Data Governance Trends and Best Practices To Implement Today
1) The document discusses best practices for data protection on Google Cloud, including setting data policies, governing access, classifying sensitive data, controlling access, encryption, secure collaboration, and incident response. 2) It provides examples of how to limit access to data and sensitive information, gain visibility into where sensitive data resides, encrypt data with customer-controlled keys, harden workloads, run workloads confidentially, collaborate securely with untrusted parties, and address cloud security incidents. 3) The key recommendations are to protect data at rest and in use through classification, access controls, encryption, confidential computing; securely share data through techniques like secure multi-party computation; and have an incident response plan to quickly address threats.



























Recommended




























































More Related Content
What's hot (20)








































Similar to Data Governance Trends and Best Practices To Implement Today (20)








































More from DATAVERSITY (20)








































Recently uploaded (20)
























Data Governance Trends and Best Practices To Implement Today
- 1. Proprietary + Confidential Data protection trends and best practices to implement today
- 2. Sam Lugani Group Product Manager Group Product Manager Google Cloud Meet today’s speaker! Rene Kolga Group Product Manager Product Manager Google Cloud
- 3. Agenda 01 Data Governance Access Controls Encryption Secure Collaboration Incident Response
- 4. 1. Setting internal data policies 2. Governing data access What is Data Governance? 3. Complying with external standards 4. Understanding the data lifecycle Data governance is everything you do to ensure data is secure, private, accurate, available, and usable
- 5. Data Protection (part of Data Governance) Key questions ● How do I limit access to my data? ● How do I protect my sensitive data and my IP? ● How do I collaborate with other companies processing their sensitive data?
- 6. What are the commitments being made by a cloud provider? Do you have explicit control over your data and how it is used? Processing your data as per your instructions. Not selling it to third parties. Not using it for for advertising. Transparent about data collection and use. Is your data is encrypted Not use your AI models for any purpose. Providing prompt data incident noti cations. Following international standards.
- 7. Scenario: I want to control access to my cloud resources Access Controls
- 8. Access Transparency Access Approval Near real-time logs whenever Google administrators access your environment on GCP Approve administrative access to your data on GCP before it happens Access Transparency (AXT) and Approval Approval (AXA) provides in depth visibility of customer data access requests: ● Resource being accessed ● Reason for access ● Access approval or denial by the customer
- 9. Scenario: I want to gain visibility into where my sensitive data resides E.g. What type of data do I store, and where can it be found? Classification
- 10. 1. Gain visibility into sensitive data 2. Protect and de-risk sensitive data 3. Integrate into virtually any workload to protect data at the source Cloud DLP helps both Cloud Customers and end users:
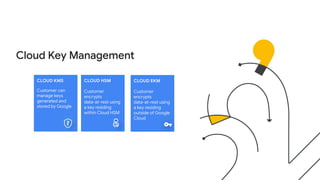
- 11. Scenario: I want the highest level of protection and control of my encryption keys. E.g. Own the full control of how data is encrypted and decrypted Cloud Key Management
- 12. Cloud Key Management CLOUD KMS Customer can manage keys generated and stored by Google CLOUD HSM Customer encrypts data-at-rest using a key residing within Cloud HSM CLOUD EKM Customer encrypts data-at-rest using a key residing outside of Google Cloud
- 13. Scenario: I want to harden my workloads against malware E.g. from remote attacks, privilege escalation, and malicious insiders Hardened VMs
- 14. Shielded VM (by default) app_z host OS host BIOS hardware and firmware Titans bins/libs guest kernel app_x bins/libs guest kernel VM_A VM_B Google KVM Malicious guest OS, including guest kernel 2 Integrity notifications to protect against tampering 3 Malicious guest system firmware, including malicious drivers 1 TPM driver TPM driver vTPM(sw) device NDA Boot time protection from ...
- 15. Scenario: I want to run my workload confidential or cryptographically isolate myself from neighbours and cloud infrastructure E.g. from malicious insiders and infrastructure 0-days Confidential Computing
- 16. Confidential VMs ● Just like a regular GCE VM ○ Anything that runs on VM runs on CVM ● Data encrypted while in-use ○ Memory encrypted, decrypted only on CPU chip ○ A key per VM ■ Random, ephemeral, generated by HW ■ Not extractable from HW ● Scale up to 224 vCPUs and 896 GiB memory System on Chip AMD Secure Processor app guest OS app guest OS Hypervisor (KVM) VM 1 VM 2 Key 2 Key 1 Memory Controller AES Encryption Engine
- 18. Scenario: I want to collaborate securely with multiple untrusted parties E.g. run secure immutable workloads without accidental data leakage or compromise Secure MPC
- 20. Example Sharing Sensitive Data Securely Data owner #1 (e.g. bank) Data owner #2 - #N (e.g. bank) Trusted Execution Environment Knowledge Knowledge Workload author (3rd party or data owner)
- 21. MPC Use Cases Healthcare Joint ML training on PHI data to optimize treatment regimes, discover new drugs and more FinTech & Web 3 Detect fraud, prevent duplicate financing, identify insurance “double dipping”, secure Web3 transactions Retail & Adtech Enable Data Clean Rooms and provide aggregation measurements in a privacy preserving way
- 23. Multi-party Computation Collaborate without trusting Retain data ownership Data is only visible to the workload and corresponding data owners in Confidential Space. Protect against operators Workload operators cannot view or change data or workload. They can only start and stop it. Multiple separate parties can securely share data with an agreed upon workload.
- 24. Scenario: I want to address a cloud security incident E.g. respond to a data theft or cryptominer issue in my cloud environment Incident Response
- 25. Cloud Is Here, This Means Threats, and This Means Incidents Cloud Is Here Gartner Forecasts Worldwide Public Cloud End-User Spending to Reach Nearly $500 Billion in 2022 Threats Are Here ● Cryptominers ● Credential abuse ● Software exploitation ● State sponsored attacks Incidents Are Growing ● Data Theft ● Multi-faceted Extortion ● Theft of Cloud Resources ● Attacks against Other Systems ● Cross cloud & hybrid environment Gartner Press Release, “Gartner Forecasts Worldwide Public Cloud End-User Spending to Reach Nearly $500 Billion in 2022,” April 19, 2022.
- 26. Incident response 1. Identification 2. Coordination 3. Resolution 4. Closure 5. Continuous improvement Best Practices in creating a scalable Incident Response Process https://cloud.google.com/docs/security/incident-response
- 27. Protecting data while it’s being store Classifying sensitive data Controlling Access to Data Key Takeaways 01 02 03 Protecting data when its being processed Secure and private multi-party computation Incident Response process 06 05 04
- 28. Thank You










