Ad
Exploits Attack on Windows Vulnerabilities
- 1. 1 | P a g e A Project Report On “ Exploiting Vulnerabilities Of Operating System Using Metasploits” Submitted By Mr.Amit Vikas Kumbhar To Mr.Sandeep Kumar Appin Technology Lab Jayanagar, Banglore IT Security and Ethical Hacking
- 2. 2 | P a g e Introduction. Exploits. Classification Metasploit. Histry of Metasploit Use Of Metasploit Metasploit Framework Exploit. Definition Types Of Exploits Payload. Definition Types Of Payload Functions Of Payload Graphical Overview of Metasploit Steps for exploiting Vulnerabilities Pre–Exploting Phase Lab setup Example 1) Exploit : Payload : Example 2) Exploit : Payload : Contents Classification. Histry of Metasploit. Use Of Metasploit. Metasploit Framework. Definition. Types Of Exploits. Definition. Types Of Payload. Functions Of Payload. Graphical Overview of Metasploit. Steps for exploiting Vulnerabilities Exploting Phase. Exploit :- windows/dcerpc/ms03_026_dcom Payload :- windows/add_user Exploit :- windows/dcerpc/ms03_026_dcom Payload :- windows/generic_shell_bind_tcp windows/dcerpc/ms03_026_dcom windows/dcerpc/ms03_026_dcom windows/generic_shell_bind_tcp
- 3. 3 | P a g e Example 3) Exploit :- windows/dcerpc/ms03_026_dcom Payload :- windows/meterpreter/bind_tcp
- 4. 4 | P a g e Introduction :- How tough is it to really compromise a system? Most security professionals are aware attacking and penetrating network devices is getting easier and attack sophistication is getting more complex. In large part this phenomenon is due to the old adage of "standing on the shoulders of giants." Many system researchers have uncovered the security weakness is common system design years ago, and as security professionals they shared the information. This allows someone with little understanding of system architecture to be able to perform more complex attacks than ever though possible. For a security professional it is possible to compromise a system without spending months learning a programming language and years learning system architecture. We can actually use technology to assist in performing penetration system penetration. Products like Core Security's Core Impact and Immunity's Canvas products have been providing this type of functionality for a few years now. These manufacturers do not just provide the technology, but they also provide training and support of their products to allow a qualified professional to perform a more methodological penetration test. It makes the task of compromising a system easier for a security administrator. The previously mentioned utilities are both fee based products, but more recently an open source product has become a common sight in penetration testing kits. This utility is called Metasploit™. Both Windows and Linux users can take advantage of the Metasploit™ product to perform a penetration test or system compromise. The utility itself is written in many programming languages including perl, C, and assembler. This environment provides many ready to use exploits and also allows for the security tester to customize them or to create their own exploit. The basic process for using the Metasploit™ console is not the most intuitive, but I think this was done to discourage the least skilled script kiddies from attempting to penetrate the system using this specific utility.
