Essential Network Security Principles - Digitdefence
0 likes18 views
Essential network security principles include implementing strong access controls, regular monitoring, and encryption to safeguard data and prevent unauthorized access. These practices protect network integrity, ensure data confidentiality, and minimize potential cyber threats.
1 of 9
Download to read offline








Ad
Recommended
Fundamentals of Securing Devices in Networking.pptx.pdf



Fundamentals of Securing Devices in Networking.pptx.pdfapurvar399 Securing devices in networking involves implementing robust measures like firewalls, encryption, and strong authentication protocols to protect against unauthorized access and cyber threats. Effective device security ensures the integrity, confidentiality, and availability of data across the network.
Network Security Fundamentals presentation



Network Security Fundamentals presentationRosy G Network Security Fundamentals focus on protecting the integrity, confidentiality, and availability of data as it travels across networks. This includes implementing measures like firewalls, intrusion detection systems, and encryption to safeguard against cyber threats, ensuring that sensitive information is secure from unauthorized access.
The Components of Cyber Security.pptx.pdf



The Components of Cyber Security.pptx.pdfapurvar399 The components of cyber security include key elements such as network security, data protection, identity and access management, and incident response. Together, they ensure the protection of systems, data, and networks from unauthorized access and cyber threats.
Cloud Security Protecting Data in the Cloud Era



Cloud Security Protecting Data in the Cloud Erayams12611 Explore strategies for cloud security and data protection in the cloud era. Learn best practices for safeguarding your data in cloud environments.
Best Practices in Cloud Security Standards.pptx.pdf



Best Practices in Cloud Security Standards.pptx.pdfapurvar399 Best practices in cloud security standards involve implementing a comprehensive framework that includes data encryption, regular security assessments, and robust access controls to protect sensitive information stored in the cloud. Organizations should also ensure compliance with industry regulations, utilize multi-factor authentication, and conduct employee training to enhance awareness of potential security threats.
Understanding the Essentials of Cloud Security



Understanding the Essentials of Cloud Securityyams12611 Learn the key principles of cloud security, including data protection, compliance, access control, and risk management strategies.
Fundamentals of Network Security - DigitDefence



Fundamentals of Network Security - DigitDefenceyams12611 Learn the basics of network security, covering essential concepts, protocols, tools, and strategies to safeguard systems effectively.
Essentials of Network and Cloud Security.pptx.pdf



Essentials of Network and Cloud Security.pptx.pdfapurvar399 Network and cloud security are critical for protecting sensitive data and systems from unauthorized access, cyberattacks, and breaches. Key essentials include encryption, multi-factor authentication, firewalls, and continuous monitoring to ensure the integrity and security of both on-premise and cloud-based infrastructures.
Preventing Network Security Threats (1).pptx (1).pdf



Preventing Network Security Threats (1).pptx (1).pdfapurvar399 Preventing network security threats requires a multi-layered approach that includes implementing robust firewalls, regular software updates, and strong access controls to safeguard sensitive data. Additionally, employee training and awareness programs are essential to equip staff with the knowledge to recognize potential threats and respond appropriately.
Network Security Model in Cryptography presentation



Network Security Model in Cryptography presentationRosy G A Network Security Model in cryptography is a framework designed to protect data during transmission by ensuring confidentiality, integrity, and authentication. It involves the use of encryption algorithms, secure protocols, and cryptographic keys to safeguard information from unauthorized access and cyber threats, maintaining secure communication across networks.
Fundamentals of Securing Network Devices.pptx.pdf



Fundamentals of Securing Network Devices.pptx.pdfapurvar399 Securing network devices involves implementing measures like strong authentication, encryption, and access control to prevent unauthorized access. Regular updates, monitoring, and secure configurations are essential to protect against vulnerabilities and cyber threats.
Key Features of Endpoint Security tools presentation



Key Features of Endpoint Security tools presentationRosy G The "Key Features of Endpoint Security Tools" presentation highlights essential components such as advanced threat detection, real-time monitoring, and encryption. It also covers multi-factor authentication, automated patch management, and endpoint detection and response (EDR) for comprehensive device protection.
HOW TO SECURE WEB AND APP DEVELOPMENT USER DATA SECURITY.pdf



HOW TO SECURE WEB AND APP DEVELOPMENT USER DATA SECURITY.pdfasiyahanif9977 In today’s Graphic Design in the UAE age, where the internet and mobile applications have become an integral part of our lives, ensuring User Data Security has become paramount.
HOW TO SECURE WEB AND APP DEVELOPMENT USER DATA SECURITY.pdf



HOW TO SECURE WEB AND APP DEVELOPMENT USER DATA SECURITY.pdfasiyahanif9977 https://nexusbeez.com/
In today’s Graphic Design in UAE age, where the internet and mobile applications have become an integral part of our lives, ensuring User Data Security has become paramount.
Exploring the Seven Key Attributes of Security Testing.pdf



Exploring the Seven Key Attributes of Security Testing.pdfAmeliaJonas2 Security Testing Service is a crucial process that evaluates the resilience of an organization's digital assets against potential cyberattacks. In this blog, we will delve into the seven key attributes of security testing and understand their significance in safeguarding our digital world.
Introduction to Cyber Security and its importance



Introduction to Cyber Security and its importanceishasindwani This document provides an introduction to cyber security. It defines cyber security as protecting cyberspace from attacks, and defines a cyber attack. It tells how much it is important to know about cybersecurity. It explains that cyberspace us where online communication occurs, via the internet. Cyber security is important because it affects everyone who uses computer and networks. So, to protect our information and data from unauthorized access we must know about cyber attacks and its preventions, also about the future of cyber security.
Soc Compliance Overview



