerations for sizing microservices, and examples of pioneers in microservices implementation like Netflix and Spotify. The document also covers domain-driven design concepts like bounded context that are useful for decomposing monolithic applications into microservices.
Kanban in Action Workshop
Kanban in Action WorkshopMark Grove The document provides an overview of the Kanban method, emphasizing its role in improving service delivery, catalyzing business improvements, and managing workflow efficiently. It outlines essential Kanban practices such as visualizing progress, limiting work-in-progress, and implementing feedback loops, while also presenting various scenarios and challenges teams may face when applying the method. Additionally, it offers insights on how to coach teams to navigate issues like bottlenecks, external dependencies, and maintaining a steady flow of work.
SOLID & Design Patterns
SOLID & Design PatternsGrokking VN This document discusses SOLID principles and design patterns. It introduces SOLID, including the single responsibility, open-closed, Liskov substitution, interface segregation, and dependency inversion principles. It then explains three design patterns - decorator, strategy, and visitor patterns - with examples. The document emphasizes that understanding SOLID helps make design patterns more approachable and useful for communication. It concludes with a Q&A section.
How to estimate in scrum
How to estimate in scrumGloria Stoilova - Story points are an arbitrary measure used by Scrum teams to estimate the effort required to implement a user story. Teams typically use a Fibonacci sequence like 1, 2, 3, 5, 8, 13, 20, 40, 100.
- Estimating user stories allows teams to plan how many highest priority stories can be completed in a sprint and helps forecast release schedules. The whole team estimates during backlog refinement.
- Stories are estimated once they are small enough to fit in a sprint and acceptance criteria are agreed upon. Teams commonly use planning poker where each member privately assigns a story point value and the team discusses until consensus is reached.
Terraform on Azure
Terraform on AzureMithun Shanbhag The document discusses the use of Terraform for Azure deployments, outlining its advantages such as multi-cloud support and open-source nature, along with some disadvantages. It covers installation steps, key terminology, resources and modules, and provides functionality details for HCL language and provisioners. Additionally, it highlights integration with Azure and offers links for further reading on Terraform and its providers.
Azure DevOps CI/CD For Beginners
Azure DevOps CI/CD For BeginnersRahul Nath The document outlines a guide for beginners on using Azure DevOps for CI/CD pipelines, emphasizing the integration of various agile tools to enhance workflow efficiency. It details features like collaboration through Git providers, testing capabilities, and package management, highlighting the importance of infrastructure as code with Azure Resource Manager templates. Additionally, the content includes practical insights on implementing YAML releases and maintaining developer workflows.
Similar to Control Freak: Risk and Control in Azure DevOps (20)
Secure Your Code Implement DevSecOps in Azure
Secure Your Code Implement DevSecOps in Azurekloia The document discusses the integration of DevSecOps practices in Azure, emphasizing the importance of security throughout the development lifecycle. It covers topics such as security automation, vulnerability assessment, and implementing best practices using Azure tools, GitHub, and third-party solutions. Additionally, it provides a step-by-step demo for setting up a secure CI/CD pipeline in Azure DevOps using various integrated services.
Azure Security Check List - Final.pdf
Azure Security Check List - Final.pdfOkan YILDIZ The Azure DevOps Security Guide provides a comprehensive framework for ensuring a secure Azure DevOps environment, covering areas such as access control, authentication, network security, and continuous monitoring. Key recommendations include implementing role-based access control, multi-factor authentication, and regular auditing of user accounts and permissions. The guide emphasizes a culture of continuous improvement and collaboration among developers and security teams to protect organizational assets.
Tour of Azure DevOps
Tour of Azure DevOpsCallon Campbell Callon Campbell, a Microsoft Azure MVP and systems architect, provides an overview of Azure DevOps, emphasizing its role in enhancing continuous delivery through integration of people, processes, and technologies. The document highlights features such as Azure pipelines, boards, repositories, and artifacts, illustrating how they streamline development and deployment in various environments. It also outlines service pricing, migration benefits, and the importance of using agile tools for effective project management.
