Deep Learning for Fraud Detection
Download as PPTX, PDF27 likes17,736 views
This document summarizes a presentation on deep learning and fraud detection. The presentation explores the state of the art in deep learning and fraud detection, provides guidance on getting results, and includes experiments. The agenda includes discussing motivation for advanced modeling in fraud detection, explaining neural networks and deep learning, and exploring sample fraud detection features and challenges. Examples of applying clustering and autoencoders to time series anomaly detection and card velocity fraud detection are also summarized.
1 of 77
Downloaded 941 times











































































Ad
Recommended
Credit Card Fraud Detection Using ML In Databricks



Credit Card Fraud Detection Using ML In DatabricksDatabricks In the Credit Card Companies, illegitimate credit card usage is a serious problem which results in a need to accurately detect fraudulent transactions vs non-fraudulent transactions. All organizations can be hugely impacted by fraud and fraudulent activities, especially those in financial services. The threat can originate from internal or external, but the effects can be devastating – including loss of consumer confidence, incarceration for those involved, even up to downfall of a corporation. Despite regular fraud prevention measures, these are constantly being put to the test in an attempt to beat the system.
Fraud detection is a task of predicting whether a card has been used by the cardholder. One of the methods to recognize fraud card usage is to leverage Machine Learning (ML) models. In order to more dynamically detect fraudulent transactions, one can train ML models on a set of dataset including credit card transaction information as well as card and demographic information of the owner of the account. This will be our goal of the project while leveraging Databricks.
Nitin sharma - Deep Learning Applications to Online Payment Fraud Detection



Nitin sharma - Deep Learning Applications to Online Payment Fraud DetectionMLconf 1. The document discusses applying deep learning techniques to fraud detection in online payments at PayPal.
2. PayPal has a complex ecosystem with millions of accounts across different countries and currencies that transact online and through mobile apps. This presents challenges for reliably separating legitimate and fraudulent transactions at scale.
3. Traditional fraud detection methods using manually engineered features are limited and performance can deteriorate over time as fraud patterns evolve. Deep learning approaches aim to automatically learn representations from raw data to build more robust models.
Build Intelligent Fraud Prevention with Machine Learning and Graphs



Build Intelligent Fraud Prevention with Machine Learning and GraphsNeo4j See how financial services, banking and retail are using graph-enhanced machine learning to thwart fraud. Fraudsters are becoming increasingly sophisticated, organized and adaptive; traditional, rule-based solutions are not broad or nimble enough to deal with this reality. This session will cover several demonstrations and real-world technical examples including preventing credit card fraud, identifying money laundering and reducing false positives.
Fraud detection



Fraud detectionInternational School of Engineering This document summarizes a project to reduce fraudulent card transactions for a US national bank. An ensemble technique using logistic regression and K-nearest neighbors was developed to classify transactions as fraudulent or legitimate in real time. The project was estimated to reduce fraudulent losses by $16-18 million while costing $4.2 million to develop. Testing on 1 year of transaction data accurately classified transactions and reduced fraudulent cases by 80-90%, saving the bank $16 million.
FinTech, AI, Machine Learning in Finance



FinTech, AI, Machine Learning in FinanceSanjiv Das Alexa, Siri, Cortana, Google Assistant
- Vision: Amazon Rekognition, Google Cloud Vision
- Natural Language: IBM Watson, Microsoft LUIS
- Recommendation: Amazon Personalize
- Translation: Google Translate, Microsoft Translator
- Speech: Amazon Polly, Google Cloud Speech
- Conversational AI: Anthropic, Anthropic, Anthropic
- Custom AI Solutions: Google Cloud AI, Microsoft Azure ML
- Low-Code AI: Anthropic, DataRobot, H2O.ai
- Edge AI: AWS Greengrass, Google Edge TPU
- AI Chips: Google TPU, Intel Nervana, Nvidia GPU
Online Payment Fraud Detection with Azure Machine Learning



Online Payment Fraud Detection with Azure Machine LearningStefano Tempesta Fraud detection is one of the earliest industrial applications of anomaly detection and machine learning. As part of the Azure Machine Learning offering, Microsoft provides a template that helps data scientists easily build and deploy an online transaction fraud detection solution. The template includes a collection of pre-configured machine learning modules, as well as custom R scripts, to enable an end-to-end solution.
This session presents best practices, design guidelines and a working implementation for building an online payment fraud detection mechanism in a SharePoint portal connected to a credit card payment gateway. The full source code of the solution is released as open source.
Big Data in Financial Services: How to Improve Performance with Data-Driven D...



Big Data in Financial Services: How to Improve Performance with Data-Driven D...Perficient, Inc. Most banking and financial services organizations have only scratched the surface of leveraging customer data to transform their business, realize new revenue opportunities, manage risk and address customer loyalty. Yet a business’s digital footprint continues to evolve as automated payments, location-based purchases, and unstructured customer communications continue to influence the technology landscape for financial services.
Fraud Detection presentation



Fraud Detection presentationHernan Huwyler Statistical data modeling
Data preprocessing
Matching algorithms
Peer group outliers and covariance
Time-series analysis
ACFE Presentation on Analytics for Fraud Detection and Mitigation



ACFE Presentation on Analytics for Fraud Detection and MitigationScott Mongeau This document discusses continuous fraud monitoring and detection through advanced analytics. It covers trends in analytics including diagnostics, network analytics, and issues with analytics. It also discusses descriptive, predictive, and prescriptive fraud analytics as an integrated process done at an industrial scale. Finally, it discusses advanced analytics methods like supervised modeling, unsupervised discovery, rules-based approaches, outlier detection, and more.
Healthcare fraud detection



Healthcare fraud detectionMahdi Esmailoghli Review of fraud detection and one example of graph analysis
Mahdi Esmailoghli
Amirkabir University of Technology(Tehran Polytechnic)
Fraud Analytics with Machine Learning and Big Data Engineering for Telecom



Fraud Analytics with Machine Learning and Big Data Engineering for TelecomSudarson Roy Pratihar Presentation of a successful project executed on telecom fraud analytics @ 3rd International conference for businees analytics and intelligence, Indian Institute of Management Bangalore
Fraud Detection Techniques



Fraud Detection TechniquesVhena Pilongo This document discusses techniques for detecting fraud, including using ACL (Audit Command Language) software. It describes common fraud schemes like creating fake vendors, payroll fraud, and lapping accounts receivable. For each scheme, it provides an overview and lists specific audit procedures that can be performed in ACL, such as sorting records by invoice number to detect patterns, joining employee and payroll files to find duplicates, and filtering addresses that are tied to multiple vendors.
Artificial Intelligence and Digital Banking - What about fraud prevention ?



Artificial Intelligence and Digital Banking - What about fraud prevention ?Jérôme Kehrli Artificial intelligence for banking fraud prevention.
A presentation on how it takes its root in the digitalisation ways and how it impacts customer experience.
Big Data Analytics in light of Financial Industry 



Big Data Analytics in light of Financial Industry Capgemini Big data and analytics have the potential to transform economies and competition by delivering new productivity growth. Effective use of big data can increase operating margins over 60% for retailers and save $300 billion in US healthcare and $250 billion in European public sector. Companies that improve decision making through big data have seen a 26% performance improvement over 3 years on average. Emerging technologies like self-driving cars will rely heavily on analyzing vast amounts of real-time sensor data.
Practical Crypto Asset Predictions rev



Practical Crypto Asset Predictions revJesus Rodriguez This presentations outlines some of the key principles for building deep learning predictive models for crypto assets. The deck includes best practices and lessons learned that provide some perspectives about the challenges and solutions about using deep learning models in the crypto space.
Evolution of Digital Bank 4.0



Evolution of Digital Bank 4.0Connected Futures The document discusses the evolution of digital banking driven by the Internet of Everything (IoE). It outlines the progression from early dial-up e-banking experiences and multichannel integration to modern digital banks that leverage full-function smartphone apps, big data analytics, 360-degree customer views, and omnichannel experiences personalized for individual customers through intercloud technologies and both structured and unstructured data.
Digital strategy for Financial Institutions



Digital strategy for Financial InstitutionsSameer Singh Jaini Sameer is a digital strategist focusing on removing friction across Banks, NBFCs, Fintechs and Software providers. He is working with Financial Institutions for establishing their digital strategy in alignment with business strategy. The digital strategy would generate value through increase in digital footprint / revenues / cross-sell. This would also reduce costs through productivity gains, automation and process realignment. Digital initiatives as part of strategy would include loan origination, Cross sell platform, Omnichannel platform, Analytics & AI, Mobility and Fintech tie-ups.
This deck is part of his open innovation approach. This can be used by anyone.
Data driven approach to KYC



Data driven approach to KYCPankaj Baid KYC Value Chain, Analytics related activities in KYC value chain, Customer Risk Rating, Trends in KYC and KYC Transformation
Tictaclabs Managed Cyber Security Services



Tictaclabs Managed Cyber Security ServicesTicTac Data Recovery Managed Cyber Security Services allow organizations to focus on daily operations without cyber security interruptions. International studies show 98% of organizations are vulnerable to attacks, with ransomware attacks growing over 2000% in the past 3 years and costing over $20 billion in 2020. An MSSP (Managed Security Services Provider) monitors infrastructure 24/7, provides endpoint protection, data protection including automated backups and disaster recovery, network protection, security operations, and forensics to ensure confidentiality, integrity and availability of data and systems. MSSPs manage all aspects of an organization's security so they can work without interruption from cyber threats.
Explain the Value of your Splunk Deployment Breakout Session



Explain the Value of your Splunk Deployment Breakout SessionSplunk This document provides best practices for documenting value realization from a Splunk deployment. It recommends aligning Splunk use with key organizational objectives. Steps include identifying current success stories, quantifying benefits realized using key metrics, and outlining additional value that can be achieved. Metrics to track include reduced incidents, faster issue resolution, and improved efficiencies. Adoption curves and staff training plans should be defined to fully realize potential value. The document aims to help customers justify further Splunk investment and expansion.
The Journey to Digital Transformation with Touch Bank



