Design and Simulation Triple-DES
Download as PPT, PDF4 likes3,080 views
The document discusses the simulation of a Triple Data Encryption Standard (Triple DES) circuit using VHDL. It provides background on Triple DES, describes the design and structure of the Triple DES circuit in VHDL, and presents the results of testing the encryption and decryption functions of the circuit through simulation. Testing showed the circuit correctly performed encryption and decryption on input data using the Triple DES algorithm. The design utilized some FPGA resources but would require a clock generator and RAM for implementation on an actual FPGA board.
1 of 34
Downloaded 363 times
































Ad
Recommended
6. cryptography



6. cryptography7wounders The document discusses cryptography concepts such as encryption algorithms, key management, digital signatures, and cryptanalysis attacks. It covers symmetric and asymmetric cryptographic systems as well as specific algorithms like DES, RSA, and elliptic curve cryptography. The document also examines requirements for secrecy, authenticity and properties of cryptographic systems.
Cryptography and Network Security



Cryptography and Network SecurityPa Van Tanku This document provides an overview of cryptography. It begins with a brief history of cryptography from ancient times to modern computer cryptography. It then defines basic concepts like encryption, decryption, plaintext and ciphertext. It describes different types of cryptography including codes, ciphers, steganography and computer ciphers. It also discusses cryptanalysis, security mechanisms like encryption, digital signatures and hash algorithms. It concludes by explaining applications of cryptography in daily life like emails and secured communication between family members.
Cryptography



CryptographyJens Patel This document provides an overview of cryptography. It defines cryptography as the science of secret writing and discusses its use in applications like ATM cards and passwords. It describes the basic components of cryptography including plaintext, ciphertext, ciphers, keys, and algorithms. It differentiates between symmetric and asymmetric key cryptography. It provides examples of traditional and modern ciphers, including DES, AES, and RSA algorithms. In conclusion, it states that cryptography techniques help maintain data security, privacy, and integrity.
DES



DESNaga Srimanyu Timmaraju DES was developed as a standard for communications and data protection by an IBM research team in response to a request from the National Bureau of Standards (now called NIST). DES uses the techniques of confusion and diffusion achieved through numerous permutations and the XOR operation. The basic DES process encrypts a 64-bit block using a 56-bit key over 16 complex rounds consisting of permutations and key-dependent calculations. Triple DES was developed as a more secure version of DES.
Cryptography



CryptographySagar Janagonda This document discusses cryptography and its various aspects. Cryptography is the science of securing communication and information. It involves encryption to encode data into an unreadable format and decryption to decode it. There are different types of cryptography like symmetric key, public key, and hash functions. Symmetric key uses a single key for encryption and decryption while public key uses different keys. Hash functions create a unique digest from data but the data cannot be recovered from the digest. Cryptography provides security features like authentication, privacy, integrity and non-repudiation. Keys are numerical values used in encryption algorithms. The document outlines advantages like privacy and disadvantages like the time needed for encryption and decryption.
Cryptography



Cryptographygueste4c97e Cryptography involves secret writing and encrypting messages so that only authorized parties can read them. It uses algorithms and keys to encrypt plaintext into ciphertext. Cryptanalysis involves breaking ciphers, while cryptography is designing ciphers. Cryptology encompasses both cryptography and cryptanalysis. Common encryption models involve plaintext being encrypted into ciphertext using a key, which is then transmitted and decrypted by the intended receiver using the same key.
Cryptography.ppt



Cryptography.pptUday Meena This document provides an overview of cryptography. It begins with basic definitions related to cryptography and a brief history of its use from ancient times to modern ciphers. It then describes different types of ciphers like stream ciphers, block ciphers, and public key cryptosystems. It also covers cryptography methods like symmetric and asymmetric algorithms. Common types of attacks on cryptosystems like brute force, chosen ciphertext, and frequency analysis are also discussed.
Cryptography - 101



Cryptography - 101n|u - The Open Security Community This document provides an overview of cryptography concepts including symmetric and asymmetric key algorithms, cryptographic hashes, and tools for cryptanalysis. It defines common terminology like plaintext, ciphertext, encryption, and decryption. Symmetric algorithms discussed include the Vernam cipher, A5/1, DES, AES, and RC4. Asymmetric algorithms covered are RSA and Diffie-Hellman key exchange. Cryptographic hashes like MD5 and SHA-1 are also summarized along with resources for cryptanalysis.
Diffie-hellman algorithm



Diffie-hellman algorithmComputer_ at_home The Diffie-Hellman algorithm was developed by Whitfield Diffie and Martin Hellman in 1976.
This algorithm was devices not to encrypt the data but to generate same private cryptographic key at both ends so that there is no need to transfer this key from one communication end to another.
Diffie – Hellman algorithm is an algorithm that allows two parties to get the shared secret key using the communication channel, which is not protected from the interception but is protected from modification.
Public Key Cryptography



Public Key CryptographyGopal Sakarkar Public key cryptography uses two keys, a public key that can encrypt messages and a private key that decrypts messages. It has six components: plain text, encryption algorithm, public and private keys, ciphertext, and decryption algorithm. Some key characteristics are that it is computationally infeasible to determine the private key from the public key alone, and encryption/decryption is easy when the relevant key is known. The requirements of public key cryptography are that it is easy to generate a public-private key pair, easy to encrypt with the public key, easy for the recipient to decrypt with the private key, and infeasible to determine the private key from the public key or recover the plaintext from the ciphertext and public key alone
Double DES & Triple DES



Double DES & Triple DESHemant Sharma Double Data Encryption Standard (2DES) and Triple Data Encryption Standard (3DES) with 2 key and 3 key.
block ciphers



block ciphersAsad Ali In cryptography, a block cipher is a deterministic algorithm operating on ... Systems as a means to effectively improve security by combining simple operations such as .... Finally, the cipher should be easily cryptanalyzable, such that it can be ...
Cipher techniques



Cipher techniquesMohd Arif The document provides an overview of cipher techniques including:
- Classical techniques like transposition ciphers, substitution ciphers including the Caesar and Playfair ciphers, and polyalphabetic ciphers like the Vigenere cipher.
- Modern techniques like stream ciphers which encrypt bits one at a time using a pseudorandom keystream, and block ciphers which encrypt blocks of text.
- It also discusses cryptanalysis techniques for analyzing ciphers and discusses how to build more secure systems using techniques like the one-time pad or combining multiple ciphers.
RSA ALGORITHM



RSA ALGORITHMSathish Kumar RSA is an asymmetric cryptographic algorithm used for encrypting and decrypting messages. It uses a public key for encryption and a private key for decryption such that a message encrypted with the public key can only be decrypted with the corresponding private key. The RSA algorithm involves three steps: key generation, encryption, and decryption. It addresses issues of key distribution and digital signatures.
Introduction to Cryptography



Introduction to CryptographySeema Goel The presentation covers the following:
Basic Terms
Cryptography
The General Goals of Cryptography
Common Types of Attacks
Substitution Ciphers
Transposition Cipher
Steganography- “Concealed Writing”
Symmetric Secret Key Encryption
Types of Symmetric Algorithms
Common Symmetric Algorithms
Asymmetric Secret Key Encryption
Common Asymmetric Algorithms
Public Key Cryptography
Hashing Techniques
Hashing Algorithms
Digital Signatures
Transport Layer Security
Public key infrastructure (PKI)
Public Key Cryptography and RSA algorithm



Public Key Cryptography and RSA algorithmIndra97065 Public Key Cryptography and RSA algorithm.Explanation and proof of RSA algorithm in details.it also describer the mathematics behind the RSA. Few mathematics theorem are given which are use in the RSA algorithm.
Cryptography



