Efficient Methodology of Sampling UVM RAL During Simulation for SoC Functional Coverage
1 like1,041 views
Paper presented at Microprocessor/ SoC Test, Security & Verification (MTV 18 ) C onference, Dcemeber 10 , 2018 , Austin, USA © 2018. Paper URL: https://ieeexplore.ieee.org/document/8746049
1 of 33
































Ad
Recommended
Ral by pushpa 



Ral by pushpa Pushpa Yakkala UVM RAL is an object-oriented model for registers inside the design. To access these design registers, UVM RAL provides ready-made base classes and APIs
axi protocol



axi protocolAzad Mishra The AXI protocol specification describes an advanced bus architecture with burst-based transactions using separate address/control and data phases over independent channels. It supports features like out-of-order transaction completion, exclusive access for atomic operations, cache coherency, and a low power interface. The AXI protocol is commonly used in System-on-Chip designs for high performance embedded processors and peripherals.
Axi protocol



Axi protocolRohit Kumar Pathak AXI is an on-chip, point to point communication protocol. It is used as a high-performance bus in various IP or SoC Systems. It is used for connecting high-performance processors with memory.
Ambha axi



Ambha axiHARINATH REDDY Advanced eXtensible Interface (AXI), part of the ARM Advanced Microcontroller Bus Architecture (AMBA3) (AXI3) and 4 (AXI4) specifications.
Axi protocol



Axi protocolAzad Mishra The document discusses Advanced eXtensible Interface (AXI), which is a third generation interface specification that is targeted at high performance systems. AXI uses separate address/control and data phases to improve performance. It supports burst transactions where only the start address is issued and multiple outstanding addresses can be in flight simultaneously. AXI consists of five channels to separate read and write operations. Simulation results showed that AXI provides higher throughput than older AMBA interfaces, though older interfaces may have lower latency in some cases. AXI's standardization and flexibility make it useful for integrating IP cores.
AMBA AHB 5



AMBA AHB 5SUNODH GARLAPATI AMBA AHB is a bus interface suitable for high-performance synthesizable designs. It defines the interface between components, such as masters, interconnects, and slaves.
APB protocol v1.0



APB protocol v1.0Azad Mishra The document describes conventions and signals used in the AMBA 3 APB protocol specification version 1.0. It summarizes write and read transfer procedures, including optional wait states using the PREADY signal. Error responses are also described. The operating states of the APB include IDLE, SETUP, and ACCESS states. PREADY controls exiting the ACCESS state.
UVM TUTORIAL;



UVM TUTORIAL;Azad Mishra The document provides an overview of the UVM configuration database and how it is used to store and access configuration data throughout the verification environment hierarchy. Key points include: the configuration database mirrors the testbench topology; it uses a string-based key system to store and retrieve entries in a hierarchical and scope-controlled manner; and the automatic configuration process retrieves entries during the build phase and configures component fields.
System verilog important



System verilog importantelumalai7 The document discusses the building blocks of a SystemVerilog testbench. It describes the program block, which encapsulates test code and allows reading/writing signals and calling module routines. Interface and clocking blocks are used to connect the testbench to the design under test. Assertions, randomization, and other features help create flexible testbenches to verify design correctness.
System verilog verification building blocks



System verilog verification building blocksNirav Desai SystemVerilog introduces key concepts like program blocks, interfaces, and clocking blocks to help with verification. Program blocks separate the testbench code from the design code to avoid race conditions. Interfaces encapsulate communication between blocks and help prevent errors from manual port connections. Clocking blocks synchronize signal drivers and allow specifying timing for sampled signals. Together these features help manage complexity when verifying designs.
System verilog coverage



System verilog coveragePushpa Yakkala Coverage is a technique used in simulation to measure how much of a design has been tested or verified. There are different types of coverage including functional coverage, which checks which features or functions have been tested, and code coverage, which measures how much of the design code has been exercised. Coverage is measured using coverage tools and reports to identify any remaining gaps or "holes" that need additional testing to fully verify the design.
Advance Peripheral Bus 



Advance Peripheral Bus SIVA NAGENDRA REDDY The Advanced Microcontroller Bus Architecture (AMBA) specification defines interfaces for connecting processor and peripherals. It aims to standardize connections to enable modular system design. The Advanced Peripheral Bus (APB) is defined by AMBA for simple peripherals like timers and I/O. It uses few signals for non-pipelined transfers in two cycles to reduce power and complexity.
Amba axi 29 3_2015



Amba axi 29 3_2015kiemnhatminh The Amba AXI protocol enables high-bandwidth and low-latency interconnect between IP blocks through separate address/control and data channels that support burst-based transactions, out-of-order completion, and register slices for high-frequency operation. It uses two-way handshaking on channels and supports various burst types including incrementing, wrapping, and fixed bursts through start addresses and calculated transfer addresses.
AMBA Ahb 2.0



AMBA Ahb 2.0Akhil Srivastava This document describes the Advanced Microcontroller Bus Architecture (AMBA) Advanced High-performance Bus (AHB) 2.0 specification. It details features of AHB such as burst transfers, split transactions, and single-cycle bus master handover. It also explains typical components in an AMBA AHB system including masters, slaves, arbitration, and bus operation with different transfer types.
SOC Verification using SystemVerilog 



SOC Verification using SystemVerilog Ramdas Mozhikunnath Introduction to SOC Verification Fundamentals and System Verilog language coding. Explains concepts on Functional Verification methodologies used in industry like OVM, UVM
SystemVerilog Assertions verification with SVAUnit - DVCon US 2016 Tutorial



SystemVerilog Assertions verification with SVAUnit - DVCon US 2016 TutorialAmiq Consulting This document provides an overview of SystemVerilog Assertions (SVAs) and the SVAUnit framework for verifying SVAs. It begins with an introduction to SVAs, including types of assertions and properties. It then discusses planning SVA development, such as identifying design characteristics and coding guidelines. The document outlines implementing SVAs and using the SVAUnit framework, which allows decoupling SVA definition from validation code. It provides an example demonstrating generating stimuli to validate an AMBA APB protocol SVA using SVAUnit. Finally, it summarizes SVAUnit's test API and features for error reporting and test coverage.
Challenges in Using UVM at SoC Level



Challenges in Using UVM at SoC LevelDVClub This document discusses challenges in using the Universal Verification Methodology (UVM) at the system-on-chip (SoC) level and proposes solutions. It outlines key features of UVM, then describes challenges like lack of control over UVM verification components from C code and difficulty reusing test cases across different levels. The document proposes a wrapper to connect UVM and SystemC ports and adds a TLM export and register-controlled sequence to allow processor control over sequences. It demonstrates controlling a sequence from a processor through this interface. Finally, it discusses areas like seamless UVM-SystemC connections that could be improved in future UVM versions.
Apb



