Docker security: Rolling out Trust in your container
1 like730 views
This document discusses various security aspects of Docker containers. It covers topics like Docker isolation, limiting privileges through capabilities and namespaces, filesystem security using SELinux/AppArmor, image signing with Docker Content Trust and Notary to ensure integrity, and tools like DockerBench for security best practices. The document emphasizes that with Docker, every process should only access necessary resources and taking a least privilege approach is important for security.
1 of 28
Downloaded 44 times



























Ad
Recommended
Docker Security and Content Trust



Docker Security and Content Trustehazlett Docker provides security features to secure content, access, and platforms. It delivers integrated security through content trust, authorization and authentication, and runtime containment using cGroups, namespaces, capabilities, seccomp profiles, and Linux security modules.
DockerCon 2016 Recap



DockerCon 2016 Recapehazlett DockerCon 2016 Recap highlights new features in Docker 1.12 including Swarm mode for orchestration without an external datastore, declarative services, routing mesh, stacks for multi-container applications, and built-in security. It also discusses Docker for Mac/Windows which now has a native experience, improved networking and file sharing, and Docker for AWS which provisions highly available Swarm clusters on AWS using CloudFormation templates. The Docker Store marketplace was introduced for validated Dockerized applications.
Container Security



Container SecuritySalman Baset Container security involves securing the host, container content, orchestration, and applications. The document discusses how container isolation evolved over time through namespaces, cgroups, capabilities, and other Linux kernel features. It also covers securing container images, orchestrators, and applications themselves. Emerging technologies like LinuxKit, Katacontainers, and MirageOS aim to provide more lightweight and secure container environments.
Docker Security Overview



Docker Security OverviewSreenivas Makam This document summarizes Docker security features as of release 1.12. It discusses key security modules like namespaces, cgroups, capabilities, seccomp, AppArmor/SELinux that provide access control and isolation in Docker containers. It also covers multi-tenant security, image signing, TLS for daemon access, and best practices like using official images and regular updates.
Container security



Container securityAnthony Chow This document discusses container security and provides information on various related topics. It begins with an overview of container security risks such as escapes and application vulnerabilities. It then covers security controls for containers like namespaces, control groups, and capabilities. Next, it discusses access control models and Linux security modules like SELinux and AppArmor that can provide container isolation. The document concludes with some third-party security offerings and emerging technologies that aim to enhance container security.
Testing Docker Security Linuxlab 2017



Testing Docker Security Linuxlab 2017Jose Manuel Ortega Candel This document summarizes a presentation on testing Docker security. It discusses security mechanisms like namespaces and cgroups that Docker uses. It covers best practices like running containers as non-root users, using read-only containers and volumes, and dropping unnecessary privileges. Tools are presented for auditing the Docker host and images for vulnerabilities, like Docker Bench Security, Lynis, Docker Security Scanning, and Anchore. The document demonstrates using these tools.
Understanding container security



Understanding container securityJohn Kinsella This document discusses container security, providing a brief history of containers, security benefits and challenges of containers, and approaches to container vulnerability management and responding to attacks. It notes that while containers are not new, their adoption has increased rapidly in recent years. The document outlines security advantages like smaller surface areas but also challenges like managing vulnerabilities across many moving parts. It recommends strategies like using official images, hardening hosts, scanning for vulnerabilities, and practicing incident response for containers.
Tokyo OpenStack Summit 2015: Unraveling Docker Security



Tokyo OpenStack Summit 2015: Unraveling Docker SecurityPhil Estes A Docker security talk that Salman Baset and Phil Estes presented at the Tokyo OpenStack Summit on October 29th, 2015. In this talk we provided an overview of the security constraints available to Docker cloud operators and users and then walked through a "lessons learned" from experiences operating IBM's public Bluemix container cloud based on Docker container technology.
Docker Container Security - A Network View



Docker Container Security - A Network ViewNeuVector A Network View of Docker - You Can't Secure What You Can't See.
Learn critical networking issues and advice for run-time container security
To watch the recorded webinar go to http://neuvector.com/docker-security-webinar
What you will learn in this technical overview:
- Top concerns for deploying containers in production
- Fundamentals of Docker container security
- A sample container exploit using the recently discovered Dirty COW vulnerability
- East-west traffic network issues on AWS and other clouds
- How NACLs, Sec Groups, and flow logs work or don't work with overlay networks
- Visualization and monitoring of containers during run-time.
- Microsegmentation of applications to isolate and protect them.
Docker Security Paradigm



Docker Security ParadigmAnis LARGUEM This document discusses security mechanisms in Docker containers, including control groups (cgroups) to limit resources, namespaces to isolate processes, and capabilities to restrict privileges. It covers secure computing modes like seccomp that sandbox system calls. Linux security modules like AppArmor and SELinux are also mentioned, along with best practices for the Docker daemon and container security overall.
How Secure Is Your Container? ContainerCon Berlin 2016



How Secure Is Your Container? ContainerCon Berlin 2016Phil Estes A conference talk at ContainerCon Europe in Berlin, Germany, given on October 5th, 2016. This is a slightly modified version of my talk first used at Docker London in July 2016.
Veer's Container Security



Veer's Container SecurityJim Barlow Container security involves securing containers at both the host and application level. At the host level, Linux technologies like namespaces, cgroups, SELinux, and seccomp provide isolation between containers. Container images are also scanned for vulnerabilities. The OpenShift platform provides additional security features like role-based access control, network policies, encrypted communications, and controls over privileged containers and storage. Application security best practices within containers include using HTTPS, securing secrets, and API management tools.
Docker Security - Continuous Container Security



Docker Security - Continuous Container SecurityDieter Reuter This document discusses Docker container security. It begins by outlining common container threats like ransomware, DDoS attacks, and privilege escalations. It then describes the need for continuous container security across the development, deployment and runtime phases. This includes techniques like image signing, user access controls, code analysis, image scanning, and host/kernel hardening. The document also discusses inspecting and protecting container network traffic and hosts from attacks. It emphasizes the challenges of monitoring large, complex deployments and automating security at scale across orchestration platforms and network overlays. Several demos are proposed to showcase micro-segmentation of applications and runtime vulnerability scanning using NeuVector.
Docker security introduction-task-2016



Docker security introduction-task-2016Ricardo Gerardi This document discusses Docker security. It begins by introducing Docker and containers, then covers securing Docker images through signing and scanning. It discusses how Docker uses namespaces and cgroups for isolation. It also addresses securing the Docker daemon and containers, as well as operational concerns around deployment, networking, monitoring, and logging of containers. It concludes by looking at future directions like unikernels and serverless architectures.
Docker: Aspects of Container Isolation



Docker: Aspects of Container Isolationallingeek Presentation on the Linux namespaces and system calls used to provide container isolation with Docker. Presented in March 2015 at http://www.meetup.com/Docker-Phoenix/ in Tempe, Arizona.
DockerCon EU 2015: Docker and PCI-DSS - Lessons learned in a security sensiti...