Cryptographyamiable_indian Cryptography involves encrypting and decrypting information using algorithms and keys. There are two main types: public key cryptography uses different keys for encryption and decryption while private (symmetric) key cryptography uses the same key. Digital signatures provide authentication by encrypting a hash of a message with a private key so receivers can validate the sender. Key management and distribution present challenges to ensure secrecy and prevent unauthorized access.
DES (Data Encryption Standard) pressentation



DES (Data Encryption Standard) pressentationsarhadisoftengg This document discusses data encryption methods. It defines encryption as hiding information so it can only be accessed by those with the key. There are two main types: symmetric encryption uses one key, while asymmetric encryption uses two different but related keys. Encryption works by scrambling data using techniques like transposition, which rearranges the order, and substitution, which replaces parts with other values. The document specifically describes the Data Encryption Standard (DES) algorithm and the public key cryptosystem, which introduced the innovative approach of using different keys for encryption and decryption.
Cryptography



CryptographyRutuja Solkar A brief introduction to Crytography,the various types of crytography and the advantages and disadvantages associated to using the following tyes with some part of the RSA algorithm
Elgamal digital signature



Elgamal digital signatureMDKAWSARAHMEDSAGAR The ElGamal digital signature scheme was described by Tahir Elgamal in 1985. It uses a key pair consisting of a public key and private key, where the private key is used to generate signatures and the public key is used to verify signatures. Signatures provide message authentication, integrity, and non-repudiation by proving the message was signed by the private key holder. The document then proceeds to describe the technical process of generating keys, signing messages, and verifying signatures using ElGamal signatures with an example.
Cryptography and Network Security William Stallings Lawrie Brown



Cryptography and Network Security William Stallings Lawrie BrownInformation Security Awareness Group Block ciphers like DES encrypt data in blocks and are based on the Feistel cipher structure. DES encrypts 64-bit blocks using a 56-bit key and 16 rounds of encryption. Modern cryptanalysis techniques like differential and linear cryptanalysis use statistical analysis to reveal weaknesses in block ciphers, though DES remains relatively secure against these attacks. Careful design of block ciphers, including aspects like non-linear substitution boxes and complex key scheduling, aims to provide security against cryptanalysis.
Trible data encryption standard (3DES)



Trible data encryption standard (3DES)Ahmed Mohamed Mahmoud This document provides an overview of the Triple Data Encryption Standard (3DES). It first briefly describes the original Data Encryption Standard (DES) and its key components including the initial and final permutations, substitution boxes, and key schedule. It then explains that 3DES applies DES three times with three different keys to strengthen security by effectively doubling the key size to 112 bits. Simulations are included showing encryption and decryption using 3DES with equal and different keys.
Cryptography



Cryptographysubodh pawar Today in modern era of internet we share some sensitive data to information transmission. but need to ensure security. So we focus on Cryptography modern technique for secure transmission of information over network.
Cryptography



CryptographyDarshini Parikh Cryptography is the practice and study of securing communication through techniques like encryption. It has evolved through manual, mechanical, and modern eras using computers. Cryptography aims to achieve goals like authentication, confidentiality, integrity, and non-repudiation. Common attacks include brute force, chosen plaintext, and differential power analysis. Symmetric cryptography uses a shared key while asymmetric uses public/private key pairs. Digital signatures and watermarks can authenticate documents. DRM and watermarks control digital content distribution.
Data Encryption Standard (DES)



Data Encryption Standard (DES)Haris Ahmed - DES (Data Encryption Standard) is a symmetric block cipher algorithm that encrypts data in 64-bit blocks using a 56-bit key. It was the first encryption standard adopted by the U.S. government for protecting sensitive unclassified federal government information.
- DES works by performing 16 rounds of complex substitutions and permutations on each data block, encrypting it using the key. It has various modes of operation like ECB, CBC, CFB, OFB, and CTR that specify how it operates on data.
- In 1998, DES was broken using a brute force attack by the Electronic Frontier Foundation in just 3 days, showing the need for stronger algorithms like AES which replaced DES as the encryption standard
Cryptography



CryptographyIGZ Software house The document discusses cryptography concepts including encryption, decryption, symmetric and asymmetric encryption techniques, cryptanalysis methods like brute force attacks, and the importance of secret keys. Symmetric encryption uses a shared secret key by both sender and receiver, while asymmetric encryption uses different public/private keys. Cryptanalysis aims to discover plaintext or keys by techniques like brute force trials or exploiting algorithm weaknesses. Longer cryptographic keys increase the difficulty of brute force attacks breaking the encryption.
Information Security & Cryptography



Information Security & CryptographyArun ACE This document provides an overview of information security and cryptography. It discusses objectives of security like avoiding data threats. It also covers topics like password auditing, data security, authentication, encryption, decryption, public and private key cryptography, digital signatures, and the RSA algorithm. It demonstrates an example of encrypting a message using RSA and decrypting the cipher text. The conclusion emphasizes the importance of information security.
PGP S/MIME



PGP S/MIMESou Jana 1. PGP (Pretty Good Privacy) provides encryption and authentication for email. It uses public key cryptography and digital signatures to encrypt messages and verify sender identity.
2. PGP offers five main services - digital signatures for authentication, symmetric encryption for confidentiality, compression, encoding for email compatibility, and message segmentation.
3. The document describes how PGP provides both authentication and encryption of messages using a combination of public key and symmetric key cryptography. Digital signatures verify the identity of the sender and encrypted symmetric keys protect the confidentiality of messages.
Triple Data Encryption Standard (t-DES) 



Triple Data Encryption Standard (t-DES) Hardik Manocha Project consists of individual modules of encryption and decryption units. Standard T-DES algorithm is implemented. Presently working on to integrate DES with AES to develop stronger crypto algorithm and test the same against Side Channel Attacks and compare different algorithms.
Web Mining & Text Mining



Web Mining & Text MiningHemant Sharma Web mining is the application of data mining techniques to extract knowledge from web data, including web content, structure, and usage data. Web content mining analyzes text, images, and other unstructured data on web pages using natural language processing and information retrieval. Web structure mining examines the hyperlinks between pages to discover relationships. Web usage mining applies data mining methods to server logs and other web data to discover patterns of user behavior on websites. Text mining aims to extract useful information from unstructured text documents using techniques like summarization, information extraction, categorization, and sentiment analysis.
Ad
More Related Content
What's hot (20)
Diffie-hellman algorithm



Diffie-hellman algorithmComputer_ at_home The Diffie-Hellman algorithm was developed by Whitfield Diffie and Martin Hellman in 1976.
This algorithm was devices not to encrypt the data but to generate same private cryptographic key at both ends so that there is no need to transfer this key from one communication end to another.
Diffie – Hellman algorithm is an algorithm that allows two parties to get the shared secret key using the communication channel, which is not protected from the interception but is protected from modification.
Public Key Cryptography



Public Key CryptographyGopal Sakarkar Public key cryptography uses two keys, a public key that can encrypt messages and a private key that decrypts messages. It has six components: plain text, encryption algorithm, public and private keys, ciphertext, and decryption algorithm. Some key characteristics are that it is computationally infeasible to determine the private key from the public key alone, and encryption/decryption is easy when the relevant key is known. The requirements of public key cryptography are that it is easy to generate a public-private key pair, easy to encrypt with the public key, easy for the recipient to decrypt with the private key, and infeasible to determine the private key from the public key or recover the plaintext from the ciphertext and public key alone
Double DES & Triple DES



Double DES & Triple DESHemant Sharma Double Data Encryption Standard (2DES) and Triple Data Encryption Standard (3DES) with 2 key and 3 key.
block ciphers



block ciphersAsad Ali In cryptography, a block cipher is a deterministic algorithm operating on ... Systems as a means to effectively improve security by combining simple operations such as .... Finally, the cipher should be easily cryptanalyzable, such that it can be ...
Cipher techniques