- 5. 5 | P a g e Exploit s: An exploit (from the same word in the French language, meaning "achievement", or "accomplishment") is a piece of software, a chunk of data, or sequence of commands that take advantage of a bug, glitch or vulnerability in order to cause unintended or unanticipated behavior to occur on computer software, hardware, or something electronic (usually computerised). This frequently includes such things as gaining control of a computer system or allowing privilege escalation or a denial of service attack. Vulnerability :- Vulnerability is a weakness which allows attacker to break into or compremise system security. Classification :- There are several methods of classifying exploits. The most common is by how the exploit contacts the vulnerable software. A 'remote exploit' works over a network and exploits the security vulnerability without any prior access to the vulnerable system. A 'local exploit' requires prior access to the vulnerable system and usually increases the privileges of the person running the exploit past those granted by the system administrator. Exploits against client application lso exist, usually consisting of modified servers that send an exploit if accessed with client application. Exploits against client applications may also require some interaction with the user and thus may be used in combination with social engineering method. This is the hacker way of getting into computers and websites for stealing data. Another classification is by the action against vulnerable system: unauthorised data access,arbitrary code execution ,denial of service. Many exploits are designed to provide superuser -level access to a computer system. However, it is also possible to use several exploits, first to gain low-level access, then to escalate privileges repeatedly until one reaches root. Normally a single exploit can only take advantage of a specific software vulnerability. Often, when an exploit is published, the vulnerability is fixed through a patch and the exploit becomes obsolete for newer versions of the
- 6. 6 | P a g e software. This is the reason why some blackhat hackers do not publish their exploits but keep them private to themselves or other crackers. Such exploits are referred to as zero day exploits' and to obtain access to such exploits is the primary desire of unskilled attackers, often nicknamed script kiddies. Types :- Exploits are commonly categorized and named by these criteria: The type of vulnerability they exploit (See the article on vulnerabilities for a list) Whether they need to be run on the same machine as the program that has the vulnerability (local) or can be run on one machine to attack a program running on another machine (remote). The result of running the exploit (Eop, Dos, Spoofing, etc...) Pivoting :- Pivoting refers to method used by Penetration Testers that uses compromised system to attack other systems on the same network to avoid restrictions such as firewall configurations, which may prohibit direct access to all machines. For example, an attacker compromises a web server on a corporate network, the attacker can then use the compromised web server to attack other systems on the network. These types of attacks are often called multi-layered attacks. Pivoting is also known as island hopping. Pivoting can further be distinguished into proxy pivoting and VPN pivoting: Proxy pivoting generally describes the practice channeling traffic through a compromised target using a proxy payload on the machine and launching attacks from this computer. This type of pivoting is restricted to certain TCP and UDP ports that are supported by the proxy. VPN pivoting enables the attacker to create an encrypted layer 2 tunnel into the compromised machine to route any network traffic through that target machine, for example to run a vulnerability scan on the internal network through the compromised machine, effectively giving the attacker full network access as if she were behind the firewall. Typically, the proxy or VPN applications enabling pivoting are executed on the target computer as the Payload (software) of an exploit.
- 7. 7 | P a g e “The Metasploit Framework is a development platform for creating security tools and exploits. The framework is used by network security professionals to perform penetration tests, system administrators to verify patch installations, product vendors to perform regression testing,and security researchers world-wide.” History of Metasploit :- The Metasploit project was originally started as a network security game by four core developers. It then developed gradually to a Perl-based framework for running, configuring, and developing exploits for well-known vulnerabilities.The 2.1 stable version of the product was released in June 2004. Since then, the development of the product and the addition of new exploits and payloads have rapidly increased. The Metasploit Project is an open-source computer security project which provides information about security vulnerabilities and aids in penetration testing and IDS signature development. Its most well-known sub-project is the Metasploit Framework, a tool for developing and executing exploit code against a remote target machine. Other important sub-projects include the Opcode Database, shellcode archive, and security research. The Metasploit Project is also well-known for anti-forensic and evasion tools, some of which are built into the Metasploit Framework. Metasploit was created by HD Moore in 2003 as a portable network game using the Perl scripting language. Later, the Metasploit Framework was then completely rewritten in the Ruby programming language. It is most notable for releasing some of the most technically sophisticated exploits to public security vulnerabilities. In addition, it is a powerful tool for third-party security researchers to investigate potential vulnerabilities. On October 21, 2009 the Metasploit Project announced that it had been acquired by Rapid7, a security company that provides unified vulnerability management solutions.