DockerCon EU 2015: Docker and PCI-DSS - Lessons learned in a security sensiti...Docker, Inc. This document summarizes Udo Seidel's presentation on Docker and PCI compliance at Amadeus. It discusses how Amadeus implemented Docker while meeting PCI requirements for security, access controls, logging, and more. Some key lessons included reusing existing security tools, having a dedicated security architect role, and emphasizing communication between security, operations and development teams. Docker provided benefits like abstraction, ease of use and mobility while allowing Amadeus to port more applications over time in compliance with PCI standards.
Container Security: How We Got Here and Where We're Going



Container Security: How We Got Here and Where We're GoingPhil Estes A talk given on Wednesday, Nov. 16th at DefragCon (DefragX) on a historical perspective on container security with a look to where we're going in the future.
Docker Container Security



Docker Container SecuritySuraj Khetani This presentation covers the basics of dockers, its security related features and how certain misconfigurations can be used to escape from container to host
Rooting Out Root: User namespaces in Docker



Rooting Out Root: User namespaces in DockerPhil Estes This talk on the progress to bring user namespace support into Docker was presented by Phil Estes at LinuxCon/ContainerCon 2015 on Wednesday, Aug. 19th, 2015
runC: The little engine that could (run Docker containers) by Docker Captain ...



runC: The little engine that could (run Docker containers) by Docker Captain ...Docker, Inc. With the announcement of the OCI by Solomon Hykes at last summer's DockerCon, a Docker-contributed reference implementation of the OCI spec, called runC, was born. While some of you may have tried runC or have a history of poking at the OS layer integration library to Linux namespaces, cgroups and the like (known as libcontainer), many of you may not know what runC offers. In this talk Phil Estes, Docker engine maintainer who has also contributed to libcontainer and runC, will show what's possible using runC as a lightweight and fast runtime environment to experiment with lower-level features of the container runtime. Phil will introduce a conversion tool called "riddler", which can inspect and convert container configurations from Docker into the proper OCI configuration bundle for easy conversion between the two environments. He'll also demonstrate how to make custom configurations for trying out security features like user namespaces and seccomp profiles.
Devops in Networking



Devops in NetworkingSreenivas Makam This document discusses DevOps in networking and provides examples of using Python libraries and Ansible to programmatically configure and monitor network devices. It describes motivations for DevOps in networking like SDN technologies, availability of network automation tools, and cloud networking. Use cases presented include configuration of L2/L3 protocols and services and network monitoring. The document also discusses network APIs, models like YANG, and tools like Ansible, Python, and protocol standards. An example demonstrates using the PyEAPI Python library to read and create VLANs on an Arista switch and using Ansible to get LLDP neighbors from a Cisco device.
Open Source Tools for Container Security and Compliance @Docker LA Meetup 2/13



Open Source Tools for Container Security and Compliance @Docker LA Meetup 2/13Zach Hill This document discusses open-source tools for security and compliance using Docker containers. It introduces Anchore, an open-source tool that allows deep inspection of container images to check for compliance with policies. Anchore performs image scanning, analyzes operating system packages and artifacts, checks for secrets or source code, and validates Dockerfiles. It generates reports on findings and can integrate with DevOps pipelines using plug-ins for notifications and policy enforcement. Anchore is open-source, extensible, and provides both a web interface and command line tools.
Networking Overview for Docker Platform



Networking Overview for Docker PlatformAditya Patawari This document provides an overview of networking in the Docker platform. It discusses the default Docker networks of none, host and bridge. It also covers user-defined networks like bridge and overlay networks. The key challenges with applications are that they are multi-tiered, dependent on other applications and third party APIs, with components residing across different containers. Docker networking aims to address these challenges.
Ten layers of container security for CloudCamp Nov 2017



Ten layers of container security for CloudCamp Nov 2017Gordon Haff This presentation describes the multiple layers at which container security should be thought about and implemented.
Docker London: Container Security



Docker London: Container SecurityPhil Estes This document summarizes a presentation on container security given by Phil Estes. It identifies several threat vectors for containers including risks from individual containers, interactions between containers, external attacks, and application security issues. It then outlines various security tools and features in Docker like cgroups, Linux Security Modules, capabilities, seccomp, and user namespaces that can help mitigate these threats. Finally, it discusses some future directions for improving container security through more secure defaults, image signing, and network security enhancements.
Docker Mentorweek beginner workshop notes



Docker Mentorweek beginner workshop notesSreenivas Makam This document summarizes a Docker mentor workshop presentation about using Docker. It introduces the presenter and their experience with Docker. It then covers choosing Docker hosts on different operating systems, accessing Azure and Docker Hub accounts, notes on using Azure with Docker, and outlines for three hands-on labs covering basic Docker usage on Linux and Windows, and operations with Docker Swarm mode and a multi-container application.
SS Introduction to Docker



SS Introduction to DockerStephane Woillez Docker provides a platform for building, shipping, and running distributed applications across environments using containers. It allows developers to quickly develop, deploy and scale applications. Docker DataCenter delivers Docker capabilities as a service and provides a unified control plane for both developers and IT operations to standardize, secure and manage containerized applications. It enables organizations to adopt modern practices like microservices, continuous integration/deployment and hybrid cloud through portable containers.
DockerCon SF 2015: Docker Security



DockerCon SF 2015: Docker SecurityDocker, Inc. Least - Privilege Microservices; slides from Diogo Mónica and Nathan McCauley's Docker Security Talk at DockerCon SF 2015.
Docker Security workshop slides



Docker Security workshop slidesDocker, Inc. Get hands-on with security features and best practices to protect your containerized services. Learn to push and verify signed images with Docker Content Trust, and collaborate with delegation roles. Intermediate to advanced level Docker experience recommended, participants will be building and pushing with Docker during the workshop.
Led By Docker Security Experts:
Riyaz Faizullabhoy
David Lawrence
Viktor Stanchev
Experience Level: Intermediate to advanced level Docker experience recommended
Drupal workshop ist 2014



Drupal workshop ist 2014Ricardo Amaro 1) O documento apresenta um workshop sobre Drupal realizado pela Drupal Portugal em 28 de Abril de 2014.
2) É introduzido o que é Drupal, como funciona a comunidade Drupal Portugal e como utilizar e customizar sites com Drupal.
3) O workshop inclui demonstrações práticas de como criar e gerir conteúdo, utilizadores, módulos e traduções em Drupal.
Ad
More Related Content
What's hot (20)
Docker Container Security - A Network View



