Ad
EXAM NOTES for DOD Standard 8570 CompTia Advanced Security Practitioner (CASP)
- 1. Notes for the CompTIA CASP exam Posted as a courtesy by: Dave Sweigert, CEH, CISSP, CISA, CHS-III, HCISPP, PCIP, PMP, SEC+ July 27, 2017 (Version Five) PREFACE EXAM OBJECTIVES (BY DOMAIN) Enterprise Security 30% Risk Management and Incident Response 20% Research and Analysis 18% Integration of Computing, Communications and Business Disciplines 16% Technical Integration of Enterprise Components 16%
- 2. Table of Contents Contents I. Enterprise Security..........................................................................................................................3 Placement of Security Appliances.......................................................................................................3 SELinux Mandatory Access Control (MAC) .......................................................................................4 Storage Area Network (SAN) ...............................................................................................................5 Multiple O/S encryption on a single SDD ...........................................................................................6 TOCTOU attacks....................................................................................................................................7 Network File System (NFS) and Common Internet File System (CIFS)........................................8 Storage Area Network (SAN) protocols..............................................................................................8 NAS vs. SANS......................................................................................................................................10 Dynamic Disk Pools vs. RAID ............................................................................................................12 Microsoft Group Policies .....................................................................................................................13 WMI filters..............................................................................................................................................14 Secure Boot ..........................................................................................................................................15 SABSA Architecture.............................................................................................................................16 II. Risk management and Incident Response..............................................................................22 Risk Terms ............................................................................................................................................22 III. Research, Analysis and Assessment ...................................................................................28 IV. Integration of Computing, Communications and Business Disciplines .....................30 Enterprise application integration enablers......................................................................................32 DEFINITIONS ...........................................................................................................................................34
- 3. I. Enterprise Security 1.1 Given a scenario, select appropriate cryptographic concepts and techniques. 1.2 Explain the security implications associated with enterprise storage. 1.3 Given a scenario, analyze network and security components, concepts and architectures. 1.4 Given a scenario, select and troubleshoot security controls for hosts. 1.5 Differentiate application vulnerabilities and select appropriate security controls. Placement of Security Appliances Firewalls STATELESS Stateless firewalls watch network traffic, and restrict or block packets based on source and destination addresses or other static values. They are not 'aware' of traffic patterns or data flows. A stateless firewall uses simple rule-sets that do not account for the possibility that a packet might be received by the firewall 'pretending' to be something you asked for. STATEFUL Stateful firewalls can watch traffic streams from end to end. They are aware of communication paths and can implement various IP Security (IPsec) functions such as tunnels and encryption. In technical terms, this means that stateful firewalls can tell what stage a TCP connection is in (open, open sent, synchronized, synchronization acknowledge or established), it can tell if the MTU has changed, whether packets have fragmented etc. http://www.inetdaemon.com/tutorials/information_security/devices/firewalls/stateful_vs_stateless_firew alls.shtml
- 4. https://i-technet.sec.s-msft.com/dynimg/IC49415.gif TPM and vTPM Trusted Platform Module (TPM). A TPM is a cryptographic processor which behaves much like a Hardware Security Module (HSM). Usually seen on newer laptops. TPM contains: true random number generator, key generator, hash generator and secure key store. Virtual Trusted Platform Module (vTPM). A vTPM is a software module that performs the function of a TPM in a virtualized environment. The TPM is a specialized chip on an endpoint device that stores RSA encryption keys specific to the host system for hardware authentication. Each TPM chip contains an RSA key pair called the Endorsement Key (EK). The vTPM makes secure storage and cryptographic functions available to operating systems and applications running in virtual machines. NOTE: BitLocker disk encryption normally requires a TPM on Windows. Microsoft’s EFS encryption can never use a TPM. The new “device encryption” feature on Windows 10 and 8.1 also requires a modern TPM, which is why it’s only enabled on new hardware. SELinux Mandatory Access Control (MAC)
- 5. MAC evolved out of the multi-level security (MLS) program at NSA and DoD. An NSA research project called SELinux added a Mandatory Access Control architecture to the Linux Kernel, which was merged into the mainline version of Linux in August 20031. NOTE: Red Hat Enterprise Linux version 4 (and later versions) come with a SELinux- enabled kernel. Storage Area Network (SAN) A storage area network (SAN) is a network which provides access to consolidated, block level data storage. SANs are primarily used to enhance storage devices, such as disk arrays, tape libraries, and optical jukeboxes, accessible to servers so that the devices appear to the operating system as locally attached devices. A SAN typically has its own network of storage devices that are generally not accessible through the local area network (LAN) by other devices2. Knowledge reminder: 1. Cryptographic concepts around hashing, code signing, PKI concepts and various encryption methods 2. Enterprise storage concepts and technologies like NAS and SAN and the associated protocols like CIFS, NFS, iSCSI and FCoE 3. Host security issues and secure concepts including secure boot, TPM and measured launch 4. Application vulnerability issues including HTML5, AJAX, Javascript and others 1 https://en.wikipedia.org/wiki/Mandatory_access_control 2 https://en.wikipedia.org/wiki/Storage_area_network
