Cross site scripting (xss) attacks issues and defense - by sandeep kumbhar
0 likes427 views
Introduction Impact of XSS attacks Types of XSS attacks Detection of XSS attacks Prevention of XSS attacks At client side At Server-side Conclusion References
1 of 16
Downloaded 11 times













![References
[1] Client-side cross-site scripting protection byEngin Kirdaa,*, Nenad Jovanovicb,
Christopher Kruegelc, Giovanni Vignac (a)Institute Eurecom, France (b) Secure
Systems Lab, Technical University Vienna, Austria (c) University of California, Santa
Barbara, USA
[2] A Server Side Solution for Protection of Web Applications from Cross-Site Scripting
Attacks A. Duraisamy, M.Sathiyamoorthy, S.Chandrasekar International Journal of
Innovative Technology and Exploring Engineering (IJITEE) ISSN: 2278 - 3075,
Volume-2, Issue-4, March 2013
[3] Prevention Of Cross-Site Scripting Attacks (XSS) On Web Applications In The Client
Side S.SHALINI, S.USHA Engineering College, Chennai- 44, Tamilnadu,
IndiaDepartment of Computer and Communication, Sri Sairam IJCSI International
Journal of Computer Science Issues, Vol. 8, Issue 4, No 1, July 2011 ISSN (Online):
1694-0814 www.IJCSI.org
[4] A Server Side Solution for Protection of Web Applications from Cross-Site Scripting
Attacks A. Duraisamy, M.Sathiyamoorthy, S.Chandrasekar
[5] Protection of Web Applications from Cross-Site Scripting Attacks in Browser Side K.
Selvamani Department of Computer Science and Engineering Anna University,
Chennai, India
Dept. of CSE, RNSIT 2012-13 14
XSS Issues and Defence](https://image.slidesharecdn.com/cross-sitescriptingxssattacksissuesanddefense-bysandeepkumbhar-190924150005/85/Cross-site-scripting-xss-attacks-issues-and-defense-by-sandeep-kumbhar-15-320.jpg)

Ad
Recommended
Cross Site Scripting(XSS)



Cross Site Scripting(XSS)Nabin Dutta Cross-site scripting (XSS) allows malicious code to be injected into web applications, potentially enabling attacks like cookie theft, account hijacking, and phishing. There are three main types of XSS attacks: reflected, stored, and DOM-based. Reflected XSS tricks the user into clicking a malicious link, while stored XSS embeds malicious code directly into the website. DOM-based XSS targets vulnerabilities in client-side scripts. XSS remains a significant threat and proper input validation and output encoding are needed to help prevent attacks.
CSRF Basics



CSRF Basicsn|u - The Open Security Community Csrf / Xsrf Basics defines CSRF as a type of web application vulnerability that allows a malicious website to send unauthorized requests to a vulnerable website using active sessions of its authorized users. CSRF tricks the victim into loading a page that contains a malicious request, which inherits the victim's identity and privileges to perform an undesired function like changing passwords. CSRF attacks target functions that cause state changes on the server but can also access sensitive data. The synchronizer token pattern is a server-side prevention technique that establishes a token on the server to validate submissions through a corresponding token in a hidden form field, marking tokens as invalid after single use.
Cross site scripting



Cross site scriptingkinish kumar Cross Site Scripting (XSS) is a type of vulnerability that allows attackers to inject client-side scripts into web pages viewed by other users. There are three main types: persistent XSS saves the attack script on the server; reflected XSS executes a script based on user-supplied input; and DOM-based XSS occurs when active browser content processes untrusted user input. Attackers use XSS to steal session cookies or other private information that can be used to impersonate users.
Cross site scripting attacks and defenses



Cross site scripting attacks and defensesMohammed A. Imran Cross-site scripting (XSS) is an injection attack where malicious scripts are injected into otherwise trusted sites. There are three main types of XSS attacks: reflected XSS occurs via URLs, stored XSS occurs when scripts are stored in a database and delivered to users, and DOM-based XSS modifies the DOM environment. XSS attacks can lead to issues like session hijacking, phishing, and port scanning. Developers can prevent XSS by validating and encoding untrusted data, and using HTTP-only and secure flags for cookies.
Cross Site Scripting



Cross Site ScriptingAli Mattash Cross-Site Scripting (XSS) is a security vulnerability that allows malicious code to be injected into web pages viewed by other users. There are three main types of XSS attacks: non-persistent reflects the user's input back without filtering; persistent stores the input and displays it later to other users; and DOM-based exploits vulnerabilities in client-side scripts. XSS attacks are used to hijack user accounts, steal cookies, and conduct phishing scams. Developers can prevent XSS by sanitizing all user input, using encoding on untrusted fields, and keeping software updated.
Cross Site Scripting ( XSS)



Cross Site Scripting ( XSS)Amit Tyagi Cross Site Scripting (XSS) is a vulnerability that allows malicious users to insert client-side code into web pages that is then executed by a user's browser. This code can steal cookies, access private information, perform actions on the user's behalf, and redirect them to malicious websites. XSS works by having the server display input containing malicious JavaScript from a request. There are different types of XSS attacks, including non-persistent, persistent, and DOM-based attacks. Prevention methods include validating, sanitizing, and escaping all user input on the server-side and client-side. Web vulnerability scanners like Burp Suite can help test for XSS and other vulnerabilities.
Deep understanding on Cross-Site Scripting and SQL Injection



Deep understanding on Cross-Site Scripting and SQL InjectionVishal Kumar This presentation will provide you the deep knowledge of the Cross-Site Scripting and SQL Injection with the remediation and prevention measures.
Cross site scripting



Cross site scriptingn|u - The Open Security Community Cross Site Scripting (XSS) is a type of injection attack where malicious scripts are injected into otherwise benign and trusted websites. XSS has been a top web application vulnerability since 1996. There are three main types of XSS attacks: reflected XSS, stored XSS, and DOM-based XSS. Reflected XSS occurs when malicious scripts come from URLs, while stored XSS happens when scripts are stored on websites. XSS can be used to steal cookies and sessions, redirect users, alter website contents, and damage an organization's reputation. Developers can prevent XSS through input validation, output encoding, and using the HttpOnly flag.
Cross-Site Scripting (XSS)



Cross-Site Scripting (XSS)Daniel Tumser Cross-Site Scripting (XSS) is a web security vulnerability that allows attackers to inject client-side scripts into web pages viewed by other users. There are three main types of XSS attacks: reflected XSS, stored XSS, and DOM-based XSS. XSS has been one of the top vulnerabilities on the OWASP Top Ten list for many years. While XSS attacks can compromise user sessions and steal sensitive data, developers can prevent XSS through proper input sanitization and output encoding. As web applications continue to grow in use, jobs in web application security and penetration testing are also expected to increase significantly in the coming years.
Cross Site Scripting Defense Presentation 



