Ad
Cryptography With PHP - ZendCon 2017 Workshop
- 1. CRYPTOGRAPHY WITH PHP MARK NIEBERGALL ZendCon 2017 Workshop https://joind.in/talk/7b305
- 2. CRYPTOGRAPHY WITH PHP ABOUT MARK NIEBERGALL ▸ PHP since 2005 ▸ Masters degree in MIS ▸ Senior Software Engineer ▸ Drug screening project ▸ UPHPU President ▸ SSCP, CSSLP Certified and SME ▸ Drones, fishing, skiing, father, husband
- 3. CRYPTOGRAPHY WITH PHP ABOUT MARK NIEBERGALL
- 4. CRYPTOGRAPHY WITH PHP ABOUT MARK NIEBERGALL
- 5. CRYPTOGRAPHY WITH PHP ABOUT MARK NIEBERGALL
- 6. CRYPTOGRAPHY WITH PHP OBJECTIVES ▸ Time on the keyboard ▸ Learn about and use PHP cryptography and hashing libraries ▸ Security considerations with implementation
- 7. CRYPTOGRAPHY WITH PHP OBJECTIVES ▸ Coding time! ▸ Various modules ▸ Estimated time (5, 10, or 15 minutes) ▸ Cryptography games will apply what was covered
- 8. CRYPTOGRAPHY WITH PHP SCHEDULE ▸ 9:00-9:30 Setup and covering slides that including terminology and cryptography ▸ 9:30-9:50 PHP hash, password hashing ▸ 9:50-10:00 Break, lock picking ▸ 10:00-10:50 CSPRNG, OpenSSL ▸ 10:50-11:00 Break, more lock picking ▸ 11:00-11:15 libsodium ▸ 11:15-11:55 Cryptography Games ▸ 11:55-12:00 Regroup and conclusion
- 9. CRYPTOGRAPHY WITH PHP OVERVIEW ▸ Environment Setup ▸ Why Cryptography ▸ Definitions ▸ Role of Cryptography ▸ Algorithms ▸ Encryption with PHP ▸ Considerations ▸ Cryptography Games
- 10. CRYPTOGRAPHY WITH PHP ENVIRONMENT SETUP
- 11. CRYPTOGRAPHY WITH PHP ENVIRONMENT SETUP ▸ PHP 5.5+, best is 7.0+ ▸ Ideally have libsodium PECL extension (see https:// paragonie.com/book/pecl-libsodium/read/00- intro.md#installing-libsodium) or 7.2 (RC) ▸ Once you are up and running, please help others ▸ Worse case, use https://3v4l.org/
- 12. CRYPTOGRAPHY WITH PHP WHY CRYPTOGRAPHY
- 13. CRYPTOGRAPHY WITH PHP WHY CRYPTOGRAPHY
- 14. CRYPTOGRAPHY WITH PHP WHY CRYPTOGRAPHY
- 15. CRYPTOGRAPHY WITH PHP WHY CRYPTOGRAPHY
- 16. CRYPTOGRAPHY WITH PHP WHY CRYPTOGRAPHY ▸ Over 100,000 incidents in 2016 with 3,141 confirmed breaches ▸ Attacks largely for financial gain ▸ Many going after sensitive data
- 17. CRYPTOGRAPHY WITH PHP WHY CRYPTOGRAPHY ▸ Review Verizon 2017 Data Breach Investigations Report ▸ Yearly report ▸ Cybersecurity investigations report ▸ Pulls from many sources ▸ Lots of informative charts
- 18. CRYPTOGRAPHY WITH PHP WHY CRYPTOGRAPHY
- 19. CRYPTOGRAPHY WITH PHP WHY CRYPTOGRAPHY Incidents by industry
- 20. CRYPTOGRAPHY WITH PHP WHY CRYPTOGRAPHY
- 21. CRYPTOGRAPHY WITH PHP WHY CRYPTOGRAPHY
- 22. CRYPTOGRAPHY WITH PHP WHY CRYPTOGRAPHY
- 23. CRYPTOGRAPHY WITH PHP WHY CRYPTOGRAPHY
- 24. CRYPTOGRAPHY WITH PHP WHY CRYPTOGRAPHY
- 25. CRYPTOGRAPHY WITH PHP WHY CRYPTOGRAPHY ▸ No organization is immune ▸ Cryptography significantly reduces breach cost ▸ Cryptography can prevent leak of actual sensitive data
