DevOps and the Future of Enterprise Security
- 1. SESSION ID: #RSAC Frank Kim DevOps and the Future of Enterprise Security DEV-F03 Founder ThinkSec @fykim www.frankkim.net
- 2. # R S A C Security Perceptions 2 “DevOps is just another excuse for developers to have root access in production.”
- 3. # R S A C Walls of Confusion 3 Developmen t Operations I want stability!I want change! WallofConfusion Image concept: http://dev2ops.org/2010/02/what-is- devops
- 5. # R S A C Security Perceptions 5 “It’s not the strongest that survive or the most intelligent that survive. It’s the ones that are most adaptable to change.” - Charles Darwin
- 6. # R S A C Monolith Architecture Security Controls 6 Common security controls are applied to each trust boundary in the monolith architecture: Client Browser MySQL Database ServerWeb Server Spring Boot / Tomcat Public Subnet Private Subnet ELB 2 3 1. Security Controls Web Application Firewall HTTPS, Rate Limiting 1 2. Security Controls Authentication, Authorization Access control, Validation 3. Security Controls System Authentication, TLS Encryption at rest
- 7. # R S A C Microservice Architecture 7 How does this change in a microservice architecture? Account Management Human Resources Discount Coupons Employee Customer Service Private Subnet MySQL Database Server Coupon Bucket Public Subnet Single Page App EBS Volume Mobile App IoT Factory Device
- 8. # R S A C Microservice Architecture Attack Surface 8 Consider the attack surface in a modern microservice architecture: Account Management Discount Coupons Customer Service Private Subnet MySQL Database Server Public Subnet Single Page App Mobile App IoT Factory Device Employee Human Resources Coupon Bucket EBS Volume
- 9. # R S A C Microservice API Gateway Architecture 9 Adding an API Gateway to provide perimeter security controls: Account Management Discount Coupons Customer Service Private Subnet MySQL Database Server Public Subnet Single Page App Mobile App IoT Factory Device Employee Human Resources Coupon Bucket EBS Volume API Gateway Authorization Access Control
- 10. # R S A C Serverless Computing 10 Serverless refers to new, non-traditional architecture Does not use dedicated containers Event-triggered computing requests Ephemeral environment Servers fully managed by 3rd party (e.g. AWS) Referred to as Functions as a service (FaaS) Example Technologies AWS Lambda, MS Azure Functions, Google Cloud Functions Amazon API Gateway
- 11. # R S A C Serverless Security Benefits 11 How does serverless improve security? • Attack surface is smaller • No servers to patch • No long running servers • That can be scanned or attacked • That can have malware installed on them • Fewer compromised servers • If malware is installed the next request brings up new, clean “server”
- 12. # R S A C Serverless Security Concerns 12 How does serverless make security harder? Attack surface is bigger (but different) Authentication and access control Compliance
- 13. # R S A C Serverless and Application Security 13 Application security is even more important with serverless If attackers have less infrastructure to attack The focus naturally shifts to the application Every function crosses a trust boundary Functions are designed to independent Therefore each function must be secured independently Apply application security best practices Input validation / sanitization must be performed in each function Perform code review and automated scans Review dependencies and libraries used by functions
- 14. # R S A C AWS WAF Security Automations Image credit: http://docs.aws.amazon.com/solutions/latest/aws-waf-security-automations/architecture.html CloudWatch Event AWS Lambda Access Handler S3 Log Bucket Amazon API Gateway AWS WAF SQL Injection & XSS protection Bad bot & scraper protection Scanner & HTTP flood protection Known attacker / bad IP protection IP whitelist / blacklist AWS Lambda Log Parser AWS Lambda IP Lists Parser Amazon CloudFront Application Load Balancer hourly Third-party IP reputation lists access logs requests to honeypot endpoint
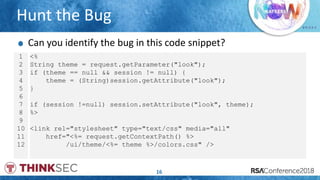
- 16. # R S A C Hunt the Bug 16 1 2 3 4 5 6 7 8 9 10 11 12 <% String theme = request.getParameter("look"); if (theme == null && session != null) { theme = (String)session.getAttribute("look"); } if (session !=null) session.setAttribute("look", theme); %> <link rel="stylesheet" type="text/css" media="all" href="<%= request.getContextPath() %> /ui/theme/<%= theme %>/colors.css" /> Can you identify the bug in this code snippet?
