Distributed Shared Memory
Download as PPTX, PDF3 likes985 views
This document discusses distributed shared memory (DSM) systems. It defines DSM as providing a logical abstraction of shared memory across interconnected nodes with distributed physical memories. It describes different types of DSM implementations, advantages of DSM, and various hardware architectures like on-chip memory, bus-based multiprocessors, and switched multiprocessors. It also covers DSM design issues such as granularity of sharing, data structures, consistency models like strict, sequential, and weak consistency, and coherence protocols.
1 of 30
Downloaded 16 times




























Ad
Recommended
Distributed concurrency control



Distributed concurrency controlBinte fatima This document discusses concurrency control algorithms for distributed database systems. It describes distributed two-phase locking (2PL), wound-wait, basic timestamp ordering, and distributed optimistic concurrency control algorithms. For distributed 2PL, transactions lock data items in a growing phase and release locks in a shrinking phase. Wound-wait prevents deadlocks by aborting younger transactions that wait on older ones. Basic timestamp ordering orders transactions based on their timestamps to ensure serializability. The distributed optimistic approach allows transactions to read and write freely until commit, when certification checks for conflicts. Maintaining consistency across distributed copies is important for concurrency control algorithms.
Distributed shared memory shyam soni



Distributed shared memory shyam soniShyam Soni Distributed shared memory (DSM) allows nodes in a cluster to access shared memory across the cluster in addition to each node's private memory. DSM uses a software memory manager on each node to map local memory into a virtual shared memory space. It consists of nodes connected by high-speed communication and each node contains components associated with the DSM system. Algorithms for implementing DSM deal with distributing shared data across nodes to minimize access latency while maintaining data coherence with minimal overhead.
Distributed design alternatives



Distributed design alternativesPooja Dixit The document discusses different distribution design alternatives for tables in a distributed database management system (DDBMS), including non-replicated and non-fragmented, fully replicated, partially replicated, fragmented, and mixed. It describes each alternative and discusses when each would be most suitable. The document also covers data replication, advantages and disadvantages of replication, and different replication techniques. Finally, it discusses fragmentation, the different types of fragmentation, and advantages and disadvantages of fragmentation.
FILE STRUCTURE IN DBMS



FILE STRUCTURE IN DBMSAbhishek Dutta This document discusses physical storage media and file organization. It describes different types of storage media like magnetic disks, flash memory, and tape storage in terms of their speed, capacity, reliability and other characteristics. It also discusses the storage hierarchy from fastest volatile cache/memory to slower non-volatile secondary storage like disks to slowest tertiary storage like tapes. The document further explains techniques like RAID and file organization to optimize storage access and reliability in the presence of disk failures.
Chap 4



Chap 4suks_87 The document discusses distributed shared memory (DSM) in three paragraphs:
1) DSM provides a virtual shared address space across loosely coupled nodes through software memory mapping. Each node caches blocks of shared memory locally to reduce network latency.
2) When a process accesses a non-local memory block, the memory manager handles the request by migrating the block over the network if needed. Cached blocks avoid repeated network transfers.
3) Key design issues include block granularity, consistency models, data location protocols, and handling replication and migration of blocks. Different protocols are used depending on whether blocks are replicated, migrating, or both.
File models and file accessing models



File models and file accessing modelsishmecse13 This document discusses different file models and methods for accessing files. It describes unstructured and structured file models, as well as mutable and immutable files. It also covers remote file access using remote service and data caching models. Finally, it discusses different units of data transfer for file access, including file-level, block-level, byte-level, and record-level transfer models.
11. dfs



11. dfsDr Sandeep Kumar Poonia A Distributed File System(DFS) is simply a classical model of a file system distributed across multiple machines.The purpose is to promote sharing of dispersed files.
Distributed Query Processing



Distributed Query ProcessingMythili Kannan This document discusses distributed database and distributed query processing. It covers topics like distributed database, query processing, distributed query processing methodology including query decomposition, data localization, and global query optimization. Query decomposition involves normalizing, analyzing, eliminating redundancy, and rewriting queries. Data localization applies data distribution to algebraic operations to determine involved fragments. Global query optimization finds the best global schedule to minimize costs and uses techniques like join ordering and semi joins. Local query optimization applies centralized optimization techniques to the best global execution schedule.
Distributed shred memory architecture



Distributed shred memory architectureMaulik Togadiya Distributed shared memory (DSM) is a memory architecture where physically separate memories can be addressed as a single logical address space. In a DSM system, data moves between nodes' main and secondary memories when a process accesses shared data. Each node has a memory mapping manager that maps the shared virtual memory to local physical memory. DSM provides advantages like shielding programmers from message passing, lower cost than multiprocessors, and large virtual address spaces, but disadvantages include potential performance penalties from remote data access and lack of programmer control over messaging.
Data Mining: Association Rules Basics



Data Mining: Association Rules BasicsBenazir Income Support Program (BISP) Association rule mining finds frequent patterns and correlations among items in transaction databases. It involves two main steps:
1) Frequent itemset generation: Finds itemsets that occur together in a minimum number of transactions (above a support threshold). This is done efficiently using the Apriori algorithm.
2) Rule generation: Generates rules from frequent itemsets where the confidence (fraction of transactions with left hand side that also contain right hand side) is above a minimum threshold. Rules are a partitioning of an itemset into left and right sides.
Distributed System ppt



