End-to-End Security in Mobile-Cloud Computing
- 1. End-to-End Security in Mobile-Cloud Computing By: Sukhpal Singh Gill PhD Research Scholar Thapar University, Patiala 0
- 2. Outline Definition, big picture, and challenges End to end security challenges System architecture Taint analysis and AOP Prototype evaluation Performance and security evaluation Cloud computing evaluation Security in Mobile Cloud Computing (current efforts) MCC architecture Mobile agent for computation offloading Proposed MCC security framework Tamper resistant approach Active Bundle Summary 1
- 3. Mobile-Cloud Computing Definition Mobile cloud computing (MCC) at its simplest, refers to an infrastructure where both the data storage and data processing happen outside of the mobile device. [1,2] Mobile cloud applications move the computing power and data storage away from the mobile devices and into powerful and centralized computing platforms located in clouds, which are then accessed over the wireless connection based on a thin native client. 2
- 4. Why Mobile-Cloud Computing? Mobile devices face many resource challenges (battery life, storage, bandwidth etc.) Cloud computing offers advantages to users by allowing them to use infrastructure, platforms and software by cloud providers at low cost and elastically in an on-demand fashion. Mobile cloud computing provides mobile users with data storage and processing services in clouds, obviating the need to have a powerful device configuration (e.g. CPU speed, memory capacity etc.), as all resource-intensive computing can be performed in the cloud. 3
- 5. The Big Picture: End-to-End Security for MCC Application code to be offloaded to the cloud for execution is bundled in a mobile agent Upon arrival at the destination (cloud host) platform, the bundle enables itself and starts executing its code Guards integrated into the agent code using AOP pointcuts check for tamper during execution (with code checksumming) Upon tamper detection, the bundle moves to a different platform, reloads its data (code) and continues/restarts execution, using the associated AOP advice Results to be sent to the request originator (mobile platform) are encrypted with a well-known authenticated encryption algorithm to ensure end-to-end authentication and integrity. 4
- 6. Security Challenges in SOA and MCC Authentication and authorization may not take place across intended end points Intermediate steps of service execution might expose messages to hostile threats External services are not verified or validated dynamically (Uninformed selection of services by user) User has no control on external service invocation within an orchestration or through a service in another service domain Violations and malicious activities in a trusted service domain remain undetected 5
- 7. End to End Security Architecture 6
- 8. End to End Security Architecture-Description Figure shows problems in end to end SOA security as follow: In this figure the current Air Force infrastructure is shown above the red dashed line. In this architecture, all services are available in the local trusted service domain and everything is under the control of domain A. Client at the edge platform decides to use a service from domain A. He will use his CAC (common access card) to authenticate into the system. The security token is sent to the IDM (identity management system) for validation check. If the user is authorized, IDM gives permission to the requested service (e.g. MX or mail service) for communication with user. New security token (which is created temporarily for the current service session) is sent back to the user and user can use the service. In a class of extended scenarios (use cases) the services in service domain A may want to use external services which are not in the same local trust boundary. In this case, other components come to the picture (below the dashed red line). This figure shows when service domain A (e.g. Air Force service portal) tries to access other governmental or public services (from external domains), it will lose track of end to end security. This figure shows that end points can be accessible to the client directly. We have addressed these issues by adding trust broker server and taint analysis modules (in external trusted service domains). 7
- 9. System Architecture and SOA Baseline Scenario 1. UDDI Registry request 2. Forwarding the service list to Trust Broker and receive a categorized list 3. Invoking a selected service 4. Second invocation by service in domain A 5. Invoking a service in public service domain 6. End points (Reply to user) 9
- 10. Baseline Scenario Details Steps: 1. Global UDDI Registry request User receives a list of services related to the requested category 2. User sends a refined list of services to Trust Broker module Trust Broker categorizes the list of services and returns a classified list Trust categories: Certified, Trusted, Untrusted services 3. Service Request User selects a service based on its criteria (QoS, Trust category of service, Security preference, etc.) and invokes that service. User creates a session with Trust Broker and selected service in Trusted Domain A. (Trust sessions are shown with dashed lines) 10
