Dear Hacker: Infrastructure Security Reality Check
- 2. Consulting services → High quality penetration tests with useful reports Applications Websites External services (edge) Internal services + configuration reviews → Incident response emergency services – immediate reaction! → Security architecture and design advisory → Forensics investigation → Security awareness For management and employees [email protected] Trainings → Security Awareness trainings for executives → CQURE Academy: over 40 advanced security trainings for IT Teams → Certificates and exams → Delivered all around the world only by a CQURE Team: training authors
- 4. Part 1: Windows internals for attacks Break Part 2: Identity & network attacks, code execution techniques Lunch Part 3: Monitoring techniques and analysis Break Part 4: Forensics techniques 09’00-10’30 10’45-12’00 13’00-15’00 15’15-17’00 12’00-13’00 10’30-10’45 15’00-15’15
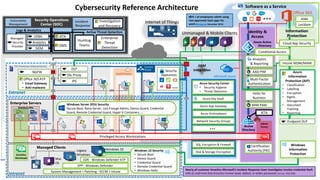
- 7. Unmanaged & Mobile Clients Sensitive Workloads Cybersecurity Reference Architecture Intranet Extranet Azure Key Vault Azure Security Center • Security Hygiene • Threat Detection System Management + Patching - SCCM + Intune Microsoft Azure On Premises Datacenter(s) NGFW IPS DLP SSL Proxy Nearly all customer breaches Microsoft’s Incident Response team investigates involve credential theft 63% of confirmed data breaches involve weak, default, or stolen passwords (Verizon 2016 DBR) IaaS/Hoster $ Windows 10 EPP - Windows Defender Office 365 ATP • Email Gateway • Anti-malware EDR - Windows Defender ATPMac OS Multi-Factor Authentication MIM PAMAzure App Gateway Network Security Groups Windows Information Protection AAD PIM Azure Antimalware Disk & Storage Encryption Endpoint DLP Shielded VMs SQL Encryption & Firewall Hello for Business Azure Information Protection (AIP) • Classification • Labelling • Encryption • Rights Management • Document Tracking • Reporting Enterprise Servers VPN VPN Domain Controllers VMs VMs Certification Authority (PKI) Incident Response Vulnerability Management Enterprise Threat Detection Analytics Managed Security Provider OMS ATA SIEM Security Operations Center (SOC) Logs & Analytics Active Threat Detection Hunting Teams Investigation and Recovery WEF SIEM Integration IoT Identity & Access 80% + of employees admit using non-approved SaaS apps for work (Stratecast, December 2013) UEBA Windows 10 Security • Secure Boot • Device Guard • Credential Guard • Remote Credential Guard • Windows Hello Managed Clients Legacy Windows Office 365 Security Appliances Intune MDM/MAM Conditional Access Cloud App Security Information Protection Windows Server 2016 Security Secure Boot, Nano Server, Just Enough Admin, Device Guard, Credential Guard, Remote Credential Guard, Hyper-V Containers, … Software as a Service Analytics & Reporting ATA Privileged Access Workstations Internet of Things ASM Lockbox Admin Forest
- 9. ➔ Assign permissions to groups rather than to users ➔ Deny permissions should be used for certain special cases ➔ Use security templates ➔ If possible, avoid changing the default permission entries on file system objects, particularly on system folders and root folders ➔ Never deny the Everyone group access to an object
- 10. ➔ Assign permissions to an object as high on the tree as possible and then apply inheritance to propagate the security settings through the tree ➔ Privileges can sometimes override permissions ➔ For permissions on Active Directory objects, make sure you understand the best practices specific to Active Directory objects
- 11. ➔ If possible, avoid changing the default permissions on AD objects ➔ Avoid granting Full Control permissions over an object or organizational unit ➔ Minimize the number of access control entries that apply to child objects ➔ When possible, assign the same set of permissions to multiple objects ➔Whenever possible, assign permissions to groups rather than users
- 12. ➔ When possible, assign access rights on a broad level rather than assigning individual user rights: ▪ Minimizing the number of access control entries will improve performance ▪ Allow "Read All Properties" or "Write All Properties" rather than individual properties ▪ Allow Read or Write access to property sets rather than individual properties ▪ A property set is a collection of attributes. For example, the Personal Information property set includes the attribute's address, personal title, and so on. By setting access on the property set, you have automatically set access on all the attributes contained in that property set ▪ Allow "Create All Child Objects" or "Delete All Child Objects," rather than specifying individual child objects ▪ Allow "All Extended Rights" rather than allowing the individual extended rights ▪ Allow "All Validated Writes" rather than allowing the individual validated rights
- 15. Class names for keys from HKLMSYSTEMCCSControlLsa HKLMSECURITYCache HKLMSECURITYPolicySecrets HKLMSECURITYPolicySecrets
- 16. DK = PBKDF2(PRF, Password, Salt, c, dkLen) Microsoft’s implementation: MSDCC2= PBKDF2(HMAC-SHA1, DCC1, username, 10240, 16) Legend
- 17. Before the attacks facilitated by pass-the-hash, we can only rejoice the "salting" by the username. There are a number pre-computed tables for users as Administrator facilitating attacks on these hashes.