The Journey to Digital Transformation with Touch BankBackbase The document summarizes the digital transformation journey of Touch Bank, a fully digital retail bank in Russia, in 3 sentences or less:
Touch Bank launched in April 2015 after a one year build, has over 70,000 customers accessing banking services through internet, mobile, and call centers with no physical branches or ATMs, and has received awards for innovation including Best Online Bank of 2015 and Most Innovative Retail Bank in Russia 2016.
Cybersecurity: Cyber Risk Management for Banks & Financial Institutions



Cybersecurity: Cyber Risk Management for Banks & Financial InstitutionsShawn Tuma Everyone should now understand that no bank or financial institution is immune from cyber risk. Many are now ready to move forward with improving their cyber risk posture but do not know what to do next or how to prioritize their resources. Recognizing that cybersecurity is an overall business risk issue that must be properly managed to comply with many laws and regulations governing banks and financial institutions, this presentation will provide a strategy for how to better understand and manage such risks by:
(1) Providing an overview of the legal and regulatory framework;
(2) Examining the most likely real-world risks; and
(3) Providing strategies for how to manage such risks, including cyber insurance and the development and implementation of an appropriate cyber risk management program (which is not as difficult as it sounds).
Shawn E. Tuma, cybersecurity and data privacy attorney at Spencer Fane, LLP, delivered the presentation titled Cybersecurity: Cyber Risk Management for Banks & Financial Institutions (and Attorneys Who Represent Them) at the Southwest Association of Bank Counsel 42nd Annual Convention on September 20, 2018 (formerly, Texas Association of Bank Counsel).
Inypay Pitch Deck - March 2023-Latest copy 2.pdf



Inypay Pitch Deck - March 2023-Latest copy 2.pdfMustafa Kuğu Inypay aims to provide next-generation financial services to underserved populations in Southeast Asia through a digital banking platform. Their solution addresses the problems of financial exclusion, lack of knowledge, and tedious paperwork that many face. They plan to launch services in Singapore, Philippines, Indonesia, and Vietnam focused on payments, savings, lending, insurance and more. Inypay expects to generate $200 million in revenue by 2026-2027 with an $2 billion valuation by targeting the large unbanked population in Southeast Asia through a digital twin tower strategy serving both retail and SME customers.
DeFi 101



DeFi 101Manish Jain DeFi is decentralized finance that relies on blockchain technology rather than central financial institutions. It provides financial instruments like lending and exchanges through decentralized applications. Popular examples include MakerDAO, which has a stablecoin pegged to the US dollar, and Uniswap, which is an automated market-making exchange. Other innovations in DeFi include NFTs, which are unique digital assets representing items like art, and distributed autonomous organizations that allow protocols to be governed by token holders. While many current DeFi projects may not last, the core ideas of decentralization and blockchain technology underlying DeFi are likely to persist.
Overview of Data Analytics in Lending Business



Overview of Data Analytics in Lending BusinessSanjay Kar AI/ML use cases
BFSI industry overview
Lending Products
Underwriting Strategy
Customer Lifecycle Management
How to prepare for becoming a banking analyst
Materials to study for statistics
What is fintech?
What is a Credit Bureau?
Books for statistics
Tools for data science
Techniques for data science
BaaS-platforms and open APIs in fintech l bank-as-a-service.com



BaaS-platforms and open APIs in fintech l bank-as-a-service.comVladislav Solodkiy What is bank-as-a-service? And why it is so necessary for Asia-Pacific region? Download as pdf in English, Chinese, Korean and Japanese on www.bank-as-a-service.com. Read more on http://www.forbes.com/sites/vladislavsolodkiy/2016/08/03/what-asian-banks-can-learn-from-amazon-about-working-for-fintech/
Trends in AML Compliance and Technology



Trends in AML Compliance and TechnologySAS Institute India Pvt. Ltd SAS was analytics sponsor at AML Summit by Fintelekt in Bangladesh and Mr. Rohan Langley, SAS Fraud & Security Expert AP presented on topic Effective AML Compliance.
SAS Anti-Money Laundering protects your assets by using advanced analytics to uncover illicit activity and comply with AML and CTF regulations.
Digital Insurance - Opportunities in India



Digital Insurance - Opportunities in IndiaThe Digital Insurer The Digital Insurer will be presenting and providing an ‘outside-in’ perspective on opportunities for digital insurance in India.
Modern Data Architecture



Modern Data ArchitectureAlexey Grishchenko This is the presentation for the talk I gave at JavaDay Kiev 2015. This is about an evolution of data processing systems from simple ones with single DWH to the complex approaches like Data Lake, Lambda Architecture and Pipeline architecture
Architectural Overview of MapR's Apache Hadoop Distribution



Architectural Overview of MapR's Apache Hadoop Distributionmcsrivas Describes the thinking behind MapR's architecture. MapR"s Hadoop achieves better reliability on commodity hardware compared to anything on the planet, including custom, proprietary hardware from other vendors. Apache HDFS and Cassandra replication is also discussed, as are SAN and NAS storage systems like Netapp and EMC.
Ad
More Related Content
What's hot (20)
ACFE Presentation on Analytics for Fraud Detection and Mitigation



ACFE Presentation on Analytics for Fraud Detection and MitigationScott Mongeau This document discusses continuous fraud monitoring and detection through advanced analytics. It covers trends in analytics including diagnostics, network analytics, and issues with analytics. It also discusses descriptive, predictive, and prescriptive fraud analytics as an integrated process done at an industrial scale. Finally, it discusses advanced analytics methods like supervised modeling, unsupervised discovery, rules-based approaches, outlier detection, and more.
Healthcare fraud detection



Healthcare fraud detectionMahdi Esmailoghli Review of fraud detection and one example of graph analysis
Mahdi Esmailoghli
Amirkabir University of Technology(Tehran Polytechnic)
Fraud Analytics with Machine Learning and Big Data Engineering for Telecom



Fraud Analytics with Machine Learning and Big Data Engineering for TelecomSudarson Roy Pratihar Presentation of a successful project executed on telecom fraud analytics @ 3rd International conference for businees analytics and intelligence, Indian Institute of Management Bangalore
Fraud Detection Techniques



Fraud Detection TechniquesVhena Pilongo This document discusses techniques for detecting fraud, including using ACL (Audit Command Language) software. It describes common fraud schemes like creating fake vendors, payroll fraud, and lapping accounts receivable. For each scheme, it provides an overview and lists specific audit procedures that can be performed in ACL, such as sorting records by invoice number to detect patterns, joining employee and payroll files to find duplicates, and filtering addresses that are tied to multiple vendors.
Artificial Intelligence and Digital Banking - What about fraud prevention ?



Artificial Intelligence and Digital Banking - What about fraud prevention ?Jérôme Kehrli Artificial intelligence for banking fraud prevention.
A presentation on how it takes its root in the digitalisation ways and how it impacts customer experience.
Big Data Analytics in light of Financial Industry 



Big Data Analytics in light of Financial Industry Capgemini Big data and analytics have the potential to transform economies and competition by delivering new productivity growth. Effective use of big data can increase operating margins over 60% for retailers and save $300 billion in US healthcare and $250 billion in European public sector. Companies that improve decision making through big data have seen a 26% performance improvement over 3 years on average. Emerging technologies like self-driving cars will rely heavily on analyzing vast amounts of real-time sensor data.
Practical Crypto Asset Predictions rev



Practical Crypto Asset Predictions revJesus Rodriguez This presentations outlines some of the key principles for building deep learning predictive models for crypto assets. The deck includes best practices and lessons learned that provide some perspectives about the challenges and solutions about using deep learning models in the crypto space.
Evolution of Digital Bank 4.0



Evolution of Digital Bank 4.0Connected Futures The document discusses the evolution of digital banking driven by the Internet of Everything (IoE). It outlines the progression from early dial-up e-banking experiences and multichannel integration to modern digital banks that leverage full-function smartphone apps, big data analytics, 360-degree customer views, and omnichannel experiences personalized for individual customers through intercloud technologies and both structured and unstructured data.
Digital strategy for Financial Institutions



Digital strategy for Financial InstitutionsSameer Singh Jaini Sameer is a digital strategist focusing on removing friction across Banks, NBFCs, Fintechs and Software providers. He is working with Financial Institutions for establishing their digital strategy in alignment with business strategy. The digital strategy would generate value through increase in digital footprint / revenues / cross-sell. This would also reduce costs through productivity gains, automation and process realignment. Digital initiatives as part of strategy would include loan origination, Cross sell platform, Omnichannel platform, Analytics & AI, Mobility and Fintech tie-ups.
This deck is part of his open innovation approach. This can be used by anyone.
Data driven approach to KYC



Data driven approach to KYCPankaj Baid KYC Value Chain, Analytics related activities in KYC value chain, Customer Risk Rating, Trends in KYC and KYC Transformation
Tictaclabs Managed Cyber Security Services



Tictaclabs Managed Cyber Security ServicesTicTac Data Recovery Managed Cyber Security Services allow organizations to focus on daily operations without cyber security interruptions. International studies show 98% of organizations are vulnerable to attacks, with ransomware attacks growing over 2000% in the past 3 years and costing over $20 billion in 2020. An MSSP (Managed Security Services Provider) monitors infrastructure 24/7, provides endpoint protection, data protection including automated backups and disaster recovery, network protection, security operations, and forensics to ensure confidentiality, integrity and availability of data and systems. MSSPs manage all aspects of an organization's security so they can work without interruption from cyber threats.
Explain the Value of your Splunk Deployment Breakout Session



Explain the Value of your Splunk Deployment Breakout SessionSplunk This document provides best practices for documenting value realization from a Splunk deployment. It recommends aligning Splunk use with key organizational objectives. Steps include identifying current success stories, quantifying benefits realized using key metrics, and outlining additional value that can be achieved. Metrics to track include reduced incidents, faster issue resolution, and improved efficiencies. Adoption curves and staff training plans should be defined to fully realize potential value. The document aims to help customers justify further Splunk investment and expansion.
The Journey to Digital Transformation with Touch Bank



The Journey to Digital Transformation with Touch BankBackbase The document summarizes the digital transformation journey of Touch Bank, a fully digital retail bank in Russia, in 3 sentences or less:
Touch Bank launched in April 2015 after a one year build, has over 70,000 customers accessing banking services through internet, mobile, and call centers with no physical branches or ATMs, and has received awards for innovation including Best Online Bank of 2015 and Most Innovative Retail Bank in Russia 2016.
Cybersecurity: Cyber Risk Management for Banks & Financial Institutions



