Ad
Elevate your Splunk Deployment by Better Understanding your Value Breakfast Session
- 1. Copyright © 2016 Splunk, Inc. Elevate your Splunk Deployment by Better Understanding your Value David Caradonna Director, Global Business Value Consulting [email protected] March, 2016
- 2. Copyright © 2016 Splunk, Inc. 2 Top Use Cases and Data Sources 3 Data Source Assessment Tool 4 Summary / Q&A 1 Business Value at Splunk Today’s Presentation
- 3. Copyright © 2016 Splunk, Inc. Maximize benefits gained from machine data by prescribing enterprise value plans that directly support our customer’s corporate objectives and enable broader impact across their business Business Value Consulting at Splunk • Should Splunk be a priority? • How much value can be realize? • Which data should be indexed? • What’s the investment and ROI? • Can Cloud be less expensive? • How is Splunk currently utilized? • How much value has been realized? • More value to be realized with current data? • Who else can benefit from this data? • When and how to establish a Splunk COE? Servicing Customers for 3 Years | 700+ Engagements Worldwide
- 4. Copyright © 2016 Splunk, Inc. Splunk should not be a Hidden Gem 4 I was never able to do this before! What business value do I get? I can search Syslog way faster now!
- 5. Copyright © 2016 Splunk, Inc. Today’s Focus Based on FY16Q3 activity Security, Compliance, and Fraud Business Analytics Industrial Data and the Internet of Things IT Operations Application Delivery Common Value Drivers | Common Data Sources
- 6. Copyright © 2016 Splunk, Inc. IT Operational Analytics (ITOA) An overview of Splunk efficiencies and Most Common Data Sources as reported by Splunk Customers IT Operations NOC, Server, Storage, Network Admins, DBA, Middleware, Application Support Teams
- 7. Copyright © 2016 Splunk, Inc. TOP 4 Use Cases for ITOA Root Cause Analysis Up to 30% unknown root causes, causing incidents to recur Incident Troubleshooting Lengthy log analysis done manual Incident Triage All hands on deck, taking up 30 to 40 minutes Failure detection Customer often informs IT Before Splunk Service Restoration Fix is implemented #4 Faster and more comprehensive root cause analysis helping to reduce incident recurrence #3 Faster investigation (MTTI) through rapid log search and correlation conducted in conjunction by different teams (everyone looks at the same data) #2 Faster triage often conducted by 1st level staff without all hands on deck #1 Better detection customer is notified by IT With Splunk Fix is implemented Event Mgmt Incident Mgmt Problem Mgmt
- 8. Copyright © 2016 Splunk, Inc. Benchmarking Splunk Customer Success Documented through 700+ engagements worldwide Reduced Sev1 and Sev2 incidents by 43% Reduced MTTR by 95% and reduce escalations by 50% Improved API performance by 50% reducing need for infrastructure upgrades and increasing user satisfaction 15-45% reduction in high priority incidents 70-90% reduction in incident investigation time 67-82% reduction in business impact 5-20% increase in infrastructure capacity utilization Customer Feedback IT Operations Analytics (ITOA)
- 9. Copyright © 2016 Splunk, Inc. Network Server & Storage • SNMP • DHCP • Firewall • Load Balancer • Network Switches • Network Routers (cisco_cdr, cisco:asa, cisco_syslog, clavister) • Netflow • Proxies Application • OS Logs (ntsyslog, snare, dhcpd, linux_secure, aix_secure, osx_secure, syslog, PERFMON:CPUTime, PERFMON:FreeDiskSpace, Win:Event, etc.) • VMWare server logs • AWS Logs (CloudTrail, CloudWatch, Config, S3, etc.) • MS Azure Logs (WADEventLogs, WADPerformanceCounter, WADDiagnostInfrastructure, etc.) • Backup logs • Storage logs Common Data Sources Documented through 700+ engagements worldwide Middleware & Database • Java – J2EE (log4J, JMS, MQ, TibcoEMS, HornetQ, RabbitMQ, Native JMS, Weblogic JMS, etc.) • Middleware (Tibco, Software AG etc.) • Web Server (access_combined, access_combined_wcookie, access_common, apache_error, iis, nginx, etc.) • Application Server (log4j, log4php, weblogic_stdout, websphere_activity, websphere_core, websphere_trlog, etc.) • Mobile Devices • Database error logs • Application Error Logs • Application Performance and Usage Logs • Application Authentication Logs • Business Process Logs (Payments status, batch upload status, customer order status, etc.) • Mail Server Logs IT Operations Analytics (ITOA)
- 10. Copyright © 2016 Splunk, Inc. Application Delivery Application Delivery An overview of Splunk efficiencies and Most Common Data Sources as reported by Splunk Customers Developers, Testers, Project Managers AND DBAs, Middleware, Application Support Teams