ApbAzad Mishra The document describes the AMBA 3 APB protocol. It has an unpipelined design to reduce complexity and power consumption. Transfers take at least two cycles with the first being a setup phase and second an access phase controlled by the PENABLE signal. Slaves can extend transfers using the PREADY signal. Errors are indicated by PSLVERR. The protocol defines read and write transfers with or without wait states.
Axi



AxiAzad Mishra The document describes the Advanced eXtensible Interface (AXI) which is a high-performance interface used in system-on-chip (SoC) designs. AXI supports separate address/control and data phases to improve performance. It allows burst-based transactions where only the start address is issued and multiple outstanding addresses can be in flight simultaneously. AXI includes features like different burst types, cache support, protection units, error handling, and unaligned transfers to enhance system performance.
System verilog assertions



System verilog assertionsHARINATH REDDY This document discusses SystemVerilog assertions (SVA). It introduces SVA and explains that assertions are used to document design functionality, check design intent is met, and determine if verification tested the design. Assertions can be specified by the design or verification engineer. The document outlines the key building blocks of SVA like sequences, properties, and assertions. It provides examples of different types of assertions and how they are used. Key concepts discussed include implication, timing windows, edge detection, and repetition operators.
AMBA 3 APB Protocol



AMBA 3 APB ProtocolSwetha GSM The Advanced Peripheral Bus (APB) is part of the Advanced Microcontroller Bus Architecture (AMBA) protocol family. It defines a low-cost interface that is optimized for minimal power consumption and reduced interface complexity.
Uvm presentation dac2011_final



Uvm presentation dac2011_finalsean chen The document describes a workshop on Universal Verification Methodology (UVM) that will cover UVM concepts and techniques for verifying blocks, IP, SOCs, and systems. The workshop agenda includes presentations on UVM concepts and architecture, sequences and phasing, TLM2 and register packages, and putting together UVM testbenches. The workshop is organized by Dennis Brophy, Stan Krolikoski, and Yatin Trivedi and will take place on June 5, 2011 in San Diego, CA.
Axi



AxiVinchipsytm Vlsitraining The document discusses the Advanced eXtensible Interface (AXI) bus. AXI is a high-performance interface that supports high clock frequencies and burst transactions. It separates address/control and data phases and allows for multiple outstanding addresses. AXI consists of five channels for read/write address, data, and responses. It provides benefits like increased throughput and flexibility over older interfaces. Some limitations are burst size constraints and overhead from separate channels.
Spi master core verification



Spi master core verificationMaulik Suthar The document describes the verification of an SPI master core using UVM. It provides details on the SPI protocol, the master core architecture and features, testbench components like agents and scoreboard, testcases that were run, and two bugs that were discovered. The verification covered functionality like different data transfer configurations and achieved 92.85% coverage of the design.
UVM Methodology Tutorial



UVM Methodology TutorialArrow Devices UVM is a standardized methodology for verifying complex IP and SOC in the semiconductor industry. UVM is an Accellera standard and developed with support from multiple vendors Aldec, Cadence, Mentor, and Synopsys. UVM 1.0 was released on 28 Feb 2011 which is widely accepted by verification Engineer across the world. UVM has evolved and undergone a series of minor releases, which introduced new features.
UVM provides the standard structure for creating test-bench and UVCs. The following features are provided by UVM
• Separation of tests from test bench
• Transaction-level communication (TLM)
• Sequences
• Factory and configuration
• Message reporting
• End-of-test mechanism
• Register layer
SystemVerilog based OVM and UVM Verification Methodologies



SystemVerilog based OVM and UVM Verification MethodologiesRamdas Mozhikunnath Introduction to System Verilog based verification methodologies - OVM and UVM concepts
For more online courses and resources follow http://verificationexcellence.in/
AMBA3.0 james_20110801



AMBA3.0 james_20110801James Chang The document describes the AXI (Advanced eXtensible Interface) bus specification. AXI uses separate address/control and data phases with 5 independent channels - read address, write address, read data, write data, and write response. It supports burst-based transactions and out-of-order transaction completion. Register slices can be inserted to increase latency and maximize frequency. AXI defines signals for address, data, strobes, IDs, valid/ready handshaking and more to enable flexible on-chip interconnects.
SPI introduction(Serial Peripheral Interface)



SPI introduction(Serial Peripheral Interface)SUNODH GARLAPATI Serial Peripheral Interface (SPI) is an interface bus commonly used to send data between microcontrollers and small peripherals such as shift registers, sensors, and SD cards.
OMA Lightweight M2M 



OMA Lightweight M2M Hamdamboy (함담보이) This document provides an overview of OMA LwM2M including:
1. A description of LwM2M and its related standard activities.
2. Details on the LwM2M specification and architectural model including objects, resources, and the client-server communication protocol.
3. A summary of the results of the 2018 OMA LwM2M Test Fest including testing of specifications and multi-vendor interoperability.
OpenPOWER Webinar 



OpenPOWER Webinar Ganesan Narayanasamy The document discusses strategies for improving application performance on POWER9 processors using IBM XL and open source compilers. It reviews key POWER9 features and outlines common bottlenecks like branches, register spills, and memory issues. It provides guidelines on using compiler options and coding practices to address these bottlenecks, such as unrolling loops, inlining functions, and prefetching data. Tools like perf are also described for analyzing performance bottlenecks.
Ad
More Related Content
What's hot (20)
System verilog important



System verilog importantelumalai7 The document discusses the building blocks of a SystemVerilog testbench. It describes the program block, which encapsulates test code and allows reading/writing signals and calling module routines. Interface and clocking blocks are used to connect the testbench to the design under test. Assertions, randomization, and other features help create flexible testbenches to verify design correctness.
System verilog verification building blocks



System verilog verification building blocksNirav Desai SystemVerilog introduces key concepts like program blocks, interfaces, and clocking blocks to help with verification. Program blocks separate the testbench code from the design code to avoid race conditions. Interfaces encapsulate communication between blocks and help prevent errors from manual port connections. Clocking blocks synchronize signal drivers and allow specifying timing for sampled signals. Together these features help manage complexity when verifying designs.
System verilog coverage



System verilog coveragePushpa Yakkala Coverage is a technique used in simulation to measure how much of a design has been tested or verified. There are different types of coverage including functional coverage, which checks which features or functions have been tested, and code coverage, which measures how much of the design code has been exercised. Coverage is measured using coverage tools and reports to identify any remaining gaps or "holes" that need additional testing to fully verify the design.
Advance Peripheral Bus 



Advance Peripheral Bus SIVA NAGENDRA REDDY The Advanced Microcontroller Bus Architecture (AMBA) specification defines interfaces for connecting processor and peripherals. It aims to standardize connections to enable modular system design. The Advanced Peripheral Bus (APB) is defined by AMBA for simple peripherals like timers and I/O. It uses few signals for non-pipelined transfers in two cycles to reduce power and complexity.
Amba axi 29 3_2015



