Cryptography and Network Security_Chapter 1.ppt
Download as PPT, PDF0 likes93 views
This document discusses key concepts in internet security. It defines computer, network, and internet security. It outlines the ITU-T X.800 standard for defining security requirements and describes security attacks, services, and mechanisms. Finally, it discusses models for implementing network security including cryptographic techniques and access controls.
1 of 21
Download to read offline




















Ad
Recommended
Unit 1.ppt



Unit 1.pptDHANABALSUBRAMANIAN This document discusses cryptography and network security. It defines computer, network, and internet security and outlines the OSI security architecture. It describes security attacks, services, and mechanisms. Specifically, it distinguishes between passive and active attacks and examines authentication, access control, data confidentiality, data integrity, and non-repudiation as security services. Finally, it presents models for providing network and network access security that utilize cryptographic techniques and access controls.
ch01-4.ppt



ch01-4.pptfaizalkhan673954 This chapter introduces key concepts in cryptography and network security. It defines computer, network, and internet security and discusses security attacks, services, and mechanisms. The chapter presents models for providing network security and controlling network access security using cryptographic techniques and trusted systems. The overall aim is to understand measures for protecting data transmission and storage.
Nw sec



Nw secshivz3 This chapter introduces key concepts in cryptography and network security. It defines computer, network, and internet security and discusses security attacks, services, and mechanisms. The chapter presents models for providing network security and controlling network access security using cryptographic techniques and trusted systems. The overall aim is to understand measures for protecting data transmission and storage.
osi-security-architectureppt.pptx



osi-security-architectureppt.pptxkumarkaushal17 This document provides an overview of cryptography and network security concepts. It defines computer, network, and internet security and states the aim is on internet security. It discusses the OSI security architecture standard, aspects of security including attacks, services, and mechanisms. It describes passive and active attacks and examples of security services and mechanisms. Finally, it presents models for network security and network access security.
Ch01



Ch01Joe Christensen This document summarizes key concepts in cryptography and network security. It defines computer, network, and internet security and outlines security services, mechanisms, and common attacks. The document discusses the OSI security architecture and how it defines five major security services: authentication, access control, data confidentiality, data integrity, and non-repudiation. It also summarizes security mechanisms and how to classify security attacks as either passive or active. The document introduces models for network security and network access security and discusses requirements for implementing these models, such as designing encryption algorithms and distributing secret keys.
Network security chapter 1



Network security chapter 1osama elfar The document provides an overview of cryptography and network security concepts. It describes the key objectives of studying this topic as understanding security requirements like confidentiality, integrity, and availability. It also discusses types of security threats and attacks. The document summarizes the main cryptographic algorithms and security architecture. It defines security services like authentication, access control, data confidentiality, and data integrity. It also discusses security mechanisms, threats, and attacks in network security.
cns unit 1.pptx



cns unit 1.pptxSaranya Natarajan The document outlines the syllabus for a course on cryptography and network security. It discusses key topics that will be covered including cryptographic algorithms, network security concepts, security services, security mechanisms, and types of security attacks. The goal is for students to understand the fundamentals of network security and how to apply cryptographic techniques and authentication schemes to secure applications and networks.
ch01.ppt



ch01.pptssuser4198c4 Cryptography and Network Security introduces key concepts in information security. It discusses security services like authentication and confidentiality, mechanisms like encryption, and attacks like interception of data. The course will focus on internet security and cryptographic techniques. It presents models for providing security during data transmission and for controlling network access. The goal is a systematic approach to defining security requirements and countering different types of threats.
CH01.ppt



CH01.pptShahidMehmood285010 This document provides an overview of cryptography and network security. It outlines the key topics to be covered, including cryptographic algorithms, network security concepts, and security standards organizations. The document also summarizes the OSI security architecture, defining security attacks, services, and mechanisms. Models for providing network and access security are presented which require selecting algorithms, distributing keys, and specifying protocols for security services.
Computer Security



Computer Securitywhbwi21Basri This document defines key terms related to computer, network, and internet security. It discusses three main aspects of information security: security attacks, security mechanisms, and security services. Security attacks are any actions that compromise security, security mechanisms are used to detect, prevent, and recover from attacks, and security services enhance security of data processing and transfer. The document also classifies security attacks as either passive (like interception) or active (like modification), and presents a model for network access security using gatekeeper functions to identify users and controls to authorize access.
Ch01



Ch01ssusere796b3 Cryptography and Network Security introduces key concepts in information security. It discusses (1) definitions of computer, network, and internet security, (2) the relationship between security services, mechanisms, and attacks, and (3) models for providing network and access security. The goal is to provide a systematic framework for defining security requirements and considering how cryptographic techniques can be used to detect, prevent, and recover from security attacks during data transmission.
Network security - OSI Security Architecture