Cipher techniquesMohd Arif The document provides an overview of cipher techniques including:
- Classical techniques like transposition ciphers, substitution ciphers including the Caesar and Playfair ciphers, and polyalphabetic ciphers like the Vigenere cipher.
- Modern techniques like stream ciphers which encrypt bits one at a time using a pseudorandom keystream, and block ciphers which encrypt blocks of text.
- It also discusses cryptanalysis techniques for analyzing ciphers and discusses how to build more secure systems using techniques like the one-time pad or combining multiple ciphers.
RSA ALGORITHM



RSA ALGORITHMSathish Kumar RSA is an asymmetric cryptographic algorithm used for encrypting and decrypting messages. It uses a public key for encryption and a private key for decryption such that a message encrypted with the public key can only be decrypted with the corresponding private key. The RSA algorithm involves three steps: key generation, encryption, and decryption. It addresses issues of key distribution and digital signatures.
Introduction to Cryptography



Introduction to CryptographySeema Goel The presentation covers the following:
Basic Terms
Cryptography
The General Goals of Cryptography
Common Types of Attacks
Substitution Ciphers
Transposition Cipher
Steganography- “Concealed Writing”
Symmetric Secret Key Encryption
Types of Symmetric Algorithms
Common Symmetric Algorithms
Asymmetric Secret Key Encryption
Common Asymmetric Algorithms
Public Key Cryptography
Hashing Techniques
Hashing Algorithms
Digital Signatures
Transport Layer Security
Public key infrastructure (PKI)
Public Key Cryptography and RSA algorithm



Public Key Cryptography and RSA algorithmIndra97065 Public Key Cryptography and RSA algorithm.Explanation and proof of RSA algorithm in details.it also describer the mathematics behind the RSA. Few mathematics theorem are given which are use in the RSA algorithm.
Cryptography



Cryptographyamiable_indian Cryptography involves encrypting and decrypting information using algorithms and keys. There are two main types: public key cryptography uses different keys for encryption and decryption while private (symmetric) key cryptography uses the same key. Digital signatures provide authentication by encrypting a hash of a message with a private key so receivers can validate the sender. Key management and distribution present challenges to ensure secrecy and prevent unauthorized access.
DES (Data Encryption Standard) pressentation



DES (Data Encryption Standard) pressentationsarhadisoftengg This document discusses data encryption methods. It defines encryption as hiding information so it can only be accessed by those with the key. There are two main types: symmetric encryption uses one key, while asymmetric encryption uses two different but related keys. Encryption works by scrambling data using techniques like transposition, which rearranges the order, and substitution, which replaces parts with other values. The document specifically describes the Data Encryption Standard (DES) algorithm and the public key cryptosystem, which introduced the innovative approach of using different keys for encryption and decryption.
Cryptography



CryptographyRutuja Solkar A brief introduction to Crytography,the various types of crytography and the advantages and disadvantages associated to using the following tyes with some part of the RSA algorithm
Elgamal digital signature



Elgamal digital signatureMDKAWSARAHMEDSAGAR The ElGamal digital signature scheme was described by Tahir Elgamal in 1985. It uses a key pair consisting of a public key and private key, where the private key is used to generate signatures and the public key is used to verify signatures. Signatures provide message authentication, integrity, and non-repudiation by proving the message was signed by the private key holder. The document then proceeds to describe the technical process of generating keys, signing messages, and verifying signatures using ElGamal signatures with an example.
Cryptography and Network Security William Stallings Lawrie Brown



Cryptography and Network Security William Stallings Lawrie BrownInformation Security Awareness Group Block ciphers like DES encrypt data in blocks and are based on the Feistel cipher structure. DES encrypts 64-bit blocks using a 56-bit key and 16 rounds of encryption. Modern cryptanalysis techniques like differential and linear cryptanalysis use statistical analysis to reveal weaknesses in block ciphers, though DES remains relatively secure against these attacks. Careful design of block ciphers, including aspects like non-linear substitution boxes and complex key scheduling, aims to provide security against cryptanalysis.
Trible data encryption standard (3DES)



Trible data encryption standard (3DES)Ahmed Mohamed Mahmoud This document provides an overview of the Triple Data Encryption Standard (3DES). It first briefly describes the original Data Encryption Standard (DES) and its key components including the initial and final permutations, substitution boxes, and key schedule. It then explains that 3DES applies DES three times with three different keys to strengthen security by effectively doubling the key size to 112 bits. Simulations are included showing encryption and decryption using 3DES with equal and different keys.
Cryptography



Cryptographysubodh pawar Today in modern era of internet we share some sensitive data to information transmission. but need to ensure security. So we focus on Cryptography modern technique for secure transmission of information over network.
Cryptography



CryptographyDarshini Parikh Cryptography is the practice and study of securing communication through techniques like encryption. It has evolved through manual, mechanical, and modern eras using computers. Cryptography aims to achieve goals like authentication, confidentiality, integrity, and non-repudiation. Common attacks include brute force, chosen plaintext, and differential power analysis. Symmetric cryptography uses a shared key while asymmetric uses public/private key pairs. Digital signatures and watermarks can authenticate documents. DRM and watermarks control digital content distribution.
Data Encryption Standard (DES)



Data Encryption Standard (DES)Haris Ahmed - DES (Data Encryption Standard) is a symmetric block cipher algorithm that encrypts data in 64-bit blocks using a 56-bit key. It was the first encryption standard adopted by the U.S. government for protecting sensitive unclassified federal government information.
- DES works by performing 16 rounds of complex substitutions and permutations on each data block, encrypting it using the key. It has various modes of operation like ECB, CBC, CFB, OFB, and CTR that specify how it operates on data.
- In 1998, DES was broken using a brute force attack by the Electronic Frontier Foundation in just 3 days, showing the need for stronger algorithms like AES which replaced DES as the encryption standard
Cryptography



CryptographyIGZ Software house The document discusses cryptography concepts including encryption, decryption, symmetric and asymmetric encryption techniques, cryptanalysis methods like brute force attacks, and the importance of secret keys. Symmetric encryption uses a shared secret key by both sender and receiver, while asymmetric encryption uses different public/private keys. Cryptanalysis aims to discover plaintext or keys by techniques like brute force trials or exploiting algorithm weaknesses. Longer cryptographic keys increase the difficulty of brute force attacks breaking the encryption.
Information Security & Cryptography



Information Security & CryptographyArun ACE This document provides an overview of information security and cryptography. It discusses objectives of security like avoiding data threats. It also covers topics like password auditing, data security, authentication, encryption, decryption, public and private key cryptography, digital signatures, and the RSA algorithm. It demonstrates an example of encrypting a message using RSA and decrypting the cipher text. The conclusion emphasizes the importance of information security.
PGP S/MIME



PGP S/MIMESou Jana 1. PGP (Pretty Good Privacy) provides encryption and authentication for email. It uses public key cryptography and digital signatures to encrypt messages and verify sender identity.
2. PGP offers five main services - digital signatures for authentication, symmetric encryption for confidentiality, compression, encoding for email compatibility, and message segmentation.
3. The document describes how PGP provides both authentication and encryption of messages using a combination of public key and symmetric key cryptography. Digital signatures verify the identity of the sender and encrypted symmetric keys protect the confidentiality of messages.
Cryptography and Network Security William Stallings Lawrie Brown



Cryptography and Network Security William Stallings Lawrie BrownInformation Security Awareness Group
Viewers also liked (20)
Triple Data Encryption Standard (t-DES) 



Triple Data Encryption Standard (t-DES) Hardik Manocha Project consists of individual modules of encryption and decryption units. Standard T-DES algorithm is implemented. Presently working on to integrate DES with AES to develop stronger crypto algorithm and test the same against Side Channel Attacks and compare different algorithms.
Web Mining & Text Mining