- 11. Copyright © 2016 Splunk, Inc. TOP 6 Use Cases for Application Delivery typical SDLC #4 Faster delivery of dashboards provide real-time visibility across all technology layers involved in processing business service transactions so bottlenecks can be swiftly identified and addressed #5 Faster Mean Time to Market on key projects through faster test failure analysis and defect remediation #6 Increased release value through improved visibility on feature efficiency patterns in order to better assess needs for future releases #2 Faster pre-production defect remediation through improved investigation of root causes #1 Faster test failure analysis for functional, performance and security test runs through analysis of test logs #3 Fewer escalations to developers from fewer production outages means developers are more focused on innovating the business
- 12. Copyright © 2016 Splunk, Inc. Benchmarking Splunk Customer Success Documented through 700+ engagements worldwide Application Delivery Shortened development cycles by 30% Reduced reporting time by 88% Increased release cycles by 8x with no additional staff Customer Feedback 80-90% faster development of reports and dashboards 70-90% reduction in time for QA test failure analysis 70-90% reduction in time for pre-prod defect investigation 10-50% improvement in time to market
- 13. Copyright © 2016 Splunk, Inc. SDLC Application Delivery Common Data Sources Documented through 700+ engagements worldwide Middleware & Database • Java – J2EE (log4J, JMS, MQ, TibcoEMS, HornetQ, RabbitMQ, Native JMS, Weblogic JMS, etc.) • Middleware (Tibco, Software AG etc.) • Web Server (access_combined, access_combined_wcookie, access_common, apache_error, iis, nginx, etc.) • Application Server (log4j, log4php, weblogic_stdout, websphere_activity, websphere_core, websphere_trlog, etc.) • Mobile Devices • Database error logs • Performance Test Logs • Functional Test Logs • Security Test Logs • Debug Logs • Release Error Logs • Code Management Logs Application • Apache Web Logs • Application Error Logs • Application Performance Logs • Application Authentication Logs • Business Process Logs (Payments status, batch upload status, customer order status, etc.) • Mail Server Logs
- 14. Copyright © 2016 Splunk, Inc. Security, Compliance and Fraud Security, Compliance, and Fraud An overview of Splunk efficiencies and Most Common Data Sources as reported by Splunk Customers Security Analysts, SOC, Compliance, Audit, Fraud teams
- 15. Copyright © 2016 Splunk, Inc. Assess Risk Deep Analysis Monitor Controls Audit & Comply TOP 4 Use Cases for Security & Compliance #4 Continuous compliance on ALL components and policies resulting in faster and simpler audits #3 Faster implementation of critical security controls (ex: CIS Top 20) across ALL layers of the organization, ultimately resulting in full enterprise visibility and a reduction in risks #2 Faster deep dive investigation on security incidents that require further proactive and reactive analysis #1 Faster 1st level triage on ALL security attacks with less resources as opposed to reviewing only a subset of attacks Web Threats Mobile & IOT Vulnerabilities Scams & Social Media Targeted Attacks Data Breaches E-Crime & Malware
- 16. Copyright © 2016 Splunk, Inc. Security, Compliance & Fraud 70-90% faster detection and triage of security events 70-90% faster investigation of security incidents 70-90% reduction in compliance reporting time 10-50% reduction in risk of data breach, IP theft, fraud Customer Feedback Benchmarking Splunk Customer Success Documented through 700+ engagements worldwide Reduced effort on security staff tasks saving more than $500,000 per year Reduced fraud & abuse by 50% converting fraudulent users to paying customers Reduced compliance reporting time by over 80% for SOX, SAS-70 and PCI a SaaS company
- 17. Copyright © 2016 Splunk, Inc. Security, Compliance & Fraud Common Data Sources Documented through 700+ engagements worldwide Network, Server & Storage • SNMP • Wire Data • DHCP • Firewall • FTP Logs • IDS Logs • Network Access Control • File access control • Network Switches • Network Routers Application & User • Wireless Network logs • Netflow • Proxies • OS Logs (ntsyslog, snare, dhcpd, linux_secure, aix_secure, osx_secure, syslog, Win:Event, etc.) • Patch Logs • VMWare server logs • AWS Logs (CloudTrail, CloudWatch, Config, etc.) • Storage logs Middleware & Database • Java – J2EE (log4J, JMS, MQ, TibcoEMS, HornetQ, RabbitMQ, Native JMS, Weblogic JMS, etc.) • Middleware (Tibco, Software AG etc.) • Web Server (access_combined, access_combined_wcookie, access_common, apache_error, iis, nginx, etc.) • Application Server (log4j, log4php, weblogic_stdout, websphere_activity, websphere_core, websphere_trlog, etc.) • Database error logs • Malware protection logs • Endpoint activity • Application Error Logs • App. Authentication Logs • Vulnerability Scanning • Mail Server Logs • Active Directory • LDAP, VPN • SDLC Security Test Logs • Mobile Devices • Physical Card Reader Logs Other • Threat Lists • OS Blacklist • IP blacklists • Restricted ports and protocols • Vulnerability Lists • Social Media Feeds • Training Logs