Distributed System pptOECLIB Odisha Electronics Control Library A distibuted system is one in which components located at networked computers communicate and coordinate their actions only by passing messages
Distributed Mutual Exclusion and Distributed Deadlock Detection



Distributed Mutual Exclusion and Distributed Deadlock DetectionSHIKHA GAUTAM This document summarizes key concepts related to distributed mutual exclusion and distributed deadlock detection. It discusses classification of distributed mutual exclusion algorithms into token-based and non-token-based approaches. For distributed mutual exclusion, it describes Lamport's algorithm, Ricart-Agrawala algorithm, Maekawa's quorum-based algorithm, and Suzuki-Kasami's token-based broadcast algorithm. It also discusses requirements for mutual exclusion such as freedom from deadlock and starvation. For distributed deadlock detection, it mentions the system model and types of deadlocks as well as approaches for prevention, avoidance, detection, and resolution of deadlocks.
8. mutual exclusion in Distributed Operating Systems



8. mutual exclusion in Distributed Operating SystemsDr Sandeep Kumar Poonia The document discusses various algorithms for achieving distributed mutual exclusion and process synchronization in distributed systems. It covers centralized, token ring, Ricart-Agrawala, Lamport, and decentralized algorithms. It also discusses election algorithms for selecting a coordinator process, including the Bully algorithm. The key techniques discussed are using logical clocks, message passing, and quorums to achieve mutual exclusion without a single point of failure.
Distributed file system



Distributed file systemAnamika Singh The document discusses key concepts related to distributed file systems including:
1. Files are accessed using location transparency where the physical location is hidden from users. File names do not reveal storage locations and names do not change when locations change.
2. Remote files can be mounted to local directories, making them appear local while maintaining location independence. Caching is used to reduce network traffic by storing recently accessed data locally.
3. Fault tolerance is improved through techniques like stateless server designs, file replication across failure independent machines, and read-only replication for consistency. Scalability is achieved by adding new nodes and using decentralized control through clustering.
Transactions and Concurrency Control



Transactions and Concurrency ControlDilum Bandara Transactions and Concurrency Control in distributed systems. Transaction properties, classification, and transaction implementation. Flat, Nested, and Distributed transactions. Inconsistent Retrievals, Lost Update, Dirty Read, and Premature Writes Problem
6.distributed shared memory



6.distributed shared memoryGd Goenka University A Distributed Shared Memory (DSM) system provides a logical abstraction of shared memory built using interconnected nodes with distributed physical memories. There are hardware, software, and hybrid DSM approaches. DSM offers simple abstraction, improved portability, potential performance gains, large unified memory space, and better performance than message passing in some applications. Consistency protocols ensure shared data coherency across distributed memories according to the memory consistency model.
Parallel Database



Parallel DatabaseVESIT/University of Mumbai The document discusses parallel databases and their architectures. It introduces parallel databases as systems that seek to improve performance through parallelizing operations like loading data, building indexes, and evaluating queries using multiple CPUs and disks. It describes three main architectures for parallel databases: shared memory, shared disk, and shared nothing. The shared nothing architecture provides linear scale-up and speed-up but is more difficult to program. The document also discusses measuring performance improvements from parallelization through speed-up and scale-up.
Concurrency Control in Distributed Database.



Concurrency Control in Distributed Database.Meghaj Mallick The document discusses various techniques for concurrency control in distributed databases, including locking-based protocols and timestamp-based protocols. Locking-based protocols use exclusive and shared locks to control concurrent access to data items. They can be implemented using a single or distributed lock manager. Timestamp-based protocols assign each transaction a unique timestamp to determine serialization order and manage concurrent execution.
Introduction to Distributed System



Introduction to Distributed SystemSunita Sahu The document provides an introduction to distributed systems, defining them as a collection of independent computers that communicate over a network to act as a single coherent system. It discusses the motivation for and characteristics of distributed systems, including concurrency, lack of a global clock, and independence of failures. Architectural categories of distributed systems include tightly coupled and loosely coupled, with examples given of different types of distributed systems such as database management systems, ATM networks, and the internet.
Database fragmentation



Database fragmentationPunjab College Of Technical Education This document discusses database fragmentation in distributed database management systems (DDBMS). Database fragmentation allows a single database object to be broken into multiple segments that can be stored across different sites on a network. This improves efficiency, security, parallelism, availability, reliability and performance. There are three main types of fragmentation: horizontal, vertical, and mixed. Horizontal fragmentation breaks data by attributes like location, vertical by attributes like departments, and mixed uses both. While fragmentation provides advantages, it also increases complexity, cost, and makes security and integrity control more difficult.
Deadlock



DeadlockRajandeep Gill The document discusses deadlocks in computer systems. It defines deadlock, presents examples, and describes four conditions required for deadlock to occur. Several methods for handling deadlocks are discussed, including prevention, avoidance, detection, and recovery. Prevention methods aim to ensure deadlocks never occur, while avoidance allows the system to dynamically prevent unsafe states. Detection identifies when the system is in a deadlocked state.
Process synchronization



Process synchronizationSyed Hassan Ali This document discusses various techniques for process synchronization. It begins by defining process synchronization as coordinating access to shared resources between processes to maintain data consistency. It then discusses critical sections, where shared data is accessed, and solutions like Peterson's algorithm and semaphores to ensure only one process accesses the critical section at a time. Semaphores use wait and signal operations on a shared integer variable to synchronize processes. The document covers binary and counting semaphores and provides an example of their use.
Parallel processing