Web Mining & Text MiningHemant Sharma Web mining is the application of data mining techniques to extract knowledge from web data, including web content, structure, and usage data. Web content mining analyzes text, images, and other unstructured data on web pages using natural language processing and information retrieval. Web structure mining examines the hyperlinks between pages to discover relationships. Web usage mining applies data mining methods to server logs and other web data to discover patterns of user behavior on websites. Text mining aims to extract useful information from unstructured text documents using techniques like summarization, information extraction, categorization, and sentiment analysis.
ASIC Implementation of Triple Data Encryption Algorithm (3DES)



ASIC Implementation of Triple Data Encryption Algorithm (3DES)Kevin Xiao Xiao The Triple DES Encryption is a data encryption algorithm which will be used to protect confidential data against unauthorized access. This algorithm can be used to encrypt and decrypt files, which applies the triple data encryption standard (3DES). The project is designed to enhance the security of data stored inside the devices. It enhances the privacy of the user and also able to protect user’s identity. Anyone who wants to read the data file inside the device needs to have the right keys in order to decrypt the file. Businesses may use it to protect corporate secrets, governments use it to secure classified information, and many individuals use it to protect personal information to guard against things like identity theft. The 3DES algorithm makes this design unique and important since it is hard to break. This project is more appropriate for an ASIC design because the project needed to be customized to implement a chip with application-specific logic for a particular use. This kind of task is more suitable for the ASIC rather than microcontroller since microcontroller usually needs more time delay and consumes much more power than ASIC design.The Triple DES Encryptor will track all bytes being transferred to a certain device and then applies bitwise operation for the encryption/decryption algorithm. FPGA will be used to off load the encryption algorithm onto the FPGA from the Atom/Linux, then the block that does the encryption will have to write over the Avalon bus to the FPGA.
Data encryption standard



Data encryption standardPrasad Prabhu DES is a widely-used method of data encryption that uses a private key chosen from 72 quadrillion possible keys to encrypt 64-bit blocks of data using 16 rounds of operations. While DES is considered strong encryption, some use triple DES for additional security. In 1997, a cooperative effort of 14,000 computers broke a DES encrypted message by trying 18 quadrillion keys out of the 72 quadrillion possibilities. DES originated at IBM in 1977 and was adopted by the U.S. government but export was restricted due to security concerns, though free software is now widely available. NIST will not recertify DES and is accepting submissions for its AES replacement standard.
Aes



AesKunal Prajapati The document discusses the Advanced Encryption Standard (AES) algorithm. AES is a symmetric block cipher that encrypts data in blocks of 128 bits using cipher keys of 128, 192, or 256 bits. It operates on a 4x4 column-major order state matrix through 10-14 rounds depending on the key size. Each round consists of four steps: byte substitution, shifting rows, mixing columns, and adding the round key. The key is expanded into a key schedule to derive a different round key for each round.
Chapter 3: Block Ciphers and the Data Encryption Standard



Chapter 3: Block Ciphers and the Data Encryption StandardShafaan Khaliq Bhatti The document discusses the Data Encryption Standard (DES) cipher. It was the most widely used symmetric cipher but has been replaced by the Advanced Encryption Standard (AES). DES encrypts data in 64-bit blocks using a 56-bit key. It operates by applying an initial permutation to the plaintext block, dividing it into halves, and performing 16 rounds of substitution and permutation using 48-bit subkeys generated from the main key. Each round includes expanding, XORing with the subkey, and applying S-boxes and permutations to provide diffusion and confusion.
Data encryption standard



Data encryption standardMohammad Golyani DES (Data Encryption Standard) algorithm is explained in detail in Persian language.
چگونگی کارکرد و ساختار الگوریتم DES
Aes (advance encryption standard) 



Aes (advance encryption standard) Sina Manavi AES (Advanced Encryption Standard) is a symmetric block cipher algorithm that was adopted as a replacement for the DES (Data Encryption Standard) algorithm. AES is considered more secure than DES due to using a larger key size and being more computationally difficult to break. While AES is fast and reliable for encrypting files and documents, it is not suitable for encrypting communications due to the key exchange problem - for that, an asymmetric algorithm like RSA is typically used to securely exchange the AES key.
Data encryption, Description, DES



Data encryption, Description, DESHuawei Technologies Telecommuncations Primer Signals, Building Blocks and Networks.
Data Encryption & Description, DES, Single and Two key Concept
Data Encryption Standard



Data Encryption StandardAmirul Wiramuda The document discusses data encryption using the Data Encryption Standard (DES) and Triple DES (TDES) functionality in Spartan-II FPGAs. It describes how DES and TDES are commonly used encryption algorithms and how a FPGA-based solution from Xilinx and Xentec provides scalability, flexibility and performance for applications requiring data encryption. It also provides technical details on how the DES algorithm works using permutations, substitutions and XOR operations over multiple rounds to encrypt data blocks.
Encryption



EncryptionIGZ Software house Encryption techniques like AES and Triple DES are used to secure data transmission over networks. AES encrypts data in blocks using symmetric encryption with variable key lengths up to 256 bits, making it more secure than older standards like DES with only a 56-bit key. Triple DES applies the DES algorithm three times with two or three keys, strengthening security compared to single DES. Stream and block ciphers differ in whether they encrypt data bits or blocks at a time.
The des algorithm illustrated



The des algorithm illustratedNIKKHILK111 The document summarizes the Data Encryption Standard (DES) algorithm in three main steps:
1. It provides background on how DES was developed by the National Bureau of Standards in response to growing needs for data encryption. DES was adopted as a standard in 1977.
2. It explains the basic mechanics of how DES works, including that it operates on 64-bit blocks of plaintext using 56-bit keys, and generates subkeys through permutations and shifts of the main key.
3. It gives an example of encrypting a sample plaintext message in hexadecimal using DES, showing how the message is padded and divided into blocks for encryption.
Illustration of ssl uses both asymmetric and symmetric encryption



Illustration of ssl uses both asymmetric and symmetric encryptionXiaoqi Zhao SSL uses both asymmetric and symmetric encryption to securely transmit data between a client and server. The server sends its public key to the client, who then encrypts a randomly generated symmetric session key with the public key and sends it to the server. The server decrypts the session key with its private key and then both sides use the session key to encrypt all further communications during that session. A new session key is generated for any subsequent connections between the client and server.
Symmetric encryption



Symmetric encryptionDR RICHMOND ADEBIAYE Modern block ciphers are widely used to provide encryption of quantities of information, and/or a cryptographic checksum to ensure the contents have not been altered. We continue to use block ciphers because they are comparatively fast, and because we know a fair amount about how to design them.
Aes 128 192_256_bits_project_report



Aes 128 192_256_bits_project_reportsakhi rehman The document describes the implementation of the Advanced Encryption Standard (AES) algorithm in Matlab. It includes:
1) An introduction to AES that describes its motivation, definitions, requirements and overall processes.
2) A high-level design section explaining the AES algorithm, its overall structure consisting of key expansion, encryption and decryption processes using operations like SubBytes, ShiftRows, MixColumns and AddRoundKey.
3) A detailed design section describing the individual operations for both encryption and decryption, including pseudo-code. It also provides illustrations of the operations.
4) Sections on key expansion and results from implementing the AES algorithm in Matlab.
Encryption Algorithms for Cloud



Encryption Algorithms for CloudMphasis In this presentation, Amali introduces the topic of SMAC and moves on to the problem area of storage in cloud. Her interest area lies in developing algorithms that make cloud storage safer.
A Tutorial on Linear and Differential Cryptanalysis by Howard M. Heys