Amba axi 29 3_2015kiemnhatminh The Amba AXI protocol enables high-bandwidth and low-latency interconnect between IP blocks through separate address/control and data channels that support burst-based transactions, out-of-order completion, and register slices for high-frequency operation. It uses two-way handshaking on channels and supports various burst types including incrementing, wrapping, and fixed bursts through start addresses and calculated transfer addresses.
AMBA Ahb 2.0



AMBA Ahb 2.0Akhil Srivastava This document describes the Advanced Microcontroller Bus Architecture (AMBA) Advanced High-performance Bus (AHB) 2.0 specification. It details features of AHB such as burst transfers, split transactions, and single-cycle bus master handover. It also explains typical components in an AMBA AHB system including masters, slaves, arbitration, and bus operation with different transfer types.
SOC Verification using SystemVerilog 



SOC Verification using SystemVerilog Ramdas Mozhikunnath Introduction to SOC Verification Fundamentals and System Verilog language coding. Explains concepts on Functional Verification methodologies used in industry like OVM, UVM
SystemVerilog Assertions verification with SVAUnit - DVCon US 2016 Tutorial



SystemVerilog Assertions verification with SVAUnit - DVCon US 2016 TutorialAmiq Consulting This document provides an overview of SystemVerilog Assertions (SVAs) and the SVAUnit framework for verifying SVAs. It begins with an introduction to SVAs, including types of assertions and properties. It then discusses planning SVA development, such as identifying design characteristics and coding guidelines. The document outlines implementing SVAs and using the SVAUnit framework, which allows decoupling SVA definition from validation code. It provides an example demonstrating generating stimuli to validate an AMBA APB protocol SVA using SVAUnit. Finally, it summarizes SVAUnit's test API and features for error reporting and test coverage.
Challenges in Using UVM at SoC Level



Challenges in Using UVM at SoC LevelDVClub This document discusses challenges in using the Universal Verification Methodology (UVM) at the system-on-chip (SoC) level and proposes solutions. It outlines key features of UVM, then describes challenges like lack of control over UVM verification components from C code and difficulty reusing test cases across different levels. The document proposes a wrapper to connect UVM and SystemC ports and adds a TLM export and register-controlled sequence to allow processor control over sequences. It demonstrates controlling a sequence from a processor through this interface. Finally, it discusses areas like seamless UVM-SystemC connections that could be improved in future UVM versions.
Apb



ApbAzad Mishra The document describes the AMBA 3 APB protocol. It has an unpipelined design to reduce complexity and power consumption. Transfers take at least two cycles with the first being a setup phase and second an access phase controlled by the PENABLE signal. Slaves can extend transfers using the PREADY signal. Errors are indicated by PSLVERR. The protocol defines read and write transfers with or without wait states.
Axi



AxiAzad Mishra The document describes the Advanced eXtensible Interface (AXI) which is a high-performance interface used in system-on-chip (SoC) designs. AXI supports separate address/control and data phases to improve performance. It allows burst-based transactions where only the start address is issued and multiple outstanding addresses can be in flight simultaneously. AXI includes features like different burst types, cache support, protection units, error handling, and unaligned transfers to enhance system performance.
System verilog assertions



System verilog assertionsHARINATH REDDY This document discusses SystemVerilog assertions (SVA). It introduces SVA and explains that assertions are used to document design functionality, check design intent is met, and determine if verification tested the design. Assertions can be specified by the design or verification engineer. The document outlines the key building blocks of SVA like sequences, properties, and assertions. It provides examples of different types of assertions and how they are used. Key concepts discussed include implication, timing windows, edge detection, and repetition operators.
AMBA 3 APB Protocol



AMBA 3 APB ProtocolSwetha GSM The Advanced Peripheral Bus (APB) is part of the Advanced Microcontroller Bus Architecture (AMBA) protocol family. It defines a low-cost interface that is optimized for minimal power consumption and reduced interface complexity.
Uvm presentation dac2011_final



Uvm presentation dac2011_finalsean chen The document describes a workshop on Universal Verification Methodology (UVM) that will cover UVM concepts and techniques for verifying blocks, IP, SOCs, and systems. The workshop agenda includes presentations on UVM concepts and architecture, sequences and phasing, TLM2 and register packages, and putting together UVM testbenches. The workshop is organized by Dennis Brophy, Stan Krolikoski, and Yatin Trivedi and will take place on June 5, 2011 in San Diego, CA.
Axi



AxiVinchipsytm Vlsitraining The document discusses the Advanced eXtensible Interface (AXI) bus. AXI is a high-performance interface that supports high clock frequencies and burst transactions. It separates address/control and data phases and allows for multiple outstanding addresses. AXI consists of five channels for read/write address, data, and responses. It provides benefits like increased throughput and flexibility over older interfaces. Some limitations are burst size constraints and overhead from separate channels.
Spi master core verification



Spi master core verificationMaulik Suthar The document describes the verification of an SPI master core using UVM. It provides details on the SPI protocol, the master core architecture and features, testbench components like agents and scoreboard, testcases that were run, and two bugs that were discovered. The verification covered functionality like different data transfer configurations and achieved 92.85% coverage of the design.
UVM Methodology Tutorial



UVM Methodology TutorialArrow Devices UVM is a standardized methodology for verifying complex IP and SOC in the semiconductor industry. UVM is an Accellera standard and developed with support from multiple vendors Aldec, Cadence, Mentor, and Synopsys. UVM 1.0 was released on 28 Feb 2011 which is widely accepted by verification Engineer across the world. UVM has evolved and undergone a series of minor releases, which introduced new features.
UVM provides the standard structure for creating test-bench and UVCs. The following features are provided by UVM
• Separation of tests from test bench
• Transaction-level communication (TLM)
• Sequences
• Factory and configuration
• Message reporting
• End-of-test mechanism
• Register layer
SystemVerilog based OVM and UVM Verification Methodologies



SystemVerilog based OVM and UVM Verification MethodologiesRamdas Mozhikunnath Introduction to System Verilog based verification methodologies - OVM and UVM concepts
For more online courses and resources follow http://verificationexcellence.in/
AMBA3.0 james_20110801



AMBA3.0 james_20110801James Chang The document describes the AXI (Advanced eXtensible Interface) bus specification. AXI uses separate address/control and data phases with 5 independent channels - read address, write address, read data, write data, and write response. It supports burst-based transactions and out-of-order transaction completion. Register slices can be inserted to increase latency and maximize frequency. AXI defines signals for address, data, strobes, IDs, valid/ready handshaking and more to enable flexible on-chip interconnects.
SPI introduction(Serial Peripheral Interface)



SPI introduction(Serial Peripheral Interface)SUNODH GARLAPATI Serial Peripheral Interface (SPI) is an interface bus commonly used to send data between microcontrollers and small peripherals such as shift registers, sensors, and SD cards.
Similar to Efficient Methodology of Sampling UVM RAL During Simulation for SoC Functional Coverage (20)
OMA Lightweight M2M 