- 18. Copyright © 2016 Splunk, Inc. Splunk Security & Compliance Best Practices RefertotheSplunkSANS20whitepaper fordetailedusecasesandexamplesof howcustomersuseSplunktoachieve theanticipatedimprovementswith: FasterDetectionofSecurityEvents FasterResearchandInvestigation ReducedRiskswithDataBreachandFraud New release coming out soon: Mapping Splunk Software to the CIS 20 CSC Version 6.0
- 19. Copyright © 2016 Splunk, Inc. Recap on Top Value Use Cases Security, Compliance, and Fraud IT Operations Application Delivery • Proactive Monitoring • Faster Incident Investigation • More Comprehensive Root Cause Analysis • Fewer Incidents • Better Capacity Planning • Faster Test Failure Analysis • Faster Pre-Production Defect Investigation • Fewer Prod Escalations • Faster Report Development • Faster Time to Market • Increased Visibility • Faster Triage of Events • Faster Incident Investigation • Improved Compliance • Risk Mitigation with Data Breach, IP Theft, Fraud
- 20. Copyright © 2016 Splunk, Inc. How can I gain the most value from all this data…?
- 21. Copyright © 2016 Splunk, Inc. to Answer that… Groups Use Cases Data How does my data overlap across different groups? How much of it is already indexed? more use cases = more value from your current data Are my current users benefiting from all the possible use cases? What else could they be doing? Can other groups leverage the data already indexed? How could they benefit from this data? What data exists in my environment? How much of it is indexed?
- 22. Copyright © 2016 Splunk, Inc. Data Source Assessment Tool Data Sources + Use Cases + Groups
- 23. Copyright © 2016 Splunk, Inc. Data Source Mapping List of 50+ data sources Mapping against high level groups IT Ops, App Support, App Dev, Security, Compliance, Fraud Mapping can be customized to reflect different environments Indicates PRIMARY Data Source for the group Indicates SECONDARY Data Source for the group
- 24. Copyright © 2016 Splunk, Inc. From an Inventory of Data Sources Identify the ones that apply to your environment 1. Estimate their daily size (ex: GB/day for an average Active Directory) 2. Estimate the total number (ex: how many Active Directories) 3. Estimate the % already indexed Splunk SEs can help you Splunk Queries to help you complete the input Data Source Sizing
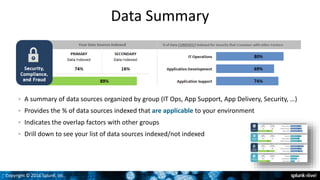
- 25. Copyright © 2016 Splunk, Inc. Data Summary A summary of data sources organized by group (IT Ops, App Support, App Delivery, Security, …) Provides the % of data sources indexed that are applicable to your environment Indicates the overlap factors with other groups Drill down to see your list of data sources indexed/not indexed
- 26. Copyright © 2016 Splunk, Inc. Data Sources Use Cases Common Splunk Use Cases % PRIMARY and SECONDARY Data Sources Indexed
- 27. Copyright © 2016 Splunk, Inc. What’s Next? Making the tool more granular Mapping data sources by team XLS is available for all of you Creating a community of adopters Contact us: [email protected]
- 28. Copyright © 2016 Splunk, Inc. Questions? Thankyou!
Editor's Notes
- #5: You all know what a great platform Splunk is. So if it’s so great, why does our team exist? Well…Users love Splunk and clearly understand the value it delivers to them operationally, but they struggle with articulating it to their senior management in business terms. This leaves executives asking what THEY get from Splunk. They understand their people love it, but can’t put dollars, euros, yuan, or yen on it easily. The Value that Splunk brings to the business is a hidden gem for most executives. When they are able to understand the business value it delivers for them, in most cases it’s priceless.
- #6: Dave - 2 MINUTES Another IMPORTANT PATTERN to talk about is this Amidst the 17 hundred IVAs completed in the past year, 90% of these were focused on IT use cases, and the typical value ranged from $2M to $3M per year Not bad for doing this on your own! But we also noticed 10% of WEB IVAs also included NON-IT user cases, and when combined IT and NON-IT use cases, the value now goes up to $10M per year So currently we’re seeing A LOT of data with IT Use Case, and A LOT of value with non-IT use cases, so combine the 2 together and you can have LARGER EAA discussions! Now why only 10% of business cases included non-IT use cases, that’s because we haven’t instrumented our tool to help you do this effectively But that’s about to change!