Ad
Design Practices for a Secure Azure Solution
- 1. Design Practices for a Secure Azure Solution Michele Leroux Bustamante Cofounder / CIO Solliance Cloud/Security Architect [email protected]
- 2. © Michele Leroux Bustamante. All rights reserved. (a few) Cloud Security Considerations Infrastructure Topology Identity Authorization Data protection Logging/audit Key management Compliance
- 3. © Michele Leroux Bustamante. All rights reserved. Infrastructure
- 4. © Michele Leroux Bustamante. All rights reserved. Infrastructure Requirements DDoS prevention Packet routing assurances Network boundaries
- 5. Customer Environment Application Tier Logic Tier Database Tier Isolated Virtual Network INTERNET Cloud Access & Firewall Layer THREAT DETECTION: DOS/IDS Layer Network Security Group Clients / End Users Microsoft Azure 443 443 VPN Remote Workers Computers Behind Firewalls ExpressRoute Peer Private fiber connections to access compute, storage and more using ExpressRoute Azure Storage • No internet access by default • Intrusion detection and DOS prevention measures • Customer can deploy additional DOS/IDS measures within their virtual networks • Penetration testing Secure development, operations, and threat mitigation practices provide a trusted foundation. Enables connection from customer sites and remote workers to Azure Virtual Networks using Site-to-Site and Point-to-Site VPNs Azure Platform • Logical isolation for customer environments and data • Centralized management via SMAPI or the Azure Portal Network Security Group Network Security Group
- 6. © Michele Leroux Bustamante. All rights reserved. OS Requirements Virtual Machines Disabling unused services on VM I.e., no guest accounts, services run with least privilege Keep machines patched, up to date Azure Security Center can help here
- 7. © Michele Leroux Bustamante. All rights reserved. OS Requirements Virtual Machines Disabling unused services on VM I.e., no guest accounts, services run with least privilege Keep machines patched, up to date Azure Security Center can help here App Services Web Apps, Logic Apps, API Apps Bare bones VMs, stripped for best practices Automatic patching handled for you
- 8. © Michele Leroux Bustamante. All rights reserved. Topology
- 9. © Michele Leroux Bustamante. All rights reserved. Topology Requirements Database should not be accessible from Internet facing applications and services Internal endpoints for back end APIs
- 10. Example Application Topology Backend Web API Browser Java Script Web App Web API Mobile App Mobile App (API) LOGIN API Gateway Partner Web API LOGIN
- 11. Virtual Network Subnet1 Web Servers Subnet2 Back End Servers Subnet3 SQL Server / Cluster HTTP/S 80/443 IaaS / Virtual Networks
- 12. Virtual Network Subnet1 Subnet2 HTTP/S 80/443 App Service Plan App Service Plan SQL Server / Cluster PaaS / IaaS Virtual Networks
- 14. Virtual Network Subnet1 Front End Stateless Web / API Services HTTP/S 80/443 Back End Stateless Compute` Stateful Compute Service Fabric / Frond End / Back End
- 15. © Michele Leroux Bustamante. All rights reserved. Identity
- 16. © Michele Leroux Bustamante. All rights reserved. Password / User Account Policies Initial password issuance Password strength Password reuse Frequency of change Admin password special requirements Hash algorithms / key lengths Inactivity, login failure, account blocking Non-obvious account names Delivery of account/password materials De-provisioning / access revocation No sharing of accounts
- 17. © Michele Leroux Bustamante. All rights reserved. IDaaS / Azure AD – how can it help? Initial password issuance Password strength Password reuse Frequency of change Admin password special requirements Hash algorithms / key lengths Inactivity, login failure, account blocking Non-obvious account names Delivery of account/password materials De-provisioning / access revocation No sharing of accounts ✔ ✔ ✔ ✔ ✔ ✔ ✔ ✔ ✔ ✔ ✔
- 18. © Michele Leroux Bustamante. All rights reserved. Typical Capabilities Browser Based Authentication Mobile Device Authentication Multi-Factor Authentication Login to your corporate directory Single Sign On (to SaaS apps) Social Login