Docker Container Security - A Network ViewNeuVector A Network View of Docker - You Can't Secure What You Can't See.
Learn critical networking issues and advice for run-time container security
To watch the recorded webinar go to http://neuvector.com/docker-security-webinar
What you will learn in this technical overview:
- Top concerns for deploying containers in production
- Fundamentals of Docker container security
- A sample container exploit using the recently discovered Dirty COW vulnerability
- East-west traffic network issues on AWS and other clouds
- How NACLs, Sec Groups, and flow logs work or don't work with overlay networks
- Visualization and monitoring of containers during run-time.
- Microsegmentation of applications to isolate and protect them.
Docker Security Paradigm



Docker Security ParadigmAnis LARGUEM This document discusses security mechanisms in Docker containers, including control groups (cgroups) to limit resources, namespaces to isolate processes, and capabilities to restrict privileges. It covers secure computing modes like seccomp that sandbox system calls. Linux security modules like AppArmor and SELinux are also mentioned, along with best practices for the Docker daemon and container security overall.
How Secure Is Your Container? ContainerCon Berlin 2016



How Secure Is Your Container? ContainerCon Berlin 2016Phil Estes A conference talk at ContainerCon Europe in Berlin, Germany, given on October 5th, 2016. This is a slightly modified version of my talk first used at Docker London in July 2016.
Veer's Container Security



Veer's Container SecurityJim Barlow Container security involves securing containers at both the host and application level. At the host level, Linux technologies like namespaces, cgroups, SELinux, and seccomp provide isolation between containers. Container images are also scanned for vulnerabilities. The OpenShift platform provides additional security features like role-based access control, network policies, encrypted communications, and controls over privileged containers and storage. Application security best practices within containers include using HTTPS, securing secrets, and API management tools.
Docker Security - Continuous Container Security



Docker Security - Continuous Container SecurityDieter Reuter This document discusses Docker container security. It begins by outlining common container threats like ransomware, DDoS attacks, and privilege escalations. It then describes the need for continuous container security across the development, deployment and runtime phases. This includes techniques like image signing, user access controls, code analysis, image scanning, and host/kernel hardening. The document also discusses inspecting and protecting container network traffic and hosts from attacks. It emphasizes the challenges of monitoring large, complex deployments and automating security at scale across orchestration platforms and network overlays. Several demos are proposed to showcase micro-segmentation of applications and runtime vulnerability scanning using NeuVector.
Docker security introduction-task-2016



Docker security introduction-task-2016Ricardo Gerardi This document discusses Docker security. It begins by introducing Docker and containers, then covers securing Docker images through signing and scanning. It discusses how Docker uses namespaces and cgroups for isolation. It also addresses securing the Docker daemon and containers, as well as operational concerns around deployment, networking, monitoring, and logging of containers. It concludes by looking at future directions like unikernels and serverless architectures.
Docker: Aspects of Container Isolation



Docker: Aspects of Container Isolationallingeek Presentation on the Linux namespaces and system calls used to provide container isolation with Docker. Presented in March 2015 at http://www.meetup.com/Docker-Phoenix/ in Tempe, Arizona.
DockerCon EU 2015: Docker and PCI-DSS - Lessons learned in a security sensiti...



DockerCon EU 2015: Docker and PCI-DSS - Lessons learned in a security sensiti...Docker, Inc. This document summarizes Udo Seidel's presentation on Docker and PCI compliance at Amadeus. It discusses how Amadeus implemented Docker while meeting PCI requirements for security, access controls, logging, and more. Some key lessons included reusing existing security tools, having a dedicated security architect role, and emphasizing communication between security, operations and development teams. Docker provided benefits like abstraction, ease of use and mobility while allowing Amadeus to port more applications over time in compliance with PCI standards.
Container Security: How We Got Here and Where We're Going



Container Security: How We Got Here and Where We're GoingPhil Estes A talk given on Wednesday, Nov. 16th at DefragCon (DefragX) on a historical perspective on container security with a look to where we're going in the future.
Docker Container Security



Docker Container SecuritySuraj Khetani This presentation covers the basics of dockers, its security related features and how certain misconfigurations can be used to escape from container to host
Rooting Out Root: User namespaces in Docker



Rooting Out Root: User namespaces in DockerPhil Estes This talk on the progress to bring user namespace support into Docker was presented by Phil Estes at LinuxCon/ContainerCon 2015 on Wednesday, Aug. 19th, 2015
runC: The little engine that could (run Docker containers) by Docker Captain ...



runC: The little engine that could (run Docker containers) by Docker Captain ...Docker, Inc. With the announcement of the OCI by Solomon Hykes at last summer's DockerCon, a Docker-contributed reference implementation of the OCI spec, called runC, was born. While some of you may have tried runC or have a history of poking at the OS layer integration library to Linux namespaces, cgroups and the like (known as libcontainer), many of you may not know what runC offers. In this talk Phil Estes, Docker engine maintainer who has also contributed to libcontainer and runC, will show what's possible using runC as a lightweight and fast runtime environment to experiment with lower-level features of the container runtime. Phil will introduce a conversion tool called "riddler", which can inspect and convert container configurations from Docker into the proper OCI configuration bundle for easy conversion between the two environments. He'll also demonstrate how to make custom configurations for trying out security features like user namespaces and seccomp profiles.
Devops in Networking



Devops in NetworkingSreenivas Makam This document discusses DevOps in networking and provides examples of using Python libraries and Ansible to programmatically configure and monitor network devices. It describes motivations for DevOps in networking like SDN technologies, availability of network automation tools, and cloud networking. Use cases presented include configuration of L2/L3 protocols and services and network monitoring. The document also discusses network APIs, models like YANG, and tools like Ansible, Python, and protocol standards. An example demonstrates using the PyEAPI Python library to read and create VLANs on an Arista switch and using Ansible to get LLDP neighbors from a Cisco device.
Open Source Tools for Container Security and Compliance @Docker LA Meetup 2/13



Open Source Tools for Container Security and Compliance @Docker LA Meetup 2/13Zach Hill This document discusses open-source tools for security and compliance using Docker containers. It introduces Anchore, an open-source tool that allows deep inspection of container images to check for compliance with policies. Anchore performs image scanning, analyzes operating system packages and artifacts, checks for secrets or source code, and validates Dockerfiles. It generates reports on findings and can integrate with DevOps pipelines using plug-ins for notifications and policy enforcement. Anchore is open-source, extensible, and provides both a web interface and command line tools.
Networking Overview for Docker Platform



