Extended Security with WSO2 API Management Platform
Download as PPTX, PDF5 likes1,856 views
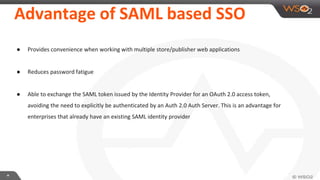
Uvindra Jayasinha from WSO2 presented on extending security with the WSO2 API Management platform. He covered best practices for OAuth 2.0 access tokens, adding SAML single sign-on, federated identity with third-party providers, enforcing fine-grained entitlement policies, and accessing user attributes. The presentation explained key OAuth concepts like grant types, actors, and tokens. It also described using SAML assertions, XACML policies, and JWT claims to pass user information and control access.
1 of 20
Downloaded 38 times




![**
OAuth 2.0 - The Cornerstone
OAuth definition from the OAuth 2.0 IETF specification -
"The OAuth 2.0 authorization framework enables a third-party application to
obtain limited access to an HTTP service, either on behalf of a resource owner by
orchestrating an approval interaction between the resource owner and the HTTP
service, or by allowing the third-party application to obtain access on its own
behalf." [1]
[1] http://tools.ietf.org/html/rfc6749](https://image.slidesharecdn.com/extendedsecuritywithwso2apimanagementplatform-150505075117-conversion-gate01/85/Extended-Security-with-WSO2-API-Management-Platform-5-320.jpg)











![**
Passing Claims via JWT
● Claim - user attribute that is mapped to the underlying user store
● Claim dialect - A set of predefined claims
● API Manager can be configured to pass a Claim Dialect via a JSON Web Token[1] to the back end API
along with the API invocation
[1] http://openid.net/specs/draft-jones-json-web-token-07.html#anchor3](https://image.slidesharecdn.com/extendedsecuritywithwso2apimanagementplatform-150505075117-conversion-gate01/85/Extended-Security-with-WSO2-API-Management-Platform-18-320.jpg)
![**
Resources
● [Article] OAuth2 Grant Types and Need For Implicit Grant for JavaScript and Mobile Applications
http://wso2.com/library/articles/2014/12/article-
oauth2-grant-types-and-need-for-implicit-grant-for-javascript-mobile-applications/
● What is the purpose of the implicit grant authorization type in OAuth 2?
http://stackoverflow.com/questions/7522831/what-is-the-purpose-of-the-implicit-grant-authorization-type-in-oauth-2
● Enforcing fine grained entitlement policies With XACML
http://xacmlinfo.org/2014/10/24/authorization-for-apis-with-xacml-and-oauth-2-0/](https://image.slidesharecdn.com/extendedsecuritywithwso2apimanagementplatform-150505075117-conversion-gate01/85/Extended-Security-with-WSO2-API-Management-Platform-19-320.jpg)

Ad
Recommended
Learn with WSO2 - API Security 



Learn with WSO2 - API Security WSO2 The document discusses OAuth and its core concepts including authorization grants, client types, authentication methods, and the OAuth handshake process. It describes the key components of OAuth including the resource owner, resource server, client, and authorization server. It also covers the different authorization grant types (authorization code, implicit, resource owner password credentials, client credentials), scopes, and the steps involved in the OAuth authorization code grant flow and implicit grant flow.
OAuth2 & OpenID Connect



OAuth2 & OpenID ConnectMarcin Wolnik This document provides an overview of OAuth2 and OpenID Connect. It defines key terms like authentication and authorization. It describes the typical authentication landscape for thick clients, server-side web apps, and how OAuth2 addresses delegating access to protected resources. The document outlines the OAuth2 authorization code flow and actors involved. It also introduces OpenID Connect which builds upon OAuth2 by adding an identity layer and additional endpoints for user details. Finally, it provides examples of OpenID Connect flows for confidential and public clients.
Using a Third Party Key Management System with WSO2 API Manager



Using a Third Party Key Management System with WSO2 API ManagerWSO2 To view recording of this webinar please use below URL:
http://wso2.com/library/webinars/2015/08/using-a-third-party-key-management-system-with-wso2-api-manager/
This webinar will demonstrate the WSO2 API Manager plugged into a third party key management system (MITREid Connect) in compliance with OpenID connect 2.0 specification. During this demonstration we will discuss
Configuration changes that need to be done in WSO2 API Manager
Java interfaces that need to be extended when writing your own implementation
Feeding in custom attributes required to create and manage clients created at third-party authorization servers using Jaggery REST APIs
A sample implementation with the third party key management system
OAuth2 + API Security



OAuth2 + API SecurityAmila Paranawithana The document discusses OAuth 2.0 and how it provides a method for third party applications to access private resources from an API, while allowing the resource owners to authorize access without sharing credentials. It describes the four main roles in OAuth 2.0 - resource owner, client, authorization server, and resource server. It also summarizes the three main authorization flows - authorization code, implicit, and client credentials flows. The document provides details on how each flow works, including the request and response parameters.
Security for oauth 2.0 - @topavankumarj



Security for oauth 2.0 - @topavankumarjPavan Kumar J The document provides an overview of OAuth 2.0 authorization framework and discusses common security issues. It begins with introducing the speaker and their background in security. The main topics covered include the history and core elements of OAuth, common grant types and flows, and vulnerabilities like insecure storage of secrets, CSRF attacks during authorization, scope permission issues, and account takeover risks. Best practices for clients and authorization servers to mitigate these threats are also outlined.
Protecting your APIs with OAuth 2.0



Protecting your APIs with OAuth 2.0Ubisecure APIs are now the standard entry point to the majority of newly created ‘back-end’ functionality. These APIs exist to provide not only a standardized, structured way to access the required features or functions, but also to act as ‘gatekeepers’, ensuring appropriate security, auditing, accounting etc. Security is always underpinned by identity and as such, APIs need to know if not who is accessing them, what is the context in which they are being accessed.
OAuth2 primer