Cross Site Scripting Defense Presentation Ikhade Maro Igbape Cross site scripting (XSS) is a type of computer security vulnerability typically found in web applications, but in proposing defensive measures for cross site scripting the websites validate the user input and determine if they are vulnerable to cross site scripting. The major considerations are input validation and output sanitization.
There are lots of defense techniques introduced nowadays and even though the coding methods used by developers are evolving to counter attack cross site scripting techniques, still the security threat persist in many web applications for the following reasons:
• The complexity of implementing the codes or methods.
• Non-existence of input data validation and output sanitization in all input fields of the application.
• Lack of knowledge in identifying hidden XSS issues etc.
This proposed project report will briefly discuss what cross site scripting is and highlight the security features and defense techniques that can help against this widely versatile attack.
Reflective and Stored XSS- Cross Site Scripting



Reflective and Stored XSS- Cross Site ScriptingInMobi Technology This presentation is from Null/OWASP/G4H November Bangalore MeetUp 2014.
technology.inmobi.com/events/null-owasp-g4h-november-meetup
Talk Outline:-
A) Reflective-(Non-Persistent Cross-site Scripting)
- What is Reflective Cross-site scripting.
- Testing for Reflected Cross site scripting
How to Test
- Black Box testing
- Bypass XSS filters
- Gray Box testing
Tools
Defending Against Reflective Cross-site scripting.
Examples of Reflective Cross-Site Scripting Attacks.
B) Stored -(Persistent Cross-site Scripting)
What is Stored Cross-site scripting.
How to Test
- Black Box testing
- Gray Box testing
Tools
Defending Against Stored Cross-site scripting.
Examples of Stored Cross-Site Scripting Attacks.
XSS- an application security vulnerability



XSS- an application security vulnerabilitySoumyasanto Sen One of the most typical web application security vulnerabilities Cross-Site Scripting (XSS). What does it mean to Developer?
How they are important? What should we keep in mind? How could we prevent this to some extend as Developer? How Attackers proceed? Many mores..
The Cross Site Scripting Guide



The Cross Site Scripting GuideDaisuke_Dan The document discusses cross-site scripting (XSS) attacks, how they work, and how to prevent them. XSS attacks involve injecting malicious HTML/JavaScript code into a website that is then executed by a user's browser and can be used to steal user data. The document covers different types of XSS attacks like stored and reflected XSS and how to prevent XSS vulnerabilities through sanitizing user input and only allowing safe HTML attributes.
Xss (cross site scripting)



Xss (cross site scripting)vinayh.vaghamshi _ Cross-site scripting (XSS) is a type of vulnerability in web applications that allows attackers to inject client-side scripts. There are three main types of XSS - reflected XSS occurs when malicious scripts are included in links or requests to the server, stored XSS happens when scripts are stored on the server through forums or comments, and local XSS executes without contacting the server through PDFs or Flash. XSS can lead to compromised user accounts, denial of service attacks, or access to users' local machines. Developers can prevent XSS through input validation, encoding output, and keeping software updated.
Owasp top 10 vulnerabilities



Owasp top 10 vulnerabilitiesOWASP Delhi Session on OWASP Top 10 Vulnerabilities presented by Aarti Bala and Saman Fatima. The session covered the below 4 vulnerabilities -
Injection,
Sensitive Data Exposure
Cross Site Scripting
Insufficient Logging and Monitoring
Cross Site Scripting: Prevention and Detection(XSS)



Cross Site Scripting: Prevention and Detection(XSS)Aman Singh Cross-Site Scripting (referred to as XSS) is a type of web application attack where malicious client-side script is injected into the application output and subsequently executed by the user’s browser.
Xss attack



Xss attackManjushree Mashal An XSS attack is a type of vulnerability that allows malicious scripts to be injected into web pages viewed by other users. There are three main types: reflected XSS occurs when a link containing malicious code is clicked; stored XSS injects code directly into a vulnerable website, potentially affecting many users; DOM-based XSS involves injecting code into a website hosted on a user's local system, allowing the attacker to access that user's browser privileges. The document provides examples of how XSS attacks work and can be used to hijack accounts, insert hostile content, steal cookies, and redirect users.
Secure coding presentation Oct 3 2020



Secure coding presentation Oct 3 2020Moataz Kamel Secure coding is the practice of developing software securely by avoiding security vulnerabilities. It involves understanding the application's attack surface and using techniques like input validation, secure authentication, access control, and encrypting sensitive data. The OWASP organization provides free tools and guidelines to help developers code securely, such as their Top 10 security risks and cheat sheets on issues like injection, authentication, and access control. Developers should use static and dynamic application security testing tools to identify vulnerabilities and continuously learn about secure coding best practices.
Cross Site Scripting (XSS)



Cross Site Scripting (XSS)Barrel Software This document discusses cross-site scripting (XSS) attacks against mobile applications. It defines XSS as a type of injection where malicious scripts are injected into trusted websites. The document describes three types of XSS attacks - reflected XSS, stored XSS, and DOM-based XSS. It provides examples of each type of attack and how attackers are able to execute scripts on a victim's machine by injecting code. The document concludes with recommendations for preventing XSS attacks, including validating all input data, encoding all output data, and setting the proper character encoding.
Web security



Web securityMuhammad Usman This document discusses various aspects of web security, including the need for security when transmitting data over the internet, common security measures like authentication, authorization, encryption, and accountability. It describes techniques for securing web applications such as SSL, firewalls, VPNs. It provides details on authentication methods like basic authentication and form-based authentication. It also explains concepts like SSL certificates, VPN types, and how firewalls and SSL work.
Xss ppt



Xss pptpenetration Tester Cross-site scripting (XSS) is the most common web application vulnerability. There are three main types of XSS attacks: reflected XSS, stored XSS, and DOM-based XSS. Reflected XSS occurs when malicious scripts are included in hyperlinks and infect the victim's browser when the link is clicked. Stored XSS involves injecting malicious scripts into the application itself, which are then executed when users access stored information. DOM-based XSS modifies the DOM environment used by client-side scripts, causing them to run unexpectedly and potentially harmfully. All XSS attacks allow attackers to hijack user sessions, insert hostile content, and fully compromise users. Applications can prevent XSS by validating all input
CSRF Attack and Its Prevention technique in ASP.NET MVC