Networking Overview for Docker PlatformAditya Patawari This document provides an overview of networking in the Docker platform. It discusses the default Docker networks of none, host and bridge. It also covers user-defined networks like bridge and overlay networks. The key challenges with applications are that they are multi-tiered, dependent on other applications and third party APIs, with components residing across different containers. Docker networking aims to address these challenges.
Ten layers of container security for CloudCamp Nov 2017



Ten layers of container security for CloudCamp Nov 2017Gordon Haff This presentation describes the multiple layers at which container security should be thought about and implemented.
Docker London: Container Security



Docker London: Container SecurityPhil Estes This document summarizes a presentation on container security given by Phil Estes. It identifies several threat vectors for containers including risks from individual containers, interactions between containers, external attacks, and application security issues. It then outlines various security tools and features in Docker like cgroups, Linux Security Modules, capabilities, seccomp, and user namespaces that can help mitigate these threats. Finally, it discusses some future directions for improving container security through more secure defaults, image signing, and network security enhancements.
Docker Mentorweek beginner workshop notes



Docker Mentorweek beginner workshop notesSreenivas Makam This document summarizes a Docker mentor workshop presentation about using Docker. It introduces the presenter and their experience with Docker. It then covers choosing Docker hosts on different operating systems, accessing Azure and Docker Hub accounts, notes on using Azure with Docker, and outlines for three hands-on labs covering basic Docker usage on Linux and Windows, and operations with Docker Swarm mode and a multi-container application.
SS Introduction to Docker



SS Introduction to DockerStephane Woillez Docker provides a platform for building, shipping, and running distributed applications across environments using containers. It allows developers to quickly develop, deploy and scale applications. Docker DataCenter delivers Docker capabilities as a service and provides a unified control plane for both developers and IT operations to standardize, secure and manage containerized applications. It enables organizations to adopt modern practices like microservices, continuous integration/deployment and hybrid cloud through portable containers.
DockerCon SF 2015: Docker Security



DockerCon SF 2015: Docker SecurityDocker, Inc. Least - Privilege Microservices; slides from Diogo Mónica and Nathan McCauley's Docker Security Talk at DockerCon SF 2015.
Viewers also liked (20)
Docker Security workshop slides



Docker Security workshop slidesDocker, Inc. Get hands-on with security features and best practices to protect your containerized services. Learn to push and verify signed images with Docker Content Trust, and collaborate with delegation roles. Intermediate to advanced level Docker experience recommended, participants will be building and pushing with Docker during the workshop.
Led By Docker Security Experts:
Riyaz Faizullabhoy
David Lawrence
Viktor Stanchev
Experience Level: Intermediate to advanced level Docker experience recommended
Drupal workshop ist 2014



Drupal workshop ist 2014Ricardo Amaro 1) O documento apresenta um workshop sobre Drupal realizado pela Drupal Portugal em 28 de Abril de 2014.
2) É introduzido o que é Drupal, como funciona a comunidade Drupal Portugal e como utilizar e customizar sites com Drupal.
3) O workshop inclui demonstrações práticas de como criar e gerir conteúdo, utilizadores, módulos e traduções em Drupal.
Docker containers & the Future of Drupal testing 



Docker containers & the Future of Drupal testing Ricardo Amaro Story of an investigation to improve cloud
The sad VirtualMachine story
Containers and non-containers
DEMO - Drupal Docker
Drupal Testbots story in a Glance
Docker as a testing automation factor
DEMO - Docker Tesbot
Integration path
Microservice architecture



Microservice architectureSlim Ouertani Microservice architecture breaks applications into small, independent services that communicate over well-defined interfaces. This document discusses key characteristics of microservices including componentization via services, decentralized governance and data management, and infrastructure automation. It also compares monoliths to microservices and covers some common pros and cons like increased operations overhead but also more evolutionary design.
How To Train Your APIs



How To Train Your APIsAshley Roach Originally presented at API Strat and Practice conference in Boston 2016 by me and Mandy Whaley, this presentation shows the multiple archetypes that you could encounter while trying to govern APIs at your company.
Building a REST API Microservice for the DevNet API Scavenger Hunt



Building a REST API Microservice for the DevNet API Scavenger HuntAshley Roach Building a REST API Microservice for the DevNet API Scavenger Hunt. Originally presented at QConSF 2016
Introduction to Infrastructure as Code & Automation / Introduction to Chef



Introduction to Infrastructure as Code & Automation / Introduction to ChefNathen Harvey The document provides an introduction to infrastructure as code using Chef. It begins with an introduction by Nathen Harvey and outlines the sys admin journey from manually managing servers to using automation and policy-driven configuration management. It then discusses how infrastructure as code with Chef allows treating infrastructure like code by programmatically provisioning and configuring components. The document demonstrates configuring resources like packages, services, files and more using Chef.
Drupalcamp es 2013 drupal with lxc docker and vagrant 



Drupalcamp es 2013 drupal with lxc docker and vagrant Ricardo Amaro This document discusses using containers like LXC and Docker to automate Drupal deployments. It begins with an introduction to the speaker and overview of virtual machines versus containers. The speaker then demonstrates using LXC containers on Ubuntu with tools like Vagrant and Puppet for configuration management. Docker is presented as an improvement allowing developers to package applications and dependencies into portable containers that can be run anywhere without reconfiguration.
DOXLON November 2016 - Data Democratization Using Splunk



DOXLON November 2016 - Data Democratization Using SplunkOutlyer This document discusses data democratization using Splunk. It describes how Splunk can be used to provide universal access to data through delegated access models, standardized data models, and automation. Key points include:
1. Splunk can implement a delegated access model using apps, indexes, and user roles to securely share sensitive data.
2. Standardized data models and semantic logging help combat knowledge fragmentation and enable consistent analysis.
3. Automating data onboarding and validation helps improve adoption by reducing backlogs and ensuring data quality.
Priming Your Teams For Microservice Deployment to the Cloud