- 26. CRYPTOGRAPHY WITH PHP WHY CRYPTOGRAPHY ▸ Attack Countermeasures ▸ Good password policy ▸ Encrypt sensitive data ▸ Encrypt computer disks and devices ▸ Keep current with patches
- 28. CRYPTOGRAPHY WITH PHP DEFINITIONS ▸ Cryptography ▸ The process of writing or reading secret messages or codes ▸ Classical cryptography started thousands of years ago ▸ Advanced during wars of 20th century ▸ The science or study of secret communications
- 29. CRYPTOGRAPHY WITH PHP DEFINITIONS ▸ Encryption ▸ To change information from one form to another especially to hide its meaning ▸ En: to make ▸ Crypto: secret or hidden ▸ The actual changing of a communication
- 30. CRYPTOGRAPHY WITH PHP DEFINITIONS ▸ Algorithm ▸ A set of steps that are followed in order to solve a mathematical problem or to complete a computer process
- 31. CRYPTOGRAPHY WITH PHP DEFINITIONS ▸ Cipher ▸ A way of changing a message to keep it secret ▸ An algorithm used to encrypt or decrypt ▸ Classically included substitution and transposition ▸ A becomes 1 ▸ A becomes Z ▸ Abc123 becomes 123Abc ▸ Backwards
- 32. CRYPTOGRAPHY WITH PHP DEFINITIONS ▸ Hash ▸ To chop into small pieces ▸ Maps data to a string ▸ One-way hash functions ▸ Schneier “workhorses of modern cryptography” ▸ Input is the message, output is the digest
- 33. CRYPTOGRAPHY WITH PHP ROLE OF CRYPTOGRAPHY
- 34. CRYPTOGRAPHY WITH PHP ROLE OF CRYPTOGRAPHY ▸ World War II ▸ Enigma Machine used by Nazi Germany ▸ Code breaking by Allies, including Alan Turing
- 35. CRYPTOGRAPHY WITH PHP ROLE OF CRYPTOGRAPHY ▸ Secure communications from third parties ▸ Confidentiality of communications
- 36. CRYPTOGRAPHY WITH PHP ROLE OF CRYPTOGRAPHY ▸ Secure data at rest ▸ Secure data in transit
- 37. CRYPTOGRAPHY WITH PHP ROLE OF CRYPTOGRAPHY ▸ First 2 A’s in the AAA Framework ▸ Authentication: credentials ▸ Authorization: encrypt and decrypt data ▸ Accounting
- 39. CRYPTOGRAPHY WITH PHP ALGORITHMS ▸ One Way Hash
- 40. CRYPTOGRAPHY WITH PHP ALGORITHMS ▸ One Way Hash ▸ Data is hashed ▸ Cannot go backwards ▸ Integrity checks ▸ Password checks ▸ Identifiers; ex: Git and Mercurial
- 41. CRYPTOGRAPHY WITH PHP ALGORITHMS ▸ One Way Hash ▸ MD5 ▸ SHA-1, SHA-2, SHA-3
- 42. CRYPTOGRAPHY WITH PHP ALGORITHMS ▸ Symmetric-Key
- 43. CRYPTOGRAPHY WITH PHP ALGORITHMS ▸ Symmetric-Key ▸ Same key to encrypt and decrypt ▸ Shared secret key ▸ Susceptible to plaintext attacks (known and chosen) and cryptanalysis (differential and linear)
- 44. CRYPTOGRAPHY WITH PHP ALGORITHMS ▸ Symmetric-Key ▸ DES ▸ Triple DES ▸ AES
- 45. CRYPTOGRAPHY WITH PHP ALGORITHMS ▸ Symmetric-Key ▸ Blowfish ▸ Twofish ▸ Threefish
- 46. CRYPTOGRAPHY WITH PHP ALGORITHMS ▸ Asymmetric-Key