- 8. 8 | P a g e Like comparable commercial products such as Immunity's Canvas or Core Security Technologies'Core Impact, Metasploit can be used to test the vulnerability of computer systems in order to protect them, and it can be used to break into remote systems. Like many information security tools, Metasploit can be used for both legitimate and unauthorized activities. Since the acquisition of the Metasploit Framework, Rapid7 has added an commercial edition called Metasploit Express, while keeping the Metasploit Framework updated and free. Metasploit's emerging position as the de facto vulnerability development framework has led in recent times to the release of software vulnerability advisories often accompanied by a third party Metasploit exploit module that highlights the exploitability, risk, and remediation of that particular bug. Metasploit 3.0 (Ruby language) is also beginning to include fuzzing tools, to discover software vulnerabilities in the first instance, rather than merely writing exploits for currently public bugs. This new avenue has been seen with the integration of the lorcon wireless (802.11) toolset into Metasploit 3.0 in November, 2006. Metasploit use :- Metasploit came about primarily to provide a framework for penetration testers to develop exploits.The typical life cycle of a vulnerability and its exploitation is as follows: 1. Discovery :- A security researcher or the vendor discovers a critical security vulnerability in the software. 2. Disclosure :-The security researcher either adheres to a responsible disclosure policy and informs the vendor, or discloses it on a public mailing list. Either way, the vendor needs to come up with a patch for the vulnerability. 3. Analysis :-The researcher or others across the world begin analyzing the vulnerability to determine its exploitability. Can it be exploited? Remotely? Would the exploitation result in remote code execution, or would it simply crash the remote service? What is the length of the exploit code that can be injected? This phase also involves debugging the vulnerable application as malicious input is injected to the vulnerable piece of code.
- 9. 9 | P a g e 4. Exploit Development :- Once the answers to the key questions are determined, the process of developing the exploit begins.This has usually been considered a bit of a black art, requiring an in-depth understanding of the processor’s registers, assembly code, offsets, and payloads. www.syngress.com 5. Testing :- This is the phase where the coder now checks the exploit code against various platforms, service pack, or patches, and possibly even for different processors (e.g., Intel, Sparc, and so on). 6. Release:- Once the exploit is tested, and the specific parameters required for its successful execution have been determined, the coder releases the exploit, either privately or on a public forum. Often, the exploit is tweaked so that it does not work right out of the box.This is usually done to dissuade script kiddies from simply downloading the exploit and running it against a vulnerable system.
- 10. 10 | P a g e Metasploit Framework This modularity of allowing to combine any exploit with any advantage of the Framework: it facilitates the tasks of attackers, exploit writers, and payload writers. Versions of the Metasploit Framework since v3.0 are written in the Programming Language. The previous version 2.7, was implem runs on all versions of Unix (including Linux and Mac OS X), and also on Windows. It includes two command line interfaces native GUI. The web interface is intended to be run from the attacker's computer. The Metasploit Framework can be extended to use external add languages. To choose an exploit and payload, some information about the target system is needed such as operating system version and installed network services. This information can be gleaned with as nmap. Nessus can, in addition, detect the target system's Metasploit Framework : This modularity of allowing to combine any exploit with any payload is the major advantage of the Framework: it facilitates the tasks of attackers, exploit writers, Versions of the Metasploit Framework since v3.0 are written in the Ruby . The previous version 2.7, was implemented in runs on all versions of Unix (including Linux and Mac OS X), and also on command line interfaces , a web-based interface and a native GUI. The web interface is intended to be run from the attacker's computer. Metasploit Framework can be extended to use external add-ons in multiple To choose an exploit and payload, some information about the target system is needed such as operating system version and installed network services. This information can be gleaned with Port scanning and OS fingerprinting in addition, detect the target system's vulnerabilities payload is the major advantage of the Framework: it facilitates the tasks of attackers, exploit writers, Ruby ented in Perl. It runs on all versions of Unix (including Linux and Mac OS X), and also on based interface and a native GUI. The web interface is intended to be run from the attacker's computer. ons in multiple To choose an exploit and payload, some information about the target system is needed such as operating system version and installed network services. This OS fingerprinting tools such vulnerabilities.