Priming Your Teams For Microservice Deployment to the CloudMatt Callanan You think of a great idea for a microservice and want to ship it to production as quickly as possible. Of course you'll need to create a Git repo with a codebase that reuses libraries you share with other services. And you'll want a build and a basic test suite. You'll want to deploy it to immutable servers using infrastructure as code that dev and ops can maintain. Centralised logging, monitoring, and HipChat notifications would also be great. Of course you'll want a load balancer and a CNAME that your other microservices can hit. You'd love to have blue-green deploys and the ability to deploy updates at any time through a Continuous Delivery pipeline. Phew! How long will it take to set all this up? A couple of days? A week? A month?
What if you could do all of this within 30 minutes? And with a click of a button soon be receiving production traffic?
Matt introduces "Primer", Expedia's microservice generation and deployment platform that enables rapid experimentation in the cloud, how it's caused unprecedented rates of learning, and explain tips and tricks on how to build one yourself with practical takeaways for everyone from the startup to the enterprise.
Video: https://www.youtube.com/watch?v=Xy4EkaXyEs4
Meetup: http://www.meetup.com/Devops-Brisbane/events/225050723/
DATA CENTER 



DATA CENTER Shekar Reddy This document provides an overview of data centers, including what they are, their components, benefits, and classifications. A data center houses servers and networking equipment to provide services like email, data storage, and web hosting. It discusses components like cooling, UPS, PDU, and backup power needed to support IT equipment. Data centers are classified based on their redundancy and availability, with tier 1 being the least redundant and tier 4 being the most fault tolerant.
S.R.E - create ultra-scalable and highly reliable systems



S.R.E - create ultra-scalable and highly reliable systemsRicardo Amaro Site Reliability Engineering enables agility and stability.
SREs use Software Engineering to automate themselves out of the Job.
My advice, if you want to implement this change in your company is to start with action items, alter your training and hiring, implement error budgets, do blameless postmortems and reduce toil.
https://events.drupal.org/dublin2016/sessions/sre-create-ultra-scalable-and-highly-reliable-systems
Drupal workshop fcul_2014



Drupal workshop fcul_2014Ricardo Amaro Este documento fornece uma introdução ao sistema de gestão de conteúdo Drupal. Apresenta os principais conceitos como nós, tipos de conteúdo, módulos, temas e como personalizar o site. Inclui também exemplos de sites construídos com Drupal e detalhes sobre a comunidade Drupal Portugal.
Docker Security



Docker SecurityBladE0341 Clair is a container vulnerability analysis service that scans container layers to detect known vulnerabilities without executing the container. It provides a list of vulnerabilities that threaten each container. The analyze-local-images tool allows analyzing local Docker images with Clair by copying an image ID. Logging multiple Docker containers can be automated by sending their logs to Logstash for indexing in Elasticsearch with a Kibana frontend, monitored alongside metrics from Cadvisor. SELinux applies Mandatory Access Control to Docker containers using the svirt_lxc_net_t type to improve security. It isolates processes but allows reading from most host labels.
Docker and Cloud - Enables for DevOps - by ACA-IT



Docker and Cloud - Enables for DevOps - by ACA-ITStijn Wijndaele DevOps is gericht op het tot stand brengen van een cultuur binnen organisaties waardoor het ontwikkelen, valideren en releasen van software sneller, meer betrouwbaar en frequenter kan verlopen. Om dit te realiseren staan het automatiseren van het 'software delivery process' en de bijhorende infrastructurele veranderingen centraal. Door de opkomst van 'Microservice Architecture' neemt het belang hiervan nog verder toe.
The free software history and communities’ journey ahead



The free software history and communities’ journey aheadRicardo Amaro "The reason why open source happened, the reason it started, was because the people who make software are artists and craftsmen. They are not just mindless drones, that show up every day and put in their hours. They spend their evenings, their weekends, unbelievable amounts of time crafting this software. And they wanna see it used by the most people, and they wanna see it used for the best purposes, typically, and they didn’t see that happening in the proprietary software world, not any of the proprietary software companies. And so they decided – because they could – to write their own world!"
Danese Cooper
DevOps meetup 16oct docker and jenkins



DevOps meetup 16oct docker and jenkinsBenoit Wilcox The document summarizes a DevOps meetup discussing Docker. It describes Docker as a tool to build, ship and run applications anywhere using containers. It outlines Docker's advantages like standardized environments and microservices approach. It also discusses how the speakers use Docker in their development and deployment processes, having developers build Docker images which are deployed through a continuous delivery pipeline to various environments.
Docker (compose) in devops - prague docker meetup



Docker (compose) in devops - prague docker meetupJuraj Kojdjak Presentation from Prague Docker meetup on 3/24/15.
Code attached to this presentation https://github.com/supowski/docker-compose-in-devops
Dockercon Europe 2014 - Continuous Delivery leveraging on Docker CaaS



Dockercon Europe 2014 - Continuous Delivery leveraging on Docker CaaSAdrien Blind This presentation focuses on a Docker usecase : the Container as a Service, which makes sense for companies.
Amplifying Docker - Alex Heneveld




Amplifying Docker - Alex Heneveld
Outlyer In this talk we look at the challenges of taking docker and using it as the basis for a cloud platform. We highlight the work done by one of our own Cloudsoft engineers Andrea Turli who has contributed an Apache jclouds provider for Docker and integrated this with the open source project Brooklyn.
Andrea has written about this in a recent blog post AMP for Docker and so using this as a starting point we show how we are building on this to create a lightweight dynamic Docker cloud and compare and contrast this with work we are doing with our latest partner Waratek to help them create a similar lightweight dynamic Java cloud using their Java application container technology.
Ad
Similar to Docker security: Rolling out Trust in your container (20)
Hack the whale



Hack the whaleMarco Ferrigno The document provides an overview of containers and Docker. It discusses why containers are important for organizing software, improving portability, and protecting infrastructure. It describes key Docker concepts like images, containers, Dockerfile for building images, and tools like Docker Compose and Docker Swarm for defining and running multi-container apps. The document recommends reading "The Art of War" and scanning systems without being detected before potentially more intrusive activities. It also briefly introduces network security pillars and buffer overflows as an attack technique.
Dockers & kubernetes detailed - Beginners to Geek



Dockers & kubernetes detailed - Beginners to GeekwiTTyMinds1 Docker is a platform for building, distributing and running containerized applications. It allows applications to be bundled with their dependencies and run in isolated containers that share the same operating system kernel. Kubernetes is an open-source system for automating deployment, scaling, and management of containerized applications. It groups Docker containers that make up an application into logical units for easy management and discovery. Docker Swarm is a native clustering tool that can orchestrate and schedule containers on machine clusters. It allows Docker containers to run as a cluster on multiple Docker hosts.
SW Docker Security



SW Docker SecurityStephane Woillez Docker provides security for containerized applications using Linux kernel features like namespaces and cgroups to isolate processes and limit resource usage. The Docker daemon manages these Linux security mechanisms to build secure containers. Docker images can also be scanned for vulnerabilities and signed with content trust to ensure only approved container images are deployed in production.
Hands on introduction to docker security for docker newbies



