Expert mining compsac-2014
0 likes490 views
The document outlines a workshop procedure for assessing risk indicators in open source software adoption, focusing on the RISCOSS analytics platform and tactical workshops involving domain experts. It details the steps involved in preparing for these workshops, managing risks, and evaluating scenarios using statistical tools and expert judgments. Additionally, it highlights applications and lessons learned from past workshops conducted in various countries.
1 of 31
Download to read offline









![10
Tacticalworkshop
protocol
Workshop procedure
Pre-TasksPart II: Community dinamicsPart I : Community dataTacticalWorkshop OrganizerDomainExpert6.Make presentation of RISCOSS project summary. 7.Explain the RISCOSS analytics platform. 8.Explain the tactical workshop Part I and Part II9.Explain the risk driver selection WS Excel File Excel File: risk driver selection WSTabsTimelinessActivenessCommunity10.Study the use case scenario 11.Assess the use case scenario overall state 12.Determine the level of the risk indicator 13.Study the use case scenario 14.Assess the use case scenario overall state 15.Determine the level of the community risk indicatorPDF File:KPA RISCOSS Analytics [more risk drivers] [not more risk drivers] RISCOSS Analytics Team1.Determine drivers and risk indicators2.Construct Bayesian networks3.Define scenarios4.Identify and contact experts5.Workshops planning and preparation16.Send the scenarios judgementPopulate BN nodes](https://image.slidesharecdn.com/expertmining-compsac-2014-140825162147-phpapp02/85/Expert-mining-compsac-2014-10-320.jpg)













![25
Related Work
Related Work
Delphi method
(QUELCE)
QuantifyingUncertaintyinEarlyCostEstimation[2]
Reliableconsensusofopinionofagroupofexperts[1]
[1]N.DalkeyandO.Helmer,“AnexperimentalapplicationoftheDelphimethodtotheuseofexperts,”.
[2]R.W.Ferguson,D.Goldenson,J.M.McCurley,R.W.Stoddard,andD.Zubrow,“QuantifyingUncertaintyinEarlyLifecycleCostEstimation(QUELCE),”](https://image.slidesharecdn.com/expertmining-compsac-2014-140825162147-phpapp02/85/Expert-mining-compsac-2014-25-320.jpg)

![27
Domain
Expert
Conclusions and further work
Conclusions and further work
Pre-Tasks
Part II:
Community
dinamics
Part I :
Community data
Tactical
Workshop
Organizer
Domain
Expert
6.Make
presentation
of RISCOSS
project
summary.
7.Explain the
RISCOSS
analytics
platform.
8.Explain the
tactical
workshop
Part I and
Part II
9.Explain the
risk driver
selection WS
Excel File
Excel File: risk driver
selection WS
Tabs
Timeliness
Activeness
Community
10.Study the
use case
scenario
11.Assess the
use case
scenario
overall state
12.Determine
the level of
the risk
indicator
13.Study the
use case
scenario
14.Assess the
use case
scenario
overall state
15.Determine
the level of
the
community
risk indicator
PDF File:KPA
RISCOSS
Analytics
[more
risk drivers]
[not more
risk drivers]
RISCOSS
Analytics
Team
1.Determine
drivers and
risk indicators
2.Construct
Bayesian
networks
3.Define
scenarios
4.Identify and
contact
experts
5.Workshops
planning and
preparation
16.Send the
scenarios
judgement
Populate BN
nodes
Domain
Expert SNA
Project Site
Code Version
Repository
Bug Tracker Mailing List IRC
Step-by-step
protocol
Data used to
construct
Bayesian
networks
Future work
Combines opinion
of domain experts
with OSS raw data
Empirical
application
&
lessons](https://image.slidesharecdn.com/expertmining-compsac-2014-140825162147-phpapp02/85/Expert-mining-compsac-2014-27-320.jpg)




Ad
Recommended
Measuring Technical Lag in Software Deployments (CHAOSScon 2020)
Measuring Technical Lag in Software Deployments (CHAOSScon 2020)Tom Mens The document discusses the concept of technical lag in software, which measures the difference between deployed software packages and their ideal counterparts, highlighting its significance in various contexts such as software deployment and package dependency management. It describes different metrics for measuring technical lag, including time, version, bugs, and vulnerabilities, and emphasizes the need for these metrics to be part of broader assessment tools for software health. The document also outlines open challenges and proposes new CHAOSS project metrics to measure software dependencies and their health.
On the Relation between Outdated Docker Containers, Severity Vulnerabilities,...
On the Relation between Outdated Docker Containers, Severity Vulnerabilities,...Tom Mens The document discusses the implications of outdated Docker containers, particularly focusing on vulnerabilities and bugs in dependencies such as npm packages. It presents findings from two empirical case studies analyzing Debian images and npm packages, revealing that a significant number of containers contain outdated, vulnerable packages, which poses security risks. Recommendations include ensuring optimal update frequencies and continuous monitoring of package versions to enhance security and stability in container deployments.
Binary Analysis - Luxembourg
Binary Analysis - LuxembourgAbhik Roychoudhury This document discusses binary analysis for vulnerability detection. It describes research conducted at the National University of Singapore on binary analysis techniques like fuzz testing, comprehension, debugging, and patching. It outlines projects with DSO National Labs and the National Research Foundation of Singapore. The research aims to enhance capabilities in detecting vulnerabilities and securing software through automated binary analysis and techniques like fuzzing.
UCC-2016, 6-9 May December, Shanghai, China
UCC-2016, 6-9 May December, Shanghai, ChinaCharith Perera The document analyzes the impact of user constraints on resource discovery in the Cloud of Things, using multiple criteria decision analysis (MCDA) algorithms. It highlights the development of a middleware architecture that enables context-aware selection of smart objects to meet user requirements, addressing gaps in existing solutions. Conclusions indicate that while the relative importance of constraints can enhance solution quality, it is more effective with fewer constraints.
Cesi2014
Cesi2014GESSI UPC Research paper at Second Intl. Workshop on Conducting Empirical Studies in Industry. CESI 2014 - An ICSE 2014 Workshop (2nd June 2014)
http://www.essi.upc.edu/~franch/cesi2014/program.html
Jcis 2015-Towards Assessing Open Source Communities' Health using SOC Concepts
Jcis 2015-Towards Assessing Open Source Communities' Health using SOC ConceptsGESSI UPC The document discusses assessing the health of open source software (OSS) ecosystems using concepts from social computing (SOC). It proposes a monitoring approach using key health indicators and the QUESO quality model to evaluate various aspects including community vitality and activeness. The findings aim to provide guidance for stakeholders in choosing between different OSS ecosystems.