- 11. 11 | P a g e In April 2010, Rapid7 released Metaploit Express, which is a commercial version of Metasploit. Based on the Metasploit Framework, it offers a graphical user interface, integrates nmap for discovery, and adds smart bruteforcing as well as automated evidence collection. Rapid7 has a full-featured 7-day trial for Metasploit Express. Exploits :- It is a code which allows an attacker to take advantage of vulnerable System. Exploit Types :- Pretty much any protocol UDP, TCP, SMB, HTTP, FTP, SMTP, TFTP, SSH, etc Active, Passive, Brute-Force Remote, Local, User-Interaction (technically remote category) Remote: windows/dcerpc/ms03_026_dcom Local: no real local examples, but doable User-Interaction--All your browser, “have to click on something,” type exploits windows/browser/ms06_013_createtextrange Payloads :- Payload is Arbitrary code that is to be executed upon successful exploitation.It is a acutal code which run on the system after exploitation. Types Of Payloads :- 1) Single [shell_reverse_tcp = inline (single)] :- A self-contained payload that performs a specific task Size varies depending on the task Example: Reverse or bind command shell
- 12. 12 | P a g e 2) Stager [shell/reverse_tcp = stager] :- A stub payload that loads / bootstraps a stage Size generally much smaller than single payloads Passes connection information onto the stage 3) Stage :- Similar to a single payload, but takes advantage of staging. Uses connection passed from the stager. Not subject to size limitations of individual vulnerabilities A stager can also be a stage Functions of Payloads :- Bind Shell: setup a socket, bind it to a specific port and listen for connection. Upon accepting a connection spawn a shell. Victim has to allow incoming connections on selected port. Reverse Shell: instead of binding to a port waiting for connection, the shellcode simply connect to a predefined IP and port number and spawn a shell. Find Tag: find socket style payloads that search for a socket based on the presence of a tag on the wire. Find_Port: payloads that search for a socket by comparing peer port names relative to the target machine. Ordinal Payloads: Uses static ordinals in WS2_32.DLL to locate symbol addresses. Leads to very tiny win32 stagers (92 byte reverse, 93 byte findsock) Reverse Http: called PassiveX payloads in 2.x. Tunnel communication over HTTP using IE 6. Payload modifies registry and launches IE, IE loads custom ActiveX control to stage the payload, Uses standard IE proxy and authorization settings, Can be used to inject VNC, Meterpreter, custom dlls. Adduser: Executes the net user x x /add & net localgroup administrators x /add Downloadexec: Download a .exe from a URL and execute it
- 13. 13 | P a g e Uploadexec: uploads a .exe from local computer and executes Exec: execute a command of your choice Dllinject: injects a custom dll (you'll have to supply the dll) VNCinject: injects a custom VNC server dll into memory Meterpreter: the super payload, custom dll injected into memory (more on Day2); tons of postexploitation tools Opcode Database The Opcode Database is an important resource for writers of new exploits. Buffer overflow exploits on Windows often require precise knowledge of the position of certain machine language opcodes in the attacked program or included DLLs. These positions differ in the various versions and patch-levels of a given operating system, and they are all documented and conveniently searchable in the Opcode Database. This allows one to write buffer overflow exploits which work across different versions of the target operating system. Shellcode Database The Shellcode database contains the payloads (also known as shellcode) used by the Metasploit Framework. These are written in assembly language and full source code is available.
- 14. 14 | P a g e Graphical Overview of Metasploit :- Steps for exploiting Vulnerabilities :- 1. Choosing and configuring an exploit(code that enters a target system by taking advantage of one of its bugs; about 300 different exploits for windows, Unix/Linux and Mac OS systems are included); 2. Checking whether the intended target system is susceptible to the chosen exploit (optional); 3. Choosing and configuring a Payload (code that will be executed on the target system upon successful entry, for instance a remote shell or aVNC Server); 4. Choosing the encoding technique to encode the payload so that the Intrusion Prevention System (IPS) will not catch the encoded payload; 5. Executing the exploit.
- 15. 15 | P a g e Pre–Exploiting Phase :- Using exploit for penetration testing is legal, hence if you want to penetratate your own system environment will not be illegal. But as I don’t have the real time environment I have created it using some third party softwares and operating systems as given below. 1) Install Vmware/Virtual PC which allows you to install various operating systems to use it at the same time.These softwares also creates a virtual network between the host operating systems and the own operating system.so the beginners can do the real practices or penetration on his own. 2) Install Metasploit Framework on the attackers system and start penetrating systems on the host operating systems installed in vmware. Lab Setup Own operating system – Windows XP professional Service pack 3 IP Address – 192.168.23.1 Host operating system 1 – Windows XP professional 2002 Services pack 1 IP Address – 192.168.23.131 Host operating system 2 – Windows XP professional Services pack 2 IP Address – 192.168.23.133
- 16. 16 | P a g e Exploiting Vulnerability :- 1) Exploit :- windows/dcerpc/ms03_026_dcom Payload :- Windows/adduser Rort :- 135 Rhost :- 192.168.23.131 Steps - Click on msfconsole on program list on start buttons.it show the below,
- 17. 17 | P a g e Steps – use any exploit from list of exploits using keyword “use” following with exploit name.