Hands on introduction to docker security for docker newbiesYigal Elefant Introducing Docker and demonstrating hands-on some of the security issues related to Docker. This presentation accompanied the demonstrations.
Testing Docker Images Security -All day dev ops 2017



Testing Docker Images Security -All day dev ops 2017Jose Manuel Ortega Candel Docker containers provide isolation and security by default through mechanisms like namespaces, cgroups, capabilities. Auditing tools check for vulnerabilities and configuration best practices to harden Docker hosts and images. Images should be signed, dependencies pinned, and a least privilege model used to minimize attack surface.
Docker



DockerNeeraj Wadhwa Containers allow multiple isolated user space instances to run on a single host operating system. Containers are seen as less flexible than virtual machines since they generally can only run the same operating system as the host. Docker adds an application deployment engine on top of a container execution environment. Docker aims to provide a lightweight way to model applications and a fast development lifecycle by reducing the time between code writing and deployment. Docker has components like the client/server, images used to create containers, and public/private registries for storing images.
Weave User Group Talk - DockerCon 2017 Recap



Weave User Group Talk - DockerCon 2017 RecapPatrick Chanezon Docker moves very fast, with an edge channel released every month and a stable release every 3 months. Patrick will talk about how Docker introduced Docker EE and a certification program for containers and plugins with Docker CE and EE 17.03 (from March), the announcements from DockerCon (April), and the many new features planned for Docker CE 17.05 in May.
This talk will be about what's new in Docker and what's next on the roadmap
Accelerate your development with Docker



Accelerate your development with DockerAndrey Hristov This document provides an overview of Docker and containers. It begins with a brief introduction to 12 Factor Applications methodology and then defines what Docker is, explaining that containers utilize Linux namespaces and cgroups to isolate processes. It describes the Docker software and ecosystem, including images, registries, Docker CLI, Docker Compose, building images with Dockerfile, and orchestrating with tools like Kubernetes. It concludes with a live demo and links to additional resources.
Accelerate your software development with Docker



Accelerate your software development with DockerAndrey Hristov Docker is in all the news and this talk presents you the technology and shows you how to leverage it to build your applications according to the 12 factor application model.
Testing Docker Images Security



Testing Docker Images SecurityJose Manuel Ortega Candel This document discusses tools and best practices for auditing Docker images for security. It begins with an introduction to Docker security concepts like namespaces, cgroups, and capabilities. It then discusses tools like Docker Security Scanning, Clair, Docker Bench Security, and Lynis that can be used to audit images. The document provides checklists for building secure Dockerfiles and consuming images. It concludes with recommendations around signing images, pinning dependencies, and using content trust and least privilege configurations.
Docker Ecosystem on Azure



Docker Ecosystem on AzurePatrick Chanezon This document discusses containerization and the Docker ecosystem. It provides a brief history of containerization technologies and an overview of Docker components like Docker Engine, Docker Hub, and Docker Inc. It also discusses developing with Docker through concepts like Dockerfiles, images, and Fig for running multi-container apps. More advanced topics covered include linking containers, volumes, Docker Machine for provisioning, and clustering with Swarm and Kubernetes.
"Docker best practice", Станислав Коленкин (senior devops, DataArt)



"Docker best practice", Станислав Коленкин (senior devops, DataArt)DataArt This document provides best practices for using Docker containers, including:
- Using "dumb-init" or "supervisord" to run multiple services in a container.
- Using named volumes over host volumes whenever possible as named volumes can be directly controlled and backed up easily.
- Writing useful entrypoint scripts to address startup issues when linking containers.
- Avoiding using the root user when possible for security.
- Techniques for reducing Docker image sizes such as using smaller base images, removing cache files and temporary packages, and combining Dockerfile commands.
The document also discusses Docker security topics like authenticating images, dropping unnecessary privileges, limiting resource consumption, and reducing large attack surfaces
Docker basics



Docker basicsClaudio Montoya This document provides an overview of Docker basics including requirements, software, architecture, and concepts. It discusses traditional servers, virtual machines, and containers. Key advantages and disadvantages of each approach are listed. Docker concepts like images, containers, layers, Dockerfile, registry, and hub are defined. Common Docker commands are also outlined.
Introduction to docker security



Introduction to docker securityWalid Ashraf This document provides an overview of Docker security. It discusses how Docker isolates containers using kernel namespaces and cgroups to limit access to resources. It describes how Docker secures communication with its daemon and stores images cryptographically. It also explains how Linux capabilities and features like AppArmor and Seccomp can restrict container access further.
Docker 101 Checonf 2016



Docker 101 Checonf 2016Patrick Chanezon This document discusses Docker and how it powers the Eclipse Che IDE platform. It provides an overview of Docker concepts like containers, images, and orchestration. It also demonstrates how to build a sample Spring Boot app as a Docker image and run it as a container. Finally, it outlines the agenda for the CheConf2016 conference, including sessions on deploying Che on OpenShift and building an IoT IDE with Che.
Practical Container Security by Mrunal Patel and Thomas Cameron, Red Hat



Practical Container Security by Mrunal Patel and Thomas Cameron, Red HatDocker, Inc. You can secure your containerized microservices without slowing down development. Through a combination of Linux kernel features and open source tools, you can isolate the host from the container and the containers from each other, as well as finding vulnerabilities and securing data. Two of Red Hat's Docker contributors will discuss the state of container security today, covering Linux namespaces, SElinux, cgroups, capabilities, scan, seccomp, and other tools you can use right now.
containers and virtualization tools ( Docker )



containers and virtualization tools ( Docker )Imo Inyang This document provides an overview of containers and virtualization tools like Docker. It defines key concepts like virtual machines (VMs), hypervisors, and containers. It explains that VMs emulate real hardware while containers abstract the operating system to increase efficiency. Docker is introduced as an open-source container platform that builds on Linux features for speed and modularity. Instructions are provided on installing Docker and using common Docker commands to build, run, and manage containerized applications.
Containerization using docker and its applications



Containerization using docker and its applicationsPuneet Kumar Bhatia (MBA, ITIL V3 Certified) This document discusses Docker, containers, and how Docker addresses challenges with complex application deployment. It provides examples of how Docker has helped companies reduce deployment times and improve infrastructure utilization. Key points covered include:
- Docker provides a platform to build, ship and run distributed applications using containers.
- Containers allow for decoupled services, fast iterative development, and scaling applications across multiple environments like development, testing, and production.
- Docker addresses the complexity of deploying applications with different dependencies and targets by using a standardized "container system" analogous to intermodal shipping containers.
- Companies using Docker have seen benefits like reducing deployment times from 9 months to 15 minutes and improving infrastructure utilization.
Containerization using docker and its applications