- 6. Multiple O/S encryption on a single SDD A solid-state drive (SSD) is a nonvolatile storage device that stores persistent data on solid-state flash memory. Solid-state drives actually aren't hard drives in the traditional sense of the term, as there are no moving parts involved. A traditional hard disk drive (HDD) consists of a spinning disk with a read/write head on a mechanical arm called an actuator. An SSD, on the other hand, has an array of semiconductor memory organized as a disk drive, using integrated circuits (ICs) rather than magnetic or optical storage media. An SSD may also be referred to as a solid-state disk3. Windows 7: The first issue here is that the only versions of Windows 7 that support Bitlocker are Enterprise and Ultimate. If you have Windows 7 Pro, you're out of luck. You may also find issues on trying to boot the Windows 7 installer on a PC with UEFI, in which case you may have to drop back to legacy mode to work round this. Unlike Windows 8, if the PC doesn't have a Trusted Platform Module, the only way to unlock the Bitlocker drive on boot is to use a USB key. Without a TPM, you cannot use a password for Bitlocker in Windows 74. If the PC is using Windows 7 Ultimate or Enterprise, or Windows 8 Pro or Enterprise, you can use BitLocker, which comes with these versions of Windows. But you have to know what you're doing. BitLocker works best in an environment where a professional IT department serves users who may not know what the word encrypt means. You can set it up so that the user doesn't even know that the drive is encrypted. When they log into Windows with their password, they get access to the encrypted files. If they log into another account, or boot with another OS, the files are unreadable. What's more, if you need to reinstall Windows, or restore the files from a backup, you'll need a special digital key that's created when you encrypt the drive. That key has to be stored elsewhere and someone has to know where to find it5. 3 http://searchsolidstatestorage.techtarget.com/definition/SSD-solid-state-drive 4 http://www.stevenmaude.co.uk/posts/a-beginners-guide-to-os-encryption-dual 5 http://www.pcworld.com/article/2858642/you-can-encrypt-your-hard-drive-but-the-protection-may-not-be- worth-the-hassle.html
- 7. TOCTOU attacks In software development, time of check to time of use (TOCTTOU or TOCTOU, pronounced "TOCK too") is a class of software bug caused by changes in a system between the checking of a condition (such as a security credential) and the use of the results of that check. This is one example of a race condition.6 Time of check (TOC) — When the resource is inspected. For example, all data from the browser is considered “tainted” because a malicious user may have manipulated it. If the data passes a validation function, then the taint may be removed and the data permitted entry deeper into the app. For example, the app checks whether an email address is well-formed or text contains <script> tags. Time of use (TOU) — When the app performs an operation on the resource. For example, inserting the data into a SQL statement or inserting text into a web page. Weaknesses occur when the app assumes the state of the resource has not changed since the last check; vulnerabilities occur when the state change relates to a security control7. CWE-367: Time-of-check Time-of-use (TOCTOU) Race Condition Description Summary The software checks the state of a resource before using that resource, but the resource's state can change between the check and the use in a way that invalidates the results of the check. This can cause the software to perform invalid actions when the resource is in an unexpected state. Extended Description This weakness can be security-relevant when an attacker can influence the state of the resource between check and use. This can happen with shared resources such as files, memory, or even variables in multithreaded programs8. CAPEC-29: Leveraging Time-of-Check and Time-of-Use (TOCTOU) Race Conditions This attack targets a race condition occurring between the time of check (state) for a resource and the time of use of a resource. The typical example is the file access. The attacker can leverage a file access race condition by "running the race", meaning that he would modify the resource between the first time the target program accesses the file and the time the target program uses the file. During that period of time, the attacker could do something such as replace the file and cause an escalation of privilege9. 6 https://en.wikipedia.org/wiki/Time_of_check_to_time_of_use 7 https://deadliestwebattacks.com/tag/toctou/ 8 https://cwe.mitre.org/data/definitions/367.html 9 https://capec.mitre.org/data/definitions/29.html
- 8. Network File System (NFS) and Common Internet File System (CIFS) What is the difference between NFS and CIFS? Can you explain when you should use CIFS vs. NFS? NFS is the "Network File System" for Unix and Linux operating systems. It allows files to be shared transparently between servers, desktops, laptops etc. It is a client/server application that allows a user to view, store and update files on a remote computer as though they were on their own computer. Using NFS, the user or a system administrator can mount all or a portion of a file system. CIFS is the "Common Internet File System" used by Windows operating systems for file sharing. CIFS uses the client/server programming model. A client program makes a request of a server program (usually in another computer) for access to a file or to pass a message to a program that runs in the server computer. The server takes the requested action and returns a response. CIFS is a public or open variation of the Server Message Block Protocol (SMB) developed and used by Microsoft, and it uses the TCP/IP protocol. NFS and CIFS are the primary file systems used in NAS. Comparing CIFS vs. NFS, CIFS tends to be a bit more "chatty" in its communications. This may require file protocol optimization over a wide area network. http://searchstorage.techtarget.com/answer/NFS-vs-CIFS Storage Area Network (SAN) protocols Internet Small Computer System Interface (iSCSI). iSCSI (I.P.-based protocol) works on top of the Transport Control Protocol (TCP) and allows the SCSI command to be sent end-to-end over local-area networks (LANs), wide-area networks (WANs) or the Internet. IBM developed iSCSI as a proof of concept in 1998, and presented the first draft of the iSCSI standard to the Internet Engineering Task Force (IETF) in 2000. The protocol was ratified in 2003. The major server vendors offer iSCSI as a connectivity option, to provide virtual machines with block-level access to storage volumes, without the need to deploy high- performance Fibre Channel hardware. iSCSI has been proven capable of supporting enterprise-class applications assuming that the specific solution can reach the desired level of performance and scalability and that management is simple enough not to negatively affect the total cost of ownership (TCO)10. 10 http://www.cisco.com/c/en/us/products/collateral/switches/nexus-5000-series-switches/white_paper_c11- 495142.html
- 9. Fibre Channel over Ethernet (FCoE). FCoe is a standards-based protocol that natively maps Fibre Channel to Ethernet for transport in a lossless Ethernet LAN. FCoE allows the consolidation of LAN and Fibre Channel SAN traffic over a single switching infrastructure in the data center. http://imexresearch.com/newsletters/images/Feb09/fcoe_vs.jpg
