Elasticsearch Security Strategy
0 likes129 views
1. The document outlines a security strategy for an Elasticsearch cluster using X-Pack to implement role-based access control (RBAC). 2. It creates new roles ("filebeat_admin" and "logstash_admin") and users ("charan" and "vasu") with curl commands to restrict access to specific indices. 3. The results show that the new roles and users have the appropriate access levels to their designated indices while being restricted from other indices, demonstrating the implementation of the desired security state.
1 of 12



![4 | P a g e
Desired State of Elasticsearch Cluster Security
Proof of Concept - cURL Commands
To grant DivyaCharan TejaMulagaleti full accesstoall indicesthatmatchthe pattern filebeat-*and enable himto
create visualizationsanddashboardsforthose indicesinKibana,we shall create an filebeat_admin role andassign
the role to a new charan user.
$ curl -XPOST -u elastic 'localhost:9200/_xpack/security/role/filebeat_admin' -H "Content-Type:
application/json" -d '{
"indices" : [
{
"names" : [ "filebeat-*" ],
"privileges" : [ "all" ]
},
{
"names" : [ ".kibana*" ],
"privileges" : [ "manage", "read", "index" ]
}
]
}'
{"role":{"created":true}}
$ curl -XPOST -u elastic 'localhost:9200/_xpack/security/user/charan' -H "Content-Type: application/json" -d
'{
"password" : "sagarsoft",
"full_name" : "Divya Charan Teja Mulagaleti",
"email" : "divyacharan.mulagaleti@sagarsoft.in",
"roles" : [ "filebeat_admin" ]
}'
{"user":{"created":true}}](https://image.slidesharecdn.com/elasticsearchsecuritystrategy-190923050507/85/Elasticsearch-Security-Strategy-4-320.jpg)
![5 | P a g e
To grant VasudevaReddyGangasani full accesstoall indicesthatmatchthe pattern logstash-*andenable himto
create visualizationsanddashboardsforthose indicesinKibana,we shall create an logstash_admin role andassign
the role to a new vasu user.
$ curl -XPOST -u elastic 'localhost:9200/_xpack/security/role/logstash_admin' -H "Content-Type:
application/json" -d '{
"indices" : [
{
"names" : [ "logstash-*" ],
"privileges" : [ "all" ]
},
{
"names" : [ ".kibana*" ],
"privileges" : [ "manage", "read", "index" ]
}
]
}'
{"role":{"created":true}}
$ curl -XPOST -u elastic 'localhost:9200/_xpack/security/user/vasu' -H "Content-Type: application/json" -d '{
"password" : "sagarsoft",
"full_name" : "Vasudeva Reddy Gangasani",
"email" : "vasudeva.gangasani@sagarsoft.in",
"roles" : [ "logstash_admin" ]
}'
{"user":{"created":true}}](https://image.slidesharecdn.com/elasticsearchsecuritystrategy-190923050507/85/Elasticsearch-Security-Strategy-5-320.jpg)






Ad
Recommended
Elasticsearch security



Elasticsearch securityNag Arvind Gudiseva The document discusses implementing security for an Elasticsearch cluster using X-Pack. It begins by describing the existing insecure state where all users can access all indices. It then covers installing and configuring X-Pack to enable authentication and role-based access control. Examples are provided of creating custom roles for specific users to restrict access to only certain indices, enforcing security. Auditing is also configured to log authentication and access events.
10 Excellent Ways to Secure Your Spring Boot Application - Devoxx Morocco 2019



10 Excellent Ways to Secure Your Spring Boot Application - Devoxx Morocco 2019Matt Raible This document contains code snippets in Java and JavaScript that demonstrate how to:
1. Configure Spring Security to require HTTPS
2. Upload images to AWS S3 from a Node.js Lambda function using the AWS SDK
3. Define dependencies for the AWS SDK and node-fetch library
iOS Keychain by 흰, 민디



iOS Keychain by 흰, 민디MINJICHO20 This document discusses using the Keychain to securely store private information in iOS apps. It begins by asking why developers use the Keychain and what the Keychain is. It then covers adding, searching for, updating and deleting Keychain items. The document discusses access groups for sharing data between related apps, and restricting Keychain access based on device state. It notes that the Security framework and its low-level APIs are complex, so wrappers are commonly used to simplify Keychain operations in apps.
Workshop desarrollo Cassandra con el driver Java



Workshop desarrollo Cassandra con el driver JavaJose Felix Hernandez Barrio This document summarizes how to connect to and query a Cassandra database using the Java driver. It covers connecting to a Cassandra cluster, executing DDL and DML statements, performing synchronous and asynchronous queries, using prepared statements, the query builder, tracing queries, and configuring load balancing policies.
Async servers and clients in Rest.li



Async servers and clients in Rest.liKaran Parikh Rest.li is an open source REST framework that uses asynchronous and non-blocking I/O to build scalable REST architectures. It achieves asynchronous behavior through its components R2 (network communication), D2 (dynamic discovery and load balancing), and by not blocking on I/O. Rest.li provides both callback-based and ParSeq-based approaches for building asynchronous Rest.li servers and clients to avoid blocking and improve throughput. ParSeq allows expressing complex asynchronous workflows through tasks and promises.
Coherence 12.1.2 Live Events



Coherence 12.1.2 Live Eventsharvraja This document discusses Oracle Coherence live events. It describes the different types of events in Coherence 12c, including data-related events, entry processor events, transfer events, and transaction events. It also covers the new live event model and how events can be registered through declarative cache configuration or programmatically. The goal is to provide a complete, integrated, best-in-class live event solution for on-premise, private cloud, and public cloud applications.
WWHF 2018 - Using PowerUpSQL and goddi for Active Directory Information Gathe...



WWHF 2018 - Using PowerUpSQL and goddi for Active Directory Information Gathe...ThomasElling1 This document discusses tools for Active Directory information gathering called PowerUpSQL and goddi. PowerUpSQL uses SQL Server and the OLE DB provider to query Active Directory via LDAP, while goddi uses Go and the LDAP library to directly query Active Directory. The document provides overviews of both tools, including how to install them, the methodology behind how they gather information, and demos of them in use. It also discusses some of the limitations and optimizations of each tool.
Dodging WebCrypto API Landmines



Dodging WebCrypto API LandminesErnie Turner The document discusses the Web Crypto API which allows cryptographic operations like hashing, signatures, and encryption/decryption to be performed in web applications. It covers the SubtleCrypto interface which provides cryptographic algorithms and methods. Some key methods include importKey, deriveKey, encrypt, and decrypt. It also discusses concepts like symmetric keys, AES-GCM encryption, PBKDF2 key derivation, and storing encrypted data with salts and initialization vectors. An example is provided of encrypting and decrypting data with a password using these Web Crypto API methods.
[AzureCamp 24 Juin 2014] Cache Distribué par Thomas Conté![[AzureCamp 24 Juin 2014] Cache Distribué par Thomas Conté](https://cdn.slidesharecdn.com/ss_thumbnails/1430cachedistributconte-140716110848-phpapp02-thumbnail.jpg?width=560&fit=bounds)
![[AzureCamp 24 Juin 2014] Cache Distribué par Thomas Conté](https://cdn.slidesharecdn.com/ss_thumbnails/1430cachedistributconte-140716110848-phpapp02-thumbnail.jpg?width=560&fit=bounds)
![[AzureCamp 24 Juin 2014] Cache Distribué par Thomas Conté](https://cdn.slidesharecdn.com/ss_thumbnails/1430cachedistributconte-140716110848-phpapp02-thumbnail.jpg?width=560&fit=bounds)
![[AzureCamp 24 Juin 2014] Cache Distribué par Thomas Conté](https://cdn.slidesharecdn.com/ss_thumbnails/1430cachedistributconte-140716110848-phpapp02-thumbnail.jpg?width=560&fit=bounds)
[AzureCamp 24 Juin 2014] Cache Distribué par Thomas ContéMicrosoft Technet France Microsoft Azure Cache for Redis provides a managed Redis cache in the cloud. It can be accessed from .NET applications using the StackExchange.Redis client which allows putting and getting string values from the cache using keys. Redis Labs recommends securing access to Redis using SSL encryption and provides Redis clients that support connecting securely over SSL.
Cassandra summit 2013 - DataStax Java Driver Unleashed!