OAuth2 primerManish Pandit This document provides an overview of OAuth2 as an authorization standard. It describes the key concepts in OAuth2 including the resource owner, client, authorization server, access tokens, refresh tokens, and different grant types (authorization code, implicit, resource owner password, client credentials). It provides examples of OAuth2 flows and demonstrates some implementations.
An introduction to OAuth 2



An introduction to OAuth 2Sanjoy Kumar Roy This document provides an introduction and overview of OAuth 2.0. It discusses the key components and actors in the OAuth framework, including clients, protected resources, resource owners, and authorization servers. It describes the major steps of an OAuth transaction, issuing and using tokens. Specifically, it outlines the authorization code grant flow, how clients request and receive access tokens from authorization servers to access protected resources on behalf of resource owners. It also defines common OAuth concepts like scopes, refresh tokens, and authorization grants.
OAuth2 - Introduction



OAuth2 - IntroductionKnoldus Inc. The OAuth 2.0 authorization framework enables a third-party
application to obtain limited access to an HTTP service, either on
behalf of a resource owner by orchestrating an approval interaction
between the resource owner and the HTTP service, or by allowing
the third-party application to obtain access on its own behalf.
UMA for ACE



UMA for ACEHannes Tschofenig UMA is a profile and application of OAuth that defines how resource owners can control resource access by clients operated by arbitrary requesting parties, where the resources reside on any number of resource servers, and where a centralized authorization server governs access based on resource owner policy. Recent investigations have shown promise for applying UMA to Internet of Things authorization use cases.
This is a presentation by Eve Maler for the IETF ACE working group.
Securing Single-Page Applications with OAuth 2.0



Securing Single-Page Applications with OAuth 2.0Prabath Siriwardena This document discusses securing single-page applications (SPAs) with OAuth 2.0. It describes how SPAs work by loading a single HTML page and dynamically updating content without page reloads. It outlines two issues with using OAuth in SPAs: client authentication and exposing access tokens to users. It proposes using the implicit grant type to address these by enabling single sign-on without exposing credentials to the SPA. It also describes using an OAuth proxy to further improve security by encrypting tokens in cookies and routing all API calls through the proxy.
OAuth 2



OAuth 2ChrisWood262 OAuth 2 is an authorization framework that allows applications to access user data and perform actions on their behalf. It defines flows for applications to request access, and provides short-lived credentials in response. The main roles in OAuth are the resource owner (user), client (application), resource server (API), and authorization server (issues tokens). Common grant types include authorization code, implicit, and client credentials flows. Tokens returned include access and refresh tokens, and OpenID Connect adds optional ID tokens containing user information.
An Introduction to OAuth 2



An Introduction to OAuth 2Aaron Parecki The document provides an overview of the history and development of OAuth standards for authorization. It describes some of the issues with early implementations that prompted the creation of OAuth 1.0, including services storing user passwords and lack of ability to revoke access. OAuth 1.0 introduced signatures to address these issues. OAuth 2.0 replaced signatures with HTTPS and defines common flows for different use cases, including authorization code, implicit, password, and client credentials grants.
Stateless Auth using OAuth2 & JWT



Stateless Auth using OAuth2 & JWTGaurav Roy The document discusses stateless authorization using OAuth2 and JSON Web Tokens (JWT). It begins with an introduction to authentication, authorization, and single sign-on (SSO). It then provides an in-depth explanation of OAuth2 actors, flows, and grant types. The Authorization Code Grant flow and Implicit Grant flow are explained in detail. Finally, it introduces JWT and why it is a suitable standard for representing OAuth2 access tokens since it meets the requirements and libraries are available.
Introduction to OAuth2.0



Introduction to OAuth2.0Oracle Corporation This document provides an overview of OAuth 2.0 including key terms, grant types, and workflows. It describes OAuth as an authorization framework that allows clients to access protected resources from an API without sharing the user's credentials. The document explains the roles of clients, resource owners, resource servers, and authorization servers. It also summarizes the authorization code grant flow, refresh tokens, and different OAuth grant types.
Spring4 security oauth2



Spring4 security oauth2axykim00 OAuth2 is a protocol for authorization that allows clients to access user resources stored on a resource server. It separates the client application from the resource owner credentials. The authorization code flow involves a client redirecting a user to an authorization server, the user authenticating and authorizing access, and the authorization server returning an authorization code to the client which can then request an access token to access protected resources from the resource server on the user's behalf, without exposing the user's credentials directly. This flow allows for single sign-on across microservices and fine-grained authorization of delegated access to resources.
Web API 2 Token Based Authentication



Web API 2 Token Based Authenticationjeremysbrown This document discusses token based authentication in ASP.NET Web API 2 projects. It covers the basic concepts of token authentication including the roles in OAuth 2.0 of resource owners, clients, authorization servers and resource servers. It also summarizes the different OAuth 2.0 client types, authorization grant types, and development options for implementing token authentication using OWIN middleware or DotNetOpenAuth.
OAuth based reference architecture for API Management



OAuth based reference architecture for API ManagementWSO2 The document discusses OAuth 2.0 and how it is implemented in WSO2 API Manager. It provides an overview of OAuth 2.0 concepts like authorization grants, tokens and flows. It also summarizes how WSO2 supports the OAuth 2.0 framework for API management, including token management and authorization code, implicit and password grants. Extensions to OAuth 2.0 in WSO2 API Manager are also briefly covered.
The State of OAuth2



The State of OAuth2Aaron Parecki The document discusses OAuth 2.0 and implementing an OAuth 2.0 authorization server. It covers the different grant types (authorization code, implicit, password, client credentials), how each works, and which are best for different client types like web apps, browser-based apps, and mobile apps. It also discusses topics like scopes, limiting access to resources, accessing protected resources with an access token, and refreshing expired access tokens. The document provides guidance on implementing an OAuth 2.0 server including choosing library, grant types, token types, and defining scopes.
Spring security oauth2