- 10. https://image.slidesharecdn.com/emcworldfcoeiscsi2009share-090522131252-phpapp01/95/fibre-channel-over-ethernet-fcoe- iscsi-and-the-converged-data-center-14-728.jpg?cb=1242998073 iSCSI, NFS, FC, and FCoE Basics iSCSI means you map your storage over TCP/IP. You typically put in dedicated Ethernet network cards and a separate network switch. Each server and each storage device has its own IP address(es), and you connect by specifying an IP address where your drive lives. In Windows, each drive shows up in Computer Manager as a hard drive, and you format it. This is called block storage. NFS means you access a file share like MyFileServerNameMyShareName, and you put files on it. In Windows, this is a mapped network drive. You access folders and files there, but you don’t see the network mapped drive in Computer Manager as a local drive letter. You don’t get exclusive access to NFS drives. You don’t need a separate network cable for NFS – you just access your file shares over whatever network you want. Fibre Channel is a lot like iSCSI, except it uses fiberoptic cables instead of Ethernet cables. It’s a separate dedicated network just for storage, so you don’t have to worry as much about performance contention – although you do still have to worry. Fibre Channel Over Ethernet (FCoE) runs the FC protocol over Ethernet cables, specifically 10Gb Ethernet. This gained niche popularity because you can use just one network (10Gb Ethernet) for both regular network traffic and storage network traffic rather than having one set of switches for fiber and one set for Ethernet. https://www.brentozar.com/archive/2012/05/storage-protocol-basics-iscsi-nfs-fibre-channel-fcoe/ NAS vs. SANS
- 11. Network-attached storage (NAS) is a file-level computer data storage server connected to a computer network providing data access to a heterogeneous group of clients. NAS is specialized for serving files either by its hardware, software, or configuration. It is often manufactured as a computer appliance – a purpose-built specialized computer. NAS systems are networked appliances which contain one or more storage drives, often arranged into logical, redundant storage containers or RAID. Network-attached storage removes the responsibility of file serving from other servers on the network. They typically provide access to files using network file sharing protocols such as NFS, SMB/CIFS, or AFP. From the mid-1990s, NAS devices began gaining popularity as a convenient method of sharing files among multiple computers. Potential benefits of dedicated network-attached storage, compared to general-purpose servers also serving files, include faster data access, easier administration, and simple configuration.11 NAS allows files to be retrieved across a computer network. It includes a dedicated hardware device (often called the head) that connects to a local area network (usually via Ethernet). This NAS “server” authenticates clients and manages file operations in much the same manner as traditional file servers, through well-established network protocols like NFS (Network File Service) and CIFS/SMB (Common Internet File System/System Message Block).12 http://cdn2.hubspot.net/hub/62530/file-14948438-png/images/difference-between-nas-and-san.png 11 https://en.wikipedia.org/wiki/Network-attached_storage 12 http://www.hosting.com/cloud-storage-the-difference-between-nas-vs-san/
- 12. As Internet technologies like TCP/IP and Ethernet have proliferated worldwide, some SAN products are making the transition from Fibre Channel to the same IP-based approach NAS uses. Also, with the rapid improvements in disk storage technology, today's NAS devices now offer capacities and performance that once were only possible with SAN. These two industry factors have led to a partial convergence of NAS and SAN approaches to network storage.13 Note about FCoE: Data is transmitted over this channel in an unencrypted fashion (as is true for NAS). Therefore, this channel can be susceptible to hackers. FCoE is NOT routable, it is operated over Ethernet. The outset of 10 G/b/p/s over Ethernet made FCoE possible. FCoE uses FCP, the Fibre Channel Protocol encapsulated in an Ethernet header. FCoE abandons IP protocol and IP addresses (e.g. 192.168.1.xx), instead employing a new 802.3 Ethertype. The approach eliminates TCP altogether, replacing it with a hardware flow control scheme which guarantees packet delivery and can match performance metrics found on native Fiber channel networks. NICs are called Converged Network Adapters (CAN). Dynamic Disk Pools vs. RAID Dynamic Disk Pooling (DDP) dynamically distributes data, spare capacity, and protection information across a pool of disk drives. DDP improves the time and performance of traditional RAID arrays. Because RAID cannot keep up with increasing disk capacities, DDP was created to be more versatile by providing better rebuild times. In an RAID array when a drive fails, the remaining drives are read, 13 https://www.lifewire.com/san-vs-nas-818005
- 13. parity recomputed, and the result is written to the spare drive. This is done from the initial logical block of the array to the last block in the array. This operation is time consuming because all data needs to be recomputed from the beginning of the array to the end of the array, and degrades performance, because although there are parallel reads, there is one single write to the spare drive. Thus, this single write becomes a bottleneck in the system. In DDP, a disk pool is a set of drives that are logically grouped together in the storage subsystem, where data is distributed across all drives in the pool. The drives in each disk pool must be of the same drive type and drive media type, and they must be similar in size. Unlike RAID, there is no specific spare drive, rather, all drives have spare space that is reserved. When a drive fails, the remaining drives are read, the missing data is recomputed, and the result is written to multiple drives in their spare space. This operation is done on the pieces of data that are missing. The result is parallel reads and parallel writes, which significantly speeds up the rebuild time after a single drive failure. Both RAID and DDP are techniques for striping data and parity information across a set of disks to provide fault tolerance, but how they operate to attain this goal is different. https://www.ibm.com/support/knowledgecenter/en/STFS69_4.0.0/ts7760_ddp.html Microsoft Group Policies Group Policy, in part, controls what users can and cannot do on a computer system: for example, to enforce a password complexity policy that prevents users from choosing an overly simple password, to allow or prevent unidentified users from remote computers to connect to a network share, to block access to the Windows Task Manager or to restrict access to certain folders. A set of such configurations is called a Group Policy Object (GPO). As part of Microsoft's IntelliMirror technologies, Group Policy aims to reduce the cost of supporting users. IntelliMirror technologies relate to the management of disconnected machines or roaming users and include roaming user profiles, folder redirection, and offline files.14 Group Policy Objects are processed in the following order (from top to bottom) 1. Local - Any settings in the computer's local policy. Prior to Windows Vista, there was only one local group policy stored per computer. Windows Vista and later Windows versions allow individual group policies per user accounts.[5] 2. Site - Any Group Policies associated with the Active Directory site in which the computer resides. (An Active Directory site is a logical grouping of computers, intended to facilitate management of those computers based on their physical proximity.) If multiple policies are linked to a site, they are processed in the order set by the administrator. 14 https://en.wikipedia.org/wiki/Group_Policy