Parallel processingPraveen Kumar Domain Decomposition, Ecosystem Modeling, Signal Processing, Parallelism in Uniprocessor Systems,Parallelism in Multiprocessor Systems,fynns classification, parallel computing.
Parallel computing persentation



Parallel computing persentationVIKAS SINGH BHADOURIA Parallel computing is computing architecture paradigm ., in which processing required to solve a problem is done in more than one processor parallel way.
The CAP Theorem 



The CAP Theorem Aleksandar Bradic The CAP Theorem : Brewer's Conjecture and the Feasibility of Consistent, Available, Partition-Tolerant Web Services
DeadLock in Operating-Systems



DeadLock in Operating-SystemsVenkata Sreeram Deadlocks-An Unconditional Waiting Situation in Operating System. We must make sure of This concept well before understanding deep in to Operating System. This PPT will understands you to get how the deadlocks Occur and how can we Detect, avoid and Prevent the deadlocks in Operating Systems.
Distributed DBMS - Unit 5 - Semantic Data Control



Distributed DBMS - Unit 5 - Semantic Data ControlGyanmanjari Institute Of Technology Semantic Data Control : View Management, Authentication – database authentication, OS authentication, Access Rights, Semantic Integrity Control – Centralized & Distributed , Cost of enforcing semantic integrity
Query processing in Distributed Database System



Query processing in Distributed Database SystemMeghaj Mallick This is an PPT of DBMS. It include the following topic"Query processing in Distributed Database System".
Lecture 6



Lecture 6Mr SMAK This document discusses parallel computer memory architectures, including shared memory, distributed memory, and hybrid architectures. Shared memory architectures allow all processors to access a global address space, but lack scalability. Distributed memory assigns separate memory to each processor requiring explicit communication between tasks. Hybrid architectures combine shared memory within nodes and distributed memory between nodes for scalability.
Lecture 6



Lecture 6Mr SMAK This document discusses parallel computer memory architectures, including shared memory, distributed memory, and hybrid architectures. Shared memory architectures allow all processors to access a global address space and include uniform memory access (UMA) and non-uniform memory access (NUMA). Distributed memory architectures require a communication network since each processor has its own local memory without a global address space. Hybrid architectures combine shared and distributed memory by networking multiple shared memory multiprocessors.
Ad
More Related Content
What's hot (20)
Distributed shred memory architecture



Distributed shred memory architectureMaulik Togadiya Distributed shared memory (DSM) is a memory architecture where physically separate memories can be addressed as a single logical address space. In a DSM system, data moves between nodes' main and secondary memories when a process accesses shared data. Each node has a memory mapping manager that maps the shared virtual memory to local physical memory. DSM provides advantages like shielding programmers from message passing, lower cost than multiprocessors, and large virtual address spaces, but disadvantages include potential performance penalties from remote data access and lack of programmer control over messaging.
Data Mining: Association Rules Basics



Data Mining: Association Rules BasicsBenazir Income Support Program (BISP) Association rule mining finds frequent patterns and correlations among items in transaction databases. It involves two main steps:
1) Frequent itemset generation: Finds itemsets that occur together in a minimum number of transactions (above a support threshold). This is done efficiently using the Apriori algorithm.
2) Rule generation: Generates rules from frequent itemsets where the confidence (fraction of transactions with left hand side that also contain right hand side) is above a minimum threshold. Rules are a partitioning of an itemset into left and right sides.
Distributed System ppt



Distributed System pptOECLIB Odisha Electronics Control Library A distibuted system is one in which components located at networked computers communicate and coordinate their actions only by passing messages
Distributed Mutual Exclusion and Distributed Deadlock Detection



Distributed Mutual Exclusion and Distributed Deadlock DetectionSHIKHA GAUTAM This document summarizes key concepts related to distributed mutual exclusion and distributed deadlock detection. It discusses classification of distributed mutual exclusion algorithms into token-based and non-token-based approaches. For distributed mutual exclusion, it describes Lamport's algorithm, Ricart-Agrawala algorithm, Maekawa's quorum-based algorithm, and Suzuki-Kasami's token-based broadcast algorithm. It also discusses requirements for mutual exclusion such as freedom from deadlock and starvation. For distributed deadlock detection, it mentions the system model and types of deadlocks as well as approaches for prevention, avoidance, detection, and resolution of deadlocks.
8. mutual exclusion in Distributed Operating Systems



8. mutual exclusion in Distributed Operating SystemsDr Sandeep Kumar Poonia The document discusses various algorithms for achieving distributed mutual exclusion and process synchronization in distributed systems. It covers centralized, token ring, Ricart-Agrawala, Lamport, and decentralized algorithms. It also discusses election algorithms for selecting a coordinator process, including the Bully algorithm. The key techniques discussed are using logical clocks, message passing, and quorums to achieve mutual exclusion without a single point of failure.
Distributed file system



Distributed file systemAnamika Singh The document discusses key concepts related to distributed file systems including:
1. Files are accessed using location transparency where the physical location is hidden from users. File names do not reveal storage locations and names do not change when locations change.
2. Remote files can be mounted to local directories, making them appear local while maintaining location independence. Caching is used to reduce network traffic by storing recently accessed data locally.
3. Fault tolerance is improved through techniques like stateless server designs, file replication across failure independent machines, and read-only replication for consistency. Scalability is achieved by adding new nodes and using decentralized control through clustering.
Transactions and Concurrency Control