- 47. CRYPTOGRAPHY WITH PHP ALGORITHMS ▸ Asymmetric-Key ▸ Heavily used in cryptography ▸ Public and private keys ▸ Public key is publicly available ▸ Private key is kept secret
- 48. CRYPTOGRAPHY WITH PHP ALGORITHMS ▸ Asymmetric-Key
- 49. CRYPTOGRAPHY WITH PHP ALGORITHMS ▸ Asymmetric-Key ▸ Public key used to authenticate messages from owner of the private key ▸ Public key used to encrypt message to send to owner of the private key ▸ Private key used to decrypt inbound messages ▸ Private key used to encrypt outbound messages
- 50. CRYPTOGRAPHY WITH PHP ALGORITHMS ▸ Asymmetric-Key (Public-Key) ▸ RSA ▸ DSA
- 51. CRYPTOGRAPHY WITH PHP ALGORITHMS ▸ Broken ▸ DES ▸ MD2, MD4, MD5 ▸ SHA-1 ▸ GOST ▸ Panama ▸ RC4
- 52. CRYPTOGRAPHY WITH PHP ENCRYPTION WITH PHP
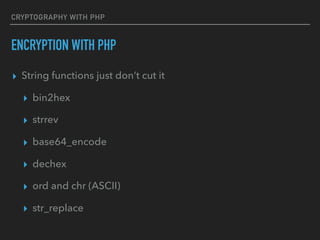
- 53. CRYPTOGRAPHY WITH PHP ENCRYPTION WITH PHP ▸ String functions just don’t cut it ▸ bin2hex ▸ strrev ▸ base64_encode ▸ dechex ▸ ord and chr (ASCII) ▸ str_replace
- 54. CRYPTOGRAPHY WITH PHP ENCRYPTION WITH PHP ▸ Hash ▸ Password hashing ▸ mcrypt ▸ CSPRNG ▸ openssl ▸ libsodium ▸ StupidPass
- 55. CRYPTOGRAPHY WITH PHP ENCRYPTION WITH PHP ▸ Hash ▸ hash_algos for array of options ▸ hash($algorithm, $message, $raw = false); ▸ hash_file for file contents hash ▸ hash_equals for comparing hashed values
- 56. CRYPTOGRAPHY WITH PHP ENCRYPTION WITH PHP ▸ Hash - Coding time! ▸ 5 minutes ▸ hash_algos for array of algorithms ▸ Output available algorithms <?php print_r(hash_algos()); ▸ See https://en.wikipedia.org/wiki/ Comparison_of_cryptographic_hash_functions
- 57. CRYPTOGRAPHY WITH PHP ENCRYPTION WITH PHP ▸ Hash - Coding time! ▸ 10 minutes ▸ hash($algorithm, $message, $raw = false); ▸ foreach hash_algos generate hash ▸ Review output content, including characters, length ▸ Does different message or message length impact hash length?
- 58. CRYPTOGRAPHY WITH PHP ENCRYPTION WITH PHP ▸ Hash - Coding time! ▸ 5 minutes ▸ hash_file for file contents hash ▸ make a text file with some text in it ▸ compare with hash of plain text
- 59. CRYPTOGRAPHY WITH PHP ENCRYPTION WITH PHP ▸ Hash ▸ == and === are not timing safe comparisons ▸ Nuances with PHP == returning true var_dump(md5('240610708') == md5(‘QNKCDZO')); var_dump(md5('aabg7XSs') == md5('aabC9RqS')); var_dump(sha1('aaroZmOk') == sha1('aaK1STfY')); var_dump(sha1('aaO8zKZF') == sha1('aa3OFF9m')); var_dump('0010e2' == '1e3'); var_dump('0x1234Ab' == '1193131'); var_dump('0xABCdef' == ' 0xABCdef');
- 60. CRYPTOGRAPHY WITH PHP ENCRYPTION WITH PHP ▸ Hash - Coding time! ▸ 15 minutes ▸ hash_equals as a timing safe hash comparison ▸ run thousands of iterations, look for patterns with averages ▸ $timeStart = microtime(true); … $timeEnd = mircotime(true); ▸ array_multisort($timing, SORT_NUMERIC);
- 61. CRYPTOGRAPHY WITH PHP ENCRYPTION WITH PHP
