Docker Security Paradigm
1 like547 views
This document discusses security mechanisms in Docker containers, including control groups (cgroups) to limit resources, namespaces to isolate processes, and capabilities to restrict privileges. It covers secure computing modes like seccomp that sandbox system calls. Linux security modules like AppArmor and SELinux are also mentioned, along with best practices for the Docker daemon and container security overall.
1 of 19
Downloaded 58 times










![User Namespaces
Docker introduced support for user
namespace in version 1.10
run as user :
--user UID:GID
Need root inside container :
--userns-remap [uid[:gid]]
Docker daemon needs to be started with : --userns-
remap=username/uid:groupname/gid”. Using “default” will create “dockremap” user
(--userns-remap=defaults)](https://image.slidesharecdn.com/dockersecurity-170315112536/85/Docker-Security-Paradigm-12-320.jpg)







Ad
Recommended
Docker Security in Production Overview



Docker Security in Production OverviewDelve Labs Delve Labs was present during the GoSec 2016 conference, where our lead DevOps engineer presented an overview of the current options available for securing Docker in production environments.
https://www.delve-labs.com
Docker security introduction-task-2016



Docker security introduction-task-2016Ricardo Gerardi This document discusses Docker security. It begins by introducing Docker and containers, then covers securing Docker images through signing and scanning. It discusses how Docker uses namespaces and cgroups for isolation. It also addresses securing the Docker daemon and containers, as well as operational concerns around deployment, networking, monitoring, and logging of containers. It concludes by looking at future directions like unikernels and serverless architectures.
Docker Security Overview



Docker Security OverviewSreenivas Makam This document summarizes Docker security features as of release 1.12. It discusses key security modules like namespaces, cgroups, capabilities, seccomp, AppArmor/SELinux that provide access control and isolation in Docker containers. It also covers multi-tenant security, image signing, TLS for daemon access, and best practices like using official images and regular updates.
Rooting Out Root: User namespaces in Docker



Rooting Out Root: User namespaces in DockerPhil Estes This talk on the progress to bring user namespace support into Docker was presented by Phil Estes at LinuxCon/ContainerCon 2015 on Wednesday, Aug. 19th, 2015
Docker 1.11 Presentation



Docker 1.11 PresentationSreenivas Makam Overview of Docker 1.11 features(Covers Docker release summary till 1.11, runc/containerd, dns load balancing ipv6 service discovery, labels, macvlan/ipvlan)
Under the Hood with Docker Swarm Mode - Drew Erny and Nishant Totla, Docker



Under the Hood with Docker Swarm Mode - Drew Erny and Nishant Totla, DockerDocker, Inc. Join SwarmKit maintainers Drew and Nishant as they showcase features that have made Swarm Mode even more powerful, without compromising the operational simplicity it was designed with. They will discuss the implementation of new features that streamline deployments, increase security, and reduce downtime. These substantial additions to Swarm Mode are completely transparent and straightforward to use, and users may not realize they're already benefiting from these improvements under the hood.
Veer's Container Security



Veer's Container SecurityJim Barlow Container security involves securing containers at both the host and application level. At the host level, Linux technologies like namespaces, cgroups, SELinux, and seccomp provide isolation between containers. Container images are also scanned for vulnerabilities. The OpenShift platform provides additional security features like role-based access control, network policies, encrypted communications, and controls over privileged containers and storage. Application security best practices within containers include using HTTPS, securing secrets, and API management tools.
Tokyo OpenStack Summit 2015: Unraveling Docker Security



Tokyo OpenStack Summit 2015: Unraveling Docker SecurityPhil Estes A Docker security talk that Salman Baset and Phil Estes presented at the Tokyo OpenStack Summit on October 29th, 2015. In this talk we provided an overview of the security constraints available to Docker cloud operators and users and then walked through a "lessons learned" from experiences operating IBM's public Bluemix container cloud based on Docker container technology.
Plug-ins: Building, Shipping, Storing, and Running - Nandhini Santhanam and T...



Plug-ins: Building, Shipping, Storing, and Running - Nandhini Santhanam and T...Docker, Inc. At Docker, we are striving to enable the extensibility of Docker via "Plugins" and make them available for developers and enterprises alike. Come attend this talk to understand what it takes to build, ship, store and run plugins. We will deep dive into plugin lifecycle management on a single engine and across a swarm cluster. We will also demonstrate how you can integrate plugins from other enterprises or developers into your ecosystem. There will be fun demos accompanying this talk! This will be session will be beneficial to you if you: 1) Are an ops team member trying to integrate Docker with your favorite storage or network vendor 2) Are Interested in extending or customizing Docker; or 3) Want to become a Docker partner, and want to make the technology integration seamless.
Introduction to docker security



Introduction to docker securityWalid Ashraf This document provides an overview of Docker security. It discusses how Docker isolates containers using kernel namespaces and cgroups to limit access to resources. It describes how Docker secures communication with its daemon and stores images cryptographically. It also explains how Linux capabilities and features like AppArmor and Seccomp can restrict container access further.
CoreOS Overview and Current Status



CoreOS Overview and Current StatusSreenivas Makam Covers overview of CoreOS and current status of CoreOS projects. Presented at Open source meetup, Bangalore(http://www.meetup.com/Bangalore-Open-Source-Meetup/events/229763724/)
Docker: Aspects of Container Isolation



Docker: Aspects of Container Isolationallingeek Presentation on the Linux namespaces and system calls used to provide container isolation with Docker. Presented in March 2015 at http://www.meetup.com/Docker-Phoenix/ in Tempe, Arizona.
Enhancing OpenShift Security for Business Critical Deployments



Enhancing OpenShift Security for Business Critical DeploymentsDevOps.com Join us for this informative session on "Enhancing OpenShift Security." Andrew Toth from Red Hat will outline typical threats and security measures to protect container deployments and will share information on built-in security features of OpenShift and Kubernetes.
Glen Kosaka from NeuVector will present how to enhance security for Kubernetes and OpenShift by using advanced run-time security features to improve visibility and protection in production.
dockerizing web application



dockerizing web applicationWalid Ashraf The document discusses how to create Dockerfiles to containerize web applications. It provides instructions for creating Dockerfiles for both Node.js and Python web applications. For Node.js, it shows how to create a Dockerfile that copies local code and dependencies into an image based on an Alpine Node image and exposes port 8080. For Python, it demonstrates a Dockerfile that copies code and dependencies into an Alpine image, installs Python and pip, exposes port 5000, and runs a Flask app.
Devops in Networking



Devops in NetworkingSreenivas Makam This document discusses DevOps in networking and provides examples of using Python libraries and Ansible to programmatically configure and monitor network devices. It describes motivations for DevOps in networking like SDN technologies, availability of network automation tools, and cloud networking. Use cases presented include configuration of L2/L3 protocols and services and network monitoring. The document also discusses network APIs, models like YANG, and tools like Ansible, Python, and protocol standards. An example demonstrates using the PyEAPI Python library to read and create VLANs on an Arista switch and using Ansible to get LLDP neighbors from a Cisco device.
How Secure Is Your Container? ContainerCon Berlin 2016



How Secure Is Your Container? ContainerCon Berlin 2016Phil Estes A conference talk at ContainerCon Europe in Berlin, Germany, given on October 5th, 2016. This is a slightly modified version of my talk first used at Docker London in July 2016.
Deep Dive into Docker Swarm Mode



Deep Dive into Docker Swarm ModeAjeet Singh Raina Since its first 1.12 release on July 2016, Docker Swarm Mode has matured enough as a clustering and scheduling tool for IT administrators and developers who can easily establish and manage a cluster of Docker nodes as a single virtual system. Swarm mode integrates the orchestration capabilities of Docker Swarm into Docker Engine itself and help administrators and developers with the ability to add or subtract container iterations as computing demands change. With sophisticated but easy to implement features like built-in Service Discovery, Routing Mesh, Secrets, declarative service model, scaling of the services, desired state reconciliation, scheduling, filters, multi-host networking model, Load-Balancing, rolling updates etc. Docker 17.06 is all set for production-ready product today. Join me webinar organised by Docker Izmir, to get familiar with the current Swarm Mode capabilities & functionalities across the heterogeneous environments.
Container security



Container securityAnthony Chow The document discusses container security, providing advantages and disadvantages of containers as well as threats. It outlines different approaches to container security including host-based methods using namespaces, control groups, and capabilities as well as container-based scanning and digital signatures. Third-party security tools are also mentioned. The document concludes with examples of using containers for microservices and network policies for protection.
Docker on openstack by OpenSource Consulting