- 14. 3. Domain - Any Group Policies associated with the Windows domain in which the computer resides. If multiple policies are linked to a domain, they are processed in the order set by the administrator. 4. Organizational Unit - Group policies assigned to the Active Directory organizational unit (OU) in which the computer or user are placed. (OUs are logical units that help organizing and managing a group of users, computers or other Active Directory objects.) If multiple policies are linked to an OU, they are processed in the order set by the administrator. http://i1-news.softpedia-static.com/images/news2/Microsoft-Patches-Critical-Remote-Code-Execution-Glitch-in-Group-Policy- 472770-2.jpg WMI filters You can use WMI filters to add a decision on when to apply a given group policy. This can be very useful when users or computers are located in a relatively flat structure instead of specific OU’s, for example. Filters can also help when you need to apply certain policies based on server roles, operating system version, network configuration, or other criteria. Windows evaluates these filters in the following order of overall Group Policy Processing: 1. Policies in hierarchy are located. 2. WMI Filters are checked. 3. Security settings are checked. 4. Finally, once everything has ‘passed’, a policy is applied.
- 15. So we find all the policies that exist in the user/computer’s Local, Site, Domain, and OU hierarchy. Then we determine if the WMI filter evaluates as TRUE. Then we verify that the user/computer has Read and Apply Group permissions for the GPO. This means that WMI filters are still less efficient than hierarchical linking, but can definitely use filters to make decisions in a non-hierarchical Active Directory design15. Secure Boot Secure Boot is a security standard developed by members of the PC industry to help make sure that your PC boots using only software that is trusted by the PC manufacturer. When the PC starts, the firmware checks the signature of each piece of boot software, including firmware drivers (Option ROMs) and the operating system. If the signatures are good, the PC boots, and the firmware gives control to the operating system. The following versions of Windows support Secure Boot: Windows 8.1, Windows Server 2012 R2, Windows RT 8.1, Windows 8, Windows Server 2012, and Windows RT16. BIOS Basic Input/Output System (BIOS) and also known as the System BIOS, ROM BIOS or PC BIOS) is a type of firmware used to perform hardware initialization during the booting process (power-on startup) on IBM PC compatible computers, and to provide runtime services for operating systems and programs.[ BIOS works by reading the first sector of the hard drive which has the next device’s address to initialize or code to execute. BIOS also selects the boot device that needs to be initialized for starting the operating system. Since BIOS has been in use since the very beginning, it still works in 16-bit mode, limiting the amount of code that can be read and executed from the firmware ROM17. UEFI Unified Extensible Firmware Interface (UEFI) is a specification for a software program that connects a computer's firmware to its operating system (OS). UEFI is expected to eventually replace BIOS. 15 https://blogs.technet.microsoft.com/askds/2008/09/11/fun-with-wmi-filters-in-group-policy/ 16 https://technet.microsoft.com/en-us/library/hh824987.aspx 17 https://www.maketecheasier.com/differences-between-uefi-and-bios/
- 16. Like BIOS, UEFI is installed at the time of manufacturing and is the first program that runs when a computer is turned on. It checks to see what hardware components the computing device has, wakes the components up and hands them over to the operating system. The new specification addresses several limitations of BIOS, including restrictions on hard disk partition size and the amount of time BIOS takes to perform its tasks. Because UEFI is programmable, original equipment manufacturer (OEM) developers can add applications and drivers, allowing UEFI to function as a lightweight operating system18. SABSA Architecture The SABSA Architecture model (Sherwood Applied Business Security Architecture) may be mentioned in the same context as the NIST (National institute of Standards and Technology) Special Publication 800-53 and the CobiT framework (Control Objectives for Information and Related Technologies). Enterprise Architecture (EA): the approach to align business requirements and strategy with the I.T. and security investments made. SABSA maps business requirements to architectural requirements. SABSA is a model and a methodology for developing risk-driven enterprise information security architectures and for delivering security infrastructure solutions that support critical business initiatives. The primary characteristic of the SABSA model is that everything must be derived from an analysis of the business requirements for security, especially those in which security has an enabling function through which new business opportunities can be developed and exploited. The process analyzes the business requirements at the outset, and creates a chain of traceability through the strategy and concept, design, implementation, and ongoing ‘manage and measure’ phases of the lifecycle to ensure that the business mandate is preserved. Framework tools created from practical experience further support the whole methodology. https://en.wikipedia.org/wiki/Sherwood_Applied_Business_Security_Architecture SABSA defines 85 common attributes; with seven main categories such as: user, management, operational, risk, technical, legal and business. 18 http://whatis.techtarget.com/definition/Unified-Extensible-Firmware-Interface-UEFI
- 17. https://image.slidesharecdn.com/8abaf9f1-1a34-4c64-bdac-f07cbf004dff-150202104945-conversion- gate02/95/sabsa-implementationpart-iver10-17-638.jpg?cb=1422874299 Applications Security Summary of application security issues (see OWASP Top Ten):