OMA Lightweight M2M Hamdamboy (함담보이) This document provides an overview of OMA LwM2M including:
1. A description of LwM2M and its related standard activities.
2. Details on the LwM2M specification and architectural model including objects, resources, and the client-server communication protocol.
3. A summary of the results of the 2018 OMA LwM2M Test Fest including testing of specifications and multi-vendor interoperability.
OpenPOWER Webinar 



OpenPOWER Webinar Ganesan Narayanasamy The document discusses strategies for improving application performance on POWER9 processors using IBM XL and open source compilers. It reviews key POWER9 features and outlines common bottlenecks like branches, register spills, and memory issues. It provides guidelines on using compiler options and coding practices to address these bottlenecks, such as unrolling loops, inlining functions, and prefetching data. Tools like perf are also described for analyzing performance bottlenecks.
chapter8.ppt clean code Boundary ppt Coding guide



chapter8.ppt clean code Boundary ppt Coding guideSanjeevSaharan5 The document discusses subroutines and control abstraction in programming languages. It reviews stack layout and how routines are allocated stack frames. It covers calling sequences and responsibilities of callers and callees. It discusses parameter passing mechanisms like value, reference, and closures. It also covers topics like generic subroutines and modules, exception handling, and coroutines.
Mod 3.pptx



Mod 3.pptxlekha349785 The document provides information about the ARM processor architecture. It discusses the key aspects of ARM including:
- ARM uses a load-store architecture with fixed-length 32-bit instructions and 3-address instruction formats.
- The main differences between RISC and CISC are that RISC executes one instruction per clock cycle while CISC takes multiple cycles per instruction.
- ARM development tools include a C compiler, assembler, linker, debugger and emulator to allow cross-development for ARM systems.
Creo Parametric and Windchill Workspace.pdf



Creo Parametric and Windchill Workspace.pdf3 HTi - Engineering Software and Solutions Learn about Windchill Workspace online at 3HTi. We delve into the Windchill Workspace server, its features, and how to use it effectively alongside Creo Parametric.
Optimica Compiler Toolkit - Overview



Optimica Compiler Toolkit - OverviewModelon The document provides an overview of the OPTIMICA Compiler Toolkit. It discusses the toolkit's capabilities for transient and steady-state time domain simulation and optimization. It also outlines Modelon's model-based development workflow using model libraries, authoring, compilers, solvers, and other technologies. Key features of the toolkit include Modelica and FMI-based computation, dynamic and steady-state simulation, optimization capabilities, and scripting APIs.
Energy efficient AI workload partitioning on multi-core systems



Energy efficient AI workload partitioning on multi-core systemsDeepak Shankar o create an AI system, the semiconductor, software, and systems team need to work together. Multi-core systems can provide extremely low latency and higher throughput at lower power consumption. But concurrent access to shared resources by multiple of AI workloads running on different cores can create higher worst-case execution time (WCET) and causes multiple system failures. Architecture exploration can be used to efficiently balance the compute, communication, synchronization, and storage. In this Webinar, we will be using Workloads from automotive, and data centers to demonstrate the methodology.
VisualSim Architect enables designers to assemble architecture models that extend from the smallest IoT to full automotive, and Radar systems to Data Centers. These models will include any combination of software, processors, ECU, RTOS and networks. Using this platform, software designer can explore the partitioning of the AI tasks (software or model) on to cores based on the latency, bandwidth, and power constraints. Within the IoT, the processor, A/D, Bluetooth and software can be modeled while an automotive design will require the network, ECU and firmware. Both have a unique mechanism to define the traffic, test scenarios and AI workloads. Hardware engineers can select cores, cores per cluster, cache hierarchy, memory controller, accelerators, and the interface topology. Software engineers can tune the partitioning, synchronization overhead, memory access schedules and scheduling.
A High-Level Programming Approach for using FPGAs in HPC using Functional Des...



A High-Level Programming Approach for using FPGAs in HPC using Functional Des...waqarnabi (1) The authors present an approach for using FPGAs in high-performance computing (HPC) that involves using functional descriptions, vector type-transformations, and cost-modeling. (2) Their approach uses type transformations to generate design variants from a functional program and develops an intermediate language and cost model. (3) The cost model provides fast, lightweight estimates of performance and resource usage for different design variants to enable automated design space exploration for FPGA-based HPC applications.
Incquery Suite Models 2020 Conference by István Ráth, CEO of IncQuery Labs



Incquery Suite Models 2020 Conference by István Ráth, CEO of IncQuery LabsIncQuery Labs This document discusses how IncQuery Suite can be used to analyze digital threads in model-based systems engineering (MBSE) projects. It provides an overview of IncQuery Suite's features for efficiently extracting and analyzing engineering data across proprietary tools, validating documents and projects, performing graph queries and full-text search, and integrating with various tools. The document also presents two case studies, one involving integrating IncQuery Suite with Airbus's application platform to enable data continuity, and another using IncQuery Suite to provide model checking as a service for SysML models.
Embedded C



Embedded CKrunal Siddhapathak The document discusses various code optimization techniques for embedded C programming, including:
1) Floating-point to fixed-point conversion to reduce cycle count and energy consumption.
2) Array folding and loop tiling/blocking to improve memory usage and locality of references.
3) Loop splitting to improve efficiency by handling regular and exception cases separately.
4) Simple loop transformations like unrolling to reduce overhead and improve speed.
Dynamic memory allocation is discouraged in safety-critical embedded systems like avionics in favor of more predictable allocators like stack-based, thread-local, and in-memory databases to increase performance, stability, and predictability.
Operationalizing Machine Learning: Serving ML Models



Operationalizing Machine Learning: Serving ML ModelsLightbend Join O’Reilly author and Lightbend Principal Architect, Boris Lublinsky, as he discusses one of the hottest topics in software engineering today: serving machine learning models.
Typically with machine learning, different groups are responsible for model training and model serving. Data scientists often introduce their own machine-learning tools, causing software engineers to create complementary model-serving frameworks to keep pace. It’s not a very efficient system. In this webinar, Boris demonstrates a more standardized approach to model serving and model scoring:
* How to develop an architecture for serving models in real time as part of input stream processing
* How this approach enables data science teams to update models without restarting existing applications
* Different ways to build this model-scoring solution, using several popular stream processing engines and frameworks
Modelon Modelica executable requirements Ansys Conference 2016



Modelon Modelica executable requirements Ansys Conference 2016Modelon The Functional Mockup Interface: FMI overview
Modelica: a very brief overview
A Real-World Example: Active Grill Shutter Controls
Vehicle Thermal Management with Modelica
Continuous Validation of System Requirements
- Intermediate results from ITEA3 MODRIO project
Iterative Controller Development Using Modelica
Conclusions
Matlab Based High Level Synthesis Engine for Area And Power Efficient Arithme...