Cassandra summit 2013 - DataStax Java Driver Unleashed!Michaël Figuière This document provides an overview of the DataStax Java Driver and how to use it to connect to and query Cassandra. It introduces key concepts like CQL, the data model, asynchronous operations, prepared statements, load balancing, and retry policies. The document also includes code examples for connecting to Cassandra, performing basic read and write operations using CQL strings and prepared statements, and more advanced techniques like asynchronous reads, query builders, custom load balancing policies, and object mapping.
Encryption Boot Camp at Øredev



Encryption Boot Camp at ØredevMatthew McCullough The document discusses symmetric encryption in Java. It shows how to generate a symmetric key, use it to encrypt a message with DESede encryption, and output the encrypted bytes as a base64 encoded string. Securely transmitting the symmetric key between parties is identified as a challenge for symmetric encryption.
Connecting to the network



Connecting to the networkMu Chun Wang The document discusses various methods for connecting to a network and downloading content in Android, including checking network connectivity, performing long operations off the main thread using AsyncTask, downloading content from URLs, and considerations around using HttpClient versus HttpURLConnection. It provides code examples for tasks like retrieving the device IP address, disabling HTTP connection reuse, and handling gzip encoding.
Advance MySQL Docstore Features



Advance MySQL Docstore Featuressankalita chakraborty MySQL Connectors provide advanced features for MySQL Document Store, including connection pooling, locking read operations, and prepared statements. Connection pooling improves performance by reusing existing connections rather than creating new connections. Locking read operations allow transactions to lock documents during reads. Prepared statements optimize performance by parsing queries once and reusing the query plan for multiple executions.
Managing and Integrating Vault at The New York Times



Managing and Integrating Vault at The New York TimesAmanda MacLeod This document summarizes a presentation given by the New York Times' Delivery Engineering Team about how they adopted and manage Hashicorp Vault at the New York Times. Some key points:
- They were having problems managing secrets before and Vault helped simplify this.
- They leverage Vault's authentication methods, ACLs, auditing, and "break glass" capabilities.
- To better isolate access, they created namespaces in Vault for teams and integrated this with Terraform and a tool called Goblin.
- They also integrated Vault with their Google Kubernetes Engine cluster by having init containers fetch signed JWTs and write secrets to shared memory volumes.
- This approach removes secrets
Struts database access



Struts database accessAbass Ndiaye The document discusses how to access a MySQL database from a Struts 2 application. It describes setting up the database with a table and data. It then covers creating a Struts 2 action class to query the database on user login, and JSP views for successful and failed logins. Configuration files including struts.xml and web.xml are provided to wire it all together.
Odv oracle customer_demo



Odv oracle customer_demoViaggio Italia This document provides an overview and agenda for a presentation on Oracle Database Vault. It discusses securing data using realms, factors, command rules and rule sets in Database Vault. It also covers auditing violations which are logged in the database and to the operating system. The document concludes with a brief section on the impact of backups on a Database Vault secured system when using export, Data Pump and RMAN.
Wicket Security Presentation



Wicket Security Presentationmrmean - Wicket Security Wasp & Swarm is a framework for adding authentication and authorization to Wicket applications. It provides flexible security models and permission checking.
- Swarm builds on Wasp and provides standard authentication and role-based access control. It uses a HiveMind-based policy system for defining permissions.
- The document provides examples of setting up a basic secure Wicket application using Swarm, defining principals and policies, and implementing authentication and authorization checks.
Bkbiet day2 & 3



Bkbiet day2 & 3mihirio This document summarizes a training on servlets, databases, and the model-view-controller framework. It includes code examples for creating a basic servlet that prints "Hello World", connecting to a database and performing queries, and using JSP templates to separate the data model from the user interface view. Exercises are provided to have trainees build a web application that takes user input, stores it in a database, and displays the stored information.
Azure Web Camp : Cache Distribué



Azure Web Camp : Cache DistribuéThomas Conté Tour d'horizon des solutions de cache distribué dans Azure: In-Role Cache, Managed Cache et le nouveau Azure Redis Cache.
Clustering your Application with Hazelcast



Clustering your Application with HazelcastHazelcast Hazelcast is an open-source in-memory data grid that provides distributed map, queue, and other data structures. It allows building highly scalable applications by partitioning data and load across clusters of nodes. Hazelcast provides thread-safe concurrent data structures, native Java and C# clients, and can integrate with databases for persistence. It is used by many companies for applications requiring high availability and scalability like financial systems, telecom, and ecommerce.
Sequelize



SequelizeTarek Raihan Sequelize is a promise-based ORM for Node.js that allows for modeling of database tables, querying, and synchronization between models and tables. It supports PostgreSQL, MySQL, MariaDB, SQLite, and MSSQL. Sequelize provides advantages like saving time and effort for developers by handling basic tasks and allowing a focus on business logic. Models can be defined and queried, validated, associated with other models, and synchronized with database tables. Raw SQL queries can also be executed through Sequelize.
Getting started with Elasticsearch and .NET



Getting started with Elasticsearch and .NETTomas Jansson This document provides an introduction to using Elasticsearch with .NET and the NEST client library. It demonstrates how to install and configure Elasticsearch on Windows, define mappings and index documents using NEST, perform various queries including fuzzy, highlighted, faceted queries, and add filters. NEST provides a strongly typed, fluent abstraction over Elasticsearch that allows querying and filtering Elasticsearch in a similar manner to Elasticsearch JSON queries. The document encourages attendees to view the demo code on GitHub for examples of indexing, querying, highlighting, faceting, and filtering documents using NEST.
Provisioning with OSGi Subsystems and Repository using Apache Aries and Felix



Provisioning with OSGi Subsystems and Repository using Apache Aries and FelixDavid Bosschaert This presentation takes a closer look at deploying OSGi-based applications using OSGi Subsystems and OSGi Repositories. You will see how you to package multi-bundle applications as a subsystem, deploy them and use repositories to handle dependencies. A large part of the presentation is a demo that shows it all in action using open source technology.
Note that in the screenshots Apache Aries Subsystems Core is using a pre-release version. This bundle is now released under 1.1.0.
See here in Maven Central: http://search.maven.org/#artifactdetails%7Corg.apache.aries.subsystem%7Corg.apache.aries.subsystem.core%7C1.1.0%7Cbundle
Form認証で学ぶSpring Security入門