Electronica informatoca
Electronica informatocaAidessita Gali Este documento describe diferentes tipos de comunicación en línea como blogs, webquests, conversaciones en línea y mensajería instantánea. Explica las estructuras y características principales de blogs y webquests, y analiza varias modalidades de conversación en línea e idiomas modificados como 1337, KeYCaPS y SMS.
Ossap final
Ossap finalGESSI UPC The document presents ossap, a method designed to facilitate the adoption of open source software (OSS) by organizations according to their strategic goals. It outlines a situational method engineering process that helps create adaptable business process models for OSS adoption. The ossap method aims to support organizations in defining and refining their OSS-aware business processes, while also paving the way for future adaptations and strategies.
Agile and the nature of decision making
Agile and the nature of decision makingDennis Stevens The document discusses risk management for large agile projects. It begins by explaining why explicit risk management is needed for large projects operating in high uncertainty. It then outlines a three part approach: [1] Identify risk drivers by defining objectives and determining factors that could impact success or failure, [2] Conduct agile risk assessments by evaluating threats and opportunities against the risk drivers, and tracking this in a risk profile, [3] Integrate risk management by planning responses, using a risk board, and including risks in acceptance criteria. The document provides examples of how to identify common risk drivers in areas like business, technical, feedback, organizational, and dependencies.
Agile and the nature of decision making
Agile and the nature of decision makingdrewz lin The document discusses risk management for large agile projects. It defines risk management and describes how agile implicitly manages risk through feedback cycles, co-located teams, and continuous delivery. However, it notes limitations of agile and traditional risk management approaches for complex projects. The document proposes identifying risk drivers, conducting agile risk assessments against those drivers, and integrating risk management into the project workflow to better handle uncertainty and interdependencies at scale.
RISCOSS platform: evaluation results
RISCOSS platform: evaluation resultsSilvia Valentini The Riscoss project, initiated by Fondazione Bruno Kessler (FBK) in collaboration with PMI-NIC, focuses on risk management in open source software (OSS) adoption. It aims to develop methods for identifying, managing, and mitigating risks associated with OSS, enhancing decision-making processes for industrial stakeholders. The project emphasizes community involvement and is structured around a three-layer approach for comprehensive risk assessment and management.
Angelo Susi' s presentation at PMI Academic Workshop 2016
Angelo Susi' s presentation at PMI Academic Workshop 2016Silvia Valentini The RISCOSS project aimed to specify risk identification, management, and mitigation methods for open source software adoption. It developed a 3-layer framework using statistical, logic-based, and multi-criteria decision making techniques to assess risks at the software, community, and business levels. The framework was evaluated through a collaboration between the Fondazione Bruno Kessler and the Project Management Institute - Trento Chapter, where volunteers used the tool to evaluate predefined and real-world scenarios and provided feedback on its usefulness and usability.
RISCOSS platform: evaluation results
RISCOSS platform: evaluation resultsSilvia Valentini The RISCOSS project, initiated in November 2012 with a budget of €3.2 million, aims to improve risk management in the adoption of open-source software (OSS) by developing methodologies and tools to identify, manage, and mitigate risks associated with OSS integration. The project has engaged various academic and industry partners to enhance decision-making processes and support the effective use of OSS, with an emphasis on community involvement and feedback from volunteers on its implementation. Evaluation results indicate that the RISCOSS platform is perceived as useful for increasing productivity and decision-making efficiency, although challenges remain in terms of ease of use and the potential for full automation in risk assessment.
crisc_wk_3.pptx
crisc_wk_3.pptxdotco The document discusses various aspects of IT risk assessment including identifying risks, assessing risk levels, examples of risk events, threat modeling, developing risk scenarios, risk analysis methodologies, and third party risk management. Some key points include:
- IT risk assessment involves determining the probability and impact of identified risks. Common risk events include regulatory changes, loss of key personnel, and ransomware attacks.
- Threat modeling is used to identify internal and external threats and design adequate controls. Vulnerabilities represent weaknesses that could be exploited by threats.
- Risk scenarios help estimate the frequency and impact of risks and imagine what could go wrong. They are developed using top-down and bottom-up approaches.
- Risk
Information systems risk assessment frame workisraf 130215042410-phpapp01
Information systems risk assessment frame workisraf 130215042410-phpapp01S Periyakaruppan CISM,ISO31000,C-EH,ITILF The document proposes an Information Systems Risk Assessment Framework (ISRAF) to improve organizational risk management. The framework aims to integrate risk assessment into the system development life cycle and business processes. It recommends a modular, hierarchical approach to conduct risk assessments at different tiers or levels of the organization. The framework provides guidelines on risk concepts, factors, analysis methods, assessment scales, and communicating results to stakeholders. The goal is to help organizations make more risk-based decisions through a systematic, repeatable risk assessment process.
Riscoss models u-qasar meeting
Riscoss models u-qasar meetingXavier Franch This document discusses open source software (OSS) adoption risks and risk modeling. It provides examples of common OSS risks like component selection errors and integration failures. It also outlines measures and indicators of risks in OSS ecosystems, like bug fix times and forum activity. The document then describes how risks can be modeled as entities with relationships, and shows how measures can provide evidence for situations and events. Finally, it discusses using statistical analysis and social network analysis to study OSS projects and communities, and using Bayesian networks to represent links between measures and risks.
Hands on IT risk assessment
Hands on IT risk assessmentGeorge Delikouras This document outlines a risk assessment methodology for organizations. It discusses how risk assessments are often not implemented formally or do not provide practical advice. The presented method uses foundation documents, risk evaluation criteria, and a multi-round review process called the Delphic Technique to provide a standardized risk assessment. It recommends developing reusable templates, defining assessment scope and objectives, using the methodology to identify and evaluate risks, and creating formal treatment plans. Time is included as a variable to show changing risks over time. The goal is for assessments to identify practical risk reduction options.
Risk profiling
Risk profilingJaume Jornet Rivas The document discusses risk profiling and its importance in categorization rather than prioritization of risks within a backlog. It provides insights into various risk dimensions and classification methods, highlighting the need for effective demand management. Additionally, the facilitator and coach views emphasize the interplay between risk assessment and decision-making processes in project management.
Data Driven Risk Management
Data Driven Risk ManagementResolver Inc. The document provides insights into risk assessment techniques, highlighting the importance of understanding risk management and machine learning as tools for evaluating risks. It covers various risk classification metrics, including impact, likelihood, and control effectiveness, as well as the role of data in predicting risk outcomes. Additionally, it emphasizes the need for effective data analysis and modeling to improve risk assessment accuracy and preparedness within organizations.
International Journal of Engineering Research and Development
International Journal of Engineering Research and DevelopmentIJERD Editor The paper discusses the importance of risk assessment in decision-making, focusing on a model that incorporates the number of activities, their duration, and resource availability to calculate a Risk Assessment Score (RAS). It proposes an algorithm to quantify contributions from these factors, ultimately aiding project managers in selecting optimal plans to minimize risks. The study highlights the need for thorough analysis in managing uncertainties to improve success rates in project completion.