- 18. There is actually not much of a difference with XP / 2003! No additional salting. PBKDF2 introduced a new variable: the number of iterations SHA1 with the same salt as before (username).
- 19. The number of iterations in PBKDF2, it is configurable through the registry: HKEY_LOCAL_MACHINESECURITYCache DWORD (32) NL$IterationCount If the number is less than 10240, it is a multiplier by 1024 (20 therefore gives 20480 iterations) If the number is greater than 10240, it is the number of iterations (rounded to 1024)
- 20. Getting the: cached data MSDCC2 1.bootkey: classes from HKLMSYSTEMCCSControlLsa + [class names for: Data, GBG, JD, Skew1] (+arrays’ permutations) int[] permutationBootKey = new int[] { 0x8, 0x5, 0x4, 0x2, 0xb, 0x9, 0xd, 0x3, 0x0, 0x6, 0x1, 0xc, 0xe, 0xa, 0xf, 0x7 }; 2.PolEKList: HKLMSECURITYPolicyPolEKList [default value] 3.lsakey: AES_DECRYPT(key, data) -> AES(bootkey, PolEKList) 4.NL$KM secret: HKLMSECURITYPolicySecretsNL$KM 5.nlkm_decrypted: AES_DECRYPT(lsakey, NL$KM secret) 6.Cache_Entry{id} -> HKLMSECURITYCacheNL${id} 7.cache_entry_decrypted -> AES_DECRYPT(nlkm_decrypted, Cache_Entry{id})
- 21. Classic Data Protection API Based on the following components: Password, data blob, entropy Is not prone to password resets! Protects from outsiders when being in offline access Effectively protects users data Stores the password history You need to be able to get access to some of your passwords from the past Conclusion:OS greatlyhelpsus to protectsecrets
- 22. Getting the: DPAPI Secrets DPAPI (classic) A. MasterKey 1. pwdhash = MD4(password) or SHA1(password) 2. pwdhash_key = HMACSHA1(pwdhash, user_sid) 3. PBKDF2(…, pwdhash_key,…), another elements from the file. Windows 10 no domain: SHA512, AES-256, 8000 rounds 4. Control – HMACSHA512 B. CREDHIST 1. pwdhash = MD4(password) or SHA1(password) 2. pwdhash_key = HMACSHA1(pwdhash, user_sid) 3. PBKDF2(…, pwdhash_key,…), another elements from the file. Windows 10 no domain: SHA512, AES-256, 8000 rounds 4. Control – HMACSHA512 C. DPAPI blob Algorithms are written in the blob itself. DPAPI-NG A. RootKey Algorithms Key derivation function: SP800_108_CTR_HMAC (SHA512) Secret agreement: Diffie-Hellman B. DPAPI blob Key derivation: KDF_SP80056A_CONCAT After getting the key, there is a need for decryption: Key wrap algorithm: RFC3394 (KEK -> CEK) Decryption: AES-256-GCM (CEK, Blob)
- 24. Used to group one or more Web Applications Purpose: Assign resources, serve as a security sandbox Use Worker Processes (w3wp.exe) Their identity is defined in Application Pool settings Process requests to the applications Passwords for AppPool identity can be ’decrypted’ even offline They are stored in the encrypted form in applicationHost.config Conclusion: IIS relies it’s security on Machine Keys (Local System)
- 25. Services Store configuration in the registry Always need some identity to run the executable! Local Security Authority (LSA) Secrets Must be stored locally, especially when domain credentials are used Can be accessed when we impersonate to Local System Their accounts should be monitored If you cannot use gMSA, MSA, use subscription for svc_ accounts (naming convention) Conclusion: Think twice before using an Administrative account, use gMSA
- 26. Chasing the obvious: NTDS.DIT, SAM The above means: To read the clear text password you need to struggle!
