Cyber Security Extortion: Defending Against Digital Shakedowns
- 1. 2017 CROWDSTRIKE, INC. ALL RIGHTS RESERVED. CYBER EXTORTION: DEFENDING AGAINST DIGITAL SHAKEDOWNS
- 2. 1 Introductions 2 Cyber Extortion: Methods and Commonalities 3 Key Trends in “Datanapping” 4 5 Strategies to Prevent Datanapping 6 Q&A “Shakedown City”: Real-world Extortion Examples
- 4. ROBIN JACKSON PRINCIPAL CONSULTANT CROWDSTRIKE SERVICES PROFESSIONAL HIGHLIGHTS • Former U.S. Army Intelligence • Expert in SCADA/Controls industry • Founder of of the first ISPs in Montana • Author and DEFCON Workshop instructor • CompTIA Security+, WetStone Certified Hacking Investigator, WetStone Certified Steganography Investigator • More than 20 years experience in malware and incident response
- 5. BRENDON MACARAEG SR. PRODUCT MARKETING MANAGER CROWDSTRIKE PROFESSIONAL HIGHLIGHTS • Former PC Magazine editorial staff member • Extensive background in product management and e-commerce application development • Prior to CrowdStrike, led GTM and product marketing efforts at Symantec for both Enterprise and Consumer security solutions • Currently leads product marketing for CrowdStrike Services and Falcon Intelligence
- 6. CYBER EXTORTION: METHODS AND THEIR COMMONALITIES
- 7. A NOTE BEFORE WE BEGIN… Both internet extortion and ransomware attacks are crimes. If your company is a victim of either activity, we recommended you report the crime to the nearest FBI field office.
- 8. TWO DISTINCT APPROACHES Both have the same goal: Extract money from the victim ATTACK AFFECTS REAL-WORLD PARADIGM Extortion Ransomware Confidentiality Integrity Availability Extortion Blackmail Kidnapping
- 9. COMMONALITIES IN APPROACHES § Pay up or something dire will happen: - Your data will be published (extortion) - You won’t be able to recover your data (ransomware) § Payment required in digital currency § Payment does not guarantee desired result § Communications obfuscated - TOR - Proton mail
- 10. DIFFERENCES IN APPROACHES § CYBER EXTORTION § Data in the wild (extortion) § Overt threat § Media component § RANSOMWARE § Small transaction commodity § Damage inflicted § Results noticeable
- 11. KEY TRENDS IN “DATANAPPING”
- 12. ex·tor·tion /ikˈstôrSH(ə)n/ noun: extortion; plural noun: extortions the practice of obtaining something, especially money, through force or threats. synonyms: blackmail, shakedown; formal exaction
- 13. INTERNET EXTORTION Internet extortion involves hacking into and controlling various industry databases, promising to release control back to the company if funds are received, or the subjects are given web administrator jobs. Similarly, the subject will threaten to compromise information about consumers in the industry database unless funds are received. https://www.ic3.gov/crimeschemes.aspx#item-10
- 14. THREAT SOPHISTICATION MALWARE NON-MALWARE ATTACKS MALWARE 40% NATION- STATES 60% NON-MALWARE ATTACKS ORGANIZED CRIMINAL GANGS HACKTIVISTS/ VIGILANTES TERRORISTS CYBER- CRIMINALS YOU NEED COMPLETE BREACH PREVENTION HARDERTOPREVENT &DETECT LOW HIGH HIGH LOW
- 15. § Under reported (less than 1/3 of victims contact FBI) § 29% of reported incidents targeted an individual in the organization § Sensitive data § Shareholder/Customer/Supplier sensitivities § May attempt to “shop” data w/ threat of exposure - Darknet - Security blog writers - Competitors § No “tools” required EXTORTION
- 16. Data Theft Intellectual Property Theft Denial of Service / Distributed Denial of Service / Quality of Service EXTORTION ENCOMPASSES MANY THREATS 1 2 3 Website Defacement 4 Illicit materials placement 5
- 17. “SHAKEDOWN CITY”: REAL-WORLD EXTORTION EXAMPLES
- 18. NOKIA INTERNET EXTORTION § 2007 Hackers stole source code for Symbian OS § Nokia reportedly paid “multi-million” ransom § Cash delivered in a parking lot § Finnish National Bureau of Investigation / Police lost the criminals
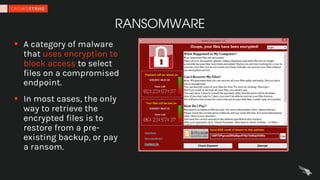
- 19. RANSOMWARE § A category of malware that uses encryption to block access to select files on a compromised endpoint. § In most cases, the only way to retrieve the encrypted files is to restore from a pre- existing backup, or pay a ransom.