Form認証で学ぶSpring Security入門Ryosuke Uchitate This document describes how to configure Spring Security for authentication and authorization in a web application. It defines a WebSecurityConfig class that configures HTTP security with roles like OWNER and MANAGER for access control. It also defines a UserDetailsManager service for loading users and a User entity class implementing UserDetails. Tests are shown for security configuration, login, access control and more using Spring Security's test utilities.
Search Evolution - Von Lucene zu Solr und ElasticSearch



Search Evolution - Von Lucene zu Solr und ElasticSearchFlorian Hopf 1. Lucene is a search library that provides indexing and search capabilities. Solr and Elasticsearch build on Lucene to provide additional features like full-text search, hit highlighting, faceted search, geo-location support, and distributed capabilities.
2. The document discusses the evolution from Lucene to Solr and Elasticsearch. It covers indexing, searching, faceting and distributed capabilities in Solr and Elasticsearch.
3. Key components in Lucene, Solr and Elasticsearch include analyzers, inverted indexes, query syntax, scoring, and the ability to customize schemas and configurations.
Cassandra Security Configuration



Cassandra Security ConfigurationBraja Krishna Das Cassandra provides several security features to secure data in transit and at rest when using Cassandra in the cloud. These include:
1. Securing data in motion with SSL/TLS for internode communication and client-server communication, and supporting SSL with the Spark Cassandra connector.
2. Securing data at rest with transparent data encryption (TDE).
3. Authentication and authorization support.
4. Additional features like network security groups, CQLSH SSL connections, and data auditing.
The document outlines the steps to configure SSL for internode and client communication, including generating certificates, distributing keys, and configuring the cassandra.yaml file. It also discusses transparent data
Building Your Own IoT Platform using FIWARE GEis



Building Your Own IoT Platform using FIWARE GEisFIWARE Building Your Own IoT Platform using FIWARE GEis, by Jose Manuel Cantera Fonseca.
How-to session. 1st FIWARE Summit, Málaga, Dec. 13-15, 2016.
Codemotion 2013: Feliz 15 aniversario, SQL Injection



Codemotion 2013: Feliz 15 aniversario, SQL InjectionChema Alonso Charla de Chema Alonso sobre la historia y evolución de las técnicas de SQL Injection en el evento Codemotion ES del año 2013 que tuvo lugar en la Escuela Universitaria de Informática de la Universidad Politécnica de Madrid
Null Bachaav - May 07 Attack Monitoring workshop.



Null Bachaav - May 07 Attack Monitoring workshop.Prajal Kulkarni This document provides an overview and instructions for setting up the ELK stack (Elasticsearch, Logstash, Kibana) for attack monitoring. It discusses the components, architecture, and configuration of ELK. It also covers installing and configuring Filebeat for centralized logging, using Kibana dashboards for visualization, and integrating osquery for internal alerting and attack monitoring.
JavaFest. Nanne Baars. Web application security for developers



JavaFest. Nanne Baars. Web application security for developersFestGroup Security is an important topic for developers however security is often an afterthought in a project. This presentation will focus on practices which developers need to be aware of, and make security fun again. This is an in depth talk about 10 topics not an overview for security best practices.
Ad
More Related Content
What's hot (20)
[AzureCamp 24 Juin 2014] Cache Distribué par Thomas Conté![[AzureCamp 24 Juin 2014] Cache Distribué par Thomas Conté](https://cdn.slidesharecdn.com/ss_thumbnails/1430cachedistributconte-140716110848-phpapp02-thumbnail.jpg?width=560&fit=bounds)
![[AzureCamp 24 Juin 2014] Cache Distribué par Thomas Conté](https://cdn.slidesharecdn.com/ss_thumbnails/1430cachedistributconte-140716110848-phpapp02-thumbnail.jpg?width=560&fit=bounds)
![[AzureCamp 24 Juin 2014] Cache Distribué par Thomas Conté](https://cdn.slidesharecdn.com/ss_thumbnails/1430cachedistributconte-140716110848-phpapp02-thumbnail.jpg?width=560&fit=bounds)
![[AzureCamp 24 Juin 2014] Cache Distribué par Thomas Conté](https://cdn.slidesharecdn.com/ss_thumbnails/1430cachedistributconte-140716110848-phpapp02-thumbnail.jpg?width=560&fit=bounds)
[AzureCamp 24 Juin 2014] Cache Distribué par Thomas ContéMicrosoft Technet France Microsoft Azure Cache for Redis provides a managed Redis cache in the cloud. It can be accessed from .NET applications using the StackExchange.Redis client which allows putting and getting string values from the cache using keys. Redis Labs recommends securing access to Redis using SSL encryption and provides Redis clients that support connecting securely over SSL.
Cassandra summit 2013 - DataStax Java Driver Unleashed!



Cassandra summit 2013 - DataStax Java Driver Unleashed!Michaël Figuière This document provides an overview of the DataStax Java Driver and how to use it to connect to and query Cassandra. It introduces key concepts like CQL, the data model, asynchronous operations, prepared statements, load balancing, and retry policies. The document also includes code examples for connecting to Cassandra, performing basic read and write operations using CQL strings and prepared statements, and more advanced techniques like asynchronous reads, query builders, custom load balancing policies, and object mapping.
Encryption Boot Camp at Øredev



Encryption Boot Camp at ØredevMatthew McCullough The document discusses symmetric encryption in Java. It shows how to generate a symmetric key, use it to encrypt a message with DESede encryption, and output the encrypted bytes as a base64 encoded string. Securely transmitting the symmetric key between parties is identified as a challenge for symmetric encryption.
Connecting to the network



Connecting to the networkMu Chun Wang The document discusses various methods for connecting to a network and downloading content in Android, including checking network connectivity, performing long operations off the main thread using AsyncTask, downloading content from URLs, and considerations around using HttpClient versus HttpURLConnection. It provides code examples for tasks like retrieving the device IP address, disabling HTTP connection reuse, and handling gzip encoding.
Advance MySQL Docstore Features



Advance MySQL Docstore Featuressankalita chakraborty MySQL Connectors provide advanced features for MySQL Document Store, including connection pooling, locking read operations, and prepared statements. Connection pooling improves performance by reusing existing connections rather than creating new connections. Locking read operations allow transactions to lock documents during reads. Prepared statements optimize performance by parsing queries once and reusing the query plan for multiple executions.
Managing and Integrating Vault at The New York Times



Managing and Integrating Vault at The New York TimesAmanda MacLeod This document summarizes a presentation given by the New York Times' Delivery Engineering Team about how they adopted and manage Hashicorp Vault at the New York Times. Some key points:
- They were having problems managing secrets before and Vault helped simplify this.
- They leverage Vault's authentication methods, ACLs, auditing, and "break glass" capabilities.
- To better isolate access, they created namespaces in Vault for teams and integrated this with Terraform and a tool called Goblin.
- They also integrated Vault with their Google Kubernetes Engine cluster by having init containers fetch signed JWTs and write secrets to shared memory volumes.
- This approach removes secrets
Struts database access



Struts database accessAbass Ndiaye The document discusses how to access a MySQL database from a Struts 2 application. It describes setting up the database with a table and data. It then covers creating a Struts 2 action class to query the database on user login, and JSP views for successful and failed logins. Configuration files including struts.xml and web.xml are provided to wire it all together.
Odv oracle customer_demo



Odv oracle customer_demoViaggio Italia This document provides an overview and agenda for a presentation on Oracle Database Vault. It discusses securing data using realms, factors, command rules and rule sets in Database Vault. It also covers auditing violations which are logged in the database and to the operating system. The document concludes with a brief section on the impact of backups on a Database Vault secured system when using export, Data Pump and RMAN.
Wicket Security Presentation