Transactions and Concurrency ControlDilum Bandara Transactions and Concurrency Control in distributed systems. Transaction properties, classification, and transaction implementation. Flat, Nested, and Distributed transactions. Inconsistent Retrievals, Lost Update, Dirty Read, and Premature Writes Problem
6.distributed shared memory



6.distributed shared memoryGd Goenka University A Distributed Shared Memory (DSM) system provides a logical abstraction of shared memory built using interconnected nodes with distributed physical memories. There are hardware, software, and hybrid DSM approaches. DSM offers simple abstraction, improved portability, potential performance gains, large unified memory space, and better performance than message passing in some applications. Consistency protocols ensure shared data coherency across distributed memories according to the memory consistency model.
Parallel Database



Parallel DatabaseVESIT/University of Mumbai The document discusses parallel databases and their architectures. It introduces parallel databases as systems that seek to improve performance through parallelizing operations like loading data, building indexes, and evaluating queries using multiple CPUs and disks. It describes three main architectures for parallel databases: shared memory, shared disk, and shared nothing. The shared nothing architecture provides linear scale-up and speed-up but is more difficult to program. The document also discusses measuring performance improvements from parallelization through speed-up and scale-up.
Concurrency Control in Distributed Database.



Concurrency Control in Distributed Database.Meghaj Mallick The document discusses various techniques for concurrency control in distributed databases, including locking-based protocols and timestamp-based protocols. Locking-based protocols use exclusive and shared locks to control concurrent access to data items. They can be implemented using a single or distributed lock manager. Timestamp-based protocols assign each transaction a unique timestamp to determine serialization order and manage concurrent execution.
Introduction to Distributed System



Introduction to Distributed SystemSunita Sahu The document provides an introduction to distributed systems, defining them as a collection of independent computers that communicate over a network to act as a single coherent system. It discusses the motivation for and characteristics of distributed systems, including concurrency, lack of a global clock, and independence of failures. Architectural categories of distributed systems include tightly coupled and loosely coupled, with examples given of different types of distributed systems such as database management systems, ATM networks, and the internet.
Database fragmentation



Database fragmentationPunjab College Of Technical Education This document discusses database fragmentation in distributed database management systems (DDBMS). Database fragmentation allows a single database object to be broken into multiple segments that can be stored across different sites on a network. This improves efficiency, security, parallelism, availability, reliability and performance. There are three main types of fragmentation: horizontal, vertical, and mixed. Horizontal fragmentation breaks data by attributes like location, vertical by attributes like departments, and mixed uses both. While fragmentation provides advantages, it also increases complexity, cost, and makes security and integrity control more difficult.
Deadlock



DeadlockRajandeep Gill The document discusses deadlocks in computer systems. It defines deadlock, presents examples, and describes four conditions required for deadlock to occur. Several methods for handling deadlocks are discussed, including prevention, avoidance, detection, and recovery. Prevention methods aim to ensure deadlocks never occur, while avoidance allows the system to dynamically prevent unsafe states. Detection identifies when the system is in a deadlocked state.
Process synchronization



Process synchronizationSyed Hassan Ali This document discusses various techniques for process synchronization. It begins by defining process synchronization as coordinating access to shared resources between processes to maintain data consistency. It then discusses critical sections, where shared data is accessed, and solutions like Peterson's algorithm and semaphores to ensure only one process accesses the critical section at a time. Semaphores use wait and signal operations on a shared integer variable to synchronize processes. The document covers binary and counting semaphores and provides an example of their use.
Parallel processing



Parallel processingPraveen Kumar Domain Decomposition, Ecosystem Modeling, Signal Processing, Parallelism in Uniprocessor Systems,Parallelism in Multiprocessor Systems,fynns classification, parallel computing.
Parallel computing persentation



Parallel computing persentationVIKAS SINGH BHADOURIA Parallel computing is computing architecture paradigm ., in which processing required to solve a problem is done in more than one processor parallel way.
The CAP Theorem 



The CAP Theorem Aleksandar Bradic The CAP Theorem : Brewer's Conjecture and the Feasibility of Consistent, Available, Partition-Tolerant Web Services
DeadLock in Operating-Systems



DeadLock in Operating-SystemsVenkata Sreeram Deadlocks-An Unconditional Waiting Situation in Operating System. We must make sure of This concept well before understanding deep in to Operating System. This PPT will understands you to get how the deadlocks Occur and how can we Detect, avoid and Prevent the deadlocks in Operating Systems.
Distributed DBMS - Unit 5 - Semantic Data Control



Distributed DBMS - Unit 5 - Semantic Data ControlGyanmanjari Institute Of Technology Semantic Data Control : View Management, Authentication – database authentication, OS authentication, Access Rights, Semantic Integrity Control – Centralized & Distributed , Cost of enforcing semantic integrity
Query processing in Distributed Database System



Query processing in Distributed Database SystemMeghaj Mallick This is an PPT of DBMS. It include the following topic"Query processing in Distributed Database System".
Similar to Distributed Shared Memory (20)
Lecture 6



Lecture 6Mr SMAK This document discusses parallel computer memory architectures, including shared memory, distributed memory, and hybrid architectures. Shared memory architectures allow all processors to access a global address space, but lack scalability. Distributed memory assigns separate memory to each processor requiring explicit communication between tasks. Hybrid architectures combine shared memory within nodes and distributed memory between nodes for scalability.
Lecture 6