Introduction to FAIR - Factor Analysis of Information Risk
Introduction to FAIR - Factor Analysis of Information RiskOsama Salah FAIR (Factor Analysis of Information Risk) is a framework for measuring and analyzing information risk in a logical and quantitative way. It consists of (1) an ontology that defines the factors that contribute to risk and their relationships, (2) methods for measuring these factors, and (3) a computational model that calculates risk by simulating the relationships between measured factors. FAIR aims to provide an objective, evidence-based approach to risk analysis and avoid common pitfalls like inaccurate models, poor communication, and focus on worst-case scenarios. It measures factors like threat frequency, vulnerability, and loss magnitude on quantitative scales to determine overall risk.
Measuring DDoS Risk using FAIR (Factor Analysis of Information Risk
Measuring DDoS Risk using FAIR (Factor Analysis of Information RiskTony Martin-Vegue The document outlines a case study presented at the Fair Conference on measuring DDoS risk for a typical US bank, detailing the analysis process through the FAIR methodology. Key steps include identifying at-risk assets, evaluating loss event frequency and magnitude, and deriving and articulating the risk involved in DDoS attacks. The study highlights various threat agents, their capabilities, and offers insights on quantitative risk assessment resources.
Dynamic vs. Traditional Probabilistic Risk Assessment Methodologies - by Huai...
Dynamic vs. Traditional Probabilistic Risk Assessment Methodologies - by Huai...ASQ Reliability Division The document compares dynamic and traditional probabilistic risk assessment methodologies. Traditional methodologies like fault trees, event sequence diagrams, and FMECA require analysts to assess possible system failures. Dynamic methodologies like Monte Carlo simulation use executable models to simulate system behavior probabilistically over time and automatically generate event sequences. Dynamic methods can address limitations of traditional approaches that rely heavily on analyst judgment.
Risk Assessment
Risk AssessmentGlen Alleman The document outlines a comprehensive risk assessment framework for software development and acquisition projects, emphasizing continuous identification and management of risks. It defines various categories and types of risks associated with software projects, including cost, performance, and technical risks, and presents strategies for effective risk management. The importance of a shared vision, proactive planning, and systematic methodologies in risk management are highlighted to ensure successful project outcomes.
Assessment Of Risk Mitigation
Assessment Of Risk MitigationEneni Oduwole The document discusses risk assessment and mitigation strategies for a bank. It outlines the process of assessing risk, which includes identifying prevalent risks, assessing their impact and frequency, developing controls, and reassessing exposures. It also evaluates options for mitigating risk, such as periodic assessments, maintaining a risk register, and reviewing contingency plans. Key considerations for selecting mitigation actions include ensuring effectiveness, cost efficiency, alignment with business operations, and consistency with regulatory requirements.
Optimization of different objective function in risk assessment system
Optimization of different objective function in risk assessment systemAlexander Decker This document summarizes a research paper that proposes a new framework for risk assessment in systems development. It describes a 9-step risk assessment methodology that includes characterizing the system, identifying threats and vulnerabilities, analyzing controls, determining likelihood and impact, calculating risk levels, recommending controls, and documenting results. Each step of the methodology is explained in detail. The goal of the risk assessment process is to help organizations identify appropriate controls to eliminate risks and determine the likelihood of future adverse events.
NIST 800 30 revision Sep 2012
NIST 800 30 revision Sep 2012S Periyakaruppan CISM,ISO31000,C-EH,ITILF The document proposes a framework called the Information Systems Risk Assessment Framework (ISRAF) that takes a hierarchical, context-centric approach to comprehensive risk management. The framework addresses key aspects of risk assessment including preparation, conducting assessment, analyzing risks both qualitatively and quantitatively, communicating results, and maintaining an organization's risk posture over time. It provides guidance on the risk assessment process and applying the results across the risk management life cycle to support various organizational decisions.
Ratneshwar jha risk analysis and mitigation precedence modeling
Ratneshwar jha risk analysis and mitigation precedence modelingPMInstituteIndia The document proposes a new risk analysis and mitigation model. The current model prioritizes risks based only on risk exposure but the proposed model considers additional factors like risk interdependencies, influence factors, and mitigation exposure over time. The proposed model involves 4 phases: 1) analyzing risk influence factors, 2) generating a risk network through dependency analysis, 3) prioritizing mitigation based on exposure and dependencies, and 4) analyzing mitigation variance over time. The benefits of the proposed model are that it provides a clearer prioritization of risks, better predictability, a more robust mitigation plan, and is more futuristic than the current model.
iStarJSON: A Lightweight Data-Format for i* Models
iStarJSON: A Lightweight Data-Format for i* ModelsGESSI UPC Istarjson is a lightweight data format developed for i* models within the context of open source software ecosystems quality analysis. The document outlines the motivation, structure, and functionality of istarjson, including its REST web services for converting, validating, and generating graphs from i* models. Future work involves releasing istarjson as an open-source project and expanding its services.
Towards iStarML 2.0: Closing Gaps from Evolved Requirements
Towards iStarML 2.0: Closing Gaps from Evolved RequirementsGESSI UPC The document discusses proposed changes to iStarML 2.0 to address requirements that have evolved for i* modeling. These include supporting new iStar 2.0 element types like qualities, refinement, and neededby relationships. Additional changes are proposed to improve scalability through attributes for hiding elements, and to enable model analysis by adding metrics tags for elements. The proposed iStarML 2.0 changes aim to close gaps between the iStar modeling language and its XML representation.
More Related Content
Similar to Expert mining compsac-2014 (20)
Agile and the nature of decision making
Agile and the nature of decision makingDennis Stevens The document discusses risk management for large agile projects. It begins by explaining why explicit risk management is needed for large projects operating in high uncertainty. It then outlines a three part approach: [1] Identify risk drivers by defining objectives and determining factors that could impact success or failure, [2] Conduct agile risk assessments by evaluating threats and opportunities against the risk drivers, and tracking this in a risk profile, [3] Integrate risk management by planning responses, using a risk board, and including risks in acceptance criteria. The document provides examples of how to identify common risk drivers in areas like business, technical, feedback, organizational, and dependencies.
Agile and the nature of decision making
Agile and the nature of decision makingdrewz lin The document discusses risk management for large agile projects. It defines risk management and describes how agile implicitly manages risk through feedback cycles, co-located teams, and continuous delivery. However, it notes limitations of agile and traditional risk management approaches for complex projects. The document proposes identifying risk drivers, conducting agile risk assessments against those drivers, and integrating risk management into the project workflow to better handle uncertainty and interdependencies at scale.