- 18. Injection (A1) Injection flaws allow attackers to relay malicious code through an application to another system. These attacks include calls to the operating system via system calls, the use of external programs via shell commands, as well as calls to backend databases via SQL (i.e., SQL injection). Whole scripts written in Perl, Python, and other languages can be injected into poorly designed applications and executed. Any time an application uses an interpreter of any type there is a danger of introducing an injection vulnerability. Input Validation (see unvalidated input, A1 con’t) Input validation is performed to ensure only properly formed data is entering the workflow in an information system, preventing malformed data from persisting in the database and triggering malfunction of various downstream components. Input validation should happen as early as possible in the data flow, preferably as soon as the data is received from the external party. https://www.owasp.org/index.php/Input_Validation_Cheat_Sheet# Goals_of_Input_Validation Broken Authentication (A2) Authentication and session management includes all aspects of handling user authentication and managing active sessions. Authentication is a critical aspect of this process, but even solid authentication mechanisms can be undermined by flawed credential management functions, including password change, forgot my password, remember my password, account update, and other related functions. Because “walk by” attacks are likely for many web applications, all account management functions should require re-authentication even if the user has a valid session id. (see also Session Management and SALTing of passwords). XSS (A3) Attacker injects a custom script. Cross-Site Scripting (XSS) attacks are a type of injection, in which malicious scripts are injected into otherwise benign and trusted web sites. XSS attacks occur when an attacker uses a web application to send malicious code, generally in the form of a browser side script, to a different end user. Flaws that allow these attacks to succeed are quite widespread and occur anywhere a web application uses input from a user within the output it generates without validating or encoding it. Vector 1: Inserting the unauthorized script Vector 2: Script is echoed back to primary site
- 19. Insecure Direct Object References – IDOR (A4) (Related to authorization of authenticated users to various applications). Potential threats can come from an authorized user of the system who alters a parameter value that directly points to an object that the user isn’t authorized to access. The user may be authorized to access the system, but not a specific object, such as a database record, specific file or even an URL. If the application doesn’t verify the user for that specific object, it can result in an insecure direct object reference flaw. Security Misconfiguration (A5) (Default pages and accounts, unpatched systems, unprotected files, etc.) Look out for presence of default access accounts, presence of unprotected files, leaving misconfiguration which allows lesser privileged user to get more secured content/ function, presence of logs in public library or available outside server/without authentication, unnecessary ports being kept open/default ports being used, availability of code files to be downloaded, exposing error message in detail to end user, exposing server technology in headers or html rendered and so on. Sensitive Data Exposure (A6) Sensitive data is information that can be used or manipulated for nefarious purposes to great effect, such as credit card numbers, tax IDs, and authentication credentials. Sensitive Data Exposure occurs when an application does not adequately protect sensitive information. The data can vary and anything from passwords, session tokens, credit card data to private health data and more can be exposed. Buffer Overflows Attackers generally use buffer overflows to corrupt the execution stack of a web application. By sending carefully crafted input to a web application, an attacker can cause the web application to execute arbitrary code, possibly taking over the machine. Attackers have managed to identify buffer overflows in a staggering array of products and components. Buffer overflow flaws can be present in both the web server and application server products that serve the static and dynamic portions of a site, or in the web application itself. Buffer overflows found in commonly-used server products are likely to become widely known and can pose a significant risk to users of these products. When web applications use libraries, such as a graphics library to generate images or a communications library to send e- mail, they open themselves to potential buffer overflow attacks. Literature detailing buffer overflow attacks against commonly-used products is readily available, and newly discovered vulnerabilities are reported almost daily. CSRF Cross-Site Request Forgery (CSRF) is an attack that forces an end user to execute unwanted actions on a web application in which they're currently authenticated. CSRF attacks specifically
- 20. target state-changing requests, not theft of data, since the attacker has no way to see the response to the forged request. With a little help of social engineering (such as sending a link via email or chat), an attacker may trick the users of a web application into executing actions of the attacker's choosing. If the victim is a normal user, a successful CSRF attack can force the user to perform state changing requests like transferring funds, changing their email address, and so forth. If the victim is an administrative account, CSRF can compromise the entire web application. Privilege escalation Privilege escalation occurs when a user gets to access more resources than is normally allowed when it should have been protected from the application. This is usually conducted from a flaw in the application. The result is that the application performs actions with more privileges than intended by the application developer or system administrator. The degree of the escalation depends on which privileges the attacker is authorized to possess and which privileges can be obtained in a successful attack. For example, a programming error that permits a user to gain extra privilege after successful authentication limits the degree of escalation because the user is already authorized to hold some privilege. Likewise, a remote attacker gaining superuser privilege without any authentication presents a greater degree of escalation. Session MGT A web session is a sequence of network HTTP request and response transactions associated to the same user. Modern and complex web applications require the retaining of information or status about each user for the duration of multiple requests. Therefore, sessions provide the ability to establish variables – such as access rights and localization settings – which will apply to each and every interaction a user has with the web application for the duration of the session. SQL injection A SQL injection attack consists of insertion or "injection" of a SQL query via the input data from the client to the application. A successful SQL injection exploit can read sensitive data from the database, modify database data (Insert/Update/Delete), execute administration operations on the database (such as shutdown the DBMS), recover the content of a given file present on the DBMS file system and in some cases issue commands to the operating system. SQL injection attacks are a type of injection attack, in
- 21. which SQL commands are injected into data-plane input in order to effect the execution of predefined SQL commands.