Lecture 6Mr SMAK This document discusses parallel computer memory architectures, including shared memory, distributed memory, and hybrid architectures. Shared memory architectures allow all processors to access a global address space and include uniform memory access (UMA) and non-uniform memory access (NUMA). Distributed memory architectures require a communication network since each processor has its own local memory without a global address space. Hybrid architectures combine shared and distributed memory by networking multiple shared memory multiprocessors.
Lecture 6



Lecture 6Mr SMAK This document discusses parallel computer memory architectures, including shared memory, distributed memory, and hybrid architectures. Shared memory architectures allow all processors to access a global address space, but lack scalability. Distributed memory assigns separate memory to each processor requiring explicit communication between tasks. Hybrid architectures combine shared memory within nodes and distributed memory between nodes for scalability.
Pram model



Pram modelMANASYJAYASURYA This document discusses Parallel Random Access Machines (PRAM), a parallel computing model where multiple processors share a single memory space. It describes the PRAM model, including different types like EREW, ERCW, CREW, and CRCW. It also summarizes approaches to parallel programming like shared memory, message passing, and data parallel models. The shared memory model emphasizes control parallelism over data parallelism, while message passing is commonly used in distributed memory systems. Data parallel programming focuses on performing operations on data sets simultaneously across processors.
Symmetric multiprocessing and Microkernel



Symmetric multiprocessing and MicrokernelManoraj Pannerselum Symmetric multiprocessing (SMP) involves connecting two or more identical processors to a single shared main memory. The processors have equal access to I/O devices and are controlled by a single operating system instance. An SMP operating system manages resources so that users see a multiprogramming uniprocessor system. Key design issues for SMP include simultaneous processes, scheduling, synchronization, memory management, and fault tolerance.
A microkernel is a small operating system core that provides modular extensions. Less essential services are built as user mode servers that communicate through the microkernel via messages. This provides advantages like uniform interfaces, extensibility, flexibility, portability, and increased security.
Chapter 10



Chapter 10Er. Nawaraj Bhandari This document discusses parallel processing and cache coherence in computer architecture. It defines parallel processing as using multiple CPUs simultaneously to execute a program faster. It describes different types of parallel processor systems based on the number of instruction and data streams. It then discusses symmetric multiprocessors (SMPs), which have multiple similar processors that share memory and I/O facilities. Finally, it explains the cache coherence problem that can occur when multiple caches contain the same data, and describes the MESI protocol used to maintain coherence between caches.
Parallel processing Concepts



Parallel processing ConceptsArmy Public School and College -Faisal This document discusses parallel processing and parallel organizations. It describes four types of parallel organizations: single instruction single data (SISD), single instruction multiple data (SIMD), multiple instruction single data (MISD), and multiple instruction multiple data (MIMD). MIMD systems are further broken down into shared memory and distributed memory architectures. Cache coherence protocols like MESI are discussed for maintaining consistency across caches in shared memory multiprocessors.
Distributed Shared Memory Systems



Distributed Shared Memory SystemsArush Nagpal Distributed shared memory (DSM) systems implement shared memory in distributed systems without physical shared memory. DSM provides a virtual shared address space across nodes. This overcomes high communication costs. Memory mapping managers map local memory to the shared space. DSM aims to build larger, less expensive parallel machines and simplify programming. It supports shared memory models like page, object, and variable-based. Issues include memory coherence, data location, replacement strategy, and thrashing. Algorithms like central server, migration, read replication, and full replication manage data distribution and consistency.
Parallel Processing (Part 2)



Parallel Processing (Part 2)Ajeng Savitri This document discusses parallel processing and multithreading in computer architecture. It defines threads and processes, and describes different approaches to multithreading including interleaved, blocked, and simultaneous multithreading. It also covers multiprocessor architectures like chip multiprocessing, and compares scalar, superscalar, and VLIW processor approaches to multithreading. Finally, it discusses parallelization techniques, cluster computing, NUMA architectures, and trends in processor design.
message passing vs shared memory



message passing vs shared memoryHamza Zahid This document compares message passing and shared memory architectures for parallel computing. It defines message passing as processors communicating through sending and receiving messages without a global memory, while shared memory allows processors to communicate through a shared virtual address space. The key difference is that message passing uses explicit communication through messages, while shared memory uses implicit communication through memory operations. It also discusses how the programming model and hardware architecture can be separated, with message passing able to support shared memory and vice versa.
Shared memory Parallelism (NOTES)



Shared memory Parallelism (NOTES)Subhajit Sahu My notes on shared memory parallelism.
Shared memory is memory that may be simultaneously accessed by multiple programs with an intent to provide communication among them or avoid redundant copies. Shared memory is an efficient means of passing data between programs. Using memory for communication inside a single program, e.g. among its multiple threads, is also referred to as shared memory [REF].
22CS201 COA



22CS201 COAKathirvel Ayyaswamy This document discusses parallel processors and multicore architecture. It begins with an introduction to parallel processors, including concurrent access to memory and cache coherency. It then discusses multicore architecture, where a single physical processor contains the logic of two or more cores. This allows increasing processing power while keeping clock speeds and power consumption lower than would be needed for a single high-speed core. Cache coherence methods like write-through, write-back, and directory-based approaches are also summarized for maintaining consistency across cores' caches when accessing shared memory.
Non-Uniform Memory Access ( NUMA)