- 20. © Michele Leroux Bustamante. All rights reserved. How else does IDaaS help? DDOS prevention at the provider, not at your app User Management Block suspicious login Prompt for MFA Protocol based protection at the app (OpenID Connect / OAuth2) Centralized user deprovisioning Audit logs, reports Compliance
- 21. © Michele Leroux Bustamante. All rights reserved. Authorization
- 22. © Michele Leroux Bustamante. All rights reserved. Authorization Requirements Access control requirements across apps API security Session lifetime, timeout Data isolation, tenancy
- 23. Application Topology Backend Web API Browser Java Script Web App JS Web API Server Process Mobile App Mobile Web API API Gateway Partner Web API Queues Third Party Apps
- 24. Application Topology - Secured Backend Web API Browser Java Script Web App JS Web API Server Process Mobile App Mobile Web API LOGIN API Gateway Partner Web API LOGIN Queues Authorization ServerThird Party Apps LOGIN
- 25. OIDC / Implicit Passive Redirect Browser 1 27 OIDC Request 4 3 POST Credentials Set Cookie 6 Web Site IDaaS Authenticate Issue Token 5 Login Page
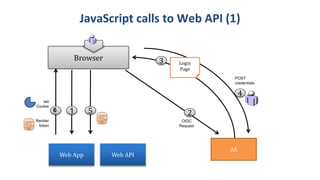
- 26. 2 OIDC Request 4 3 POST credentials AS Login Page Browser 16 set Cookie Render token 5 Web App Web API JavaScript calls to Web API (1)
- 27. JavaScript calls to Web API (2) Browser Web API HTML /JS token is passed in the Authorization header 1 Validate Token / Authorize Access 2 token is embedded in the page
- 28. 2 Delegation Request 3 AS 1 Backend Web API 4 Browser Java Script Web App Web API Calling APIs / Act-As
- 29. © Michele Leroux Bustamante. All rights reserved. Data protection
- 30. © Michele Leroux Bustamante. All rights reserved. Do you ever have to “fix” things in the production db?
- 31. © Michele Leroux Bustamante. All rights reserved. Database Access Requirements Limited to individuals Application / system accounts Few admin / read only All access to data is controlled via applications Never, never, never log in to the database and fix issues directly with content/data At least this is the goal Build tools to solve data problems instead, track repeat offenders
- 32. © Michele Leroux Bustamante. All rights reserved. Data Protection Requirements Encryption in transit, at rest, in use Crypto NIST approved Use code modules with FIPS-140-compliance Vendor List: http://csrc.nist.gov/cryptval/ No sharing of identifiable information Identifiers, PII, PHI
- 33. Data Encryption Azure Portal Azure Data Center Azure Data Center Encrypts most communications HTTPS Azure provides a number of options for encryption and data protection. Customers can use: • HTTPS to storage • HTTPS all endpoints • TLS web client to server
- 34. © Michele Leroux Bustamante. All rights reserved. Ever copy production data for dev/test?
- 35. © Michele Leroux Bustamante. All rights reserved. SQL DB Data Masking
- 36. © Michele Leroux Bustamante. All rights reserved. Key Management
- 37. Blob Storage Keys and SAS Service Public Blob Access create update delete read list Service Private Container read access for limited time with shared access key shared access policy Browser Client Shared Access Signature (SAS) >1 hour requires authentication header in request (no browser)
- 38. © Michele Leroux Bustamante. All rights reserved. Key Vault Store your private keys, shared secrets, other connections, securely FIPS compliant option HSM storage ($$) Examples Private keys, certs, passwords Connection strings Secrets and account names for service bus, storage, search, redis, etc.
- 39. © Michele Leroux Bustamante. All rights reserved. Logging / Audit
- 40. © Michele Leroux Bustamante. All rights reserved. Logging / Audit Requirements Log access to infrastructure, host environment Log all admin access All login, failure, retry, lockout, logout No PII/PHI in logs Retention policy 1 year (typically)
- 41. © Michele Leroux Bustamante. All rights reserved. Do you review your logs actively?