CSRF Attack and Its Prevention technique in ASP.NET MVCSuvash Shah As the name suggests Cross Site Request Forgery Attack deals with the forgery of the trusted website of an authorized user with unwanted action. . These attacks have been called the “sleeping giant” of web-based vulnerabilities, because many sites on the Internet fail to protect against them and because they have been largely ignored by the web development and security communities . Our project aims at attacking the victim user by including a link or script in a page that accesses a site to which the user is known or is supposed to have been authenticated. Deep analysis of CSRF attack and finding the possibilities to mitigate the CSRF attack is our main focus and our objective on this project.
Introduction to Cross Site Scripting ( XSS )



Introduction to Cross Site Scripting ( XSS )Irfad Imtiaz Contents :
- Introduction
- Description as A Widely Used Hacking Technique
- How it is used in Hacking
- What can be done with XSS
#XSS, #Hacking, #Security, #CookieStealing, #InternetBug, #HTMLInjection
Sincerely,
Irfad Imtiaz
OWASP Top 10 Web Application Vulnerabilities



OWASP Top 10 Web Application VulnerabilitiesSoftware Guru This document provides an overview of the OWASP Top 10 Risk Rating Methodology. It explains how risks are rated based on four factors: threat agent, attack vector, technical impact, and business impact. Each factor is given a rating of 1-3 (easy to difficult) and these ratings are multiplied together to calculate an overall weighted risk rating. An example of how this methodology would be applied to an SQL injection vulnerability is also provided.
VAPT PRESENTATION full.pptx



VAPT PRESENTATION full.pptxDARSHANBHAVSAR14 The document provides information on vulnerability assessment and penetration testing. It defines vulnerability assessment as a systematic approach to finding security issues in a network or system through manual and automated scanning. Penetration testing involves exploring and exploiting any vulnerabilities that are found to confirm their existence and potential damage. The document outlines the types of testing as blackbox, graybox, and whitebox. It also lists some common tools used for testing like Nmap, ZAP, Nikto, WPScan, and HostedScan. Finally, it provides examples of specific vulnerabilities found and their solutions, such as outdated themes/plugins, backup files being accessible, and SQL injection issues.
Top 10 Web Security Vulnerabilities (OWASP Top 10)



Top 10 Web Security Vulnerabilities (OWASP Top 10)Brian Huff The document summarizes the top 10 security vulnerabilities in web applications according to the Open Web Application Security Project (OWASP). These include injection flaws, cross-site scripting, broken authentication and session management, insecure direct object references, cross-site request forgery, security misconfiguration, insecure cryptographic storage, failure to restrict URL access, insufficient transport layer protection, and unvalidated redirects and forwards. Countermeasures for each vulnerability are also provided.
Web application security



Web application securityKapil Sharma The document discusses web application security and provides an overview of common vulnerabilities like SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF). It summarizes the OWASP Top 10 list of most critical web app security risks, including injection flaws, broken authentication, sensitive data exposure, and more. The document also offers best practices for developing more securely, like using prepared statements, validating and sanitizing input, and implementing authentication and session management properly.
Directory Traversal & File Inclusion Attacks



Directory Traversal & File Inclusion AttacksRaghav Bisht Directory traversal, also known as path traversal, allows attackers to access files and directories outside of the web server's designated root folder. This can lead to attacks like file inclusion, where malicious code is executed on the server, and source code disclosure, where sensitive application code is revealed. Local file inclusion allows attackers to include files from the local web server, while remote file inclusion includes files from external websites, potentially allowing remote code execution on the vulnerable server.
XSS: From alert(1) to crypto mining malware



XSS: From alert(1) to crypto mining malwareOmer Meshar Cross-site scripting (XSS) allows malicious scripts to be injected into otherwise benign websites. There are three main types of XSS attacks: stored, reflected, and DOM-based. Attackers use XSS to conduct activities like session hijacking, phishing, installing malware, and crypto mining. Defenses against XSS include input validation, output encoding, security headers, code reviews, and web application firewalls. XSS remains a challenging problem even with preventative measures in place.
Tracing out Cross Site Scripting Vulnerabilities in Modern Scripts



Tracing out Cross Site Scripting Vulnerabilities in Modern ScriptsEswar Publications Web Technologies were primarily designed to cater the need of ubiquitousness. The security concern has been overlooked and such overlooks resulted in vulnerabilities. These vulnerabilities are being highly exploited by hackers in various ways to compromise security. When vulnerability is blocked, the attacker traces out a different mechanism to exploit it. Cross site scripting (XSS) attack is also an exploitation of one of the vulnerabilities existing in the web applications. This paper traces out the vulnerability in functions and attributes of modern scripts to carry out cross site scripting attack and suggests preventive measures.
Ad
More Related Content
What's hot (20)
Cross-Site Scripting (XSS)



Cross-Site Scripting (XSS)Daniel Tumser Cross-Site Scripting (XSS) is a web security vulnerability that allows attackers to inject client-side scripts into web pages viewed by other users. There are three main types of XSS attacks: reflected XSS, stored XSS, and DOM-based XSS. XSS has been one of the top vulnerabilities on the OWASP Top Ten list for many years. While XSS attacks can compromise user sessions and steal sensitive data, developers can prevent XSS through proper input sanitization and output encoding. As web applications continue to grow in use, jobs in web application security and penetration testing are also expected to increase significantly in the coming years.
Cross Site Scripting Defense Presentation 



Cross Site Scripting Defense Presentation Ikhade Maro Igbape Cross site scripting (XSS) is a type of computer security vulnerability typically found in web applications, but in proposing defensive measures for cross site scripting the websites validate the user input and determine if they are vulnerable to cross site scripting. The major considerations are input validation and output sanitization.
There are lots of defense techniques introduced nowadays and even though the coding methods used by developers are evolving to counter attack cross site scripting techniques, still the security threat persist in many web applications for the following reasons:
• The complexity of implementing the codes or methods.
• Non-existence of input data validation and output sanitization in all input fields of the application.
• Lack of knowledge in identifying hidden XSS issues etc.
This proposed project report will briefly discuss what cross site scripting is and highlight the security features and defense techniques that can help against this widely versatile attack.
Reflective and Stored XSS- Cross Site Scripting



Reflective and Stored XSS- Cross Site ScriptingInMobi Technology This presentation is from Null/OWASP/G4H November Bangalore MeetUp 2014.
technology.inmobi.com/events/null-owasp-g4h-november-meetup
Talk Outline:-
A) Reflective-(Non-Persistent Cross-site Scripting)
- What is Reflective Cross-site scripting.
- Testing for Reflected Cross site scripting
How to Test
- Black Box testing
- Bypass XSS filters
- Gray Box testing
Tools
Defending Against Reflective Cross-site scripting.
Examples of Reflective Cross-Site Scripting Attacks.
B) Stored -(Persistent Cross-site Scripting)
What is Stored Cross-site scripting.
How to Test
- Black Box testing
- Gray Box testing
Tools
Defending Against Stored Cross-site scripting.
Examples of Stored Cross-Site Scripting Attacks.
XSS- an application security vulnerability