A Tutorial on Linear and Differential Cryptanalysis by Howard M. HeysInformation Security Awareness Group This document provides a tutorial on linear and differential cryptanalysis. It summarizes the attacks and applies them to a simple substitution-permutation network cipher as an example. The tutorial explains how to construct linear expressions to exploit the nonlinear properties of the cipher's S-boxes. It also introduces the "piling-up principle", which shows that combining independent biased variables results in a cumulative bias according to a simple formula. The overall goal is to provide an intuitive explanation of these cryptanalysis techniques for novice cryptanalysts.
A Tutorial on Linear and Differential Cryptanalysis by Howard M. Heys



A Tutorial on Linear and Differential Cryptanalysis by Howard M. HeysInformation Security Awareness Group
Ad
Similar to Design and Simulation Triple-DES (20)
Analysis of Cryptographic Algorithms



Analysis of Cryptographic Algorithmsijsrd.com Presently on a daily basis sharing the information over web is becoming a significant issue due to security problems. Thus lots of techniques are needed to protect the shared info in academic degree unsecured channel. The present work target cryptography to secure the data whereas causing inside the network. Encryption has come up as a solution, and plays an awfully necessary role in data security. This security mechanism uses some algorithms to scramble info into unclear text which can be exclusively being decrypted by party those possesses the associated key. This paper is expounded the varied forms of algorithmic rule for encryption & decryption: DES, AES, RSA, and Blowfish. It helps to hunt out the best algorithmic rule.
IMAGE SECURITY BY 3 DES.pdf



IMAGE SECURITY BY 3 DES.pdfDhamuKing1 This document discusses using Triple DES (Data Encryption Standard) to encrypt images for security. It begins with an introduction to the need for encrypting digital images. It then provides background on DES and how Triple DES works by applying the DES cipher algorithm three times with independent keys. The document outlines the Triple DES encryption and decryption process and references used in the project code, which is written in Python.
New Technique Using Multiple Symmetric keys for Multilevel Encryption



New Technique Using Multiple Symmetric keys for Multilevel EncryptionIJERA Editor In a world of accelerating communications, cryptography has become an essential component of the modern
means of communication systems. The emergence of the webas a reliable medium for commerce and
communication has made cryptography an essential component. Many algorithms or ciphers are in use
nowadays. The quality of the cipher is judged byits ability to prevent an unrelated party fromknowingthe
original content of the encrypted message. The proposed “Multilevel Encryption Model” is a cryptosystem that
adopts the basic principles of cryptography. It uses five symmetric keys (multiple)
in floating point numbers, plaintext, substitution techniques and key combinations with unintelligible
sequence to produce the ciphertext. The decryption process is also designed to reproduce the plaintext
Js2517181724



Js2517181724IJERA Editor IJERA (International journal of Engineering Research and Applications) is International online, ... peer reviewed journal. For more detail or submit your article, please visit www.ijera.com
Js2517181724



Js2517181724IJERA Editor The document describes the design of a custom cryptographic processor for implementing symmetric key operations. The processor is implemented on an FPGA using Verilog. It includes instruction units to perform logical operations, arithmetic operations, and finite field arithmetic needed for symmetric key algorithms like AES, Blowfish, RC5, RC6, IDEA. The processor is pipelined for high speed and includes modules for an ALU, control unit, registers, and multiplexers. Experimental results showed the processor operates at high speed with low area and delay compared to a general purpose processor.
Proposing an Encryption Algorithm based on DES



Proposing an Encryption Algorithm based on DESInternational Journal of Science and Research (IJSR) In this paper, a new method for key generation using Data Encryption Standard (DES) is proposed in order to make it more secure than DES algorithm, but at the same time faster than 3DES algorithm. Some parts of the DES are modified to improve its security and performance aspects. The proposed algorithm is named XS-DES (Extra Secure DES). We modify the process of key generation to improve its level of security, and present the proposed algorithm’s design structure in more detail. We increase the size of the key from 64 bits into 128 bits, and then split the key into two halves, left and right (Kl, Kr), and each one consists of 64 bits. XS-DES will be used to encrypt some important information inside the database, like passwords, exam scores, and other confidential details. In other words, to increase the security in the database and protect it from attackers, all critical information must be encrypted using a strong encryption algorithm and a more secure algorithm (XS-DES) is proposed here. A workable Online Examination System (OES) that applies XS-DES and the original DES algorithms is developed. It has gone through some preliminary testings and a comparison is performed between the results of these algorithms based on their strengths in handling database attackers.
New modification on feistel DES algorithm based on multi-level keys 



New modification on feistel DES algorithm based on multi-level keys IJECEIAES The data encryption standard (DES) is one of the most common symmetric encryption algorithms, but it experiences many problems. For example, it uses only one function (XOR) in the encryption process, and the combination of data is finite because it occurs only twice and operates on bits. This paper presents a new modification of the DES to overcome these problems. This could be done through adding a new level of security by increasing the key space (using three keys) during the 16 rounds of the standard encryption algorithm and by replacing the predefined XOR operation with a new # operation. Our proposed algorithm uses three keys instead of one. The first key is the input key used for encrypting and decrypting operations. The second key is used for determining the number of bits, while the third key is used for determining the table numbers, which are from 0 to 255. Having evaluated the complexity of our proposed algorithm, the results show that it is the most complex compared with the well-known DES and other modified algorithms. Consequently, in our proposed algorithm, the attacker try a number of attempts 2 1173 at minimum to decrypt the message. This means that the proposed DES algorithm will increase the security level of the well-known DES.
Slide cipher based encryption



Slide cipher based encryptionMizi Mohamad This document provides information about cipher-based encryption in Java, including:
- It describes common cipher categories like block ciphers and stream ciphers, and symmetric vs asymmetric key algorithms.
- It explains the Cipher class in Java and algorithms supported like DES, Triple DES, and Blowfish. It also covers cipher modes like ECB, CBC, CFB and padding schemes.
- It provides details on how to use the Cipher class to initialize ciphers, encrypt/decrypt data by feeding it in blocks, and obtaining results. It includes a sample code example.
- It discusses special considerations for initializing password-based ciphers that require a salt and iteration count.
Hardware Implementation of Algorithm for Cryptanalysis



Hardware Implementation of Algorithm for Cryptanalysisijcisjournal Cryptanalysis of block ciphers involves massive computations which are independent of each other and can
be instantiated simultaneously so that the solution space is explored at a faster rate. With the advent of low
cost Field Programmable Gate Arrays (FPGA’s), building special purpose hardware for computationally
intensive applications has now become possible. For this the Data Encryption Standard (DES) is used as a
proof of concept. This paper presents the design for Hardware implementation of DES cryptanalysis on
FPGA using exhaustive key search. Two architectures viz. Rolled and Unrolled DES architecture are compared
and based on experimental result the Rolled architecture is implemented on FPGA. The aim of this
work is to make cryptanalysis faster and better.
Final report



Final reportJagbir Kalirai This document discusses lightweight cryptography techniques for RFID systems with limited resources. It compares the Data Encryption Standard (DES) algorithm and a simplified version called Lightweight DES (DESL). DESL reduces gate complexity by eliminating initial/final permutations and using a single S-box, providing around a 20% reduction in gates compared to DES while maintaining throughput. The document also briefly introduces the Advanced Encryption Standard (AES) algorithm.
secure file storage on cloud using hybrid Cryptography ppt.pptx



secure file storage on cloud using hybrid Cryptography ppt.pptxNishmithaHc The document proposes a system for secure file storage on cloud using hybrid cryptography. It uses AES, 3DES and RC6 algorithms to encrypt files before uploading to the cloud. This provides higher security than using a single encryption algorithm. The system allows users to register, login, encrypt files, upload encrypted files to cloud, request files from cloud, decrypt files. It aims to provide secure data storage with less encryption/decryption time compared to existing systems.
secure file Storage on cloud ppt



secure file Storage on cloud pptNishmithaHc The document proposes a system for secure file storage on cloud using hybrid cryptography. It uses AES, 3DES, and RC6 algorithms to encrypt files before uploading to the cloud. This provides higher security than using a single encryption algorithm. The system allows users to register, login, encrypt files, upload encrypted files to cloud, request files from cloud, decrypt files. It aims to provide secure data storage with less encryption/decryption time compared to existing systems.
82 86