RISCOSS platform: evaluation results
RISCOSS platform: evaluation resultsSilvia Valentini The Riscoss project, initiated by Fondazione Bruno Kessler (FBK) in collaboration with PMI-NIC, focuses on risk management in open source software (OSS) adoption. It aims to develop methods for identifying, managing, and mitigating risks associated with OSS, enhancing decision-making processes for industrial stakeholders. The project emphasizes community involvement and is structured around a three-layer approach for comprehensive risk assessment and management.
Angelo Susi' s presentation at PMI Academic Workshop 2016
Angelo Susi' s presentation at PMI Academic Workshop 2016Silvia Valentini The RISCOSS project aimed to specify risk identification, management, and mitigation methods for open source software adoption. It developed a 3-layer framework using statistical, logic-based, and multi-criteria decision making techniques to assess risks at the software, community, and business levels. The framework was evaluated through a collaboration between the Fondazione Bruno Kessler and the Project Management Institute - Trento Chapter, where volunteers used the tool to evaluate predefined and real-world scenarios and provided feedback on its usefulness and usability.
RISCOSS platform: evaluation results
RISCOSS platform: evaluation resultsSilvia Valentini The RISCOSS project, initiated in November 2012 with a budget of €3.2 million, aims to improve risk management in the adoption of open-source software (OSS) by developing methodologies and tools to identify, manage, and mitigate risks associated with OSS integration. The project has engaged various academic and industry partners to enhance decision-making processes and support the effective use of OSS, with an emphasis on community involvement and feedback from volunteers on its implementation. Evaluation results indicate that the RISCOSS platform is perceived as useful for increasing productivity and decision-making efficiency, although challenges remain in terms of ease of use and the potential for full automation in risk assessment.
crisc_wk_3.pptx
crisc_wk_3.pptxdotco The document discusses various aspects of IT risk assessment including identifying risks, assessing risk levels, examples of risk events, threat modeling, developing risk scenarios, risk analysis methodologies, and third party risk management. Some key points include:
- IT risk assessment involves determining the probability and impact of identified risks. Common risk events include regulatory changes, loss of key personnel, and ransomware attacks.
- Threat modeling is used to identify internal and external threats and design adequate controls. Vulnerabilities represent weaknesses that could be exploited by threats.
- Risk scenarios help estimate the frequency and impact of risks and imagine what could go wrong. They are developed using top-down and bottom-up approaches.
- Risk
Information systems risk assessment frame workisraf 130215042410-phpapp01
Information systems risk assessment frame workisraf 130215042410-phpapp01S Periyakaruppan CISM,ISO31000,C-EH,ITILF The document proposes an Information Systems Risk Assessment Framework (ISRAF) to improve organizational risk management. The framework aims to integrate risk assessment into the system development life cycle and business processes. It recommends a modular, hierarchical approach to conduct risk assessments at different tiers or levels of the organization. The framework provides guidelines on risk concepts, factors, analysis methods, assessment scales, and communicating results to stakeholders. The goal is to help organizations make more risk-based decisions through a systematic, repeatable risk assessment process.
Riscoss models u-qasar meeting
Riscoss models u-qasar meetingXavier Franch This document discusses open source software (OSS) adoption risks and risk modeling. It provides examples of common OSS risks like component selection errors and integration failures. It also outlines measures and indicators of risks in OSS ecosystems, like bug fix times and forum activity. The document then describes how risks can be modeled as entities with relationships, and shows how measures can provide evidence for situations and events. Finally, it discusses using statistical analysis and social network analysis to study OSS projects and communities, and using Bayesian networks to represent links between measures and risks.
Hands on IT risk assessment
Hands on IT risk assessmentGeorge Delikouras This document outlines a risk assessment methodology for organizations. It discusses how risk assessments are often not implemented formally or do not provide practical advice. The presented method uses foundation documents, risk evaluation criteria, and a multi-round review process called the Delphic Technique to provide a standardized risk assessment. It recommends developing reusable templates, defining assessment scope and objectives, using the methodology to identify and evaluate risks, and creating formal treatment plans. Time is included as a variable to show changing risks over time. The goal is for assessments to identify practical risk reduction options.
Risk profiling
Risk profilingJaume Jornet Rivas The document discusses risk profiling and its importance in categorization rather than prioritization of risks within a backlog. It provides insights into various risk dimensions and classification methods, highlighting the need for effective demand management. Additionally, the facilitator and coach views emphasize the interplay between risk assessment and decision-making processes in project management.
Data Driven Risk Management
Data Driven Risk ManagementResolver Inc. The document provides insights into risk assessment techniques, highlighting the importance of understanding risk management and machine learning as tools for evaluating risks. It covers various risk classification metrics, including impact, likelihood, and control effectiveness, as well as the role of data in predicting risk outcomes. Additionally, it emphasizes the need for effective data analysis and modeling to improve risk assessment accuracy and preparedness within organizations.
International Journal of Engineering Research and Development
International Journal of Engineering Research and DevelopmentIJERD Editor The paper discusses the importance of risk assessment in decision-making, focusing on a model that incorporates the number of activities, their duration, and resource availability to calculate a Risk Assessment Score (RAS). It proposes an algorithm to quantify contributions from these factors, ultimately aiding project managers in selecting optimal plans to minimize risks. The study highlights the need for thorough analysis in managing uncertainties to improve success rates in project completion.
Introduction to FAIR - Factor Analysis of Information Risk
Introduction to FAIR - Factor Analysis of Information RiskOsama Salah FAIR (Factor Analysis of Information Risk) is a framework for measuring and analyzing information risk in a logical and quantitative way. It consists of (1) an ontology that defines the factors that contribute to risk and their relationships, (2) methods for measuring these factors, and (3) a computational model that calculates risk by simulating the relationships between measured factors. FAIR aims to provide an objective, evidence-based approach to risk analysis and avoid common pitfalls like inaccurate models, poor communication, and focus on worst-case scenarios. It measures factors like threat frequency, vulnerability, and loss magnitude on quantitative scales to determine overall risk.
Measuring DDoS Risk using FAIR (Factor Analysis of Information Risk
Measuring DDoS Risk using FAIR (Factor Analysis of Information RiskTony Martin-Vegue The document outlines a case study presented at the Fair Conference on measuring DDoS risk for a typical US bank, detailing the analysis process through the FAIR methodology. Key steps include identifying at-risk assets, evaluating loss event frequency and magnitude, and deriving and articulating the risk involved in DDoS attacks. The study highlights various threat agents, their capabilities, and offers insights on quantitative risk assessment resources.
Dynamic vs. Traditional Probabilistic Risk Assessment Methodologies - by Huai...
Dynamic vs. Traditional Probabilistic Risk Assessment Methodologies - by Huai...ASQ Reliability Division The document compares dynamic and traditional probabilistic risk assessment methodologies. Traditional methodologies like fault trees, event sequence diagrams, and FMECA require analysts to assess possible system failures. Dynamic methodologies like Monte Carlo simulation use executable models to simulate system behavior probabilistically over time and automatically generate event sequences. Dynamic methods can address limitations of traditional approaches that rely heavily on analyst judgment.