Spring security oauth2axykim00 OAuth2 is a protocol for authorization that allows clients limited access to user accounts and specifies four methods for obtaining an access token, including the authorization code flow. The authorization code flow involves a client redirecting a user to an authorization server, the user authorizing access, and the authorization server issuing an authorization code to the client, which can then request an access token to access a resource server on the user's behalf, while avoiding exposing the user's credentials directly.
OpenID vs OAuth - Identity on the Web



OpenID vs OAuth - Identity on the WebRichard Metzler The document discusses identity management protocols OpenID and OAuth. OpenID allows users to use a single digital identity across multiple websites, while OAuth allows websites to grant third party applications access to user data without sharing passwords. The document outlines the roles, flows, and differences between the two protocols, and proposes a project to implement an OAuth service provider and consumer as an example.
Spring4 security oauth2



Spring4 security oauth2Sang Shin The document discusses OAuth2 and the authorization code flow. OAuth2 is a protocol for authorization that allows clients to obtain limited access to user accounts and reduces the scope of access. It involves four main actors: a resource owner (user), client app, authorization server, and resource server. The authorization code flow involves the client redirecting the user to the authorization server to log in, the user authorizing access, and the authorization server issuing an authorization code to the client, which can then request an access token to access protected resources from the resource server on the user's behalf.
Best Practices in Building an API Security Ecosystem



Best Practices in Building an API Security EcosystemPrabath Siriwardena Enterprise API adoption has gone beyond predictions. It has become the 'coolest' way of exposing business functionalities to the outside world. Both your public and private APIs, need to be protected, monitored and managed.
This session focuses on API Security. There are so many options out there to make someone easily confused. When to select one over the other is always a question - and you need to deal with it quite carefully to identify and isolate the tradeoffs. Security is not an afterthought. It has to be an integral part of any development project - so as for APIs. API security has evolved a lot in last five years. This talk covers best practices in building an API Security Ecosystem with OAuth 2.0, UMA, SCIM, XACML and LDAP.
OAuth - Open API Authentication



OAuth - Open API Authenticationleahculver http://www.justin.tv/hackertv/49975/Tech_Talk_1_Leah_Culver_on_OAuth
Tech talk about OAuth, and open standard for API authentication. Originally broadcast on Justin.tv.
Oauth 2.0 security



Oauth 2.0 securityvinoth kumar OAuth 2.0
Oauth2.0 is an “authorization” framework for web applications. It permits selective access to a user’s resource without disclosing the password to the website which asks for the resource.
Agenda for the session:
What is Oauth 2.0
Oauth 2.0 Terminologies
Oauth workflow
Exploiting Oauth for fun and profit
Reference
OAuth 2.0



OAuth 2.0Uwe Friedrichsen This slide deck gives an introduction to OAuth 2.0, starting with some concepts, explaining the flow plus a few hints. The reminder of the slides are about implementing an OAuth 2.0 server using the Apache Amber library (renamed to Apache Oltu lately). My impression is that many developers shy away as soon as they hear "security" and so I did not only want to talk about the concepts of OAuth 2.0 but also wanted to show how easily you can implement an OAuth 2.0 server ... hope it reduces the fear of contact a bit ... ;-)
Modern Security with OAuth 2.0 and JWT and Spring by Dmitry Buzdin



Modern Security with OAuth 2.0 and JWT and Spring by Dmitry BuzdinJava User Group Latvia Have you ever wondered how single-sign-on on sites like Google and Facebook works? Are you a fan of stateless application architectures? Do you want to learn how to put together a modern security approach for your next Spring Boot project? If the answer is yes, to anything above, then this session is for you. Dmitry will explain what is OAuth 2.0 and JWT, why are they popular, and how to integrate them in Java project.
Enabling Cloud Native Security with OAuth2 and Multi-Tenant UAA 



Enabling Cloud Native Security with OAuth2 and Multi-Tenant UAA Will Tran UAA, as a core component of Cloud Foundry, is responsible for authenticating and authorizing requests between platform users (e.g. those that push apps) and platform components (e.g. the cloud controller). But when it came to doing auth for the apps you push and the end users of those apps, using the built-in UAA wasn't the best fit, and you could easily end up shooting yourself in the foot. Until now. This talk will guide you though UAA's new multi-tenancy features, and show you how to use the built-in UAA to create arbitrary authorization scenarios for your products without the danger of affecting the security of the core platform. With this level of freedom, you'll have complete and fine-grained control over who is allowed to access your product's components, and how those components are allowed to interact with one another.
Combining WSO2 API Manager with WSO2 BAM for billing in the energy industry



Combining WSO2 API Manager with WSO2 BAM for billing in the energy industryWSO2 This document discusses using WSO2 API Manager and BAM for billing in the energy industry. It provides an overview of the presenters and their roles, an agenda that includes using the API Manager for publishing APIs and billing and combining it with BAM, and a case study of an energy company's challenges in securely managing APIs and clients. The document then covers the architecture and features of API Manager that address the company's needs like access control, tracing requests, and ensuring availability and performance.
Leveraging federation capabilities of Identity Server for API gateway



Leveraging federation capabilities of Identity Server for API gatewayWSO2 This document provides information about single sign-on (SSO) authentication options for web applications. It discusses the Shibboleth SSO system, which provides SSO using Security Assertion Markup Language (SAML) standards. Also mentioned are OpenID and SAML SSO as other common SSO protocols that allow users to log in to multiple applications without re-entering credentials. The document appears to be an overview of SSO technologies for web applications.
Ad
More Related Content
What's hot (20)
OAuth2 - Introduction