- 62. CRYPTOGRAPHY WITH PHP ENCRYPTION WITH PHP
- 63. CRYPTOGRAPHY WITH PHP ENCRYPTION WITH PHP
- 64. CRYPTOGRAPHY WITH PHP ENCRYPTION WITH PHP ▸ 10 minute break ▸ Lock picking
- 65. CRYPTOGRAPHY WITH PHP ENCRYPTION WITH PHP ▸ CSPRNG
- 66. CRYPTOGRAPHY WITH PHP ENCRYPTION WITH PHP ▸ CSPRNG ▸ Cryptographically Secure Pseudo-Random Number Generator (CSPRNG) ▸ Part of PHP 7 core ▸ For PHP < 7: composer require paragonie/random_compat
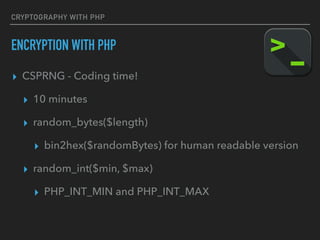
- 67. CRYPTOGRAPHY WITH PHP ENCRYPTION WITH PHP ▸ CSPRNG - Coding time! ▸ 10 minutes ▸ random_bytes($length) ▸ bin2hex($randomBytes) for human readable version ▸ random_int($min, $max) ▸ PHP_INT_MIN and PHP_INT_MAX
- 68. CRYPTOGRAPHY WITH PHP ENCRYPTION WITH PHP
- 69. CRYPTOGRAPHY WITH PHP ENCRYPTION WITH PHP
- 70. CRYPTOGRAPHY WITH PHP ENCRYPTION WITH PHP
- 71. CRYPTOGRAPHY WITH PHP ENCRYPTION WITH PHP
- 72. CRYPTOGRAPHY WITH PHP ENCRYPTION WITH PHP ▸ Password hashing
- 73. CRYPTOGRAPHY WITH PHP ENCRYPTION WITH PHP ▸ Password hashing ▸ $insecure = md5($password); ▸ Too fast ▸ Brute force ▸ 5f4dcc3b5aa765d61d8327deb882cf99
- 74. CRYPTOGRAPHY WITH PHP ENCRYPTION WITH PHP ▸ Password hashing ▸ Anthony Ferrara RFC in 2012 to simplify password hashing ▸ Use password_hash and password_verfiy (PHP 5.5+) ▸ $current = password_hash($password, PASSWORD_DEFAULT); ▸ PASSWORD_DEFAULT can change over time, currently is blowfish, max password length of 72 ▸ $isValid = password_verify($password, $current);
- 75. CRYPTOGRAPHY WITH PHP ENCRYPTION WITH PHP ▸ Password hashing ▸ Salt generated automatically ▸ Deprecated as option in PHP 7 ▸ Option ‘cost’, target time it takes ▸ password_hash($password, PASSWORD_DEFAULT, [‘cost’ => 10]);
- 76. CRYPTOGRAPHY WITH PHP ENCRYPTION WITH PHP ▸ Password hashing - Coding time! ▸ 10 minutes ▸ password_hash($password, PASSWORD_DEFAULT, [‘cost’ => 10]); ▸ notice output pattern, repeat for same password, try variations, different costs ▸ $2y$10$i49TRWieyhYtQ6P.76R5aOwRisUIqnQJxS6tszUobVkGG8bP9/XsW ▸ $2y$ for algorithm ▸ 10 for cost ▸ 22 character salt, varies by algorithm ▸ Hash as the rest
- 77. CRYPTOGRAPHY WITH PHP ENCRYPTION WITH PHP ▸ Password hashing - Coding time! ▸ 10 minutes ▸ password_verify($plaintext, $hash); ▸ password_needs_rehash($hash, PASSWORD_DEFAULT, $options) ▸ Timing safe check
- 78. CRYPTOGRAPHY WITH PHP ENCRYPTION WITH PHP
- 79. CRYPTOGRAPHY WITH PHP ENCRYPTION WITH PHP
- 80. CRYPTOGRAPHY WITH PHP ENCRYPTION WITH PHP
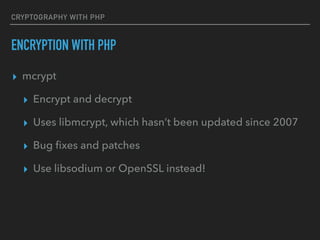
- 81. CRYPTOGRAPHY WITH PHP ENCRYPTION WITH PHP ▸ mcrypt
- 82. CRYPTOGRAPHY WITH PHP ENCRYPTION WITH PHP ▸ mcrypt ▸ Encrypt and decrypt ▸ Uses libmcrypt, which hasn’t been updated since 2007 ▸ Bug fixes and patches ▸ Use libsodium or OpenSSL instead!