- 42. © Michele Leroux Bustamante. All rights reserved. Azure Security Center Azure Security Center Recommend actions to take to secure your VMs Define policies Export logs for analysis Integration with Operations Management System (OMS)
- 43. © Michele Leroux Bustamante. All rights reserved. COMPLIANCE in general
- 44. © Michele Leroux Bustamante. All rights reserved. Compliance Requirements Infrastructure ISO 27001 SAS 70 Type II, SSAE 16 Audit Third party review / NIST SP 800-53 Third party pen test OWASP or OSSTMM Third party NESSUS scan http://azure.microsoft.com/en-us/support/trust-center/compliance/
- 45. Compliance and Certifications Audit Certified * In Progress Azure’s certification process is ongoing with annual updates and increasing breadth of coverage. Azure manages compliance with: • ISO 27001 • SOC1 / SOC2 • HIPAA BAA • DPA / EU-MC • UK G-Cloud / IL2 • PCI DSS • FedRAMP
- 46. © Michele Leroux Bustamante. All rights reserved. About Michele Michele Leroux Bustamante [email protected] @michelebusta Solliance Cofounder Cloud / Security Architect Microsoft Regional Director since 2003 Microsoft MVP – Microsoft Azure Azure Elite, Azure Insider
Editor's Notes
- #2: Design Practices for a Secure Azure Solution When companies endeavor to move their applications and services to the cloud, they tend to worry more about security up front. Interestingly, platforms such as Azure provide an even more secure environment than most self-managed co-location facilities can hope to offer, not to mention the plethora of features on the platform that help you secure your solutions end to end. In this session Michele will review the mini-avalanche that comprises Azure security across features. Taking the architect's view of the platform (with demos) she’ll cover best practices for securing Azure solutions end to end and discuss the tangential benefits of moving to Azure and how it can help you with checking the boxes on those pesky security surveys.
- #3: Customers worry about cloud security But the truth is, the cloud can also improve the security of your solution in some ways The remaining issues, are probably issues whether you are in the cloud, or not
- #4: When you think about security for a solution, what do you think about? From a high level…list… In this session, I want to take you through the types of questions I frequently encounter helping customers “prove their security” to their customers We will review the topics listed here and within each some of the key questions I see on questionnaires that ask people for proof of trust In the process, I’ll draw from the special sauce Azure provides in terms of features for data protection, key management, identity, networking and generally secure solution design and implementation
- #6: Easy win, if you word it right Do you have DDOS protection measures in place? Do you have appropriate isolation? Assurance of packet routing to correct tenant? Do you have appropriate network boundaries to protect data/assets? (this is on you)
- #7: Azure fabric provides 3 layers of DOS prevention before it reaches your servers You can further secure your VMs with sw firewalls, appliances, IDS (specific client rules not just packet patterns) Add networking tiers, VPN and dedicated express route if you have $ Azure part of hacking challenge; constantly pen testing looking for holes, practicing recovery
- #8: Also related to infrastructure, VM security Do you keep patched? Do you remove guest accounts? Least privilege for services? Access to logs for forensic study? Will show ASC and OMS later Patch a machine with Resource Manager (get RM, update something, redeploy)
- #9: Portal tour
- #10: Also related to infrastructure, VM security Do you keep patched? Do you remove guest accounts? Least privilege for services? Access to logs for forensic study? Will show ASC and OMS later Patch a machine with Resource Manager (get RM, update something, redeploy)
- #13: Good practice topology to check that box There are other ways to be secure calling db, defense in depth, ip restrictions, protected account creds, roles and separation of tables
- #14: For example you may build a multi-tier IaaS deployment Use subnets and network security groups to ensure appropriate restrictions to subnet 2, 3
- #15: Can also achieve this with PaaS using app service environment
- #16: In this case, azure only access to sql otherwise firewall rules Can still shield behind API to public access and call from inside your azure services Service fabric endpionts can’t be reached without http endpoint exposed so the physical tier only needed if you have compliance requirement
- #17: Only the cluster has access Still may need token flow, however
- #21: From a checklist perspective, a lot of requests for proof of recommended practices for password and user account management
- #23: Password writeback Multifactor auth
- #26: Password writeback Multifactor auth
- #28: Seems obvious but these are also important questions that pop up
- #41: FIDO on Windows 10
- #42: Many features for encryption OOB in transit all HTTPS within azure Only bitlocker encrypted vhd uploaded SQL server TDE, SQL masking
- #47: What should you do? At minimum, using dynamic data masking; after copying, for all PII Ideally, do not copy; mask it on the way: maskme.net
- #48: Server=tcp:snapboarddemo.database.windows.net,1433;Database=SnapboardTdeCopy;User ID=snapadmin@snapboarddemo;Password={your_password_here};Encrypt=True;TrustServerCertificate=False;Connection Timeout=30; Sn@pB0rdDemo