OAuth2 - IntroductionKnoldus Inc. The OAuth 2.0 authorization framework enables a third-party
application to obtain limited access to an HTTP service, either on
behalf of a resource owner by orchestrating an approval interaction
between the resource owner and the HTTP service, or by allowing
the third-party application to obtain access on its own behalf.
UMA for ACE



UMA for ACEHannes Tschofenig UMA is a profile and application of OAuth that defines how resource owners can control resource access by clients operated by arbitrary requesting parties, where the resources reside on any number of resource servers, and where a centralized authorization server governs access based on resource owner policy. Recent investigations have shown promise for applying UMA to Internet of Things authorization use cases.
This is a presentation by Eve Maler for the IETF ACE working group.
Securing Single-Page Applications with OAuth 2.0



Securing Single-Page Applications with OAuth 2.0Prabath Siriwardena This document discusses securing single-page applications (SPAs) with OAuth 2.0. It describes how SPAs work by loading a single HTML page and dynamically updating content without page reloads. It outlines two issues with using OAuth in SPAs: client authentication and exposing access tokens to users. It proposes using the implicit grant type to address these by enabling single sign-on without exposing credentials to the SPA. It also describes using an OAuth proxy to further improve security by encrypting tokens in cookies and routing all API calls through the proxy.
OAuth 2



OAuth 2ChrisWood262 OAuth 2 is an authorization framework that allows applications to access user data and perform actions on their behalf. It defines flows for applications to request access, and provides short-lived credentials in response. The main roles in OAuth are the resource owner (user), client (application), resource server (API), and authorization server (issues tokens). Common grant types include authorization code, implicit, and client credentials flows. Tokens returned include access and refresh tokens, and OpenID Connect adds optional ID tokens containing user information.
An Introduction to OAuth 2



An Introduction to OAuth 2Aaron Parecki The document provides an overview of the history and development of OAuth standards for authorization. It describes some of the issues with early implementations that prompted the creation of OAuth 1.0, including services storing user passwords and lack of ability to revoke access. OAuth 1.0 introduced signatures to address these issues. OAuth 2.0 replaced signatures with HTTPS and defines common flows for different use cases, including authorization code, implicit, password, and client credentials grants.
Stateless Auth using OAuth2 & JWT



Stateless Auth using OAuth2 & JWTGaurav Roy The document discusses stateless authorization using OAuth2 and JSON Web Tokens (JWT). It begins with an introduction to authentication, authorization, and single sign-on (SSO). It then provides an in-depth explanation of OAuth2 actors, flows, and grant types. The Authorization Code Grant flow and Implicit Grant flow are explained in detail. Finally, it introduces JWT and why it is a suitable standard for representing OAuth2 access tokens since it meets the requirements and libraries are available.
Introduction to OAuth2.0



Introduction to OAuth2.0Oracle Corporation This document provides an overview of OAuth 2.0 including key terms, grant types, and workflows. It describes OAuth as an authorization framework that allows clients to access protected resources from an API without sharing the user's credentials. The document explains the roles of clients, resource owners, resource servers, and authorization servers. It also summarizes the authorization code grant flow, refresh tokens, and different OAuth grant types.
Spring4 security oauth2



Spring4 security oauth2axykim00 OAuth2 is a protocol for authorization that allows clients to access user resources stored on a resource server. It separates the client application from the resource owner credentials. The authorization code flow involves a client redirecting a user to an authorization server, the user authenticating and authorizing access, and the authorization server returning an authorization code to the client which can then request an access token to access protected resources from the resource server on the user's behalf, without exposing the user's credentials directly. This flow allows for single sign-on across microservices and fine-grained authorization of delegated access to resources.
Web API 2 Token Based Authentication



Web API 2 Token Based Authenticationjeremysbrown This document discusses token based authentication in ASP.NET Web API 2 projects. It covers the basic concepts of token authentication including the roles in OAuth 2.0 of resource owners, clients, authorization servers and resource servers. It also summarizes the different OAuth 2.0 client types, authorization grant types, and development options for implementing token authentication using OWIN middleware or DotNetOpenAuth.
OAuth based reference architecture for API Management



OAuth based reference architecture for API ManagementWSO2 The document discusses OAuth 2.0 and how it is implemented in WSO2 API Manager. It provides an overview of OAuth 2.0 concepts like authorization grants, tokens and flows. It also summarizes how WSO2 supports the OAuth 2.0 framework for API management, including token management and authorization code, implicit and password grants. Extensions to OAuth 2.0 in WSO2 API Manager are also briefly covered.
The State of OAuth2



The State of OAuth2Aaron Parecki The document discusses OAuth 2.0 and implementing an OAuth 2.0 authorization server. It covers the different grant types (authorization code, implicit, password, client credentials), how each works, and which are best for different client types like web apps, browser-based apps, and mobile apps. It also discusses topics like scopes, limiting access to resources, accessing protected resources with an access token, and refreshing expired access tokens. The document provides guidance on implementing an OAuth 2.0 server including choosing library, grant types, token types, and defining scopes.
Spring security oauth2



Spring security oauth2axykim00 OAuth2 is a protocol for authorization that allows clients limited access to user accounts and specifies four methods for obtaining an access token, including the authorization code flow. The authorization code flow involves a client redirecting a user to an authorization server, the user authorizing access, and the authorization server issuing an authorization code to the client, which can then request an access token to access a resource server on the user's behalf, while avoiding exposing the user's credentials directly.
OpenID vs OAuth - Identity on the Web



OpenID vs OAuth - Identity on the WebRichard Metzler The document discusses identity management protocols OpenID and OAuth. OpenID allows users to use a single digital identity across multiple websites, while OAuth allows websites to grant third party applications access to user data without sharing passwords. The document outlines the roles, flows, and differences between the two protocols, and proposes a project to implement an OAuth service provider and consumer as an example.
Spring4 security oauth2