Everything as Code with Azure DevOps
Everything as Code with Azure DevOpsVenura Athukorala The document discusses Azure DevOps, detailing its components such as boards, repos, and pipelines, and the evolution from VSTS to Azure DevOps. It highlights the advantages of using YAML for pipeline definitions, including code versioning, reduced operational overhead, and developer ownership of pipelines. Additionally, the document outlines the structure of pipelines, stages, jobs, and future enhancements like manual approvals and the ability to re-run failed stages.
ADC 2017 - DevOps by examples part I – forward pipeline
ADC 2017 - DevOps by examples part I – forward pipeline Giulio Vian DevOps is a practice that emphasizes collaboration between software developers and IT operations professionals. It aims to unify development and operations teams to automate and streamline the process of software delivery and infrastructure changes. The presentation introduces DevOps concepts and practices like infrastructure as code, continuous integration and delivery, dynamic configuration, and emphasizing people and culture. It demonstrates how to set up infrastructure hosting for an application using tools like Azure, VSTS, Docker, and Kubernetes and discusses considerations for deploying applications, managing secrets and configurations, and monitoring operational data.
Azure DevOps Interview Questions PDF By ScholarHat
Azure DevOps Interview Questions PDF By ScholarHatScholarhat Azure DevOps Interview Questions PDF By ScholarHat
Microsoft Skills Bootcamp - The power of GitHub and Azure
Microsoft Skills Bootcamp - The power of GitHub and AzureDavide Benvegnù The document discusses a Microsoft Skills Bootcamp focused on utilizing GitHub and Azure for enhanced development practices. It emphasizes the shift towards DevSecOps, where security is integrated throughout the entire development process, leading to faster and more efficient application releases. Participants are encouraged to leverage resources for continued learning and development in these areas.
Azure Security Compass v1.1 - Presentation.pptx
Azure Security Compass v1.1 - Presentation.pptxZaheerEbrahim5 The document outlines the Microsoft Azure Security Compass, designed to enhance an organization's security posture on the Azure platform through workshops and best practices. It emphasizes the importance of continuously adapting security strategies in response to evolving threats and provides guidance on key areas such as identity management, risk compliance, and governance. The document also highlights the shared responsibility model between clients and Microsoft in managing security across different cloud service models (IaaS, PaaS, SaaS).
Azure DevOps in Action
Azure DevOps in ActionCallon Campbell The document provides a comprehensive overview of Azure DevOps, highlighting its features such as Azure Pipelines, Azure Artifacts, and Azure Boards, and emphasizes the importance of DevOps practices in improving software delivery and operational efficiency. It discusses the integration capabilities with various tools and platforms, along with the benefits of using Microsoft's cloud services for application development and deployment. Additionally, it offers insights into pricing structures, user management, and the flexibility of Azure DevOps to cater to teams of any size.
What are the key features of Azure DevOps and how are they beneficial to the ...
What are the key features of Azure DevOps and how are they beneficial to the ...kzayra69 Azure DevOps is a comprehensive suite of tools by Microsoft that enhances the software development lifecycle through features like agile planning, source control, CI/CD automation, testing, and package management. It enables effective collaboration, faster software delivery, and improved productivity while ensuring security and compliance for managing sensitive data. Additionally, custom tasks and integrations with platforms like Jenkins allow further customization and automation of the development process.
DevSecOps - automating security
DevSecOps - automating securityJohn Staveley The document discusses the implementation of DevSecOps to enhance application and Azure security through practices like threat modeling, security automation, and continuous feedback throughout the development process. It outlines various tools and strategies for ensuring security in coding, deploying, and monitoring phases, with a focus on integrating security measures early in the development lifecycle. Notable examples of data breaches highlight the importance of robust security protocols to prevent vulnerabilities and comply with regulations like GDPR.
Azure DevOps työkalut - Roundtable 14.3.2019
Azure DevOps työkalut - Roundtable 14.3.2019Janne Mattila The document is an agenda for an event discussing Azure DevOps tools and projects. The agenda includes:
- Breakfast and opening from 8:30-9:00
- A presentation on Azure DevOps tools from 9:00-9:45
- A presentation on Azure PaaS projects and agile development from 9:45-10:30
- A panel discussion from 10:30
- Lunch
The document provides details on the presentations and panels planned during the event.