XSS- an application security vulnerabilitySoumyasanto Sen One of the most typical web application security vulnerabilities Cross-Site Scripting (XSS). What does it mean to Developer?
How they are important? What should we keep in mind? How could we prevent this to some extend as Developer? How Attackers proceed? Many mores..
The Cross Site Scripting Guide



The Cross Site Scripting GuideDaisuke_Dan The document discusses cross-site scripting (XSS) attacks, how they work, and how to prevent them. XSS attacks involve injecting malicious HTML/JavaScript code into a website that is then executed by a user's browser and can be used to steal user data. The document covers different types of XSS attacks like stored and reflected XSS and how to prevent XSS vulnerabilities through sanitizing user input and only allowing safe HTML attributes.
Xss (cross site scripting)



Xss (cross site scripting)vinayh.vaghamshi _ Cross-site scripting (XSS) is a type of vulnerability in web applications that allows attackers to inject client-side scripts. There are three main types of XSS - reflected XSS occurs when malicious scripts are included in links or requests to the server, stored XSS happens when scripts are stored on the server through forums or comments, and local XSS executes without contacting the server through PDFs or Flash. XSS can lead to compromised user accounts, denial of service attacks, or access to users' local machines. Developers can prevent XSS through input validation, encoding output, and keeping software updated.
Owasp top 10 vulnerabilities



Owasp top 10 vulnerabilitiesOWASP Delhi Session on OWASP Top 10 Vulnerabilities presented by Aarti Bala and Saman Fatima. The session covered the below 4 vulnerabilities -
Injection,
Sensitive Data Exposure
Cross Site Scripting
Insufficient Logging and Monitoring
Cross Site Scripting: Prevention and Detection(XSS)



Cross Site Scripting: Prevention and Detection(XSS)Aman Singh Cross-Site Scripting (referred to as XSS) is a type of web application attack where malicious client-side script is injected into the application output and subsequently executed by the user’s browser.
Xss attack



Xss attackManjushree Mashal An XSS attack is a type of vulnerability that allows malicious scripts to be injected into web pages viewed by other users. There are three main types: reflected XSS occurs when a link containing malicious code is clicked; stored XSS injects code directly into a vulnerable website, potentially affecting many users; DOM-based XSS involves injecting code into a website hosted on a user's local system, allowing the attacker to access that user's browser privileges. The document provides examples of how XSS attacks work and can be used to hijack accounts, insert hostile content, steal cookies, and redirect users.
Secure coding presentation Oct 3 2020



Secure coding presentation Oct 3 2020Moataz Kamel Secure coding is the practice of developing software securely by avoiding security vulnerabilities. It involves understanding the application's attack surface and using techniques like input validation, secure authentication, access control, and encrypting sensitive data. The OWASP organization provides free tools and guidelines to help developers code securely, such as their Top 10 security risks and cheat sheets on issues like injection, authentication, and access control. Developers should use static and dynamic application security testing tools to identify vulnerabilities and continuously learn about secure coding best practices.
Cross Site Scripting (XSS)



Cross Site Scripting (XSS)Barrel Software This document discusses cross-site scripting (XSS) attacks against mobile applications. It defines XSS as a type of injection where malicious scripts are injected into trusted websites. The document describes three types of XSS attacks - reflected XSS, stored XSS, and DOM-based XSS. It provides examples of each type of attack and how attackers are able to execute scripts on a victim's machine by injecting code. The document concludes with recommendations for preventing XSS attacks, including validating all input data, encoding all output data, and setting the proper character encoding.
Web security



Web securityMuhammad Usman This document discusses various aspects of web security, including the need for security when transmitting data over the internet, common security measures like authentication, authorization, encryption, and accountability. It describes techniques for securing web applications such as SSL, firewalls, VPNs. It provides details on authentication methods like basic authentication and form-based authentication. It also explains concepts like SSL certificates, VPN types, and how firewalls and SSL work.
Xss ppt



Xss pptpenetration Tester Cross-site scripting (XSS) is the most common web application vulnerability. There are three main types of XSS attacks: reflected XSS, stored XSS, and DOM-based XSS. Reflected XSS occurs when malicious scripts are included in hyperlinks and infect the victim's browser when the link is clicked. Stored XSS involves injecting malicious scripts into the application itself, which are then executed when users access stored information. DOM-based XSS modifies the DOM environment used by client-side scripts, causing them to run unexpectedly and potentially harmfully. All XSS attacks allow attackers to hijack user sessions, insert hostile content, and fully compromise users. Applications can prevent XSS by validating all input
CSRF Attack and Its Prevention technique in ASP.NET MVC



CSRF Attack and Its Prevention technique in ASP.NET MVCSuvash Shah As the name suggests Cross Site Request Forgery Attack deals with the forgery of the trusted website of an authorized user with unwanted action. . These attacks have been called the “sleeping giant” of web-based vulnerabilities, because many sites on the Internet fail to protect against them and because they have been largely ignored by the web development and security communities . Our project aims at attacking the victim user by including a link or script in a page that accesses a site to which the user is known or is supposed to have been authenticated. Deep analysis of CSRF attack and finding the possibilities to mitigate the CSRF attack is our main focus and our objective on this project.
Introduction to Cross Site Scripting ( XSS )



Introduction to Cross Site Scripting ( XSS )Irfad Imtiaz Contents :
- Introduction
- Description as A Widely Used Hacking Technique
- How it is used in Hacking
- What can be done with XSS
#XSS, #Hacking, #Security, #CookieStealing, #InternetBug, #HTMLInjection
Sincerely,
Irfad Imtiaz
OWASP Top 10 Web Application Vulnerabilities



OWASP Top 10 Web Application VulnerabilitiesSoftware Guru This document provides an overview of the OWASP Top 10 Risk Rating Methodology. It explains how risks are rated based on four factors: threat agent, attack vector, technical impact, and business impact. Each factor is given a rating of 1-3 (easy to difficult) and these ratings are multiplied together to calculate an overall weighted risk rating. An example of how this methodology would be applied to an SQL injection vulnerability is also provided.
VAPT PRESENTATION full.pptx