Risk Assessment
Risk AssessmentGlen Alleman The document outlines a comprehensive risk assessment framework for software development and acquisition projects, emphasizing continuous identification and management of risks. It defines various categories and types of risks associated with software projects, including cost, performance, and technical risks, and presents strategies for effective risk management. The importance of a shared vision, proactive planning, and systematic methodologies in risk management are highlighted to ensure successful project outcomes.
Assessment Of Risk Mitigation
Assessment Of Risk MitigationEneni Oduwole The document discusses risk assessment and mitigation strategies for a bank. It outlines the process of assessing risk, which includes identifying prevalent risks, assessing their impact and frequency, developing controls, and reassessing exposures. It also evaluates options for mitigating risk, such as periodic assessments, maintaining a risk register, and reviewing contingency plans. Key considerations for selecting mitigation actions include ensuring effectiveness, cost efficiency, alignment with business operations, and consistency with regulatory requirements.
Optimization of different objective function in risk assessment system
Optimization of different objective function in risk assessment systemAlexander Decker This document summarizes a research paper that proposes a new framework for risk assessment in systems development. It describes a 9-step risk assessment methodology that includes characterizing the system, identifying threats and vulnerabilities, analyzing controls, determining likelihood and impact, calculating risk levels, recommending controls, and documenting results. Each step of the methodology is explained in detail. The goal of the risk assessment process is to help organizations identify appropriate controls to eliminate risks and determine the likelihood of future adverse events.
NIST 800 30 revision Sep 2012
NIST 800 30 revision Sep 2012S Periyakaruppan CISM,ISO31000,C-EH,ITILF The document proposes a framework called the Information Systems Risk Assessment Framework (ISRAF) that takes a hierarchical, context-centric approach to comprehensive risk management. The framework addresses key aspects of risk assessment including preparation, conducting assessment, analyzing risks both qualitatively and quantitatively, communicating results, and maintaining an organization's risk posture over time. It provides guidance on the risk assessment process and applying the results across the risk management life cycle to support various organizational decisions.
Ratneshwar jha risk analysis and mitigation precedence modeling
Ratneshwar jha risk analysis and mitigation precedence modelingPMInstituteIndia The document proposes a new risk analysis and mitigation model. The current model prioritizes risks based only on risk exposure but the proposed model considers additional factors like risk interdependencies, influence factors, and mitigation exposure over time. The proposed model involves 4 phases: 1) analyzing risk influence factors, 2) generating a risk network through dependency analysis, 3) prioritizing mitigation based on exposure and dependencies, and 4) analyzing mitigation variance over time. The benefits of the proposed model are that it provides a clearer prioritization of risks, better predictability, a more robust mitigation plan, and is more futuristic than the current model.
Information systems risk assessment frame workisraf 130215042410-phpapp01
Information systems risk assessment frame workisraf 130215042410-phpapp01S Periyakaruppan CISM,ISO31000,C-EH,ITILF
Dynamic vs. Traditional Probabilistic Risk Assessment Methodologies - by Huai...
Dynamic vs. Traditional Probabilistic Risk Assessment Methodologies - by Huai...ASQ Reliability Division
More from GESSI UPC (20)
iStarJSON: A Lightweight Data-Format for i* Models
iStarJSON: A Lightweight Data-Format for i* ModelsGESSI UPC Istarjson is a lightweight data format developed for i* models within the context of open source software ecosystems quality analysis. The document outlines the motivation, structure, and functionality of istarjson, including its REST web services for converting, validating, and generating graphs from i* models. Future work involves releasing istarjson as an open-source project and expanding its services.
Towards iStarML 2.0: Closing Gaps from Evolved Requirements
Towards iStarML 2.0: Closing Gaps from Evolved RequirementsGESSI UPC The document discusses proposed changes to iStarML 2.0 to address requirements that have evolved for i* modeling. These include supporting new iStar 2.0 element types like qualities, refinement, and neededby relationships. Additional changes are proposed to improve scalability through attributes for hiding elements, and to enable model analysis by adding metrics tags for elements. The proposed iStarML 2.0 changes aim to close gaps between the iStar modeling language and its XML representation.
Monitoring the service-based system lifecycle with SALMon
Monitoring the service-based system lifecycle with SALMonGESSI UPC The document discusses the monitoring of service-based systems during their lifecycle, focusing on the Salmon framework. It emphasizes the importance of quality assessment, service selection, and adaptation methods within service-oriented computing. Key features include various monitoring techniques and extensibility for new metrics and service types.
Aligning Business Goals and Risks in OSS Adoption
Aligning Business Goals and Risks in OSS AdoptionGESSI UPC The document presents a model-based approach to align business goals and risks in open source software (OSS) adoption. It introduces a 3-layer approach to gather data on OSS projects and communities, identify risk indicators, and perform business analysis. It proposes integrating goal models and risk models using a foundational ontology to relate their concepts. The document demonstrates aligning an example business goal model with a risk model and analyzing how identified risks could impact business goals. Future work is outlined to refine the alignment process and further validate the approach.
RISCOSS: Gestión del riesgo en proyectos open source (Open Expo Day2015)
RISCOSS: Gestión del riesgo en proyectos open source (Open Expo Day2015)GESSI UPC El documento presenta el proyecto RISCOSS, el cual desarrolla una metodología y plataforma de software para gestionar los riesgos asociados con la adopción de software de código abierto. La plataforma permite identificar, analizar y mitigar riesgos a través de la recolección y análisis de datos de proyectos y comunidades de código abierto. Se muestra una demostración de las funcionalidades básicas de la plataforma RISCOSS.
Open expo2015 riscoss
Open expo2015 riscossGESSI UPC El documento presenta el proyecto RISCOSS, enfocado en la gestión de riesgos y costos en la adopción de software de código abierto (OSS). Se discuten las motivaciones, los riesgos asociados y la importancia de una gestión efectiva para mitigar impactos negativos en los negocios. Además, se menciona la plataforma RISCOSS como una herramienta para gestionar estos riesgos y facilitar la integración de OSS de manera innovadora.
Oss2015
Oss2015GESSI UPC The document discusses the framework for modeling open source software (OSS) ecosystems, highlighting their significance as business drivers and the increasing complexity and scale of software systems. It emphasizes the need for understanding, evaluating, and monitoring the health and quality of OSS ecosystems through a structured modeling process. Key concepts include collaboration among actors, the evolution of software projects, and the establishment of metrics and evaluation techniques for assessing ecosystem dynamics.
Mobility4 all
Mobility4 allGESSI UPC El documento describe el proyecto Mobility4All, cuyos objetivos son facilitar la movilidad de los ciudadanos con impedimentos, apoyar a los municipios en la detección y supresión de barreras arquitectónicas, y atraer visitantes con impedimentos para su movilidad. El proyecto involucra a municipalidades, centros de investigación y actores tecnológicos en el desarrollo de una plataforma y contenidos para mejorar la accesibilidad urbana y los procesos de gestión municipal.