Network security - OSI Security ArchitectureBharathiKrishna6 The OSI Security Architecture provides a systematic framework for defining security attacks, mechanism, and services.
COMPUTER SECURITY



COMPUTER SECURITYSHUBHA CHATURVEDI This document discusses computer security and defines key related terms. It defines computer security as protecting systems to maintain integrity, availability, and confidentiality of information. It also discusses concepts like data confidentiality, privacy, data integrity, system integrity, and availability. Additional concepts discussed are authenticity, accountability, and the OSI security architecture which focuses on security attacks, mechanisms, and services.
Cyber Security Part-I.pptx



Cyber Security Part-I.pptxRavikumarVadana The document provides an overview of the internet, including its history and evolution. It discusses how the internet began as ARPANET in 1959 and transitioned to use packet switching. It also describes common internet devices, security threats like interruption and modification, and security services like authentication, integrity, and availability. The roles of organizations in internet standardization are outlined, as well as common attacks like buffer overflows, format string vulnerabilities, and session hijacking.
امن نظم المعلومات وامن الشبكات



امن نظم المعلومات وامن الشبكاتAmr Rashed This document provides an overview of information security topics including:
- Types of security attacks such as those from internal and external attackers.
- Key security concepts like confidentiality, integrity, and availability.
- Examples of security violations involving unauthorized access or modification of files.
- The importance of considering security attacks, mechanisms, and services as major axes in network security.
dokumen.tips_1-cryptography-and-network-security-third-edition-by-william-sta...



dokumen.tips_1-cryptography-and-network-security-third-edition-by-william-sta...NISHASOMSCS113 This document provides an overview of cryptography and network security. It defines key terms like computer security, network security, and internet security. It describes common security attacks like eavesdropping, tampering, fabrication, and denial of service. It also outlines security services, security mechanisms, and the OSI security architecture. The document models network security and network access security.
Computer Security Chapter 1



Computer Security Chapter 1Temesgen Berhanu This document provides an introduction to information security concepts. It defines information security as protecting information and systems from unauthorized access, use, disclosure, disruption or destruction. The key aspects of information security are confidentiality, integrity and availability. Basic security terminology like identification, authentication, access control and confidentiality are explained. Common network vulnerabilities like weak passwords, protocol design flaws, and unauthorized access through modems are also discussed. The importance of network security is to protect company assets, gain competitive advantage and ensure regulatory compliance.
Lecture-01,02-1 Information security introduction.ppt



Lecture-01,02-1 Information security introduction.pptNasirAli233814 Information security introduction, cryptography, encryption Decryption
Basics -1.pptx kiy fdest xfderwe dgdar d



Basics -1.pptx kiy fdest xfderwe dgdar dSoundaryaBC2 X.800 defines a security service as a protocol layer service that ensures system and data transfer security in open systems. RFC 4949 defines it as a service providing specific protection to system resources, implementing security policies through security mechanisms.
X.800 defines a security service iyew gt



X.800 defines a security service iyew gtSoundaryaBC2 X.800 defines a security service as a protocol layer service that ensures system and data transfer security in open systems. RFC 4949 defines it as a service providing specific protection to system resources, implementing security policies through security mechanisms.
CRYPTOGRAPHY & NETWORK SECURITY



CRYPTOGRAPHY & NETWORK SECURITYJyothishmathi Institute of Technology and Science Karimnagar This document provides an overview of a university course on Cryptography and Network Security. It begins with the course syllabus, which outlines topics like security concepts, cryptography concepts and techniques, and types of security attacks. It then discusses key security concepts such as security services, security mechanisms, security attacks, and models for network and access security. It provides examples of security services like authentication, access control, and data confidentiality. It also describes security mechanisms and different classes of security attacks. The document concludes by listing reference books, online videos, related courses, tutorials, and sample multiple choice and problems related to cryptography and network security.
Introduction to security



Introduction to securityMukesh Chinta This ppt contains information about definition of computer & information security, types of attacks, services, mechanisms, controls and model for network security
Security Ch-1.pptx



Security Ch-1.pptxKeenboonAsaffaa This document provides an overview of network and information security. It discusses key concepts like the OSI security architecture, security attacks, mechanisms, and services. It explains why security is important to protect company assets, gain competitive advantages, comply with regulations, and ensure job security. The security trinity of prevention, detection, and response is also explained. Basic security terminology is defined, including authentication, access control, confidentiality, availability, data integrity, accountability, and non-repudiation. Finally, it discusses what a security policy is and its importance.
Intro-2013.pptIntro-2013.pptIntro-2013.ppt