Soc Compliance OverviewFabio Ferrari In this quick presentation I included the SOC key points and the five key sections of the Trust Service Criteria for SOC 2 Compliance.
9 Best Enterprise Data Security and Privacy Practices in 2025_compressed (1).pdf



9 Best Enterprise Data Security and Privacy Practices in 2025_compressed (1).pdfHawkShield Data Security and Privacy remain essential priorities which enterprises need to focus on during the upcoming years through 2025.
https://www.hawkshield.ai/blog/best-data-security-and-privacy-practices-for-2025
Key Features of Top Cyber Security Companies.pptx.pdf



Key Features of Top Cyber Security Companies.pptx.pdfapurvar399 Top cybersecurity companies offer key features such as advanced threat detection, comprehensive incident response, and proactive risk management to safeguard organizations from evolving cyber threats. Additionally, they provide tailored security solutions, regular vulnerability assessments, and robust compliance support to ensure organizations maintain a strong security posture.
Cyber Cops: CloudSecurity - Safeguarding Data in the Cloud



Cyber Cops: CloudSecurity - Safeguarding Data in the CloudCybercops Cloud computing provides enterprises with unmatched advantages in the age of digital transformation, including scalability and cost effectiveness. To safeguard sensitive data, these benefits are accompanied by additional security issues that need to be resolved. This presentation, presented by Cyber Cops, explores the essential elements of cloud security, looking at possible threats and offering best practices for protecting your data in the cloud. Discover how to create a strong cloud security plan to safeguard the most important assets in your company.
CS-1,2.pdf



CS-1,2.pdftechuniverso01 Identification and Authentication:
• How it works: Users and devices are identified and authenticated to ensure they are who they claim to be. This often involves the use of usernames and passwords, multi-factor authentication (MFA), biometrics, or other authentication methods.
Tools and Techniques for Cloud Security download



Tools and Techniques for Cloud Security downloadRosy G Cloud security tools and techniques safeguard data, applications, and infrastructure within cloud environments. Key methods include encryption, identity and access management (IAM), and continuous monitoring, providing businesses with robust protection against cyber threats and ensuring data privacy.
Introduction to Cloud Security Tools (1).pptx.pdf



Introduction to Cloud Security Tools (1).pptx.pdfRosy G Importance of cloud security and key challenges of cloud security
Top Cybersecurity Interview Questions.pdf



Top Cybersecurity Interview Questions.pdfinfosec train In today’s fast-paced digital landscape, staying ahead in cybersecurity is more crucial than ever. Understanding the **𝐓𝐨𝐩 𝐂𝐲𝐛𝐞𝐫𝐬𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐈𝐧𝐭𝐞𝐫𝐯𝐢𝐞𝐰 𝐐𝐮𝐞𝐬𝐭𝐢𝐨𝐧𝐬** can make all the difference for candidates and hiring managers alike.
Master Your next Cyber security Interview Questions.pdf



Master Your next Cyber security Interview Questions.pdfInfosecTrain In today’s fast-paced digital landscape, staying ahead in cybersecurity is more crucial than ever. Understanding the **𝐓𝐨𝐩 𝐂𝐲𝐛𝐞𝐫𝐬𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐈𝐧𝐭𝐞𝐫𝐯𝐢𝐞𝐰 𝐐𝐮𝐞𝐬𝐭𝐢𝐨𝐧𝐬** can make all the difference for candidates and hiring managers alike.
For more info to Checkout :- https://www.infosectrain.com/blog/top-cyber-security-interview-questions/
👉 **𝐃𝐨𝐰𝐧𝐥𝐨𝐚𝐝 𝐨𝐮𝐫 𝐠𝐮𝐢𝐝𝐞 𝐭𝐨𝐝𝐚𝐲** to equip yourself with the knowledge needed to stand out in your cybersecurity interviews!
Comment below with your favorite interview question or share your interview experiences! Let’s learn from each other!
InfosecTrain Top Cybersecurity Interview Questions



InfosecTrain Top Cybersecurity Interview Questionspriyanshamadhwal2 In today’s fast-paced digital landscape, staying ahead in cybersecurity is more crucial than ever. Understanding the 𝐓𝐨𝐩 𝐂𝐲𝐛𝐞𝐫𝐬𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐈𝐧𝐭𝐞𝐫𝐯𝐢𝐞𝐰 𝐐𝐮𝐞𝐬𝐭𝐢𝐨𝐧𝐬 can make all the difference for candidates and hiring managers alike.
View more: https://www.infosectrain.com/category/cybersecurity/
Top Cybersecurity Interview Question.pdf



Top Cybersecurity Interview Question.pdfinfosecTrain In today's fast-paced digital landscape, staying ahead in cybersecurity is more crucial than ever. Understanding the Top Cybersecurity Interview Questions can make all the difference for candidates and hiring managers alike.
InfosecTrain.com
Download our guide today to equip yourself with the knowledge needed to stand out in your cybersecurity interviews!
What is Authentication in Network Security| Digitdefence



What is Authentication in Network Security| DigitdefenceRosy G Authentication in network security is the process of verifying the identity of users or devices before granting access to systems or data. It ensures that only authorized individuals can access sensitive information, preventing unauthorized access and potential security breaches.
How to Choose the Penetration Testing Services for Your Need| Digitdefence