VAPT PRESENTATION full.pptxDARSHANBHAVSAR14 The document provides information on vulnerability assessment and penetration testing. It defines vulnerability assessment as a systematic approach to finding security issues in a network or system through manual and automated scanning. Penetration testing involves exploring and exploiting any vulnerabilities that are found to confirm their existence and potential damage. The document outlines the types of testing as blackbox, graybox, and whitebox. It also lists some common tools used for testing like Nmap, ZAP, Nikto, WPScan, and HostedScan. Finally, it provides examples of specific vulnerabilities found and their solutions, such as outdated themes/plugins, backup files being accessible, and SQL injection issues.
Top 10 Web Security Vulnerabilities (OWASP Top 10)



Top 10 Web Security Vulnerabilities (OWASP Top 10)Brian Huff The document summarizes the top 10 security vulnerabilities in web applications according to the Open Web Application Security Project (OWASP). These include injection flaws, cross-site scripting, broken authentication and session management, insecure direct object references, cross-site request forgery, security misconfiguration, insecure cryptographic storage, failure to restrict URL access, insufficient transport layer protection, and unvalidated redirects and forwards. Countermeasures for each vulnerability are also provided.
Web application security



Web application securityKapil Sharma The document discusses web application security and provides an overview of common vulnerabilities like SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF). It summarizes the OWASP Top 10 list of most critical web app security risks, including injection flaws, broken authentication, sensitive data exposure, and more. The document also offers best practices for developing more securely, like using prepared statements, validating and sanitizing input, and implementing authentication and session management properly.
Directory Traversal & File Inclusion Attacks



Directory Traversal & File Inclusion AttacksRaghav Bisht Directory traversal, also known as path traversal, allows attackers to access files and directories outside of the web server's designated root folder. This can lead to attacks like file inclusion, where malicious code is executed on the server, and source code disclosure, where sensitive application code is revealed. Local file inclusion allows attackers to include files from the local web server, while remote file inclusion includes files from external websites, potentially allowing remote code execution on the vulnerable server.
Similar to Cross site scripting (xss) attacks issues and defense - by sandeep kumbhar (20)
XSS: From alert(1) to crypto mining malware



XSS: From alert(1) to crypto mining malwareOmer Meshar Cross-site scripting (XSS) allows malicious scripts to be injected into otherwise benign websites. There are three main types of XSS attacks: stored, reflected, and DOM-based. Attackers use XSS to conduct activities like session hijacking, phishing, installing malware, and crypto mining. Defenses against XSS include input validation, output encoding, security headers, code reviews, and web application firewalls. XSS remains a challenging problem even with preventative measures in place.
Tracing out Cross Site Scripting Vulnerabilities in Modern Scripts



Tracing out Cross Site Scripting Vulnerabilities in Modern ScriptsEswar Publications Web Technologies were primarily designed to cater the need of ubiquitousness. The security concern has been overlooked and such overlooks resulted in vulnerabilities. These vulnerabilities are being highly exploited by hackers in various ways to compromise security. When vulnerability is blocked, the attacker traces out a different mechanism to exploit it. Cross site scripting (XSS) attack is also an exploitation of one of the vulnerabilities existing in the web applications. This paper traces out the vulnerability in functions and attributes of modern scripts to carry out cross site scripting attack and suggests preventive measures.
Cross Site Scripting Attacks and Preventive Measures



Cross Site Scripting Attacks and Preventive MeasuresIRJET Journal This document summarizes cross-site scripting (XSS) attacks and preventive measures. It discusses that XSS attacks allow attackers to inject malicious scripts into web pages through inputs like search fields or comment boxes. There are three main types of XSS attacks: non-persistent reflect XSS through query parameters, persistent stored XSS by storing scripts on servers, and DOM-based XSS using document object model functions. Input validation and code filtering are effective preventive measures. The document also proposes a script filtering algorithm to sanitize inputs and prevent execution of malicious scripts.
tas-s6-software-engineering-slide-deck-secure-software-architecture.pptx



tas-s6-software-engineering-slide-deck-secure-software-architecture.pptxMostafa Taghizade about secure software architecture
Software Security Engineering



Software Security EngineeringMarco Morana The document discusses approaches to building secure web applications, including establishing software security processes and maturity levels. It covers security activities like threat modeling, defining security requirements, secure coding standards, security testing, and metrics. Business cases for software security focus on reducing costs of vulnerabilities, threats to web apps, and root causes being application vulnerabilities and design flaws.
Analysis of XSS attack Mitigation techniques based on Platforms and Browsers



Analysis of XSS attack Mitigation techniques based on Platforms and Browserscscpconf In the recent years, everything is in web. It may be Organization’s administration software,
Custom ERP application, Employee portals or Real estate portals. The Social networking sites
like Face book, Twitter, MySpace which is a web application is been used by millions of users
around the world. So web applications have become very popular among users. Hence they are
observed and may be exploited by hackers. Researchers and industry experts state that the
Cross-site Scripting (XSS) is the one of the top most vulnerabilities in the web application. The
cross-site scripting has become a common vulnerability of many web sites and web
applications. XSS consists in the exploitation of input validation flaws, with the purpose of
injecting arbitrary script code which is later executed at the web browser of the victim.
According to OSWAP, Cross-site scripting attacks on web applications have experienced an
important rise in recent year. This demands an efficient approach on the server side to protect
the users of the application as the reason for the vulnerability primarily lies on the server side.
The actual exploitation is within the victim’s web browser on the client-side. Therefore, an
operator of a web application has only very limited evidence of XSS issues. However, there are
many solutions for this vulnerability. But such techniques may degrade the performance of the
system. In such scenarios challenge is to decide which method, platform, browser and
middleware can be used to overcome the vulnerabilities, with reasonable performance over
head to the system. Inspired by this problem, we present performance comparison of two mitigation techniques for Cross-site Scripting (XSS) at the server side based on the parameters like application’s platform, middleware technology and browser used by the end user. We implemented Mitigation parsing technique using database and replace technique in different platforms, middleware and checked its performance. We calculated the time taken by different browsers to render the pages using two techniques under different platform and middleware. In this paper we proposed the best combination of development platform, browser and the middleware for the two mitigation technique with respect to developer and end users.
XSS filter on Server side



XSS filter on Server sidecuteboysmith project for the final year of engineering
.to create a signature based model on server side
to prevent XSS attacks
Security in the cloud protecting your cloud apps



Security in the cloud protecting your cloud appsCenzic The document discusses security best practices for cloud applications. It notes that 75% of cyber attacks target internet applications and over 400 new vulnerabilities are discovered each month. The top vulnerabilities include cross-site scripting, SQL injection, and insecure direct object references. The document provides examples of how these vulnerabilities can be exploited by hackers and recommends best practices like input validation, output encoding, secure authentication and session management to help protect applications.
IRJET- A Survey on Various Cross-Site Scripting Attacks and Few Prevention Ap...