Intro-2013.pptIntro-2013.pptIntro-2013.ppttahirnaquash2 This document provides an overview of a university course on network and computer security. It outlines the course structure, including topics on cryptography, network security concepts, and laboratory exercises. It also defines key security terms like threats, attacks, security services, and security mechanisms.
Introduction to Network security



Introduction to Network securitymohanad alobaidey This document provides an overview of network security concepts including:
- Types of network security such as access control, application security, email security, and wireless security.
- Security attacks are classified as either passive (eavesdropping) or active (modifying data).
- Security mechanisms are designed to detect, prevent, or recover from security attacks using techniques like cryptography.
- Security services enhance system protection by using mechanisms to counter attacks and replicate functions of physical documents.
- Defense methods include encryption, software/hardware controls, policies, and physical controls.
ch01.ppt University of Education Lahore D



ch01.ppt University of Education Lahore DMuhammadShan87 Cyber Security Of Crypto Graphy
University of Education Lahore Pakistan
Module 3.pdf



Module 3.pdfSitamarhi Institute of Technology This document provides an overview of various topics related to cyber security including infrastructure and network security, system security, server security, operating system (OS) security, physical security, network packet sniffing, network design simulation, denial of service (DOS) and distributed denial of service (DDOS) attacks, asset management and audits, intrusion detection and prevention techniques, host-based intrusion prevention systems, security information management, network session analysis, system integrity validation, and some open-source, free and trial tools that can be used for security purposes like DOS/DDOS attacks, packet sniffing, firewalls, and intrusion detection.
Aptitude question tricks_Shanthi prabha R.pdf



Aptitude question tricks_Shanthi prabha R.pdfshanthishyam Tricks of Mathematics Exam Question, find the LCM,HCM, Factorization,Cube root trick, Find time and work calculations, Codingand Decoding, Number Analogy
Ad
More Related Content
Similar to Cryptography and Network Security_Chapter 1.ppt (20)
CH01.ppt



CH01.pptShahidMehmood285010 This document provides an overview of cryptography and network security. It outlines the key topics to be covered, including cryptographic algorithms, network security concepts, and security standards organizations. The document also summarizes the OSI security architecture, defining security attacks, services, and mechanisms. Models for providing network and access security are presented which require selecting algorithms, distributing keys, and specifying protocols for security services.
Computer Security



Computer Securitywhbwi21Basri This document defines key terms related to computer, network, and internet security. It discusses three main aspects of information security: security attacks, security mechanisms, and security services. Security attacks are any actions that compromise security, security mechanisms are used to detect, prevent, and recover from attacks, and security services enhance security of data processing and transfer. The document also classifies security attacks as either passive (like interception) or active (like modification), and presents a model for network access security using gatekeeper functions to identify users and controls to authorize access.
Ch01



Ch01ssusere796b3 Cryptography and Network Security introduces key concepts in information security. It discusses (1) definitions of computer, network, and internet security, (2) the relationship between security services, mechanisms, and attacks, and (3) models for providing network and access security. The goal is to provide a systematic framework for defining security requirements and considering how cryptographic techniques can be used to detect, prevent, and recover from security attacks during data transmission.
Network security - OSI Security Architecture



Network security - OSI Security ArchitectureBharathiKrishna6 The OSI Security Architecture provides a systematic framework for defining security attacks, mechanism, and services.
COMPUTER SECURITY



COMPUTER SECURITYSHUBHA CHATURVEDI This document discusses computer security and defines key related terms. It defines computer security as protecting systems to maintain integrity, availability, and confidentiality of information. It also discusses concepts like data confidentiality, privacy, data integrity, system integrity, and availability. Additional concepts discussed are authenticity, accountability, and the OSI security architecture which focuses on security attacks, mechanisms, and services.
Cyber Security Part-I.pptx



Cyber Security Part-I.pptxRavikumarVadana The document provides an overview of the internet, including its history and evolution. It discusses how the internet began as ARPANET in 1959 and transitioned to use packet switching. It also describes common internet devices, security threats like interruption and modification, and security services like authentication, integrity, and availability. The roles of organizations in internet standardization are outlined, as well as common attacks like buffer overflows, format string vulnerabilities, and session hijacking.
امن نظم المعلومات وامن الشبكات



امن نظم المعلومات وامن الشبكاتAmr Rashed This document provides an overview of information security topics including:
- Types of security attacks such as those from internal and external attackers.
- Key security concepts like confidentiality, integrity, and availability.
- Examples of security violations involving unauthorized access or modification of files.
- The importance of considering security attacks, mechanisms, and services as major axes in network security.
dokumen.tips_1-cryptography-and-network-security-third-edition-by-william-sta...