- 27. Getting the: Hash SAM 1. bootkey: classes from HKLMSYSTEMCCSControlLsa + [class names for: Data, GBG, JD, Skew1] (+arrays’ permutations) 2. F: HKLMSAMSAMDomainsAccount [F – value] string aqwerty = “!@#$%^&*()qwertyUIOPAzxcvbnmQQQQQQQQQQQQ)(*@&%0”; string anum = “01234567890123456789012345678901234567890”; 3. rchbootkey: MD5(string created after arytmetic functions with F, aqwerty, anum, bootkey) 4. hbootkey: RC4(key, data) -> RC4(rchbootkey, F) 5. MD5(…,hbootkey,…) -> RC4(…)-> DES(…, F) to get the hash (MD4)
- 28. Admin Environment On-Premises Datacenters 3rd Party SaaS Customer and Partner AccessBranch Office Intranet and Remote PCs High Value Assets 3rd Party IaaS Mobile Devices Microsoft Azure Office 365 Azure Active Directory Rights Management Services Key Management ServicesIaaS PaaS
- 29. Active Directory and Administrators control all the assets
- 30. One small mistake can lead to attacker control Attackers Can • Steal any data • Encrypt any data • Modify documents • Impersonate users • Disrupt business operations Active Directory and Administrators control all the assets
- 31. Tier 2 Workstation & Device Admins Tier 0 Domain & Enterprise Admins Tier 1 Server Admins 1. Beachhead (Phishing Attack, etc.) 2. Lateral Movement a. Steal Credentials b. Compromise more hosts & credentials 3. Privilege Escalation a. Get Domain Admin credentials 4. Execute Attacker Mission a. Steal data, destroy systems, etc. b. Persist Presence Compromises privileged access 24-48 Hours
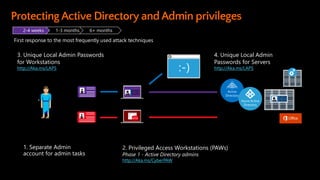
- 33. 2-4 weeks 1-3 months 6+ months Detect Attacks Harden ConfigurationDomain Controller (DC) Host Attacks Credential Theft & Abuse Reduce Agent Attack Surface Attacker Stealth Prevent Escalation Prevent Lateral Traversal Increase Privilege Usage Visibility AD Attacks Assign Least Privilege Attack Defense Securing Privileged Access Three Stage Roadmap http://aka.ms/privsec
- 34. 1. Separate Admin account for admin tasks 3. Unique Local Admin Passwords for Workstations http://Aka.ms/LAPS 2. Privileged Access Workstations (PAWs) Phase 1 - Active Directory admins http://Aka.ms/CyberPAW 4. Unique Local Admin Passwords for Servers http://Aka.ms/LAPS 2-4 weeks 1-3 months 6+ months First response to the most frequently used attack techniques
- 35. 2-4 weeks 1-3 months 6+ months DC Host Attacks Credential Theft & Abuse Attacker Stealth AD Attacks Top Priority Mitigations Attack Defense Detect Attacks Harden DC configuration Reduce DC Agent attack surface Prevent Escalation Prevent Lateral Traversal Increase Privilege Usage Visibility Assign Least Privilege
- 36. 2. Time-bound privileges (no permanent admins) http://aka.ms/PAM http://aka.ms/AzurePIM 1. Privileged Access Workstations (PAWs) Phases 2 and 3 –All Admins and additional hardening (Credential Guard, RDP Restricted Admin, etc.) http://aka.ms/CyberPAW 4. Just Enough Admin (JEA) for DC Maintenance http://aka.ms/JEA 987252 1 6. Attack Detection http://aka.ms/ata 5. Lower attack surface of Domain and DCs http://aka.ms/HardenAD 2-4 weeks 1-3 months 6+ months Build visibility and control of administrator activity, increase protection against typical follow-up attacks 3. Multi-factor for elevation
- 37. 2-4 weeks 1-3 months 6+ monthsAttack Prevent Escalation Defense
- 38. 2. Smartcard or Passport Authentication for all admins http://aka.ms/Passport 1. Modernize Roles and Delegation Model 3. Admin Forest for Active Directory administrators http://aka.ms/ESAE 5. Shielded VMs for virtual DCs (Server 2016 Hyper-V Fabric) http://aka.ms/shieldedvms 4. Code Integrity Policy for DCs (Server 2016) 2-4 weeks 1-3 months 6+ months Move to proactive security posture
- 39. 2-4 weeks 1-3 months 6+ monthsAttack Prevent Escalation Prevent Lateral Traversal Defense
- 40. Credentials not sent to cloud only stored locally Every machine must be registered Active Directory password is not shared
- 41. What is the most successful path for the attack right now?