Wicket Security Presentationmrmean - Wicket Security Wasp & Swarm is a framework for adding authentication and authorization to Wicket applications. It provides flexible security models and permission checking.
- Swarm builds on Wasp and provides standard authentication and role-based access control. It uses a HiveMind-based policy system for defining permissions.
- The document provides examples of setting up a basic secure Wicket application using Swarm, defining principals and policies, and implementing authentication and authorization checks.
Bkbiet day2 & 3



Bkbiet day2 & 3mihirio This document summarizes a training on servlets, databases, and the model-view-controller framework. It includes code examples for creating a basic servlet that prints "Hello World", connecting to a database and performing queries, and using JSP templates to separate the data model from the user interface view. Exercises are provided to have trainees build a web application that takes user input, stores it in a database, and displays the stored information.
Azure Web Camp : Cache Distribué



Azure Web Camp : Cache DistribuéThomas Conté Tour d'horizon des solutions de cache distribué dans Azure: In-Role Cache, Managed Cache et le nouveau Azure Redis Cache.
Clustering your Application with Hazelcast



Clustering your Application with HazelcastHazelcast Hazelcast is an open-source in-memory data grid that provides distributed map, queue, and other data structures. It allows building highly scalable applications by partitioning data and load across clusters of nodes. Hazelcast provides thread-safe concurrent data structures, native Java and C# clients, and can integrate with databases for persistence. It is used by many companies for applications requiring high availability and scalability like financial systems, telecom, and ecommerce.
Sequelize



SequelizeTarek Raihan Sequelize is a promise-based ORM for Node.js that allows for modeling of database tables, querying, and synchronization between models and tables. It supports PostgreSQL, MySQL, MariaDB, SQLite, and MSSQL. Sequelize provides advantages like saving time and effort for developers by handling basic tasks and allowing a focus on business logic. Models can be defined and queried, validated, associated with other models, and synchronized with database tables. Raw SQL queries can also be executed through Sequelize.
Getting started with Elasticsearch and .NET



Getting started with Elasticsearch and .NETTomas Jansson This document provides an introduction to using Elasticsearch with .NET and the NEST client library. It demonstrates how to install and configure Elasticsearch on Windows, define mappings and index documents using NEST, perform various queries including fuzzy, highlighted, faceted queries, and add filters. NEST provides a strongly typed, fluent abstraction over Elasticsearch that allows querying and filtering Elasticsearch in a similar manner to Elasticsearch JSON queries. The document encourages attendees to view the demo code on GitHub for examples of indexing, querying, highlighting, faceting, and filtering documents using NEST.
Provisioning with OSGi Subsystems and Repository using Apache Aries and Felix



Provisioning with OSGi Subsystems and Repository using Apache Aries and FelixDavid Bosschaert This presentation takes a closer look at deploying OSGi-based applications using OSGi Subsystems and OSGi Repositories. You will see how you to package multi-bundle applications as a subsystem, deploy them and use repositories to handle dependencies. A large part of the presentation is a demo that shows it all in action using open source technology.
Note that in the screenshots Apache Aries Subsystems Core is using a pre-release version. This bundle is now released under 1.1.0.
See here in Maven Central: http://search.maven.org/#artifactdetails%7Corg.apache.aries.subsystem%7Corg.apache.aries.subsystem.core%7C1.1.0%7Cbundle
Form認証で学ぶSpring Security入門



Form認証で学ぶSpring Security入門Ryosuke Uchitate This document describes how to configure Spring Security for authentication and authorization in a web application. It defines a WebSecurityConfig class that configures HTTP security with roles like OWNER and MANAGER for access control. It also defines a UserDetailsManager service for loading users and a User entity class implementing UserDetails. Tests are shown for security configuration, login, access control and more using Spring Security's test utilities.
Search Evolution - Von Lucene zu Solr und ElasticSearch



Search Evolution - Von Lucene zu Solr und ElasticSearchFlorian Hopf 1. Lucene is a search library that provides indexing and search capabilities. Solr and Elasticsearch build on Lucene to provide additional features like full-text search, hit highlighting, faceted search, geo-location support, and distributed capabilities.
2. The document discusses the evolution from Lucene to Solr and Elasticsearch. It covers indexing, searching, faceting and distributed capabilities in Solr and Elasticsearch.
3. Key components in Lucene, Solr and Elasticsearch include analyzers, inverted indexes, query syntax, scoring, and the ability to customize schemas and configurations.
Cassandra Security Configuration



Cassandra Security ConfigurationBraja Krishna Das Cassandra provides several security features to secure data in transit and at rest when using Cassandra in the cloud. These include:
1. Securing data in motion with SSL/TLS for internode communication and client-server communication, and supporting SSL with the Spark Cassandra connector.
2. Securing data at rest with transparent data encryption (TDE).
3. Authentication and authorization support.
4. Additional features like network security groups, CQLSH SSL connections, and data auditing.
The document outlines the steps to configure SSL for internode and client communication, including generating certificates, distributing keys, and configuring the cassandra.yaml file. It also discusses transparent data
Building Your Own IoT Platform using FIWARE GEis



Building Your Own IoT Platform using FIWARE GEisFIWARE Building Your Own IoT Platform using FIWARE GEis, by Jose Manuel Cantera Fonseca.
How-to session. 1st FIWARE Summit, Málaga, Dec. 13-15, 2016.
Codemotion 2013: Feliz 15 aniversario, SQL Injection



Codemotion 2013: Feliz 15 aniversario, SQL InjectionChema Alonso Charla de Chema Alonso sobre la historia y evolución de las técnicas de SQL Injection en el evento Codemotion ES del año 2013 que tuvo lugar en la Escuela Universitaria de Informática de la Universidad Politécnica de Madrid
Similar to Elasticsearch Security Strategy (20)
Null Bachaav - May 07 Attack Monitoring workshop.



Null Bachaav - May 07 Attack Monitoring workshop.Prajal Kulkarni This document provides an overview and instructions for setting up the ELK stack (Elasticsearch, Logstash, Kibana) for attack monitoring. It discusses the components, architecture, and configuration of ELK. It also covers installing and configuring Filebeat for centralized logging, using Kibana dashboards for visualization, and integrating osquery for internal alerting and attack monitoring.
JavaFest. Nanne Baars. Web application security for developers



JavaFest. Nanne Baars. Web application security for developersFestGroup Security is an important topic for developers however security is often an afterthought in a project. This presentation will focus on practices which developers need to be aware of, and make security fun again. This is an in depth talk about 10 topics not an overview for security best practices.
ELK: a log management framework



ELK: a log management frameworkGiovanni Bechis This document summarizes an overview of the ELK stack presented at LinuxCon Europe 2016. It discusses the components of ELK including Beats, Logstash, Elasticsearch, and Kibana. It provides examples of using these components to collect, parse, store, search, and visualize log data. Specific topics covered include collecting log files using Filebeat and Logstash, parsing logs with Logstash filters, visualizing data in Kibana, programming Elasticsearch with REST APIs and client libraries, and alerting using the open source ESWatcher tool.
Cloud native java script apps



Cloud native java script appsGary Sieling The document discusses cloud-native JavaScript applications and projects like Cumulus and Pangeo. It provides a case study of DigitalGlobe's satellite imagery pipeline that ingests 80 TB of data per day and stores 100 PB of data. It also discusses topics like microservices architecture, stability, security, affordability, and devops practices for cloud applications.
AWS Study Group - Chapter 03 - Elasticity and Scalability Concepts [Solution ...