dokumen.tips_1-cryptography-and-network-security-third-edition-by-william-sta...NISHASOMSCS113 This document provides an overview of cryptography and network security. It defines key terms like computer security, network security, and internet security. It describes common security attacks like eavesdropping, tampering, fabrication, and denial of service. It also outlines security services, security mechanisms, and the OSI security architecture. The document models network security and network access security.
Computer Security Chapter 1



Computer Security Chapter 1Temesgen Berhanu This document provides an introduction to information security concepts. It defines information security as protecting information and systems from unauthorized access, use, disclosure, disruption or destruction. The key aspects of information security are confidentiality, integrity and availability. Basic security terminology like identification, authentication, access control and confidentiality are explained. Common network vulnerabilities like weak passwords, protocol design flaws, and unauthorized access through modems are also discussed. The importance of network security is to protect company assets, gain competitive advantage and ensure regulatory compliance.
Lecture-01,02-1 Information security introduction.ppt



Lecture-01,02-1 Information security introduction.pptNasirAli233814 Information security introduction, cryptography, encryption Decryption
Basics -1.pptx kiy fdest xfderwe dgdar d



Basics -1.pptx kiy fdest xfderwe dgdar dSoundaryaBC2 X.800 defines a security service as a protocol layer service that ensures system and data transfer security in open systems. RFC 4949 defines it as a service providing specific protection to system resources, implementing security policies through security mechanisms.
X.800 defines a security service iyew gt



X.800 defines a security service iyew gtSoundaryaBC2 X.800 defines a security service as a protocol layer service that ensures system and data transfer security in open systems. RFC 4949 defines it as a service providing specific protection to system resources, implementing security policies through security mechanisms.
CRYPTOGRAPHY & NETWORK SECURITY



CRYPTOGRAPHY & NETWORK SECURITYJyothishmathi Institute of Technology and Science Karimnagar This document provides an overview of a university course on Cryptography and Network Security. It begins with the course syllabus, which outlines topics like security concepts, cryptography concepts and techniques, and types of security attacks. It then discusses key security concepts such as security services, security mechanisms, security attacks, and models for network and access security. It provides examples of security services like authentication, access control, and data confidentiality. It also describes security mechanisms and different classes of security attacks. The document concludes by listing reference books, online videos, related courses, tutorials, and sample multiple choice and problems related to cryptography and network security.
Introduction to security



Introduction to securityMukesh Chinta This ppt contains information about definition of computer & information security, types of attacks, services, mechanisms, controls and model for network security
Security Ch-1.pptx



Security Ch-1.pptxKeenboonAsaffaa This document provides an overview of network and information security. It discusses key concepts like the OSI security architecture, security attacks, mechanisms, and services. It explains why security is important to protect company assets, gain competitive advantages, comply with regulations, and ensure job security. The security trinity of prevention, detection, and response is also explained. Basic security terminology is defined, including authentication, access control, confidentiality, availability, data integrity, accountability, and non-repudiation. Finally, it discusses what a security policy is and its importance.
Intro-2013.pptIntro-2013.pptIntro-2013.ppt



Intro-2013.pptIntro-2013.pptIntro-2013.ppttahirnaquash2 This document provides an overview of a university course on network and computer security. It outlines the course structure, including topics on cryptography, network security concepts, and laboratory exercises. It also defines key security terms like threats, attacks, security services, and security mechanisms.
Introduction to Network security



Introduction to Network securitymohanad alobaidey This document provides an overview of network security concepts including:
- Types of network security such as access control, application security, email security, and wireless security.
- Security attacks are classified as either passive (eavesdropping) or active (modifying data).
- Security mechanisms are designed to detect, prevent, or recover from security attacks using techniques like cryptography.
- Security services enhance system protection by using mechanisms to counter attacks and replicate functions of physical documents.
- Defense methods include encryption, software/hardware controls, policies, and physical controls.
ch01.ppt University of Education Lahore D



ch01.ppt University of Education Lahore DMuhammadShan87 Cyber Security Of Crypto Graphy
University of Education Lahore Pakistan
Module 3.pdf



Module 3.pdfSitamarhi Institute of Technology This document provides an overview of various topics related to cyber security including infrastructure and network security, system security, server security, operating system (OS) security, physical security, network packet sniffing, network design simulation, denial of service (DOS) and distributed denial of service (DDOS) attacks, asset management and audits, intrusion detection and prevention techniques, host-based intrusion prevention systems, security information management, network session analysis, system integrity validation, and some open-source, free and trial tools that can be used for security purposes like DOS/DDOS attacks, packet sniffing, firewalls, and intrusion detection.
More from shanthishyam (12)
Aptitude question tricks_Shanthi prabha R.pdf