Containerization using docker and its applicationsPuneet Kumar Bhatia (MBA, ITIL V3 Certified) This document discusses Docker, containers, and containerization. It begins by explaining why containers and Docker have become popular, noting that modern applications are increasingly decoupled services that require fast, iterative development and deployment to multiple environments. It then discusses how deployment has become complex with diverse stacks, frameworks, databases and targets. Docker addresses this problem by providing a standardized way to package applications into containers that are portable and can run anywhere. The document provides examples of results organizations have seen from using Docker, such as significantly reduced deployment times and increased infrastructure efficiency. It also covers Docker concepts like images, containers, the Dockerfile and Docker Compose.
Tech talk on docker with demo



Tech talk on docker with demoSandeep Karnawat This presentation was given at ThoughtWorks pune during meetup. It describes about Docker, Docker general commands and underhood of it.
Ad
Recently uploaded (20)
Value Stream Mapping Worskshops for Intelligent Continuous Security



Value Stream Mapping Worskshops for Intelligent Continuous SecurityMarc Hornbeek This presentation provides detailed guidance and tools for conducting Current State and Future State Value Stream Mapping workshops for Intelligent Continuous Security.
The Gaussian Process Modeling Module in UQLab



The Gaussian Process Modeling Module in UQLabJournal of Soft Computing in Civil Engineering We introduce the Gaussian process (GP) modeling module developed within the UQLab software framework. The novel design of the GP-module aims at providing seamless integration of GP modeling into any uncertainty quantification workflow, as well as a standalone surrogate modeling tool. We first briefly present the key mathematical tools on the basis of GP modeling (a.k.a. Kriging), as well as the associated theoretical and computational framework. We then provide an extensive overview of the available features of the software and demonstrate its flexibility and user-friendliness. Finally, we showcase the usage and the performance of the software on several applications borrowed from different fields of engineering. These include a basic surrogate of a well-known analytical benchmark function; a hierarchical Kriging example applied to wind turbine aero-servo-elastic simulations and a more complex geotechnical example that requires a non-stationary, user-defined correlation function. The GP-module, like the rest of the scientific code that is shipped with UQLab, is open source (BSD license).
Structural Response of Reinforced Self-Compacting Concrete Deep Beam Using Fi...



Structural Response of Reinforced Self-Compacting Concrete Deep Beam Using Fi...Journal of Soft Computing in Civil Engineering Analysis of reinforced concrete deep beam is based on simplified approximate method due to the complexity of the exact analysis. The complexity is due to a number of parameters affecting its response. To evaluate some of this parameters, finite element study of the structural behavior of the reinforced self-compacting concrete deep beam was carried out using Abaqus finite element modeling tool. The model was validated against experimental data from the literature. The parametric effects of varied concrete compressive strength, vertical web reinforcement ratio and horizontal web reinforcement ratio on the beam were tested on eight (8) different specimens under four points loads. The results of the validation work showed good agreement with the experimental studies. The parametric study revealed that the concrete compressive strength most significantly influenced the specimens’ response with the average of 41.1% and 49 % increment in the diagonal cracking and ultimate load respectively due to doubling of concrete compressive strength. Although the increase in horizontal web reinforcement ratio from 0.31 % to 0.63 % lead to average of 6.24 % increment on the diagonal cracking load, it does not influence the ultimate strength and the load-deflection response of the beams. Similar variation in vertical web reinforcement ratio leads to an average of 2.4 % and 15 % increment in cracking and ultimate load respectively with no appreciable effect on the load-deflection response.
ADVXAI IN MALWARE ANALYSIS FRAMEWORK: BALANCING EXPLAINABILITY WITH SECURITY



ADVXAI IN MALWARE ANALYSIS FRAMEWORK: BALANCING EXPLAINABILITY WITH SECURITYijscai With the increased use of Artificial Intelligence (AI) in malware analysis there is also an increased need to
understand the decisions models make when identifying malicious artifacts. Explainable AI (XAI) becomes
the answer to interpreting the decision-making process that AI malware analysis models use to determine
malicious benign samples to gain trust that in a production environment, the system is able to catch
malware. With any cyber innovation brings a new set of challenges and literature soon came out about XAI
as a new attack vector. Adversarial XAI (AdvXAI) is a relatively new concept but with AI applications in
many sectors, it is crucial to quickly respond to the attack surface that it creates. This paper seeks to
conceptualize a theoretical framework focused on addressing AdvXAI in malware analysis in an effort to
balance explainability with security. Following this framework, designing a machine with an AI malware
detection and analysis model will ensure that it can effectively analyze malware, explain how it came to its
decision, and be built securely to avoid adversarial attacks and manipulations. The framework focuses on
choosing malware datasets to train the model, choosing the AI model, choosing an XAI technique,
implementing AdvXAI defensive measures, and continually evaluating the model. This framework will
significantly contribute to automated malware detection and XAI efforts allowing for secure systems that
are resilient to adversarial attacks.
Fort night presentation new0903 pdf.pdf.



Fort night presentation new0903 pdf.pdf.anuragmk56 This is the document of fortnight review progress meeting
Artificial Intelligence (AI) basics.pptx



Artificial Intelligence (AI) basics.pptxaditichinar its all about Artificial Intelligence(Ai) and Machine Learning and not on advanced level you can study before the exam or can check for some information on Ai for project
Data Structures_Introduction to algorithms.pptx



Data Structures_Introduction to algorithms.pptxRushaliDeshmukh2 Concept of Problem Solving, Introduction to Algorithms, Characteristics of Algorithms, Introduction to Data Structure, Data Structure Classification (Linear and Non-linear, Static and Dynamic, Persistent and Ephemeral data structures), Time complexity and Space complexity, Asymptotic Notation - The Big-O, Omega and Theta notation, Algorithmic upper bounds, lower bounds, Best, Worst and Average case analysis of an Algorithm, Abstract Data Types (ADT)
Raish Khanji GTU 8th sem Internship Report.pdf



Raish Khanji GTU 8th sem Internship Report.pdfRaishKhanji This report details the practical experiences gained during an internship at Indo German Tool
Room, Ahmedabad. The internship provided hands-on training in various manufacturing technologies, encompassing both conventional and advanced techniques. Significant emphasis was placed on machining processes, including operation and fundamental
understanding of lathe and milling machines. Furthermore, the internship incorporated
modern welding technology, notably through the application of an Augmented Reality (AR)
simulator, offering a safe and effective environment for skill development. Exposure to
industrial automation was achieved through practical exercises in Programmable Logic Controllers (PLCs) using Siemens TIA software and direct operation of industrial robots
utilizing teach pendants. The principles and practical aspects of Computer Numerical Control
(CNC) technology were also explored. Complementing these manufacturing processes, the
internship included extensive application of SolidWorks software for design and modeling tasks. This comprehensive practical training has provided a foundational understanding of
key aspects of modern manufacturing and design, enhancing the technical proficiency and readiness for future engineering endeavors.
International Journal of Distributed and Parallel systems (IJDPS)