- 11. Baseline Scenario Details (Cont.) 4. Trusted domain A will invoke another service in Trusted domain B. Taint Analysis module will intercept the communications and reports any illegal external invocation Trust session will be extended to this domain (a new trust link between domain A and trust broker) 5. Step four is repeated. At this moment, an external service invocation to a public service is detected by Taint Analysis module This will be reported to Trust Broker. Trust Broker will maintain the trustworthiness of this SOA service orchestration and if needed can stop it. Service in service domain B invokes a service in an public (Maybe untrusted) domain C (Possibility of deploying Taint Analysis in this domain) 6. Service end points to user The response of SOA invocation can be sent directly to the user 11
- 12. Taint Analysis What is Taint Analysis? Related to IFC (Information Flow Control) How it fits into solution for AFRL? Independent of services (We do not need to change the services or access the source code of services) Interception of Service execution (Service will remain transparent) 28
- 13. Taint Analysis Using AOP (Aspect Oriented Programming) Instrumenting classes based on predefined pointcuts Low performance overhead (ideal solution) How it works? Load-time instrumentation The whole Application server is under control Granularity Package/Class level Method level Field level Instrumenting classes in action pipeline 29
- 14. What is AOP? Some programming tasks cannot be neatly encapsulated in objects, but must be scattered throughout the program AOP is a programming methodology to help with crosscutting concerns Crosscutting concerns: Functionality whose implementation spans multiple modules AOP helps to implement them without modifying the original code Many examples: Logging and tracing, Transaction management, security, caching, error handling, business rules, performance monitoring… 13
- 15. AOP Concepts Join point An identifiable point in the execution of a program. An specific pattern of execution Example patterns: execution of a method, access to a class field, loading of a class, … Pointcut A set of join points as a program construct. Advice During the service execution, when a join point of a pointcut is matched then a piece of code called advice is executed. An advice may log the event or report the event back to a server (trust broker in the proposed project) Each advice is associated with one or more pointcuts. 14
- 16. Experience with AOP for End-to-End Cloud Service Security Need to ensure trustworthiness of results from external services (which could outsource functionality to other services) A general service-oriented architecture (SOA) problem We proposed an information flow tracking approach [5]: Based on taint analysis (tracking external service calls) and trust broker (a trusted third party evaluating trustworthiness of services, keeping track of service invocation chains, reporting invocation history to clients) All interactions secured with WS-Security 15
- 17. AOP for Taint Analysis Load-time instrumentation of classes as they are loaded into the JVM at runtime Access to source code is not required Instrumenting classes based on predefined pointcuts Pointcuts are specified based on security policies and requirements Low performance overhead Independent of services (We do not need to change the services or access the source code of services) Interception of Service execution (Service will remain transparent) 16
- 18. AOP for Taint Analysis 17
- 19. AOP for Taint Analysis The previous diagram shows the internal of a service in an application server. A service is composed of a series of actions called action pipeline which are invoked when a message is received. Every class is associated with a business class (Java class) Taint analysis monitors the execution of classes to find certain pointcuts (illegal service invocation in this scenario) When an illegal service invocation is detected, taint analysis module reports the incident back to trust broker 18
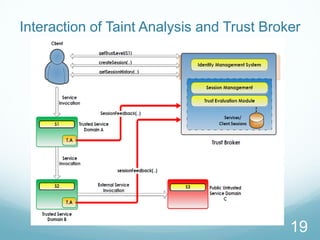
- 20. Interaction of Taint Analysis and Trust Broker 19
- 21. Interaction of Taint Analysis and Trust Broker The diagram illustrates how taint analysis (T.A) and trust broker modules work together. It shows a SOA service which is composed of three services S1-S3 (S1 and S2 are trusted; S3 is untrusted/public) T.A modules monitor the service invocations and then report the events back to trust broker through sessionFeedback. Trust broker maintains the sessions of end to end service invocations and reports to the clients In policy enforcement scenarios, trust broker can decide to send a termination command to T.A modules (based on user policies) 20