82 86Editor IJARCET This document discusses and compares several cryptography algorithms. It begins by introducing symmetric key algorithms like DES, AES, and Blowfish that use the same key for encryption and decryption. It then covers asymmetric key algorithms like RSA that use a public key for encryption and private key for decryption. The document evaluates the algorithms by describing their basic workings, including key sizes, block sizes, number of rounds, and encryption/decryption processes. It aims to study these cryptography algorithms and analyze their performance characteristics.
82 86



82 86Editor IJARCET This document analyzes and compares the performance of various cryptography algorithms. It discusses symmetric key algorithms like DES, AES, Blowfish and IDEA as well as asymmetric algorithms like RSA and Diffie-Hellman. The performance is evaluated based on parameters like encryption/decryption time, memory usage and throughput. Experiments show that Blowfish has better performance than AES for encrypting audio files, with lower average encryption and decryption times. In conclusion, cryptography is important for network security and Blowfish performs encryption/decryption more efficiently than AES for audio files.
Java implementation and performance evaluation of some



Java implementation and performance evaluation of someAlexander Decker This document summarizes a study that compares the performance of four symmetric block ciphers - DES, Triple DES, AES, and Blowfish - under Windows XP and Linux operating systems. The algorithms were implemented in Java using the Java Cryptography Architecture and Java Cryptography Extension. Performance was evaluated based on CPU execution time for encryption, decryption, and key generation operations on files of varying sizes. Test results showed that Blowfish had the fastest performance, followed by AES and then DES, with Triple DES being the slowest. Performance was better under Linux than Windows XP for all algorithms.
DARE Algorithm: A New Security Protocol by Integration of Different Cryptogra...



DARE Algorithm: A New Security Protocol by Integration of Different Cryptogra...IJECEIAES This document proposes a new hybrid cryptographic algorithm called DARE that integrates Digital Signature Algorithm (DSA) for key generation, Data Encryption Standard (DES) for key scheduling, and Advanced Encryption Standard (AES) and Rivest–Shamir–Adleman (RSA) algorithms for encryption. It presents a block diagram of the algorithm and describes the key generation, encryption, and decryption processes. As an example, it generates keys using a passphrase and encrypts a sample message to demonstrate that the algorithm is achievable.
Module 2 network and computer security



Module 2 network and computer securityDeepak John Advanced Encryption Standard, Multiple Encryption and Triple DES, Block Cipher Modes of
operation, Stream Ciphers and RC4, Confidentiality using Symmetric Encryption, Introduction
to Number Theory: Prime Numbers, Fermat’s and Euler’s Theorems, Testing for Primality, The
Chinese Remainder Theorem, Discrete Logarithms, Public-Key Cryptography and RSA
Biomedical image transmission based on Modified feistal algorithm



Biomedical image transmission based on Modified feistal algorithmijcsit This document presents a high-performance hardware implementation of a biomedical image encryption system using a modified Feistal algorithm. The encryption algorithm is based on DES with a novel key scheduling technique. The encrypted images are unintelligible but have high clarity when decrypted. The system is implemented on an FPGA and achieves an encryption rate of 35.5 Gbit/s. It uses different keys each clock cycle, making the encrypted images very difficult to break.
J0445255



J0445255IJERA Editor International Journal of Engineering Research and Applications (IJERA) is an open access online peer reviewed international journal that publishes research and review articles in the fields of Computer Science, Neural Networks, Electrical Engineering, Software Engineering, Information Technology, Mechanical Engineering, Chemical Engineering, Plastic Engineering, Food Technology, Textile Engineering, Nano Technology & science, Power Electronics, Electronics & Communication Engineering, Computational mathematics, Image processing, Civil Engineering, Structural Engineering, Environmental Engineering, VLSI Testing & Low Power VLSI Design etc.
Georgy Nosenko - An introduction to the use SMT solvers for software security



Georgy Nosenko - An introduction to the use SMT solvers for software securityDefconRussia The document discusses how SMT solvers can be used for software security applications such as bug hunting, exploit generation, protection analysis, and malware analysis by modeling portions of code or algorithms as logical formulas that can then be analyzed using an SMT solver to prove properties or generate inputs. It provides examples of how SMT solvers have been used to find integer overflows, help with program verification, and aid in defeating simple hashing algorithms.
Ad
Recently uploaded (20)
Manifest Pre-Seed Update | A Humanoid OEM Deeptech In France



Manifest Pre-Seed Update | A Humanoid OEM Deeptech In Francechb3 The latest updates on Manifest's pre-seed stage progress.
Complete Guide to Advanced Logistics Management Software in Riyadh.pdf



Complete Guide to Advanced Logistics Management Software in Riyadh.pdfSoftware Company Explore the benefits and features of advanced logistics management software for businesses in Riyadh. This guide delves into the latest technologies, from real-time tracking and route optimization to warehouse management and inventory control, helping businesses streamline their logistics operations and reduce costs. Learn how implementing the right software solution can enhance efficiency, improve customer satisfaction, and provide a competitive edge in the growing logistics sector of Riyadh.
Dev Dives: Automate and orchestrate your processes with UiPath Maestro



Dev Dives: Automate and orchestrate your processes with UiPath MaestroUiPathCommunity This session is designed to equip developers with the skills needed to build mission-critical, end-to-end processes that seamlessly orchestrate agents, people, and robots.
📕 Here's what you can expect:
- Modeling: Build end-to-end processes using BPMN.
- Implementing: Integrate agentic tasks, RPA, APIs, and advanced decisioning into processes.
- Operating: Control process instances with rewind, replay, pause, and stop functions.
- Monitoring: Use dashboards and embedded analytics for real-time insights into process instances.
This webinar is a must-attend for developers looking to enhance their agentic automation skills and orchestrate robust, mission-critical processes.
👨🏫 Speaker:
Andrei Vintila, Principal Product Manager @UiPath
This session streamed live on April 29, 2025, 16:00 CET.
Check out all our upcoming Dev Dives sessions at https://community.uipath.com/dev-dives-automation-developer-2025/.
Linux Support for SMARC: How Toradex Empowers Embedded Developers



Linux Support for SMARC: How Toradex Empowers Embedded DevelopersToradex Toradex brings robust Linux support to SMARC (Smart Mobility Architecture), ensuring high performance and long-term reliability for embedded applications. Here’s how:
• Optimized Torizon OS & Yocto Support – Toradex provides Torizon OS, a Debian-based easy-to-use platform, and Yocto BSPs for customized Linux images on SMARC modules.
• Seamless Integration with i.MX 8M Plus and i.MX 95 – Toradex SMARC solutions leverage NXP’s i.MX 8 M Plus and i.MX 95 SoCs, delivering power efficiency and AI-ready performance.
• Secure and Reliable – With Secure Boot, over-the-air (OTA) updates, and LTS kernel support, Toradex ensures industrial-grade security and longevity.
• Containerized Workflows for AI & IoT – Support for Docker, ROS, and real-time Linux enables scalable AI, ML, and IoT applications.
• Strong Ecosystem & Developer Support – Toradex offers comprehensive documentation, developer tools, and dedicated support, accelerating time-to-market.
With Toradex’s Linux support for SMARC, developers get a scalable, secure, and high-performance solution for industrial, medical, and AI-driven applications.
Do you have a specific project or application in mind where you're considering SMARC? We can help with Free Compatibility Check and help you with quick time-to-market
For more information: https://www.toradex.com/computer-on-modules/smarc-arm-family
Mobile App Development Company in Saudi Arabia