- 42. :) THE ANATOMY OF AN ATTACK Healthy Computer User Receives Email User Lured to Malicious Site Device Infected with Malware
- 43. HelpDesk Logs into Device Identity Stolen, Attacker Has Increased Privs :) Healthy Computer User Receives Email User Lured to Malicious Site Device Infected with Malware
- 44. User Lured to Malicious Site Device Infected with Malware HelpDesk Logs into Device Identity Stolen, Attacker Has Increased Privs ceives il
- 46. “PASS THE HASH” ATTACKS Today’s security challenge
- 48. User: Adm... Hash:E1977 Fred’s Laptop Fred’s User Session User: Fred Password hash: A3D7… Sue’s Laptop Sue’s User Session Malware Session User: Administrator Password hash: E1977… Malware User Session User: Adm… Hash: E1977 User: Sue Hash: C9DF User: Sue Password hash: C9DF… File Server User: Sue Hash:C9DF 1 3 4 1. FRED RUNS MALWARE, HE IS A LOCAL ADMINISTRATOR 2. THERE IS A PASS THE HASH SESSION ESTABLISHED WITH ANOTHER COMPUTER 3. MALWARE INFECTS SUE’S LAPTOP AS FRED 4. MALWARE INFECTS FILE SERVER AS SUE 2
- 49. Pass-The-Hash Solution: Virtual Secure Mode VSM uses Hyper-V powered secure execution environment to protect derived credentials – you can get things in but can’t get things out Decouples NTLM hash from logon secret Fully randomizes and manages full length NTLM hash to prevent brute force attack Derived credentials that VSM protected LSA Service gives to Windows are non- replayable
- 50. Credential Guard uses virtualization- based security to isolate secrets such as cached credentials Mitigates pass-the-hash or pass- the-ticket attacks Takes advantage of hardware security including secure boot and virtualization
- 51. Virtual Secure Mode Virtual Secure Mode (VSM) Kernel LocalSecurity AuthService Hypervisor Hardware Windows Kernel Apps VirtualTPM Hyper-Visor CodeIntegrity
- 52. Windows 10 Enterprise or Education editions Unified Extensible Firmware Interface (UEFI) 2.3.1 or greater Virtualization Extensions such as Intel VT-X, AMD-V and SLAT must be enabled x64 version of Windows IOMMU, such as Intel VT-d, AMD-Vi TPM 2.0 BIOS lockdown
- 53. Credential Guard can also be deployed on virtual machine Virtual machine must fulfill following requirements: Generation 2 VM Enabled virtual TPM Running Windows 10 or Windows 2016
- 54. Once an attacker has administrative privileges on a machine, it's possible to pull from the memory space of the operating system With IUM, there's a boundary: Drivers can't get into the Local Security Authority Strict signing is enforced in the IUM Credentials are encrypted
- 55. Enabling Credential Guard blocks: Kerberos DES encryption support Kerberos unconstrained delegation Extracting the Kerberos TGT NTLMv1 Applications will prompt and expose credentials to risk: Digest authentication Credential delegation MS-CHAPv2
- 56. Credential Guard does not protect: Local accounts Microsoft accounts AD database on domain controllers Against key loggers Credman When deployed in VM it protects against attacks inside VM, however not against attacks originating from host.
- 59. How to enable VSM?
- 60. How to enable VSM?