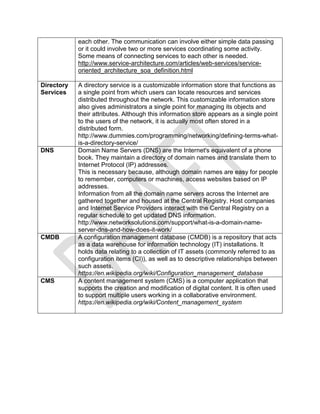
- 22. II. Risk management and Incident Response 2.1 Interpret business and industry influences and explain associated security risks. 2.2 Given a scenario, execute risk mitigation planning, strategies and controls. 2.3 Compare and contrast security, privacy policies and procedures based on organizational requirements. 2.4 Given a scenario, conduct incident response and recovery procedures. Risk concepts identify risk management techniques used to secure a network environment define new and changing models and strategies that are used to secure a network environment identify the security concerns that are associated with integrating diverse industries define the implications of creating third party information security identify the impact of de-perimeterization of network resources identify how internal and external influences affect network security define the information classification techniques and how they can be used when securing a network environment discuss CIA decisions and the requirements and policies that can be put in place when securing a network environment work with CIA aggregate scores in order to secure a network environment define how to create plans for worse case scenarios that can affect your organization define the system specific risk analysis techniques used to secure a network environment analyze the magnitude of impacts caused by events when you are securing a network environment calculate the likelihood of threats that can affect network security calculate the ROI and TCO of resources when securing a network environment define risk appetite strategies when securing a network environment define the risk management process when securing a network environment define the enterprise security architecture frameworks that can be used when securing a network environment define the methods for continuous improvement and monitoring when securing a network environment define how to use business continuity planning when securing a network environment define the role IT Governance plays when securing a network environment to understand basic security risks, mitigation, and prevention
- 23. Risk Terms RISK: Risk is the likelihood or probability that an event will occur that will cause a realization of a threat. Key words: occurrence, event, realization. THREAT: Threat is the potential of a risk – in that the threat is an agent that COULD cause potential damage to the enterprise. A threat could be a condition, circumstance, environment, etc.; such as: rain storm, civil unrest, bomb threat, etc. TYPES OF THREATS: Usually defined in three classes: natural, man-made, technological driven. Or, restated: natural, technology, human-caused. VULNERABILITY: A vulnerability is a weakness in the enterprise (hardware, software, procedural, etc.) that MAY be exploited by a threat agent. Once exploited, the vulnerability now is a realized risk that is damaging the organization. http://acriafrica.com/images/risk.gif ASSET IDENTIFUICATION: Normally an asset inventory. This can include hardware, software, intellectual property, etc. Essentially anything of value that can be damaged.
- 24. INFORMATION CLASSIFICATION: This process attempts to create priorities as to how data is protected by creating categories (see TOP SECRET, SECRET, CONFIDENTIAL for example). Labeling information as to how it should be classified can help align needed resources to information protection. Security Requirements Traceability Matrix (SRTM) is a grid that supplies documentation and a straightforward presentation of the required elements for security of a system. It is vital to incorporate the best level of security in technical projects that require such. SRTM can be used for any type of project. Requirements and tests can be easily tracked in relationship to one another. SRTM assures accountability for all processes and completion of all work. An SRTM between security requirements and test activities have a grid, comparable to an Excel spreadsheet. This spreadsheet contains a column for these items: Requirement identification number Description of the requirement Source of the requirement Objective of the test Verification method for the test19 19 https://www.cybrary.it/study-guides/what-is-the-security-requirements-traceability-matrix-srtm/
- 26. It also is necessary to keep abreast of any changes in the way users are performing their jobs. For example, suppose that over time, users are increasingly using chat sessions rather than email to discuss sensitive issues. In this situation, securing instant messaging communications becomes just as important as securing email. To keep up with the ever- changing ways users are choosing to work, you should: ■ Periodically monitor user behaviors to discover new areas of risk, including identifying not only new work methods but also any risky behaviors, such as writing passwords on sticky notes. ■ Mitigate, deter, and prevent risks (through training and new security policies). ■ Anticipate behaviors before they occur by researching trends (for example, mobile devices and user behavior trends). One of the factors that can change the risk profile of a particular activity or process is a change in the way the company does business. As partnerships are formed,mergers completed, assets sold, and new technologies introduced, security is always impacted in some way. The following business model and strategy require a fresh look at all parts of the enterprise security policies and procedures: - Partnerships - Outsourcing - Cloud Computing - Merger and Demerger/Divestiture
- 27. Third-party outsourcing is a liability that many organizations do not consider as part of their risk assessment. Any outsourcing agreement must ensure that the information that is entrusted to the other organization is protected by the proper security measures to fulfill all the regulatory and legal requirements. Like third-party outsourcing agreements, contract and procurement processes must be formalized. Organizations should establish procedures for managing all contracts and procurements to ensure that they include all the regulatory and legal requirements. Periodic reviews should occur to ensure that the contracted organization is complying with the guidelines of the contract. System Specific Risk Analysis Inventory Threat assessment Evaluation Management Monitoring