Cybersecurity: Cyber Risk Management for Banks & Financial InstitutionsShawn Tuma Everyone should now understand that no bank or financial institution is immune from cyber risk. Many are now ready to move forward with improving their cyber risk posture but do not know what to do next or how to prioritize their resources. Recognizing that cybersecurity is an overall business risk issue that must be properly managed to comply with many laws and regulations governing banks and financial institutions, this presentation will provide a strategy for how to better understand and manage such risks by:
(1) Providing an overview of the legal and regulatory framework;
(2) Examining the most likely real-world risks; and
(3) Providing strategies for how to manage such risks, including cyber insurance and the development and implementation of an appropriate cyber risk management program (which is not as difficult as it sounds).
Shawn E. Tuma, cybersecurity and data privacy attorney at Spencer Fane, LLP, delivered the presentation titled Cybersecurity: Cyber Risk Management for Banks & Financial Institutions (and Attorneys Who Represent Them) at the Southwest Association of Bank Counsel 42nd Annual Convention on September 20, 2018 (formerly, Texas Association of Bank Counsel).
Inypay Pitch Deck - March 2023-Latest copy 2.pdf



Inypay Pitch Deck - March 2023-Latest copy 2.pdfMustafa Kuğu Inypay aims to provide next-generation financial services to underserved populations in Southeast Asia through a digital banking platform. Their solution addresses the problems of financial exclusion, lack of knowledge, and tedious paperwork that many face. They plan to launch services in Singapore, Philippines, Indonesia, and Vietnam focused on payments, savings, lending, insurance and more. Inypay expects to generate $200 million in revenue by 2026-2027 with an $2 billion valuation by targeting the large unbanked population in Southeast Asia through a digital twin tower strategy serving both retail and SME customers.
DeFi 101



DeFi 101Manish Jain DeFi is decentralized finance that relies on blockchain technology rather than central financial institutions. It provides financial instruments like lending and exchanges through decentralized applications. Popular examples include MakerDAO, which has a stablecoin pegged to the US dollar, and Uniswap, which is an automated market-making exchange. Other innovations in DeFi include NFTs, which are unique digital assets representing items like art, and distributed autonomous organizations that allow protocols to be governed by token holders. While many current DeFi projects may not last, the core ideas of decentralization and blockchain technology underlying DeFi are likely to persist.
Overview of Data Analytics in Lending Business



Overview of Data Analytics in Lending BusinessSanjay Kar AI/ML use cases
BFSI industry overview
Lending Products
Underwriting Strategy
Customer Lifecycle Management
How to prepare for becoming a banking analyst
Materials to study for statistics
What is fintech?
What is a Credit Bureau?
Books for statistics
Tools for data science
Techniques for data science
BaaS-platforms and open APIs in fintech l bank-as-a-service.com



BaaS-platforms and open APIs in fintech l bank-as-a-service.comVladislav Solodkiy What is bank-as-a-service? And why it is so necessary for Asia-Pacific region? Download as pdf in English, Chinese, Korean and Japanese on www.bank-as-a-service.com. Read more on http://www.forbes.com/sites/vladislavsolodkiy/2016/08/03/what-asian-banks-can-learn-from-amazon-about-working-for-fintech/
Trends in AML Compliance and Technology



Trends in AML Compliance and TechnologySAS Institute India Pvt. Ltd SAS was analytics sponsor at AML Summit by Fintelekt in Bangladesh and Mr. Rohan Langley, SAS Fraud & Security Expert AP presented on topic Effective AML Compliance.
SAS Anti-Money Laundering protects your assets by using advanced analytics to uncover illicit activity and comply with AML and CTF regulations.
Digital Insurance - Opportunities in India



Digital Insurance - Opportunities in IndiaThe Digital Insurer The Digital Insurer will be presenting and providing an ‘outside-in’ perspective on opportunities for digital insurance in India.
Viewers also liked (13)
Modern Data Architecture



Modern Data ArchitectureAlexey Grishchenko This is the presentation for the talk I gave at JavaDay Kiev 2015. This is about an evolution of data processing systems from simple ones with single DWH to the complex approaches like Data Lake, Lambda Architecture and Pipeline architecture
Architectural Overview of MapR's Apache Hadoop Distribution



Architectural Overview of MapR's Apache Hadoop Distributionmcsrivas Describes the thinking behind MapR's architecture. MapR"s Hadoop achieves better reliability on commodity hardware compared to anything on the planet, including custom, proprietary hardware from other vendors. Apache HDFS and Cassandra replication is also discussed, as are SAN and NAS storage systems like Netapp and EMC.
Simplifying Big Data Analytics with Apache Spark



Simplifying Big Data Analytics with Apache SparkDatabricks Apache Spark is a fast and general-purpose cluster computing system for large-scale data processing. It improves on MapReduce by allowing data to be kept in memory across jobs, enabling faster iterative jobs. Spark consists of a core engine along with libraries for SQL, streaming, machine learning, and graph processing. The document discusses new APIs in Spark including DataFrames, which provide a tabular interface like in R/Python, and data sources, which allow plugging external data systems into Spark. These changes aim to make Spark easier for data scientists to use at scale.
Hands on MapR -- Viadea



Hands on MapR -- Viadeaviadea The document discusses MapR cluster management using the MapR CLI. It provides examples of starting and stopping a MapR cluster, managing nodes, volumes, mirrors and schedules. Specific examples include creating volumes, linking mirrors to volumes, syncing mirrors, moving volumes and nodes to different topologies, and creating schedules to automate tasks.
MapR and Cisco Make IT Better



MapR and Cisco Make IT BetterMapR Technologies You’re not the only one still loading your data into data warehouses and building marts or cubes out of it. But today’s data requires a much more accessible environment that delivers real-time results. Prepare for this transformation because your data platform and storage choices are about to undergo a re-platforming that happens once in 30 years.
With the MapR Converged Data Platform (CDP) and Cisco Unified Compute System (UCS), you can optimize today’s infrastructure and grow to take advantage of what’s next. Uncover the range of possibilities from re-platforming by intimately understanding your options for density, performance, functionality and more.
MapR Tutorial Series



MapR Tutorial Seriesselvaraaju MapR clusters disks into storage pools for data distribution. By default, storage pools contain 3 disks each. The mrconfig command can be used to create, remove, and manage storage pools and disks. Each node supports up to 36 storage pools. Zookeeper should always be started before other services and is critical for high availability. Logs are centrally stored for 30 days by default and can be configured through yarn-site.xml.
MapR M7: Providing an enterprise quality Apache HBase API



MapR M7: Providing an enterprise quality Apache HBase APImcsrivas The document provides an overview of MapR M7, an integrated system for structured and unstructured data. M7 combines aspects of LSM trees and B-trees to provide faster reads and writes compared to Apache HBase. It achieves instant recovery from failures through its use of micro write-ahead logs and parallel region recovery. Benchmark results show MapR M7 providing 5-11x faster performance than HBase for common operations like reads, updates, and scans.
Apache Spark & Hadoop



Apache Spark & HadoopMapR Technologies http://bit.ly/1BTaXZP – Hadoop has been a huge success in the data world. It’s disrupted decades of data management practices and technologies by introducing a massively parallel processing framework. The community and the development of all the Open Source components pushed Hadoop to where it is now.
That's why the Hadoop community is excited about Apache Spark. The Spark software stack includes a core data-processing engine, an interface for interactive querying, Sparkstreaming for streaming data analysis, and growing libraries for machine-learning and graph analysis. Spark is quickly establishing itself as a leading environment for doing fast, iterative in-memory and streaming analysis.
This talk will give an introduction the Spark stack, explain how Spark has lighting fast results, and how it complements Apache Hadoop.
Keys Botzum - Senior Principal Technologist with MapR Technologies
Keys is Senior Principal Technologist with MapR Technologies, where he wears many hats. His primary responsibility is interacting with customers in the field, but he also teaches classes, contributes to documentation, and works with engineering teams. He has over 15 years of experience in large scale distributed system design. Previously, he was a Senior Technical Staff Member with IBM, and a respected author of many articles on the WebSphere Application Server as well as a book.
Apache Spark in Depth: Core Concepts, Architecture & Internals



Apache Spark in Depth: Core Concepts, Architecture & InternalsAnton Kirillov Slides cover Spark core concepts of Apache Spark such as RDD, DAG, execution workflow, forming stages of tasks and shuffle implementation and also describes architecture and main components of Spark Driver. The workshop part covers Spark execution modes , provides link to github repo which contains Spark Applications examples and dockerized Hadoop environment to experiment with
MapR Data Analyst



MapR Data Analystselvaraaju This document provides an overview of Pig and Hive for data analysis. It covers how Pig uses Pig Latin for scripts and handles different data types. Hive uses HQL and relies on MapReduce, with details on databases, tables, and query optimization. The document also discusses Hive configuration options and commands.
Apache Spark 2.0: Faster, Easier, and Smarter



Apache Spark 2.0: Faster, Easier, and SmarterDatabricks In this webcast, Reynold Xin from Databricks will be speaking about Apache Spark's new 2.0 major release.
The major themes for Spark 2.0 are:
- Unified APIs: Emphasis on building up higher level APIs including the merging of DataFrame and Dataset APIs
- Structured Streaming: Simplify streaming by building continuous applications on top of DataFrames allow us to unify streaming, interactive, and batch queries.
- Tungsten Phase 2: Speed up Apache Spark by 10X
Introduction to Spark Internals



Introduction to Spark InternalsPietro Michiardi The document provides an overview of Apache Spark internals and Resilient Distributed Datasets (RDDs). It discusses:
- RDDs are Spark's fundamental data structure - they are immutable distributed collections that allow transformations like map and filter to be applied.
- RDDs track their lineage or dependency graph to support fault tolerance. Transformations create new RDDs while actions trigger computation.
- Operations on RDDs include narrow transformations like map that don't require data shuffling, and wide transformations like join that do require shuffling.
- The RDD abstraction allows Spark's scheduler to optimize execution through techniques like pipelining and cache reuse.
Apache Spark Architecture