Docker on openstack by OpenSource ConsultingOpen Source Consulting It's presentation for technet 2015 in korea.
I changed the format to pptx,
목차는 아래와 같습니다.
Openstack 인프라 구축 (4 node 구성) [ 30분]
Openstack 위에 VM 생성 [ 20분 ]
docker 구축 기초 [ 30분]
오픈스택에 docker를 연결 [ 30분]
Docker로 WEB서비스 구축 [ 15분]
Openstack 위에 Docker로 WEB서비스 구축 [ 15분]
Docker로 jenkins 구현 [30분]
Docker Security and Content Trust



Docker Security and Content Trustehazlett Docker provides security features to secure content, access, and platforms. It delivers integrated security through content trust, authorization and authentication, and runtime containment using cGroups, namespaces, capabilities, seccomp profiles, and Linux security modules.
Docker security: Rolling out Trust in your container



Docker security: Rolling out Trust in your containerRonak Kogta This document discusses various security aspects of Docker containers. It covers topics like Docker isolation, limiting privileges through capabilities and namespaces, filesystem security using SELinux/AppArmor, image signing with Docker Content Trust and Notary to ensure integrity, and tools like DockerBench for security best practices. The document emphasizes that with Docker, every process should only access necessary resources and taking a least privilege approach is important for security.
Oscon London 2016 - Docker from Development to Production



Oscon London 2016 - Docker from Development to ProductionPatrick Chanezon Docker revolutionized how developers and operations teams build, ship, and run applications, enabling them to leverage the latest advancements in software development: the microservice architecture style, the immutable infrastructure deployment style, and the DevOps cultural model.
Existing software layers are not a great fit to leverage these trends. Infrastructure as a service is too low level; platform as a service is too high level; but containers as a service (CaaS) is just right. Container images are just the right level of abstraction for DevOps, allowing developers to specify all their dependencies at build time, building and testing an artifact that, when ready to ship, is the exact thing that will run in production. CaaS gives ops teams the tools to control how to run these workloads securely and efficiently, providing portability between different cloud providers and on-premises deployments.
Patrick Chanezon offers a detailed overview of the latest evolutions to the Docker ecosystem enabling CaaS: standards (OCI, CNCF), infrastructure (runC, containerd, Notary), platform (Docker, Swarm), and services (Docker Cloud, Docker Datacenter). Patrick ends with a demo showing how to do in-container development of a Spring Boot application on a Mac running a preconfigured IDE in a container, provision a highly available Swarm cluster using Docker Datacenter on a cloud provider, and leverage the latest Docker tools to build, ship, and run a polyglot application architected as a set of microservices—including how to set up load balancing.
Docker Runtime Security



Docker Runtime SecuritySysdig While there have been many improvements around securing containers, there is still a large gap in monitoring the behaviour of containers in production. Sysdig Falco is an open source behavioural activity monitor for containerized environments.
Sysdig Falco can detect and alert on anomalous behaviour at the application, file, system, and network level. In this session get a deep dive into Falco: How does behavioural security differ from existing security solutions like image scanning, seccomp, SELinux or AppArmor? What can Sysdig Falco detect? Building and customizing rules for your Docker and Kubernetes apps. Forensics analysis with Sysdig Inspect even when the container doesn't exist anymore!
Read more on:
https://sysdig.com/blog/docker-runtime-security/
https://sysdig.com/blog/runtime-security-kubernetes-sysdig-falco/
KVM and docker LXC Benchmarking with OpenStack



KVM and docker LXC Benchmarking with OpenStackBoden Russell Passive benchmarking with docker LXC and KVM using OpenStack hosted in SoftLayer. These results provide initial incite as to why LXC as a technology choice offers benefits over traditional VMs and seek to provide answers as to the typical initial LXC question -- "why would I consider Linux Containers over VMs" from a performance perspective.
Results here provide insight as to:
- Cloudy ops times (start, stop, reboot) using OpenStack.
- Guest micro benchmark performance (I/O, network, memory, CPU).
- Guest micro benchmark performance of MySQL; OLTP read, read / write complex and indexed insertion.
- Compute node resource consumption; VM / Container density factors.
- Lessons learned during benchmarking.
The tests here were performed using OpenStack Rally to drive the OpenStack cloudy tests and various other linux tools to test the guest performance on a "micro level". The nova docker virt driver was used in the Cloud scenario to realize VMs as docker LXC containers and compared to the nova virt driver for libvirt KVM.
Please read the disclaimers in the presentation as this is only intended to be the "chip of the ice burg".
Containers: The What, Why, and How



Containers: The What, Why, and HowSneha Inguva In this presentation, I will be presenting the what, why, and how of containers at the Digital Ocean in Hyderabad.
Exploring Docker Security



Exploring Docker SecurityPatrick Kleindienst These are the slides from a talk I gave for our Secure Systems course in the degree program Computer Science and Media at Stuttgart Media University.
Running High Performance and Fault Tolerant Elasticsearch Clusters on Docker



Running High Performance and Fault Tolerant Elasticsearch Clusters on DockerSematext Group, Inc. Sematext engineer Rafal Kuc (@kucrafal) walks through the details of running high-performance, fault tolerant Elasticsearch clusters on Docker. Topics include: Containers vs. Virtual Machines, running the official Elasticsearch container, container constraints, good network practices, dealing with storage, data-only Docker volumes, scaling, time-based data, multiple tiers and tenants, indexing with and without routing, querying with and without routing, routing vs. no routing, and monitoring. Talk was delivered at DevOps Days Warsaw 2015.
Docker toolbox



Docker toolboxYonghwee Kim The Docker Toolbox installs several components to allow users to run Docker on their Mac systems without running a Linux VM directly. It includes the Docker client, Docker Machine, Docker Compose, Docker Kitematic, and Oracle VirtualBox. Docker Machine is used to create and connect to a lightweight Linux VM hosted by VirtualBox where the Docker daemon runs. This allows users to work with Docker images and containers without having to manage a separate Linux environment.
How to Become a Thought Leader in Your Niche



How to Become a Thought Leader in Your NicheLeslie Samuel Are bloggers thought leaders? Here are some tips on how you can become one. Provide great value, put awesome content out there on a regular basis, and help others.
LXC, Docker, security: is it safe to run applications in Linux Containers?



LXC, Docker, security: is it safe to run applications in Linux Containers?Jérôme Petazzoni The document discusses the security of running applications in Linux containers. It begins by acknowledging that containers were not originally designed with security in mind. However, it then outlines several techniques that can be used to improve security, such as running containers without root privileges, dropping capabilities, enabling security modules like SELinux, and limiting access to devices and system calls. For the most security-sensitive tasks, it recommends running containers inside virtual machines to isolate them further. In the end, it argues that with the right precautions, containers can be used securely for many applications.
Ad
More Related Content
What's hot (20)
Plug-ins: Building, Shipping, Storing, and Running - Nandhini Santhanam and T...



Plug-ins: Building, Shipping, Storing, and Running - Nandhini Santhanam and T...Docker, Inc. At Docker, we are striving to enable the extensibility of Docker via "Plugins" and make them available for developers and enterprises alike. Come attend this talk to understand what it takes to build, ship, store and run plugins. We will deep dive into plugin lifecycle management on a single engine and across a swarm cluster. We will also demonstrate how you can integrate plugins from other enterprises or developers into your ecosystem. There will be fun demos accompanying this talk! This will be session will be beneficial to you if you: 1) Are an ops team member trying to integrate Docker with your favorite storage or network vendor 2) Are Interested in extending or customizing Docker; or 3) Want to become a Docker partner, and want to make the technology integration seamless.
Introduction to docker security



Introduction to docker securityWalid Ashraf This document provides an overview of Docker security. It discusses how Docker isolates containers using kernel namespaces and cgroups to limit access to resources. It describes how Docker secures communication with its daemon and stores images cryptographically. It also explains how Linux capabilities and features like AppArmor and Seccomp can restrict container access further.
CoreOS Overview and Current Status



CoreOS Overview and Current StatusSreenivas Makam Covers overview of CoreOS and current status of CoreOS projects. Presented at Open source meetup, Bangalore(http://www.meetup.com/Bangalore-Open-Source-Meetup/events/229763724/)
Docker: Aspects of Container Isolation



Docker: Aspects of Container Isolationallingeek Presentation on the Linux namespaces and system calls used to provide container isolation with Docker. Presented in March 2015 at http://www.meetup.com/Docker-Phoenix/ in Tempe, Arizona.
Enhancing OpenShift Security for Business Critical Deployments