How to Choose the Penetration Testing Services for Your Need| DigitdefenceRosy G Choosing the right penetration testing services is crucial for identifying vulnerabilities and securing your network. Look for a provider with experience, a comprehensive approach, and a track record of successful security assessments, like DigitDefence, to ensure the best protection for your business.
Ad
More Related Content
Similar to Essential Network Security Principles - Digitdefence (20)
Preventing Network Security Threats (1).pptx (1).pdf



Preventing Network Security Threats (1).pptx (1).pdfapurvar399 Preventing network security threats requires a multi-layered approach that includes implementing robust firewalls, regular software updates, and strong access controls to safeguard sensitive data. Additionally, employee training and awareness programs are essential to equip staff with the knowledge to recognize potential threats and respond appropriately.
Network Security Model in Cryptography presentation



Network Security Model in Cryptography presentationRosy G A Network Security Model in cryptography is a framework designed to protect data during transmission by ensuring confidentiality, integrity, and authentication. It involves the use of encryption algorithms, secure protocols, and cryptographic keys to safeguard information from unauthorized access and cyber threats, maintaining secure communication across networks.
Fundamentals of Securing Network Devices.pptx.pdf



Fundamentals of Securing Network Devices.pptx.pdfapurvar399 Securing network devices involves implementing measures like strong authentication, encryption, and access control to prevent unauthorized access. Regular updates, monitoring, and secure configurations are essential to protect against vulnerabilities and cyber threats.
Key Features of Endpoint Security tools presentation



Key Features of Endpoint Security tools presentationRosy G The "Key Features of Endpoint Security Tools" presentation highlights essential components such as advanced threat detection, real-time monitoring, and encryption. It also covers multi-factor authentication, automated patch management, and endpoint detection and response (EDR) for comprehensive device protection.
HOW TO SECURE WEB AND APP DEVELOPMENT USER DATA SECURITY.pdf



HOW TO SECURE WEB AND APP DEVELOPMENT USER DATA SECURITY.pdfasiyahanif9977 In today’s Graphic Design in the UAE age, where the internet and mobile applications have become an integral part of our lives, ensuring User Data Security has become paramount.
HOW TO SECURE WEB AND APP DEVELOPMENT USER DATA SECURITY.pdf



HOW TO SECURE WEB AND APP DEVELOPMENT USER DATA SECURITY.pdfasiyahanif9977 https://nexusbeez.com/
In today’s Graphic Design in UAE age, where the internet and mobile applications have become an integral part of our lives, ensuring User Data Security has become paramount.
Exploring the Seven Key Attributes of Security Testing.pdf



Exploring the Seven Key Attributes of Security Testing.pdfAmeliaJonas2 Security Testing Service is a crucial process that evaluates the resilience of an organization's digital assets against potential cyberattacks. In this blog, we will delve into the seven key attributes of security testing and understand their significance in safeguarding our digital world.
Introduction to Cyber Security and its importance



Introduction to Cyber Security and its importanceishasindwani This document provides an introduction to cyber security. It defines cyber security as protecting cyberspace from attacks, and defines a cyber attack. It tells how much it is important to know about cybersecurity. It explains that cyberspace us where online communication occurs, via the internet. Cyber security is important because it affects everyone who uses computer and networks. So, to protect our information and data from unauthorized access we must know about cyber attacks and its preventions, also about the future of cyber security.
Soc Compliance Overview



Soc Compliance OverviewFabio Ferrari In this quick presentation I included the SOC key points and the five key sections of the Trust Service Criteria for SOC 2 Compliance.
9 Best Enterprise Data Security and Privacy Practices in 2025_compressed (1).pdf



9 Best Enterprise Data Security and Privacy Practices in 2025_compressed (1).pdfHawkShield Data Security and Privacy remain essential priorities which enterprises need to focus on during the upcoming years through 2025.
https://www.hawkshield.ai/blog/best-data-security-and-privacy-practices-for-2025
Key Features of Top Cyber Security Companies.pptx.pdf



Key Features of Top Cyber Security Companies.pptx.pdfapurvar399 Top cybersecurity companies offer key features such as advanced threat detection, comprehensive incident response, and proactive risk management to safeguard organizations from evolving cyber threats. Additionally, they provide tailored security solutions, regular vulnerability assessments, and robust compliance support to ensure organizations maintain a strong security posture.
Cyber Cops: CloudSecurity - Safeguarding Data in the Cloud



Cyber Cops: CloudSecurity - Safeguarding Data in the CloudCybercops Cloud computing provides enterprises with unmatched advantages in the age of digital transformation, including scalability and cost effectiveness. To safeguard sensitive data, these benefits are accompanied by additional security issues that need to be resolved. This presentation, presented by Cyber Cops, explores the essential elements of cloud security, looking at possible threats and offering best practices for protecting your data in the cloud. Discover how to create a strong cloud security plan to safeguard the most important assets in your company.
CS-1,2.pdf



CS-1,2.pdftechuniverso01 Identification and Authentication:
• How it works: Users and devices are identified and authenticated to ensure they are who they claim to be. This often involves the use of usernames and passwords, multi-factor authentication (MFA), biometrics, or other authentication methods.
Tools and Techniques for Cloud Security download



Tools and Techniques for Cloud Security downloadRosy G Cloud security tools and techniques safeguard data, applications, and infrastructure within cloud environments. Key methods include encryption, identity and access management (IAM), and continuous monitoring, providing businesses with robust protection against cyber threats and ensuring data privacy.
Introduction to Cloud Security Tools (1).pptx.pdf