- 18. 18 | P a g e Steps – watch exploits options “show options” to fill with appropriate values with “set ” keyword.
- 19. 19 | P a g e Steps – This is the target host operating system on vmware on whos IP address is 192.168.23.131
- 20. 20 | P a g e Steps – set the value of RHOST with target IP address. set other default values if you want to change.
- 21. 21 | P a g e Steps - To see the list of PAYLOADS use command “Show payloads” and select the PAYLOAD you want to set with keyword following with PAYLOAD name.
- 22. 22 | P a g e Steps - Type “show option ” again to set values of PAYLOADS and set it appropriately. set TARGET the same as the target operating system if there are multiple targets shown in options .
- 23. 23 | P a g e Steps - To exploit the vulnerability type the keyword “exploit” it will start attacking on the given target system.
- 24. 24 | P a g e Steps – Target system after exploiting the vulnerability it created a new user account “Metasploit ” with password “metasploit” with administrator privileges.
- 25. 25 | P a g e 2) Exploit :- windows/dcerpc/ms03_026_dcom Payload :- generic/shell_bind_tcp Rort :- 135 Rhost :- 192.168.23.131 Steps – select any exploit.
- 26. 26 | P a g e The Target systems IP address.
- 27. 27 | P a g e Step - set IP address of target system as “set HOST ” following with ip.
- 28. 28 | P a g e Step – set PAYLOAD generic/shell_bind_tcp
- 29. 29 | P a g e Step :- use exploits to execute attack on the Target system
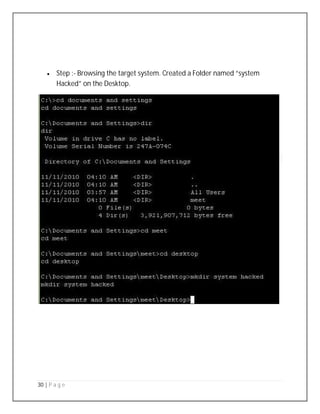
- 30. 30 | P a g e Step :- Browsing the target system. Created a Folder named “system Hacked” on the Desktop.
- 31. 31 | P a g e Screen shot :- These is the screen shot of the target system after attack where you can see the folder named “Hacked system” which is remotely created by the attacker which identifies the system is vulnerable. Remotely created folder on target system
- 32. 32 | P a g e 3) Exploit :- windows/dcerpc/ms03_026_dcom Payload :- Windows/meterpreter/bind_tcp Rort :- 135 Rhost :- 192.168.23.133 Windows/dcerpc/ms-3_026_dcom exploit is selected to exploit the target system vulnerabilities.
- 33. 33 | P a g e Here the options are checked using the command show options
- 34. 34 | P a g e In this step the PAYLOAD windows/meterpreter/bind_tcp is set to attack on the target system.
- 35. 35 | P a g e This step starts exploiting the target system.
- 36. 36 | P a g e Here Using “ipconfig ” command the IP address and other useful information is carried out.
- 37. 37 | P a g e Using metasploit core commands we can read,write or delete the data on the target sytem as show below.
- 38. 38 | P a g e Here as per the file extension type or file name type we can search any file on any directory as show below I typed “search –d c: -f * .txt” to search all text files which shows following result.
- 39. 39 | P a g e As per search I found some file named “Confidential.txt” on the desktop of user “meet” so I went on the path where the file exsist and Downloaded with the command “Download confidential.txt”
- 40. 40 | P a g e Previously downloaded file is copided in the local attackers system in the folder of the “Metasploit” in Program Files as show below, Downloaded confidential file from Target system remotely
- 41. 41 | P a g e Here is the file we downloaded from the attackers system as we can see it resides on the desktop.