Matlab Based High Level Synthesis Engine for Area And Power Efficient Arithme...ijceronline Embedded systems used in real-time applications require low power, less area and a high computation speed. For digital signal processing (DSP), image processing and communication applications, data are often received at a continuously high rate. Embedded processors have to cope with this high data rate and process the incoming data based on specific application requirements. Even though there are many different application domains, they all require arithmetic operations that quickly compute the desired values using a larger range of operation, reconfigurable behavior, low power and high precision. The type of necessary arithmetic operations may vary greatly among different applications. The RTL-based design and verification of one or more of these functions may be time-consuming. Some High Level Synthesis tools reduce this design and verification time but may not be optimal or suitable for low power applications. The developed MATLAB-based Arithmetic Engine improves design time and reduces the verification process, but the key point is to use a unified design that combines some of the basic operations with more complex operations to reduce area and power consumption. The results indicate that using the Arithmetic Engine from a simple design to more complex systems can improve design time by reducing the verification time by up to 62%. The MATLAB-based Arithmetic Engine generates structural RTL code, a testbench, and gives the designers more control. The MATLAB-based design and verification engine uses optimized algorithms for better accuracy at a better throughput.
Basics of micro controllers for biginners



Basics of micro controllers for biginnersGerwin Makanyanga The document provides an overview of microprocessors and microcontrollers. It discusses the basic architecture of microprocessors, including the Von Neumann and Harvard architectures. It compares RISC and CISC instruction sets. Microcontrollers are defined as single-chip computers containing a CPU, memory, and I/O ports. Common PIC microcontrollers are described along with their characteristics such as speed, memory types, and analog/digital capabilities. The document also outlines best practices for selecting a suitable microcontroller for a project, including identifying hardware interfaces, memory needs, programming tools, and cost/power constraints.
Advanced computer architecture lesson 5 and 6



Advanced computer architecture lesson 5 and 6Ismail Mukiibi The document discusses reduced instruction set computers (RISC) and compares them to complex instruction set computers (CISC). Key characteristics of RISC include simple, uniform instructions that are executed in one cycle; register-to-register operations with simple addressing modes; and a large number of registers to optimize register usage and minimize memory accesses. Studies show programs use simple operations, operands, and addressing modes most frequently, informing the RISC design which aims to efficiently support common cases through hard-wired, streamlined instructions.
A Fast and Accurate Cost Model for FPGA Design Space Exploration in HPC Appli...



A Fast and Accurate Cost Model for FPGA Design Space Exploration in HPC Appli...waqarnabi Slides for our paper at RAW, nominated for best paper award, related to our work on developing an optimizing compiler for running scientific code on FPGAs.
Machine Learning At Speed: Operationalizing ML For Real-Time Data Streams



Machine Learning At Speed: Operationalizing ML For Real-Time Data StreamsLightbend Audience: Architects, Data Scientists, Developers
Technical level: Introductory
From home intrusion detection, to self-driving cars, to keeping data center operations healthy, Machine Learning (ML) has become one of the hottest topics in software engineering today. While much of the focus has been on the actual creation of the algorithms used in ML, the less talked-about challenge is how to serve these models in production, often utilizing real-time streaming data.
The traditional approach to model serving is to treat the model as code, which means that ML implementation has to be continually adapted for model serving. As the amount of machine learning tools and techniques grows, the efficiency of such an approach is becoming more questionable. Additionally, machine learning and model serving are driven by very different quality of service requirements; while machine learning is typically batch, dealing with scalability and processing power, model serving is mostly concerned with performance and stability.
In this webinar with O’Reilly author and Lightbend Principal Architect, Boris Lublinsky, we will define an alternative approach to model serving, based on treating the model itself as data. Using popular frameworks like Akka Streams and Apache Flink, Boris will review how to implement this approach, explaining how it can help you:
* Achieve complete decoupling between the model implementation for machine learning and model serving, enforcing better standardization of your model serving implementation.
* Enable dynamic updates of the served model without having to restart the system.
* Utilize Tensorflow and PMML as model representation and their usage for building “real time updatable” model serving architecture.
AutomationML: A Model-Driven View



AutomationML: A Model-Driven ViewLuca Berardinelli AutomationML (Automation Markup Language) is a neutral data format based on XML for the storage and exchange of plant engineering information, which is provided as open standard. Goal of AutomationML is to interconnect the heterogeneous tool landscape of modern engineering tools in their different disciplines, e.g. mechanical plant engineering, electrical design, HMI development, PLC, robot control.
This presentation provides an overview on AutomationML and a model-driven engineering view on its integration capabilities.
Introduction to arm processor



Introduction to arm processorRAMPRAKASHT1 This document provides an introduction to the ARM processor architecture. It discusses key aspects of ARM including the ARM programming model, instruction set, memory hierarchy, and development tools. ARM is a popular reduced instruction set computing (RISC) architecture used in many portable electronic devices due to its low power consumption.
Ad
More from Sameh El-Ashry (8)
How to create SystemVerilog verification environment?



How to create SystemVerilog verification environment?Sameh El-Ashry Basic knowledge for the verification engineer to learn the art of creating SystemVerilog verification environment.
Starting from the specifications extraction till coverage closure.
Chipions session 2021 - VLSI career



Chipions session 2021 - VLSI careerSameh El-Ashry The document discusses VLSI (Very Large Scale Integration) and chip design. It provides an overview of the differences between IP (Intellectual Property) and System on Chip (SoC), describing a typical SoC as consisting of components like processors, memory blocks, interfaces, and analog circuits. The chip design flow is summarized as moving from design to tapeout. Research centers for VLSI in Egypt are listed, along with a comparison of VLSI companies in Egypt between 2017 and 2021.
On Error Injection for NoC Platforms: A UVM-based Practical Case Study



On Error Injection for NoC Platforms: A UVM-based Practical Case StudySameh El-Ashry Paper presented at
NoCArc'17, October 15, 2017, Boston, MA, USA © 2017
paper URL: https://dl.acm.org/doi/10.1145/3139540.3139544
A reusable verification environment for NoC platforms using UVM



A reusable verification environment for NoC platforms using UVMSameh El-Ashry This document proposes reusable UVM verification environments for network-on-chip (NoC) platforms. It describes motivations for using NoCs instead of buses for multicore system interconnects. The document then outlines the benefits of the UVM methodology for verifying complex designs. It proposes separate UVM environments for verifying a single router using either a predictor or reference model, and an environment for verifying an entire NoC by reusing the single router environment. Simulation results are presented to evaluate average latency and throughput metrics. The goal is to develop reusable UVM environments that can be easily adapted for different NoC configurations and router architectures.
verification_planning_systemverilog_uvm_2020



verification_planning_systemverilog_uvm_2020Sameh El-Ashry This document provides an overview of a training session on SystemVerilog for verification. The agenda includes verification planning, course contents on SystemVerilog basics and verification techniques, chip design flow, old verification languages, verification approaches, and a case study on verifying an arithmetic logic unit. Verification planning concepts like test plans, features and test types, specifications extraction, and measurements are also discussed.
On the verification of configurable nocs in simulation and hardware emulation...