Introduction to Cloud Security Tools (1).pptx.pdfRosy G Importance of cloud security and key challenges of cloud security
Top Cybersecurity Interview Questions.pdf



Top Cybersecurity Interview Questions.pdfinfosec train In today’s fast-paced digital landscape, staying ahead in cybersecurity is more crucial than ever. Understanding the **𝐓𝐨𝐩 𝐂𝐲𝐛𝐞𝐫𝐬𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐈𝐧𝐭𝐞𝐫𝐯𝐢𝐞𝐰 𝐐𝐮𝐞𝐬𝐭𝐢𝐨𝐧𝐬** can make all the difference for candidates and hiring managers alike.
Master Your next Cyber security Interview Questions.pdf



Master Your next Cyber security Interview Questions.pdfInfosecTrain In today’s fast-paced digital landscape, staying ahead in cybersecurity is more crucial than ever. Understanding the **𝐓𝐨𝐩 𝐂𝐲𝐛𝐞𝐫𝐬𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐈𝐧𝐭𝐞𝐫𝐯𝐢𝐞𝐰 𝐐𝐮𝐞𝐬𝐭𝐢𝐨𝐧𝐬** can make all the difference for candidates and hiring managers alike.
For more info to Checkout :- https://www.infosectrain.com/blog/top-cyber-security-interview-questions/
👉 **𝐃𝐨𝐰𝐧𝐥𝐨𝐚𝐝 𝐨𝐮𝐫 𝐠𝐮𝐢𝐝𝐞 𝐭𝐨𝐝𝐚𝐲** to equip yourself with the knowledge needed to stand out in your cybersecurity interviews!
Comment below with your favorite interview question or share your interview experiences! Let’s learn from each other!
InfosecTrain Top Cybersecurity Interview Questions



InfosecTrain Top Cybersecurity Interview Questionspriyanshamadhwal2 In today’s fast-paced digital landscape, staying ahead in cybersecurity is more crucial than ever. Understanding the 𝐓𝐨𝐩 𝐂𝐲𝐛𝐞𝐫𝐬𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐈𝐧𝐭𝐞𝐫𝐯𝐢𝐞𝐰 𝐐𝐮𝐞𝐬𝐭𝐢𝐨𝐧𝐬 can make all the difference for candidates and hiring managers alike.
View more: https://www.infosectrain.com/category/cybersecurity/
Top Cybersecurity Interview Question.pdf



Top Cybersecurity Interview Question.pdfinfosecTrain In today's fast-paced digital landscape, staying ahead in cybersecurity is more crucial than ever. Understanding the Top Cybersecurity Interview Questions can make all the difference for candidates and hiring managers alike.
InfosecTrain.com
Download our guide today to equip yourself with the knowledge needed to stand out in your cybersecurity interviews!
More from Rosy G (19)
What is Authentication in Network Security| Digitdefence



What is Authentication in Network Security| DigitdefenceRosy G Authentication in network security is the process of verifying the identity of users or devices before granting access to systems or data. It ensures that only authorized individuals can access sensitive information, preventing unauthorized access and potential security breaches.
How to Choose the Penetration Testing Services for Your Need| Digitdefence



How to Choose the Penetration Testing Services for Your Need| DigitdefenceRosy G Choosing the right penetration testing services is crucial for identifying vulnerabilities and securing your network. Look for a provider with experience, a comprehensive approach, and a track record of successful security assessments, like DigitDefence, to ensure the best protection for your business.
Cyber Threats and Network Vulnerabilities (1).pdf



Cyber Threats and Network Vulnerabilities (1).pdfRosy G
Cyber threats refer to malicious attempts to breach, damage, or steal data from systems, often through hacking, malware, or phishing. Network vulnerabilities are weaknesses in a system’s architecture or security protocols that make it susceptible to such attacks. Addressing both threats and vulnerabilities is critical to safeguarding sensitive data and maintaining the integrity of digital infrastructures.
The Role of Cybersecurity Companies in Data Protection.pptx.pdf



The Role of Cybersecurity Companies in Data Protection.pptx.pdfRosy G Cybersecurity companies play a critical role in safeguarding sensitive data from cyber threats by providing advanced security solutions, such as encryption, threat detection, and incident response. They help businesses implement proactive measures to prevent data breaches, ensuring compliance with regulations and protecting both customer and company data. With the increasing sophistication of cyberattacks, these companies are essential in maintaining trust, privacy, and business continuity in today's digital world.
What is Phishing Attack --- Digitdefence



What is Phishing Attack --- DigitdefenceRosy G A phishing attack is a cyberattack where attackers impersonate legitimate entities to trick individuals into revealing sensitive information, such as passwords or credit card numbers. These attacks typically occur through deceptive emails, websites, or messages designed to look trustworthy.
Introduction to Email Virus | Digitdefence



Introduction to Email Virus | DigitdefenceRosy G An Email Virus is a malicious program spread through email attachments or links, designed to infect devices and steal sensitive information. Recognizing suspicious emails and avoiding unverified attachments is crucial to safeguarding your system.
How Can You Prevent Phishing | Digitdefence



How Can You Prevent Phishing | DigitdefenceRosy G Preventing phishing involves staying vigilant against suspicious emails or messages and verifying links before clicking. Use tools like multi-factor authentication and regularly update your software to protect personal and financial information from cybercriminals.
How to Become a Cybersecurity Expert | Digitdefence