Er14
Er14GESSI UPC The document discusses the modeling and application of open-source software (OSS) adoption strategies to support organizations in integrating OSS into their business models. It outlines research questions related to OSS projects, activities, and their alignment with organizational goals. Additionally, it presents an ontology for OSS adoption strategies and proposes future work to explore the connections between business models and OSS strategies.
QuESo: a Quality Model for Open Source Software Ecosystems
QuESo: a Quality Model for Open Source Software EcosystemsGESSI UPC This document presents QuESo, a quality model for measuring the quality of open source software ecosystems. It consists of three dimensions: community quality, ecosystem network quality, and platform quality. The authors describe developing the model through a systematic literature review to identify relevant metrics, which were then organized into the quality characteristics and sub-characteristics. Examples of applying the QuESo model for risk analysis and assessing an open source community's health are provided. Future work could involve defining a complete quality assessment process based on the model.
MoDRE 2014 @ RE keynote -- NFR-Aware MDD Processes
MoDRE 2014 @ RE keynote -- NFR-Aware MDD ProcessesGESSI UPC The keynote presentation by Xavier Franch at MODRE 2014 discusses the integration of non-functional requirements (NFRs) in model-driven development (MDD) processes, highlighting the importance of NFRs in software architecture and design decisions. The talk reviews empirical studies and emphasizes the need for MDD processes to be aware of NFRs to improve system quality and performance. Several research directions are suggested, including better representation of NFRs and linking them to architectural decisions.
Quantifying the Impact of OSS Adoption Risks with the help of i* Models
Quantifying the Impact of OSS Adoption Risks with the help of i* ModelsGESSI UPC The document discusses a method for assessing the risks associated with open source software (OSS) adoption using I* models, presented at an I* workshop in June 2014. It emphasizes the importance of understanding the OSS ecosystem, identifying risk drivers, and modeling the interplay between different actors and goals to evaluate potential risks. Future work includes deepening the analysis of connections between indicators, risks, and strategies, as well as integrating model-based and statistical reasoning techniques.
Applying Business Strategy Models in Organizations
Applying Business Strategy Models in OrganizationsGESSI UPC The document outlines a workshop on applying business strategy models in organizations focusing on open source software (OSS). It discusses various strategies for OSS adoption, acquisition, and integration, emphasizing the importance of aligning business models with strategic requirements. The conclusion highlights future work on validating the instantiation operations used in OSS strategies.
Slides refsq'14 ds v1
Slides refsq'14 ds v1GESSI UPC The document proposes using software requirement patterns (SRPs) to improve requirements engineering (RE) by enabling reuse of textual requirements. It defines SRPs as templates that generate natural language requirements from parameters. A PAtterns Based RE framework (PABRE) is designed to facilitate SRP use, addressing research questions about SRP structure/semantics, integration into RE processes, and benefits. The approach involves defining SRPs and a catalog, designing and implementing the PABRE system, and validating the framework and assets. Future work includes improving SRP relationships, evolving PABRE assets, and conducting a validation case study.
A Context Ontology for Service Provisioning and Consumption
A Context Ontology for Service Provisioning and ConsumptionGESSI UPC This document presents the development of a context ontology for service provisioning and consumption. It outlines the ontology development process, including specification, knowledge acquisition from 30 papers, and conceptualization of the knowledge. It also describes a use case scenario and conclusions. The paper aims to provide a unified context ontology and consolidate context information from a service-centric perspective to improve service provisioning and consumption.
Practical Experiences in Designing and Conducting Empirical Studies in Indust...
Practical Experiences in Designing and Conducting Empirical Studies in Indust...GESSI UPC Research paper at Second Intl. Workshop on Conducting Empirical Studies in Industry. CESI 2014 - An ICSE 2014 Workshop (2nd June 2014)
http://www.essi.upc.edu/~franch/cesi2014/program.html
Assessing Open Source Communities' using Service Oritented Computing concepts
Assessing Open Source Communities' using Service Oritented Computing conceptsGESSI UPC The document discusses assessing the health of open source software communities using concepts from service-oriented computing. It proposes monitoring key health indicators of communities by treating monitoring tools as services that can obtain and apply metrics. This would allow analyzing community data to inform strategies for proactively adapting communities and selecting appropriate open source software. Monitoring could be done actively through embedded sensors or passively through data retrieved from tools.
DB searches vs. snowballing
DB searches vs. snowballingGESSI UPC The document compares two methods for conducting systematic literature reviews: database searches and backward snowballing. It aims to determine the extent to which the two methods find the same papers and draw the same conclusions. The results show the initial and final paper sets from each method are different in number and composition, though some papers overlap. While patterns identified allow for similar conclusions, analyzing only unique papers per method reveals slightly different identified patterns. The conclusion is that the two methods are not highly dependent on each other but combining them generates a more comprehensive analysis, though requires more work. More comparison studies are needed to fairly evaluate the methods.
AK+MDD+NFRs
AK+MDD+NFRsGESSI UPC This document discusses an approach called AK+MDD+NFRs that combines architectural knowledge (AK), model-driven development (MDD), and non-functional requirements (NFRs). It presents an ontology called Arteon with four modules for requirements, reasoning and decision making, architectural elements, and MDD concepts. Architectural decisions are made through either constraint satisfaction or quality-oriented approaches. Ongoing work includes improving the ontology design, populating it with knowledge, validating it with case studies, and providing tool support.
Arteon: Architectural and Technology Ontology
Arteon: Architectural and Technology OntologyGESSI UPC The document provides an overview of the Arteon method and model. It discusses the context, outlines the method which involves requirements analysis, architectural decision making, and increasing knowledge. It then describes the Arteon model which represents requirements, architectural elements, and reasoning in interconnected ontologies. Finally, it discusses ongoing work to improve the ontology design, populate it with knowledge, validate it with case studies, and provide tool support.
Ad
Recently uploaded (20)
Proposal for folders structure division in projects.pdf
Proposal for folders structure division in projects.pdfMohamed Ahmed Proposal for folders structure division in projects
Rapid Prototyping for XR: Lecture 1 Introduction to Prototyping
Rapid Prototyping for XR: Lecture 1 Introduction to PrototypingMark Billinghurst Lecture 1 of a course on Rapid Prototyping for XR taught by Mark Billinghurst at Oulu University on June 9th, 2025. This lecture presents an Introduction to Prototyping.
Complete University of Calculus :: 2nd edition
Complete University of Calculus :: 2nd editionShabista Imam Master the language of change with the Complete Guidance Book of Calculus—your comprehensive resource for understanding the core concepts and applications of differential and integral calculus. Designed for high school, college, and self-study learners, this book takes a clear, intuitive approach to a subject often considered challenging.