Apache Spark ArchitectureAlexey Grishchenko This is the presentation I made on JavaDay Kiev 2015 regarding the architecture of Apache Spark. It covers the memory model, the shuffle implementations, data frames and some other high-level staff and can be used as an introduction to Apache Spark
Ad
Similar to Deep Learning for Fraud Detection (20)
How to find what you didn't know to look for, oractical anomaly detection



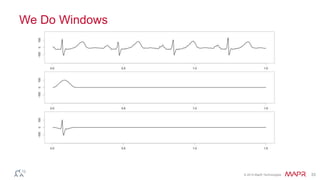
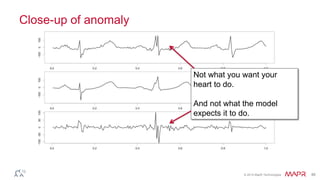
How to find what you didn't know to look for, oractical anomaly detectionDataWorks Summit This document summarizes Ted Dunning's presentation on anomaly detection, time-series databases, and deep learning. The presentation discusses what anomaly detection is, provides examples of detecting anomalies in time-series data, and explains how techniques like sparse coding, autoencoders, and deep learning can be used to build probabilistic models of normal behavior and detect anomalies. It also discusses how these techniques can be applied to build time-series databases that enable semantic search and anomaly detection in real-time and long-term data.
Mathematical bridges From Old to New



Mathematical bridges From Old to NewMapR Technologies The document discusses various techniques for anomaly detection in streaming data. It begins by outlining the basic steps of building an anomaly detection model and detecting anomalies in new data. It then discusses challenges in setting an appropriate threshold to determine what constitutes an anomaly. The document explores using adaptive thresholds and algorithms like t-digest to help determine outliers. It also discusses challenges like non-stationary data and more complex models, as well as techniques like clustering and autoencoders to model time series data.
Anomaly Detection - New York Machine Learning



Anomaly Detection - New York Machine LearningTed Dunning Anomaly detection is the art of finding what you don't know how to ask for. In this talk, I walk through the why and how of building probabilistic models for a variety of problems including continuous signals and web traffic. This talk blends theory and practice in a highly approachable way.
How to tell which algorithms really matter



How to tell which algorithms really matterDataWorks Summit This document discusses how to determine which algorithms and techniques really matter for practical applications.
It provides examples of techniques that had a big impact on recommendations, such as result dithering which improved user experience more than advances in recommendation algorithms. It also discusses how techniques like Bayesian bandits and online clustering with sketches can enable effective exploration and handle large, streaming data. Additionally, it describes how search and recommendations can recursively improve each other through indicator matrices.
Anomaly Detection: How to find what you didn’t know to look for



Anomaly Detection: How to find what you didn’t know to look forTed Dunning A description of a range of basic anomaly detection methods that can be applied to practical problems.
Strata 2014 Anomaly Detection



Strata 2014 Anomaly DetectionTed Dunning This talk describes the general architecture common to anomaly detections systems that are based on probabilistic models. By examining several realistic use cases, I illustrate the common themes and practical implementation methods.
How to Determine which Algorithms Really Matter



How to Determine which Algorithms Really MatterDataWorks Summit Ted Dunning presents on algorithms that really matter for deploying machine learning systems. The most important advances are often not the algorithms but how they are implemented, including making them deployable, robust, transparent, and with the proper skillsets. Clever prototypes don't matter if they can't be standardized. Sketches that produce many weighted centroids can enable online clustering at scale. Recursive search and recommendations, where one implements the other, can also be important.
Hadoop and R Go to the Movies



Hadoop and R Go to the MoviesDataWorks Summit This document discusses using machine learning algorithms to model energy use. It describes how evolutionary algorithms can be used to model energy use in homes and offices, which can help identify problems and save energy. Specifically, it discusses using a meta-evolutionary algorithm that adapts the mutation rate over time based on what has worked best. This approach converges faster than traditional evolutionary algorithms. The document then discusses challenges with visualizing high-dimensional models and solutions for diagnostic visualization and video generation to help understand the machine learning process and solutions.
Predictive Analytics with Hadoop



Predictive Analytics with HadoopDataWorks Summit This document discusses predictive analytics using Hadoop. It provides examples of recommendation and classification using big data. It describes obtaining large training datasets through crowdsourcing and implicit feedback. It also discusses operational considerations for predictive models, including snapshotting data, leveraging NFS for ingestion, and ensuring high availability. The document concludes with a question and answer section.
HUG_Ireland_Streaming_Ted_Dunning



HUG_Ireland_Streaming_Ted_DunningJohn Mulhall A presentation by Ted Dunning of MapR on why Streaming Matters made to the Hadoop User Group (HUG) Ireland at Hadoop Summit on April 12th 2016. This presentation covers streaming and why it is so important in any big data solution
Practical Computing With Chaos



Practical Computing With ChaosDataWorks Summit Ted Dunning presents on practical machine learning techniques. He discusses randomized geo-coding to derive keys that preserve locality. He demonstrates Thompson sampling, a Bayesian approach to exploration versus exploitation tradeoffs. He also covers using dithering to add noise that improves signals and synthetic data generation without privacy violations by sharing only statistical summaries.
Practical Computing with Chaos



Practical Computing with ChaosMapR Technologies Ted Dunning gives a presentation on practical machine learning techniques. He discusses randomized geo-coding to embed spatial data in a total order. He demonstrates Thompson sampling, a Bayesian approach to exploration-exploitation tradeoffs. He also covers dithering in signals and generating synthetic data when real data cannot be shared due to privacy issues.
How the Internet of Things are Turning the Internet Upside Down



How the Internet of Things are Turning the Internet Upside DownDataWorks Summit - The document discusses how time series data from sensors can be ingested and analyzed at large scales. It describes how traditional internet architecture concentrates resources at the core while sensors and devices reside at the edge, producing large amounts of time series data.
- It then summarizes techniques for ingesting and analyzing time series data at rates of millions to hundreds of millions of data points per second using technologies like OpenTSDB, HBase, and MapR databases. This involves batching data at the edge and optimized storage designs.
- The document concludes by discussing the advantages of MapR for time series use cases due to its high ingestion rates and integration with query engines like Drill for flexible analysis of large time series datasets
Dealing with an Upside Down Internet



Dealing with an Upside Down InternetMapR Technologies From the Hadoop Summit 2015 Session with Ted Dunning:
Just when we thought the last mile problem was solved, the Internet of Things is turning the last mile problem of the consumer internet into the first mile problem of the industrial internet. This inversion impacts every aspect of the design of networked applications. I will show how to use existing Hadoop ecosystem tools, such as Spark, Drill and others, to deal successfully with this inversion. I will present real examples of how data from things leads to real business benefits and describe real techniques for how these examples work.
Strata 2014-tdunning-anomaly-detection-140211162923-phpapp01



Strata 2014-tdunning-anomaly-detection-140211162923-phpapp01MapR Technologies This talk describes the general architecture common to anomaly detections systems that are based on probabilistic models. By examining several realistic use cases, I illustrate the common themes and practical implementation methods.
Realistic Synthetic Generation Allows Secure Development



Realistic Synthetic Generation Allows Secure DevelopmentDataWorks Summit Ted Dunning is the Chief Applications Architect at MapR Technologies. He has authored short books on real-world Hadoop, time series databases, anomaly detection, and recommendations. The document discusses how to generate realistic simulated data for testing anomaly detection and fraud analytics systems while keeping the actual customer data private. It describes parametric simulation techniques to match key performance indicators and failure modes rather than precise data distributions in order to emulate complex behaviors and test detection algorithms. Various statistical and database methods are presented for generating different types of numeric, symbolic, and behavioral data.
Realistic Synthetic Generation Allows Secure Development



Realistic Synthetic Generation Allows Secure DevelopmentMapR Technologies From the Hadoop Summit 2015 Session with Ted Dunning.
Open source is great, if developed in the open. Privacy is great, but things have to be private. So what happens when you find an open source bug with private data? How do you even file the bug report? Likewise, how can you develop fraud detection algorithms in academic settings when the training data can't be transported outside a secure perimeter. One answer is really good fake data. Good enough to fool the bug. Good enough to emulate the fraud. I will describe log-synth and several physics based approaches that can do this and tell some real stories about fake data.
Deep Learning vs. Cheap Learning



Deep Learning vs. Cheap LearningMapR Technologies The document discusses how big data has enabled new opportunities by changing scaling laws and problem landscapes. Specifically, linearly scaling costs with big data now make it feasible to process large amounts of data, opening up many problems that were previously impossible or too difficult. This has created many "green field" opportunities where simple approaches can solve important problems. Two examples discussed are using log analysis to detect security threats and using transaction histories to find a common point of compromise for a data breach.
Sharing Sensitive Data Securely



Sharing Sensitive Data SecurelyTed Dunning These are the slides from my talk at FAR Con in Minneapolis recently. The topics are the implications of buried treasure hoards on data security, horror stories and new, simpler and provably secure methods for public data disclosure.
Which Algorithms Really Matter



Which Algorithms Really MatterTed Dunning This is the position talk that I gave at CIKM. Included are 4 algorithms that I feel don't get much academic attention, but which are very important industrially. It isn't necessarily true that these algorithms *should* get academic attention, but I do feel that it is true that they are quite important pragmatically speaking.
Ad
More from DataWorks Summit/Hadoop Summit (20)
Running Apache Spark & Apache Zeppelin in Production



Running Apache Spark & Apache Zeppelin in ProductionDataWorks Summit/Hadoop Summit This document discusses running Apache Spark and Apache Zeppelin in production. It begins by introducing the author and their background. It then covers security best practices for Spark deployments, including authentication using Kerberos, authorization using Ranger/Sentry, encryption, and audit logging. Different Spark deployment modes like Spark on YARN are explained. The document also discusses optimizing Spark performance by tuning executor size and multi-tenancy. Finally, it covers security features for Apache Zeppelin like authentication, authorization, and credential management.
State of Security: Apache Spark & Apache Zeppelin