Aptitude question tricks_Shanthi prabha R.pdfshanthishyam Tricks of Mathematics Exam Question, find the LCM,HCM, Factorization,Cube root trick, Find time and work calculations, Codingand Decoding, Number Analogy
C&NS_FIREWALLS.ppt



C&NS_FIREWALLS.pptshanthishyam This document discusses network security and firewalls. It describes how firewalls provide perimeter defense and control access between interconnected networks. Several types of firewalls are mentioned, including packet filtering firewalls, stateful firewalls, application-level gateways, and proxies. The document also briefly discusses access control models, multilevel security models like Bell-LaPadula, and security evaluation standards such as Common Criteria.
TOKEN BUS & TOKEN RING.ppt



TOKEN BUS & TOKEN RING.pptshanthishyam The document discusses IEEE 802 subgroups and local area network (LAN) technologies such as token bus and token ring. It provides details on:
- IEEE 802 subgroups and their responsibilities for various networking standards
- How token passing works on token bus and token ring networks, with stations passing a token frame that allows the holder to transmit data
- Standards such as IEEE 802.4 for token bus and IEEE 802.5 for token ring
- Key aspects of token ring and token bus networks, including frame formats, priority schemes, and how data is transmitted and errors are handled.
SINGLE SOURCE SHORTEST PATH.ppt



SINGLE SOURCE SHORTEST PATH.pptshanthishyam This document discusses several algorithms for finding single-source shortest paths in graphs:
1) Bellman-Ford algorithm can handle graphs with negative edge weights by detecting negative cycles. It runs in O(VE) time.
2) For directed acyclic graphs (DAGs), topological sorting followed by relaxation yields the shortest paths from a single source in O(V+E) time.
3) Dijkstra's algorithm uses a greedy approach to find single-source shortest paths in graphs with non-negative edge weights.
FDS- Basic Concepts.ppt



FDS- Basic Concepts.pptshanthishyam Requirements
Analysis: bottom-up vs. top-down
Design: data objects and operations
Refinement and Coding
Verification
Program Proving
Testing
Debugging
Three dimensional geometric transformations



Three dimensional geometric transformationsshanthishyam This document discusses 3D geometric transformations in OpenGL, including translation, rotation, and scaling. It provides the mathematical definitions and matrix representations for transformations around the X, Y, and Z axes as well as arbitrary axes. It also covers combining multiple transformations through matrix multiplication and the order of transformations. OpenGL functions for common transformations like glTranslate, glRotate, and glScale are also presented.
OSI reference model



OSI reference modelshanthishyam The document discusses the OSI reference model and TCP/IP reference model.
The OSI model has 7 layers - physical, data link, network, transport, session, presentation and application layer. Each layer performs a well-defined function with minimal information flow across layer boundaries.
The TCP/IP model has 4 layers - link, internet, transport and application. The internet layer uses IP to allow packets to independently travel across networks. Transport layer uses TCP for reliable connections and UDP for fast delivery. Application layer contains protocols like HTTP, FTP, SMTP.
Database concepts



Database conceptsshanthishyam This document discusses database concepts and security models. It covers relational database concepts like tables, relations, attributes, tuples, primary keys and foreign keys. It then discusses security requirements for databases like physical integrity, logical integrity, element integrity, auditability, access control and availability. It describes the SQL security model of users, actions, objects, privileges and views. It also covers weaknesses of the discretionary access control model and alternatives like mandatory access controls.
Curve modeling



Curve modelingshanthishyam This document discusses different types of spline curves used for modeling, including polynomial splines, interpolation splines, and approximation splines. It describes linear spline interpolation which uses linear polynomials to pass through control points. Cubic spline interpolation is discussed next, using cubic polynomials and additional constraints to determine coefficients. Natural cubic splines are described as satisfying C2 continuity across knots. Hermit splines are introduced as allowing local control of tangents at endpoints. Blending functions for Hermit splines are provided.
Cryptography and network security



Cryptography and network securityshanthishyam This document discusses symmetric encryption techniques in cryptography and network security. Symmetric encryption, also called conventional or secret-key encryption, involves a sender and recipient sharing a common key to encrypt plaintext into ciphertext and decrypt ciphertext back into plaintext. The document defines basic terminology related to symmetric encryption techniques, including plaintext, ciphertext, cipher, key, encryption, decryption, cryptography, cryptanalysis, and cryptology.
Computer networks



Computer networksshanthishyam This document discusses different types of computer networks at various scales, from personal area networks to wide area networks and the Internet. It describes the key characteristics of different network types, including transmission technologies, scale, examples of wireless and wired local area networks, metropolitan area networks, and wide area networks. The document also discusses topics like virtual private networks, Internet service providers, and how networks have evolved to connect individuals and organizations globally.
Ad
Recently uploaded (20)
How to Set warnings for invoicing specific customers in odoo