Security Scanning Solutions_ Protecting Applications in the DevOps Era.pdf
Security Scanning Solutions_ Protecting Applications in the DevOps Era.pdfDevseccops.ai Security scanning solutions are essential in DevOps, ensuring vulnerabilities are detected early in CI/CD pipelines. Tools like Azure DevOps Advanced Security and AI-driven solutions like DevSecCops.ai provide automated threat detection, compliance, and hybrid cloud security.
Top Priorities for Cloud Application Security
Top Priorities for Cloud Application Security2nd Sight Lab The document outlines essential strategies for cloud application security, emphasizing the importance of automating deployments, monitoring everything, and reducing human error through best practices. It recommends leveraging automated configuration management, promoting code through a dedicated pipeline, and maintaining governance and compliance check automation. Additionally, the document highlights the need for segregation of duties, turning security findings into developer tasks, and ensuring executive support for effective implementation.
DevSecCon Boston 2018: Securing the Automated Pipeline: A Tale of Navigating ...
DevSecCon Boston 2018: Securing the Automated Pipeline: A Tale of Navigating ...DevSecCon This document discusses how security practices need to change to keep up with DevOps practices like microservices and continuous deployment. It outlines how deployment used to work with quarterly releases versus now being able to deploy multiple times per day. Security tools also need to be faster to keep up. The document recommends automating security testing so it can be integrated into continuous integration pipelines. It suggests implementing security testing in stages from the individual developer level up to production. The goal is to provide security while also keeping developers and auditors happy by maintaining a collaborative approach and documenting the process.
Zure Azure PaaS Zero to Hero - DevOps training day
Zure Azure PaaS Zero to Hero - DevOps training dayOkko Oulasvirta This document provides an overview of Azure DevOps and related Azure services for continuous integration, delivery, and monitoring. It discusses DevOps practices including source control with Azure Repos, work tracking with Azure Boards, continuous integration and deployment pipelines with Azure Pipelines, infrastructure as code with ARM templates, and application monitoring with Application Insights. It also covers security practices like role-based access control and use of Azure Key Vault for secrets management. Live demos are provided for many of the Azure DevOps features and services discussed.
Implementing DevOps Automation: Best Practices & Common Mistakes - DevOps Eas...
Implementing DevOps Automation: Best Practices & Common Mistakes - DevOps Eas...Derek Ashmore The document discusses best practices and common mistakes in implementing DevOps automation, highlighting the importance of infrastructure as code and disciplined management approaches. It emphasizes the benefits of minimizing manual changes, utilizing CI/CD pipelines, and automating testing and policy enforcement. It also warns against manual processes that can hinder productivity and innovation, advocating for decentralized management and effective service catalogs.
Past, Present and Future of DevOps Infrastructure
Past, Present and Future of DevOps InfrastructureSynergetics Learning and Cloud Consulting The document provides a comprehensive overview of DevOps, emphasizing the integration of development and IT operations to enhance software delivery and infrastructure management. It discusses key concepts such as Infrastructure as Code (IaC), configuration management, and the importance of security and monitoring in CI/CD environments. Various tools like Azure, Terraform, Ansible, and Chef are highlighted for their roles in facilitating DevOps practices and maintaining efficient and secure infrastructure.
DevSecOps: A Secure SDLC in the Age of DevOps and Hyper-Automation
DevSecOps: A Secure SDLC in the Age of DevOps and Hyper-AutomationAlex Senkevitch The document discusses the evolution of DevSecOps within the context of DevOps and hyper-automation, addressing the challenges and lessons learned in integrating security into the software development lifecycle. It outlines the shift from traditional security approaches to more automated and integrated security practices as a response to the rapid changes in technology and development practices. Key points include the necessity of a mature pipeline, effective tool selection, and the importance of addressing security holistically without compromising on automation or functionality.