Non-Uniform Memory Access ( NUMA)Nakul Manchanda NUMA (Non-Uniform Memory Access) is a computer memory design that allows for multiprocessor systems where the memory access time depends on the location of the memory relative to the processor. With NUMA, accessing some regions of memory will take longer than others. The document discusses the background of NUMA, how it impacts operating system policies and programming approaches, and provides performance comparisons between UMA (Uniform Memory Access) and NUMA architectures.
Parallel computing



Parallel computingVinay Gupta Parallel computing involves solving computational problems simultaneously using multiple processors. It can save time and money compared to serial computing and allow larger problems to be solved. Parallel programs break problems into discrete parts that can be solved concurrently on different CPUs. Shared memory parallel computers allow all processors to access a global address space, while distributed memory systems require communication between separate processor memories. Hybrid systems combine shared and distributed memory architectures.
Distributed shared memory ch 5



Distributed shared memory ch 5Alagappa Government Arts College, Karaikudi The document discusses distributed shared memory (DSM) which provides a shared memory abstraction for loosely coupled distributed systems. DSM allows processes on different nodes in a distributed system to access shared memory as if it were a single logical memory. It implements this shared memory space through caching blocks of data in local memories and migrating blocks between nodes when needed to service memory requests. Key aspects of DSM systems covered include memory coherence protocols to ensure data consistency and techniques for managing caching and data migration between distributed nodes.
Multiprocessor Scheduling



Multiprocessor SchedulingKhadija Saleem This document discusses scheduling for tightly coupled multiprocessor systems. It describes two types of multiprocessor systems: loosely coupled systems where each processor has its own memory and I/O, and tightly coupled systems where processors share main memory. It also defines levels of granularity in parallel applications from independent to fine-grained parallelism. The key issues in multiprocessor scheduling are process assignment, multiprogramming, and dispatching. Different strategies like load sharing, gang scheduling, and dedicated assignment are used to address these issues.
distributed shared memory



distributed shared memoryAshish Kumar Distributed shared memory (DSM) provides processes with a shared address space across distributed memory systems. DSM exists only virtually through primitives like read and write operations. It gives the illusion of physically shared memory while allowing loosely coupled distributed systems to share memory. DSM refers to applying this shared memory paradigm using distributed memory systems connected by a communication network. Each node has CPUs, memory, and blocks of shared memory can be cached locally but migrated on demand between nodes to maintain consistency.
Distributed Shared Memory Systems



Distributed Shared Memory SystemsAnkit Gupta Distributed shared memory (DSM) systems implement a shared memory model in distributed systems without physical shared memory. DSM provides a virtual shared address space between nodes. It overcomes high communication costs by moving data to the location of access. DSM research aims to build less expensive and larger parallel machines while eliminating programming difficulties of other architectures. DSM models include object, variable, page, and hardware-based approaches. Key issues in developing DSM involve granularity, memory coherence, replacement strategies, and avoiding thrashing. Common DSM algorithms are central server, migration, read replication, and full replication models.
Overview of Distributed Systems



Overview of Distributed Systemsvampugani This document provides an overview of distributed systems. It discusses tightly-coupled and loosely-coupled multiprocessor systems, with loosely-coupled systems referring to distributed systems that have independent processors, memories, and operating systems. The document outlines some key properties of distributed systems, including that they consist of independent nodes that communicate through message passing, and accessing remote resources is more expensive than local resources. It also summarizes some advantages and challenges of distributed systems.
Ad
Recently uploaded (20)
fluke dealers in bangalore..............



fluke dealers in bangalore..............Haresh Vaswani The Fluke 925 is a vane anemometer, a handheld device designed to measure wind speed, air flow (volume), and temperature. It features a separate sensor and display unit, allowing greater flexibility and ease of use in tight or hard-to-reach spaces. The Fluke 925 is particularly suitable for HVAC (heating, ventilation, and air conditioning) maintenance in both residential and commercial buildings, offering a durable and cost-effective solution for routine airflow diagnostics.
Level 1-Safety.pptx Presentation of Electrical Safety



Level 1-Safety.pptx Presentation of Electrical SafetyJoseAlbertoCariasDel Level 1-Safety.pptx Presentation of Electrical Safety
RICS Membership-(The Royal Institution of Chartered Surveyors).pdf



RICS Membership-(The Royal Institution of Chartered Surveyors).pdfMohamedAbdelkader115 Glad to be one of only 14 members inside Kuwait to hold this credential.
Please check the members inside kuwait from this link:
https://www.rics.org/networking/find-a-member.html?firstname=&lastname=&town=&country=Kuwait&member_grade=(AssocRICS)&expert_witness=&accrediation=&page=1
railway wheels, descaling after reheating and before forging



railway wheels, descaling after reheating and before forgingJavad Kadkhodapour railway wheels, descaling after reheating and before forging
"Feed Water Heaters in Thermal Power Plants: Types, Working, and Efficiency G...



"Feed Water Heaters in Thermal Power Plants: Types, Working, and Efficiency G...Infopitaara A feed water heater is a device used in power plants to preheat water before it enters the boiler. It plays a critical role in improving the overall efficiency of the power generation process, especially in thermal power plants.
🔧 Function of a Feed Water Heater:
It uses steam extracted from the turbine to preheat the feed water.
This reduces the fuel required to convert water into steam in the boiler.
It supports Regenerative Rankine Cycle, increasing plant efficiency.
🔍 Types of Feed Water Heaters:
Open Feed Water Heater (Direct Contact)
Steam and water come into direct contact.
Mixing occurs, and heat is transferred directly.
Common in low-pressure stages.
Closed Feed Water Heater (Surface Type)
Steam and water are separated by tubes.
Heat is transferred through tube walls.
Common in high-pressure systems.
⚙️ Advantages:
Improves thermal efficiency.
Reduces fuel consumption.
Lowers thermal stress on boiler components.
Minimizes corrosion by removing dissolved gases.
15th International Conference on Computer Science, Engineering and Applicatio...