State of Security: Apache Spark & Apache ZeppelinDataWorks Summit/Hadoop Summit This document discusses Spark security and provides an overview of authentication, authorization, encryption, and auditing in Spark. It describes how Spark leverages Kerberos for authentication and uses services like Ranger and Sentry for authorization. It also outlines how communication channels in Spark are encrypted and some common issues to watch out for related to Spark security.
Unleashing the Power of Apache Atlas with Apache Ranger



Unleashing the Power of Apache Atlas with Apache RangerDataWorks Summit/Hadoop Summit The document discusses the Virtual Data Connector project which aims to leverage Apache Atlas and Apache Ranger to provide unified metadata and access governance across data sources. Key points include:
- The project aims to address challenges of understanding, governing, and controlling access to distributed data through a centralized metadata catalog and policies.
- Apache Atlas provides a scalable metadata repository while Apache Ranger enables centralized access governance. The project will integrate these using a virtualization layer.
- Enhancements to Atlas and Ranger are proposed to better support the project's goals around a unified open metadata platform and metadata-driven governance.
- An initial minimum viable product will be built this year with the goal of an open, collaborative ecosystem around shared
Enabling Digital Diagnostics with a Data Science Platform



Enabling Digital Diagnostics with a Data Science PlatformDataWorks Summit/Hadoop Summit This document discusses using a data science platform to enable digital diagnostics in healthcare. It provides an overview of healthcare data sources and Yale/YNHH's data science platform. It then describes the data science journey process using a clinical laboratory use case as an example. The goal is to use big data and machine learning to improve diagnostic reproducibility, throughput, turnaround time, and accuracy for laboratory testing by developing a machine learning algorithm and real-time data processing pipeline.
Revolutionize Text Mining with Spark and Zeppelin



Revolutionize Text Mining with Spark and ZeppelinDataWorks Summit/Hadoop Summit This document discusses using Apache Spark and MLlib for text mining on big data. It outlines common text mining applications, describes how Spark and MLlib enable scalable machine learning on large datasets, and provides examples of text mining workflows and pipelines that can be built with Spark MLlib algorithms and components like tokenization, feature extraction, and modeling. It also discusses customizing ML pipelines and the Zeppelin notebook platform for collaborative data science work.
Double Your Hadoop Performance with Hortonworks SmartSense



Double Your Hadoop Performance with Hortonworks SmartSenseDataWorks Summit/Hadoop Summit This document compares the performance of Hive and Spark when running the BigBench benchmark. It outlines the structure and use cases of the BigBench benchmark, which aims to cover common Big Data analytical properties. It then describes sequential performance tests of Hive+Tez and Spark on queries from the benchmark using a HDInsight PaaS cluster, finding variations in performance between the systems. Concurrency tests are also run by executing multiple query streams in parallel to analyze throughput.
Hadoop Crash Course



Hadoop Crash CourseDataWorks Summit/Hadoop Summit The document discusses modern data applications and architectures. It introduces Apache Hadoop, an open-source software framework for distributed storage and processing of large datasets across clusters of commodity hardware. Hadoop provides massive scalability and easy data access for applications. The document outlines the key components of Hadoop, including its distributed storage, processing framework, and ecosystem of tools for data access, management, analytics and more. It argues that Hadoop enables organizations to innovate with all types and sources of data at lower costs.
Data Science Crash Course



Data Science Crash CourseDataWorks Summit/Hadoop Summit This document provides an overview of data science and machine learning. It discusses what data science and machine learning are, including extracting insights from data and computers learning without being explicitly programmed. It also covers Apache Spark, which is an open source framework for large-scale data processing. Finally, it discusses common machine learning algorithms like regression, classification, clustering, and dimensionality reduction.
Apache Spark Crash Course



Apache Spark Crash CourseDataWorks Summit/Hadoop Summit This document provides an overview of Apache Spark, including its capabilities and components. Spark is an open-source cluster computing framework that allows distributed processing of large datasets across clusters of machines. It supports various data processing workloads including streaming, SQL, machine learning and graph analytics. The document discusses Spark's APIs like DataFrames and its libraries like Spark SQL, Spark Streaming, MLlib and GraphX. It also provides examples of using Spark for tasks like linear regression modeling.
Dataflow with Apache NiFi



Dataflow with Apache NiFiDataWorks Summit/Hadoop Summit This document provides an overview of Apache NiFi and dataflow. It begins with an introduction to the challenges of moving data effectively within and between systems. It then discusses Apache NiFi's key features for addressing these challenges, including guaranteed delivery, data buffering, prioritized queuing, and data provenance. The document outlines NiFi's architecture and components like repositories and extension points. It also previews a live demo and invites attendees to further discuss Apache NiFi at a Birds of a Feather session.
Schema Registry - Set you Data Free



Schema Registry - Set you Data FreeDataWorks Summit/Hadoop Summit Many Organizations are currently processing various types of data and in different formats. Most often this data will be in free form, As the consumers of this data growing it’s imperative that this free-flowing data needs to adhere to a schema. It will help data consumers to have an expectation of about the type of data they are getting and also they will be able to avoid immediate impact if the upstream source changes its format. Having a uniform schema representation also gives the Data Pipeline a really easy way to integrate and support various systems that use different data formats.
SchemaRegistry is a central repository for storing, evolving schemas. It provides an API & tooling to help developers and users to register a schema and consume that schema without having any impact if the schema changed. Users can tag different schemas and versions, register for notifications of schema changes with versions etc.
In this talk, we will go through the need for a schema registry and schema evolution and showcase the integration with Apache NiFi, Apache Kafka, Apache Storm.
Building a Large-Scale, Adaptive Recommendation Engine with Apache Flink and ...



Building a Large-Scale, Adaptive Recommendation Engine with Apache Flink and ...DataWorks Summit/Hadoop Summit There is increasing need for large-scale recommendation systems. Typical solutions rely on periodically retrained batch algorithms, but for massive amounts of data, training a new model could take hours. This is a problem when the model needs to be more up-to-date. For example, when recommending TV programs while they are being transmitted the model should take into consideration users who watch a program at that time.
The promise of online recommendation systems is fast adaptation to changes, but methods of online machine learning from streams is commonly believed to be more restricted and hence less accurate than batch trained models. Combining batch and online learning could lead to a quickly adapting recommendation system with increased accuracy. However, designing a scalable data system for uniting batch and online recommendation algorithms is a challenging task. In this talk we present our experiences in creating such a recommendation engine with Apache Flink and Apache Spark.
Real-Time Anomaly Detection using LSTM Auto-Encoders with Deep Learning4J on ...



Real-Time Anomaly Detection using LSTM Auto-Encoders with Deep Learning4J on ...DataWorks Summit/Hadoop Summit DeepLearning is not just a hype - it outperforms state-of-the-art ML algorithms. One by one. In this talk we will show how DeepLearning can be used for detecting anomalies on IoT sensor data streams at high speed using DeepLearning4J on top of different BigData engines like ApacheSpark and ApacheFlink. Key in this talk is the absence of any large training corpus since we are using unsupervised machine learning - a domain current DL research threats step-motherly. As we can see in this demo LSTM networks can learn very complex system behavior - in this case data coming from a physical model simulating bearing vibration data. Once draw back of DeepLearning is that normally a very large labaled training data set is required. This is particularly interesting since we can show how unsupervised machine learning can be used in conjunction with DeepLearning - no labeled data set is necessary. We are able to detect anomalies and predict braking bearings with 10 fold confidence. All examples and all code will be made publicly available and open sources. Only open source components are used.
Mool - Automated Log Analysis using Data Science and ML



Mool - Automated Log Analysis using Data Science and MLDataWorks Summit/Hadoop Summit QE automation for large systems is a great step forward in increasing system reliability. In the big-data world, multiple components have to come together to provide end-users with business outcomes. This means, that QE Automations scenarios need to be detailed around actual use cases, cross-cutting components. The system tests potentially generate large amounts of data on a recurring basis, verifying which is a tedious job. Given the multiple levels of indirection, the false positives of actual defects are higher, and are generally wasteful.
At Hortonworks, we’ve designed and implemented Automated Log Analysis System - Mool, using Statistical Data Science and ML. Currently the work in progress has a batch data pipeline with a following ensemble ML pipeline which feeds into the recommendation engine. The system identifies the root cause of test failures, by correlating the failing test cases, with current and historical error records, to identify root cause of errors across multiple components. The system works in unsupervised mode with no perfect model/stable builds/source-code version to refer to. In addition the system provides limited recommendations to file/open past tickets and compares run-profiles with past runs.
How Hadoop Makes the Natixis Pack More Efficient 



How Hadoop Makes the Natixis Pack More Efficient DataWorks Summit/Hadoop Summit Improving business performance is never easy! The Natixis Pack is like Rugby. Working together is key to scrum success. Our data journey would undoubtedly have been so much more difficult if we had not made the move together.
This session is the story of how ‘The Natixis Pack’ has driven change in its current IT architecture so that legacy systems can leverage some of the many components in Hortonworks Data Platform in order to improve the performance of business applications. During this session, you will hear:
• How and why the business and IT requirements originated
• How we leverage the platform to fulfill security and production requirements
• How we organize a community to:
o Guard all the players, no one gets left on the ground!
o Us the platform appropriately (Not every problem is eligible for Big Data and standard databases are not dead)
• What are the most usable, the most interesting and the most promising technologies in the Apache Hadoop community
We will finish the story of a successful rugby team with insight into the special skills needed from each player to win the match!
DETAILS
This session is part business, part technical. We will talk about infrastructure, security and project management as well as the industrial usage of Hive, HBase, Kafka, and Spark within an industrial Corporate and Investment Bank environment, framed by regulatory constraints.
HBase in Practice 



HBase in Practice DataWorks Summit/Hadoop Summit HBase is a distributed, column-oriented database that stores data in tables divided into rows and columns. It is optimized for random, real-time read/write access to big data. The document discusses HBase's key concepts like tables, regions, and column families. It also covers performance tuning aspects like cluster configuration, compaction strategies, and intelligent key design to spread load evenly. Different use cases are suitable for HBase depending on access patterns, such as time series data, messages, or serving random lookups and short scans from large datasets. Proper data modeling and tuning are necessary to maximize HBase's performance.
The Challenge of Driving Business Value from the Analytics of Things (AOT)