- 22. Evaluation of the Proposed Solution Security Evaluation The implemented prototype will be evaluated in terms of its effectiveness in mitigating various attacks including the following attacks XML Rewriting Attack DoS Attack Performance Evaluation Response Time Throughput 37
- 23. SOA Security Evaluation We are evaluating the proposed prototype in terms of its effectiveness in mitigating various attacks In-transit Sniffing or Spoofing While information in SOAP message is in transit on the wire, various entities can see it SOAP messages could be spoofed by various tools Attack Scenarios XML Rewriting Attack Replay Attacks They poison the SOAP messages and send them to a server with a forged client signature. This attack can be lethal since an attacker spoofs a user’s identity Denial of Service attack 38
- 24. XML Rewriting Attack Exploring how certain XML rewriting attacks can be detected by the Tainted Analysis component and Trust Broker XML rewriting attack commonly refers to the class of attacks which involve in modifying the SOAP message. (Replay, Redirect, Man in the middle, multiple header etc.) WS Client Attacker Web service provider
- 25. XML Rewriting Attack-Cont. Basic Replay Attack: Replace the entire current message with an old message. (Assuming no security headers present) Replay when security headers present : Replace the current SOAP body with an old SOAP body but keep the current SOAP body at the same time to satisfy the security validations. 40
- 26. XML Rewriting (Replay Attack) Cache the messages and replay old messages on Web service A which will then make subsequent calls from A to have older session ID/ Message ID. Web Service A MethodCall( param ) { } Web Service B Web Service C XML Rewriting Attack
- 27. XML Rewriting Attack Generation We extended TCPMon which is an Open source debugging utility for web service calls. The tool listens on a specified port and collect the request and response messages. Customized to intercept, change the SOAP message (redirect or replay) and resent to the receiver. Examine how the Tainted analysis and Trust broker modules behave in this case.
- 28. Cloud Setup – Baseline 51
- 29. Taint Analysis Experiment Setup in Amazon EC2 28
- 30. Taint Analysis Experiments in Amazon EC2 0 100 200 300 400 500 600 1 2 4 8 16 response time (ms) number of simultaneous requests baseline taint analysis AOP has low overhead, thus suitable for real-time MCC as well 29
- 32. MCC General Architecture 31 AAA: Authentication, Authorization and Accounting HA: Home Agent
- 33. MCC Architecture Mobile devices are connected to the mobile networks via base stations that establish and control the connections and functional interfaces between the networks and mobile devices. Mobile users’ requests and information are transmitted to the central processors that are connected to servers providing mobile network services. The subscribers’ requests are delivered to a cloud through the Internet. In the cloud, cloud controllers process the requests to provide mobile users with the corresponding cloud services. 32
- 34. MCC Security Challenges Lack of control on resources and multi-tenancy of different users’ applications on the same physical machine make cloud platforms vulnerable to attacks “Hey, You, Get Off of My Cloud!”[3] In addition to privacy issues, programs running in the cloud are prone to: Tampering with code/data/execution flow/ communication Masquerading Mobile code can navigate through multiple platforms before returning to the origin, giving rise to the end-to-end security problem, which involves decreasing control with every further hop in the chain of platforms. Security mechanisms should satisfy the constraints of (1) real-time response under intermittent network connection; (2) keeping communication costs at minimum; (3) incurring limited computation overhead 33
- 35. Mobile Agents for Computation Offloading A mobile agent is a software program with mobility, which can be sent out from a computer into a network and roam among the nodes in the network autonomously to finish its task on behalf of its owner. Mobile agent migration follows these steps: 1. Process suspension/new process creation 2. Process conversion into a message with all state information 3. Message routing to destination server 4. Message reconstitution into executable 5. Execution continuation with next instruction 34
- 36. Advantages of Mobile (Autonomous) Agents for MCC Mobile agents can provide better support for mobile clients (reduced network communication). Mobile agents are capable of moving across different cloud machine instances transparently, which makes them capable of migrating to a different location for reasons including poor performance or an attack-prone runtime environment. Mobile agents can be equipped with techniques to check self-integrity independent of the host platform, for tamper detection. Mobile agents can clone themselves on multiple cloud hosts to achieve better runtime performance. 35