Enhancing OpenShift Security for Business Critical DeploymentsDevOps.com Join us for this informative session on "Enhancing OpenShift Security." Andrew Toth from Red Hat will outline typical threats and security measures to protect container deployments and will share information on built-in security features of OpenShift and Kubernetes.
Glen Kosaka from NeuVector will present how to enhance security for Kubernetes and OpenShift by using advanced run-time security features to improve visibility and protection in production.
dockerizing web application



dockerizing web applicationWalid Ashraf The document discusses how to create Dockerfiles to containerize web applications. It provides instructions for creating Dockerfiles for both Node.js and Python web applications. For Node.js, it shows how to create a Dockerfile that copies local code and dependencies into an image based on an Alpine Node image and exposes port 8080. For Python, it demonstrates a Dockerfile that copies code and dependencies into an Alpine image, installs Python and pip, exposes port 5000, and runs a Flask app.
Devops in Networking



Devops in NetworkingSreenivas Makam This document discusses DevOps in networking and provides examples of using Python libraries and Ansible to programmatically configure and monitor network devices. It describes motivations for DevOps in networking like SDN technologies, availability of network automation tools, and cloud networking. Use cases presented include configuration of L2/L3 protocols and services and network monitoring. The document also discusses network APIs, models like YANG, and tools like Ansible, Python, and protocol standards. An example demonstrates using the PyEAPI Python library to read and create VLANs on an Arista switch and using Ansible to get LLDP neighbors from a Cisco device.
How Secure Is Your Container? ContainerCon Berlin 2016



How Secure Is Your Container? ContainerCon Berlin 2016Phil Estes A conference talk at ContainerCon Europe in Berlin, Germany, given on October 5th, 2016. This is a slightly modified version of my talk first used at Docker London in July 2016.
Deep Dive into Docker Swarm Mode



Deep Dive into Docker Swarm ModeAjeet Singh Raina Since its first 1.12 release on July 2016, Docker Swarm Mode has matured enough as a clustering and scheduling tool for IT administrators and developers who can easily establish and manage a cluster of Docker nodes as a single virtual system. Swarm mode integrates the orchestration capabilities of Docker Swarm into Docker Engine itself and help administrators and developers with the ability to add or subtract container iterations as computing demands change. With sophisticated but easy to implement features like built-in Service Discovery, Routing Mesh, Secrets, declarative service model, scaling of the services, desired state reconciliation, scheduling, filters, multi-host networking model, Load-Balancing, rolling updates etc. Docker 17.06 is all set for production-ready product today. Join me webinar organised by Docker Izmir, to get familiar with the current Swarm Mode capabilities & functionalities across the heterogeneous environments.
Container security



Container securityAnthony Chow The document discusses container security, providing advantages and disadvantages of containers as well as threats. It outlines different approaches to container security including host-based methods using namespaces, control groups, and capabilities as well as container-based scanning and digital signatures. Third-party security tools are also mentioned. The document concludes with examples of using containers for microservices and network policies for protection.
Docker on openstack by OpenSource Consulting



Docker on openstack by OpenSource ConsultingOpen Source Consulting It's presentation for technet 2015 in korea.
I changed the format to pptx,
목차는 아래와 같습니다.
Openstack 인프라 구축 (4 node 구성) [ 30분]
Openstack 위에 VM 생성 [ 20분 ]
docker 구축 기초 [ 30분]
오픈스택에 docker를 연결 [ 30분]
Docker로 WEB서비스 구축 [ 15분]
Openstack 위에 Docker로 WEB서비스 구축 [ 15분]
Docker로 jenkins 구현 [30분]
Docker Security and Content Trust



Docker Security and Content Trustehazlett Docker provides security features to secure content, access, and platforms. It delivers integrated security through content trust, authorization and authentication, and runtime containment using cGroups, namespaces, capabilities, seccomp profiles, and Linux security modules.
Docker security: Rolling out Trust in your container



Docker security: Rolling out Trust in your containerRonak Kogta This document discusses various security aspects of Docker containers. It covers topics like Docker isolation, limiting privileges through capabilities and namespaces, filesystem security using SELinux/AppArmor, image signing with Docker Content Trust and Notary to ensure integrity, and tools like DockerBench for security best practices. The document emphasizes that with Docker, every process should only access necessary resources and taking a least privilege approach is important for security.
Oscon London 2016 - Docker from Development to Production



Oscon London 2016 - Docker from Development to ProductionPatrick Chanezon Docker revolutionized how developers and operations teams build, ship, and run applications, enabling them to leverage the latest advancements in software development: the microservice architecture style, the immutable infrastructure deployment style, and the DevOps cultural model.
Existing software layers are not a great fit to leverage these trends. Infrastructure as a service is too low level; platform as a service is too high level; but containers as a service (CaaS) is just right. Container images are just the right level of abstraction for DevOps, allowing developers to specify all their dependencies at build time, building and testing an artifact that, when ready to ship, is the exact thing that will run in production. CaaS gives ops teams the tools to control how to run these workloads securely and efficiently, providing portability between different cloud providers and on-premises deployments.
Patrick Chanezon offers a detailed overview of the latest evolutions to the Docker ecosystem enabling CaaS: standards (OCI, CNCF), infrastructure (runC, containerd, Notary), platform (Docker, Swarm), and services (Docker Cloud, Docker Datacenter). Patrick ends with a demo showing how to do in-container development of a Spring Boot application on a Mac running a preconfigured IDE in a container, provision a highly available Swarm cluster using Docker Datacenter on a cloud provider, and leverage the latest Docker tools to build, ship, and run a polyglot application architected as a set of microservices—including how to set up load balancing.
Docker Runtime Security



Docker Runtime SecuritySysdig While there have been many improvements around securing containers, there is still a large gap in monitoring the behaviour of containers in production. Sysdig Falco is an open source behavioural activity monitor for containerized environments.
Sysdig Falco can detect and alert on anomalous behaviour at the application, file, system, and network level. In this session get a deep dive into Falco: How does behavioural security differ from existing security solutions like image scanning, seccomp, SELinux or AppArmor? What can Sysdig Falco detect? Building and customizing rules for your Docker and Kubernetes apps. Forensics analysis with Sysdig Inspect even when the container doesn't exist anymore!
Read more on:
https://sysdig.com/blog/docker-runtime-security/
https://sysdig.com/blog/runtime-security-kubernetes-sysdig-falco/
KVM and docker LXC Benchmarking with OpenStack



KVM and docker LXC Benchmarking with OpenStackBoden Russell Passive benchmarking with docker LXC and KVM using OpenStack hosted in SoftLayer. These results provide initial incite as to why LXC as a technology choice offers benefits over traditional VMs and seek to provide answers as to the typical initial LXC question -- "why would I consider Linux Containers over VMs" from a performance perspective.
Results here provide insight as to:
- Cloudy ops times (start, stop, reboot) using OpenStack.
- Guest micro benchmark performance (I/O, network, memory, CPU).
- Guest micro benchmark performance of MySQL; OLTP read, read / write complex and indexed insertion.
- Compute node resource consumption; VM / Container density factors.
- Lessons learned during benchmarking.
The tests here were performed using OpenStack Rally to drive the OpenStack cloudy tests and various other linux tools to test the guest performance on a "micro level". The nova docker virt driver was used in the Cloud scenario to realize VMs as docker LXC containers and compared to the nova virt driver for libvirt KVM.
Please read the disclaimers in the presentation as this is only intended to be the "chip of the ice burg".
Containers: The What, Why, and How



Containers: The What, Why, and HowSneha Inguva In this presentation, I will be presenting the what, why, and how of containers at the Digital Ocean in Hyderabad.
Exploring Docker Security



Exploring Docker SecurityPatrick Kleindienst These are the slides from a talk I gave for our Secure Systems course in the degree program Computer Science and Media at Stuttgart Media University.
Running High Performance and Fault Tolerant Elasticsearch Clusters on Docker



Running High Performance and Fault Tolerant Elasticsearch Clusters on DockerSematext Group, Inc. Sematext engineer Rafal Kuc (@kucrafal) walks through the details of running high-performance, fault tolerant Elasticsearch clusters on Docker. Topics include: Containers vs. Virtual Machines, running the official Elasticsearch container, container constraints, good network practices, dealing with storage, data-only Docker volumes, scaling, time-based data, multiple tiers and tenants, indexing with and without routing, querying with and without routing, routing vs. no routing, and monitoring. Talk was delivered at DevOps Days Warsaw 2015.
Docker toolbox



Docker toolboxYonghwee Kim The Docker Toolbox installs several components to allow users to run Docker on their Mac systems without running a Linux VM directly. It includes the Docker client, Docker Machine, Docker Compose, Docker Kitematic, and Oracle VirtualBox. Docker Machine is used to create and connect to a lightweight Linux VM hosted by VirtualBox where the Docker daemon runs. This allows users to work with Docker images and containers without having to manage a separate Linux environment.
Viewers also liked (20)
How to Become a Thought Leader in Your Niche



How to Become a Thought Leader in Your NicheLeslie Samuel Are bloggers thought leaders? Here are some tips on how you can become one. Provide great value, put awesome content out there on a regular basis, and help others.
LXC, Docker, security: is it safe to run applications in Linux Containers?