Structured Programming with C++ :: Kjell Backman
Structured Programming with C++ :: Kjell BackmanShabista Imam Step into the world of high-performance programming with the Complete Guidance Book of C++ Programming—a definitive resource for mastering one of the most powerful and versatile languages in computer science.
Whether you're a beginner looking to learn the fundamentals or an intermediate developer aiming to sharpen your skills, this book walks you through C++ from the ground up. You'll start with basics like variables, control structures, and functions, then progress to object-oriented programming (OOP), memory management, file handling, templates, and the Standard Template Library (STL).
Abraham Silberschatz-Operating System Concepts (9th,2012.12).pdf
Abraham Silberschatz-Operating System Concepts (9th,2012.12).pdfShabista Imam Complete book of operating system edition 9
Rapid Prototyping for XR: Lecture 5 - Cross Platform Development
Rapid Prototyping for XR: Lecture 5 - Cross Platform DevelopmentMark Billinghurst This is lecture 5 in the course about Rapid Prototyping for XR, taught by Mark Billinghurst. This lecture is about Cross Platform Development.
Rapid Prototyping for XR: Lecture 4 - High Level Prototyping.
Rapid Prototyping for XR: Lecture 4 - High Level Prototyping.Mark Billinghurst This is lecture 4 in the course on Rapid Prototyping for XR, taught by Mark Billinghurst on June 11th, 2025. This lecture is about High Level Prototyping.
Complete guidance book of Asp.Net Web API
Complete guidance book of Asp.Net Web APIShabista Imam Unlock the full potential of modern web development with the Complete Guidance Book of ASP.NET Web API—your all-in-one resource for mastering RESTful services using Microsoft’s powerful ASP.NET Core framework. This book takes you on a step-by-step journey from beginner to expert, covering everything from routing and controllers to security, performance optimization, and real-world architecture.
How to Un-Obsolete Your Legacy Keypad Design
How to Un-Obsolete Your Legacy Keypad DesignEpec Engineered Technologies For any number of circumstances, obsolescence risk is ever present in the electronics industry. This is especially true for human-to-machine interface hardware, such as keypads, touchscreens, front panels, bezels, etc. This industry is known for its high mix and low-volume builds, critical design requirements, and high costs to requalify hardware. Because of these reasons, many programs will face end-of-life challenges both at the component level as well as at the supplier level.
Redesigns and qualifications can take months or even years, so proactively managing this risk is the best way to deter this. If an LED is obsolete or a switch vendor has gone out of business, there are options to proceed.
In this webinar, we cover options to redesign and reverse engineer legacy keypad and touchscreen designs.
For more information on our HMI solutions, visit https://www.epectec.com/user-interfaces.
Machine Learning - Classification Algorithms
Machine Learning - Classification Algorithmsresming1 This covers traditional machine learning algorithms for classification. It includes Support vector machines, decision trees, Naive Bayes classifier , neural networks, etc.
It also discusses about model evaluation and selection. It discusses ID3 and C4.5 algorithms. It also describes k-nearest neighbor classifer.
(Continuous Integration and Continuous Deployment/Delivery) is a fundamental ...
(Continuous Integration and Continuous Deployment/Delivery) is a fundamental ...ketan09101 (Continuous Integration and Continuous Deployment/Delivery) is a fundamental practice in DevOps that streamlines software development and deployment.
Generative AI & Scientific Research : Catalyst for Innovation, Ethics & Impact
Generative AI & Scientific Research : Catalyst for Innovation, Ethics & ImpactAlqualsaDIResearchGr Invited keynote at the Artificial Intelligence Symposium on AI-powered Research Innovation, taking place at ENSEM (L'École Nationale Supérieure d'Électricité et de Mécanique), Casablanca on June 21, 2025. I’ll be giving a keynote titled: "Generative AI & Scientific Research: Catalyst for Innovation, Ethics & Impact". Looking forward to engaging with researchers and doctoral students on how Generative AI is reshaping the future of science, from discovery to governance — with both opportunities and responsibilities in focus.
#AI hashtag#GenerativeAI #ScientificResearch #Innovation #Ethics #Keynote #AIinScience #GAI #ResearchInnovation #Casablanca
1. Thinking, Creative Thinking, Innovation
2. Societies Evolution from 1.0 to 5.0
3. AI - 3P Approach, Use Cases & Innovation
4. GAI & Creativity
5. TrustWorthy AI
6. Guidelines on The Responsible use of GAI In Research
International Journal of Advanced Information Technology (IJAIT)
International Journal of Advanced Information Technology (IJAIT)ijait International journal of advanced Information technology (IJAIT) is a bi monthly open access peer-
reviewed journal, will act as a major forum for the presentation of innovative ideas, approaches,
developments, and research projects in the area advanced information technology applications and
services. It will also serve to facilitate the exchange of information between researchers and industry
professionals to discuss the latest issues and advancement in the area of advanced IT. Core areas of
advanced IT and multi-disciplinary and its applications will be covered during the conferences.
Call For Papers - 17th International Conference on Wireless & Mobile Networks...
Call For Papers - 17th International Conference on Wireless & Mobile Networks...hosseinihamid192023 17th International Conference on Wireless & Mobile Networks (WiMoNe 2025) will provide
an excellent international forum for sharing knowledge and results in theory, methodology and
applications of Wireless & Mobile computing Environment. Current information age is witnessing
a dramatic use of digital and electronic devices in the workplace and beyond. Wireless, Mobile
Networks & its applications had received a significant and sustained research interest in terms of
designing and deploying large scale and high performance computational applications in real life.
The aim of the conference is to provide a platform to the researchers and practitioners from both
academia as well as industry to meet and share cutting-edge development in the field.