- 20. § 777* § Al-Namrood* § Alma § Alpha § AlphaLocker § AndroidLocker/Dogspect us § Android/Lockerpin § Android/Lockdroid.E § Android.Lockscreen § Angler Exploit Kit § AnonPop § Apocalypse* § ApocalypseVM* § Autolocky* § Badblock* § Bart* § Bitcrypter/Bitcryptor* § BitLocker § Blank Slate Campaign attacks § Browlock § Cerber (version 1*) § Charger § Chimera* § CoinVault* § Coverton § Crowti § CrypBoss* § CryptoBlock § CryptoDefense* § CryptInfinite* § CrypMIC § Crypt38 § Crypt888 (see also Mircop) § CryptFile2 § Cryptobit § CryptoHitman § CryptoHost (a.k.a. Manamecrypt) § Cryptojoker § Cryptolocker § CryptoMix § CryptoRoger § Cryptowall § CryptXXX § CryptXXX v.1 & 2* § CryptXXX v1, 2, 3, 4, 5* § CryPy § Crysis § CTB-Locker § Cyber.Police § DDoS Extortion and Ransomware § Delilah § DeriaLock § DetoxCrypto § Dharma – see Crysis § DMA Locker* § Doxing as a Service § Dridex-related § DXXD § ElGato § ElasticSearch § Encryptor RAAS § Enigma § Enrume § Erebus § Evil Santa Ded § Fabiansomware* § FairWare § Faketoken § Fantom § FBI virus § FenixLocker* § FireCrypt § Flocker § FLUX: see Ransomware as a Service § Globe* § Goliath § Gomasom* § Hades Locker § Harasom* § HDD Cryptor § Hitler § HolyCrypt § HOSTMAN: see Ransomware as a Service § HydraCrypt* § JapanLocker § JBoss Backdoors § Jigsaw*/CryptoHit § Karmen § Kelihos § KeRanger § KeyBTC* § KillDisk § KimcilWare § Kirk § Koolova § Kovter § LeChiffre § Lechiffree* § Legion § Lockdroid § Locker § Locky § LogicLocker § Magic § Maktub § Mamba (See HDD Cryptor) § Manamecrypt (a.k.a. CryptoHost) § Marlboro § MarsJoke* § Mircop* § Mischa § MongoDB hacking § Nanolocker § Nemucod* § ‘Notification’ ransomware § Odin § Operation Global III* § OSX.FileCoder.E {see Patcher} § OSX.Filezip {see Patcher} § PadCrypt § Patcher § PClock* § PetrWrap § Petya* § Philadelphia* § PHP Ransomware § Polyglot – see MarsJoke* § Pompous § Popcorn Time § PornDroid § PoshCoder § PowerWare* § Power Worm § Princess Locker § PWSSynch-B § RAA § Rakhni & similar* § Rannoh* § RanRan § Ranscam § Ransoc § Ransom32 § Ransomlock.AT § Ransomware Affiliate Network: see Ransomware as a Service § Ransomware as a Service § RensenWare § Rokku § Sage § Samas § SamSam § Sarento § Satan: see also Ransomware as a Service § Satana § Serpent § 7ev3n § Shade § Shade v1 & 2* § Shark § shc – see JapanLocker § Shujin § Simplocker § Slocker § SNSLocker* § Spora § Stampado* § Surprise § SZFlocker § TeamXRat § Tech Support Scams and Ransomware § Teerac § Telecrypt § TeslaCrypt § TeslaCrypt v1, 2, 3, 4* § Tescrypt § Tordow (Android.spy.Tordow) § Towelroot § Troldesh § TrueCrypter § UmbreCrypt* § Vandev* § VinCE [See Tech Support Scams and Ransomware] § Virlock § Wildfire* § WannaCry § Xorist* § Xpan § Zcryptor § Zepto RANSOMWARE FAMILIES IN THE WILD (190)