15th International Conference on Computer Science, Engineering and Applicatio...IJCSES Journal #computerscience #programming #coding #technology #programmer #python #computer #developer #tech #coder #javascript #java #codinglife #html #code #softwaredeveloper #webdeveloper #software #cybersecurity #linux #computerengineering #webdevelopment #softwareengineer #machinelearning #hacking #engineering #datascience #css #programmers #pythonprogramming
International Journal of Distributed and Parallel systems (IJDPS)



International Journal of Distributed and Parallel systems (IJDPS)samueljackson3773 The growth of Internet and other web technologies requires the development of new
algorithms and architectures for parallel and distributed computing. International journal of
Distributed and parallel systems is a bimonthly open access peer-reviewed journal aims to
publish high quality scientific papers arising from original research and development from
the international community in the areas of parallel and distributed systems. IJDPS serves
as a platform for engineers and researchers to present new ideas and system technology,
with an interactive and friendly, but strongly professional atmosphere.
Lidar for Autonomous Driving, LiDAR Mapping for Driverless Cars.pptx



Lidar for Autonomous Driving, LiDAR Mapping for Driverless Cars.pptxRishavKumar530754 LiDAR-Based System for Autonomous Cars
Autonomous Driving with LiDAR Tech
LiDAR Integration in Self-Driving Cars
Self-Driving Vehicles Using LiDAR
LiDAR Mapping for Driverless Cars
Data Structures_Introduction to algorithms.pptx



Data Structures_Introduction to algorithms.pptxRushaliDeshmukh2 Concept of Problem Solving, Introduction to Algorithms, Characteristics of Algorithms, Introduction to Data Structure, Data Structure Classification (Linear and Non-linear, Static and Dynamic, Persistent and Ephemeral data structures), Time complexity and Space complexity, Asymptotic Notation - The Big-O, Omega and Theta notation, Algorithmic upper bounds, lower bounds, Best, Worst and Average case analysis of an Algorithm, Abstract Data Types (ADT)
Fort night presentation new0903 pdf.pdf.



Fort night presentation new0903 pdf.pdf.anuragmk56 This is the document of fortnight review progress meeting
Data Structures_Searching and Sorting.pptx



Data Structures_Searching and Sorting.pptxRushaliDeshmukh2 Sorting Order and Stability in Sorting.
Concept of Internal and External Sorting.
Bubble Sort,
Insertion Sort,
Selection Sort,
Quick Sort and
Merge Sort,
Radix Sort, and
Shell Sort,
External Sorting, Time complexity analysis of Sorting Algorithms.
Avnet Silica's PCIM 2025 Highlights Flyer



Avnet Silica's PCIM 2025 Highlights FlyerWillDavies22 See what you can expect to find on Avnet Silica's stand at PCIM 2025.
DATA-DRIVEN SHOULDER INVERSE KINEMATICS YoungBeom Kim1 , Byung-Ha Park1 , Kwa...



DATA-DRIVEN SHOULDER INVERSE KINEMATICS YoungBeom Kim1 , Byung-Ha Park1 , Kwa...charlesdick1345 This paper proposes a shoulder inverse kinematics (IK) technique. Shoulder complex is comprised of the sternum, clavicle, ribs, scapula, humerus, and four joints.
Degree_of_Automation.pdf for Instrumentation and industrial specialist



Degree_of_Automation.pdf for Instrumentation and industrial specialistshreyabhosale19 degree of Automation for industrial and Instrumentation learners.
π0.5: a Vision-Language-Action Model with Open-World Generalization



π0.5: a Vision-Language-Action Model with Open-World GeneralizationNABLAS株式会社 今回の資料「Transfusion / π0 / π0.5」は、画像・言語・アクションを統合するロボット基盤モデルについて紹介しています。
拡散×自己回帰を融合したTransformerをベースに、π0.5ではオープンワールドでの推論・計画も可能に。
This presentation introduces robot foundation models that integrate vision, language, and action.
Built on a Transformer combining diffusion and autoregression, π0.5 enables reasoning and planning in open-world settings.
Value Stream Mapping Worskshops for Intelligent Continuous Security



Value Stream Mapping Worskshops for Intelligent Continuous SecurityMarc Hornbeek This presentation provides detailed guidance and tools for conducting Current State and Future State Value Stream Mapping workshops for Intelligent Continuous Security.
"Boiler Feed Pump (BFP): Working, Applications, Advantages, and Limitations E...