Mobile App Development Company in Saudi ArabiaSteve Jonas EmizenTech is a globally recognized software development company, proudly serving businesses since 2013. With over 11+ years of industry experience and a team of 200+ skilled professionals, we have successfully delivered 1200+ projects across various sectors. As a leading Mobile App Development Company In Saudi Arabia we offer end-to-end solutions for iOS, Android, and cross-platform applications. Our apps are known for their user-friendly interfaces, scalability, high performance, and strong security features. We tailor each mobile application to meet the unique needs of different industries, ensuring a seamless user experience. EmizenTech is committed to turning your vision into a powerful digital product that drives growth, innovation, and long-term success in the competitive mobile landscape of Saudi Arabia.
Rusty Waters: Elevating Lakehouses Beyond Spark



Rusty Waters: Elevating Lakehouses Beyond Sparkcarlyakerly1 Spark is a powerhouse for large datasets, but when it comes to smaller data workloads, its overhead can sometimes slow things down. What if you could achieve high performance and efficiency without the need for Spark?
At S&P Global Commodity Insights, having a complete view of global energy and commodities markets enables customers to make data-driven decisions with confidence and create long-term, sustainable value. 🌍
Explore delta-rs + CDC and how these open-source innovations power lightweight, high-performance data applications beyond Spark! 🚀
Cyber Awareness overview for 2025 month of security



Cyber Awareness overview for 2025 month of securityriccardosl1 Cyber awareness training educates employees on risk associated with internet and malicious emails
tecnologias de las primeras civilizaciones.pdf



tecnologias de las primeras civilizaciones.pdffjgm517 descaripcion detallada del avance de las tecnologias en mesopotamia, egipto, roma y grecia.
Noah Loul Shares 5 Steps to Implement AI Agents for Maximum Business Efficien...



Noah Loul Shares 5 Steps to Implement AI Agents for Maximum Business Efficien...Noah Loul Artificial intelligence is changing how businesses operate. Companies are using AI agents to automate tasks, reduce time spent on repetitive work, and focus more on high-value activities. Noah Loul, an AI strategist and entrepreneur, has helped dozens of companies streamline their operations using smart automation. He believes AI agents aren't just tools—they're workers that take on repeatable tasks so your human team can focus on what matters. If you want to reduce time waste and increase output, AI agents are the next move.
AI Changes Everything – Talk at Cardiff Metropolitan University, 29th April 2...



AI Changes Everything – Talk at Cardiff Metropolitan University, 29th April 2...Alan Dix Talk at the final event of Data Fusion Dynamics: A Collaborative UK-Saudi Initiative in Cybersecurity and Artificial Intelligence funded by the British Council UK-Saudi Challenge Fund 2024, Cardiff Metropolitan University, 29th April 2025
https://alandix.com/academic/talks/CMet2025-AI-Changes-Everything/
Is AI just another technology, or does it fundamentally change the way we live and think?
Every technology has a direct impact with micro-ethical consequences, some good, some bad. However more profound are the ways in which some technologies reshape the very fabric of society with macro-ethical impacts. The invention of the stirrup revolutionised mounted combat, but as a side effect gave rise to the feudal system, which still shapes politics today. The internal combustion engine offers personal freedom and creates pollution, but has also transformed the nature of urban planning and international trade. When we look at AI the micro-ethical issues, such as bias, are most obvious, but the macro-ethical challenges may be greater.
At a micro-ethical level AI has the potential to deepen social, ethnic and gender bias, issues I have warned about since the early 1990s! It is also being used increasingly on the battlefield. However, it also offers amazing opportunities in health and educations, as the recent Nobel prizes for the developers of AlphaFold illustrate. More radically, the need to encode ethics acts as a mirror to surface essential ethical problems and conflicts.
At the macro-ethical level, by the early 2000s digital technology had already begun to undermine sovereignty (e.g. gambling), market economics (through network effects and emergent monopolies), and the very meaning of money. Modern AI is the child of big data, big computation and ultimately big business, intensifying the inherent tendency of digital technology to concentrate power. AI is already unravelling the fundamentals of the social, political and economic world around us, but this is a world that needs radical reimagining to overcome the global environmental and human challenges that confront us. Our challenge is whether to let the threads fall as they may, or to use them to weave a better future.
Role of Data Annotation Services in AI-Powered Manufacturing



Role of Data Annotation Services in AI-Powered ManufacturingAndrew Leo From predictive maintenance to robotic automation, AI is driving the future of manufacturing. But without high-quality annotated data, even the smartest models fall short.
Discover how data annotation services are powering accuracy, safety, and efficiency in AI-driven manufacturing systems.
Precision in data labeling = Precision on the production floor.
Into The Box Conference Keynote Day 1 (ITB2025)



Into The Box Conference Keynote Day 1 (ITB2025)Ortus Solutions, Corp This is the keynote of the Into the Box conference, highlighting the release of the BoxLang JVM language, its key enhancements, and its vision for the future.
Semantic Cultivators : The Critical Future Role to Enable AI



Semantic Cultivators : The Critical Future Role to Enable AIartmondano By 2026, AI agents will consume 10x more enterprise data than humans, but with none of the contextual understanding that prevents catastrophic misinterpretations.
The Evolution of Meme Coins A New Era for Digital Currency ppt.pdf



The Evolution of Meme Coins A New Era for Digital Currency ppt.pdfAbi john Analyze the growth of meme coins from mere online jokes to potential assets in the digital economy. Explore the community, culture, and utility as they elevate themselves to a new era in cryptocurrency.
What is Model Context Protocol(MCP) - The new technology for communication bw...



What is Model Context Protocol(MCP) - The new technology for communication bw...Vishnu Singh Chundawat The MCP (Model Context Protocol) is a framework designed to manage context and interaction within complex systems. This SlideShare presentation will provide a detailed overview of the MCP Model, its applications, and how it plays a crucial role in improving communication and decision-making in distributed systems. We will explore the key concepts behind the protocol, including the importance of context, data management, and how this model enhances system adaptability and responsiveness. Ideal for software developers, system architects, and IT professionals, this presentation will offer valuable insights into how the MCP Model can streamline workflows, improve efficiency, and create more intuitive systems for a wide range of use cases.
#StandardsGoals for 2025: Standards & certification roundup - Tech Forum 2025



#StandardsGoals for 2025: Standards & certification roundup - Tech Forum 2025BookNet Canada Book industry standards are evolving rapidly. In the first part of this session, we’ll share an overview of key developments from 2024 and the early months of 2025. Then, BookNet’s resident standards expert, Tom Richardson, and CEO, Lauren Stewart, have a forward-looking conversation about what’s next.
Link to recording, transcript, and accompanying resource: https://bnctechforum.ca/sessions/standardsgoals-for-2025-standards-certification-roundup/
Presented by BookNet Canada on May 6, 2025 with support from the Department of Canadian Heritage.
TrustArc Webinar: Consumer Expectations vs Corporate Realities on Data Broker...



TrustArc Webinar: Consumer Expectations vs Corporate Realities on Data Broker...TrustArc Most consumers believe they’re making informed decisions about their personal data—adjusting privacy settings, blocking trackers, and opting out where they can. However, our new research reveals that while awareness is high, taking meaningful action is still lacking. On the corporate side, many organizations report strong policies for managing third-party data and consumer consent yet fall short when it comes to consistency, accountability and transparency.
This session will explore the research findings from TrustArc’s Privacy Pulse Survey, examining consumer attitudes toward personal data collection and practical suggestions for corporate practices around purchasing third-party data.
Attendees will learn:
- Consumer awareness around data brokers and what consumers are doing to limit data collection
- How businesses assess third-party vendors and their consent management operations
- Where business preparedness needs improvement
- What these trends mean for the future of privacy governance and public trust
This discussion is essential for privacy, risk, and compliance professionals who want to ground their strategies in current data and prepare for what’s next in the privacy landscape.
Massive Power Outage Hits Spain, Portugal, and France: Causes, Impact, and On...