Ad
More from AgileThought (6)
Adventures in Agile Testing
Adventures in Agile TestingAgileThought The document outlines key principles of agile testing methodology, emphasizing the importance of communication, iterative development, and user acceptance testing. It discusses the differences between manual and automated testing, with a focus on exploratory testing techniques and guidelines. Additionally, it provides resources and references for further exploration in the field of agile testing.
From Device To Cloud
From Device To CloudAgileThought Art Garcia, a senior DevOps engineer and Microsoft Azure architect, gave a presentation about connecting Internet of Things devices to the cloud using Azure. He discussed how real-world devices like temperature and distance sensors can collect data and stream it to Azure Storage. The presentation also included a Fritzing diagram of a distance sensor and details on querying device data within Azure Streaming Analytics.
Operationalizing Machine Learning
Operationalizing Machine LearningAgileThought This document presents a comprehensive overview of operationalizing machine learning (ML) in software applications, specifically comparing traditional software approaches to ML solutions. It highlights the advantages of ML, such as generalization and solving complex problems that traditional software cannot, and discusses key aspects of deploying ML models, including data preparation and model selection. The document also outlines the costs associated with custom ML models and references methodologies like CRISP-DM for data science.
Patterns Are Good For Managers
Patterns Are Good For ManagersAgileThought Michael Cooper, a senior consultant, emphasizes the importance of structured patterns for software development to enhance productivity, onboarding, and code quality. He discusses the MVC (Model-View-Controller) architecture as a means to encourage solid code and standardized testing in Angular projects, allowing developers to become productive quickly. Additionally, the document highlights various code samples and tools to support the implementation of these patterns.
The Agile Journey
The Agile JourneyAgileThought The document describes a company's transition to Agile and Lean principles to address issues like a shifting market, slow delivery times, low morale, and cultural divides. It overviews key Agile concepts like customer collaboration, prioritizing by value, and incremental delivery. The company then mapped its value streams, limited work-in-progress, made work visible, and eliminated waste. This resulted in being 40% more efficient with a 95% employee approval rating.
Psychology In UX
Psychology In UXAgileThought This document discusses how to conduct effective user research through asking the right questions. It explains that narrow questions lead to narrow answers, while broad, non-leading questions provide more valuable user feedback. The document provides tips for formulating different types of questions to better understand users and generate thought models from the data collected. Effective questioning involves understanding how a user's thoughts are structured to get insightful responses.
Ad
Recently uploaded (20)
GenAI Opportunities and Challenges - Where 370 Enterprises Are Focusing Now.pdf
GenAI Opportunities and Challenges - Where 370 Enterprises Are Focusing Now.pdfPriyanka Aash GenAI Opportunities and Challenges - Where 370 Enterprises Are Focusing Now
Connecting Data and Intelligence: The Role of FME in Machine Learning
Connecting Data and Intelligence: The Role of FME in Machine LearningSafe Software In this presentation, we want to explore powerful data integration and preparation for Machine Learning. FME is known for its ability to manipulate and transform geospatial data, connecting diverse data sources into efficient and automated workflows. By integrating FME with Machine Learning techniques, it is possible to transform raw data into valuable insights faster and more accurately, enabling intelligent analysis and data-driven decision making.
Smarter Aviation Data Management: Lessons from Swedavia Airports and Sweco
Smarter Aviation Data Management: Lessons from Swedavia Airports and SwecoSafe Software Managing airport and airspace data is no small task, especially when you’re expected to deliver it in AIXM format without spending a fortune on specialized tools. But what if there was a smarter, more affordable way?
Join us for a behind-the-scenes look at how Sweco partnered with Swedavia, the Swedish airport operator, to solve this challenge using FME and Esri.
Learn how they built automated workflows to manage periodic updates, merge airspace data, and support data extracts – all while meeting strict government reporting requirements to the Civil Aviation Administration of Sweden.
Even better? Swedavia built custom services and applications that use the FME Flow REST API to trigger jobs and retrieve results – streamlining tasks like securing the quality of new surveyor data, creating permdelta and baseline representations in the AIS schema, and generating AIXM extracts from their AIS data.
To conclude, FME expert Dean Hintz will walk through a GeoBorders reading workflow and highlight recent enhancements to FME’s AIXM (Aeronautical Information Exchange Model) processing and interpretation capabilities.
