Data Quality in Test Automation Navigating the Path to Reliable Testing
- 1. Data Quality in Test Automation: Navigating the Path to Reliable Testing Presented by: Lokeshwaran Senior Automation Consultant
- 2. Lack of etiquette and manners is a huge turn off. KnolX Etiquettes Punctuality Join the session 5 minutes prior to the session start time. We start on time and conclude on time! Feedback Make sure to submit a constructive feedback for all sessions as it is very helpful for the presenter. Silent Mode Keep your mobile devices in silent mode, feel free to move out of session in case you need to attend an urgent call. Avoid Disturbance Avoid unwanted chit chat during the session.
- 3. 1. Introduction to Data Quality in Test Automation 2. Challenges in Ensuring Data Quality 3. Data Preparation Techniques 4. Effective Data Maintenance Strategies 5. Ensuring Data Security in Test Automation 6. Demo and QA
- 4. Introduction to Data Quality in Test Automation Test data management is the success of your QA processes. Without proper management, your testing efforts may be compromised, resulting in inaccurate test results and missed defects. Test Data
- 5. What is test data ? Introduction to Data Quality in Test Automation Why is it so important ? How to use test data efficiently ? Test data refers to the input, parameters, or conditions used in software testing to verify the correctness, reliability, and performance of a software application. Test data is essential for verifying software functionality, detecting defects, and validating requirements, ultimately ensuring software quality and mitigating risks in software development projects. Efficient use of test data involves selecting representative datasets, automating data generation and management, and prioritizing high-impact test cases, optimizing testing efforts and ensuring thorough coverage of critical scenarios.
- 6. Important Facts on Quality Test Data Accurate and Relevant Testing Improved Test Coverage Data Integrity and Security Validation of Business Rules and Logic Cost and Time Savings
- 7. Important Facts on Quality Test Data • Accurate and Relevant Testing: By having accurate and relevant test data, you can replicate real-life scenarios and accurately assess the performance and functionality of your software. • Improved Test Coverage: Test data management allows you to cover a wide range of test scenarios, ensuring that all possible use cases are tested thoroughly. • Data Integrity and Security: Test data management involves ensuring the integrity and security of the test data throughout the testing process. This includes protecting sensitive information, complying with data privacy regulations, and maintaining data consistency to avoid any inconsistencies in test results. • Validation of Business Rules and Logic: Validation of business rules and logic involves verifying that the software accurately interprets and executes the predefined rules and logic governing its behaviour. • Cost and Time Savings: Quality test data ensures efficient test automation, leading to cost and time savings by reducing manual effort, accelerating testing cycles, and enabling accurate validation of software functionality.
- 9. Challenges in Ensuring Data Quality O M K M B Obtaining Relevant Test Data Keeping Data Up-to-Date Managing Large Volume of Test Data Maintaining Data Consistency Best Practices for Addressing Data Quality Challenges
- 11. Data Preparation Techniques Data preparation serves as the foundational process in data analysis, encompassing a series of essential steps to refine raw data into a usable format for analysis. These steps include identifying and rectifying inconsistencies, transforming data into a standardized structure, and arranging it systematically to facilitate efficient analysis. By meticulously cleaning, transforming, and organizing data, analysts ensure its accuracy, consistency, and relevance, paving the way for more insightful and accurate analysis outcomes. Techniques
- 12. Different Techniques being used 01 02 03 04 05 07 06 Data Cleaning Data Transformation Data Integration Data Reduction Data Formatting Feature Scaling Data Partitioning
- 13. Data cleaning • Data cleaning is the foundational step of data preparation. • It involves managing missing values through techniques like imputation, deletion, or prediction. • Removing duplicate entries is essential to prevent redundancy and maintain data integrity. • Correcting errors and inconsistencies within the dataset ensures accuracy and reliability. • Overall, data cleaning sets the stage for robust and meaningful data analysis. DATA
- 14. Data Transformation Normalization: It involves scaling numerical data to a common range, often between 0 and 1, facilitating fair comparisons between different features. Standardization: It transforms numerical data to have a mean of 0 and a standard deviation of 1, aiding in data interpretation and model training. Encoding: Its categorical variables converts qualitative data into numerical format, enabling inclusion in statistical models. Feature engineering: It enhances model performance by creating new predictive features from existing ones, uncovering deeper insights from the data.