- 61. How to enable VSM? …and reboot the machine
- 69. Set SPNs for services to avoid NTLM: SetSPN –L <your service account for AGPM/SQL/Exch/Custom> SetSPN –A Servicename/FQDN of hostname/FQDN of domain domainserviceaccount Reconsider using Kerberos authentication all over https://technet.microsoft.com/en-us/library/jj865668.aspx Require SPN target name validation Microsoft network server: Server SPN target name validation level Reconsider turning on SMB Signing
- 70. Setting Group Policy Setting Registry Key Required * Digitally sign communications (always) – Enabled RequireSecuritySignature = 1 Not Required ** Digitally sign communications (always) – Disabled RequireSecuritySignature = 0 * The default setting for signing on a Domain Controller (defined via Group Policy) is “Required”. ** The default setting for signing on SMB2 Servers and SMB Clients is “Not Required”. Server – Required Server – Not Required Client – Required Signed Signed Client – Not Required Signed* Not Signed** Effective behavior for SMB2/3: * Default for Domain Controller SMB traffic. ** Default for all other SMB traffic.
- 72. ~ 50% of organizations have experienced a malware infection via email in the past calendar year $115 per user – amount spent on security software in 2014 When $33 of that was underutilized or never used ~ 84% of IT Pros believe they need at least to double their staff to respond to security issues When 49% of security positions were left unfilled in 2014 Source: http://pwc.com
- 73. Sad facts Photo: the New York Times Magazine
- 74. Encrypts data
- 76. In theory: Once the payment is verified, the program will decrypt the files The private key that is used to decrypt the infected files is on the C&C server "C:WindowsSYSWOW64cmd.exe" /C "C:WindowsSysnativevssadmin.exe" Delete Shadows /All /Quiet Encrypts data stored on network shares if the shared folders are mapped as a drive letter on the infected computer Infection spawns two processes of itself It was a normal PDF file…
- 77. 1. Back up your data 2. 3. 4. 5. 6. 7. 8. 9. 10. 11. Arrange Security Awareness campaigns
- 78. The high level steps to configure code integrity: Group devices into similar roles – some systems might require different policies (or you may wish to enable CCI for only select systems such as Point of Sale systems or Kiosks. Use PowerShell to create integrity policies from “golden” PCs (use the New-CIPolicy Cmdlet) After auditing, merge code integrity policies using PowerShell (if needed) (Merge-CIPolicy Cmdlet) Discover unsigned LOB apps and generate security catalogs as needed (Package Inspector & signtool.exe – more info on this in a subsequent post) Deploy code integrity policies and catalog files (GP Setting Below + Copying .cat files to catroot – C:WindowsSystem32{F750E6C3-38EE-11D1-85E5- 00C04FC295EE}) The Group Policy setting in question is Computer Configuration Administrative Templates System Device Guard Deploy Code Integrity Policy
- 83. Disk
- 85. Memory Handles Processes Hidden Processes (ActiveProcessLinks) Files that can be extracted Threads Modules Registry API Hooks Services UserAssist Shellbags ShimCache Event Logs Timeline
- 86. Getting the: Hash SAM 1. bootkey: classes from HKLMSYSTEMCCSControlLsa + [class names for: Data, GBG, JD, Skew1] (+arrays’ permutations) 2. F: HKLMSAMSAMDomainsAccount [F – value] string aqwerty = “!@#$%^&*()qwertyUIOPAzxcvbnmQQQQQQQQQQQQ)(*@&%0”; string anum = “01234567890123456789012345678901234567890”; 3. rchbootkey: MD5(string created after arytmetic functions with F, aqwerty, anum, bootkey) 4. hbootkey: RC4(key, data) -> RC4(rchbootkey, F) 5. MD5(…,hbootkey,…) -> RC4(…)-> DES(…, F) to get the hash (MD4)