On the verification of configurable nocs in simulation and hardware emulation...Sameh El-Ashry The document summarizes a thesis presentation on verifying configurable Networks-on-Chip (NoCs) using a Universal Verification Methodology (UVM)-based tool. The presentation outlines the research goals of proposing a UVM verification architecture to verify NoCs with different topologies, routing algorithms, and flow control. It describes case studies on a base router and configurable Daniel router. It proposes generic UVM architectures and error injection methodologies to support simulation and hardware emulation of NoCs. Simulation results on performance metrics and functional coverage techniques are also summarized.
Functional verification techniques EW16 session



Functional verification techniques EW16 sessionSameh El-Ashry Functional verification is one of the key bottlenecks in the rapid design of integrated circuits. It is estimated that verification in its entirety accounts for up to 60% of design resources, including duration, computer resources and total personnel. The three primary tools used in logic and functional verification of commercial integrated circuits are simulation (at various levels), emulation at the chip level, and formal verification.
Code Management Workshop



Code Management WorkshopSameh El-Ashry Working in teams is more effective than individual work, But the main obstacle that any corporate faces is the synchronization between each team, One of the functions that is affected by this obstacle is 'Coding', Working on massive and multidisciplinary projects which need the contribution of several teams specially at the coding phase is opposed by the miss coordination when running the mother code.
So corporate developed some tools to overcome this situation using code version control and Tracker System.
Ad
Recently uploaded (20)
Structural Response of Reinforced Self-Compacting Concrete Deep Beam Using Fi...



Structural Response of Reinforced Self-Compacting Concrete Deep Beam Using Fi...Journal of Soft Computing in Civil Engineering Analysis of reinforced concrete deep beam is based on simplified approximate method due to the complexity of the exact analysis. The complexity is due to a number of parameters affecting its response. To evaluate some of this parameters, finite element study of the structural behavior of the reinforced self-compacting concrete deep beam was carried out using Abaqus finite element modeling tool. The model was validated against experimental data from the literature. The parametric effects of varied concrete compressive strength, vertical web reinforcement ratio and horizontal web reinforcement ratio on the beam were tested on eight (8) different specimens under four points loads. The results of the validation work showed good agreement with the experimental studies. The parametric study revealed that the concrete compressive strength most significantly influenced the specimens’ response with the average of 41.1% and 49 % increment in the diagonal cracking and ultimate load respectively due to doubling of concrete compressive strength. Although the increase in horizontal web reinforcement ratio from 0.31 % to 0.63 % lead to average of 6.24 % increment on the diagonal cracking load, it does not influence the ultimate strength and the load-deflection response of the beams. Similar variation in vertical web reinforcement ratio leads to an average of 2.4 % and 15 % increment in cracking and ultimate load respectively with no appreciable effect on the load-deflection response.
Lidar for Autonomous Driving, LiDAR Mapping for Driverless Cars.pptx



Lidar for Autonomous Driving, LiDAR Mapping for Driverless Cars.pptxRishavKumar530754 LiDAR-Based System for Autonomous Cars
Autonomous Driving with LiDAR Tech
LiDAR Integration in Self-Driving Cars
Self-Driving Vehicles Using LiDAR
LiDAR Mapping for Driverless Cars
Introduction to FLUID MECHANICS & KINEMATICS



Introduction to FLUID MECHANICS & KINEMATICSnarayanaswamygdas Fluid mechanics is the branch of physics concerned with the mechanics of fluids (liquids, gases, and plasmas) and the forces on them. Originally applied to water (hydromechanics), it found applications in a wide range of disciplines, including mechanical, aerospace, civil, chemical, and biomedical engineering, as well as geophysics, oceanography, meteorology, astrophysics, and biology.
It can be divided into fluid statics, the study of various fluids at rest, and fluid dynamics.
Fluid statics, also known as hydrostatics, is the study of fluids at rest, specifically when there's no relative motion between fluid particles. It focuses on the conditions under which fluids are in stable equilibrium and doesn't involve fluid motion.
Fluid kinematics is the branch of fluid mechanics that focuses on describing and analyzing the motion of fluids, such as liquids and gases, without considering the forces that cause the motion. It deals with the geometrical and temporal aspects of fluid flow, including velocity and acceleration. Fluid dynamics, on the other hand, considers the forces acting on the fluid.
Fluid dynamics is the study of the effect of forces on fluid motion. It is a branch of continuum mechanics, a subject which models matter without using the information that it is made out of atoms; that is, it models matter from a macroscopic viewpoint rather than from microscopic.
Fluid mechanics, especially fluid dynamics, is an active field of research, typically mathematically complex. Many problems are partly or wholly unsolved and are best addressed by numerical methods, typically using computers. A modern discipline, called computational fluid dynamics (CFD), is devoted to this approach. Particle image velocimetry, an experimental method for visualizing and analyzing fluid flow, also takes advantage of the highly visual nature of fluid flow.
Fundamentally, every fluid mechanical system is assumed to obey the basic laws :
Conservation of mass
Conservation of energy
Conservation of momentum
The continuum assumption
For example, the assumption that mass is conserved means that for any fixed control volume (for example, a spherical volume)—enclosed by a control surface—the rate of change of the mass contained in that volume is equal to the rate at which mass is passing through the surface from outside to inside, minus the rate at which mass is passing from inside to outside. This can be expressed as an equation in integral form over the control volume.
The continuum assumption is an idealization of continuum mechanics under which fluids can be treated as continuous, even though, on a microscopic scale, they are composed of molecules. Under the continuum assumption, macroscopic (observed/measurable) properties such as density, pressure, temperature, and bulk velocity are taken to be well-defined at "infinitesimal" volume elements—small in comparison to the characteristic length scale of the system, but large in comparison to molecular length scale
Data Structures_Introduction to algorithms.pptx



Data Structures_Introduction to algorithms.pptxRushaliDeshmukh2 Concept of Problem Solving, Introduction to Algorithms, Characteristics of Algorithms, Introduction to Data Structure, Data Structure Classification (Linear and Non-linear, Static and Dynamic, Persistent and Ephemeral data structures), Time complexity and Space complexity, Asymptotic Notation - The Big-O, Omega and Theta notation, Algorithmic upper bounds, lower bounds, Best, Worst and Average case analysis of an Algorithm, Abstract Data Types (ADT)
Compiler Design_Lexical Analysis phase.pptx