LXC, Docker, security: is it safe to run applications in Linux Containers?Jérôme Petazzoni The document discusses the security of running applications in Linux containers. It begins by acknowledging that containers were not originally designed with security in mind. However, it then outlines several techniques that can be used to improve security, such as running containers without root privileges, dropping capabilities, enabling security modules like SELinux, and limiting access to devices and system calls. For the most security-sensitive tasks, it recommends running containers inside virtual machines to isolate them further. In the end, it argues that with the right precautions, containers can be used securely for many applications.
Docker bday #4 intro deck



Docker bday #4 intro deckSurit Aryal This document summarizes the agenda and activities for a Docker birthday meetup in Kathmandu. The meetup included celebrations, talks on Docker topics, socializing, and hands-on Docker labs. Over 130 meetups were held worldwide with over 6,000 RSVPs to celebrate Docker's 4th birthday. The labs guided participants through exercises on the Play with Docker website using a discount code for DockerCon.
2016.1.25



2016.1.25Surit Aryal This document discusses familiarity with Windows and the availability of games and software on other platforms. It notes that while Windows is familiar to many users, other platforms like Linux distributions through Steam OS and Android have growing market shares and software support through apps and games. Alternatives to Windows are increasingly viable options.
The How and Why of Container Vulnerability Management



The How and Why of Container Vulnerability ManagementBlack Duck by Synopsys The document discusses container vulnerability management. It describes the attacker model and how attackers exploit vulnerabilities. It emphasizes that open source code has less security support than closed source commercial code. The document outlines how to secure container contents and environment through techniques like enabling Linux security modules, using a minimal OS, and limiting privileges. It recommends verifying the trustworthiness of container sources and checking for vulnerable open source components. Black Duck software is introduced as a tool to analyze open source usage and risks.
Seven problems of Linux Containers



Seven problems of Linux ContainersKirill Kolyshkin OpenVZ, which has turned 7 recently, is an implementation of lightweight virtualization technology for Linux, something which is also referred to as LXC or just containers. The talk gives an insight into 7 different problems with containers and how they were solved. While most of these problems and solutions belongs in the Linux kernel, kernel knowledge is not expected from the audience.
Contain your risk: Deploy secure containers with trust and confidence



Contain your risk: Deploy secure containers with trust and confidenceBlack Duck by Synopsys Presented on September 22, 2016 by Brent Baude, Principle Software Engineer, Atomic and Docker Development, Red Hat; Randy Kilmon, VP, Engineering, Black Duck
Organizations are increasingly turning to container environments to meet the demand for faster, more agile software development. But a 2015 study conducted by Forrester Consulting on behalf of Red Hat revealed that 53% of IT operations and development decision makers at global enterprises reported container security concerns as a barrier to adoption.
The challenges of managing security risk increase in scope and complexity when hundreds or even thousands of different open source software components and licenses are part of your application code base. Since 2014, more than 6,000 new open source security vulnerabilities have been reported, making it essential to have good visibility into and control over the open source in use in order to understand if any known vulnerabilities are present.
In this webinar, experts from Red Hat and Black Duck will share the latest insights and recommendations for securing the open source in your containers, including protecting them from vulnerabilities like Heartbleed, Shellshock and Venom. You’ll learn:
• Why container environments present new application security challenges, including those posed by ever-increasing open source use.
• How to scan applications running in containers to identify open source in use and map known open source security vulnerabilities.
• Best practices and methodologies for deploying secure containers with trust and confidence.
Docker: automation for the rest of us



Docker: automation for the rest of usJérôme Petazzoni Docker landed almost two years ago, making it possible to build, ship, and run
any Linux application, on any platform, it was quickly adopted by developers
and ops, like no other tool before. The CI/CD industry even took it to
production long before it was stamped "production-ready."
Why does everyone (or almost!) love Docker? Because it puts powerful
automation abilities within the hands of normal developers. Automation
almost always involves building distribution packages, virtual machine
images, or writing configuration management manifests. With Docker,
those tasks are radically transformed: sometimes they're far easier than before,
other times they're no longer needed at all. Either way, the intervention
of a seasoned sysadmin guru is no longer required.
Docker, Linux Containers, and Security: Does It Add Up?



Docker, Linux Containers, and Security: Does It Add Up?Jérôme Petazzoni Containers are becoming increasingly popular. They have many advantages over virtual machines: they boot faster, have less performance overhead, and use less resources. However, those advantages also stem from the fact that containers share the kernel of their host, instead of abstracting an new independent environment. This sharing has significant security implications, as kernel exploits can now lead to host-wide escalations.
In this presentation, we will:
- Review the actual security risks, in particular for multi-tenant environments running arbitrary applications and code
- Discuss how to mitigate those risks
- Focus on containers as implemented by Docker and the libcontainer project, but the discussion also stands for plain containers as implemented by LXC
[Impact Lab] IT инструменты для проекта![[Impact Lab] IT инструменты для проекта](https://cdn.slidesharecdn.com/ss_thumbnails/it-150904044847-lva1-app6892-thumbnail.jpg?width=560&fit=bounds)
![[Impact Lab] IT инструменты для проекта](https://cdn.slidesharecdn.com/ss_thumbnails/it-150904044847-lva1-app6892-thumbnail.jpg?width=560&fit=bounds)
![[Impact Lab] IT инструменты для проекта](https://cdn.slidesharecdn.com/ss_thumbnails/it-150904044847-lva1-app6892-thumbnail.jpg?width=560&fit=bounds)
![[Impact Lab] IT инструменты для проекта](https://cdn.slidesharecdn.com/ss_thumbnails/it-150904044847-lva1-app6892-thumbnail.jpg?width=560&fit=bounds)
[Impact Lab] IT инструменты для проектаDmitry Spodarets Презентация для Impact Lab - http://socialcamp.od.ua/impact_lab/
Performance comparison between Linux Containers and Virtual Machines



Performance comparison between Linux Containers and Virtual MachinesSoheila Dehghanzadeh This presentation is based on http://ieeexplore.ieee.org/xpl/articleDetails.jsp?reload=true&arnumber=7164727&punumber%3D7153311%26filter%3DAND(p_IS_Number%3A7164643)%26pageNumber%3D3
Docker containers & the Future of Drupal testing 



Docker containers & the Future of Drupal testing Ricardo Amaro Story of an investigation to improve cloud
The sad VirtualMachine story
Containers and non-containers
DEMO - Drupal Docker
Drupal Testbots story in a Glance
Docker as a testing automation factor
DEMO - Docker Tesbot
Integration path
Building a REST API Microservice for the DevNet API Scavenger Hunt



Building a REST API Microservice for the DevNet API Scavenger HuntAshley Roach Building a REST API Microservice for the DevNet API Scavenger Hunt. Originally presented at QConSF 2016
Microservice architecture



Microservice architectureSlim Ouertani Microservice architecture breaks applications into small, independent services that communicate over well-defined interfaces. This document discusses key characteristics of microservices including componentization via services, decentralized governance and data management, and infrastructure automation. It also compares monoliths to microservices and covers some common pros and cons like increased operations overhead but also more evolutionary design.
Drupal workshop ist 2014



Drupal workshop ist 2014Ricardo Amaro 1) O documento apresenta um workshop sobre Drupal realizado pela Drupal Portugal em 28 de Abril de 2014.
2) É introduzido o que é Drupal, como funciona a comunidade Drupal Portugal e como utilizar e customizar sites com Drupal.
3) O workshop inclui demonstrações práticas de como criar e gerir conteúdo, utilizadores, módulos e traduções em Drupal.
How To Train Your APIs