- 87. Getting the: service account secrets 1. bootkey: klasy z HKLMSYSTEMCCSControlLsa + [class names for: Data, GBG, JD, Skew1] int[] permutationBootKey = new int[] { 0x8, 0x5, 0x4, 0x2, 0xb, 0x9, 0xd, 0x3, 0x0, 0x6, 0x1, 0xc, 0xe, 0xa, 0xf, 0x7 }; 2. PolEKList: HKLMSECURITYPolicyPolEKList [default value] 3. lsakey: AES_DECRYPT(key, data) -> AES(bootkey, PolEKList) 4. NL$KM secret: HKLMSECURITYPolicySecretsNL$KM 5. nlkm_decrypted: AES_DECRYPT(lsakey, NL$KM secret)
- 88. Getting the: DPAPI Secrets DPAPI (classic) A. MasterKey 1. pwdhash = MD4(password) or SHA1(password) 2. pwdhash_key = HMACSHA1(pwdhash, user_sid) 3. PBKDF2(…, pwdhash_key,…), another elements from the file. Windows 10 no domain: SHA512, AES-256, 8000 rounds 4. Control – HMACSHA512 B. CREDHIST 1. pwdhash = MD4(password) or SHA1(password) 2. pwdhash_key = HMACSHA1(pwdhash, user_sid) 3. PBKDF2(…, pwdhash_key,…), another elements from the file. Windows 10 no domain: SHA512, AES-256, 8000 rounds 4. Control – HMACSHA512 C. DPAPI blob Algorithms are written in the blob itself. DPAPI-NG A. RootKey Algorithms Key derivation function: SP800_108_CTR_HMAC (SHA512) Secret agreement: Diffie-Hellman B. DPAPI blob Key derivation: KDF_SP80056A_CONCAT After getting the key, there is a need for decryption: Key wrap algorithm: RFC3394 (KEK -> CEK) Decryption: AES-256-GCM (CEK, Blob)
- 89. Getting the: cached data MSDCC2 1.bootkey: classes from HKLMSYSTEMCCSControlLsa + [class names for: Data, GBG, JD, Skew1] (+arrays’ permutations) int[] permutationBootKey = new int[] { 0x8, 0x5, 0x4, 0x2, 0xb, 0x9, 0xd, 0x3, 0x0, 0x6, 0x1, 0xc, 0xe, 0xa, 0xf, 0x7 }; 2.PolEKList: HKLMSECURITYPolicyPolEKList [default value] 3.lsakey: AES_DECRYPT(key, data) -> AES(bootkey, PolEKList) 4.NL$KM secret: HKLMSECURITYPolicySecretsNL$KM 5.nlkm_decrypted: AES_DECRYPT(lsakey, NL$KM secret) 6.Cache_Entry{id} -> HKLMSECURITYCacheNL${id} 7.cache_entry_decrypted -> AES_DECRYPT(nlkm_decrypted, Cache_Entry{id})
- 90. Getting the: DPAPI-NG Secrets DPAPI-NG A. RootKey Algorithms Key derivation function: SP800_108_CTR_HMAC (SHA512) Secret agreement: Diffie-Hellman B. DPAPI blob Key derivation: KDF_SP80056A_CONCAT After getting the key, there is a need for decryption: Key wrap algorithm: RFC3394 (KEK -> CEK) Decryption: AES-256-GCM (CEK, Blob)
- 91. Tier 2 Workstation & Device Admins Tier 0 Domain & Enterprise Admins Tier 1 Server Admins 2. Restrict Lateral Movement a. Random Local Password 1. Restrict Privilege Escalation a. Privileged Access Workstations b. Assess AD Security 4. Organizational Preparation a. Strategic Roadmap b. Technical Education Restrict Lateral Movement Restrict Privilege Escalation Attack Detection Advanced Threat Analytics (ATA) Hunt for Adversaries 3. Attack Detection a. Attack Detection b. Hunt for Adversaries Organizational Preparation Education Strategy & Integration
- 92. Vulnerability Management Continuous vulnerability discovery Context-Aware Analysis Prioritization Remediation and Tracking Put on the Hacker’s Shoes External + Internal + Web Penetration tests Configuration reviews Prevention



















![Getting the: cached data
MSDCC2
1.bootkey: classes from HKLMSYSTEMCCSControlLsa + [class