- 21. RANSOMWARE TYPES OF THREATS § Small ransoms are associated with commodity versions which are delivered via automatic means (Locky, Cryptolocker, etc.) § Large ransoms are demanded by hackers who manually penetrate systems, discover key systems and then encrypt those systems. (Samas, Dharma)
- 22. HOLLYWOOD PRESBYTERIAN HOSPITAL § 16,175 Patients § Public reports still attribute Locky, but security researchers watching Samas portals saw the ransom demand for the exact amount paid in BTC. § Large ransom size ($17,000 US) also aligns with a targeted Samas attack § Services restored ten days after the attack
- 23. STRATEGIES TO PREVENT “DATANAPPING”
- 24. PRIOR TO AN EVENT § User Training: raise awareness of threat environment, including “after hours” personal internet activity § Tabletop exercises § Penetration testing § Rigorous backups § Media/Communications plan § Sensitive data encrypted, both at rest and in motion § Proper instrumentation: Falcon Platform
- 25. DURING AN EVENT § Early detection § Immediate interruption § Standard IR procedures
- 26. SUCCESSFUL EXFILTRATION § Contact Law Enforcement § Control media as best as possible § Interruption of attempts to disperse information § Monitor dark net activity § Don’t feed the “trolls”
- 28. CROWDSTRIKE SERVICES DEFENDS AGAINST & RESPONDS TO SECURITY INCIDENTS HELPING YOU DEFEAT THE ADVERSARY SERVICE PORTFOLIO: Thorough investigation and accelerated recovery time enable remediation on day one INCIDENT RESPONSE Anticipate threats, prepare your network, improve your team’s ability to prevent damage from attacks PROACTIVE SERVICES
- 29. INCIDENT RESPONSE SERVICES With an immediate and comprehensive understanding of attacker activity, we stop breaches fast. Identify attacker activity, scope and impact on your organization Engage the attackers’ tactics and actions with appropriate methods Determine how best to detect and manage future attacker activity END GOAL Get our clients back to normal business operations quickly
- 30. 2017 CROWDSTRIKE, INC. ALL RIGHTS RESERVED. Questions? Please submit all questions in the Q&A chat right below the presentation slides Contact Us Additional Information Join Weekly Demos crowdstrike.com/productdemos Featured Asset: Falcon Test Drive Website: crowdstrike.com Email: [email protected] Number: 1.888.512.8902 (US)



















![§ 777*
§ Al-Namrood*
§ Alma
§ Alpha
§ AlphaLocker
§ AndroidLocker/Dogspect
us
§ Android/Lockerpin
§ Android/Lockdroid.E
§ Android.Lockscreen
§ Angler Exploit Kit
§ AnonPop
§ Apocalypse*
§ ApocalypseVM*
§ Autolocky*
§ Badblock*
§ Bart*
§ Bitcrypter/Bitcryptor*
§ BitLocker
§ Blank Slate Campaign
attacks
§ Browlock
§ Cerber (version 1*)
§ Charger
§ Chimera*
§ CoinVault*
§ Coverton
§ Crowti
§ CrypBoss*
§ CryptoBlock
§ CryptoDefense*
§ CryptInfinite*
§ CrypMIC
§ Crypt38
§ Crypt888 (see also
Mircop)
§ CryptFile2
§ Cryptobit
§ CryptoHitman
§ CryptoHost (a.k.a.