- 37. Proposed Computation Offloading Framework 36
- 38. Proposed Framework Components Cloud directory service: A Web service (trusted third party) that maintains an up-to-date database of virtual machine instances (VMIs) available for use in the cloud Execution manager (elasticity manager): Service on mobile platform that makes the decision regarding the execution platform of the different program partitions Mobile agent containers: Provide an execution environment for program partitions Virtual machine instances (cloud hosts): Host containers of the mobile agents (program partitions) sent to the cloud 37
- 39. Proposed Framework in Action 1. When a mobile application is launched, the execution manager contacts the cloud directory service to get a list of available machine instances in the cloud 2. An execution plan containing offloading decisions for the agent-based partitions is created by the execution manager 3. For partitions to be offloaded, a bridge is formed between the callers of those partitions and their selected cloud hosts, through which the partitions migrate to the selected hosts 4. Upon migration, the partitions start executing and communicate their output data to the callers through the same bridge 38
- 40. Experiments with Proposed Framework – Sudoku Solver Execution time to find all possible solutions for a Sudoku puzzle with different numbers of initially filled cells, for mobile-device only vs. offloaded execution 39
- 41. Experiments with Proposed Framework – Face Recognition Execution time for a face recognition program with different numbers of pictures to compare against, for mobile-device only vs. offloaded execution 40
- 42. Adding Security to MCC Framework The performance results with the proposed MCC framework are promising for real-time mobile computing. Need to add end-to-end tamper resistance (integrity verification) functionality without: 1. Significantly increasing response time 2. Increasing communication costs 3. Incurring high computational overhead Solution: Self-protecting application partitions 41
- 43. Proposed Tamper Resistance Approach Self-protecting agents: The autonomous agents used in the MCC framework can be augmented with integrity verification constructs called software guards (similar to the work by Chang and Atallah [7]) that are executed during runtime Guard: is a piece of code responsible for performing certain security-related actions during program execution. Example Guard: checksum code which can be used for integrity verification Integrity checkpoints are distributed throughout the agent code to ensure timely detection of tamper Upon tamper detection, the agent stops execution, moves to a different platform and either (a) resumes execution from the last integrity-verified checkpoint or (b) starts execution from the beginning 42
- 44. Experience with Self-Protecting Agents: Active Bundles Active Bundle: Data protection mechanism encapsulating data with metadata and a virtual machine Data protected from within instead of outside 43
- 45. Enabling of an Active Bundle 44
- 46. Active Bundles for MCC We have successfully applied the idea of active bundles for 1. Secure data dissemination in a peer-to-peer network of UAVs [8] 2. Identity management in cloud computing [6] A similar idea with some modifications can be applied to MCC: The data of the bundle now consists of application code to be executed on the foreign (cloud) platform The trustworthiness of a host is now determined by the bundle itself during runtime based on integrity checks instead of (or in addition to) information from a trusted third party. 45
- 47. How to Achieve Dynamic Tamper Detection? Need to distribute integrity checkpoints throughout the agent code without needing to modify the software Need to take the appropriate measures in case of tamper detection in a way that is transparent to the software Need to keep runtime overhead at minimum 46 The solution is to use Aspect Oriented Programming (AOP) for guards
- 48. The Big Picture and Summary Application code to be offloaded to the cloud for execution is bundled in a mobile agent Upon arrival at the destination (cloud host) platform, the bundle enables itself and starts executing its code Guards integrated into the agent code using AOP pointcuts check for tamper during execution (with code checksumming) Upon tamper detection, the bundle moves to a different platform, reloads its data (code) and continues/restarts execution, using the associated AOP advice Results to be sent to the request originator (mobile platform) are encrypted with a well-known authenticated encryption algorithm to ensure end-to-end authentication and integrity.47



![Mobile-Cloud Computing Definition
Mobile cloud computing (MCC) at its simplest, refers
to an infrastructure where both the data storage and
data processing happen outside of the mobile device.