How To Train Your APIsAshley Roach Originally presented at API Strat and Practice conference in Boston 2016 by me and Mandy Whaley, this presentation shows the multiple archetypes that you could encounter while trying to govern APIs at your company.
Open Source Tools for Container Security and Compliance @Docker LA Meetup 2/13



Open Source Tools for Container Security and Compliance @Docker LA Meetup 2/13Zach Hill This document discusses open-source tools for security and compliance using Docker containers. It introduces Anchore, an open-source tool that allows deep inspection of container images to check for compliance with policies. Anchore performs image scanning, analyzes operating system packages and artifacts, checks for secrets or source code, and validates Dockerfiles. It generates reports on findings and can integrate with DevOps pipelines using plug-ins for notifications and policy enforcement. Anchore is open-source, extensible, and provides both a web interface and command line tools.
Introduction to Infrastructure as Code & Automation / Introduction to Chef



Introduction to Infrastructure as Code & Automation / Introduction to ChefNathen Harvey The document provides an introduction to infrastructure as code using Chef. It begins with an introduction by Nathen Harvey and outlines the sys admin journey from manually managing servers to using automation and policy-driven configuration management. It then discusses how infrastructure as code with Chef allows treating infrastructure like code by programmatically provisioning and configuring components. The document demonstrates configuring resources like packages, services, files and more using Chef.
Drupalcamp es 2013 drupal with lxc docker and vagrant 



Drupalcamp es 2013 drupal with lxc docker and vagrant Ricardo Amaro This document discusses using containers like LXC and Docker to automate Drupal deployments. It begins with an introduction to the speaker and overview of virtual machines versus containers. The speaker then demonstrates using LXC containers on Ubuntu with tools like Vagrant and Puppet for configuration management. Docker is presented as an improvement allowing developers to package applications and dependencies into portable containers that can be run anywhere without reconfiguration.
Priming Your Teams For Microservice Deployment to the Cloud



Priming Your Teams For Microservice Deployment to the CloudMatt Callanan You think of a great idea for a microservice and want to ship it to production as quickly as possible. Of course you'll need to create a Git repo with a codebase that reuses libraries you share with other services. And you'll want a build and a basic test suite. You'll want to deploy it to immutable servers using infrastructure as code that dev and ops can maintain. Centralised logging, monitoring, and HipChat notifications would also be great. Of course you'll want a load balancer and a CNAME that your other microservices can hit. You'd love to have blue-green deploys and the ability to deploy updates at any time through a Continuous Delivery pipeline. Phew! How long will it take to set all this up? A couple of days? A week? A month?
What if you could do all of this within 30 minutes? And with a click of a button soon be receiving production traffic?
Matt introduces "Primer", Expedia's microservice generation and deployment platform that enables rapid experimentation in the cloud, how it's caused unprecedented rates of learning, and explain tips and tricks on how to build one yourself with practical takeaways for everyone from the startup to the enterprise.
Video: https://www.youtube.com/watch?v=Xy4EkaXyEs4
Meetup: http://www.meetup.com/Devops-Brisbane/events/225050723/
Ad
Similar to Docker Security Paradigm (20)
Securing Applications and Pipelines on a Container Platform



Securing Applications and Pipelines on a Container PlatformAll Things Open Presented at: Open Source 101 at Home
Presented by: Veer Muchandi, Red Hat Inc
Abstract: While everyone wants to do Containers and Kubernetes, they don’t know what they are getting into from Security perspective. This session intends to take you from “I don’t know what I don’t know” to “I know what I don’t know”. This helps you to make informed choices on Application Security.
Kubernetes as a Container Platform is becoming a de facto for every enterprise. In my interactions with enterprises adopting container platform, I come across common questions:
- How does application security work on this platform? What all do I need to secure?
- How do I implement security in pipelines?
- What about vulnerabilities discovered at a later point in time?
- What are newer technologies like Istio Service Mesh bring to table?
In this session, I will be addressing these commonly asked questions that every enterprise trying to adopt an Enterprise Kubernetes Platform needs to know so that they can make informed decisions.
Security on a Container Platform



Security on a Container PlatformAll Things Open Presented at All Things Open 2018
Presented by Veer Muchandi with Red Hat Inc.
10/22/18 - 2:15 PM - Security Track
Docker London: Container Security



Docker London: Container SecurityPhil Estes This document summarizes a presentation on container security given by Phil Estes. It identifies several threat vectors for containers including risks from individual containers, interactions between containers, external attacks, and application security issues. It then outlines various security tools and features in Docker like cgroups, Linux Security Modules, capabilities, seccomp, and user namespaces that can help mitigate these threats. Finally, it discusses some future directions for improving container security through more secure defaults, image signing, and network security enhancements.
Docker Container: isolation and security



Docker Container: isolation and security宇 傅 Linux namespaces and control groups (cgroups) provide isolation and security for Docker containers. Namespaces isolate processes by PID, network, IPC, mount points, etc. Cgroups limit CPU, memory, storage resources. Capabilities and security models like seccomp, AppArmor further harden containers by dropping privileges and blocking risky syscalls. Together, these mechanisms isolate containers and applications from hosts, other containers, and external attacks while still allowing resource sharing through the kernel.
Securing Applications and Pipelines on a Container Platform



Securing Applications and Pipelines on a Container PlatformAll Things Open The document discusses securing applications on a container platform. It covers considerations for security at the host operating system level, during container builds, and at runtime. Specific techniques discussed include Linux namespaces and cgroups for isolation, SELinux and MCS labels for access control between containers, capability dropping to restrict privileges, and read-only mounts. Container scanning and signing images are also covered.
Linux Container Technology 101



Linux Container Technology 101inside-BigData.com Christian Kniep from Docker Inc. gave this talk at the Stanford HPC Conference.
"This talk will recap the history of and what constitutes Linux Containers, before laying out how the technology is employed by various engines and what problems these engines have to solve. Afterward, Christian will elaborate on why the advent of standards for images and runtimes moved the discussion from building and distributing containers to orchestrating containerized applications at scale. In conclusion, attendees will get an update on what problems still hinder the adoption of containers for distributed high performance workloads and how Docker is addressing these issues."
Christian Kniep is a Technical Account Manager at Docker, Inc. With a 10 year journey rooted in the HPC parts of the german automotive industry, Christian Kniep started to support CAE applications and VR installations. When told at a conference that HPC can not learn anything from the emerging Cloud and BigData companies, he became curious and was leading the containerization effort of the cloud-stack at Playstation Now. Christian joined Docker Inc in 2017 to help push the adoption forward and be part of the innovation instead of an external bystander. During the day he helps Docker customers in the EMEA region to fully utilize the power of containers; at night he likes to explore new emerging trends by containerizing them first and seek application in the nebulous world of DevOps.
Watch the video: https://wp.me/p3RLHQ-i4X
Learn more: http://docker.com
and
http://hpcadvisorycouncil.com
Sign up for our insideHPC Newsletter: http://insidehpc.com
Fast boot



Fast bootSZ Lin This document discusses methods for reducing Linux boot times, focusing on hardware architecture, the boot process, kernel optimizations, and the init system. It recommends using faster storage like SSDs, optimizing bootloaders like GRUB, improving kernel decompression with LZ4, disabling unnecessary processes, and switching to systemd for network configuration to reduce boot times to as little as 2 seconds.
First steps on CentOs7



First steps on CentOs7Marc Cortinas Val Namespaces, Cgroups and systemd document discusses:
1. Namespaces and cgroups which provide isolation and resource management capabilities in Linux.
2. Systemd which is a system and service manager that aims to boot faster and improve dependencies between services.
3. Key components of systemd include unit files, systemctl, and tools to manage services, devices, mounts and other resources.
Unraveling Docker Security: Lessons From a Production Cloud



Unraveling Docker Security: Lessons From a Production CloudSalman Baset Unraveling Docker Security: Lessons From a Production Cloud
This document discusses Docker security issues in a multi-tenant cloud deployment model where containers from different tenants run on the same host machine. It outlines threats like containers attacking other containers or the host, and describes Docker features for isolation like namespaces, cgroups, capabilities, AppArmor, and restricting the Docker API. Putting these protections together can help provide security, but inherent issues remain with shared kernel access and some features needing further implementation.
POUG2022_OracleDbNestInsideOut.pptx



POUG2022_OracleDbNestInsideOut.pptxMahmoud Hatem This document discusses Oracle DbNest and Linux containers. It begins by defining DbNest and containers, then discusses the fundamental Linux technologies they are based on such as namespaces, cgroups, capabilities, and seccomp. It provides details on specific namespaces like mount, PID, user, and network namespaces. It also discusses capabilities, cgroups, bind mounting, and pivot rooting. The document concludes with a demonstration of building containers and filtering syscalls with seccomp profiles.
Container Performance Analysis