Spring4 security oauth2Sang Shin The document discusses OAuth2 and the authorization code flow. OAuth2 is a protocol for authorization that allows clients to obtain limited access to user accounts and reduces the scope of access. It involves four main actors: a resource owner (user), client app, authorization server, and resource server. The authorization code flow involves the client redirecting the user to the authorization server to log in, the user authorizing access, and the authorization server issuing an authorization code to the client, which can then request an access token to access protected resources from the resource server on the user's behalf.
Best Practices in Building an API Security Ecosystem



Best Practices in Building an API Security EcosystemPrabath Siriwardena Enterprise API adoption has gone beyond predictions. It has become the 'coolest' way of exposing business functionalities to the outside world. Both your public and private APIs, need to be protected, monitored and managed.
This session focuses on API Security. There are so many options out there to make someone easily confused. When to select one over the other is always a question - and you need to deal with it quite carefully to identify and isolate the tradeoffs. Security is not an afterthought. It has to be an integral part of any development project - so as for APIs. API security has evolved a lot in last five years. This talk covers best practices in building an API Security Ecosystem with OAuth 2.0, UMA, SCIM, XACML and LDAP.
OAuth - Open API Authentication



OAuth - Open API Authenticationleahculver http://www.justin.tv/hackertv/49975/Tech_Talk_1_Leah_Culver_on_OAuth
Tech talk about OAuth, and open standard for API authentication. Originally broadcast on Justin.tv.
Oauth 2.0 security



Oauth 2.0 securityvinoth kumar OAuth 2.0
Oauth2.0 is an “authorization” framework for web applications. It permits selective access to a user’s resource without disclosing the password to the website which asks for the resource.
Agenda for the session:
What is Oauth 2.0
Oauth 2.0 Terminologies
Oauth workflow
Exploiting Oauth for fun and profit
Reference
OAuth 2.0



OAuth 2.0Uwe Friedrichsen This slide deck gives an introduction to OAuth 2.0, starting with some concepts, explaining the flow plus a few hints. The reminder of the slides are about implementing an OAuth 2.0 server using the Apache Amber library (renamed to Apache Oltu lately). My impression is that many developers shy away as soon as they hear "security" and so I did not only want to talk about the concepts of OAuth 2.0 but also wanted to show how easily you can implement an OAuth 2.0 server ... hope it reduces the fear of contact a bit ... ;-)
Modern Security with OAuth 2.0 and JWT and Spring by Dmitry Buzdin



Modern Security with OAuth 2.0 and JWT and Spring by Dmitry BuzdinJava User Group Latvia Have you ever wondered how single-sign-on on sites like Google and Facebook works? Are you a fan of stateless application architectures? Do you want to learn how to put together a modern security approach for your next Spring Boot project? If the answer is yes, to anything above, then this session is for you. Dmitry will explain what is OAuth 2.0 and JWT, why are they popular, and how to integrate them in Java project.
Enabling Cloud Native Security with OAuth2 and Multi-Tenant UAA 



Enabling Cloud Native Security with OAuth2 and Multi-Tenant UAA Will Tran UAA, as a core component of Cloud Foundry, is responsible for authenticating and authorizing requests between platform users (e.g. those that push apps) and platform components (e.g. the cloud controller). But when it came to doing auth for the apps you push and the end users of those apps, using the built-in UAA wasn't the best fit, and you could easily end up shooting yourself in the foot. Until now. This talk will guide you though UAA's new multi-tenancy features, and show you how to use the built-in UAA to create arbitrary authorization scenarios for your products without the danger of affecting the security of the core platform. With this level of freedom, you'll have complete and fine-grained control over who is allowed to access your product's components, and how those components are allowed to interact with one another.
Viewers also liked (19)
Combining WSO2 API Manager with WSO2 BAM for billing in the energy industry



Combining WSO2 API Manager with WSO2 BAM for billing in the energy industryWSO2 This document discusses using WSO2 API Manager and BAM for billing in the energy industry. It provides an overview of the presenters and their roles, an agenda that includes using the API Manager for publishing APIs and billing and combining it with BAM, and a case study of an energy company's challenges in securely managing APIs and clients. The document then covers the architecture and features of API Manager that address the company's needs like access control, tracing requests, and ensuring availability and performance.
Leveraging federation capabilities of Identity Server for API gateway



Leveraging federation capabilities of Identity Server for API gatewayWSO2 This document provides information about single sign-on (SSO) authentication options for web applications. It discusses the Shibboleth SSO system, which provides SSO using Security Assertion Markup Language (SAML) standards. Also mentioned are OpenID and SAML SSO as other common SSO protocols that allow users to log in to multiple applications without re-entering credentials. The document appears to be an overview of SSO technologies for web applications.
WSO2Con EU 2015: Securing, Monitoring and Monetizing APIs



WSO2Con EU 2015: Securing, Monitoring and Monetizing APIsWSO2 WSO2Con EU 2015: Securing, Monitoring and Monetizing APIs
Businesses today are rapidly moving from being service enabled to being API enabled. Moving into the world of APIs brings together its own set of complexities and challenges that are tough to tackle. API security, performance, scalability, monitoring and notifications are key areas to be focusing your engineering efforts on. The WSO2 Carbon platform is a complete open source enterprise middleware platform which includes products catering to your various different enterprise needs.
This talk will focus on leveraging the extensive feature set and extensible nature of the WSO2 platform to secure, monitor and monetize your APIs. It will also touch upon some of WSO2’s experiences with customers in building API ecosystems that suit modern day enterprises.
Presenter:
Nuwan Dias
Technical Lead,
WSO2
Implementing API Facade using WSO2 API Management Platform