How to Become a Cybersecurity Expert | DigitdefenceRosy G Becoming a cybersecurity expert involves gaining a deep understanding of network security, data protection, and threat management. It requires a combination of technical skills, certifications, and hands-on experience to stay ahead of evolving cyber threats.
Why is Cybersecurity Important for Your Privacy | Digitdefence



Why is Cybersecurity Important for Your Privacy | DigitdefenceRosy G Cybersecurity is crucial for your privacy because it protects your personal data from unauthorized access and potential misuse. With strong cybersecurity measures in place, your sensitive information remains secure from cybercriminals, ensuring your privacy is upheld online.
Importance of Security Devices in Networking | Digitdefence



Importance of Security Devices in Networking | DigitdefenceRosy G Security devices in networking, such as firewalls and intrusion detection systems, are essential for safeguarding data and preventing unauthorized access. They ensure a secure and reliable network environment for businesses and users.
Introduction to Pentesting in Cybersecurity | Digitdefence



Introduction to Pentesting in Cybersecurity | DigitdefenceRosy G Pentesting, or penetration testing, is a critical cybersecurity process where ethical hackers simulate cyberattacks to identify vulnerabilities in systems, networks, or applications. It strengthens defenses by addressing security gaps proactively.
Why Google Cloud Security Matters for Businesses | Digitdefence



Why Google Cloud Security Matters for Businesses | DigitdefenceRosy G Google Cloud Security matters for businesses as it provides robust, scalable protection for sensitive data, applications, and workloads. It ensures compliance, resilience against cyber threats, and peace of mind in a rapidly evolving digital landscape.
Importance of Risk Analysis for Cybersecurity - Digitdefence



Importance of Risk Analysis for Cybersecurity - DigitdefenceRosy G Risk analysis is crucial for identifying vulnerabilities and threats within an organization’s cybersecurity framework, helping to prioritize protective measures. Digitdefence offers comprehensive risk analysis services to assess potential risks and ensure robust protection against cyber threats.
The Types of Cyber Security - Digitdefence



The Types of Cyber Security - DigitdefenceRosy G Cybersecurity encompasses various types, including network security, information security, and application security, each aimed at protecting systems from different kinds of threats. Digitdefence offers comprehensive cybersecurity services, ensuring robust protection against these evolving cyber risks.
Types of Firewalls in Cyber Security- Digitdefence



Types of Firewalls in Cyber Security- DigitdefenceRosy G Firewalls in cybersecurity include Packet-Filtering Firewalls, which inspect packets based on IP addresses and ports; Stateful Inspection Firewalls, which track active connections for greater security; Proxy Firewalls, which filter traffic at the application level; and Next-Generation Firewalls (NGFW), combining multiple layers of filtering, including deep packet inspection and intrusion prevention.
How Malware Puts Your Security at Risk- Digitdefence



How Malware Puts Your Security at Risk- DigitdefenceRosy G Malware can infiltrate your systems, stealing sensitive data, disrupting operations, and opening the door to further cyberattacks. It exploits system vulnerabilities, putting both personal and business information at significant risk.
What is Firewall in Cloud Computing - Digitdefence



What is Firewall in Cloud Computing - DigitdefenceRosy G A firewall in cloud computing is a security system that monitors and controls incoming and outgoing network traffic based on predetermined security rules, protecting cloud-based assets from unauthorized access and cyber threats. Cloud firewalls act as a virtual barrier, securing data flow between cloud services and users, and preventing potential breaches.
What is Identity and Access Management.pdf



What is Identity and Access Management.pdfRosy G Identity and Access Management (IAM) is a cybersecurity framework that ensures only authorized users can access specific resources within a system. It involves processes like authentication and access control to protect sensitive data and prevent unauthorized access.
Why Cloud Server Security Is Essential for Your Business.pptx.pdf



Why Cloud Server Security Is Essential for Your Business.pptx.pdfRosy G Cloud server security protects sensitive business data from cyber threats, ensuring continuous operations and safeguarding customer trust. A secure cloud environment also helps prevent costly breaches and compliance issues, vital for business stability and growth.
Ad
Recently uploaded (20)
SCI BIZ TECH QUIZ (OPEN) PRELIMS XTASY 2025.pptx



SCI BIZ TECH QUIZ (OPEN) PRELIMS XTASY 2025.pptxRonisha Das SCI BIZ TECH QUIZ (OPEN) PRELIMS - XTASY 2025
Political History of Pala dynasty Pala Rulers NEP.pptx



Political History of Pala dynasty Pala Rulers NEP.pptxArya Mahila P. G. College, Banaras Hindu University, Varanasi, India. The Pala kings were people-protectors. In fact, Gopal was elected to the throne only to end Matsya Nyaya. Bhagalpur Abhiledh states that Dharmapala imposed only fair taxes on the people. Rampala abolished the unjust taxes imposed by Bhima. The Pala rulers were lovers of learning. Vikramshila University was established by Dharmapala. He opened 50 other learning centers. A famous Buddhist scholar named Haribhadra was to be present in his court. Devpala appointed another Buddhist scholar named Veerdeva as the vice president of Nalanda Vihar. Among other scholars of this period, Sandhyakar Nandi, Chakrapani Dutta and Vajradatta are especially famous. Sandhyakar Nandi wrote the famous poem of this period 'Ramcharit'.
Introduction to Vibe Coding and Vibe Engineering



Introduction to Vibe Coding and Vibe EngineeringDamian T. Gordon Introduction to Vibe Coding and Vibe Engineering
YSPH VMOC Special Report - Measles Outbreak Southwest US 4-30-2025.pptx