IRJET- A Survey on Various Cross-Site Scripting Attacks and Few Prevention Ap...IRJET Journal This document discusses cross-site scripting (XSS) attacks and methods to prevent them. It describes different types of XSS attacks, including reflected, stored, DOM-based, and induced XSS. It also outlines several existing prevention approaches, such as input validation, output encoding, and firewalls. The document then proposes a method to detect base64-encoded malicious scripts by decoding the input, applying a regular expression to detect attack vectors, and properly escaping any detected scripts. Overall, the document provides an overview of XSS attacks and compares limitations of common prevention techniques, concluding with a proposed approach to enhance defenses against base64 obfuscated XSS scripts.
Application Security Architecture and Threat Modelling



Application Security Architecture and Threat ModellingPriyanka Aash 95% of attacks are against “Web Servers and Web Applications”
Security Architecture and SDLC
3 Tier – Web App Architecture
Would you trust the code?
Traditional SDLC
Secure SDLC
SAST vs. DAST
C01461422



C01461422IOSR Journals This document discusses secure web application development and preventing common vulnerabilities. It begins with an introduction on why web applications are often vulnerable and the importance of secure development. It then provides details on secure development lifecycles and practices, describes top vulnerabilities like injection flaws and cross-site scripting, and provides guidance on how to prevent each vulnerability through practices like input validation, output encoding, and access controls. The goal is to help developers understand security risks and how to build more robust applications through secure coding and threat modeling.
Study of Cross-Site Scripting Attacks and Their Countermeasures



Study of Cross-Site Scripting Attacks and Their CountermeasuresEditor IJCATR In present-day time, most of the associations are making use of web services for improved services to their
clients. With the upturn in count of web users, there is a considerable hike in the web attacks. Thus, security becomes
the dominant matter in web applications. The disparate kind of vulnerabilities resulted in the disparate types of attacks.
The attackers may take benefit of these vulnerabilities and can misuse the data in the database. Study indicates that
more than 80% of the web applications are vulnerable to cross-site scripting (XSS) attacks. XSS is one of the fatal
attacks & it has been practiced over the maximum number of well-known search engines and social sites. In this paper,
we have considered XSS attacks, its types and different methods employed to resist these attacks with their
corresponding limitations. Additionally, we have discussed the proposed approach for countering XSS attack and how
this approach is superior to others.
Web security 2010



Web security 2010Alok Babu This document discusses software security and common vulnerabilities in web applications such as SQL injection and cross-site scripting (XSS). It explains that SQL injection exploits vulnerabilities in database applications by injecting malicious SQL code via user input, while XSS injects client-side scripts by storing malicious code in websites. The document demonstrates how these attacks work and can be used to steal sensitive data or inject malware onto users' computers. It emphasizes the importance of validating, sanitizing, and escaping all user input to prevent such vulnerabilities.
ImageSubXSS: an image substitute technique to prevent Cross-Site Scripting at...



ImageSubXSS: an image substitute technique to prevent Cross-Site Scripting at...IJECEIAES Cross-Site Scripting (XSS) is one of serious web application attack. Web applications are involved in every activity of human life. JavaScript plays a major role in these web applications. In XSS attacks hacker inject malicious JavaScript into a trusted web application, execution of that malicious script may steal sensitive information from the user. Previous solutions to prevent XSS attacks require a lot of effort to integrate into existing web applications, some solutions works at client-side and some solutions works based on filter list which needs to be updated regularly. In this paper, we propose an Image Substitute technique (ImageSubXSS) to prevent Cross-Site Scripting attacks which works at the server-side. The proposed solution is implemented and evaluated on a number of XSS attacks. With a single line, developers can integrate ImageSubXSS into their applications and the proposed solution is able to prevent XSS attacks effectively.
XSS-Alert-Pentration testing tool



XSS-Alert-Pentration testing toolArjun Jain This document summarizes a presentation on cross-site scripting (XSS) attacks and the XSS Alert tool. It defines XSS as enabling attackers to inject client-side scripts into web pages. It describes three types of XSS attacks and provides an example of a reflected XSS attack. It also discusses DOM security, how XSS Alert works to detect XSS vulnerabilities, and demonstrates an XSS attack on a Yahoo server.
Discovering the Value of Verifying Web Application Security Using IBM Rationa...



Discovering the Value of Verifying Web Application Security Using IBM Rationa...Alan Kan The document discusses a workshop on web application security using IBM Rational AppScan. It introduces the importance of securing web applications and provides an overview of common vulnerabilities like cross-site scripting and SQL injection. The workshop aims to help attendees understand application security risks and how to use AppScan to automate vulnerability scanning and analysis. Hands-on labs are included to demonstrate AppScan's vulnerability detection capabilities.
OWASP Top 10 And Insecure Software Root Causes



OWASP Top 10 And Insecure Software Root CausesMarco Morana This document discusses common web application vulnerabilities and their root causes. It provides an overview of the OWASP Top 10 list of vulnerabilities, describing each vulnerability type, how attackers exploit them, examples of insecure code that enables the vulnerabilities, and recommendations for secure coding practices to prevent the vulnerabilities. Specific vulnerabilities covered include cross-site scripting, SQL injection, malicious file execution, insecure direct object references, cross-site request forgery, and information leakage from error handling. The document emphasizes the importance of following secure coding standards and input validation to prevent vulnerabilities.
Web application security I



Web application security IMd Syed Ahamad This document summarizes a presentation on web application security. It discusses common web application vulnerabilities like injection flaws, broken authentication, cross-site scripting, and more. It covers the OWASP top 10 list of risks and provides examples to illustrate injection attacks, cross-site scripting bugs, and how vulnerabilities can be prevented through practices like input validation, output encoding, and using vulnerability scanners. The goal is to both prevent vulnerabilities and implement detection mechanisms for web applications.
Cross Site Scripting (XSS)



Cross Site Scripting (XSS)Avi Aryan Cross-site scripting (XSS) is a type of computer security vulnerability that enables attackers to inject client-side scripts into web pages viewed by other users. There are two types: reflected XSS involves including malicious code in a URL link, while stored XSS embeds malicious code directly into a website database. To prevent XSS attacks, developers should validate, escape, and sanitize all user input before displaying it. For example, by filtering HTML tags and encoding special characters. An infamous example is a 2005 MySpace XSS worm that spread to millions of users by automatically adding anyone who visited an infected profile as a friend.
Prevention of Cross-Site Scripting using Hash Technique