- 83. CRYPTOGRAPHY WITH PHP ENCRYPTION WITH PHP ▸ openssl
- 84. CRYPTOGRAPHY WITH PHP ENCRYPTION WITH PHP ▸ openssl ▸ Generate and verify signatures ▸ Certificate Signing Requests (CSR) ▸ Encrypt and decrypt data ▸ Actively supported
- 85. CRYPTOGRAPHY WITH PHP ENCRYPTION WITH PHP ▸ openssl ▸ Private key generation ▸ openssl_pkey_new([$configs]); ▸ openssl_pkey_export_to_file($privateKey, $fileName); ▸ openssl_free_key($privateKey);
- 86. CRYPTOGRAPHY WITH PHP ENCRYPTION WITH PHP ▸ openssl ▸ Configuration defaults to openssl.conf ▸ digest_alg: Digest method to use ▸ x509_extensions: Extensions to use for x509 cert ▸ req_extensions: Extensions to use for CSR ▸ private_key_bits: Bits for private key generation ▸ private_key_type: Type of key ▸ encrypt_key: Export key with passphrase ▸ encrypt_key_cipher: Cipher for key
- 87. CRYPTOGRAPHY WITH PHP ENCRYPTION WITH PHP ▸ openssl - Coding time! ▸ 5 minutes ▸ Private key generation ▸ $config = [‘private_key_bits’ => 2048, 'private_key_type' => OPENSSL_KEYTYPE_RSA]; ▸ openssl_pkey_new([$configs]); ▸ openssl_pkey_export_to_file($privateKey, $fileName); ▸ openssl_free_key($privateKey);
- 88. CRYPTOGRAPHY WITH PHP ENCRYPTION WITH PHP
- 89. CRYPTOGRAPHY WITH PHP ENCRYPTION WITH PHP
- 90. CRYPTOGRAPHY WITH PHP ENCRYPTION WITH PHP ▸ openssl - Coding time! ▸ 5 minutes ▸ Public key generation ▸ Continue on from private key generation ▸ openssl_pkey_get_details($privateKey); ▸ file_put_contents(‘public.pem’, $details[‘key’]); ▸ Array with keys ‘bits’, ‘key’ (public key), ‘rsa’, ‘type’
- 91. CRYPTOGRAPHY WITH PHP ENCRYPTION WITH PHP
- 92. CRYPTOGRAPHY WITH PHP ENCRYPTION WITH PHP
- 93. CRYPTOGRAPHY WITH PHP ENCRYPTION WITH PHP ▸ openssl - Coding time! ▸ 5 minutes ▸ Encrypting data with the public key, decrypt with private ▸ $isEncrypted = openssl_public_encrypt($message, $encrypted, file_get_contents(‘public.pem’)); ▸ $isDecrypted = openssl_private_decrypt($encrypted, $decrypted, file_get_contents(‘private.pem’);
- 94. CRYPTOGRAPHY WITH PHP ENCRYPTION WITH PHP ▸ openssl - Coding time! ▸ 5 minutes ▸ Encrypting data with the private key, decrypt with public ▸ $isEncrypted = openssl_private_encrypt($message, $encrypted, file_get_contents(‘private.pem’)); ▸ $isDecrypted = openssl_public_decrypt($encrypted, $decrypted, file_get_contents(‘public.pem’);
- 95. CRYPTOGRAPHY WITH PHP ENCRYPTION WITH PHP ▸ cracklib
- 96. CRYPTOGRAPHY WITH PHP ENCRYPTION WITH PHP ▸ cracklib ▸ PECL extension, must be installed ▸ Checks complexity of passwords ▸ Still experimental
- 97. CRYPTOGRAPHY WITH PHP ENCRYPTION WITH PHP ▸ cracklib ▸ crack_opendict(‘/path/to/dictionary’) ▸ crack_check($dictionary, $password) ▸ crack_getlastmessage() ▸ crack_closedict($dictionary)
- 98. CRYPTOGRAPHY WITH PHP ENCRYPTION WITH PHP ▸ cracklib ▸ it's WAY too short ▸ it is too short ▸ it does not contain enough DIFFERENT characters ▸ it is all whitespace ▸ it is too simplistic/systematic ▸ it looks like a National Insurance number. ▸ it is based on a dictionary word ▸ it is based on a (reversed) dictionary word ▸ strong password