- 17. # R S A C Hunt the Bug – XSS 17 1 2 3 4 5 6 7 8 9 10 11 12 <% String theme = request.getParameter("look"); if (theme == null && session != null) { theme = (String)session.getAttribute("look"); } if (session !=null) session.setAttribute("look", theme); %> <link rel="stylesheet" type="text/css" media="all" href="<%= request.getContextPath() %> /ui/theme/<%= theme %>/colors.css" /> Can you identify the bug in this code snippet?
- 18. # R S A C AngularJS Output Encoding 18 ngBind for HTML tags <div ng-controller="ExampleController"> <label>Enter name: <input type="text" ng-model="name"></label><br> Hello <span ng-bind="name"></span>! </div> <div ng-controller="ExampleController" class="expressions"> Expression:<input type='text' ng-model="expr" size="80"/> <button ng-click="addExp(expr)">Evaluate</button> <ul> <li ng-repeat="expr in exprs track by $index"> [ <a href="" ng-click="removeExp($index)">X</a> ] <code>{{expr}}</code> => <span ng-bind="$parent.$eval(expr)"></span> </li> </ul> </div> Output from AngularJS expressions
- 19. # R S A C Static Analysis Tools 19 Free / open source: Find Security Bugs, Phan, Puma Scan, Brakeman, Bandit, Flawfinder, QARK Commercial: HP Fortify, Checkmarx, Coverity, IBM AppScan Source, Klocwork, Veracode, Brakeman Pro
- 20. # R S A C Secure Code Spell Checker 20
- 21. # R S A C bit.ly/secdevops-toolchain
- 23. # R S A C Critical Security Controls (CSC) 23
- 24. # R S A C Infrastructure as Code 24 Different approaches to set up and manage systems • Traditional: manual checklists and scripts, ad hoc changes/fixes made by system administrators at runtime • Modern: treating Infrastructure as Code and configuration management as system engineering Configuration management with scripts is not scalable Error prone and leads to configuration drift over time Configuration management tools • Chef, Puppet, Ansible, Salt/Saltstack, CFEngine
- 25. # R S A C Automate Standard Configurations 25 InstancePublic: Type: AWS::EC2::Instance Properties: IamInstanceProfile: !Ref InstanceProfilePhotoReadOnly ImageId: !FindInMap [Images, !Ref "AWS::Region", ecs] InstanceType: "t2.micro" KeyName: "secretKey" SecurityGroupIds: - !Ref SecurityGroupPublic SubnetId: !Ref SubnetPublic UserData: Fn::Base64: !Sub | #!/bin/bash -xe yum update -y 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 AWS CloudFormation to create EC2 instance
- 26. # R S A C Conduct Asset Inventory 26 1 2 3 aws ec2 describe-instances --output json | jq '.Reservations[].Instances[] | [.LaunchTime, .InstanceType, .InstanceId, .SecurityGroups[].GroupId, .Tags[].Value]' 1 2 3 4 5 6 7 8 9 [ "2017-01-08T18:51:46.000Z", "t2.micro", "i-0500510e3f808d2ee", "sg-7caf4600" , "prod-springline-aws-web", "Springboot MVC target application“ , "SANSapp.user" ] [ "2017-01-08T18:55:02.000Z", "t2.micro", "i-0e74e490c2ebc5d37", "sg-79af4605" ,"qa-springline-aws-web", "QA Springboot MVC target application“ , "SANSapp.user" ] Command line call to retrieve all EC2 instances Output
- 27. # R S A C Continuous Vulnerability Remediation 27 Blue/Green Deployment Divert traffic from one environment to another Each running a different version of the application Benefits of blue/green deployments Reduced downtime Improved ability to rollback Faster deployment of features and bug fixes Use blue/green deploys when you have: Immutable infrastructure Well defined environment boundary Ability to automate changes
- 28. # R S A C AWS Elastic Container Service (ECS) 28 Blue Green Blue Green ECS Container Instance ECS Container Instance Service Description Task Definition Blue ECS Service Service Description Task Definition Green ECS Service Deployment process Use original blue service and task def Create new green service and task def Map new green service to the Application Load Balancer (ALB) Scale up green service by increasing number of tasks Remove blue service, setting tasks to 0