Compiler Design_Lexical Analysis phase.pptxRushaliDeshmukh2 The role of the lexical analyzer
Specification of tokens
Finite state machines
From a regular expressions to an NFA
Convert NFA to DFA
Transforming grammars and regular expressions
Transforming automata to grammars
Language for specifying lexical analyzers
fluke dealers in bangalore..............



fluke dealers in bangalore..............Haresh Vaswani The Fluke 925 is a vane anemometer, a handheld device designed to measure wind speed, air flow (volume), and temperature. It features a separate sensor and display unit, allowing greater flexibility and ease of use in tight or hard-to-reach spaces. The Fluke 925 is particularly suitable for HVAC (heating, ventilation, and air conditioning) maintenance in both residential and commercial buildings, offering a durable and cost-effective solution for routine airflow diagnostics.
Compiler Design Unit1 PPT Phases of Compiler.pptx



Compiler Design Unit1 PPT Phases of Compiler.pptxRushaliDeshmukh2 Compiler phases
Lexical analysis
Syntax analysis
Semantic analysis
Intermediate (machine-independent) code generation
Intermediate code optimization
Target (machine-dependent) code generation
Target code optimization
"Boiler Feed Pump (BFP): Working, Applications, Advantages, and Limitations E...



"Boiler Feed Pump (BFP): Working, Applications, Advantages, and Limitations E...Infopitaara A Boiler Feed Pump (BFP) is a critical component in thermal power plants. It supplies high-pressure water (feedwater) to the boiler, ensuring continuous steam generation.
⚙️ How a Boiler Feed Pump Works
Water Collection:
Feedwater is collected from the deaerator or feedwater tank.
Pressurization:
The pump increases water pressure using multiple impellers/stages in centrifugal types.
Discharge to Boiler:
Pressurized water is then supplied to the boiler drum or economizer section, depending on design.
🌀 Types of Boiler Feed Pumps
Centrifugal Pumps (most common):
Multistage for higher pressure.
Used in large thermal power stations.
Positive Displacement Pumps (less common):
For smaller or specific applications.
Precise flow control but less efficient for large volumes.
🛠️ Key Operations and Controls
Recirculation Line: Protects the pump from overheating at low flow.
Throttle Valve: Regulates flow based on boiler demand.
Control System: Often automated via DCS/PLC for variable load conditions.
Sealing & Cooling Systems: Prevent leakage and maintain pump health.
⚠️ Common BFP Issues
Cavitation due to low NPSH (Net Positive Suction Head).
Seal or bearing failure.
Overheating from improper flow or recirculation.
theory-slides-for react for beginners.pptx



theory-slides-for react for beginners.pptxsanchezvanessa7896 Everything you need to know about react.
π0.5: a Vision-Language-Action Model with Open-World Generalization



π0.5: a Vision-Language-Action Model with Open-World GeneralizationNABLAS株式会社 今回の資料「Transfusion / π0 / π0.5」は、画像・言語・アクションを統合するロボット基盤モデルについて紹介しています。
拡散×自己回帰を融合したTransformerをベースに、π0.5ではオープンワールドでの推論・計画も可能に。
This presentation introduces robot foundation models that integrate vision, language, and action.
Built on a Transformer combining diffusion and autoregression, π0.5 enables reasoning and planning in open-world settings.
Degree_of_Automation.pdf for Instrumentation and industrial specialist



Degree_of_Automation.pdf for Instrumentation and industrial specialistshreyabhosale19 degree of Automation for industrial and Instrumentation learners.
Level 1-Safety.pptx Presentation of Electrical Safety



Level 1-Safety.pptx Presentation of Electrical SafetyJoseAlbertoCariasDel Level 1-Safety.pptx Presentation of Electrical Safety
ADVXAI IN MALWARE ANALYSIS FRAMEWORK: BALANCING EXPLAINABILITY WITH SECURITY



ADVXAI IN MALWARE ANALYSIS FRAMEWORK: BALANCING EXPLAINABILITY WITH SECURITYijscai With the increased use of Artificial Intelligence (AI) in malware analysis there is also an increased need to
understand the decisions models make when identifying malicious artifacts. Explainable AI (XAI) becomes
the answer to interpreting the decision-making process that AI malware analysis models use to determine
malicious benign samples to gain trust that in a production environment, the system is able to catch
malware. With any cyber innovation brings a new set of challenges and literature soon came out about XAI
as a new attack vector. Adversarial XAI (AdvXAI) is a relatively new concept but with AI applications in
many sectors, it is crucial to quickly respond to the attack surface that it creates. This paper seeks to
conceptualize a theoretical framework focused on addressing AdvXAI in malware analysis in an effort to
balance explainability with security. Following this framework, designing a machine with an AI malware
detection and analysis model will ensure that it can effectively analyze malware, explain how it came to its
decision, and be built securely to avoid adversarial attacks and manipulations. The framework focuses on
choosing malware datasets to train the model, choosing the AI model, choosing an XAI technique,
implementing AdvXAI defensive measures, and continually evaluating the model. This framework will
significantly contribute to automated malware detection and XAI efforts allowing for secure systems that
are resilient to adversarial attacks.
Structural Response of Reinforced Self-Compacting Concrete Deep Beam Using Fi...