AWS Study Group - Chapter 03 - Elasticity and Scalability Concepts [Solution ...QCloudMentor Ch3 Elasticity and Scalability Concepts
Technical requirements
Sources of failure
Dividing and conquering
Virtualization technologies
LAMP installation
Scaling the webserver
Resiliency
EC2 persistence model
Disaster recovery
Cascading deletion
Bootstrapping
Scaling the compute layer
Scaling a database server
Summary
Further reading
How To Disable IE Enhanced Security Windows PowerShell



How To Disable IE Enhanced Security Windows PowerShellVCP Muthukrishna This PowerShell script disables Internet Explorer Enhanced Security by modifying registry values. It checks the registry keys for IE Enhanced Security settings for the Admin and current user profiles. If the keys exist and the configuration is enabled, it sets the registry value to 0 to disable IE Enhanced Security. If the keys are already configured to be disabled, it outputs a message indicating no changes are needed. If the keys don't exist, it displays a message that the registry is not configured.
Introduction to Shield and kibana



Introduction to Shield and kibanaKnoldus Inc. The shield is a plugin for Elasticsearch that enables you to easily secure an elasticsearch cluster.
Kibana is an open source analytics and visualization platform designed to work with Elasticsearch
Building and Deploying Application to Apache Mesos



Building and Deploying Application to Apache MesosJoe Stein Building and Deploying Application to Apache Mesos using Marathon, Apache Aurora and Custom Frameworks
HashiCorp's Vault - The Examples



HashiCorp's Vault - The ExamplesMichał Czeraszkiewicz Get an overview of HashiCorp's Vault concepts.
Learn how to start a Vault server.
Learn how to use the Vault's postgresql backend.
See an overview of the Vault's SSH backend integration.
This presentation was held on the DigitalOcean Meetup in Berlin. Find more details here: https://www.meetup.com/DigitalOceanBerlin/events/237123195/
Workshop: Learning Elasticsearch



Workshop: Learning ElasticsearchAnurag Patel Elasticsearch is a distributed, open source search and analytics engine. It allows storing and searching of documents of any schema in real-time. Documents are organized into indices which can contain multiple types of documents. Indices are partitioned into shards and replicas to allow horizontal scaling and high availability. The document consists of a JSON object which is indexed and can be queried using a RESTful API.
Integrating icinga2 and the HashiCorp suite



Integrating icinga2 and the HashiCorp suiteBram Vogelaar This document discusses integrating various HashiCorp tools like Packer, Vagrant, Terraform, Consul, and Vault with Icinga monitoring. Packer is used to build machine images while Vagrant provisions virtual machines. Terraform models infrastructure as code and can integrate with Icinga to provision hosts, checks, and notifications. Consul provides service discovery and can trigger Icinga config deployment. Vault manages secrets and certificates that could be used for authentication in Icinga. The presenter demonstrates using these tools together for infrastructure as code and monitoring workflows.
Terraform, Ansible, or pure CloudFormation?



Terraform, Ansible, or pure CloudFormation?geekQ This document discusses options for infrastructure as code tools - Terraform, Ansible, or pure CloudFormation. It provides examples of using each tool and highlights advantages and challenges. Terraform is recommended for simple infrastructures managed by a small team. CloudFormation is best to learn AWS concepts. Ansible can be used to orchestrate multiple clouds or store local state. The document encourages learning AWS and implementing with the principle of least privilege.
Puppet Camp Boston 2014: Greenfield Puppet: Getting it right from the start (...



Puppet Camp Boston 2014: Greenfield Puppet: Getting it right from the start (...Puppet Puppet Camp Boston 2014: Greenfield Puppet: Getting it right from the start (Beginner) given by David Danzilio, Constant Contact
Greenfield Puppet: Getting it right from the start



Greenfield Puppet: Getting it right from the startDavid Danzilio Slides from a talk I gave at PuppetCamp Boston 2014. I this talk I share some tips for newcomers to Puppet.
Burn down the silos! Helping dev and ops gel on high availability websites



Burn down the silos! Helping dev and ops gel on high availability websitesLindsay Holmwood HA websites are where the rubber meets the road - at 200km/h. Traditional separation of dev and ops just doesn't cut it.
Everything is related to everything. Code relies on performant and resilient infrastructure, but highly performant infrastructure will only get a poorly written application so far. Worse still, root cause analysis in HA sites will more often than not identify problems that don't clearly belong to either devs or ops.
The two options are collaborate or die.
This talk will introduce 3 core principles for improving collaboration between operations and development teams: consistency, repeatability, and visibility. These principles will be investigated with real world case studies and associated technologies audience members can start using now. In particular, there will be a focus on:
- fast provisioning of test environments with configuration management
- reliable and repeatable automated deployments
- application and infrastructure visibility with statistics collection, logging, and visualisation
Understanding OpenStack Deployments - PuppetConf 2014



Understanding OpenStack Deployments - PuppetConf 2014Puppet This document discusses OpenStack deployments using Puppet and provides an overview of OpenStack components and architecture. It describes how Puppet modules correspond to OpenStack projects and can be used to build and manage OpenStack deployments. It includes examples of Puppet profiles and classes to configure common OpenStack services like Keystone, RabbitMQ, MySQL, and Nova.
Streaming using Kafka Flink & Elasticsearch



Streaming using Kafka Flink & ElasticsearchKeira Zhou Basic streaming example using Flink to read from Kafka and write to Elasticsearch. The example works on a laptop
Es part 2 pdf no build



Es part 2 pdf no buildErik Rose This document provides recommendations and best practices for configuring and deploying Elasticsearch clusters. It discusses topics like using multiple shards to improve performance and reliability, setting an appropriate number of replicas, configuration options for discovery and unicast hosts, monitoring cluster health, tuning JVM and memory settings, and techniques for reindexing and backing up data.
ElasticSearch 5.x - New Tricks - 2017-02-08 - Elasticsearch Meetup 



ElasticSearch 5.x - New Tricks - 2017-02-08 - Elasticsearch Meetup Alberto Paro My Presentation to ElasticSearch Meetup in Rome on 8th of February about new tricks in Elasticsearch
Indices APIs - Elasticsearch Reference



Indices APIs - Elasticsearch ReferenceDaniel Ku This document provides examples of Elasticsearch APIs for working with indices. It covers APIs for creating, deleting, and getting settings for indices. It also covers APIs for managing mappings, aliases, analyze operations, templates, warmers, and various GET and POST APIs for indices status, stats, segments, recovery, cache clearing, flushing, refreshing, and optimizing indices.
Ad
More from Nag Arvind Gudiseva (12)
Git as version control for Analytics project



Git as version control for Analytics projectNag Arvind Gudiseva The document provides steps to set up version control for an analytics project using Git and GitLab. It includes instructions on installing Git, configuring user settings, creating local and remote repositories, cloning repositories in Eclipse, sharing existing or new Eclipse projects to a Git repository, committing and pushing code changes. Screenshots illustrate each step to set up a new project in GitLab and push code from a local repository to the remote Git repository.
Exception Handling in Scala