Prevention of Cross-Site Scripting using Hash TechniqueIJCSIS Research Publications Cookies are the mechanisms that maintain an
authentication state between the user and web application.
Therefore cookies are the possible targets for the attackers. Cross
Site Scripting (XSS) attack is one of such attacks against the web
applications in which a user has to compromise its browser’s
resources (e.g. cookies). In this paper, a novel technique of
SHA_512 Hash Technique is introduced whose aim is to make
cookies worthless for the attackers. The work done in HTTP
protocol with windows10.
Ad
Recently uploaded (19)
Top Vancouver Green Business Ideas for 2025 Powered by 4GoodHosting



Top Vancouver Green Business Ideas for 2025 Powered by 4GoodHostingsteve198109 Vancouver in 2025 is more than scenic views, yoga studios, and oat milk lattes—it’s a thriving hub for eco-conscious entrepreneurs looking to make a real difference. If you’ve ever dreamed of launching a purpose-driven business, now is the time. Whether it’s urban mushroom farming, upcycled furniture sales, or vegan skincare sold online, your green idea deserves a strong digital foundation.
The 2025 Canadian eCommerce landscape is being shaped by trends like sustainability, local innovation, and consumer trust. To stay ahead, eco-startups need reliable hosting that aligns with their values. That’s where 4GoodHosting.com comes in—one of the top-rated Vancouver web hosting providers of 2025. Offering secure, sustainable, and Canadian-based hosting solutions, they help green entrepreneurs build their brand with confidence and conscience.
As eCommerce in Canada embraces localism and environmental responsibility, choosing a hosting provider that shares your vision is essential. 4GoodHosting goes beyond just hosting websites—they champion Canadian businesses, sustainable practices, and meaningful growth.
So go ahead—start that eco-friendly venture. With Vancouver web hosting from 4GoodHosting, your green business and your values are in perfect sync.
IT Services Workflow From Request to Resolution



IT Services Workflow From Request to Resolutionmzmziiskd IT Services Workflow From Request to Resolution
Best web hosting Vancouver 2025 for you business



Best web hosting Vancouver 2025 for you businesssteve198109 Vancouver in 2025 is more than scenic views, yoga studios, and oat milk lattes—it’s a thriving hub for eco-conscious entrepreneurs looking to make a real difference. If you’ve ever dreamed of launching a purpose-driven business, now is the time. Whether it’s urban mushroom farming, upcycled furniture sales, or vegan skincare sold online, your green idea deserves a strong digital foundation.
The 2025 Canadian eCommerce landscape is being shaped by trends like sustainability, local innovation, and consumer trust. To stay ahead, eco-startups need reliable hosting that aligns with their values. That’s where 4GoodHosting.com comes in—one of the top-rated Vancouver web hosting providers of 2025. Offering secure, sustainable, and Canadian-based hosting solutions, they help green entrepreneurs build their brand with confidence and conscience.
As eCommerce in Canada embraces localism and environmental responsibility, choosing a hosting provider that shares your vision is essential. 4GoodHosting goes beyond just hosting websites—they champion Canadian businesses, sustainable practices, and meaningful growth.
So go ahead—start that eco-friendly venture. With Vancouver web hosting from 4GoodHosting, your green business and your values are in perfect sync.
Reliable Vancouver Web Hosting with Local Servers & 24/7 Support



Reliable Vancouver Web Hosting with Local Servers & 24/7 Supportsteve198109 Looking for powerful and affordable web hosting in Vancouver? 4GoodHosting offers premium Canadian web hosting solutions designed specifically for individuals, startups, and businesses across British Columbia. With local data centers in Vancouver and Toronto, we ensure blazing-fast website speeds, superior uptime, and enhanced data privacy—all critical for your business success in today’s competitive digital landscape.
Our Vancouver web hosting plans are packed with value—starting as low as $2.95/month—and include secure cPanel management, free domain transfer, one-click WordPress installs, and robust email support with anti-spam protection. Whether you're hosting a personal blog, business website, or eCommerce store, our scalable cloud hosting packages are built to grow with you.
Enjoy enterprise-grade features like daily backups, DDoS protection, free SSL certificates, and unlimited bandwidth on select plans. Plus, our expert Canadian support team is available 24/7 to help you every step of the way.
At 4GoodHosting, we understand the needs of local Vancouver businesses. That’s why we focus on speed, security, and service—all hosted on Canadian soil. Start your online journey today with a reliable hosting partner trusted by thousands across Canada.
APNIC Update, presented at NZNOG 2025 by Terry Sweetser



APNIC Update, presented at NZNOG 2025 by Terry SweetserAPNIC Terry Sweetser, Training Delivery Manager (South Asia & Oceania) at APNIC presented an APNIC update at NZNOG 2025 held in Napier, New Zealand from 9 to 11 April 2025.
APNIC -Policy Development Process, presented at Local APIGA Taiwan 2025



APNIC -Policy Development Process, presented at Local APIGA Taiwan 2025APNIC Joyce Chen, Senior Advisor, Strategic Engagement at APNIC, presented on 'APNIC Policy Development Process' at the Local APIGA Taiwan 2025 event held in Taipei from 19 to 20 April 2025.
highend-srxseries-services-gateways-customer-presentation.pptx



highend-srxseries-services-gateways-customer-presentation.pptxelhadjcheikhdiop Juniper High End Series
Perguntas dos animais - Slides ilustrados de múltipla escolha



Perguntas dos animais - Slides ilustrados de múltipla escolhasocaslev Slides ilustrados de múltipla escolha
DNS Resolvers and Nameservers (in New Zealand)



DNS Resolvers and Nameservers (in New Zealand)APNIC Geoff Huston, Chief Scientist at APNIC, presented on 'DNS Resolvers and Nameservers in New Zealand' at NZNOG 2025 held in Napier, New Zealand from 9 to 11 April 2025.
Smart Mobile App Pitch Deck丨AI Travel App Presentation Template



Smart Mobile App Pitch Deck丨AI Travel App Presentation Templateyojeari421237 🚀 Smart Mobile App Pitch Deck – "Trip-A" | AI Travel App Presentation Template
This professional, visually engaging pitch deck is designed specifically for developers, startups, and tech students looking to present a smart travel mobile app concept with impact.
Whether you're building an AI-powered travel planner or showcasing a class project, Trip-A gives you the edge to impress investors, professors, or clients. Every slide is cleanly structured, fully editable, and tailored to highlight key aspects of a mobile travel app powered by artificial intelligence and real-time data.
💼 What’s Inside:
- Cover slide with sleek app UI preview
- AI/ML module implementation breakdown
- Key travel market trends analysis
- Competitor comparison slide
- Evaluation challenges & solutions
- Real-time data training model (AI/ML)
- “Live Demo” call-to-action slide
🎨 Why You'll Love It:
- Professional, modern layout with mobile app mockups
- Ideal for pitches, hackathons, university presentations, or MVP launches
- Easily customizable in PowerPoint or Google Slides
- High-resolution visuals and smooth gradients
📦 Format:
- PPTX / Google Slides compatible
- 16:9 widescreen
- Fully editable text, charts, and visuals
Mobile database for your company telemarketing or sms marketing campaigns. Fr...