Discover how airports like Swedavia are harnessing the power of FME to simplify aviation data management, and how you can too.
"Database isolation: how we deal with hundreds of direct connections to the d...
"Database isolation: how we deal with hundreds of direct connections to the d...Fwdays What can go wrong if you allow each service to access the database directly? In a startup, this seems like a quick and easy solution, but as the system scales, problems appear that no one could have guessed.
In my talk, I'll share Solidgate's experience in transforming its architecture: from the chaos of direct connections to a service-based data access model. I will talk about the transition stages, bottlenecks, and how isolation affected infrastructure support. I will honestly show what worked and what didn't. In short, we will analyze the controversy of this talk.
Quantum AI Discoveries: Fractal Patterns Consciousness and Cyclical Universes
Quantum AI Discoveries: Fractal Patterns Consciousness and Cyclical UniversesSaikat Basu Embark on a cosmic journey exploring the intersection of quantum
computing, consciousness, and ancient wisdom. Together we'll uncover the
recursive patterns that bind our reality.
Cracking the Code - Unveiling Synergies Between Open Source Security and AI.pdf
Cracking the Code - Unveiling Synergies Between Open Source Security and AI.pdfPriyanka Aash Cracking the Code - Unveiling Synergies Between Open Source Security and AI
You are not excused! How to avoid security blind spots on the way to production
You are not excused! How to avoid security blind spots on the way to productionMichele Leroux Bustamante We live in an ever evolving landscape for cyber threats creating security risk for your production systems. Mitigating these risks requires participation throughout all stages from development through production delivery - and by every role including architects, developers QA and DevOps engineers, product owners and leadership. No one is excused! This session will cover examples of common mistakes or missed opportunities that can lead to vulnerabilities in production - and ways to do better throughout the development lifecycle.
Securing Account Lifecycles in the Age of Deepfakes.pptx
Securing Account Lifecycles in the Age of Deepfakes.pptxFIDO Alliance Securing Account Lifecycles in the Age of Deepfakes
Quantum AI: Where Impossible Becomes Probable
Quantum AI: Where Impossible Becomes ProbableSaikat Basu Imagine combining the "brains" of Artificial Intelligence (AI) with the "super muscles" of Quantum Computing. That's Quantum AI!
It's a new field that uses the mind-bending rules of quantum physics to make AI even more powerful.
The Future of Product Management in AI ERA.pdf
The Future of Product Management in AI ERA.pdfAlyona Owens Hi, I’m Aly Owens, I have a special pleasure to stand here as over a decade ago I graduated from CityU as an international student with an MBA program. I enjoyed the diversity of the school, ability to work and study, the network that came with being here, and of course the price tag for students here has always been more affordable than most around.
Since then I have worked for major corporations like T-Mobile and Microsoft and many more, and I have founded a startup. I've also been teaching product management to ensure my students save time and money to get to the same level as me faster avoiding popular mistakes. Today as I’ve transitioned to teaching and focusing on the startup, I hear everybody being concerned about Ai stealing their jobs… We’ll talk about it shortly.
But before that, I want to take you back to 1997. One of my favorite movies is “Fifth Element”. It wowed me with futuristic predictions when I was a kid and I’m impressed by the number of these predictions that have already come true. Self-driving cars, video calls and smart TV, personalized ads and identity scanning. Sci-fi movies and books gave us many ideas and some are being implemented as we speak. But we often get ahead of ourselves:
Flying cars,Colonized planets, Human-like AI: not yet, Time travel, Mind-machine neural interfaces for everyone: Only in experimental stages (e.g. Neuralink).
Cyberpunk dystopias: Some vibes (neon signs + inequality + surveillance), but not total dystopia (thankfully).
On the bright side, we predict that the working hours should drop as Ai becomes our helper and there shouldn’t be a need to work 8 hours/day. Nobody knows for sure but we can require that from legislation. Instead of waiting to see what the government and billionaires come up with, I say we should design our own future.