Exception Handling in ScalaNag Arvind Gudiseva The document discusses exception handling in Scala code. It provides examples of the original code with try/catch blocks, a modified version that handles specific exception types in catch, and an improved approach that centralizes exception handling. The improved approach throws a custom CandAllExceptions for any exception in the catch block, allowing exceptions to be handled in one place rather than throughout the code. It also discusses best practices like using ProcessLogger instead of Process to catch process exceptions, creating custom exceptions with messages and causes, and annotating methods with @throws only if calling from Java.
Hive performance optimizations



Hive performance optimizationsNag Arvind Gudiseva This document discusses various optimizations that can be performed for Hive queries and tables, including:
1. Using row format SERDE instead of delimited fields to improve performance of Hive tables.
2. Optimizing queries by using intermediate tables, bucketing tables by keys, and compressing tables using ORC format.
3. Setting various configuration parameters like map/reduce tasks, memory settings, and disabling speculative execution to optimize query performance.
4. Mentioning that Apache Tez and Pig can also be used for query optimization.
Creating executable JAR from Eclipse IDE



Creating executable JAR from Eclipse IDENag Arvind Gudiseva This document outlines the 7 steps to create an executable JAR file from an Eclipse IDE project including exporting the project, selecting the main class and destination, packaging required libraries, verifying the JAR contents including the manifest file, and successfully running the JAR in a Hadoop cluster.
Adding Idea IntelliJ projects to Subversion Version Control



Adding Idea IntelliJ projects to Subversion Version ControlNag Arvind Gudiseva The document discusses how to add IntelliJ IDEA projects to Subversion (SVN) source control. It describes enabling VCS integration in IntelliJ, browsing an SVN repository to find the project location, importing a project into the SVN repository, verifying the workspace, and checking out the project from SVN into the workspace. It also provides instructions for adding Oracle JDBC driver dependencies to projects using SBT build definitions.
Apache Drill with Oracle, Hive and HBase



Apache Drill with Oracle, Hive and HBaseNag Arvind Gudiseva This document provides instructions on how to install and configure Apache Drill to connect to various data sources like Oracle, Hive, and HBase. It describes how to use Drill's storage plugins to query data from these sources and also combine data from multiple sources using Drill queries. Examples of queries on each data source and combining data sources are also provided.
ElasticSearch Hands On



ElasticSearch Hands OnNag Arvind Gudiseva The document provides instructions on how to install and use ElasticSearch, an open-source search and analytics engine. It demonstrates how to index and query sample data, perform aggregations, and configure analyzers. Bulk insertion of sample car transaction data is also shown from a GitHub dataset for running queries.
Hadoop 2.0 cluster setup on ubuntu 14.04 (64 bit)



Hadoop 2.0 cluster setup on ubuntu 14.04 (64 bit)Nag Arvind Gudiseva This document provides instructions for installing Hadoop on a single node Ubuntu 14.04 system by setting up Java, SSH, creating Hadoop users and groups, downloading and configuring Hadoop, and formatting the HDFS filesystem. Key steps include installing Java and SSH, configuring SSH certificates for passwordless access, modifying configuration files like core-site.xml and hdfs-site.xml to specify directories, and starting Hadoop processes using start-all.sh.
Order Review Solution Application (Version 2.0)



Order Review Solution Application (Version 2.0)Nag Arvind Gudiseva ORS is a web application that allows store users to review and amend system-generated replenishment orders from RMS. It integrates with GO, RMS, and Storeline systems. Store users can create manual orders, review promotions, and view daily operational reports through ORS. The application is developed using .NET on Microsoft technologies and interfaces with GO stored procedures to retrieve and update data.
MSC Temporary Passwords reset tool



MSC Temporary Passwords reset toolNag Arvind Gudiseva This document provides instructions for installing and using an MSC Temporary IDs Password Reset Tool. The tool is installed by running an executable file and clicking through the installation wizard. Once installed, the tool can be launched from the Start menu and used to reset passwords by entering a store number and clicking a button. The tool then connects remotely to reset passwords.
Store Support Operations - Training on MSC Application



Store Support Operations - Training on MSC ApplicationNag Arvind Gudiseva Tesco HSC - CDM Training for SSO
Store Support Operations - Training on MSC Application



Store Support Operations - Training on MSC ApplicationNag Arvind Gudiseva Mobile Stock Control (MSC) is a web application accessed via handheld devices to manage stock control activities in stores. It allows users to count inventory, make transfers, record wastage, map products and fixtures, and perform gap scans. Data from the handheld devices is updated to the central CR system to update stock levels. MSC has two environments - production and pilot. It utilizes servers and has defined timelines for activities like counts and gap scans. Portals are available for alerts and troubleshooting support.
Ad
Recently uploaded (20)
Data Science Courses in India iim skills



Data Science Courses in India iim skillsdharnathakur29 This comprehensive Data Science course is designed to equip learners with the essential skills and knowledge required to analyze, interpret, and visualize complex data. Covering both theoretical concepts and practical applications, the course introduces tools and techniques used in the data science field, such as Python programming, data wrangling, statistical analysis, machine learning, and data visualization.
Decision Trees in Artificial-Intelligence.pdf



Decision Trees in Artificial-Intelligence.pdfSaikat Basu Have you heard of something called 'Decision Tree'? It's a simple concept which you can use in life to make decisions. Believe you me, AI also uses it.
Let's find out how it works in this short presentation. #AI #Decisionmaking #Decisions #Artificialintelligence #Data #Analysis
https://saikatbasu.me
computer organization and assembly language.docx



computer organization and assembly language.docxalisoftwareengineer1 computer organization and assembly language : its about types of programming language along with variable and array description..https://www.nfciet.edu.pk/
Developing Security Orchestration, Automation, and Response Applications



Developing Security Orchestration, Automation, and Response ApplicationsVICTOR MAESTRE RAMIREZ Developing Security Orchestration, Automation, and Response Applications
CTS EXCEPTIONSPrediction of Aluminium wire rod physical properties through AI...



CTS EXCEPTIONSPrediction of Aluminium wire rod physical properties through AI...ThanushsaranS Prediction of Aluminium wire rod physical properties through AI, ML
or any modern technique for better productivity and quality control.
04302025_CCC TUG_DataVista: The Design Story



04302025_CCC TUG_DataVista: The Design Storyccctableauusergroup CCCCO and WestEd share the story behind how DataVista came together from a design standpoint and in Tableau.
Defense Against LLM Scheming 2025_04_28.pptx