- 28. III. Research, Analysis and Assessment 3.1 Apply research methods to determine industry trends and impact to the enterprise. 3.2 Analyze scenarios to secure the enterprise. 3.3 Given a scenario, select methods or tools appropriate to conduct an assessment and analyze results. identify the best practices and new technologies for dealing with new systems identify how client-side attacks, vulnerabilities, and threats affect network security define how zero-day and emergent threats can affect network security define how end-user cloud storage and business integration can affect network security identify the role of the CERT team and what members should be on it define how conventions, threats actors, and threat intelligence are used to create network security define the role RFPs, RFQs, FRIs, and agreements play in network security identify how benchmarks and baselines are used to create network security define how prototypes and testing are used to create network security define how cost benefit analysis is used when creating network security plans identify how metrics collection and analysis is used when creating network security plans identify how trend data and cyber defense are used when creating network security define the role existing security controls play when creating network security identify how reverse engineering can be used in order to create network security define how performance, latency, scalability, and capability affect network security define how usability, maintainability, availability, and recovery affect network security identify how lessons learned and after-action reports are used to reinforce network security define how judgment calls are used when network security issues arise define how network analysis tools are used when securing network environments identify how exploitation tools can be used both to test and exploit network environments define how passive reconnaissance and intelligence gathering tools can be used to test network environments
- 29. define how assessment, sandboxing, and debugging can be used to test the security of network environments identify how penetration testing can be used to ensure security in network environments identify the differences between black box, white box, and gray box testing techniques define how reconnaissance, fingerprinting, and social engineering can be used to test the security of network environments Understand basic security, mitigation and prevention techniques
- 30. IV. Integration of Computing, Communications and Business Disciplines 4.1 Given a scenario, facilitate collaboration across diverse business units to achieve security goals. 4.2 Given a scenario, select the appropriate control to secure communications and collaboration solutions. 4.3 Implement security activities across the technology life cycle. identify the role of sales staff and programmers in network security implementations identify the role of database and network administrators in network security implementations identify the role of management and finance in network security implementations identify the role of human resources and emergency response in network security implementations identify the role of facilities and physical security managers in network security implementations identify how different business units must collaborate and use security guidance identify how conferencing and messaging solutions are used to secure network environments identify how desktop sharing, remote assistance, and presence affect network security define how telephony must be secured define the need for security when working with collaboration sites identify how over-the-air technologies can be secured in a network environment identify how change management, operations, and maintenance are used to secure network environments identify how commissioning, reuse, and disposal affect network security identify the importance of the Security System Development Life Cycle when developing network security identify how to use the Security Requirements Traceability Matrix identify how testing and Agile, waterfall, and spiral methodologies are used when securing a networked environment identify how device tracking technologies are used when securing a network environment identify how object tracking and containment technologies are used when securing a network environment increasing Network Security Knowledge
- 31. V. Technical Integration of Enterprise Components 5.1 Given a scenario, integrate hosts, storage, networks and applications into a secure enterprise architecture. 5.2 Given a scenario, integrate advanced authentication and authorization technologies to support enterprise objectives. define how secure data flows can be used to meet changing business needs define how standards are used to secure a network environment define how interoperability issues affect network security define how cloud and virtualized environments affect network security define how the vulnerabilities associated with virtual machines will affect network security define how to secure on-demand cloud computing define how data aggregation and isolation is used to aid in securing a network environment identify how provisioning and de-provisioning of resources affects network security understand how to secure virtual environments define how mergers, acquisitions, and divestitures can affect network security define how network secure segmentation and delegation can affect network security define how logical and physical deployment diagrams are used to create secure network environments define how a secure infrastructure design is used when creating network security plans define how storage integration can be used to aid in securing a network environment define how CRM, ERP, and GRC are used to aid in creating a secure network environment define how ESB, SOA, and directory services are used to aid in creating a secure network environment define how DNS, CMDB, and CMS are used to aid in creating a secure network environment identify how advanced authentication can help in creating a secure network environment define how attestation and identity propagation can help in creating a secure network environment identify how federation can help in creating a secure network environment identify how the RADIUS trust model can be used to help create a secure network environment identify how the LDAP trust model can be used to help create a secure network environment