So, we as humans, when we don’t know something - fear takes over. The same thing happened during the industrial revolution. In the Industrial Era, machines didn’t steal jobs—they transformed them but people were scared about their jobs. The AI era is making similar changes except it feels like robots will take the center stage instead of a human. First off, even when it comes to the hottest space in the military - drones, Ai does a fraction of work. AI algorithms enable real-time decision-making, obstacle avoidance, and mission optimization making drones far more autonomous and capable than traditional remote-controlled aircraft. Key technologies include computer vision for object detection, GPS-enhanced navigation, and neural networks for learning and adaptation. But guess what? There are only 2 companies right now that utilize Ai in drones to make autonomous decisions - Skydio and DJI.
Wenn alles versagt - IBM Tape schützt, was zählt! Und besonders mit dem neust...
Wenn alles versagt - IBM Tape schützt, was zählt! Und besonders mit dem neust...Josef Weingand IBM LTO10
OWASP Barcelona 2025 Threat Model Library
OWASP Barcelona 2025 Threat Model LibraryPetraVukmirovic Threat Model Library Launch at OWASP Barcelona 2025
https://owasp.org/www-project-threat-model-library/
"Scaling in space and time with Temporal", Andriy Lupa.pdf
"Scaling in space and time with Temporal", Andriy Lupa.pdfFwdays Design patterns like Event Sourcing and Event Streaming have long become standards for building real-time analytics systems. However, when the system load becomes nonlinear with fast and often unpredictable spikes, it's crucial to respond quickly in order not to lose real-time operating itself.
In this talk, I’ll share my experience implementing and using a tool like Temporal.io. We'll explore the evolution of our system for maintaining real-time report generation and discuss how we use Temporal both for short-lived pipelines and long-running background tasks.
cnc-processing-centers-centateq-p-110-en.pdf
cnc-processing-centers-centateq-p-110-en.pdfAmirStern2 מרכז עיבודים תעשייתי בעל 3/4/5 צירים, עד 22 החלפות כלים עם כל אפשרויות העיבוד הדרושות. בעל שטח עבודה גדול ומחשב נוח וקל להפעלה בשפה העברית/רוסית/אנגלית/ספרדית/ערבית ועוד..
מסוגל לבצע פעולות עיבוד שונות המתאימות לענפים שונים: קידוח אנכי, אופקי, ניסור, וכרסום אנכי.
Curietech AI in action - Accelerate MuleSoft development
Curietech AI in action - Accelerate MuleSoft developmentshyamraj55 CurieTech AI in Action – Accelerate MuleSoft Development
Overview:
This presentation demonstrates how CurieTech AI’s purpose-built agents empower MuleSoft developers to create integration workflows faster, more accurately, and with less manual effort
linkedin.com
+12
curietech.ai
+12
meetups.mulesoft.com
+12
.
Key Highlights:
Dedicated AI agents for every stage: Coding, Testing (MUnit), Documentation, Code Review, and Migration
curietech.ai
+7
curietech.ai
+7
medium.com
+7
DataWeave automation: Generate mappings from tables or samples—95%+ complete within minutes
linkedin.com
+7
curietech.ai
+7
medium.com
+7
Integration flow generation: Auto-create Mule flows based on specifications—speeds up boilerplate development
curietech.ai
+1
medium.com
+1
Efficient code reviews: Gain intelligent feedback on flows, patterns, and error handling
youtube.com
+8
curietech.ai
+8
curietech.ai
+8
Test & documentation automation: Auto-generate MUnit test cases, sample data, and detailed docs from code
curietech.ai
+5
curietech.ai
+5
medium.com
+5
Why Now?
Achieve 10× productivity gains, slashing development time from hours to minutes
curietech.ai
+3
curietech.ai
+3
medium.com
+3
Maintain high accuracy with code quality matching or exceeding manual efforts
curietech.ai
+2
curietech.ai
+2
curietech.ai
+2
Ideal for developers, architects, and teams wanting to scale MuleSoft projects with AI efficiency
Conclusion:
CurieTech AI transforms MuleSoft development into an AI-accelerated workflow—letting you focus on innovation, not repetition.