How to Set warnings for invoicing specific customers in odooCeline George Odoo 16 offers a powerful platform for managing sales documents and invoicing efficiently. One of its standout features is the ability to set warnings and block messages for specific customers during the invoicing process.
How to Customize Your Financial Reports & Tax Reports With Odoo 17 Accounting



How to Customize Your Financial Reports & Tax Reports With Odoo 17 AccountingCeline George The Accounting module in Odoo 17 is a complete tool designed to manage all financial aspects of a business. Odoo offers a comprehensive set of tools for generating financial and tax reports, which are crucial for managing a company's finances and ensuring compliance with tax regulations.
Michelle Rumley & Mairéad Mooney, Boole Library, University College Cork. Tra...



Michelle Rumley & Mairéad Mooney, Boole Library, University College Cork. Tra...Library Association of Ireland
Geography Sem II Unit 1C Correlation of Geography with other school subjects



Geography Sem II Unit 1C Correlation of Geography with other school subjectsProfDrShaikhImran The correlation of school subjects refers to the interconnectedness and mutual reinforcement between different academic disciplines. This concept highlights how knowledge and skills in one subject can support, enhance, or overlap with learning in another. Recognizing these correlations helps in creating a more holistic and meaningful educational experience.
SCI BIZ TECH QUIZ (OPEN) PRELIMS XTASY 2025.pptx



SCI BIZ TECH QUIZ (OPEN) PRELIMS XTASY 2025.pptxRonisha Das SCI BIZ TECH QUIZ (OPEN) PRELIMS - XTASY 2025
CBSE - Grade 8 - Science - Chemistry - Metals and Non Metals - Worksheet



CBSE - Grade 8 - Science - Chemistry - Metals and Non Metals - WorksheetSritoma Majumder Introduction
All the materials around us are made up of elements. These elements can be broadly divided into two major groups:
Metals
Non-Metals
Each group has its own unique physical and chemical properties. Let's understand them one by one.
Physical Properties
1. Appearance
Metals: Shiny (lustrous). Example: gold, silver, copper.
Non-metals: Dull appearance (except iodine, which is shiny).
2. Hardness
Metals: Generally hard. Example: iron.
Non-metals: Usually soft (except diamond, a form of carbon, which is very hard).
3. State
Metals: Mostly solids at room temperature (except mercury, which is a liquid).
Non-metals: Can be solids, liquids, or gases. Example: oxygen (gas), bromine (liquid), sulphur (solid).
4. Malleability
Metals: Can be hammered into thin sheets (malleable).
Non-metals: Not malleable. They break when hammered (brittle).
5. Ductility
Metals: Can be drawn into wires (ductile).
Non-metals: Not ductile.
6. Conductivity
Metals: Good conductors of heat and electricity.
Non-metals: Poor conductors (except graphite, which is a good conductor).
7. Sonorous Nature
Metals: Produce a ringing sound when struck.
Non-metals: Do not produce sound.
Chemical Properties
1. Reaction with Oxygen
Metals react with oxygen to form metal oxides.
These metal oxides are usually basic.
Non-metals react with oxygen to form non-metallic oxides.
These oxides are usually acidic.
2. Reaction with Water
Metals:
Some react vigorously (e.g., sodium).
Some react slowly (e.g., iron).
Some do not react at all (e.g., gold, silver).
Non-metals: Generally do not react with water.
3. Reaction with Acids
Metals react with acids to produce salt and hydrogen gas.
Non-metals: Do not react with acids.
4. Reaction with Bases
Some non-metals react with bases to form salts, but this is rare.
Metals generally do not react with bases directly (except amphoteric metals like aluminum and zinc).
Displacement Reaction
More reactive metals can displace less reactive metals from their salt solutions.
Uses of Metals
Iron: Making machines, tools, and buildings.
Aluminum: Used in aircraft, utensils.
Copper: Electrical wires.
Gold and Silver: Jewelry.
Zinc: Coating iron to prevent rusting (galvanization).
Uses of Non-Metals
Oxygen: Breathing.
Nitrogen: Fertilizers.
Chlorine: Water purification.
Carbon: Fuel (coal), steel-making (coke).
Iodine: Medicines.
Alloys
An alloy is a mixture of metals or a metal with a non-metal.
Alloys have improved properties like strength, resistance to rusting.
Introduction to Vibe Coding and Vibe Engineering



Introduction to Vibe Coding and Vibe EngineeringDamian T. Gordon Introduction to Vibe Coding and Vibe Engineering
Social Problem-Unemployment .pptx notes for Physiotherapy Students