"Boiler Feed Pump (BFP): Working, Applications, Advantages, and Limitations E...Infopitaara A Boiler Feed Pump (BFP) is a critical component in thermal power plants. It supplies high-pressure water (feedwater) to the boiler, ensuring continuous steam generation.
⚙️ How a Boiler Feed Pump Works
Water Collection:
Feedwater is collected from the deaerator or feedwater tank.
Pressurization:
The pump increases water pressure using multiple impellers/stages in centrifugal types.
Discharge to Boiler:
Pressurized water is then supplied to the boiler drum or economizer section, depending on design.
🌀 Types of Boiler Feed Pumps
Centrifugal Pumps (most common):
Multistage for higher pressure.
Used in large thermal power stations.
Positive Displacement Pumps (less common):
For smaller or specific applications.
Precise flow control but less efficient for large volumes.
🛠️ Key Operations and Controls
Recirculation Line: Protects the pump from overheating at low flow.
Throttle Valve: Regulates flow based on boiler demand.
Control System: Often automated via DCS/PLC for variable load conditions.
Sealing & Cooling Systems: Prevent leakage and maintain pump health.
⚠️ Common BFP Issues
Cavitation due to low NPSH (Net Positive Suction Head).
Seal or bearing failure.
Overheating from improper flow or recirculation.
Ad
Distributed Shared Memory
- 2. Basic Concepts Of DSM: A DSM system provides a logical abstraction of shared memory which is built using a set of interconnected nodes having physically distributed memories.
- 3. Types of DSMs Hardware level DSM Software level DSM Hybrid level DSM
- 4. Advantages of DSM Simple abstraction Improved portability of distributed application programs Provides better performance in some applications Large memory space at no extra cost Better than message passing systems
- 5. Hardware architectures On chip memory Bus based multiprocessor Ring based multiprocessor Switched multiprocessor
- 6. On chip memory In this CPU portion of the chip has a address and data lines that directly connect to the memory portion. Such chips are used in cars appliances and even toys
- 7. Bus based multiprocessor All CPUs connected to one bus (backplane) Memory and peripherals are accessed via shared bus. System looks the same from any processor.
- 8. Ring DSM architecture Shred memory : Private areas Shared areas
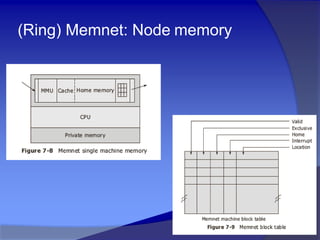
- 9. (Ring) Memnet: Node memory
- 10. Switched multiprocessor: Multiple clusters interconnected by a bus offer better scalability Example : Dash system
- 11. NUMA Multiprocessor Non-uniform memory access (NUMA) is a computer memory design used multiprocessing, where the memory access time depends on the memory location relative to the processor. Under NUMA, a processor can access its own local memory faster than non-local memory. The benefits of NUMA are limited to particular workloads, notably on servers where the data is often associated strongly with certain tasks or users.
- 12. UMA Multiprocessor Uniform memory access (UMA) is a shared memory architecture used in parallel computers. All theprocessors in the UMA model share the physical memoryuniformly. In a UMA architecture, access time to a memory location is independent of which processor makes the request or which memory chip contains the transferred data. Uniform memory access computer architectures are often contrasted with non-uniform memory access (NUMA) architectures. In the UMA architecture, each processor may use a private cache. Peripherals are also shared in some fashion. The UMA model is suitable for general purpose and time sharing applications by multiple users. It can be used to speed up the execution of a single large program in time- critical applications.
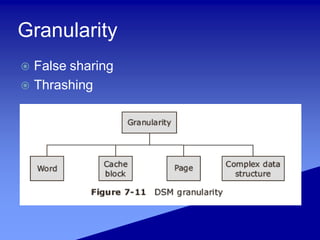
- 14. DSM design issues Granularity of sharing Structure of data Consistency models Coherence protocols
- 15. Granularity False sharing Thrashing
- 16. Thrashing: False sharing Techniques to reduce thrashing: Application controlled lock Pin the block to a node for specific time Customize algorithm to shared data usage pattern
- 17. DSM structure Organization of data items in the shared memory
- 18. Consistency models Refers to how recent the shared memory updates are visible to all the other processes running on different machines
- 19. Strict consistency Strongest form of consistency. All write operations are visible to all processes.
- 20. Sequential consistency All processors in the system observe the same ordering of reads and writes which are issued in sequence by the individual processors
- 21. Causal consistency Weakening of sequential consistency for better concurrency Causally related operation is the one which has influenced the other operation
- 22. PRAM consistency Pipelined Random Access Memory consistency Write operations performed by different processes may be seen by different processes in different orders All write operations of a single process are pipelined Simple, easy to implement and has good performance.
- 23. Processor consistency Adheres to the PRAM consistency Constraint on memory coherence Order in which the memory operations are seen by two processors need not be identical, but the order of writes issued by each processor must be preserved
- 24. Weak consistency Use a special variable called the synchronization variable. Very difficult to show and keep track of the changes at time to time.
- 25. Properties of the weak consistency model: Access to synchronization variables is sequentially consistent. Only when all previous writes are completed everywhere, access to synchronizations variable is allowed. Until all previous accesses to synchronization variables are performed, no read write data access operations will be allowed.
- 26. Entry consistency • Use acquire and release at the start and end of each critical section, respectively. • Each ordinary shared variable is associated with some synchronization variable such as a lock or barrier. • Entry consistency (EC) is similar to LRC but more relaxed; shared data is explicitly associated with synchronization primitives and is made consistent when such an operation is performed
- 27. Scope consistency A scope is a limited view of memory with respect to which memory references are performed
- 28. Coherence protocols Specifies how the rules set by the memory consistency model are to be implemented
- 29. Coherence algorithms Maintain consistency among replicas
- 30. Thank you <./.>