Container Performance AnalysisBrendan Gregg The document summarizes a talk on container performance analysis. It discusses identifying bottlenecks at the host, container, and kernel level using various Linux performance tools. It then provides an overview of how containers work in Linux using namespaces and control groups (cgroups). Finally, it demonstrates some example commands like docker stats, systemd-cgtop, and bcc/BPF tools that can be used to analyze containers and cgroups from the host system.
Advanced Namespaces and cgroups



Advanced Namespaces and cgroupsKernel TLV The document provides an overview of the cgroup subsystem and namespace subsystem in Linux, which form the basis of Linux containers. It discusses how cgroups and namespaces enable lightweight virtualization of processes through isolation of resources and namespaces. It then covers specific aspects of cgroups like the memory, CPU, devices, and PIDs controllers. It also summarizes the key differences and improvements in the cgroup v2 implementation, such as having a single unified hierarchy and consistent controller interfaces.
Container Performance Analysis Brendan Gregg, Netflix



Container Performance Analysis Brendan Gregg, NetflixDocker, Inc. The document summarizes a talk on container performance analysis. It discusses identifying bottlenecks at the host, container, and kernel level using various Linux performance tools. It also provides an overview of how containers work in Linux using namespaces and control groups (cgroups). Specifically, it demonstrates analyzing resource usage and limitations for containers using tools like docker stats, systemd-cgtop, and investigating namespaces.
Dockers zero to hero



Dockers zero to heroNicolas De Loof présentation de l'utilisation de Docker, du niveau 0 "je joue avec sur mon poste" au niveau Docker Hero "je tourne en prod".
Ce talk fait suite à l'intro de @dgageot et ne comporte donc pas l'intro "c'est quoi Docker ?".
Container & kubernetes



Container & kubernetesTed Jung Container technologies use namespaces and cgroups to provide isolation between processes and limit resource usage. Docker builds on these technologies using a client-server model and additional features like images, containers, and volumes to package and run applications reliably and at scale. Kubernetes builds on Docker to provide a platform for automating deployment, scaling, and operations of containerized applications across clusters of hosts. It uses labels and pods to group related containers together and services to provide discovery and load balancing for pods.
Secure container: Kata container and gVisor



Secure container: Kata container and gVisorChing-Hsuan Yen Kata Container & gVisor provide approaches to securely isolate containers by keeping them out of the direct kernel space. Kata Container uses virtual machines with lightweight kernels to isolate containers, while gVisor uses a userspace kernel implemented in Go to provide isolation. Both aim to protect the host kernel by preventing containers from accessing kernel resources directly. Kata Container has a larger memory footprint than gVisor due to its use of virtual machines, but provides stronger isolation of containers.
Artem Zhurbila - docker clusters (solit 2015)



Artem Zhurbila - docker clusters (solit 2015)Artem Zhurbila About docker cluster management tools
1. Base concepts of cluster
management and docker
2. Docker Swarm
3. Amazon EC2 Container Service
4. Kubernetes
5. Mesosphere
Evolution of Linux Containerization 



Evolution of Linux Containerization WSO2 This document discusses the evolution of Linux container virtualization, including technologies like LXC, Docker, CoreOS, and Kubernetes. It provides an overview of key concepts in virtualization like namespaces, cgroups, AppArmor, SELinux, and seccomp. It also summarizes features of Linux container engines like LXC, and container platforms like Docker, CoreOS, and the Kubernetes container cluster management system.
Evoluation of Linux Container Virtualization



Evoluation of Linux Container VirtualizationImesh Gunaratne Hypervisors, Linux Containers, Linux Kernel features used by Containers, LXC Engine, Docker, CoreOS and Kubernetes
linux installation.pdf



linux installation.pdfMuhammadShoaibHussai2 This document provides information about installing and configuring Linux, Apache web server, PostgreSQL database, and Apache Tomcat on a Linux system. It discusses installing Ubuntu using VirtualBox, creating users and groups, setting file permissions, important Linux files and directories. It also covers configuring Apache server and Tomcat, installing and configuring PostgreSQL, and some self-study questions about the Linux boot process, run levels, finding the kernel version and learning about NIS, NFS, and RPM package management.
Ad
Recently uploaded (20)
tecnologias de las primeras civilizaciones.pdf



tecnologias de las primeras civilizaciones.pdffjgm517 descaripcion detallada del avance de las tecnologias en mesopotamia, egipto, roma y grecia.
HCL Nomad Web – Best Practices and Managing Multiuser Environments



HCL Nomad Web – Best Practices and Managing Multiuser Environmentspanagenda Webinar Recording: https://www.panagenda.com/webinars/hcl-nomad-web-best-practices-and-managing-multiuser-environments/
HCL Nomad Web is heralded as the next generation of the HCL Notes client, offering numerous advantages such as eliminating the need for packaging, distribution, and installation. Nomad Web client upgrades will be installed “automatically” in the background. This significantly reduces the administrative footprint compared to traditional HCL Notes clients. However, troubleshooting issues in Nomad Web present unique challenges compared to the Notes client.
Join Christoph and Marc as they demonstrate how to simplify the troubleshooting process in HCL Nomad Web, ensuring a smoother and more efficient user experience.
In this webinar, we will explore effective strategies for diagnosing and resolving common problems in HCL Nomad Web, including
- Accessing the console
- Locating and interpreting log files
- Accessing the data folder within the browser’s cache (using OPFS)
- Understand the difference between single- and multi-user scenarios
- Utilizing Client Clocking
Complete Guide to Advanced Logistics Management Software in Riyadh.pdf



Complete Guide to Advanced Logistics Management Software in Riyadh.pdfSoftware Company Explore the benefits and features of advanced logistics management software for businesses in Riyadh. This guide delves into the latest technologies, from real-time tracking and route optimization to warehouse management and inventory control, helping businesses streamline their logistics operations and reduce costs. Learn how implementing the right software solution can enhance efficiency, improve customer satisfaction, and provide a competitive edge in the growing logistics sector of Riyadh.
Technology Trends in 2025: AI and Big Data Analytics



Technology Trends in 2025: AI and Big Data AnalyticsInData Labs At InData Labs, we have been keeping an ear to the ground, looking out for AI-enabled digital transformation trends coming our way in 2025. Our report will provide a look into the technology landscape of the future, including:
-Artificial Intelligence Market Overview
-Strategies for AI Adoption in 2025
-Anticipated drivers of AI adoption and transformative technologies
-Benefits of AI and Big data for your business
-Tips on how to prepare your business for innovation
-AI and data privacy: Strategies for securing data privacy in AI models, etc.
Download your free copy nowand implement the key findings to improve your business.
Mobile App Development Company in Saudi Arabia



Mobile App Development Company in Saudi ArabiaSteve Jonas EmizenTech is a globally recognized software development company, proudly serving businesses since 2013. With over 11+ years of industry experience and a team of 200+ skilled professionals, we have successfully delivered 1200+ projects across various sectors. As a leading Mobile App Development Company In Saudi Arabia we offer end-to-end solutions for iOS, Android, and cross-platform applications. Our apps are known for their user-friendly interfaces, scalability, high performance, and strong security features. We tailor each mobile application to meet the unique needs of different industries, ensuring a seamless user experience. EmizenTech is committed to turning your vision into a powerful digital product that drives growth, innovation, and long-term success in the competitive mobile landscape of Saudi Arabia.
Transcript: #StandardsGoals for 2025: Standards & certification roundup - Tec...