- 99. CRYPTOGRAPHY WITH PHP ENCRYPTION WITH PHP ▸ 10 minute break ▸ Find group of up to 4 for games
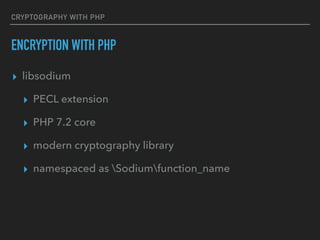
- 100. CRYPTOGRAPHY WITH PHP ENCRYPTION WITH PHP ▸ libsodium
- 101. CRYPTOGRAPHY WITH PHP ENCRYPTION WITH PHP ▸ libsodium ▸ PECL extension ▸ PHP 7.2 core ▸ modern cryptography library ▸ namespaced as Sodiumfunction_name
- 102. CRYPTOGRAPHY WITH PHP ENCRYPTION WITH PHP ▸ libsodium - Coding time! ▸ 10 minutes ▸ Cryptographically secure randomness ▸ Sodiumrandombytes_buf($numberBytes) with each byte being a random value between 0 and 255 (bin2hex for readability) ▸ Sodiumrandombytes_random16() for random integer between 0 and 65535 ▸ Sodiumrandombytes_uniform($maxPlusOne) for uniformly distributed random integers between 0 and max
- 103. CRYPTOGRAPHY WITH PHP ENCRYPTION WITH PHP ▸ libsodium - Coding time! ▸ 10 minutes ▸ Secret-key encryption and decryption ▸ $key = Sodiumrandombytes_buf(SodiumCRYPTO_SECRETBOX_KEYBYTES); ▸ $nonce = Sodiumrandombytes_buf(SodiumCRYPTO_SECRETBOX_NONCEBYTES); ▸ $ciphertext = Sodiumcrypto_secretbox('test', $nonce, $key); ▸ $plaintext = Sodiumcrypto_secretbox_open($ciphertext, $nonce, $key);
- 104. CRYPTOGRAPHY WITH PHP ENCRYPTION WITH PHP ▸ libsodium ▸ Public-key encryption and decryption ▸ Sodiumcrypto_box_* functions
- 105. CRYPTOGRAPHY WITH PHP ENCRYPTION WITH PHP ▸ libsodium ▸ Much more functionality ▸ Password hashing and checking ▸ Key signing ▸ Message Authentication Code (MAC) ▸ Hashing
- 106. CRYPTOGRAPHY WITH PHP ENCRYPTION WITH PHP ▸ StupidPass
- 107. CRYPTOGRAPHY WITH PHP ENCRYPTION WITH PHP ▸ StupidPass ▸ composer require northox/stupid-password ▸ $stupidPass = new StupidPass; ▸ $isValid = $stupidPass->validate($password); ▸ $stupidPass->getErrors(); ▸ new StupidPass($maxLength, $environmental, $pathToDictionary, $errorText, $options);
- 108. CRYPTOGRAPHY WITH PHP ENCRYPTION WITH PHP ▸ StupidPass - Coding time! ▸ 10 minutes ▸ install composer, StupidPass ▸ Try out common passwords, custom dictionary, see the errors ▸ composer require northox/stupid-password ▸ $stupidPass = new StupidPass; ▸ $isValid = $stupidPass->validate($password); ▸ $stupidPass->getErrors(); ▸ new StupidPass($maxLength, $environmental, $pathToDictionary, $errorText, $options);
- 110. CRYPTOGRAPHY WITH PHP CONSIDERATIONS ▸ Salts ▸ Algorithm costs ▸ Timing attacks ▸ Brute force attacks ▸ Rainbow tables ▸ Max message length
- 111. CRYPTOGRAPHY WITH PHP CONSIDERATIONS ▸ Salts ▸ Increased security for digest if done correctly ▸ Ex: $salt . $password ▸ Pepper debate ▸ Let password_hash generate the salt for you ▸ Different salt per password or message
- 112. CRYPTOGRAPHY WITH PHP CONSIDERATIONS ▸ Algorithm Costs ▸ Default cost for password_hash is 10 ▸ Higher cost leads to more processing time ▸ 8-12 is generally a good baseline ▸ Might change depending on hardware available