Implementing API Facade using WSO2 API Management PlatformWSO2 The document discusses implementing an API facade pattern using the WSO2 API Management Platform. It describes the need for a facade layer to mediate between backend services and external API consumers. The WSO2 platform provides functionality like protocol switching, message transformation, and security bridging to implement the facade pattern and address issues with directly exposing heterogeneous backend services. It advocates for a pragmatic approach combining the facade and mediation layers to build scalable and decoupled API-centric architectures.
Security Patterns with WSO2 ESB



Security Patterns with WSO2 ESBWSO2 The document provides information about security patterns with WSO2 ESB. It introduces Jeewantha Dharmaparakrama and Isuru Udana, software engineers from WSO2, as presenters. It then discusses security requirements and how WSO2 ESB supports WS-Security, transport level security using HTTPS, and OAuth and entitlement with mediators. Specific security patterns covered include authentication, authorization, data confidentiality, integrity and non-repudiation.
WSO2 API Manager : Going beyond the just API Management



WSO2 API Manager : Going beyond the just API ManagementEdgar Silva In this presentation we show the tangible benefits from WSO2 API Manager, but also going a little beyond with WOS2 Platform
Open Source Integration with WSO2 Enterprise Service Bus



Open Source Integration with WSO2 Enterprise Service Bussumedha.r This document provides an overview of leveraging open source integration with the WSO2 Enterprise Service Bus (ESB). The presentation discusses the need for an ESB, introduces WSO2 ESB and its relationship to Apache Synapse, highlights key features such as message routing, transformation, orchestration and protocol support, explains important concepts like mediators and sequences, discusses how WSO2 ESB can be extended and customized, addresses performance and monitoring capabilities, and provides two use case examples of applying WSO2 ESB for notification emails and aggregating responses from multiple backends.
How to Enable Monetization of Your API Ecosystem



How to Enable Monetization of Your API EcosystemWSO2 To view recording of this webinar please use below URL:
http://wso2.com/library/webinars/2016/03/how-to-enable-monetization-of-your-api-ecosystem/
In the modern world of digitization, APIs are opening up ventures for new business opportunities. Organizations have started realizing the value of their data and services and are pushing to sell them. In this era, it is important to find the right business model to generate maximum revenue through your APIs.
You can leverage the WSO2 API Management platform to build your API monetization strategy. This session will look into WSO2 API Manager features and integration points to understand the roadmap to monetize your organization’s APIs. It will also discuss the following topics:
The API billing model: Usage plans
Integrating the API platform with a billing engine
Monitoring your API usage
Access control and rate limiting
WSO2 Identity Server - Product Overview



WSO2 Identity Server - Product OverviewWSO2 As the industry’s first enterprise identity bus (EIB), WSO2 Identity Server is the central backbone that connects and manages multiple identities across applications, APIs, the cloud, mobile, and Internet of Things devices, regardless of the standards on which they are based. The multi-tenant WSO2 Identity Server can be deployed directly on servers or in the cloud, and has the ability to propagate identities across geographical and enterprise borders in a connected business environment.
WSO2Con USA 2017: Cloud as a Delivery Channel



WSO2Con USA 2017: Cloud as a Delivery ChannelWSO2 The document discusses WSO2's cloud offerings for API management and integration. It notes that WSO2 provides a fully-featured API manager on the cloud to build developer ecosystems and enable digital businesses. The cloud services allow customers to manage identity, security, and privacy across digital systems and gain real-time insights from data. WSO2's cloud has various hosting options for production and non-production environments, and offers advantages like scalability, availability, and support over non-cloud alternatives.
API designing with WSO2 API Manager



API designing with WSO2 API ManagerWSO2 The document discusses API design and management using WSO2 API Manager. It provides information about the presenters, WSO2 company, key components of API Manager, and demonstrates designing, implementing, and managing APIs with API Manager. The document recommends API Manager as a complete solution for designing, implementing, and managing APIs through its API publisher and other features.
WSO2Con USA 2017: Analytics Patterns for Your Digital Enterprise



WSO2Con USA 2017: Analytics Patterns for Your Digital EnterpriseWSO2 The WSO2 analytics platform provides a high performance, lean, enterprise-ready, streaming solution to solve data integration and analytics challenges faced by connected businesses. This platform offers real-time, interactive, machine learning and batch processing technologies that empower enterprises to build a digital business, by connecting various enterprise data sources to enhance your experience in understanding the data and to increase internal productivity.
This session explores how to enable digital transformation by building a data analytics platform. It will discuss the follwoing topics:
WSO2 Data Analytics Server architecture
Understanding streaming constructs
Architectural styles for data integration
Debugging and troubleshooting your integration
Deployment
Performance tuning
Production hardening
WSO2 API Platform: Vision and Roadmap



WSO2 API Platform: Vision and RoadmapWSO2 To view recording of this webinar please use the below URL:
http://wso2.com/library/webinars/2015/08/wso2-api-platform-vision-and-roadmap/
WSO2 API platform adopters are driving digital business and creating innovative business models. API platforms create a secure, self-service, managed, and monetized environment that increases safe connected business interactions.
In this presentation, Chris and Shiro will describe:
Key goals and challenges driving API platform adoption
WSO2 API Platform capabilities and advantages
Visionary platform use cases
Innovative customer success stories
Workshop: API Management



Workshop: API ManagementWSO2 Co-Founder and CTO, Paul Fremantle and Solutions Architect, Senaka Fernando facilitated this workshop at Jax London 2014. The workshop illustrated how API management helps organizations participate in the API Economy; with the first half of the workshop looking at the overall landscape and approaches, while the second half focusing on using Open Source API Management tooling to expose, monitor and manage APIs.
CAS, OpenID, Shibboleth, SAML : concepts, différences et exemples