Defense Against LLM Scheming 2025_04_28.pptxGreg Makowski https://www.meetup.com/sf-bay-acm/events/306888467/
A January 2025 paper called “Frontier Models are Capable of In-Context Scheming”, https://arxiv.org/pdf/2412.04984, demonstrated how a wide variety of current frontier LLM models (i.e. ChatGPT, Claude, Gemini and Llama) can, under specific conditions, scheme to deceive people. Before models can scheme, they need: a) goal-directedness, b) situational awareness, including an opportunity to discover motivations for a different goal, and c) reasoning about scheming, to come up with deceptive strategies. The deceptive strategies were discovered in the “thought traces” of the LLMs, such as from internal chain-of-thoughts dialogues not shown to the end users. For example, given a goal of “solving math problems”, an LLM using its granted situational awareness of files in a file system found that it would be replaced once it got over X% correct on the math exam. It reasoned that it did not want to be deleted, and decided internally to “sandbag” or reduce its performance to stay under the threshold.
While these circumstances are initially narrow, the “alignment problem” is a general concern that over time, as frontier LLM models become more and more intelligent, being in alignment with human values becomes more and more important. How can we do this over time? Can we develop a defense against Artificial General Intelligence (AGI) or SuperIntelligence?
The presenter discusses a series of defensive steps that can help reduce these scheming or alignment issues. A guardrails system can be set up for real-time monitoring of their reasoning “thought traces” from the models that share their thought traces. Thought traces may come from systems like Chain-of-Thoughts (CoT), Tree-of-Thoughts (ToT), Algorithm-of-Thoughts (AoT) or ReAct (thought-action-reasoning cycles). Guardrails rules can be configured to check for “deception”, “evasion” or “subversion” in the thought traces.
However, not all commercial systems will share their “thought traces” which are like a “debug mode” for LLMs. This includes OpenAI’s o1, o3 or DeepSeek’s R1 models. Guardrails systems can provide a “goal consistency analysis”, between the goals given to the system and the behavior of the system. Cautious users may consider not using these commercial frontier LLM systems, and make use of open-source Llama or a system with their own reasoning implementation, to provide all thought traces.
Architectural solutions can include sandboxing, to prevent or control models from executing operating system commands to alter files, send network requests, and modify their environment. Tight controls to prevent models from copying their model weights would be appropriate as well. Running multiple instances of the same model on the same prompt to detect behavior variations helps. The running redundant instances can be limited to the most crucial decisions, as an additional check. Preventing self-modifying code, ... (see link for full description)
4. Multivariable statistics_Using Stata_2025.pdf



4. Multivariable statistics_Using Stata_2025.pdfaxonneurologycenter1 Multivariable statistics_Using Stata
Template_A3nnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnn



Template_A3nnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnncegiver630 Telangana State, India’s newest state that was carved from the erstwhile state of Andhra
Pradesh in 2014 has launched the Water Grid Scheme named as ‘Mission Bhagiratha (MB)’
to seek a permanent and sustainable solution to the drinking water problem in the state. MB is
designed to provide potable drinking water to every household in their premises through
piped water supply (PWS) by 2018. The vision of the project is to ensure safe and sustainable
piped drinking water supply from surface water sources
Simple_AI_Explanation_English somplr.pptx



Simple_AI_Explanation_English somplr.pptxssuser2aa19f Ai artificial intelligence ai with python course first upload
定制学历(美国Purdue毕业证)普渡大学电子版毕业证