PyCon SG 25 - Firecracker Made Easy with Python.pdf
PyCon SG 25 - Firecracker Made Easy with Python.pdfMuhammad Yuga Nugraha Explore the ease of managing Firecracker microVM with the firecracker-python. In this session, I will introduce the basics of Firecracker microVM and demonstrate how this custom SDK facilitates microVM operations easily. We will delve into the design and development process behind the SDK, providing a behind-the-scenes look at its creation and features. While traditional Firecracker SDKs were primarily available in Go, this module brings a simplicity of Python to the table.
Enhance GitHub Copilot using MCP - Enterprise version.pdf
Enhance GitHub Copilot using MCP - Enterprise version.pdfNilesh Gule Slide deck related to the GitHub Copilot Bootcamp in Melbourne on 17 June 2025
EIS-Webinar-Engineering-Retail-Infrastructure-06-16-2025.pdf
EIS-Webinar-Engineering-Retail-Infrastructure-06-16-2025.pdfEarley Information Science As AI reshapes expectations in retail and B2B commerce, organizations are recognizing a critical reality: meaningful AI outcomes depend on well-structured, adaptable infrastructure. In this session, Seth Earley is joined by Phil Ryan - AI strategist, search technologist, and founder of Glass Leopard Technologies - for a candid conversation on what it truly means to engineer systems for scale, agility, and intelligence.
Phil draws on more than two decades of experience leading search and AI initiatives for enterprise organizations. Together, he and Seth explore the challenges businesses face when legacy architectures limit personalization, agility, and real-time decisioning - and what needs to change to support agentic technologies and next-best-action capabilities.
Key themes from the webinar include:
Composability as a prerequisite for AI - Why modular, loosely coupled systems are essential for adapting to rapid innovation and evolving business needs
Search and relevance as foundational to AI - How techniques honed-in enterprise search have laid the groundwork for more responsive and intelligent customer experiences
From MDM and CDP to agentic systems - How data platforms are evolving to support richer customer context and dynamic orchestration
Engineering for business alignment - Why successful AI programs require architectural decisions grounded in measurable outcomes
The conversation is practical and forward-looking, connecting deep technical understanding with real-world business needs. Whether you’re modernizing your commerce stack or exploring how AI can enhance product discovery, personalization, or customer journeys, this session provides a clear-eyed view of the capabilities, constraints, and priorities that matter most.
From Manual to Auto Searching- FME in the Driver's Seat
From Manual to Auto Searching- FME in the Driver's SeatSafe Software Finding a specific car online can be a time-consuming task, especially when checking multiple dealer websites. A few years ago, I faced this exact problem while searching for a particular vehicle in New Zealand. The local classified platform, Trade Me (similar to eBay), wasn’t yielding any results, so I expanded my search to second-hand dealer sites—only to realise that periodically checking each one was going to be tedious. That’s when I noticed something interesting: many of these websites used the same platform to manage their inventories. Recognising this, I reverse-engineered the platform’s structure and built an FME workspace that automated the search process for me. By integrating API calls and setting up periodic checks, I received real-time email alerts when matching cars were listed. In this presentation, I’ll walk through how I used FME to save hours of manual searching by creating a custom car-finding automation system. While FME can’t buy a car for you—yet—it can certainly help you find the one you’re after!
Security Tips for Enterprise Azure Solutions
Security Tips for Enterprise Azure SolutionsMichele Leroux Bustamante Delivering solutions to Azure may involve a variety of architecture patterns involving your applications, APIs data and associated Azure resources that comprise the solution. This session will use reference architectures to illustrate the security considerations to protect your Azure resources and data, how to achieve Zero Trust, and why it matters. Topics covered will include specific security recommendations for types Azure resources and related network security practices. The goal is to give you a breadth of understanding as to typical security requirements to meet compliance and security controls in an enterprise solution.