- 113. CRYPTOGRAPHY WITH PHP CONSIDERATIONS ▸ Timing Attacks ▸ Analyzing timing for algorithms ▸ Time variation for hashing, encrypting, decrypting ▸ Ex: Username not found, no password check attempted ▸ Ex: String comparisons stop after first mismatch ▸ Timing safety built into functions, take same time for positive or negative match
- 114. CRYPTOGRAPHY WITH PHP CONSIDERATIONS ▸ Brute Force Attacks ▸ Timing attack used to brute force list of usernames ▸ Dictionary attack using dictionary and common passwords ▸ Take time ▸ Advanced Persistent Threat (APT)
- 115. CRYPTOGRAPHY WITH PHP CONSIDERATIONS ▸ Brute Force Attacks ▸ Countermeasures ▸ Lock accounts, but causes Denial of Service ▸ Add time to each login ▸ Lock by IP address ▸ Vary failed login attempt behavior (Ex: HTTP status, redirect)
- 116. CRYPTOGRAPHY WITH PHP CONSIDERATIONS ▸ Brute Force Attacks ▸ Countermeasures ▸ Key words in HTML comments (invalid login, bad username or password) ▸ Security questions ▸ CAPTCHA ▸ Add another factor (multi-factor authentication)
- 117. CRYPTOGRAPHY WITH PHP CONSIDERATIONS ▸ Rainbow Tables ▸ Table with hashes already figured out ▸ Used for hashing that always generates same hash for an input ▸ Counter with modern algorithms, salts ▸ Common for MD5, SHA1, and other older algorithms
- 118. CRYPTOGRAPHY WITH PHP CONSIDERATIONS ▸ Rainbow Tables ▸ Internet search for the hash ▸ Online hash cracking sites
- 119. CRYPTOGRAPHY WITH PHP CONSIDERATIONS ▸ Max Message Length ▸ Only X characters considered when generating hash ▸ Ex: MD5 max is 128 characters in, 32 hex out ▸ Ex: password_hash max is 72 characters
- 120. CRYPTOGRAPHY WITH PHP CONSIDERATIONS ▸ Identify sensitive data ▸ Determine appropriate encryption ▸ Use cryptography to keep data safe
- 121. CRYPTOGRAPHY WITH PHP CONSIDERATIONS ▸ Cryptography can help minimize damage ▸ Electronic data breaches ▸ Stolen electronic devices ▸ Data transmission
- 122. CRYPTOGRAPHY WITH PHP CONSIDERATIONS ▸ Cryptography cannot help minimize damage ▸ Phishing attacks ▸ Credential theft ▸ Escalation of privileges ▸ DoS/DDoS ▸ Social engineering
- 123. CRYPTOGRAPHY WITH PHP CONSIDERATIONS ▸ Security education ▸ Verizon Data Breach Investigation Report ▸ SANS Institution, email digest ▸ Krebs on Security blog ▸ OWASP ▸ BrightTALK
- 124. CRYPTOGRAPHY WITH PHP CRYPTOGRAPHY GAMES
- 125. CRYPTOGRAPHY WITH PHP CRYPTOGRAPHY GAMES ▸ Groups of up to 4 ▸ 11:15-11:20 Instructions and rules, get in groups ▸ 11:20-11:45 Coding time! ▸ 11:45-11:55 Review answers ▸ 11:55-12:00 Closing
- 126. CRYPTOGRAPHY WITH PHP CRYPTOGRAPHY GAMES ▸ Get into your groups of up to 4
- 127. CRYPTOGRAPHY WITH PHP CRYPTOGRAPHY GAMES ▸ Instructions and rules ▸ Use PHP ▸ Decrypt the data ▸ Record how you decrypted the message ▸ Record plain text answer ▸ Winning team is team with most correct answers
- 128. CRYPTOGRAPHY WITH PHP CRYPTOGRAPHY GAMES ▸ Time is up!