International Journal of Distributed and Parallel systems (IJDPS)samueljackson3773 The growth of Internet and other web technologies requires the development of new
algorithms and architectures for parallel and distributed computing. International journal of
Distributed and parallel systems is a bimonthly open access peer-reviewed journal aims to
publish high quality scientific papers arising from original research and development from
the international community in the areas of parallel and distributed systems. IJDPS serves
as a platform for engineers and researchers to present new ideas and system technology,
with an interactive and friendly, but strongly professional atmosphere.
RICS Membership-(The Royal Institution of Chartered Surveyors).pdf



RICS Membership-(The Royal Institution of Chartered Surveyors).pdfMohamedAbdelkader115 Glad to be one of only 14 members inside Kuwait to hold this credential.
Please check the members inside kuwait from this link:
https://www.rics.org/networking/find-a-member.html?firstname=&lastname=&town=&country=Kuwait&member_grade=(AssocRICS)&expert_witness=&accrediation=&page=1
railway wheels, descaling after reheating and before forging



railway wheels, descaling after reheating and before forgingJavad Kadkhodapour railway wheels, descaling after reheating and before forging
Degree_of_Automation.pdf for Instrumentation and industrial specialist



Degree_of_Automation.pdf for Instrumentation and industrial specialistshreyabhosale19 degree of Automation for industrial and Instrumentation learners.
Structural Response of Reinforced Self-Compacting Concrete Deep Beam Using Fi...



Structural Response of Reinforced Self-Compacting Concrete Deep Beam Using Fi...Journal of Soft Computing in Civil Engineering
Docker security: Rolling out Trust in your container
- 1. Ronak Kogta Docker Security Rolling out trust in your container
- 2. Buzz is catching on, and so is technology Neatly packs multiple applications on one operating system Gives you way to compose clusters, manage them and play with them at the scale of 100,000 Docker Docker Docker
- 3. A very secure system which is not user-friendly will not be secure for long. (because people will find a way to go around it) Usable Security is a principle of building security systems while considering human workflows. Speed Efficiency Learnability Memorability User Preference Idea of Usable Security
- 4. Its going to be everywhere Your Desktop, Workstation & Cloud Infrastructure. Your Production, Development & Testing Cycles. It is going to be used by everyone Your team, clients, and partners. Independent developers and teams who are using your images. We should definitely think about #docker-security Docker Space
- 5. How safe is docker isolation ? If some malicious user has docker daemon access, what to do ? Can I use security policies over docker ? SELINUX,APPARMOR,GRSEC Can I really trust docker image I install ? Can i ssh to docker container ? Lets think..
- 6. Every process must be able to access only the information and resources that are necessary for its legitimate purpose - Diogo Mónica, Docker Linux namespaces (isolated view of system.) Cgroups (limit and isolate the resource usage.) Linux Security Modules (Apparmor,SELINUX) Capabilities Per-container ulimit User-namespaces: root inside is not root outside Seccomp: Individual syscall filtering (like chrome sandbox) Enter Least Privilege
- 9. Cgroups, ulimit & User Namespaces Docker root is not real root. (User Namespaces) Docker ulimit With cgroups, you can control on the resource usage of container docker run --lxc-conf=lxc.cgroup.cpuset.cpus = 0,1 ..
- 10. Root has certain capabilities, but we don’t want our container to have all those capabilities Each container can have some of the capabilities of root, but not all. Mounting operations Access to raw sockets (prevent opening privileged ports, spoofing) Some file system operations (mkdev, chown, chattrs) Loading kernel modules Capabilites
- 11. man 7 capabilities Docker by default drops some capabilities sys_admin, sys_time, sys_nice,..... Capabilites docker run –cap-drop=CHOWN ... docker run –cap-add=MKNOD ...
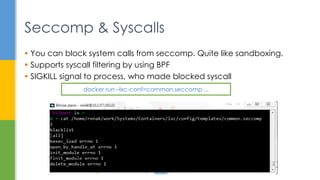
- 12. Seccomp & Syscalls System Calls OS Utilities IP Tables Other User Programs Device Drivers NetFilter Other Kernel Components
- 14. Seccomp & Syscalls You can block system calls from seccomp. Quite like sandboxing. Supports syscall filtering by using BPF SIGKILL signal to process, who made blocked syscall docker run –lxc-conf=common.seccomp ...
- 15. More... Combine Docker with AppArmor/SELinux/TOMOYO Profiles These profiles help you in deciding minimal privilege for each application. Preventing permission escalation and unauthorized information disclosure (or worse). Within the container configuration the related AppArmor profile can be defined with lxc.aa_profile. docker run –security-opt label:type:svirt_apche ...
- 16. GRSEC and PaX Use a hardened Linux kernel for host, with kernel patches. User Mappings Map user/group ids lxc.id_map = u 0 1000000 65536 lxc.id_map = g 0 1000000 65536 Couple it with docker run –lxc-conf= More...
- 17. Can you really trust your images ? Docker Notary
- 18. Trusted Cross Platform content distribution Trusted Client – Server Interaction Publisher signed content Publisher Key validates integrity of content Platform Agnostic to distribute any content https://github.com/docker/notary Docker Notary
- 19. Docker Content Trust Publisher Registry User User User
- 20. Two keys are generated when publisher first pushes image. Tagging Key Exists for each new repository that publisher owns Can be shared with collaborators easily. Offline Key Users see this key as official publisher’s key Important in establishing trust. Only needed when creating new repository or rotating existing repository Publisher’s View
- 21. Once Images are signed, TUF maintains ensures Integrity & Freshness of Content Notion of Timestamp Key Needed to ensure freshness guarantees Generated at remote server. Docker maintains it for you http://theupdateframework.com/ Trust Update Framework
- 22. Lets Attack ?
- 23. Lets Attack ?
- 24. Lets Attack ?
- 25. export DOCKER_CONTENT_TRUST=1 Docker Content Trust
- 26. Security Script that checks for dozens of common best- practices around deploying Docker containers in produtions. https://dockerbench.com DockerBench
- 27. Thanks
- 28. Questions ?? IRC: #docker #docker-security Google Group: Hyderabad Docker Users Join Docker Movement