The Challenge of Driving Business Value from the Analytics of Things (AOT)DataWorks Summit/Hadoop Summit There has been an explosion of data digitising our physical world – from cameras, environmental sensors and embedded devices, right down to the phones in our pockets. Which means that, now, companies have new ways to transform their businesses – both operationally, and through their products and services – by leveraging this data and applying fresh analytical techniques to make sense of it. But are they ready? The answer is “no” in most cases.
In this session, we’ll be discussing the challenges facing companies trying to embrace the Analytics of Things, and how Teradata has helped customers work through and turn those challenges to their advantage.
Breaking the 1 Million OPS/SEC Barrier in HOPS Hadoop



Breaking the 1 Million OPS/SEC Barrier in HOPS HadoopDataWorks Summit/Hadoop Summit In this talk, we will present a new distribution of Hadoop, Hops, that can scale the Hadoop Filesystem (HDFS) by 16X, from 70K ops/s to 1.2 million ops/s on Spotiy's industrial Hadoop workload. Hops is an open-source distribution of Apache Hadoop that supports distributed metadata for HSFS (HopsFS) and the ResourceManager in Apache YARN. HopsFS is the first production-grade distributed hierarchical filesystem to store its metadata normalized in an in-memory, shared nothing database. For YARN, we will discuss optimizations that enable 2X throughput increases for the Capacity scheduler, enabling scalability to clusters with >20K nodes. We will discuss the journey of how we reached this milestone, discussing some of the challenges involved in efficiently and safely mapping hierarchical filesystem metadata state and operations onto a shared-nothing, in-memory database. We will also discuss the key database features needed for extreme scaling, such as multi-partition transactions, partition-pruned index scans, distribution-aware transactions, and the streaming changelog API. Hops (www.hops.io) is Apache-licensed open-source and supports a pluggable database backend for distributed metadata, although it currently only support MySQL Cluster as a backend. Hops opens up the potential for new directions for Hadoop when metadata is available for tinkering in a mature relational database.
From Regulatory Process Verification to Predictive Maintenance and Beyond wit...



From Regulatory Process Verification to Predictive Maintenance and Beyond wit...DataWorks Summit/Hadoop Summit In high-risk manufacturing industries, regulatory bodies stipulate continuous monitoring and documentation of critical product attributes and process parameters. On the other hand, sensor data coming from production processes can be used to gain deeper insights into optimization potentials. By establishing a central production data lake based on Hadoop and using Talend Data Fabric as a basis for a unified architecture, the German pharmaceutical company HERMES Arzneimittel was able to cater to compliance requirements as well as unlock new business opportunities, enabling use cases like predictive maintenance, predictive quality assurance or open world analytics. Learn how the Talend Data Fabric enabled HERMES Arzneimittel to become data-driven and transform Big Data projects from challenging, hard to maintain hand-coding jobs to repeatable, future-proof integration designs.
Talend Data Fabric combines Talend products into a common set of powerful, easy-to-use tools for any integration style: real-time or batch, big data or master data management, on-premises or in the cloud.
Backup and Disaster Recovery in Hadoop 



Backup and Disaster Recovery in Hadoop DataWorks Summit/Hadoop Summit While you could be tempted assuming data is already safe in a single Hadoop cluster, in practice you have to plan for more. Questions like: "What happens if the entire datacenter fails?, or "How do I recover into a consistent state of data, so that applications can continue to run?" are not a all trivial to answer for Hadoop. Did you know that HDFS snapshots are handling open files not as immutable? Or that HBase snapshots are executed asynchronously across servers and therefore cannot guarantee atomicity for cross region updates (which includes tables)? There is no unified and coherent data backup strategy, nor is there tooling available for many of the included components to build such a strategy. The Hadoop distributions largely avoid this topic as most customers are still in the "single use-case" or PoC phase, where data governance as far as backup and disaster recovery (BDR) is concerned are not (yet) important. This talk first is introducing you to the overarching issue and difficulties of backup and data safety, looking at each of the many components in Hadoop, including HDFS, HBase, YARN, Oozie, the management components and so on, to finally show you a viable approach using built-in tools. You will also learn not to take this topic lightheartedly and what is needed to implement and guarantee a continuous operation of Hadoop cluster based solutions.
Building a Large-Scale, Adaptive Recommendation Engine with Apache Flink and ...



Building a Large-Scale, Adaptive Recommendation Engine with Apache Flink and ...DataWorks Summit/Hadoop Summit
Real-Time Anomaly Detection using LSTM Auto-Encoders with Deep Learning4J on ...



Real-Time Anomaly Detection using LSTM Auto-Encoders with Deep Learning4J on ...DataWorks Summit/Hadoop Summit
The Challenge of Driving Business Value from the Analytics of Things (AOT)



The Challenge of Driving Business Value from the Analytics of Things (AOT)DataWorks Summit/Hadoop Summit
From Regulatory Process Verification to Predictive Maintenance and Beyond wit...



From Regulatory Process Verification to Predictive Maintenance and Beyond wit...DataWorks Summit/Hadoop Summit
Recently uploaded (20)
TrsLabs - Fintech Product & Business Consulting



TrsLabs - Fintech Product & Business ConsultingTrs Labs Hybrid Growth Mandate Model with TrsLabs
Strategic Investments, Inorganic Growth, Business Model Pivoting are critical activities that business don't do/change everyday. In cases like this, it may benefit your business to choose a temporary external consultant.
An unbiased plan driven by clearcut deliverables, market dynamics and without the influence of your internal office equations empower business leaders to make right choices.
Getting things done within a budget within a timeframe is key to Growing Business - No matter whether you are a start-up or a big company
Talk to us & Unlock the competitive advantage
Heap, Types of Heap, Insertion and Deletion



Heap, Types of Heap, Insertion and DeletionJaydeep Kale This pdf will explain what is heap, its type, insertion and deletion in heap and Heap sort
Generative Artificial Intelligence (GenAI) in Business



Generative Artificial Intelligence (GenAI) in BusinessDr. Tathagat Varma My talk for the Indian School of Business (ISB) Emerging Leaders Program Cohort 9. In this talk, I discussed key issues around adoption of GenAI in business - benefits, opportunities and limitations. I also discussed how my research on Theory of Cognitive Chasms helps address some of these issues
Mobile App Development Company in Saudi Arabia



Mobile App Development Company in Saudi ArabiaSteve Jonas EmizenTech is a globally recognized software development company, proudly serving businesses since 2013. With over 11+ years of industry experience and a team of 200+ skilled professionals, we have successfully delivered 1200+ projects across various sectors. As a leading Mobile App Development Company In Saudi Arabia we offer end-to-end solutions for iOS, Android, and cross-platform applications. Our apps are known for their user-friendly interfaces, scalability, high performance, and strong security features. We tailor each mobile application to meet the unique needs of different industries, ensuring a seamless user experience. EmizenTech is committed to turning your vision into a powerful digital product that drives growth, innovation, and long-term success in the competitive mobile landscape of Saudi Arabia.
#StandardsGoals for 2025: Standards & certification roundup - Tech Forum 2025



#StandardsGoals for 2025: Standards & certification roundup - Tech Forum 2025BookNet Canada Book industry standards are evolving rapidly. In the first part of this session, we’ll share an overview of key developments from 2024 and the early months of 2025. Then, BookNet’s resident standards expert, Tom Richardson, and CEO, Lauren Stewart, have a forward-looking conversation about what’s next.
Link to recording, transcript, and accompanying resource: https://bnctechforum.ca/sessions/standardsgoals-for-2025-standards-certification-roundup/
Presented by BookNet Canada on May 6, 2025 with support from the Department of Canadian Heritage.
TrustArc Webinar: Consumer Expectations vs Corporate Realities on Data Broker...



TrustArc Webinar: Consumer Expectations vs Corporate Realities on Data Broker...TrustArc Most consumers believe they’re making informed decisions about their personal data—adjusting privacy settings, blocking trackers, and opting out where they can. However, our new research reveals that while awareness is high, taking meaningful action is still lacking. On the corporate side, many organizations report strong policies for managing third-party data and consumer consent yet fall short when it comes to consistency, accountability and transparency.
This session will explore the research findings from TrustArc’s Privacy Pulse Survey, examining consumer attitudes toward personal data collection and practical suggestions for corporate practices around purchasing third-party data.
Attendees will learn:
- Consumer awareness around data brokers and what consumers are doing to limit data collection
- How businesses assess third-party vendors and their consent management operations
- Where business preparedness needs improvement
- What these trends mean for the future of privacy governance and public trust
This discussion is essential for privacy, risk, and compliance professionals who want to ground their strategies in current data and prepare for what’s next in the privacy landscape.
HCL Nomad Web – Best Practices and Managing Multiuser Environments



HCL Nomad Web – Best Practices and Managing Multiuser Environmentspanagenda Webinar Recording: https://www.panagenda.com/webinars/hcl-nomad-web-best-practices-and-managing-multiuser-environments/
HCL Nomad Web is heralded as the next generation of the HCL Notes client, offering numerous advantages such as eliminating the need for packaging, distribution, and installation. Nomad Web client upgrades will be installed “automatically” in the background. This significantly reduces the administrative footprint compared to traditional HCL Notes clients. However, troubleshooting issues in Nomad Web present unique challenges compared to the Notes client.
Join Christoph and Marc as they demonstrate how to simplify the troubleshooting process in HCL Nomad Web, ensuring a smoother and more efficient user experience.
In this webinar, we will explore effective strategies for diagnosing and resolving common problems in HCL Nomad Web, including
- Accessing the console
- Locating and interpreting log files
- Accessing the data folder within the browser’s cache (using OPFS)
- Understand the difference between single- and multi-user scenarios
- Utilizing Client Clocking
Technology Trends in 2025: AI and Big Data Analytics



Technology Trends in 2025: AI and Big Data AnalyticsInData Labs At InData Labs, we have been keeping an ear to the ground, looking out for AI-enabled digital transformation trends coming our way in 2025. Our report will provide a look into the technology landscape of the future, including:
-Artificial Intelligence Market Overview
-Strategies for AI Adoption in 2025
-Anticipated drivers of AI adoption and transformative technologies
-Benefits of AI and Big data for your business
-Tips on how to prepare your business for innovation
-AI and data privacy: Strategies for securing data privacy in AI models, etc.
Download your free copy nowand implement the key findings to improve your business.
Dev Dives: Automate and orchestrate your processes with UiPath Maestro