Social Problem-Unemployment .pptx notes for Physiotherapy StudentsDrNidhiAgarwal Unemployment is a major social problem, by which not only rural population have suffered but also urban population are suffered while they are literate having good qualification.The evil consequences like poverty, frustration, revolution
result in crimes and social disorganization. Therefore, it is
necessary that all efforts be made to have maximum.
employment facilities. The Government of India has already
announced that the question of payment of unemployment
allowance cannot be considered in India
One Hot encoding a revolution in Machine learning



One Hot encoding a revolution in Machine learningmomer9505 A brief introduction to ONE HOT encoding a way to communicate with machines
Quality Contril Analysis of Containers.pdf



Quality Contril Analysis of Containers.pdfDr. Bindiya Chauhan Quality control test for containers, rubber closures and secondary packing materials.
How to Manage Opening & Closing Controls in Odoo 17 POS



How to Manage Opening & Closing Controls in Odoo 17 POSCeline George In Odoo 17 Point of Sale, the opening and closing controls are key for cash management. At the start of a shift, cashiers log in and enter the starting cash amount, marking the beginning of financial tracking. Throughout the shift, every transaction is recorded, creating an audit trail.
To study the nervous system of insect.pptx



To study the nervous system of insect.pptxArshad Shaikh The *nervous system of insects* is a complex network of nerve cells (neurons) and supporting cells that process and transmit information. Here's an overview:
Structure
1. *Brain*: The insect brain is a complex structure that processes sensory information, controls behavior, and integrates information.
2. *Ventral nerve cord*: A chain of ganglia (nerve clusters) that runs along the insect's body, controlling movement and sensory processing.
3. *Peripheral nervous system*: Nerves that connect the central nervous system to sensory organs and muscles.
Functions
1. *Sensory processing*: Insects can detect and respond to various stimuli, such as light, sound, touch, taste, and smell.
2. *Motor control*: The nervous system controls movement, including walking, flying, and feeding.
3. *Behavioral responThe *nervous system of insects* is a complex network of nerve cells (neurons) and supporting cells that process and transmit information. Here's an overview:
Structure
1. *Brain*: The insect brain is a complex structure that processes sensory information, controls behavior, and integrates information.
2. *Ventral nerve cord*: A chain of ganglia (nerve clusters) that runs along the insect's body, controlling movement and sensory processing.
3. *Peripheral nervous system*: Nerves that connect the central nervous system to sensory organs and muscles.
Functions
1. *Sensory processing*: Insects can detect and respond to various stimuli, such as light, sound, touch, taste, and smell.
2. *Motor control*: The nervous system controls movement, including walking, flying, and feeding.
3. *Behavioral responses*: Insects can exhibit complex behaviors, such as mating, foraging, and social interactions.
Characteristics
1. *Decentralized*: Insect nervous systems have some autonomy in different body parts.
2. *Specialized*: Different parts of the nervous system are specialized for specific functions.
3. *Efficient*: Insect nervous systems are highly efficient, allowing for rapid processing and response to stimuli.
The insect nervous system is a remarkable example of evolutionary adaptation, enabling insects to thrive in diverse environments.
The insect nervous system is a remarkable example of evolutionary adaptation, enabling insects to thrive
K12 Tableau Tuesday - Algebra Equity and Access in Atlanta Public Schools



K12 Tableau Tuesday - Algebra Equity and Access in Atlanta Public Schoolsdogden2 Algebra 1 is often described as a “gateway” class, a pivotal moment that can shape the rest of a student’s K–12 education. Early access is key: successfully completing Algebra 1 in middle school allows students to complete advanced math and science coursework in high school, which research shows lead to higher wages and lower rates of unemployment in adulthood.
Learn how The Atlanta Public Schools is using their data to create a more equitable enrollment in middle school Algebra classes.
Operations Management (Dr. Abdulfatah Salem).pdf



Operations Management (Dr. Abdulfatah Salem).pdfArab Academy for Science, Technology and Maritime Transport This version of the lectures is provided free of charge to graduate students studying the Operations Management course at the MBA level.
Handling Multiple Choice Responses: Fortune Effiong.pptx



Handling Multiple Choice Responses: Fortune Effiong.pptxAuthorAIDNationalRes INTRO TO STATISTICS
INTRO TO SPSS INTERFACE
CLEANING MULTIPLE CHOICE RESPONSE DATA WITH EXCEL
ANALYZING MULTIPLE CHOICE RESPONSE DATA
INTERPRETATION
Q & A SESSION
PRACTICAL HANDS-ON ACTIVITY
Marie Boran Special Collections Librarian Hardiman Library, University of Gal...