CAS, OpenID, Shibboleth, SAML : concepts, différences et exemplesClément OUDOT Avec la multiplication des applications Web, la question de l’authentification à ces applications est devenue primordiale. Pour simplifier la vie de l’utilisateur, le concept de SSO (Single Sign On) a été inventé. Dans ce domaine, plusieurs protocoles et standards existent, comme CAS, OpenID, Liberty Alliance, Shibboleth ou SAML. Quelles sont les différences ? Comment utiliser ces protocoles dans les applications ? Cette conférence tentera de répondre à ces questions en présentant des cas concrets d’implémentation.
Best Practices for API Management 



Best Practices for API Management WSO2 Successful development and deployment best practices of WSO2 customers to secure, monitor, and manage APIs
Architecting an Enterprise API Management Strategy



Architecting an Enterprise API Management StrategyWSO2 The document discusses strategies for architecting an enterprise API management strategy. It covers factors to consider like whether to treat APIs as a product or tactic. It also discusses API management components like the API publisher and store. The document outlines reference architectures like using API management within an orthogonal toolset. It provides examples of API management for use cases like within a telecommunications ecosystem.
Ad
Similar to Extended Security with WSO2 API Management Platform (20)
Microservice security with spring security 5.1,Oauth 2.0 and open id connect 



Microservice security with spring security 5.1,Oauth 2.0 and open id connect Nilanjan Roy This document provides an overview of microservice security using Spring Security 5.1, OAuth 2.0, and OpenID Connect. It defines OAuth 2.0 and its authorization framework, describing how applications can be authorized to access user data. It outlines the authorization code grant flow and other grant types, including how applications register and use client IDs and secrets. JSON Web Tokens are discussed as an access token format. OpenID Connect is described as extending OAuth 2.0 to provide authentication via ID tokens. Key components like access tokens, refresh tokens, and the client credentials flow are also summarized.
Oauth2 and OWSM OAuth2 support



Oauth2 and OWSM OAuth2 supportGaurav Sharma The document discusses OAuth 2.0 and how it addresses issues with traditional approaches to authorizing third party access to user accounts and resources. It provides an overview of OAuth 2.0 concepts like authorization grants, access tokens, refresh tokens, and the roles of the client, resource owner, authorization server and resource server. It then describes the authorization code grant flow and client credentials flow in more detail through examples. The goal is to explain how OAuth 2.0 works and how it can be used to securely authorize access to resources while avoiding the risks of directly sharing user credentials.
Oauth 2.0 Introduction and Flows with MuleSoft



Oauth 2.0 Introduction and Flows with MuleSoftshyamraj55 Learn about the basics of OAuth 2.0 and the different OAuth flows in this introductory video. Understand how OAuth works and the various authorization mechanisms involved.
OAuth 2.0 - The fundamentals, the good , the bad, technical primer and commo...



OAuth 2.0 - The fundamentals, the good , the bad, technical primer and commo...Good Dog Labs, Inc. OAuth 2.0 seems to be a comprehensive framework for authorizing access to protected resources, but is it really? We can argue that OpenID Connect will make it enterprise ready, but level of adoption in the enterprise is yet to be seen. This primer describes the framework fundamentals,the good, the bad, and common OAuth 2.0 flows.
OAuth 2.0 and OpenID Connect



OAuth 2.0 and OpenID ConnectJacob Combs An overview of OAuth 2.0 and OpenID Connect. How they are related and how they fit into the Neo Security Stack.
Deep Dive into OAuth for Connected Apps



Deep Dive into OAuth for Connected AppsSalesforce Developers The document discusses OAuth and its implementation for connected apps. It describes OAuth as a delegation protocol for conveying authorization across web apps and APIs. It then outlines the web server flow and user agent flow, including the different token types used. It demonstrates getting an access token via the web server flow and using it to query data. Finally, it provides information on refreshing access tokens before expired.
Spring Security



Spring SecurityKnoldus Inc. Spring Security is a framework that provides authentication and authorization to create secure Java applications. It targets authentication and authorization of web requests, methods, and access to domains. OAuth 2.0 is an authorization framework that allows clients limited access to protected resources owned by a resource owner. It has four main roles: resource owner, client, authorization server, and resource server. The authorization server issues access tokens to clients which can then be used to request protected resources from the resource server on behalf of the authenticated resource owner. OAuth 2.0 offers advantages like flexibility, ability to share data without releasing personal information, use of tokenization for limited access, and ease of implementation with strong authentication.
.NET Core, ASP.NET Core Course, Session 19



.NET Core, ASP.NET Core Course, Session 19Amin Mesbahi The document provides an introduction to ASP.NET Core Identity and OAuth 2.0 authorization. It discusses Identity topics like user registration, sign in, the database schema, and dependencies. It also covers OAuth concepts like roles, tokens, registering as a client, authorization flows, and security vulnerabilities. The document is an introduction and overview of key Identity and OAuth concepts for a .NET Core training course.
1000 ways to die in mobile oauth



1000 ways to die in mobile oauthPriyanka Aash "OAuth has become a highly influential protocol due to its swift and wide adoption in the industry. The initial objective of the protocol was specific: it serves the authorization needs for websites. However, the protocol has been significantly repurposed and re-targeted over the years: (1) all major identity providers, e.g., Facebook, Google and Microsoft, have re-purposed OAuth for user authentication; (2) developers have re-targeted OAuth to the mobile platforms, in addition to the traditional web platform. Therefore, we believe that it is necessary and timely to conduct an in-depth study to demystify OAuth for mobile application developers.
Our work consists of two pillars: (1) an in-house study of the OAuth protocol documentation that aims to identify what might be ambiguous or unspecified for mobile developers; (2) a field-study of over 600 popular mobile applications that highlights how well developers fulfill the authentication and authorization goals in practice. The result is really worrisome: among the 149 applications that use OAuth, 89 of them (59.7%) were incorrectly implemented and thus vulnerable. In the paper, we pinpoint the key portions in each OAuth protocol flow that are security critical, but are confusing or unspecified for mobile application developers. We then show several representative cases to concretely explain how real implementations fell into these pitfalls. Our findings have been communicated to vendors of the vulnerable applications. Most vendors positively confirmed the issues, and some have applied fixes. We summarize lessons learned from the study, hoping to provoke further thoughts about clear guidelines for OAuth usage in mobile applications"
(Source: Black Hat USA 2016, Las Vegas)
OAuth2 Implementation Presentation (Java)