Transcript: #StandardsGoals for 2025: Standards & certification roundup - Tec...BookNet Canada Book industry standards are evolving rapidly. In the first part of this session, we’ll share an overview of key developments from 2024 and the early months of 2025. Then, BookNet’s resident standards expert, Tom Richardson, and CEO, Lauren Stewart, have a forward-looking conversation about what’s next.
Link to recording, presentation slides, and accompanying resource: https://bnctechforum.ca/sessions/standardsgoals-for-2025-standards-certification-roundup/
Presented by BookNet Canada on May 6, 2025 with support from the Department of Canadian Heritage.
Special Meetup Edition - TDX Bengaluru Meetup #52.pptx



Special Meetup Edition - TDX Bengaluru Meetup #52.pptxshyamraj55 We’re bringing the TDX energy to our community with 2 power-packed sessions:
🛠️ Workshop: MuleSoft for Agentforce
Explore the new version of our hands-on workshop featuring the latest Topic Center and API Catalog updates.
📄 Talk: Power Up Document Processing
Dive into smart automation with MuleSoft IDP, NLP, and Einstein AI for intelligent document workflows.
Procurement Insights Cost To Value Guide.pptx



Procurement Insights Cost To Value Guide.pptxJon Hansen Procurement Insights integrated Historic Procurement Industry Archives, serves as a powerful complement — not a competitor — to other procurement industry firms. It fills critical gaps in depth, agility, and contextual insight that most traditional analyst and association models overlook.
Learn more about this value- driven proprietary service offering here.
AI and Data Privacy in 2025: Global Trends



AI and Data Privacy in 2025: Global TrendsInData Labs In this infographic, we explore how businesses can implement effective governance frameworks to address AI data privacy. Understanding it is crucial for developing effective strategies that ensure compliance, safeguard customer trust, and leverage AI responsibly. Equip yourself with insights that can drive informed decision-making and position your organization for success in the future of data privacy.
This infographic contains:
-AI and data privacy: Key findings
-Statistics on AI data privacy in the today’s world
-Tips on how to overcome data privacy challenges
-Benefits of AI data security investments.
Keep up-to-date on how AI is reshaping privacy standards and what this entails for both individuals and organizations.
Enhancing ICU Intelligence: How Our Functional Testing Enabled a Healthcare I...



Enhancing ICU Intelligence: How Our Functional Testing Enabled a Healthcare I...Impelsys Inc. Impelsys provided a robust testing solution, leveraging a risk-based and requirement-mapped approach to validate ICU Connect and CritiXpert. A well-defined test suite was developed to assess data communication, clinical data collection, transformation, and visualization across integrated devices.
Generative Artificial Intelligence (GenAI) in Business



Generative Artificial Intelligence (GenAI) in BusinessDr. Tathagat Varma My talk for the Indian School of Business (ISB) Emerging Leaders Program Cohort 9. In this talk, I discussed key issues around adoption of GenAI in business - benefits, opportunities and limitations. I also discussed how my research on Theory of Cognitive Chasms helps address some of these issues
Increasing Retail Store Efficiency How can Planograms Save Time and Money.pptx



Increasing Retail Store Efficiency How can Planograms Save Time and Money.pptxAnoop Ashok In today's fast-paced retail environment, efficiency is key. Every minute counts, and every penny matters. One tool that can significantly boost your store's efficiency is a well-executed planogram. These visual merchandising blueprints not only enhance store layouts but also save time and money in the process.
Dev Dives: Automate and orchestrate your processes with UiPath Maestro



Dev Dives: Automate and orchestrate your processes with UiPath MaestroUiPathCommunity This session is designed to equip developers with the skills needed to build mission-critical, end-to-end processes that seamlessly orchestrate agents, people, and robots.
📕 Here's what you can expect:
- Modeling: Build end-to-end processes using BPMN.
- Implementing: Integrate agentic tasks, RPA, APIs, and advanced decisioning into processes.
- Operating: Control process instances with rewind, replay, pause, and stop functions.
- Monitoring: Use dashboards and embedded analytics for real-time insights into process instances.
This webinar is a must-attend for developers looking to enhance their agentic automation skills and orchestrate robust, mission-critical processes.
👨🏫 Speaker:
Andrei Vintila, Principal Product Manager @UiPath
This session streamed live on April 29, 2025, 16:00 CET.
Check out all our upcoming Dev Dives sessions at https://community.uipath.com/dev-dives-automation-developer-2025/.
AI Changes Everything – Talk at Cardiff Metropolitan University, 29th April 2...



AI Changes Everything – Talk at Cardiff Metropolitan University, 29th April 2...Alan Dix Talk at the final event of Data Fusion Dynamics: A Collaborative UK-Saudi Initiative in Cybersecurity and Artificial Intelligence funded by the British Council UK-Saudi Challenge Fund 2024, Cardiff Metropolitan University, 29th April 2025
https://alandix.com/academic/talks/CMet2025-AI-Changes-Everything/
Is AI just another technology, or does it fundamentally change the way we live and think?
Every technology has a direct impact with micro-ethical consequences, some good, some bad. However more profound are the ways in which some technologies reshape the very fabric of society with macro-ethical impacts. The invention of the stirrup revolutionised mounted combat, but as a side effect gave rise to the feudal system, which still shapes politics today. The internal combustion engine offers personal freedom and creates pollution, but has also transformed the nature of urban planning and international trade. When we look at AI the micro-ethical issues, such as bias, are most obvious, but the macro-ethical challenges may be greater.
At a micro-ethical level AI has the potential to deepen social, ethnic and gender bias, issues I have warned about since the early 1990s! It is also being used increasingly on the battlefield. However, it also offers amazing opportunities in health and educations, as the recent Nobel prizes for the developers of AlphaFold illustrate. More radically, the need to encode ethics acts as a mirror to surface essential ethical problems and conflicts.
At the macro-ethical level, by the early 2000s digital technology had already begun to undermine sovereignty (e.g. gambling), market economics (through network effects and emergent monopolies), and the very meaning of money. Modern AI is the child of big data, big computation and ultimately big business, intensifying the inherent tendency of digital technology to concentrate power. AI is already unravelling the fundamentals of the social, political and economic world around us, but this is a world that needs radical reimagining to overcome the global environmental and human challenges that confront us. Our challenge is whether to let the threads fall as they may, or to use them to weave a better future.
Rusty Waters: Elevating Lakehouses Beyond Spark



Rusty Waters: Elevating Lakehouses Beyond Sparkcarlyakerly1 Spark is a powerhouse for large datasets, but when it comes to smaller data workloads, its overhead can sometimes slow things down. What if you could achieve high performance and efficiency without the need for Spark?
At S&P Global Commodity Insights, having a complete view of global energy and commodities markets enables customers to make data-driven decisions with confidence and create long-term, sustainable value. 🌍
Explore delta-rs + CDC and how these open-source innovations power lightweight, high-performance data applications beyond Spark! 🚀
HCL Nomad Web – Best Practices und Verwaltung von Multiuser-Umgebungen



HCL Nomad Web – Best Practices und Verwaltung von Multiuser-Umgebungenpanagenda Webinar Recording: https://www.panagenda.com/webinars/hcl-nomad-web-best-practices-und-verwaltung-von-multiuser-umgebungen/
HCL Nomad Web wird als die nächste Generation des HCL Notes-Clients gefeiert und bietet zahlreiche Vorteile, wie die Beseitigung des Bedarfs an Paketierung, Verteilung und Installation. Nomad Web-Client-Updates werden “automatisch” im Hintergrund installiert, was den administrativen Aufwand im Vergleich zu traditionellen HCL Notes-Clients erheblich reduziert. Allerdings stellt die Fehlerbehebung in Nomad Web im Vergleich zum Notes-Client einzigartige Herausforderungen dar.
Begleiten Sie Christoph und Marc, während sie demonstrieren, wie der Fehlerbehebungsprozess in HCL Nomad Web vereinfacht werden kann, um eine reibungslose und effiziente Benutzererfahrung zu gewährleisten.
In diesem Webinar werden wir effektive Strategien zur Diagnose und Lösung häufiger Probleme in HCL Nomad Web untersuchen, einschließlich
- Zugriff auf die Konsole
- Auffinden und Interpretieren von Protokolldateien
- Zugriff auf den Datenordner im Cache des Browsers (unter Verwendung von OPFS)
- Verständnis der Unterschiede zwischen Einzel- und Mehrbenutzerszenarien
- Nutzung der Client Clocking-Funktion
TrsLabs - Fintech Product & Business Consulting