Mobile database for your company telemarketing or sms marketing campaigns. Fr...DataProvider1 Why Mobile Database Services are Important: Powering the Future of Mobile Applications
Understanding the Tor Network and Exploring the Deep Web



Understanding the Tor Network and Exploring the Deep Webnabilajabin35 While the Tor network, Dark Web, and Deep Web can seem mysterious and daunting, they are simply parts of the internet that prioritize privacy and anonymity. Using tools like Ahmia and onionland search, users can explore these hidden spaces responsibly and securely. It’s essential to understand the technology behind these networks, as well as the risks involved, to navigate them safely. Visit https://torgol.com/
Ad
Cross site scripting (xss) attacks issues and defense - by sandeep kumbhar
- 1. Cross-Site Scripting (XSS) Attacks Issues and Defense by Sandeep Kumbhar M. Tech CSE, R N S I T Bangalore
- 2. Contents Introduction Impact of XSS attacks Types of XSS attacks Detection of XSS attacks Prevention of XSS attacks At client side At Server side Conclusion References Dept. of CSE, RNSIT 2012-13 1 XSS Issues and Defence
- 3. Introduction What is XSS attack? Why it is popular? Inputs for XSS attacks? Dept. of CSE, RNSIT 2012-13 2 XSS Issues and Defence
- 4. Impact of XSS attack Access to authentication credentials for Web application Cookies, Username and Password XSS is not a harmless flaw Normal users Access to personal data (Credit card, Bank Account) Misuse account (order expensive goods) Denial-of-Service Crash User’s Browser, Pop-Up-Flooding, Redirection Access to user’s machine Use ActiveX objects to control machine Upload local data to attacker's machine Spoil public image of company Load main frame content from other locations Dept. of CSE, RNSIT 2012-13 4 XSS Issues and Defence
- 5. Types of XSS Attacks Dept. of CSE, RNSIT 2012-13 3 Non-persistent or Reflected Cross-Site Scripting attacks Persistent or Stored Cross-Site Scripting attacks DOM based Cross-Site Scripting attacks XSS Issues and Defence
- 6. Reflected XSS Attacks Attacker provided script is embedded in the web page generated by the server as an immediate response of an HTTP request. Dept. of CSE, RNSIT 2012-13 5 http://myserver.com/test.jsp?name=Stefan <HTML> <Body> Welcome Stefan </Body> </HTML> XSS Issues and Defence
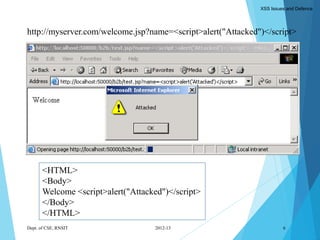
- 7. Dept. of CSE, RNSIT 2012-13 6 http://myserver.com/welcome.jsp?name=<script>alert("Attacked")</script> <HTML> <Body> Welcome <script>alert("Attacked")</script> </Body> </HTML> XSS Issues and Defence
- 8. Stored XSS Attacks Attacker provided script is stored to a database and later retrieved and embedded in the web page generated by the server Dept. of CSE, RNSIT 2012-13 7 XSS Issues and Defence
- 9. Dept. of CSE, RNSIT 2012-13 8 Unvalidated Input resulted in a Cross-Site Scripting Attack and the theft of the Administrator’s Cookie XSS Issues and Defence
- 10. Detection Of XSS Check if special characters are encoded <XSS> vs. <XSS> Check if a double quote escape can be evaded <script>alert(String.fromCharCode(88, 83, 83));<script> Check if script can be executed <script>alert(“XSS”)</script> Dept. of CSE, RNSIT 2012-13 9 XSS Issues and Defence
- 11. Detection Of XSS Cont.. Check if input filtering can be evaded <SCRIPT>alert("XSS");//</SCRIPT> Denial of service <script>alert(document.cookie);</script>article.php?title= <meta%20httpequiv="refresh"%20content="0;"> Dept. of CSE, RNSIT 2012-13 10 XSS Issues and Defence
- 12. Prevention of XSS Attacks - At Client/Browser Side Dept. of CSE, RNSIT 2012-13 11 XSS Issues and Defence Figure: Architecture for Cross-Site Scripting in Browser side
- 13. Prevention of XSS Attacks - At Server Side Dept. of CSE, RNSIT 2012-13 12 XSS Issues and Defence Figure: Architecture for Cross-Site Scripting in Server side
- 14. Conclusion Dept. of CSE, RNSIT 2012-13 13 XSS Issues and Defence Always practice using testing tools during the design phase to eliminate XSS holes in the application. Input validation and HTML escaping are essential, yet that must be applied at all application points accepting data. There is a misconception sometimes applied to XSS holes in general which leads to a disagreement in the security community as to the importance of cross-site scripting vulnerabilities. XSS-Prevention Best Practices Implement XSS-Prevention in application Do not assume input values are always good Do not trust client side validation Check and validate all input before processing Do not echo any input value without validation Use one conceptual solution in all applications
- 15. References [1] Client-side cross-site scripting protection byEngin Kirdaa,*, Nenad Jovanovicb, Christopher Kruegelc, Giovanni Vignac (a)Institute Eurecom, France (b) Secure Systems Lab, Technical University Vienna, Austria (c) University of California, Santa Barbara, USA [2] A Server Side Solution for Protection of Web Applications from Cross-Site Scripting Attacks A. Duraisamy, M.Sathiyamoorthy, S.Chandrasekar International Journal of Innovative Technology and Exploring Engineering (IJITEE) ISSN: 2278 - 3075, Volume-2, Issue-4, March 2013 [3] Prevention Of Cross-Site Scripting Attacks (XSS) On Web Applications In The Client Side S.SHALINI, S.USHA Engineering College, Chennai- 44, Tamilnadu, IndiaDepartment of Computer and Communication, Sri Sairam IJCSI International Journal of Computer Science Issues, Vol. 8, Issue 4, No 1, July 2011 ISSN (Online): 1694-0814 www.IJCSI.org [4] A Server Side Solution for Protection of Web Applications from Cross-Site Scripting Attacks A. Duraisamy, M.Sathiyamoorthy, S.Chandrasekar [5] Protection of Web Applications from Cross-Site Scripting Attacks in Browser Side K. Selvamani Department of Computer Science and Engineering Anna University, Chennai, India Dept. of CSE, RNSIT 2012-13 14 XSS Issues and Defence
- 16. Thank You.!