Ad
Expert mining compsac-2014
- 1. Expert Mining for Evaluating Risk Indicators ScenariosOscar Franco-Bedoya, Dolors Costal, Soraya Hidalgo, Ron Ben-JacobMonday 21st July 2014
- 2. 2 Background Workshop procedure Generalization of the approach Applications and lessons learned Related work Conclusions and further work Outline
- 3. 3 Background
- 4. 4 Background
- 5. 5 Background Managing risk in open source adoption
- 6. 6 Identification Mitigation methods Management Advanced tools Provides Platform Methods OSS adoption projects To support a In Uses Ecosystem modeling Statistical tools Risk Management i.e. i.e. i.e. Bayesian Networks Social network analysis Expert scenarios assessment e.g. e.g. e.g. Background Risks Systematic protocol uses
- 7. 7 Background Project Site Code Version Repository Bug Tracker Mailing List IRC Ecosystem hubs Project indexes Social Media Twitter Facebook I Raw Data SNA Measures Risk Indicators: • Project • Community • Contextual II Indicators Scenario-based Assessment Domain Expert Business Analysis • Business goals III Business Goals 3-Layered RISCOSS approach Number of downloads Number of event references Centrality Number of open bugs
- 8. 8 Outline Background Workshop procedure Generalization of the approach Applications and lessons learned Related work Conclusions and further work Outline
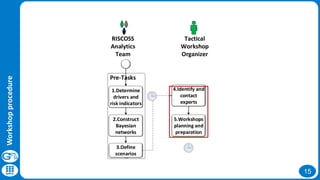
- 9. 9 The RISCOSS tactical workshop is designed to permit experts to assess risk indicators Workshop procedure
- 10. 10 Tacticalworkshop protocol Workshop procedure Pre-TasksPart II: Community dinamicsPart I : Community dataTacticalWorkshop OrganizerDomainExpert6.Make presentation of RISCOSS project summary. 7.Explain the RISCOSS analytics platform. 8.Explain the tactical workshop Part I and Part II9.Explain the risk driver selection WS Excel File Excel File: risk driver selection WSTabsTimelinessActivenessCommunity10.Study the use case scenario 11.Assess the use case scenario overall state 12.Determine the level of the risk indicator 13.Study the use case scenario 14.Assess the use case scenario overall state 15.Determine the level of the community risk indicatorPDF File:KPA RISCOSS Analytics [more risk drivers] [not more risk drivers] RISCOSS Analytics Team1.Determine drivers and risk indicators2.Construct Bayesian networks3.Define scenarios4.Identify and contact experts5.Workshops planning and preparation16.Send the scenarios judgementPopulate BN nodes
- 11. 11 Pre-Tasks Tactical Workshop Organizer RISCOSS Analytics Team 1.Determine drivers and risk indicators 2.Construct Bayesian networks 3.Define scenarios 4.Identify and contact experts 5.Workshops planning and preparation Correspond to tasks that must be done before conducting the tactical workshop Workshop procedure
- 12. 12 Pre-Tasks Tactical Workshop Organizer RISCOSS Analytics Team 1.Determine drivers and risk indicators 2.Construct Bayesian networks 3.Define scenarios 4.Identify and contact experts 5.Workshops planning and preparation Workshop procedure Risk Driver Forum posts per day Forum messages per thread Mail per day Overall community size Number of developers involved Number of testers (individuals providing feedback) Number of companies using the software Companies supporting the project (adding to code) Risk Indicator Activeness
- 13. 13 Pre-Tasks Tactical Workshop Organizer RISCOSS Analytics Team 1.Determine drivers and risk indicators 2.Construct Bayesian networks 3.Define scenarios 4.Identify and contact experts 5.Workshops planning and preparation Workshop procedure
- 14. 14 Pre-Tasks Tactical Workshop Organizer RISCOSS Analytics Team 1.Determine drivers and risk indicators 2.Construct Bayesian networks 3.Define scenarios 4.Identify and contact experts 5.Workshops planning and preparation Workshop procedure
- 15. 15 Pre-Tasks Tactical Workshop Organizer RISCOSS Analytics Team 1.Determine drivers and risk indicators 2.Construct Bayesian networks 3.Define scenarios 4.Identify and contact experts 5.Workshops planning and preparation Workshop procedure
- 16. 16 The tactical workshops begin with an exposition about the main topics that will be covered Workshop procedure 6.Make presentation of RISCOSS project summary. 7.Explain the RISCOSS analytics platform. 8.Explain the tactical workshop Part I and Part II PDF File:KPA RISCOSS Analytics Tactical Workshop Organizer
- 17. 17 Workshop procedure 9.Explain the risk driver selection WS Excel File Excel File: risk driver selection WS Tabs Timeliness Activeness Community Tactical Workshop Organizer
- 18. 18 Workshop procedure Part I : Community data Domain Expert 10.Study the use case scenario 11.Assess the use case scenario overall state 12.Determine the level of the risk indicator
- 19. 19 Workshop procedure Part II: Community dinamics 13.Study the use case scenario 14.Assess the use case scenario overall state 15.Determine the level of the community risk indicator 16.Send the scenarios judgement Domain Expert
- 20. 20 Outline Outline Background Workshop procedure Generalization of the approach Applications and lessons learned Related work Conclusions and further work
- 21. 21 Generalization of the approach
- 22. 22 Outline Outline Background Workshop procedure Generalization of the approach Applications and lessons learned Related work Conclusions and further work
- 23. 23 Applications and lessons learned Applications and lessons learned We have conducted 10 technical workshops In private and official organizations and academic institutions. The experts were from different countries. France, Israel, Italy, Spain, and Netherlands There are some inconsistencies in the scenarios The scenarios were designed using random number generators While the domain experts are conducting the tactical workshops, The degree of "calibration" of their judgement improves
- 24. 24 Outline Outline Background Workshop procedure Generalization of the approach Applications and lessons learned Related work Conclusions and further work
- 25. 25 Related Work Related Work Delphi method (QUELCE) QuantifyingUncertaintyinEarlyCostEstimation[2] Reliableconsensusofopinionofagroupofexperts[1] [1]N.DalkeyandO.Helmer,“AnexperimentalapplicationoftheDelphimethodtotheuseofexperts,”. [2]R.W.Ferguson,D.Goldenson,J.M.McCurley,R.W.Stoddard,andD.Zubrow,“QuantifyingUncertaintyinEarlyLifecycleCostEstimation(QUELCE),”
- 26. 26 Outline Outline Background Workshop procedure Generalization of the approach Applications and lessons learned Related work Conclusions and further work
- 27. 27 Domain Expert Conclusions and further work Conclusions and further work Pre-Tasks Part II: Community dinamics Part I : Community data Tactical Workshop Organizer Domain Expert 6.Make presentation of RISCOSS project summary. 7.Explain the RISCOSS analytics platform. 8.Explain the tactical workshop Part I and Part II 9.Explain the risk driver selection WS Excel File Excel File: risk driver selection WS Tabs Timeliness Activeness Community 10.Study the use case scenario 11.Assess the use case scenario overall state 12.Determine the level of the risk indicator 13.Study the use case scenario 14.Assess the use case scenario overall state 15.Determine the level of the community risk indicator PDF File:KPA RISCOSS Analytics [more risk drivers] [not more risk drivers] RISCOSS Analytics Team 1.Determine drivers and risk indicators 2.Construct Bayesian networks 3.Define scenarios 4.Identify and contact experts 5.Workshops planning and preparation 16.Send the scenarios judgement Populate BN nodes Domain Expert SNA Project Site Code Version Repository Bug Tracker Mailing List IRC Step-by-step protocol Data used to construct Bayesian networks Future work Combines opinion of domain experts with OSS raw data Empirical application & lessons
- 28. 28 Outline Outline Background Workshop procedure Generalization of the approach Applications and lessons learned Related work Conclusions and further work
- 29. 29 SEeD4FI
- 30. Thanks for your attention Comments and Questions
- 31. 31 SEeD4FI