Massive Power Outage Hits Spain, Portugal, and France: Causes, Impact, and On...Aqusag Technologies In late April 2025, a significant portion of Europe, particularly Spain, Portugal, and parts of southern France, experienced widespread, rolling power outages that continue to affect millions of residents, businesses, and infrastructure systems.
HCL Nomad Web – Best Practices und Verwaltung von Multiuser-Umgebungen



HCL Nomad Web – Best Practices und Verwaltung von Multiuser-Umgebungenpanagenda Webinar Recording: https://www.panagenda.com/webinars/hcl-nomad-web-best-practices-und-verwaltung-von-multiuser-umgebungen/
HCL Nomad Web wird als die nächste Generation des HCL Notes-Clients gefeiert und bietet zahlreiche Vorteile, wie die Beseitigung des Bedarfs an Paketierung, Verteilung und Installation. Nomad Web-Client-Updates werden “automatisch” im Hintergrund installiert, was den administrativen Aufwand im Vergleich zu traditionellen HCL Notes-Clients erheblich reduziert. Allerdings stellt die Fehlerbehebung in Nomad Web im Vergleich zum Notes-Client einzigartige Herausforderungen dar.
Begleiten Sie Christoph und Marc, während sie demonstrieren, wie der Fehlerbehebungsprozess in HCL Nomad Web vereinfacht werden kann, um eine reibungslose und effiziente Benutzererfahrung zu gewährleisten.
In diesem Webinar werden wir effektive Strategien zur Diagnose und Lösung häufiger Probleme in HCL Nomad Web untersuchen, einschließlich
- Zugriff auf die Konsole
- Auffinden und Interpretieren von Protokolldateien
- Zugriff auf den Datenordner im Cache des Browsers (unter Verwendung von OPFS)
- Verständnis der Unterschiede zwischen Einzel- und Mehrbenutzerszenarien
- Nutzung der Client Clocking-Funktion
AI and Data Privacy in 2025: Global Trends



AI and Data Privacy in 2025: Global TrendsInData Labs In this infographic, we explore how businesses can implement effective governance frameworks to address AI data privacy. Understanding it is crucial for developing effective strategies that ensure compliance, safeguard customer trust, and leverage AI responsibly. Equip yourself with insights that can drive informed decision-making and position your organization for success in the future of data privacy.
This infographic contains:
-AI and data privacy: Key findings
-Statistics on AI data privacy in the today’s world
-Tips on how to overcome data privacy challenges
-Benefits of AI data security investments.
Keep up-to-date on how AI is reshaping privacy standards and what this entails for both individuals and organizations.
What is Model Context Protocol(MCP) - The new technology for communication bw...



What is Model Context Protocol(MCP) - The new technology for communication bw...Vishnu Singh Chundawat
Design and Simulation Triple-DES
- 1. Simulation on Triple Data Encryption standard Adviser Aj. Jarern Vongshumyen By Chatsiri Rattana 47221163 Woranart Hasawayukul 47221858
- 2. Agenda Introduction Theory on Triple DES Design on Triple DES Testing and Result on Triple DES Conclusion
- 3. Introduction
- 4. Background Low security of general data transfer. Use encryption system to secure the data communicates. Then we choose Triple-DES. Apply for design digital circuit by using VHDL(VHSIC Hardware Description Language).
- 5. Objective To learn about Triple-DES(Triple-Data Encryption Standard) algorithm. To learn about VHDL(VHSIC Hardware Description Language) coding. Can design an implementable digital circuit of Triple-DES. Can simulate a circuit that perform result of encryption and decryption.
- 6. Tools for Development Xilinx Inc.Webpack 8.2i. ModelSim
- 7. Theory on Triple DES
- 8. What is DES? DES - Data Encryption Standard Symmetric system - uses the same key to encrypt/decrypt data. Ciphertext Plaintext DES Key Key Encrypt Decrypt
- 9. DES Algorithm Structure The algorithm consists of: An initial permutation of the input data Sixteen rounds of the same process –the DES round A final inverse initial permutation of the data
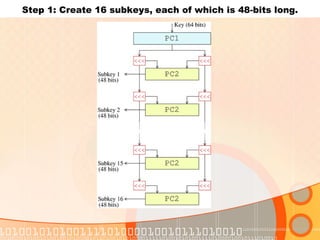
- 10. Step 1: Create 16 subkeys, each of which is 48-bits long.
- 11. Step 2: Encode each 64-bit block of data The Feistel ( F ) function
- 12. Mode of 3DES 3 DES – EDE (2 keys 3DES) Keys = 112 bits C = E k1 ( D k2 (E k1 (M)))
- 13. 3DES-EDE E D E k 1 k 2 k 1 Plaintext Ciphertext D E D k 1 k 2 k 1 Ciphertext Plaintext
- 14. Design on Triple DES
- 15. Schematic On Top Module
- 16. Coding Entity Top module entity test_tdestop is Port ( data_intdes : in std_logic_vector ( 0 to 63 ) ; key1_intdes : in std_logic_vector ( 0 to 63 ) ; key2_intdes : in std_logic_vector ( 0 to 63 ) ; key3_intdes : in std_logic_vector ( 0 to 63 ) ; clock : in std_logic; function_selecttdes : in std_logic; set_out : in std_logic; lddatatdes : in std_logic; ldkeytdes : in std_logic; resettdes : in std_logic; data_outtdes : out std_logic_vector ( 0 to 63 ) ; out_readytdes : out std_logic ) ;
- 18. DESCIPHERTOP 1,2,3 KEYSCHEDULE DES
- 19. KEYSCHEDULE
- 20. DESTOP
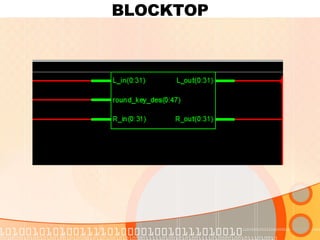
- 21. BLOCKTOP
- 23. ADDKEY
- 24. SBOX
- 25. PBOX
- 26. ADDLEFT
- 27. Device Utilization Summary Logic Utilization Used Available Utilization Slices 1398 4656 30 % Slice FF 1140 9312 12% IOB 305 232 131% GCLKs 1 24 4% MAX CLK 77.548MHz
- 28. Testing and Result on Triple DES
- 29. Test by Test Bench and Wave Form Injection Key 1,2,3 and Data to Triple DES Key1<=“DataBit”,Key2<=“DataBit”,Key3<=“DataBit” Use Text I/O Read and Write Data to Triple DES write write(out_data_out,data_outtdes); writeline(logdata_out,out_data_out); read readline(read_inputtest,read_inputtest_line); read(read_inputtest_line,input_temp); Test Bench not permission injection Output
- 30. Strategy for test Encryption Decryption Text File Text File Data
- 31. Test Triple DES ( Encryption ) Input Output
- 32. Test of Triple DES ( Decryption ) Input Output
- 33. Conclusion
- 34. Conclusion Can design and simulation circuit . Use function for simulation circuit. Can Applied Algorithm Triple DES . Circuit has delay time and cannot control some gate. Can synthesis on FPGA board but it need clock generator and RAM. Large IOB must has floorplanning to save spaces that use.


![[Hello world 오픈 세미나]ffmpeg android](https://cdn.slidesharecdn.com/ss_thumbnails/helloworldffmpegandroid-130214011214-phpapp02-thumbnail.jpg?width=560&fit=bounds)