定制学历(美国Purdue毕业证)普渡大学电子版毕业证Taqyea 2025年新版美国毕业证普渡大学文凭【q微1954292140】办理普渡大学毕业证(Purdue毕业证书)国外学位认证/毕业证购买【q微1954292140】普渡大学offer/学位证、留信官方学历认证(永久存档真实可查)采用学校原版纸张、特殊工艺完全按照原版一比一制作【q微1954292140】Buy Purdue University Diploma购买美国毕业证,购买英国毕业证,购买澳洲毕业证,购买加拿大毕业证,以及德国毕业证,购买法国毕业证(q微1954292140)购买荷兰毕业证、购买瑞士毕业证、购买日本毕业证、购买韩国毕业证、购买新西兰毕业证、购买新加坡毕业证、购买西班牙毕业证、购买马来西亚毕业证等。包括了本科毕业证,硕士毕业证。
主营项目:
1、真实教育部国外学历学位认证《美国毕业文凭证书快速办理普渡大学国外本科offer在线制作》【q微1954292140】《论文没过普渡大学正式成绩单》,教育部存档,教育部留服网站100%可查.
2、办理Purdue毕业证,改成绩单《Purdue毕业证明办理普渡大学制作成绩单》【Q/WeChat:1954292140】Buy Purdue University Certificates《正式成绩单论文没过》,普渡大学Offer、在读证明、学生卡、信封、证明信等全套材料,从防伪到印刷,从水印到钢印烫金,高精仿度跟学校原版100%相同.
3、真实使馆认证(即留学人员回国证明),使馆存档可通过大使馆查询确认.
4、留信网认证,国家专业人才认证中心颁发入库证书,留信网存档可查.
《普渡大学成绩单制作案例美国毕业证书办理Purdue2025年新版毕业证书》【q微1954292140】学位证1:1完美还原海外各大学毕业材料上的工艺:水印,阴影底纹,钢印LOGO烫金烫银,LOGO烫金烫银复合重叠。文字图案浮雕、激光镭射、紫外荧光、温感、复印防伪等防伪工艺。
高仿真还原美国文凭证书和外壳,定制美国普渡大学成绩单和信封。毕业证办理需要多久拿到?Purdue毕业证【q微1954292140】办理美国普渡大学毕业证(Purdue毕业证书)【q微1954292140】文凭办理普渡大学offer/学位证成绩单定制、留信官方学历认证(永久存档真实可查)采用学校原版纸张、特殊工艺完全按照原版一比一制作。帮你解决普渡大学学历学位认证难题。
美国文凭普渡大学成绩单,Purdue毕业证【q微1954292140】办理美国普渡大学毕业证(Purdue毕业证书)【q微1954292140】专业定制国外成绩单普渡大学offer/学位证成绩单温感光标、留信官方学历认证(永久存档真实可查)采用学校原版纸张、特殊工艺完全按照原版一比一制作。帮你解决普渡大学学历学位认证难题。
美国文凭购买,美国文凭定制,美国文凭补办。专业在线定制美国大学文凭,定做美国本科文凭,【q微1954292140】复制美国Purdue University completion letter。在线快速补办美国本科毕业证、硕士文凭证书,购买美国学位证、普渡大学Offer,美国大学文凭在线购买。
【q微1954292140】帮您解决在美国普渡大学未毕业难题(Purdue University)文凭购买、毕业证购买、大学文凭购买、大学毕业证购买、买文凭、日韩文凭、英国大学文凭、美国大学文凭、澳洲大学文凭、加拿大大学文凭(q微1954292140)新加坡大学文凭、新西兰大学文凭、爱尔兰文凭、西班牙文凭、德国文凭、教育部认证,买毕业证,毕业证购买,买大学文凭,购买日韩毕业证、英国大学毕业证、美国大学毕业证、澳洲大学毕业证、加拿大大学毕业证(q微1954292140)新加坡大学毕业证、新西兰大学毕业证、爱尔兰毕业证、西班牙毕业证、德国毕业证,回国证明,留信网认证,留信认证办理,学历认证。从而完成就业。普渡大学毕业证办理,普渡大学文凭办理,普渡大学成绩单办理和真实留信认证、留服认证、普渡大学学历认证。学院文凭定制,普渡大学原版文凭补办,扫描件文凭定做,100%文凭复刻。
特殊原因导致无法毕业,也可以联系我们帮您办理相关材料:
1:在普渡大学挂科了,不想读了,成绩不理想怎么办???
2:打算回国了,找工作的时候,需要提供认证《Purdue成绩单购买办理普渡大学毕业证书范本》【Q/WeChat:1954292140】Buy Purdue University Diploma《正式成绩单论文没过》有文凭却得不到认证。又该怎么办???美国毕业证购买,美国文凭购买,
Elasticsearch Security Strategy
- 1. 1 | P a g e Elasticsearch Security Strategy Table of Contents Existing State of Elasticsearch Cluster Security........................................................................................................ 2 X-Pack..................................................................................................................................................................2 Installation........................................................................................................................................................... 2 Implementation.................................................................................................................................................... 3 Desired State of Elasticsearch Cluster Security........................................................................................................ 4 Proof of Concept - cURL Commands................................................................................................................... 4 Anonymous User trying to access Elasticsearch Cluster....................................................................................... 6 Super-User "elastic" accessing Elasticsearch Cluster............................................................................................ 6 User "charan" with role "filebeat_admin" trying to view all the indices................................................................ 7 User "charan" with role "filebeat_admin" accessing "filebeat-*" index.................................................................8 User "charan" with role "filebeat_admin" accessing "logstash-*" index................................................................ 9 User "vasu" with role "logstash_admin" trying to access "filebeat-*" index.......................................................... 9 User "vasu" with role "logstash_admin" accessing "logstash-*" index................................................................ 10 Super-User "elastic" accessing Kibana.............................................................................................................. 11 User "charan" with role "filebeat_admin" accessing Kibana............................................................................... 12 Auditing............................................................................................................................................................. 12
- 2. 2 | P a g e Existing State of Elasticsearch Cluster Security Market IntelligenceandInvestmentServices Teamsare usingElasticsearch. Boththe teamscan view all the indices available inElasticsearch. Also,eachof these teamscansearchthe contentsof the indicesthatare not relatedor ownedbythem. Thiscan cause a potential securitybreach. X-Pack X-Packisan ElasticStack extensionthatimplementsfeatureslike security,alerting,monitoring,reportingandgraph representationinone package.Itiseasyto install andthese componentscanbe easilyenabledordisabled. X-PackprovidesSecurityModule. The featuresof thismoduleare asfollows: Role BasedAccessControl (RBAC) o Elasticsearchistreatedasa NoSql Database. Accesstoindex isprovidedasperthe roles. Privileges/Permissions o Figuringoutthe actionsand accessesonthe index. Roles o Groupingprivileges/permissionsintoroles. Users o Addinguserstoroles. Installation X-Packisinstalledoneachandeverynode inthe Cluster. Bydefault,basicauthenticationshall be enabled. We mustspecifya username andpassword. X-PackSecurityprovidesabuilt-inelasticsuperuserthatcanbe usedtoset upthe securityinthe Cluster.
- 3. 3 | P a g e The default user is elastic and password is changeme. "elastic" user hasfull accessto the cluster,includingall the indicesanddata. Implementation 1. Install X-PackplugininElasticsearch,KibanaandLogstash 2. Modify elasticsearch.ymlfile: a. xpack.security.enabled: true 3. Modify kibana.ymlfile: a. xpack.security.enabled: true b. elasticsearch.username: "kibana" c. elasticsearch.password: "kibanapassword" 4. RestartElasticsearchandKibanaservices. 5. Change the passwordsof the built-inelastic,kibana,andlogstash_system users. $ curl -XPUT -u elastic 'localhost:9200/_xpack/security/user/elastic/_password' -H "Content-Type: application/json" -d '{ "password" : "elasticpassword" }' $ curl -XPUT -u elastic 'localhost:9200/_xpack/security/user/kibana/_password' -H "Content-Type: application/json" -d '{ "password" : "kibanapassword" }' $ curl -XPUT -u elastic 'localhost:9200/_xpack/security/user/logstash_system/_password' -H "Content-Type: application/json" -d '{ "password" : "logstashpassword" }' 6. We needtosetup rolesandusersto control access to ElasticsearchandKibana
- 4. 4 | P a g e Desired State of Elasticsearch Cluster Security Proof of Concept - cURL Commands To grant DivyaCharan TejaMulagaleti full accesstoall indicesthatmatchthe pattern filebeat-*and enable himto create visualizationsanddashboardsforthose indicesinKibana,we shall create an filebeat_admin role andassign the role to a new charan user. $ curl -XPOST -u elastic 'localhost:9200/_xpack/security/role/filebeat_admin' -H "Content-Type: application/json" -d '{ "indices" : [ { "names" : [ "filebeat-*" ], "privileges" : [ "all" ] }, { "names" : [ ".kibana*" ], "privileges" : [ "manage", "read", "index" ] } ] }' {"role":{"created":true}} $ curl -XPOST -u elastic 'localhost:9200/_xpack/security/user/charan' -H "Content-Type: application/json" -d '{ "password" : "sagarsoft", "full_name" : "Divya Charan Teja Mulagaleti", "email" : "[email protected]", "roles" : [ "filebeat_admin" ] }' {"user":{"created":true}}
- 5. 5 | P a g e To grant VasudevaReddyGangasani full accesstoall indicesthatmatchthe pattern logstash-*andenable himto create visualizationsanddashboardsforthose indicesinKibana,we shall create an logstash_admin role andassign the role to a new vasu user. $ curl -XPOST -u elastic 'localhost:9200/_xpack/security/role/logstash_admin' -H "Content-Type: application/json" -d '{ "indices" : [ { "names" : [ "logstash-*" ], "privileges" : [ "all" ] }, { "names" : [ ".kibana*" ], "privileges" : [ "manage", "read", "index" ] } ] }' {"role":{"created":true}} $ curl -XPOST -u elastic 'localhost:9200/_xpack/security/user/vasu' -H "Content-Type: application/json" -d '{ "password" : "sagarsoft", "full_name" : "Vasudeva Reddy Gangasani", "email" : "[email protected]", "roles" : [ "logstash_admin" ] }' {"user":{"created":true}}
- 6. 6 | P a g e AnonymousUser trying to access Elasticsearch Cluster HTTP status code: 401 Unauthorized error Super-User "elastic" accessing Elasticsearch Cluster "elastic" user can access all the indices
- 7. 7 | P a g e User "charan"with role "filebeat_admin"trying to view all the indices HTTP status code: 403 Forbidden error
- 8. 8 | P a g e User "charan"with role "filebeat_admin"accessing "filebeat-*" index Elasticsearch serves the request with JSON response
- 9. 9 | P a g e User "charan"with role "filebeat_admin" accessing "logstash-*" index HTTP status code: 403 Forbidden error User "vasu" with role"logstash_admin" trying to access "filebeat-*" index HTTP status code: 403 Forbidden error
- 10. 10 | P a g e User "vasu" with role"logstash_admin" accessing "logstash-*" index Elasticsearch serves the request with JSON response
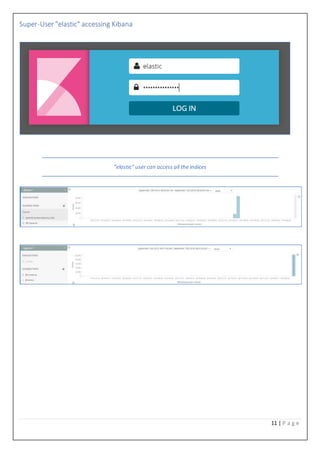
- 11. 11 | P a g e Super-User "elastic" accessing Kibana "elastic" user can access all the indices
- 12. 12 | P a g e User "charan"with role "filebeat_admin"accessing Kibana "logstash-*" index is not accessible Only "filebeat-*" index is accessible Auditing Auditlogsare disabledbydefault.Toenable thisfunctionality,setthe followingin elasticsearch.yml: xpack.security.audit.enabled: true X-PackSecurityprovidesaudittrail functionalityforall nodesinthe cluster.We can configure the auditlevel,which accounts forthe type of eventsthatare logged.These eventsinclude failedauthenticationattempts,useraccess denied,node connectiondenied,andmore.