- 129. CRYPTOGRAPHY WITH PHP CRYPTOGRAPHY GAMES ▸ Answers
- 130. CRYPTOGRAPHY WITH PHP CRYPTOGRAPHY GAMES ▸ Conclusion ▸ Leverage PHP cryptography and hashing features ▸ Use modern libraries ▸ Encrypt sensitive information ▸ Hash passwords correctly
- 131. CRYPTOGRAPHY WITH PHP QUESTIONS? ▸ Rate on joind.in ▸ https://joind.in/talk/7b305
- 132. CRYPTOGRAPHY WITH PHP SOURCES ▸ Merriam-Webster Dictionary online ▸ PHP.net documentation ▸ Virendra Chandak https://www.virendrachandak.com ▸ OWASP ▸ Verizon 2017 Data Breach Investigations Report ▸ https://paragonie.com/book/pecl-libsodium/read/00-intro.md ▸ https://www.cryptologie.net/article/268/how-to-compare-password-hashes- in-php/ ▸ http://blog.ircmaxell.com/2014/11/its-all-about-time.html









































































![CRYPTOGRAPHY WITH PHP
ENCRYPTION WITH PHP
▸ Password hashing
▸ Salt generated automatically
▸ Deprecated as option in PHP 7
▸ Option ‘cost’, target time it takes
▸ password_hash($password, PASSWORD_DEFAULT,
[‘cost’ => 10]);](https://image.slidesharecdn.com/cryptographywithphpworkshopzendcon-171020174409/85/Cryptography-With-PHP-ZendCon-2017-Workshop-75-320.jpg)
![CRYPTOGRAPHY WITH PHP
ENCRYPTION WITH PHP
▸ Password hashing - Coding time!
▸ 10 minutes
▸ password_hash($password, PASSWORD_DEFAULT, [‘cost’ => 10]);
▸ notice output pattern, repeat for same password, try variations,
different costs
▸ $2y$10$i49TRWieyhYtQ6P.76R5aOwRisUIqnQJxS6tszUobVkGG8bP9/XsW
▸ $2y$ for algorithm
▸ 10 for cost
▸ 22 character salt, varies by algorithm
▸ Hash as the rest](https://image.slidesharecdn.com/cryptographywithphpworkshopzendcon-171020174409/85/Cryptography-With-PHP-ZendCon-2017-Workshop-76-320.jpg)







![CRYPTOGRAPHY WITH PHP
ENCRYPTION WITH PHP
▸ openssl
▸ Private key generation
▸ openssl_pkey_new([$configs]);
▸ openssl_pkey_export_to_file($privateKey, $fileName);
▸ openssl_free_key($privateKey);](https://image.slidesharecdn.com/cryptographywithphpworkshopzendcon-171020174409/85/Cryptography-With-PHP-ZendCon-2017-Workshop-85-320.jpg)

![CRYPTOGRAPHY WITH PHP
ENCRYPTION WITH PHP
▸ openssl - Coding time!
▸ 5 minutes
▸ Private key generation
▸ $config = [‘private_key_bits’ => 2048, 'private_key_type' =>
OPENSSL_KEYTYPE_RSA];
▸ openssl_pkey_new([$configs]);
▸ openssl_pkey_export_to_file($privateKey, $fileName);
▸ openssl_free_key($privateKey);](https://image.slidesharecdn.com/cryptographywithphpworkshopzendcon-171020174409/85/Cryptography-With-PHP-ZendCon-2017-Workshop-87-320.jpg)


![CRYPTOGRAPHY WITH PHP
ENCRYPTION WITH PHP
▸ openssl - Coding time!
▸ 5 minutes
▸ Public key generation
▸ Continue on from private key generation
▸ openssl_pkey_get_details($privateKey);
▸ file_put_contents(‘public.pem’, $details[‘key’]);
▸ Array with keys ‘bits’, ‘key’ (public key), ‘rsa’, ‘type’](https://image.slidesharecdn.com/cryptographywithphpworkshopzendcon-171020174409/85/Cryptography-With-PHP-ZendCon-2017-Workshop-90-320.jpg)





















































![[2017.03.18] hst binary training part 1](https://cdn.slidesharecdn.com/ss_thumbnails/2017-170324055826-thumbnail.jpg?width=560&fit=bounds)














![Filesystem Management with Flysystem - php[tek] 2023](https://cdn.slidesharecdn.com/ss_thumbnails/filesystemmanagementwithflysystem-phptek2023-230514204651-488affd7-thumbnail.jpg?width=560&fit=bounds)
![Leveling Up With Unit Testing - php[tek] 2023](https://cdn.slidesharecdn.com/ss_thumbnails/levelingupwithunittesting-phptek2023-230514204446-cf06ada2-thumbnail.jpg?width=560&fit=bounds)





