- 42. 42 | P a g e Here we deleted that file from the storage device of the target system.
- 43. 43 | P a g e Now you can see that the file we deleted is not visible on the desktop as we know it is deleted.
- 44. 44 | P a g e Bibilography www.exploits.com www.google.com www.wikipedia.com











![11 | P a g e
In April 2010, Rapid7 released Metaploit Express, which is a commercial version
of Metasploit. Based on the Metasploit Framework, it offers a graphical user
interface, integrates nmap for discovery, and adds smart bruteforcing as well as
automated evidence collection. Rapid7 has a full-featured 7-day trial for Metasploit
Express.
Exploits :-
It is a code which allows an attacker to take advantage of vulnerable
System.
Exploit Types :-
Pretty much any protocol UDP, TCP, SMB, HTTP, FTP, SMTP, TFTP,
SSH, etc
Active, Passive, Brute-Force
Remote, Local, User-Interaction (technically remote category)
Remote: windows/dcerpc/ms03_026_dcom
Local: no real local examples, but doable
User-Interaction--All your browser, “have to click on something,” type
exploits
windows/browser/ms06_013_createtextrange
Payloads :-
Payload is Arbitrary code that is to be executed upon successful exploitation.It is
a acutal code which run on the system after exploitation.
Types Of Payloads :-
1) Single [shell_reverse_tcp = inline (single)] :-
A self-contained payload that performs a specific task
Size varies depending on the task
Example: Reverse or bind command shell](https://image.slidesharecdn.com/c7e61e3e-7b97-491c-8818-a8696b3dbacc-150717183516-lva1-app6892/85/Exploits-Attack-on-Windows-Vulnerabilities-11-320.jpg)
![12 | P a g e
2) Stager [shell/reverse_tcp = stager] :-
A stub payload that loads / bootstraps a stage
Size generally much smaller than single payloads
Passes connection information onto the stage
3) Stage :-
Similar to a single payload, but takes advantage of staging.
Uses connection passed from the stager.
Not subject to size limitations of individual vulnerabilities
A stager can also be a stage
Functions of Payloads :-
Bind Shell: setup a socket, bind it to a specific port and listen for connection.
Upon accepting a connection spawn a shell. Victim has to allow incoming
connections on selected port.
Reverse Shell: instead of binding to a port waiting for connection, the shellcode
simply connect to a predefined IP and port number and spawn a shell.
Find Tag: find socket style payloads that search for a socket based on the
presence of a tag on the wire.
Find_Port: payloads that search for a socket by comparing peer port names
relative to the target machine.
Ordinal Payloads: Uses static ordinals in WS2_32.DLL to locate symbol
addresses. Leads to very tiny win32 stagers (92 byte reverse, 93 byte findsock)
Reverse Http: called PassiveX payloads in 2.x. Tunnel communication over
HTTP using IE 6. Payload modifies registry and launches IE, IE loads custom
ActiveX control to stage the payload, Uses standard IE proxy and authorization
settings, Can be used to inject VNC, Meterpreter, custom dlls.
Adduser: Executes the net user x x /add & net localgroup administrators x /add
Downloadexec: Download a .exe from a URL and execute it](https://image.slidesharecdn.com/c7e61e3e-7b97-491c-8818-a8696b3dbacc-150717183516-lva1-app6892/85/Exploits-Attack-on-Windows-Vulnerabilities-12-320.jpg)






















































































![Chapter 9 system penetration [compatibility mode]](https://cdn.slidesharecdn.com/ss_thumbnails/chapter9systempenetrationcompatibilitymode-160414004635-thumbnail.jpg?width=560&fit=bounds)