TrsLabs - Fintech Product & Business ConsultingTrs Labs Hybrid Growth Mandate Model with TrsLabs
Strategic Investments, Inorganic Growth, Business Model Pivoting are critical activities that business don't do/change everyday. In cases like this, it may benefit your business to choose a temporary external consultant.
An unbiased plan driven by clearcut deliverables, market dynamics and without the influence of your internal office equations empower business leaders to make right choices.
Getting things done within a budget within a timeframe is key to Growing Business - No matter whether you are a start-up or a big company
Talk to us & Unlock the competitive advantage
Docker Security Paradigm
- 1. By Anis LARGUEM Docker Security Paradigm
- 2. Container Security Control Groups 2 3 Introduction1 Namespaces4 Capabilities5 Summary First Meetup Secure computing mode6
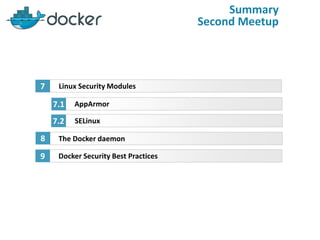
- 3. Summary Second Meetup Linux Security Modules AppArmor 7 7.1 SELinux7.2 The Docker daemon8 Docker Security Best Practices9
- 5. Container Security Containers use several mechanisms for security : Control Groups (cgroups) Namespaces. Capabilities. Seccomp. Linux security mechanisms. The Docker daemon.
- 6. Control Groups (cgroups) By default, a container has no resource constraints and can use as much of a given resource as the host’s kernel scheduler will allow… https://docs.docker.com/engine/admin/resource_constraints/
- 7. Control Groups (cgroups) Denial Of Service (cpu, memory, disk) Fork bomb :(){:|:&};: Human Redable : bomb() { bomb | bomb & }; bomb import os while 1: os.fork() perl -e "fork while fork" &
- 8. Control Groups (cgroups) Limit a container's resources Docker provides ways to control how much memory, CPU, or block IO a container can use, setting runtime configuration flags of the docker run command. docker run -it -m 500M --kernel-memory 50M --cpu-shares 512 --blkio- weight 400 --name ubuntu1 ubuntu bash
- 9. Control Groups (cgroups) Option Description -m or --me- mory= The maximum amount of memory the container can use. If you set this option, the minimum allowed value is 4m (4 megabyte). --memory- swap* The amount of memory this container is allowed to swap to disk. See --memory- swap details. --memory- swappiness By default, the host kernel can swap out a percentage of anonymous pages used by a container. You can set --memory-swappiness to a value between 0 and 100, to tune this percentage. See --memory-swappiness details. --memory- reservation Allows you to specify a soft limit smaller than --memory which is activated when Docker detects contention or low memory on the host machine. If you use --memory-reservation, it must be set lower than --memory in order for it to take precedence. Because it is a soft limit, it does not guarantee that the container will not exceed the limit. --kernel- memory The maximum amount of kernel memory the container can use. The minimum allowed value is 4m. Because kernel memory cannot be swapped out, a container which is starved of kernel memory may block host machine resources, which can have side effects on the host machine and on other containers. See --kernel- memory details. --cpus=<va- lue> Specify how much of the available CPU resources a container can use. For ins- tance, if the host machine has two CPUs and you set --cpus="1.5", the container will be guaranteed to be able to access at most one and a half of the CPUs. This is the equivalent of setting --cpu-period="100000" and --cpu-quota="150000". Available in Docker 1.13 and higher. --cpu-pe- riod=<va- lue> Specify the CPU CFS scheduler period, which is used alongside --cpu-quota. De- faults to 1 second, expressed in micro-seconds. Most users do not change this from the default. If you use Docker 1.13 or higher, use --cpus instead. …
- 10. Control Groups (cgroups) Prevent fork bombs: A new cgroup (PIDs subsystem ) to limit the number of processes that can be forked inside a cgroup. Kernel 4.3+ & Docker 1.11+ (--pids-limit)
- 11. Namespaces : By default containers run with full root privileges root in container == root outside container Never run applications as root inside the container.
- 12. User Namespaces Docker introduced support for user namespace in version 1.10 run as user : --user UID:GID Need root inside container : --userns-remap [uid[:gid]] Docker daemon needs to be started with : --userns- remap=username/uid:groupname/gid”. Using “default” will create “dockremap” user (--userns-remap=defaults)
- 13. Docker internals Architecture & Layouts Capabilites Capabilities divide system access into logical groups that may be individually granted to, or removed from, different processes. Capabilities allow system administrators to fine-tune what a process is allowed to do The capabilities are divided into four sets : Effective Permitted Inheritable Ambient (since Linux 4.3) The use of capabilities is not limited to processes. They are also placed on the executable files
- 14. Default Capabilities Capability Key Capability Description SETPCAP Modify process capabilities. MKNOD Create special files using mknod(2). AUDIT_WRITE Write records to kernel auditing log. CHOWN Make arbitrary changes to file UIDs and GIDs (see chown(2)). NET_RAW Use RAW and PACKET sockets. DAC_OVERRIDE Bypass file read, write, and execute permission checks. FOWNER Bypass permission checks on operations that normally require the file system UID of the process to match the UID of the file. FSETID Don’t clear set-user-ID and set-group-ID permission bits when a file is modified. KILL Bypass permission checks for sending signals. SETGID Make arbitrary manipulations of process GIDs and supplementary GID list. SETUID Make arbitrary manipulations of process UIDs. NET_BIND_SERVICE Bind a socket to internet domain privileged ports (port numbers less than 1024). SYS_CHROOT Use chroot(2), change root directory. SETFCAP Set file capabilities. --cap-add: Add Linux capabilities --cap-drop: Drop Linux capabilities
- 15. Capabilities that can be added Capability Key Capability Description SYS_MODULE Load and unload kernel modules. SYS_RAWIO Perform I/O port operations (iopl(2) and ioperm(2)). SYS_PACCT Use acct(2), switch process accounting on or off. SYS_ADMIN Perform a range of system administration operations. SYS_NICE Raise process nice value (nice(2), setpriority(2)) and change the nice value for arbitrary processes. SYS_RESOURCE Override resource Limits. SYS_TIME Set system clock (settimeofday(2), stime(2), adjtimex(2)); set real-time (hardware) clock. SYS_TTY_CONFIG Use vhangup(2); employ various privileged ioctl(2) operations on virtual terminals. AUDIT_CONTROL Enable and disable kernel auditing; change auditing filter rules; retrieve auditing status and filtering rules. MAC_OVERRIDE Allow MAC configuration or state changes. Implemented for the Smack LSM. MAC_ADMIN Override Mandatory Access Control (MAC). Implemented for the Smack Linux Security Module (LSM). NET_ADMIN Perform various network-related operations. SYSLOG Perform privileged syslog(2) operations. DAC_READ_SEARCH Bypass file read permission checks and directory read and execute permission checks. LINUX_IMMUTABLE Set the FS_APPEND_FL and FS_IMMUTABLE_FL i-node flags. NET_BROADCAST Make socket broadcasts, and listen to multicasts. IPC_LOCK Lock memory (mlock(2), mlockall(2), mmap(2), shmctl(2)). IPC_OWNER Bypass permission checks for operations on System V IPC objects. SYS_PTRACE Trace arbitrary processes using ptrace(2). SYS_BOOT Use reboot(2) and kexec_load(2), reboot and load a new kernel for later execution. LEASE Establish leases on arbitrary files (see fcntl(2)). WAKE_ALARM Trigger something that will wake up the system. BLOCK_SUSPEND Employ features that can block system suspend.
- 16. Secure computing mode Seccomp is used to restrict the set of system calls applications can make seccomp is a sandboxing facility in the Linux kernel that acts like a firewall for system calls (syscalls). Seccomp is an existing open source project originally created for Google Chrome. It uses Berkeley Packet Filter (BPF) rules to filter syscalls.
- 17. Example of blocked syscall Syscall Description acct Accounting syscall which could let containers disable their own resource limits or process accounting. Also gated by CAP_SYS_PACCT. add_key Prevent containers from using the kernel keyring, which is not namespaced. adjtimex Similar to clock_settime and settimeofday, time/date is not namespaced. Also gated by CAP_SYS_TIME. bpf Deny loading potentially persistent bpf programs into kernel, already gated by CAP_SYS_ADMIN. clock_adjtime Time/date is not namespaced. Also gated by CAP_SYS_TIME. clock_settime Time/date is not namespaced. Also gated by CAP_SYS_TIME. clone Deny cloning new namespaces. Also gated by CAP_SYS_ADMIN for CLONE_* flags, except CLONE_USERNS. create_module Deny manipulation and functions on kernel modules. Obsolete. Also gated by CAP_SYS_MODULE. delete_module Deny manipulation and functions on kernel modules. Also gated by CAP_SYS_MODULE. …
- 18. larguas@ubuntu:~$ strace -c -f -S name ps 2>&1 1>/dev/null | tail -n +3 | head -n -2 | awk '{print $(NF)}' access arch_prctl brk close execve fstat Futex Write … Seccomp and the no-new-privileges option Seccomp policies have to be applied before executing your container and be less specific unless you use: --security-opt no-new-privileges
- 19. To be continued… Linux Security Modules AppArmor 7 7.1 SELinux7.2 The Docker daemon8 Docker Security Best Practices9