YSPH VMOC Special Report - Measles Outbreak Southwest US 4-30-2025.pptxYale School of Public Health - The Virtual Medical Operations Center (VMOC) A measles outbreak originating in West Texas has been linked to confirmed cases in New Mexico, with additional cases reported in Oklahoma and Kansas. The current case count is 795 from Texas, New Mexico, Oklahoma, and Kansas. 95 individuals have required hospitalization, and 3 deaths, 2 children in Texas and one adult in New Mexico. These fatalities mark the first measles-related deaths in the United States since 2015 and the first pediatric measles death since 2003.
The YSPH Virtual Medical Operations Center Briefs (VMOC) were created as a service-learning project by faculty and graduate students at the Yale School of Public Health in response to the 2010 Haiti Earthquake. Each year, the VMOC Briefs are produced by students enrolled in Environmental Health Science Course 581 - Public Health Emergencies: Disaster Planning and Response. These briefs compile diverse information sources – including status reports, maps, news articles, and web content– into a single, easily digestible document that can be widely shared and used interactively. Key features of this report include:
- Comprehensive Overview: Provides situation updates, maps, relevant news, and web resources.
- Accessibility: Designed for easy reading, wide distribution, and interactive use.
- Collaboration: The “unlocked" format enables other responders to share, copy, and adapt seamlessly. The students learn by doing, quickly discovering how and where to find critical information and presenting it in an easily understood manner.
How to Customize Your Financial Reports & Tax Reports With Odoo 17 Accounting



How to Customize Your Financial Reports & Tax Reports With Odoo 17 AccountingCeline George The Accounting module in Odoo 17 is a complete tool designed to manage all financial aspects of a business. Odoo offers a comprehensive set of tools for generating financial and tax reports, which are crucial for managing a company's finances and ensuring compliance with tax regulations.
Odoo Inventory Rules and Routes v17 - Odoo Slides



Odoo Inventory Rules and Routes v17 - Odoo SlidesCeline George Odoo's inventory management system is highly flexible and powerful, allowing businesses to efficiently manage their stock operations through the use of Rules and Routes.
How to track Cost and Revenue using Analytic Accounts in odoo Accounting, App...



How to track Cost and Revenue using Analytic Accounts in odoo Accounting, App...Celine George Analytic accounts are used to track and manage financial transactions related to specific projects, departments, or business units. They provide detailed insights into costs and revenues at a granular level, independent of the main accounting system. This helps to better understand profitability, performance, and resource allocation, making it easier to make informed financial decisions and strategic planning.
YSPH VMOC Special Report - Measles Outbreak Southwest US 5-3-2025.pptx



YSPH VMOC Special Report - Measles Outbreak Southwest US 5-3-2025.pptxYale School of Public Health - The Virtual Medical Operations Center (VMOC) A measles outbreak originating in West Texas has been linked to confirmed cases in New Mexico, with additional cases reported in Oklahoma and Kansas. The current case count is 817 from Texas, New Mexico, Oklahoma, and Kansas. 97 individuals have required hospitalization, and 3 deaths, 2 children in Texas and one adult in New Mexico. These fatalities mark the first measles-related deaths in the United States since 2015 and the first pediatric measles death since 2003.
The YSPH Virtual Medical Operations Center Briefs (VMOC) were created as a service-learning project by faculty and graduate students at the Yale School of Public Health in response to the 2010 Haiti Earthquake. Each year, the VMOC Briefs are produced by students enrolled in Environmental Health Science Course 581 - Public Health Emergencies: Disaster Planning and Response. These briefs compile diverse information sources – including status reports, maps, news articles, and web content– into a single, easily digestible document that can be widely shared and used interactively. Key features of this report include:
- Comprehensive Overview: Provides situation updates, maps, relevant news, and web resources.
- Accessibility: Designed for easy reading, wide distribution, and interactive use.
- Collaboration: The “unlocked" format enables other responders to share, copy, and adapt seamlessly. The students learn by doing, quickly discovering how and where to find critical information and presenting it in an easily understood manner.
CURRENT CASE COUNT: 817 (As of 05/3/2025)
• Texas: 688 (+20)(62% of these cases are in Gaines County).
• New Mexico: 67 (+1 )(92.4% of the cases are from Eddy County)
• Oklahoma: 16 (+1)
• Kansas: 46 (32% of the cases are from Gray County)
HOSPITALIZATIONS: 97 (+2)
• Texas: 89 (+2) - This is 13.02% of all TX cases.
• New Mexico: 7 - This is 10.6% of all NM cases.
• Kansas: 1 - This is 2.7% of all KS cases.
DEATHS: 3
• Texas: 2 – This is 0.31% of all cases
• New Mexico: 1 – This is 1.54% of all cases
US NATIONAL CASE COUNT: 967 (Confirmed and suspected):
INTERNATIONAL SPREAD (As of 4/2/2025)
• Mexico – 865 (+58)
‒Chihuahua, Mexico: 844 (+58) cases, 3 hospitalizations, 1 fatality
• Canada: 1531 (+270) (This reflects Ontario's Outbreak, which began 11/24)
‒Ontario, Canada – 1243 (+223) cases, 84 hospitalizations.
• Europe: 6,814
To study the nervous system of insect.pptx