- 32. identify how the Active Directory trust model can be used to help create a secure network environment to integrate hosts, storage, networks and applications into a secure enterprise architecture, and integrate advanced authentication and authorization technologies to support enterprise objectives Enterprise application integration enablers CRM Customer relationship management (CRM) is a term that refers to practices, strategies and technologies that companies use to manage and analyze customer interactions and data throughout the customer lifecycle, with the goal of improving business relationships with customers, assisting in customer retention and driving sales growth. CRM systems are designed to compile information on customers across different channels -- or points of contact between the customer and the company -- which could include the company's website, telephone, live chat, direct mail, marketing materials and social media. http://searchcrm.techtarget.com/definition/CRM ERP Enterprise resource planning (ERP) is business process management software that allows an organization to use a system of integrated applications to manage the business and automate many back office functions related to technology, services and human resources. ERP software integrates all facets of an operation — including product planning, development, manufacturing, sales and marketing — in a single database, application and user interface. http://www.webopedia.com/TERM/E/ERP.html GRC Governance, Risk Management, and Compliance (GRC) are three facets that help assuring that an organization meets its objectives. Governance is the combination of processes established and executed by the directors (or the board of directors) that are reflected in the organization's structure and how it is managed and led toward achieving goals. Risk management is predicting and managing risks that could hinder the organization to achieve its objectives. Compliance refers to adhering with the company's policies, procedures, laws and regulations. https://en.wikipedia.org/wiki/Governance,_risk_management,_and_com pliance ESB What is Enterprise Service Bus (ESB). ESB is an open standards- based distributed synchronous or asynchronous messaging middleware that provides secure interoperability between enterprise applications via XML, Web services interfaces and standardized rules-based routing of documents. www.webopedia.com/TERM/E/ESB.html SOA Service-Oriented Architecture (SOA). A service-oriented architecture is essentially a collection of services. These services communicate with
- 33. each other. The communication can involve either simple data passing or it could involve two or more services coordinating some activity. Some means of connecting services to each other is needed. http://www.service-architecture.com/articles/web-services/service- oriented_architecture_soa_definition.html Directory Services A directory service is a customizable information store that functions as a single point from which users can locate resources and services distributed throughout the network. This customizable information store also gives administrators a single point for managing its objects and their attributes. Although this information store appears as a single point to the users of the network, it is actually most often stored in a distributed form. http://www.dummies.com/programming/networking/defining-terms-what- is-a-directory-service/ DNS Domain Name Servers (DNS) are the Internet's equivalent of a phone book. They maintain a directory of domain names and translate them to Internet Protocol (IP) addresses. This is necessary because, although domain names are easy for people to remember, computers or machines, access websites based on IP addresses. Information from all the domain name servers across the Internet are gathered together and housed at the Central Registry. Host companies and Internet Service Providers interact with the Central Registry on a regular schedule to get updated DNS information. http://www.networksolutions.com/support/what-is-a-domain-name- server-dns-and-how-does-it-work/ CMDB A configuration management database (CMDB) is a repository that acts as a data warehouse for information technology (IT) installations. It holds data relating to a collection of IT assets (commonly referred to as configuration items (CI)), as well as to descriptive relationships between such assets. https://en.wikipedia.org/wiki/Configuration_management_database CMS A content management system (CMS) is a computer application that supports the creation and modification of digital content. It is often used to support multiple users working in a collaborative environment. https://en.wikipedia.org/wiki/Content_management_system
- 34. DEFINITIONS













![parity recomputed, and the result is written to the spare drive. This is done from the initial logical block
of the array to the last block in the array. This operation is time consuming because all data needs to
be recomputed from the beginning of the array to the end of the array, and degrades performance,
because although there are parallel reads, there is one single write to the spare drive. Thus, this single
write becomes a bottleneck in the system.
In DDP, a disk pool is a set of drives that are logically grouped together in the storage
subsystem, where data is distributed across all drives in the pool. The drives in each disk pool
must be of the same drive type and drive media type, and they must be similar in size. Unlike RAID,
there is no specific spare drive, rather, all drives have spare space that is reserved. When a drive fails,
the remaining drives are read, the missing data is recomputed, and the result is written to multiple
drives in their spare space. This operation is done on the pieces of data that are missing. The result is
parallel reads and parallel writes, which significantly speeds up the rebuild time after a single drive
failure.
Both RAID and DDP are techniques for striping data and parity information across a set of disks to
provide fault tolerance, but how they operate to attain this goal is different.
https://www.ibm.com/support/knowledgecenter/en/STFS69_4.0.0/ts7760_ddp.html
Microsoft Group Policies
Group Policy, in part, controls what users can and cannot do on a computer system: for
example, to enforce a password complexity policy that prevents users from choosing an
overly simple password, to allow or prevent unidentified users from remote computers to
connect to a network share, to block access to the Windows Task Manager or to restrict
access to certain folders. A set of such configurations is called a Group Policy Object
(GPO).
As part of Microsoft's IntelliMirror technologies, Group Policy aims to reduce the cost of
supporting users. IntelliMirror technologies relate to the management of disconnected
machines or roaming users and include roaming user profiles, folder redirection, and
offline files.14
Group Policy Objects are processed in the following order (from top to bottom)
1. Local - Any settings in the computer's local policy. Prior to Windows Vista, there
was only one local group policy stored per computer. Windows Vista and later
Windows versions allow individual group policies per user accounts.[5]
2. Site - Any Group Policies associated with the Active Directory site in which the
computer resides. (An Active Directory site is a logical grouping of computers,
intended to facilitate management of those computers based on their physical
proximity.) If multiple policies are linked to a site, they are processed in the order
set by the administrator.
14
https://en.wikipedia.org/wiki/Group_Policy](https://image.slidesharecdn.com/sweigert-notes-comptiacaspexam-july-27-170725185056/85/EXAM-NOTES-for-DOD-Standard-8570-CompTia-Advanced-Security-Practitioner-CASP-13-320.jpg)