Dev Dives: Automate and orchestrate your processes with UiPath MaestroUiPathCommunity This session is designed to equip developers with the skills needed to build mission-critical, end-to-end processes that seamlessly orchestrate agents, people, and robots.
📕 Here's what you can expect:
- Modeling: Build end-to-end processes using BPMN.
- Implementing: Integrate agentic tasks, RPA, APIs, and advanced decisioning into processes.
- Operating: Control process instances with rewind, replay, pause, and stop functions.
- Monitoring: Use dashboards and embedded analytics for real-time insights into process instances.
This webinar is a must-attend for developers looking to enhance their agentic automation skills and orchestrate robust, mission-critical processes.
👨🏫 Speaker:
Andrei Vintila, Principal Product Manager @UiPath
This session streamed live on April 29, 2025, 16:00 CET.
Check out all our upcoming Dev Dives sessions at https://community.uipath.com/dev-dives-automation-developer-2025/.
Cybersecurity Identity and Access Solutions using Azure AD



Cybersecurity Identity and Access Solutions using Azure ADVICTOR MAESTRE RAMIREZ Cybersecurity Identity and Access Solutions using Azure AD
AI and Data Privacy in 2025: Global Trends



AI and Data Privacy in 2025: Global TrendsInData Labs In this infographic, we explore how businesses can implement effective governance frameworks to address AI data privacy. Understanding it is crucial for developing effective strategies that ensure compliance, safeguard customer trust, and leverage AI responsibly. Equip yourself with insights that can drive informed decision-making and position your organization for success in the future of data privacy.
This infographic contains:
-AI and data privacy: Key findings
-Statistics on AI data privacy in the today’s world
-Tips on how to overcome data privacy challenges
-Benefits of AI data security investments.
Keep up-to-date on how AI is reshaping privacy standards and what this entails for both individuals and organizations.
Procurement Insights Cost To Value Guide.pptx



Procurement Insights Cost To Value Guide.pptxJon Hansen Procurement Insights integrated Historic Procurement Industry Archives, serves as a powerful complement — not a competitor — to other procurement industry firms. It fills critical gaps in depth, agility, and contextual insight that most traditional analyst and association models overlook.
Learn more about this value- driven proprietary service offering here.
Rusty Waters: Elevating Lakehouses Beyond Spark



Rusty Waters: Elevating Lakehouses Beyond Sparkcarlyakerly1 Spark is a powerhouse for large datasets, but when it comes to smaller data workloads, its overhead can sometimes slow things down. What if you could achieve high performance and efficiency without the need for Spark?
At S&P Global Commodity Insights, having a complete view of global energy and commodities markets enables customers to make data-driven decisions with confidence and create long-term, sustainable value. 🌍
Explore delta-rs + CDC and how these open-source innovations power lightweight, high-performance data applications beyond Spark! 🚀
HCL Nomad Web – Best Practices und Verwaltung von Multiuser-Umgebungen



HCL Nomad Web – Best Practices und Verwaltung von Multiuser-Umgebungenpanagenda Webinar Recording: https://www.panagenda.com/webinars/hcl-nomad-web-best-practices-und-verwaltung-von-multiuser-umgebungen/
HCL Nomad Web wird als die nächste Generation des HCL Notes-Clients gefeiert und bietet zahlreiche Vorteile, wie die Beseitigung des Bedarfs an Paketierung, Verteilung und Installation. Nomad Web-Client-Updates werden “automatisch” im Hintergrund installiert, was den administrativen Aufwand im Vergleich zu traditionellen HCL Notes-Clients erheblich reduziert. Allerdings stellt die Fehlerbehebung in Nomad Web im Vergleich zum Notes-Client einzigartige Herausforderungen dar.
Begleiten Sie Christoph und Marc, während sie demonstrieren, wie der Fehlerbehebungsprozess in HCL Nomad Web vereinfacht werden kann, um eine reibungslose und effiziente Benutzererfahrung zu gewährleisten.
In diesem Webinar werden wir effektive Strategien zur Diagnose und Lösung häufiger Probleme in HCL Nomad Web untersuchen, einschließlich
- Zugriff auf die Konsole
- Auffinden und Interpretieren von Protokolldateien
- Zugriff auf den Datenordner im Cache des Browsers (unter Verwendung von OPFS)
- Verständnis der Unterschiede zwischen Einzel- und Mehrbenutzerszenarien
- Nutzung der Client Clocking-Funktion
Andrew Marnell: Transforming Business Strategy Through Data-Driven Insights



Andrew Marnell: Transforming Business Strategy Through Data-Driven InsightsAndrew Marnell With expertise in data architecture, performance tracking, and revenue forecasting, Andrew Marnell plays a vital role in aligning business strategies with data insights. Andrew Marnell’s ability to lead cross-functional teams ensures businesses achieve sustainable growth and operational excellence.
Transcript: #StandardsGoals for 2025: Standards & certification roundup - Tec...



Transcript: #StandardsGoals for 2025: Standards & certification roundup - Tec...BookNet Canada Book industry standards are evolving rapidly. In the first part of this session, we’ll share an overview of key developments from 2024 and the early months of 2025. Then, BookNet’s resident standards expert, Tom Richardson, and CEO, Lauren Stewart, have a forward-looking conversation about what’s next.
Link to recording, presentation slides, and accompanying resource: https://bnctechforum.ca/sessions/standardsgoals-for-2025-standards-certification-roundup/
Presented by BookNet Canada on May 6, 2025 with support from the Department of Canadian Heritage.
What is Model Context Protocol(MCP) - The new technology for communication bw...



What is Model Context Protocol(MCP) - The new technology for communication bw...Vishnu Singh Chundawat The MCP (Model Context Protocol) is a framework designed to manage context and interaction within complex systems. This SlideShare presentation will provide a detailed overview of the MCP Model, its applications, and how it plays a crucial role in improving communication and decision-making in distributed systems. We will explore the key concepts behind the protocol, including the importance of context, data management, and how this model enhances system adaptability and responsiveness. Ideal for software developers, system architects, and IT professionals, this presentation will offer valuable insights into how the MCP Model can streamline workflows, improve efficiency, and create more intuitive systems for a wide range of use cases.
Increasing Retail Store Efficiency How can Planograms Save Time and Money.pptx



Increasing Retail Store Efficiency How can Planograms Save Time and Money.pptxAnoop Ashok In today's fast-paced retail environment, efficiency is key. Every minute counts, and every penny matters. One tool that can significantly boost your store's efficiency is a well-executed planogram. These visual merchandising blueprints not only enhance store layouts but also save time and money in the process.
What is Model Context Protocol(MCP) - The new technology for communication bw...