names for: Data, GBG, JD, Skew1] (+arrays’ permutations)
int[] permutationBootKey = new int[] { 0x8, 0x5, 0x4, 0x2,
0xb, 0x9, 0xd, 0x3, 0x0, 0x6, 0x1, 0xc, 0xe, 0xa, 0xf, 0x7
};
2.PolEKList: HKLMSECURITYPolicyPolEKList [default value]
3.lsakey: AES_DECRYPT(key, data) -> AES(bootkey, PolEKList)
4.NL$KM secret: HKLMSECURITYPolicySecretsNL$KM
5.nlkm_decrypted: AES_DECRYPT(lsakey, NL$KM secret)
6.Cache_Entry{id} -> HKLMSECURITYCacheNL${id}
7.cache_entry_decrypted -> AES_DECRYPT(nlkm_decrypted,
Cache_Entry{id})](https://image.slidesharecdn.com/igniteprecon2018cqurev2-180923163426/85/Dear-Hacker-Infrastructure-Security-Reality-Check-20-320.jpg)






![Getting the: Hash
SAM
1. bootkey: classes from HKLMSYSTEMCCSControlLsa +
[class names for: Data, GBG, JD, Skew1] (+arrays’
permutations)
2. F: HKLMSAMSAMDomainsAccount [F – value] string
aqwerty =
“!@#$%^&*()qwertyUIOPAzxcvbnmQQQQQQQQQQQQ)(*@&%0”;
string anum =
“01234567890123456789012345678901234567890”;
3. rchbootkey: MD5(string created after arytmetic
functions with F, aqwerty, anum, bootkey)
4. hbootkey: RC4(key, data) -> RC4(rchbootkey, F)
5. MD5(…,hbootkey,…) -> RC4(…)-> DES(…, F) to get the
hash (MD4)](https://image.slidesharecdn.com/igniteprecon2018cqurev2-180923163426/85/Dear-Hacker-Infrastructure-Security-Reality-Check-27-320.jpg)

























































![Getting the: Hash
SAM
1. bootkey: classes from HKLMSYSTEMCCSControlLsa +
[class names for: Data, GBG, JD, Skew1] (+arrays’
permutations)
2. F: HKLMSAMSAMDomainsAccount [F – value] string
aqwerty =
“!@#$%^&*()qwertyUIOPAzxcvbnmQQQQQQQQQQQQ)(*@&%0”;
string anum =
“01234567890123456789012345678901234567890”;
3. rchbootkey: MD5(string created after arytmetic
functions with F, aqwerty, anum, bootkey)
4. hbootkey: RC4(key, data) -> RC4(rchbootkey, F)
5. MD5(…,hbootkey,…) -> RC4(…)-> DES(…, F) to get the
hash (MD4)](https://image.slidesharecdn.com/igniteprecon2018cqurev2-180923163426/85/Dear-Hacker-Infrastructure-Security-Reality-Check-86-320.jpg)
![Getting the: service account secrets
1. bootkey: klasy z HKLMSYSTEMCCSControlLsa + [class
names for: Data, GBG, JD, Skew1] int[] permutationBootKey =
new int[] { 0x8, 0x5, 0x4, 0x2, 0xb, 0x9, 0xd, 0x3, 0x0, 0x6,
0x1, 0xc, 0xe, 0xa, 0xf, 0x7 };
2. PolEKList: HKLMSECURITYPolicyPolEKList [default value]
3. lsakey: AES_DECRYPT(key, data) -> AES(bootkey, PolEKList)
4. NL$KM secret: HKLMSECURITYPolicySecretsNL$KM
5. nlkm_decrypted: AES_DECRYPT(lsakey, NL$KM secret)](https://image.slidesharecdn.com/igniteprecon2018cqurev2-180923163426/85/Dear-Hacker-Infrastructure-Security-Reality-Check-87-320.jpg)

![Getting the: cached data
MSDCC2
1.bootkey: classes from HKLMSYSTEMCCSControlLsa + [class
names for: Data, GBG, JD, Skew1] (+arrays’ permutations)
int[] permutationBootKey = new int[] { 0x8, 0x5, 0x4, 0x2,
0xb, 0x9, 0xd, 0x3, 0x0, 0x6, 0x1, 0xc, 0xe, 0xa, 0xf, 0x7
};
2.PolEKList: HKLMSECURITYPolicyPolEKList [default value]
3.lsakey: AES_DECRYPT(key, data) -> AES(bootkey, PolEKList)
4.NL$KM secret: HKLMSECURITYPolicySecretsNL$KM
5.nlkm_decrypted: AES_DECRYPT(lsakey, NL$KM secret)
6.Cache_Entry{id} -> HKLMSECURITYCacheNL${id}
7.cache_entry_decrypted -> AES_DECRYPT(nlkm_decrypted,
Cache_Entry{id})](https://image.slidesharecdn.com/igniteprecon2018cqurev2-180923163426/85/Dear-Hacker-Infrastructure-Security-Reality-Check-89-320.jpg)










































