[1,2]
Mobile cloud applications move the computing power
and data storage away from the mobile devices and
into powerful and centralized computing platforms
located in clouds, which are then accessed over the
wireless connection based on a thin native client.
2](https://image.slidesharecdn.com/end-to-endsecurityinmobile-cloudcomputing-151123092931-lva1-app6891/85/End-to-End-Security-in-Mobile-Cloud-Computing-3-320.jpg)












![Experience with AOP for End-to-End Cloud
Service Security
Need to ensure trustworthiness of results from external
services (which could outsource functionality to other
services) A general service-oriented architecture
(SOA) problem
We proposed an information flow tracking approach [5]:
Based on taint analysis (tracking external service calls)
and trust broker (a trusted third party evaluating
trustworthiness of services, keeping track of service
invocation chains, reporting invocation history to clients)
All interactions secured with WS-Security
15](https://image.slidesharecdn.com/end-to-endsecurityinmobile-cloudcomputing-151123092931-lva1-app6891/85/End-to-End-Security-in-Mobile-Cloud-Computing-16-320.jpg)
















![MCC Security Challenges
Lack of control on resources and multi-tenancy of different
users’ applications on the same physical machine make cloud
platforms vulnerable to attacks “Hey, You, Get Off of My
Cloud!”[3]
In addition to privacy issues, programs running in the cloud are
prone to:
Tampering with code/data/execution flow/ communication
Masquerading
Mobile code can navigate through multiple platforms before
returning to the origin, giving rise to the end-to-end security
problem, which involves decreasing control with every further hop
in the chain of platforms.
Security mechanisms should satisfy the constraints of (1) real-time
response under intermittent network connection; (2) keeping
communication costs at minimum; (3) incurring limited
computation overhead
33](https://image.slidesharecdn.com/end-to-endsecurityinmobile-cloudcomputing-151123092931-lva1-app6891/85/End-to-End-Security-in-Mobile-Cloud-Computing-34-320.jpg)








![Proposed Tamper Resistance Approach
Self-protecting agents: The autonomous agents used in the
MCC framework can be augmented with integrity verification
constructs called software guards (similar to the work by
Chang and Atallah [7]) that are executed during runtime
Guard: is a piece of code responsible for performing certain
security-related actions during program execution.
Example Guard: checksum code which can be used for
integrity verification
Integrity checkpoints are distributed throughout the agent
code to ensure timely detection of tamper
Upon tamper detection, the agent stops execution, moves to
a different platform and either (a) resumes execution from
the last integrity-verified checkpoint or (b) starts execution
from the beginning
42](https://image.slidesharecdn.com/end-to-endsecurityinmobile-cloudcomputing-151123092931-lva1-app6891/85/End-to-End-Security-in-Mobile-Cloud-Computing-43-320.jpg)


![Active Bundles for MCC
We have successfully applied the idea of active
bundles for
1. Secure data dissemination in a peer-to-peer network of
UAVs [8]
2. Identity management in cloud computing [6]
A similar idea with some modifications can be applied
to MCC:
The data of the bundle now consists of application code
to be executed on the foreign (cloud) platform
The trustworthiness of a host is now determined by the
bundle itself during runtime based on integrity checks
instead of (or in addition to) information from a trusted
third party.
45](https://image.slidesharecdn.com/end-to-endsecurityinmobile-cloudcomputing-151123092931-lva1-app6891/85/End-to-End-Security-in-Mobile-Cloud-Computing-46-320.jpg)