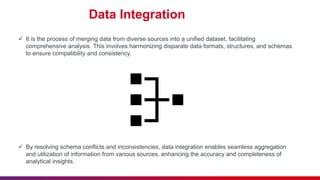
- 15. Data Integration It is the process of merging data from diverse sources into a unified dataset, facilitating comprehensive analysis. This involves harmonizing disparate data formats, structures, and schemas to ensure compatibility and consistency. By resolving schema conflicts and inconsistencies, data integration enables seamless aggregation and utilization of information from various sources, enhancing the accuracy and completeness of analytical insights.
- 16. Data Reduction It involves techniques to decrease the complexity and size of datasets while preserving their essential information: Dimensionality Reduction: Utilizing methods such as Principal Component Analysis (PCA) or feature selection to condense the number of variables in the dataset. This simplifies analysis, reduces computational burden, and can help in visualizing high- dimensional data. Sampling: Extracting a representative subset of the data for analysis. This is particularly beneficial for large datasets where analysing the entire dataset is impractical. Sampling techniques ensure that the selected subset retains the statistical properties of the original data, allowing for meaningful analysis while reducing computational resources and processing time.
- 17. Data Formatting • Consistency Check: It involves verifying that data types across the dataset are uniform, ensuring compatibility for analysis tools and algorithms. • Correcting Formats: This step rectifies any inconsistencies or errors in data formats, such as ensuring dates are formatted consistently and accurately, enhancing data integrity and usability. • Standardization: By standardizing data types, it promotes efficiency in data processing and analysis, minimizing errors and facilitating seamless integration with analytical tools and systems. It ensures consistency and suitability of data types for analysis:
- 18. Feature scaling It is a preprocessing step in machine learning: • Normalization: It involves scaling features to a similar range, typically between 0 and 1 or -1 and 1. • Avoiding Dominance: By ensuring all features contribute proportionally to the model, it prevents certain features from dominating others during training. • Enhancing Model Performance: Feature scaling promotes convergence in optimization algorithms and improves the stability and performance of machine learning models, particularly those sensitive to feature magnitudes, such as gradient-based algorithms
- 19. Data partitioning It involves dividing the dataset into subsets: • Training Set: This subset is used to train the machine learning model, capturing patterns and relationships in the data. • Validation Set: It helps tune model hyperparameters and assess its performance during training, preventing overfitting. • Testing Set: Reserved for evaluating the model's performance on unseen data, providing an unbiased estimate of its generalization ability.
- 21. Effective Data Maintenance Strategies • Regular Backups: Implement frequent data duplication to mitigate loss from system failures or cyberattacks. • Data Cleaning: Regularly validate and clean data to remove errors and inconsistencies. • Data Security Measures: Employ encryption, access controls, and monitoring to safeguard against unauthorized access. • Data Lifecycle Management: Define retention periods and disposal procedures in compliance with regulations. • Data Quality Monitoring: Continuously monitor accuracy, completeness, and consistency metrics. • Regular Updates and Patching: Keep systems up-to-date to address vulnerabilities.
- 22. Effective Data Maintenance Strategies • Metadata Management: Maintain comprehensive metadata for efficient data discovery and governance. • Training and Documentation: Provide training on best practices and document procedures for consistency. • Performance Monitoring and Optimization: Monitor system performance and optimize resource utilization. • Disaster Recovery Planning: Develop and test plans for data restoration and continuity of operations. • Compliance with Regulations: Ensure compliance with data protection regulations. • Regular Audits and Reviews: Conduct periodic audits to identify areas for improvement and ensure compliance.
- 24. Best Practices for Data Security Tools and Technologies Data Security Risks Discussion of common security risks in test automation, such as unauthorized access to sensitive data, data breaches, and privacy violations. Examples of potential consequences of data security breaches in automated testing environments. Implementing robust access controls and encryption techniques, alongside regular security audits and secure data handling protocols, are essential best practices for ensuring data security in test automation, mitigating risks and safeguarding sensitive information. Utilize encryption libraries, access control mechanisms, and security testing frameworks to enhance data security in test automation, ensuring protection against unauthorized access and potential data breaches. Ensuring Data Security in Test Automation