Manamecrypt)
§ Cryptojoker
§ Cryptolocker
§ CryptoMix
§ CryptoRoger
§ Cryptowall
§ CryptXXX
§ CryptXXX v.1 & 2*
§ CryptXXX v1, 2, 3, 4, 5*
§ CryPy
§ Crysis
§ CTB-Locker
§ Cyber.Police
§ DDoS Extortion and
Ransomware
§ Delilah
§ DeriaLock
§ DetoxCrypto
§ Dharma – see Crysis
§ DMA Locker*
§ Doxing as a Service
§ Dridex-related
§ DXXD
§ ElGato
§ ElasticSearch
§ Encryptor RAAS
§ Enigma
§ Enrume
§ Erebus
§ Evil Santa Ded
§ Fabiansomware*
§ FairWare
§ Faketoken
§ Fantom
§ FBI virus
§ FenixLocker*
§ FireCrypt
§ Flocker
§ FLUX: see Ransomware
as a Service
§ Globe*
§ Goliath
§ Gomasom*
§ Hades Locker
§ Harasom*
§ HDD Cryptor
§ Hitler
§ HolyCrypt
§ HOSTMAN: see
Ransomware as a
Service
§ HydraCrypt*
§ JapanLocker
§ JBoss Backdoors
§ Jigsaw*/CryptoHit
§ Karmen
§ Kelihos
§ KeRanger
§ KeyBTC*
§ KillDisk
§ KimcilWare
§ Kirk
§ Koolova
§ Kovter
§ LeChiffre
§ Lechiffree*
§ Legion
§ Lockdroid
§ Locker
§ Locky
§ LogicLocker
§ Magic
§ Maktub
§ Mamba (See HDD
Cryptor)
§ Manamecrypt (a.k.a.
CryptoHost)
§ Marlboro
§ MarsJoke*
§ Mircop*
§ Mischa
§ MongoDB hacking
§ Nanolocker
§ Nemucod*
§ ‘Notification’
ransomware
§ Odin
§ Operation Global III*
§ OSX.FileCoder.E {see
Patcher}
§ OSX.Filezip {see Patcher}
§ PadCrypt
§ Patcher
§ PClock*
§ PetrWrap
§ Petya*
§ Philadelphia*
§ PHP Ransomware
§ Polyglot – see MarsJoke*
§ Pompous
§ Popcorn Time
§ PornDroid
§ PoshCoder
§ PowerWare*
§ Power Worm
§ Princess Locker
§ PWSSynch-B
§ RAA
§ Rakhni & similar*
§ Rannoh*
§ RanRan
§ Ranscam
§ Ransoc
§ Ransom32
§ Ransomlock.AT
§ Ransomware Affiliate
Network: see
Ransomware as a
Service
§ Ransomware as a
Service
§ RensenWare
§ Rokku
§ Sage
§ Samas
§ SamSam
§ Sarento
§ Satan: see also
Ransomware as a
Service
§ Satana
§ Serpent
§ 7ev3n
§ Shade
§ Shade v1 & 2*
§ Shark
§ shc – see JapanLocker
§ Shujin
§ Simplocker
§ Slocker
§ SNSLocker*
§ Spora
§ Stampado*
§ Surprise
§ SZFlocker
§ TeamXRat
§ Tech Support Scams and
Ransomware
§ Teerac
§ Telecrypt
§ TeslaCrypt
§ TeslaCrypt v1, 2, 3, 4*
§ Tescrypt
§ Tordow
(Android.spy.Tordow)
§ Towelroot
§ Troldesh
§ TrueCrypter
§ UmbreCrypt*
§ Vandev*
§ VinCE [See Tech Support
Scams and
Ransomware]
§ Virlock
§ Wildfire*
§ WannaCry
§ Xorist*
§ Xpan
§ Zcryptor
§ Zepto
RANSOMWARE FAMILIES IN THE WILD (190)](https://image.slidesharecdn.com/slidesharecrowdstrikedatanapping-170622182532/85/Cyber-Security-Extortion-Defending-Against-Digital-Shakedowns-20-320.jpg)