What is Model Context Protocol(MCP) - The new technology for communication bw...Vishnu Singh Chundawat
Deep Learning for Fraud Detection
- 1. © 2014 MapR Technologies 1© 2014 MapR Technologies
- 2. © 2014 MapR Technologies 2 Contact Information Ted Dunning Chief Applications Architect at MapR Technologies Committer & PMC for Apache’s Drill, Zookeeper & others VP of Incubator at Apache Foundation Email [email protected] [email protected] Twitter @ted_dunning
- 3. © 2014 MapR Technologies 3 Goals for Today • Explore the state of the art for deep-learning and fraud detection • Separate at least some of the wheat from the chaff • Provide some realistic guidance for getting results
- 4. © 2014 MapR Technologies 4 Goals for Today • Explore the state of the art for deep-learning and fraud detection • Separate at least some of the wheat from the chaff • Provide some realistic guidance for getting results • Play with cool stuff !
- 5. © 2014 MapR Technologies 5 Agenda • Motivation • What are neural networks and deep learning? • It can be simpler than you think • But, no free lunch / you get what you pay / other clever aphorism • Some experiments • Where to go from here
- 6. © 2014 MapR Technologies 6 Motivation For Advanced Modeling in Fraud • Neural networks have completely dominated credit card fraud detection since late 80’s – Random forest, tree ensembles often used in other kinds of fraud and churn models • The reason is rule-based systems simply don’t work – Well, they do work at first – Fraudsters change tactics, you add rules, interaction mayhem ensues • And learning algorithms really do work – Fraudsters change tactics, you add features and retrain
- 7. © 2014 MapR Technologies 7 So learning is good
- 8. © 2014 MapR Technologies 8 So learning is good But good learning is hard
- 9. © 2014 MapR Technologies 9 So learning is good But good learning is hard And finding good features is really hard
- 10. © 2014 MapR Technologies 10 Some Sample Features • Charge size relative to previous averages for card • Charge size relative to previous average for merchant • Known merchant or not • Doubled transaction • AVS or CVV2 mismatch
- 11. © 2014 MapR Technologies 11 Some Sample Features • Charge size relative to previous averages for card • Charge size relative to previous average for merchant • Known merchant or not • Doubled transaction • Address Verification System or CVV2 mismatch
- 12. © 2014 MapR Technologies 12 Some Sample Features • Charge size relative to previous averages for card • Charge size relative to previous average for merchant • Known merchant or not • Doubled transaction • Address Verification System or Card Verification Value mismatch
- 13. © 2014 MapR Technologies 13 Some Sample Features • Charge size relative to previous averages for card • Charge size relative to previous average for merchant • Known merchant or not • Doubled transaction • Address Verification System or Card Verification Value mismatch • Unusual region for card • Unusual time-of-day relative to history • Magstripe use if chip available • (hundreds more)
- 14. © 2014 MapR Technologies 14 Sequence Based Features • Plausible pattern matching (rent a car, pay for gas at airport) • Probe transactions (gas in wrong place, pizza, big charge) • Previous transaction at compromised merchant • Card velocity
- 15. © 2014 MapR Technologies 15 Key Problems • Good guys need data … that means that fraudsters get first chance at bat • Good guys are careful and test systems before releasing • Bad guys have many low-risk transactions and can change methods quickly • In some areas, fraudster adapt techniques in hours
- 16. © 2014 MapR Technologies 16 Making up features is easy Finding features that add real lift is very hard
- 17. © 2014 MapR Technologies 17 What are neural networks and deep learning? • Start simple … imagine we have 20 features, 0 or 1 – Let’s yell “Fraud” if any of the features is a 1 – Houston, we have a model • But this model isn’t any better than a rule • Also doesn’t have any interesting Greek letters
- 18. © 2014 MapR Technologies 18 Real-world Intrudes • We assumed all features are equally good – What if some are kind of poor or weak? • Can we weight different features more or less? – Can we learn these weights from data?
- 19. © 2014 MapR Technologies 19 Real-world Intrudes • We assumed all features are equally good – What if some are kind of poor or weak? • Can we weight different features more or less? – Can we learn these weights from data?
- 20. © 2014 MapR Technologies 20 Learning Works • Yes. We can learn these models • How we measure error is important • We must have good features • Even good features may need transformation – Take logs of times and monetary values – Subtract means, scale, bin values
- 21. © 2014 MapR Technologies 21 Not Good Enough • We need combinations of models • Simple linear combinations aren’t subtle enough • Enter multi-level models – Can we learn a model that uses combinations of inputs – Where each of those combinations is a model that we learn?
- 22. © 2014 MapR Technologies 22 Yes, Virginia, There IS a Santa Claus Each circle is a sum and a (soft) threshold Arrows are multiplication by a learned weight
- 23. © 2014 MapR Technologies 23 Errors on Output Can Propagate Each circle is sends error to each arrow Arrows weight back- propagating errors Inputs Hidden layer
- 24. © 2014 MapR Technologies 24 Success! Triumph! World domination!
- 25. © 2014 MapR Technologies 25 World domination! With some reservations because features are hard
- 26. © 2014 MapR Technologies 26 Turtles All the Way Down – We Wish • This learning works well for just a few layers • This is still a big deal … – with cool features, we can build real systems • With many layers, the learning no longer converges • Well … until recently
- 27. © 2014 MapR Technologies 27 Model Learning in an Ideal World • If we could just learn the features – Maybe unsupervised, maybe supervised – And at the same time learn the model • Presumably we could build models quicker • And more easily • And we wouldn’t have to dirty our minds with pedestrian domain knowledge
- 28. © 2014 MapR Technologies 28 Example 1 – (not very) Deep Auto-encoder • Let’s take an example where we can learn features • Data is EKG traces • We want to find anomalies – No supervised training
- 29. © 2014 MapR Technologies 29 Spot the Anomaly Anomaly?
- 30. © 2014 MapR Technologies 30 Maybe not!
- 31. © 2014 MapR Technologies 31 Where’s Waldo? This is the real anomaly
- 32. © 2014 MapR Technologies 32 Normal Isn’t Just Normal • What we want is a model of what is normal • What doesn’t fit the model is the anomaly • For simple signals, the model can be simple … • The real world is rarely so accommodating x ~ m(t)+ N(0,e)
- 33. © 2014 MapR Technologies 33 We Do Windows
- 34. © 2014 MapR Technologies 34 We Do Windows
- 35. © 2014 MapR Technologies 35 We Do Windows
- 36. © 2014 MapR Technologies 36 We Do Windows
- 37. © 2014 MapR Technologies 37 We Do Windows
- 38. © 2014 MapR Technologies 38 We Do Windows
- 39. © 2014 MapR Technologies 39 We Do Windows
- 40. © 2014 MapR Technologies 40 We Do Windows
- 41. © 2014 MapR Technologies 41 We Do Windows
- 42. © 2014 MapR Technologies 42 Windows on the World • The set of windowed signals is a nice model of our original signal • Clustering can find the prototypes – Fancier techniques available using sparse coding • The result is a dictionary of shapes • New signals can be encoded by shifting, scaling and adding shapes from the dictionary
- 43. © 2014 MapR Technologies 43 Most Common Shapes (for EKG)
- 44. © 2014 MapR Technologies 44 Reconstructed signal Original signal Reconstructed signal Reconstruction error < 1 bit / sample
- 45. © 2014 MapR Technologies 45 An Anomaly Original technique for finding 1-d anomaly works against reconstruction error
- 46. © 2014 MapR Technologies 46 Close-up of anomaly Not what you want your heart to do. And not what the model expects it to do.
- 47. © 2014 MapR Technologies 47 A Different Kind of Anomaly
- 48. © 2014 MapR Technologies 48 Some k-means Caveats • But Eamonn Keogh says that k-means can’t work on time-series • That is silly … and kind of correct, k-means does have limits – Other kinds of auto-encoders are much more powerful • More fun and code demos at – https://github.com/tdunning/k-means-auto-encoder http://www.cs.ucr.edu/~eamonn/meaningless.pdf
- 49. © 2014 MapR Technologies 49 The Limits of Clustering as Auto-encoder • Clustering is like trying to tile your sample distribution • Can be used to approximate a signal • Filling d dimensional region with k clusters should give • If d is large, this is no good e » 1/ kd
- 50. © 2014 MapR Technologies 50 0 500 1000 1500 2000 −2−1012 Time series training data (first 2000 samples) Time Test data Reconstruction Error
- 51. © 2014 MapR Technologies 51 0 500 1000 1500 2000 0.000.050.100.15 Reconstruction error for time−series data Centroids MAVError Training data Held−out data
- 52. © 2014 MapR Technologies 52 Moral For Auto-encoders • The simplest auto-encoders can be good models • For more complex spaces/signals, more elaborate models may be required – Winner take (absolutely) all may be problematic – In particular, models that allow sparse linear combination may be better • Consider deep learning, recurrent networks, denoising
- 53. © 2014 MapR Technologies 53 How Does Clustering Do Reconstruction? x1 x2 ... xn-1 xn Input For normalized cluster centroids, dot-product and distance are equivalent
- 54. © 2014 MapR Technologies 54 How Does Clustering Do Reconstruction? x1 x2 ... xn-1 xn Input Winner takes all with k-means
- 55. © 2014 MapR Technologies 55 How Does Clustering Do Reconstruction? x1 x2 ... xn-1 xn x'1 x'2 ... x'n-1 x'n Input Hidden layer (clusters) Reconstruction Dot-product scales centroid to reconstruct
- 56. © 2014 MapR Technologies 56 AKA - Neural Network x1 x2 ... xn-1 xn x'1 x'2 ... x'n-1 x'n Input Hidden layer (clusters) Reconstruction
- 57. © 2014 MapR Technologies 57 What If … We Had More Layers? ... ... ... ... ... ... ... ... ... ... ... ... ... ... A B A'
- 58. © 2014 MapR Technologies 58 Other Thoughts • What if we allow more than one cluster to be active? – k-sparse learning!
- 59. © 2014 MapR Technologies 59 Other Thoughts • What if we allow more than one cluster to be active? – k-sparse learning!
- 60. © 2014 MapR Technologies 60 Other Thoughts • What if we allow more than one cluster to be active? – k-sparse learning!
- 61. © 2014 MapR Technologies 61 Other Thoughts • What if we allow more than one cluster to be active? – k-sparse learning! • Well, almost
- 62. © 2014 MapR Technologies 62 The Point of Deep Learning • It isn’t just many hidden layers in a neural network • The goal is to eliminate feature engineering by learning features as well as the classifier
- 63. © 2014 MapR Technologies 63 Experiment 3 – Card Velocity • Most features so far are inherent in the data • Few are true sequence features • Card velocity is a pure combination – Starting point can be anywhere – The issue is where the next point is relative to starting point
- 64. © 2014 MapR Technologies 64 Card Velocity Non-fraud steps are reasonable in terms of distance and time Fraudulent use of card by multiple attackers results in big, fast jumps
- 65. © 2014 MapR Technologies 65 Synthetic Data Example • Generate random point • Take four small steps • If fraud, second step can be large • Result is five positions, each in 3-d on surface of a sphere – Data shape is N x (5 x 3) • Add secondary features containing step size … N x 4
- 66. © 2014 MapR Technologies 66 The Truth is Out There • With the right feature (step-size), it is trivial to spot the fraud • Here we show the step size between positions • Fraud cases take a big jump that others don’t • But they can be anywhere
- 67. © 2014 MapR Technologies 67 But Dimensionality Bites Hard • With the step-size feature, learning succeeds instantly with the simplest models and gets nearly perfect accuracy • Without the step-size feature, learning with TensorFlow gets modest accuracy after substantial learning cost (work in progress, could do better with lots more tuning) • The problem is that there are two many combinations of 15 variables, we need a very specific combination of three pair-wise diffs combined non-linearly into a distance
- 68. © 2014 MapR Technologies 68 104 105 106 1 0 0.2 0.4 0.6 0.8 Data Size AUCorPrecision AUC Precision
- 69. © 2014 MapR Technologies 69 We have a bona fide revolution But old tricks still pay
- 70. © 2014 MapR Technologies 70 Greenfield Problem Landscape
- 71. © 2014 MapR Technologies 71 Mature Problem Landscape
- 72. © 2014 MapR Technologies 72 Summary • There is too much to say in 40 minutes, let’s talk some more at the MapR booth • Deep learning, especially with systems like TensorFlow have huge promise • Deep learning trades learning architecture engineering for feature engineering • There are powerful middle grounds
- 73. © 2014 MapR Technologies 73
- 74. © 2014 MapR Technologies 74 Short Books by Ted Dunning & Ellen Friedman • Published by O’Reilly in 2014 - 2016 • For sale from Amazon or O’Reilly • Free e-books currently available courtesy of MapR http://bit.ly/ebook-real- world-hadoop http://bit.ly/mapr-tsdb- ebook http://bit.ly/ebook- anomaly http://bit.ly/recommend ation-ebook
- 75. © 2014 MapR Technologies 75 Streaming Architecture by Ted Dunning and Ellen Friedman © 2016 (published by O’Reilly) Free copies at book signing today http://bit.ly/mapr-ebook-streams
- 76. © 2014 MapR Technologies 76 Thank You!
- 77. © 2014 MapR Technologies 77 Q&A @mapr maprtech [email protected] Engage with us! MapR maprtech mapr-technologies