Marie Boran Special Collections Librarian Hardiman Library, University of Gal...Library Association of Ireland Phoenix – A Collaborative Renewal of Children’s and Young People’s Services Clare Doyle - Cork City Libraries
World war-1(Causes & impacts at a glance) PPT by Simanchala Sarab(BABed,sem-4...



World war-1(Causes & impacts at a glance) PPT by Simanchala Sarab(BABed,sem-4...larencebapu132 This is short and accurate description of World war-1 (1914-18)
It can give you the perfect factual conceptual clarity on the great war
Regards Simanchala Sarab
Student of BABed(ITEP, Secondary stage)in History at Guru Nanak Dev University Amritsar Punjab 🙏🙏
To study Digestive system of insect.pptx



To study Digestive system of insect.pptxArshad Shaikh Education is one thing no one can take away from you.”
Michelle Rumley & Mairéad Mooney, Boole Library, University College Cork. Tra...



Michelle Rumley & Mairéad Mooney, Boole Library, University College Cork. Tra...Library Association of Ireland
Operations Management (Dr. Abdulfatah Salem).pdf



Operations Management (Dr. Abdulfatah Salem).pdfArab Academy for Science, Technology and Maritime Transport
Marie Boran Special Collections Librarian Hardiman Library, University of Gal...



Marie Boran Special Collections Librarian Hardiman Library, University of Gal...Library Association of Ireland
Ad
Cryptography and Network Security_Chapter 1.ppt
- 1. R.SHANTHI PRABHA M.Sc., M.Phil., ASSISTANT PROFESSOR DEPARTMENT OF COMPUTER SCIENCE SACWC, CUMBUM
- 2. Information Security requirements have changed in recent times traditionally provided by physical and administrative mechanisms computer use requires automated tools to protect files and other stored information use of networks and communications links requires measures to protect data during transmission
- 3. Computer Security - generic name for the collection of tools designed to protect data and to thwart hackers Network Security - measures to protect data during their transmission Internet Security - measures to protect data during their transmission over a collection of interconnected networks
- 4. our focus is on Internet Security which consists of measures to deter, prevent, detect, and correct security violations that involve the transmission & storage of information
- 6. ITU-T X.800 “Security Architecture for OSI” defines a systematic way of defining and providing security requirements for us it provides a useful, if abstract, overview of concepts we will study
- 7. consider 3 aspects of information security: security attack security mechanism security service
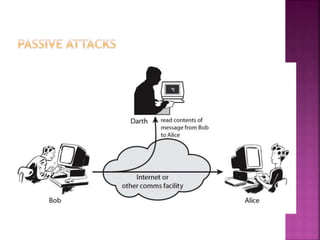
- 8. any action that compromises the security of information owned by an organization information security is about how to prevent attacks, or failing that, to detect attacks on information-based systems often threat & attack used to mean same thing have a wide range of attacks can focus of generic types of attacks passive active
- 11. enhance security of data processing systems and information transfers of an organization intended to counter security attacks using one or more security mechanisms often replicates functions normally associated with physical documents which, for example, have signatures, dates; need protection from disclosure, tampering, or destruction; be notarized or witnessed; be recorded or licensed
- 12. X.800: “a service provided by a protocol layer of communicating open systems, which ensures adequate security of the systems or of data transfers” RFC 2828: “a processing or communication service provided by a system to give a specific kind of protection to system resources”
- 13. Authentication - assurance that the communicating entity is the one claimed Access Control - prevention of the unauthorized use of a resource Data Confidentiality –protection of data from unauthorized disclosure Data Integrity - assurance that data received is as sent by an authorized entity Non-Repudiation - protection against denial by one of the parties in a communication
- 14. feature designed to detect, prevent, or recover from a security attack no single mechanism that will support all services required however one particular element underlies many of the security mechanisms in use: cryptographic techniques hence our focus on this topic
- 15. specific security mechanisms: encipherment, digital signatures, access controls, data integrity, authentication exchange, traffic padding, routing control, notarization pervasive security mechanisms: trusted functionality, security labels, event detection, security audit trails, security recovery
- 17. using this model requires us to: 1. design a suitable algorithm for the security transformation 2. generate the secret information (keys) used by the algorithm 3. develop methods to distribute and share the secret information 4. specify a protocol enabling the principals to use the transformation and secret information for a security service
- 19. using this model requires us to: 1. select appropriate gatekeeper functions to identify users 2. implement security controls to ensure only authorised users access designated information or resources trusted computer systems may be useful to help implement this model
- 20. have considered: definitions for: computer, network, internet security X.800 standard security attacks, services, mechanisms models for network (access) security