- 29. # R S A C Create a new “green” ECS Service Increase the desired count for the “green” service Turn off the “blue” service when ready Deploying Application Updates 29 aws ecs update-service --cluster DM-ecs --service $GreenService --desired-count 1 aws ecs update-service --cluster DM-ecs --service $BlueService --desired-count 0 aws cloudformation deploy --template-file green-web-ecs-service.yaml --stack-name green- web-ecs-service
- 30. # R S A C Key Takeaways 30 Understand DevOps Next week: Begin to understand the DevOps CI/CD pipeline and modern architectures used in your organization Support DevOps In three months: Inject security into the CI/CD pipeline in an easy to use way Adopt DevOps In six months: Leverage DevOps principles and practices to improve your security program
- 31. #RSAC Frank Kim @fykim www.frankkim.net Material based on SANS DEV540 Secure DevOps and Cloud Application Security
Editor's Notes
- #8: Note: EBS stands for Elastic Block Store
- #13: Attack surface is bigger (but different) Anyone can deploy a function Cost to deploy a function is effectively zero (not charged for idle time) Difficult to track and delete functions Authentication and access control Who has permission to deploy functions? How do you lock down what each function can do? Compliance Which functions will handle sensitive data and where is it stored? Are there multitenancy risks? Is your implementation itself compliance?
- #22: SANS Secure DevOps Toolchain poster available at: https://www.sans.org/security-resources/posters/appsec/secure-devops-toolchain-swat-checklist-60 Graphic used with permission. Presenter is a creator of the image.

















![# R S A C
AngularJS Output Encoding
18
ngBind for HTML tags
<div ng-controller="ExampleController">
<label>Enter name: <input type="text" ng-model="name"></label><br>
Hello <span ng-bind="name"></span>!
</div>
<div ng-controller="ExampleController" class="expressions">
Expression:<input type='text' ng-model="expr" size="80"/>
<button ng-click="addExp(expr)">Evaluate</button>
<ul>
<li ng-repeat="expr in exprs track by $index">
[ <a href="" ng-click="removeExp($index)">X</a> ]
<code>{{expr}}</code> => <span ng-bind="$parent.$eval(expr)"></span>
</li>
</ul>
</div>
Output from AngularJS expressions](https://image.slidesharecdn.com/devopsandthefutureofenterprisesecurity-180424160016/85/DevOps-and-the-Future-of-Enterprise-Security-18-320.jpg)






![# R S A C
Automate Standard Configurations
25
InstancePublic:
Type: AWS::EC2::Instance
Properties:
IamInstanceProfile: !Ref InstanceProfilePhotoReadOnly
ImageId: !FindInMap [Images, !Ref "AWS::Region", ecs]
InstanceType: "t2.micro"
KeyName: "secretKey"
SecurityGroupIds:
- !Ref SecurityGroupPublic
SubnetId: !Ref SubnetPublic
UserData:
Fn::Base64:
!Sub |
#!/bin/bash -xe
yum update -y
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
AWS CloudFormation to create EC2 instance](https://image.slidesharecdn.com/devopsandthefutureofenterprisesecurity-180424160016/85/DevOps-and-the-Future-of-Enterprise-Security-25-320.jpg)
![# R S A C
Conduct Asset Inventory
26
1
2
3
aws ec2 describe-instances --output json | jq
'.Reservations[].Instances[] | [.LaunchTime, .InstanceType, .InstanceId,
.SecurityGroups[].GroupId, .Tags[].Value]'
1
2
3
4
5
6
7
8
9
[ "2017-01-08T18:51:46.000Z", "t2.micro", "i-0500510e3f808d2ee", "sg-7caf4600"
, "prod-springline-aws-web", "Springboot MVC target application“
, "SANSapp.user"
]
[
"2017-01-08T18:55:02.000Z", "t2.micro", "i-0e74e490c2ebc5d37", "sg-79af4605"
,"qa-springline-aws-web", "QA Springboot MVC target application“
, "SANSapp.user"
]
Command line call to retrieve all EC2 instances
Output](https://image.slidesharecdn.com/devopsandthefutureofenterprisesecurity-180424160016/85/DevOps-and-the-Future-of-Enterprise-Security-26-320.jpg)