Structural Response of Reinforced Self-Compacting Concrete Deep Beam Using Fi...Journal of Soft Computing in Civil Engineering
Efficient Methodology of Sampling UVM RAL During Simulation for SoC Functional Coverage
- 1. Efficient Methodology of Sampling UVM RAL during Simulation for SoC Functional Coverage Authors Sameh El-Ashry, [email protected] Ahmed Adel, [email protected] Microprocessor/SoC Test, Security & Verification (MTV18) Conference, Dcemeber 10, 2018, Austin, USA © 2018
- 2. Outline • Motivation. • Introduction. • The Proposed UVM RAL Generation Flow. • The Proposed UVM RAL Backdoor. • Conclusions. 2
- 3. Motivation 3 Why? How? • Why Functional Coverage? • We need good coverage model. • Sampling problem in bad coverage model. • Ex: Sampling on the clock is dangerous for simulation performance. • Sampling on the change of the register. • Efficient backdoor technique is proposed using RAL model.
- 4. Motivation2 • Register files verification represent critical part of any digital design verification process. • One of the most powerful ways to model memories and register files is using Register Abstraction Layer (RAL) which is part of the UVM. • This paper will go through the process of UVM Register model generation with its coverage model using Synopsys tools. 4
- 5. Motivation3 • We propose an efficient and automated methodology of functional coverage UVM- based verification environment supported by RAL model, backdoor access and how to automatically generate it starting from IP-XACT model till producing the UVM RAL model. • The proposed methodology has strong flexibility in frequent design specification changes. • The proposed functional coverage technique is applied to beat performance degradation and enhance the simulation. 5
- 7. Register Abstraction Layer (RAL) • Verification engineers use register models to ease the stimulus generation and the functional checking. • A register model consists of a set of register definitions, register instances clustered under a register block and their address mappings into Design Under Test's (DUT) address space. • RAL allows modeling and verification of hardware registers and memory blocks, the UVM register layer provides read() or write() tasks that can be called from a UVM sequence. 7
- 8. UVM Register Library Features 8 • Read and write for the registers and the memories as part of the normal operation. • Modeling registers, memory blocks and analyze the register activity. • Checking the DUT registers and memories against a shadow device (with shadow registers) at the scoreboard. • Collect coverage on the registers that are created at the RAL model (point to improve). • Initialize the DUT registers and memories. • Randomize the contents of DUT registers and memories.
- 9. The Proposed UVM RAL Generation Flow • The UVM RAL Generation Flow • The Proposed Generic, Scalable, and Configurable UVM Architecture 9
- 10. The UVM RAL Generation Flow • UVM provides mapping of register content of DUT, a layer for accessing register, and memory locations within DUT which is called as RAL. • Once a description of the available registers and memories in a design is available, ralgen tool proposed by Synopsys can automatically generate the UVM RAL for these registers. 10
- 11. The UVM RAL Generation Flow2 11 • Figure describes the flow of the UVM register model generation starting from the Excel spreadsheet register file, the generating of Register Abstraction Layer File (RALF) format. Register File Excel Format IP-XACT Schema Format RALF Model UVM Register Model UVM Register Model Generation Flow ralgen Tool ralgen Tool User Script
- 12. The Proposed UVM Architecture 12 • The designed testbench uses a UVM methodology and constrained random verification techniques. • The goal is to meet the expected functional coverage metrics, and verifying the digital hardware parts in System-on-Chip (SoC) ,and wireless systems.
- 13. The Proposed UVM Architecture2 13 • The verification environment was designed to verify a network consisting of up to four PHYs (DUTs) and can be configured to support extra DUTs as shown in Figure. • One RAL model is implemented, although we created instances from the RAL model for each peer.
- 14. The Proposed Generic UVM Architecture3 14 • A shared functional coverage model is implemented for all DUTs as some scenarios may happen at the transmitter side, others scenarios may happen at the receiver side.
- 15. The Proposed UVM Architecture4 15 • One coverage database is needed for the network so the total coverage percentage is easily merged by automatic way due to the shared functional coverage model. • A structured testbench is built using classes based on UVM supported by UVM RAL model and RAL backdoor access.
- 16. The Proposed UVM Architecture5 16 • Another effect of using the RAL model is that the total coverage closure time is reduced due to an automatic integration for the functional coverage and the covergroups results for all DUT’s instances. • The automatic integration is achieved by mapping all the DUT’s instances to the same covergroups at the RAL model.
- 17. The Proposed UVM Architecture6 17 • There is one more important thing to simulation performance. • The number of calling the sample coverage task badly affects simulation performance next to the size of design. • Thus, the concept of backdoor for specific data path has been applied to register modeling.
- 18. The Proposed UVM RAL Backdoor • Conventional UVM Backdoor classes • Modified UVM Backdoor classes for Coverage Sampling • Proposed Backdoor Sampling Technique for Checking Proposes 18
- 19. Backdoor Access 19 • Front-door access uses the same bus interface for observing operations. This is commonly used in simulation-based register verification because it does not require an additional interface for observation. • Back-door access uses a different interface for observation – usually direct access to registers. • Backdoor access enables efficient observation, but requires the use of an additional interface. • Backdoor improves the efficiency of verifying registers as it can access register locations with little or no simulation time.
- 20. EDA Vendors RAL Generators 20 • The input specification of a register model such as IPXACT, System RDL, Excel file or word file (typically in IPXACT or RALF in our case study) contains all of the necessary information to generate the UVM register model leveraging the UVM base class library. Commercial or open source generators ralgen tool IP_XACT System RDL Excel file Word file UVM Classes RAL Registers Backdoor read/Write Tasks Backdoor Classes for Registers Model Coverage UVM Register Model
- 21. Conventional UVM Backdoor classes 21 • There is a lack of literature discussing the backdoor technique using the hierarchical HDL path based backdoors. • We discuss the backdoor mechanism and the challenges associated with it. • In this mechanism, register constructs are accessed using the Verilog style cross- module references. • This would be relatively less intensive with regards to simulation performance as the HDL paths are all resolved at the compile time.
- 22. Generated UVM RAL read/write backdoor tasks 22 • The interface would contain tasks defined within it to access the constructs that are used to model registers in the RTL of the DUT.
- 23. Generated UVM RAL backdoor classes 23 • The usage of the backdoor classes and the signatures will not change which will allow existing RTL code to work seamlessly with the newly generated model.
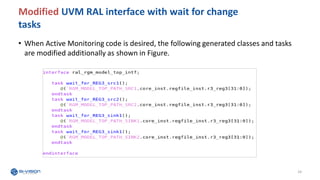
- 24. Modified UVM RAL interface with wait for change tasks 24 • When Active Monitoring code is desired, the following generated classes and tasks are modified additionally as shown in Figure.
- 25. Modified UVM RAL backdoor classes 25 • The additional code in the interface file would be as shown: Sampling event to use it in coverage sampling at the base_test to achieve high performance coverage/simulation.
- 26. Modified UVM RAL backdoor interface. 26
- 27. Functional Coverage Model Generation 27 • The coverage model is created at the proposed UVM environment by our scripts to generate covergroups for the desired registers only and avoid the auto generated coverage model from the ralgen tool for all registers that are created at the RAL model so that a higher coverage simulation performance is achieved. ralgen tool IP_XACT UVM Classes RAL Registers Backdoor read/Write Tasks (will be modified) Backdoor Classes for Registers (will be modified) RAL with Model Coverage UVM Register Model User Script bins_reg_1.txt bins_reg_2.txt bins_reg_N.txt
- 28. Sampling of the coverage model 28 • The sampling of the coverage model for coverage closure is happening at the UVM test layer and is controlled using the event trigger for high simulation performance as shown in Figure.
- 29. Sampling for Scoreboard Checking 29 • The scoreboard peeks registers to use the register’s value in a comparison process, the scoreboard may pull up on the change of the register based on an event that is triggered from the backdoor classes as shown in Figure.
- 30. Conclusions • Commercial or open source tools support the automatic generation for the functional coverage model and the covergroups for all implemented registers at the RAL model. • The auto-generated covergroups are not the most efficient coverage method as the verification engineers may need to exclude some undesirable registers from the final coverage report based on the verification coverage plan that is prepared at the starting of the project. • The coverage sampling of undesirable registers may lead to low simulation performance, a new efficient methodology is proposed for the coverage sampling based on RAL backdoor access to achieve the highest simulation performance. • The automated methodology has strong flexibility and high-level maintainability upon frequent specification changes. 30
- 31. 31 Questions?
- 32. Thank You