To study the nervous system of insect.pptxArshad Shaikh The *nervous system of insects* is a complex network of nerve cells (neurons) and supporting cells that process and transmit information. Here's an overview:
Structure
1. *Brain*: The insect brain is a complex structure that processes sensory information, controls behavior, and integrates information.
2. *Ventral nerve cord*: A chain of ganglia (nerve clusters) that runs along the insect's body, controlling movement and sensory processing.
3. *Peripheral nervous system*: Nerves that connect the central nervous system to sensory organs and muscles.
Functions
1. *Sensory processing*: Insects can detect and respond to various stimuli, such as light, sound, touch, taste, and smell.
2. *Motor control*: The nervous system controls movement, including walking, flying, and feeding.
3. *Behavioral responThe *nervous system of insects* is a complex network of nerve cells (neurons) and supporting cells that process and transmit information. Here's an overview:
Structure
1. *Brain*: The insect brain is a complex structure that processes sensory information, controls behavior, and integrates information.
2. *Ventral nerve cord*: A chain of ganglia (nerve clusters) that runs along the insect's body, controlling movement and sensory processing.
3. *Peripheral nervous system*: Nerves that connect the central nervous system to sensory organs and muscles.
Functions
1. *Sensory processing*: Insects can detect and respond to various stimuli, such as light, sound, touch, taste, and smell.
2. *Motor control*: The nervous system controls movement, including walking, flying, and feeding.
3. *Behavioral responses*: Insects can exhibit complex behaviors, such as mating, foraging, and social interactions.
Characteristics
1. *Decentralized*: Insect nervous systems have some autonomy in different body parts.
2. *Specialized*: Different parts of the nervous system are specialized for specific functions.
3. *Efficient*: Insect nervous systems are highly efficient, allowing for rapid processing and response to stimuli.
The insect nervous system is a remarkable example of evolutionary adaptation, enabling insects to thrive in diverse environments.
The insect nervous system is a remarkable example of evolutionary adaptation, enabling insects to thrive
UNIT 3 NATIONAL HEALTH PROGRAMMEE. SOCIAL AND PREVENTIVE PHARMACY



UNIT 3 NATIONAL HEALTH PROGRAMMEE. SOCIAL AND PREVENTIVE PHARMACYDR.PRISCILLA MARY J NATIONAL HEALTH PROGRAMMEE
Quality Contril Analysis of Containers.pdf



Quality Contril Analysis of Containers.pdfDr. Bindiya Chauhan Quality control test for containers, rubber closures and secondary packing materials.
One Hot encoding a revolution in Machine learning



One Hot encoding a revolution in Machine learningmomer9505 A brief introduction to ONE HOT encoding a way to communicate with machines
Understanding P–N Junction Semiconductors: A Beginner’s Guide



Understanding P–N Junction Semiconductors: A Beginner’s GuideGS Virdi Dive into the fundamentals of P–N junctions, the heart of every diode and semiconductor device. In this concise presentation, Dr. G.S. Virdi (Former Chief Scientist, CSIR-CEERI Pilani) covers:
What Is a P–N Junction? Learn how P-type and N-type materials join to create a diode.
Depletion Region & Biasing: See how forward and reverse bias shape the voltage–current behavior.
V–I Characteristics: Understand the curve that defines diode operation.
Real-World Uses: Discover common applications in rectifiers, signal clipping, and more.
Ideal for electronics students, hobbyists, and engineers seeking a clear, practical introduction to P–N junction semiconductors.
How to Manage Opening & Closing Controls in Odoo 17 POS



How to Manage Opening & Closing Controls in Odoo 17 POSCeline George In Odoo 17 Point of Sale, the opening and closing controls are key for cash management. At the start of a shift, cashiers log in and enter the starting cash amount, marking the beginning of financial tracking. Throughout the shift, every transaction is recorded, creating an audit trail.
The ever evoilving world of science /7th class science curiosity /samyans aca...



The ever evoilving world of science /7th class science curiosity /samyans aca...Sandeep Swamy The Ever-Evolving World of
Science
Welcome to Grade 7 Science4not just a textbook with facts, but an invitation to
question, experiment, and explore the beautiful world we live in. From tiny cells
inside a leaf to the movement of celestial bodies, from household materials to
underground water flows, this journey will challenge your thinking and expand
your knowledge.
Notice something special about this book? The page numbers follow the playful
flight of a butterfly and a soaring paper plane! Just as these objects take flight,
learning soars when curiosity leads the way. Simple observations, like paper
planes, have inspired scientific explorations throughout history.
LDMMIA Reiki Master Spring 2025 Mini Updates



LDMMIA Reiki Master Spring 2025 Mini UpdatesLDM Mia eStudios As of Mid to April Ending, I am building a new Reiki-Yoga Series. No worries, they are free workshops. So far, I have 3 presentations so its a gradual process. If interested visit: https://www.slideshare.net/YogaPrincess
https://ldmchapels.weebly.com
Blessings and Happy Spring. We are hitting Mid Season.
Multi-currency in odoo accounting and Update exchange rates automatically in ...