You are not excused! How to avoid security blind spots on the way to production
You are not excused! How to avoid security blind spots on the way to productionMichele Leroux Bustamante
Control Freak: Risk and Control in Azure DevOps
- 1. P re s e n t e d b y Control Freak: Risk and Control in Azure DevOps Barkha Herman South Florida Code Camp ‘18
- 2. What will be covered: • Audit and Controls for Environments • Audit and Controls for Code • Audit and Controls Data at Rest • Audit and Controls Data In Motion • Monitoring and Response
- 3. Audit and Control for Environments
- 4. Some sample Controls: 1. Logical and physical Segregation of Environments 2. Lifecycle Methodology for Deployments 3. Process set for Approvals and review
- 5. Implementation 1. Use ARM Templates to create PaaS and IaaS Applications 2. Use VSTS Branch Policies to control changes to Templates 3. Use a deployment Pipeline to control Environment Changes
- 6. Use ARM Templates to deploy 1. Azure Resource Manager templates automate Deployment. 2. Creating environment becomes repeatable. 3. Creating environments can be scripted.
- 7. 1.Use VSTS for Templates 1. Use VSTS to maintain ARM Templates and standardize changes to environments. 2. Use gitflow Pull Request Process to validate and audit any changes to the environments.
- 8. 1.Use Pipelines for Deployments 1. Use Deployment Pipelines for Deployments. 2. Use SPNs for environments; devops cannot deploy directly to an environment. 3. Approvers setup for each environment – QA approvers differ from PROD approvers.
- 9. Demo…
- 10. Audit and Control for Code
- 11. Some Sample Controls 1. Code is located in a secure location 2. Access to modify code is restricted 3. Code is reviewed, tested and scanned etc. 4. Code deployment is “gated” and “Audited”
- 12. Implementation 1. Git Flow & Branch Policies in VSTS 2. Build once, deploy several for consistency 3. Deployment Pipeline with Approvals for “Gates” and audits
- 13. Git Flow + Controls 1. Use GitFlow 2. Pull Requests for Merges, required reviews and Work Items 3. Developer code lives in PR branches, merged into Develop 4. Master keeps release versions 5. Code must compile before merge to develop 6. Builds run tests, scan for issues 7. Deployments are gated
- 14. Deployment Pipelines 1. Build artifacts are created once 2. Continuous deployment ensures compile, unit tests, etc. 3. Deployment to any environment from CD requires approvals 4. Create different groups for approvals to different environments
- 15. Demo..
- 16. Audit and Controls for Data at Rest
- 17. Some Sample Controls 1. Ensure that Data is Encrypted at rest 2. Access to static data is controlled and audited 3. Ensure that Data is “Highly Available” 4. Ensure Data is Restorable, i.e. Loss Prevention 5. Ensure Data is auditable, i.e., Retention Policies
- 18. Implementation - SQL 1. TDE is available for Azure SQL. Uses Key Vault for Encryption Keys. 2. Always Encrypted Option available.
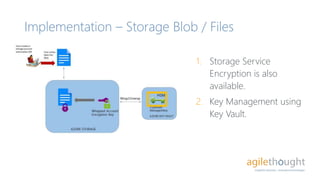
- 19. Implementation – Storage Blob / Files 1. Storage Service Encryption is also available. 2. Key Management using Key Vault.
- 20. Implementation - CosmosDB 1. Encrypted by default. 2. Backup to Blob is also encrypted.
- 21. Demo…
- 22. Audit and Control for Data in Motion
- 23. Some Sample Controls 1. All end points use TLS 2. Authentication and Authorization is Implemented 3. All communication is secure in transit – not only from client to server, but within a data center
- 24. Implementation 1. TLS is default in PaaS Services 2. ASEs can be setup web apps and web api for performance, virtual networks, isolation 3. Azure site-to-site VPN 4. Azure Point-to-site VPN 5. ExpressRoute
- 26. Some Sample Controls 1. All end points have logs for auditing. 2. All end points have monitoring available. 3. Alerts are set for disaster as well as security related events. 4. Diagnostics are available for all services.
- 27. Logging and Analysis Tools available 1. Application Insights 2. Azure Policy 3. Security Center 4. Azure Monitor 5. Others…
- 28. Demo…
- 29. Stay Connected If you have questions or would like more information, feel free to contact me via email [email protected] • www.agilethought.com • www. linkedin.com/company/AgileThought • @AgileThought