Multi-currency in odoo accounting and Update exchange rates automatically in ...Celine George Most business transactions use the currencies of several countries for financial operations. For global transactions, multi-currency management is essential for enabling international trade.
Metamorphosis: Life's Transformative Journey



Metamorphosis: Life's Transformative JourneyArshad Shaikh *Metamorphosis* is a biological process where an animal undergoes a dramatic transformation from a juvenile or larval stage to a adult stage, often involving significant changes in form and structure. This process is commonly seen in insects, amphibians, and some other animals.
Political History of Pala dynasty Pala Rulers NEP.pptx



Political History of Pala dynasty Pala Rulers NEP.pptxArya Mahila P. G. College, Banaras Hindu University, Varanasi, India.
YSPH VMOC Special Report - Measles Outbreak Southwest US 4-30-2025.pptx



YSPH VMOC Special Report - Measles Outbreak Southwest US 4-30-2025.pptxYale School of Public Health - The Virtual Medical Operations Center (VMOC)
YSPH VMOC Special Report - Measles Outbreak Southwest US 5-3-2025.pptx



YSPH VMOC Special Report - Measles Outbreak Southwest US 5-3-2025.pptxYale School of Public Health - The Virtual Medical Operations Center (VMOC)
Ad
Essential Network Security Principles - Digitdefence
- 2. The CIA Triad: Confidentiality, Integrity, and Availability 01 02 03 Confidentiality Defined Integrity Assurance Availability Importance Ensures that sensitive information is accessed only by authorized individuals, employing encryption and access controls to protect data from unauthorized disclosure. Involves maintaining the accuracy and consistency of data over its lifecycle, utilizing checksums and hashing techniques to detect unauthorized modifications. Guarantees that information and resources are accessible to authorized users when needed, emphasizing the need for redundancy, failover systems, and regular maintenance. digitdefence.com
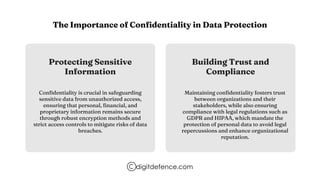
- 3. The Importance of Confidentiality in Data Protection Protecting Sensitive Information Building Trust and Compliance Confidentiality is crucial in safeguarding sensitive data from unauthorized access, ensuring that personal, financial, and proprietary information remains secure through robust encryption methods and strict access controls to mitigate risks of data breaches. Maintaining confidentiality fosters trust between organizations and their stakeholders, while also ensuring compliance with legal regulations such as GDPR and HIPAA, which mandate the protection of personal data to avoid legal repercussions and enhance organizational reputation. digitdefence.com
- 4. Ensuring Data Integrity: Methods and Practices Data Validation Techniques Use of Checksums and Hashing Regular Audits and Monitoring Implementing rigorous data validation methods, such as input validation and data type checks, ensures that only accurate and expected data is processed, reducing the risk of corruption and maintaining overall data integrity. Employing checksums and cryptographic hashing algorithms allows for the detection of unauthorized changes to data, providing a mechanism to verify integrity during data transmission and storage. Conducting regular audits and continuous monitoring of data access and modifications helps identify potential integrity breaches early, enabling timely corrective actions to preserve the accuracy and reliability of critical information. digitdefence.com
- 5. 01 02 03 Availability: Keeping Systems Accessible and Functional Redundancy Strategies Load Balancing Techniques Regular Maintenance Practices Implementing redundancy through backup systems and failover mechanisms ensures that critical services remain operational during hardware failures or outages, minimizing downtime and maintaining user access. Utilizing load balancing distributes network traffic across multiple servers, enhancing system performance and availability by preventing any single server from becoming a bottleneck or point of failure. Conducting routine maintenance, including software updates and system checks, is essential for identifying potential vulnerabilities and ensuring that systems remain functional and accessible to authorized users at all times. digitdefence.com
- 6. The Role of Firewalls in Network Security Firewall Functionality Overview Types of Firewalls Integration with Security Policies Firewalls act as a barrier between trusted internal networks and untrusted external networks, monitoring and controlling incoming and outgoing traffic based on predetermined security rules to prevent unauthorized access. Various types of firewalls, including packet-filtering, stateful inspection, and application-layer firewalls, offer different levels of security and functionality, allowing organizations to choose the best fit for their specific network architecture. Effective firewall implementation requires alignment with broader security policies, ensuring that they not only block malicious traffic but also support overall network security strategies through regular updates and configuration reviews. digitdefence.com
- 7. Regular Software Updates and Patch Management Regular software updates are crucial for addressing vulnerabilities, as they provide essential security patches that protect systems from emerging threats and exploits targeting outdated software. Importance of Timely Updates 01 Implementing automated patch management solutions streamlines the update process, ensuring that all software components are consistently updated without manual intervention, reducing the risk of human error. Automated Patch Management Systems 02 Prior to deployment, thorough testing and validation of updates are necessary to prevent compatibility issues and ensure that new patches do not disrupt existing system functionality or performance. Testing and Validation Procedures 03 digitdefence.com
- 8. The Importance of Security Audits Identifying Vulnerabilities Compliance and Regulatory Requirements Enhancing Security Policies Security audits systematically evaluate an organization's security posture, identifying vulnerabilities and weaknesses in systems and processes that could be exploited by attackers, thereby enabling proactive risk management. Regular security audits help organizations meet compliance standards and regulatory requirements, such as GDPR and HIPAA, ensuring that they adhere to legal obligations while protecting sensitive data from breaches. The insights gained from security audits inform the development and refinement of security policies and practices, fostering a culture of continuous improvement in network security measures to adapt to evolving threats. digitdefence.com
- 9. The Impact of Cloud Computing on Security Shared Responsibility Model In cloud computing, security responsibilities are shared between the provider and the customer, necessitating clear understanding and delineation of roles to ensure comprehensive protection against threats. Data Breach Risks The migration of sensitive data to cloud environments increases exposure to potential data breaches, highlighting the need for robust encryption and access controls to safeguard information from unauthorized access. Compliance Challenges Organizations must navigate complex compliance landscapes when utilizing cloud services, as varying regulations require adherence to specific security standards, necessitating ongoing assessments and adjustments to security practices. digitdefence.com