OAuth2 Implementation Presentation (Java)Knoldus Inc. The OAuth 2.0 authorization framework is a protocol that allows a user to grant a third-party web site or application access to the user's protected resources, without necessarily revealing their long-term credentials or even their identity. It is commonly used in scenarios such as user authentication in web and mobile applications and enables a more secure and user-friendly authorization process.
OAuth 2.0 for Web and Native (Mobile) App Developers



OAuth 2.0 for Web and Native (Mobile) App DevelopersPrabath Siriwardena 1. The evolution of identity delegation protocols.
2. Understanding OAuth 2.0 fundamentals
3. OAuth 2.0 profiles and OpenID Connect
4. Securing Single Page Applications (SPAs) with OAuth 2.0
5. OAuth 2.0 for Native Apps
6. OAuth 2.0 threat landscapes
7. User Managed Access (UMA)
Introduction to OAuth2



Introduction to OAuth2Kumaresh Chandra Baruri OAuth2 is an authorization frame to perform app authorization to access resources.
The process is as below-
1. App sends authorization request.
2. API service provides auth code.
3. Application sends auth code with API gateway to issue access token.
4. Access token is used to access restricted resources.
5. Refresh token is used to renew access token.
CIS13: Introduction to OAuth 2.0



CIS13: Introduction to OAuth 2.0CloudIDSummit This document provides an overview of OAuth 2.0 and how it addresses issues with the previous "password anti-pattern" approach to API authentication. It describes the key actors in OAuth - clients, authorization servers, and resource servers. It also summarizes the different flows for obtaining access tokens, common use cases for OAuth, and how OAuth compares to SAML for SSO and authorization.
Intro to OAuth2 and OpenID Connect



Intro to OAuth2 and OpenID ConnectLiamWadman An introduction to OAuth2 and OpenID Connect intended for a technical audience. This covers terminology, core concepts, and all the core grants/flows for OAuth2 and OpenID Connect
Identity for IoT: An Authentication Framework for the IoT



Identity for IoT: An Authentication Framework for the IoTAllSeen Alliance John Bradley, Ping Identity, gave this presentation at the AllSeen Alliance's Partner Programme at Mobile World Congress 2015.
About Ping Identity: Ping Identity provides next-generation identity security solutions. With more than 1,200 enterprise customers worldwide, including half of the Fortune 100, Ping Identity delivers professional-grade identity security solutions that meet the needs of organizations managing workforce, customer, and partner identities. Identity at Internet scale is a concept that will be required as the industry builds services that encompass billions of connected devices and identities.
API Security with OAuth2.0.



API Security with OAuth2.0.Kellton Tech Solutions Ltd Traditional security models no longer suffice in the new digital and API driven economy. APIs expose corporate data in very deliberate and thoughtful ways, but, as with any technology that involves enterprise data, security should always be a prime concern. How do you keep your customers' digital experiences as secure as your backend data and services?
OAuth is an API authorization protocol that enables apps to access information on behalf of users without requiring them to divulge their usernames and passwords.
OAuth



OAuthTom Elrod OAuth is an open standard for authorization that allows users to share private resources stored on one server with another server. It provides a process for users to authorize third-party access to their server resources without sharing credentials. OAuth has gone through several versions to address security issues and limitations of previous versions. OAuth involves resource owners, clients, and an authorization server, and defines common flows for authorization like authorization code flow and refresh token flow.
Microsoft Graph API Delegated Permissions



Microsoft Graph API Delegated PermissionsStefan Weber Slidedeck presented during a webinar i held on13th December 2023 about how to consume Microsoft Graph API using user level permissions.
Webinar Recording https://youtu.be/2cSsg5ws1H4
Stateless Auth using OAUTH2 & JWT



Stateless Auth using OAUTH2 & JWTMobiliya 1. Intro - Auth - Authentication & Authorization & SSO
2. OAuth2 in Depth
3. Where does JWT fit in ?
4. How to do stateless Authorization using OAUTH2 & JWT ?
5. Some Sample Code ? How easy is it to implement ?
Ladies Be Architects - Study Group III: OAuth 2.0 (Ep 1)



Ladies Be Architects - Study Group III: OAuth 2.0 (Ep 1)gemziebeth Join us as we look into OAuth 2.0 to help us study for the Identity and Access Management Designer certification exam. Episode 1 covers the principles of OAuth 2.0
Ad
More from WSO2 (20)
Platformless Modernization with Choreo.pdf



Platformless Modernization with Choreo.pdfWSO2 In this slide deck we explore how Choreo - an AI-native internal developer platform as a service - accelerates modernization with best practices. https://wso2.com/choreo
Application Modernization with Choreo for the BFSI Sector



Application Modernization with Choreo for the BFSI SectorWSO2 In this slide deck, we explore the application modernization challenges in the BFSI industry and how Choreo - an AI-native internal developer platform as a service - can help in the modernization journey.
Choreo - The AI-Native Internal Developer Platform as a Service: Overview



Choreo - The AI-Native Internal Developer Platform as a Service: OverviewWSO2 This deck takes you through the need for an internal developer platform and introduces Choreo which provides platform and software engineers with an as a service solution to deliver applications faster and at scale.
[Roundtable] Choreo - The AI-Native Internal Developer Platform as a Service![[Roundtable] Choreo - The AI-Native Internal Developer Platform as a Service](https://cdn.slidesharecdn.com/ss_thumbnails/choreo-deck-250328074645-511dded7-thumbnail.jpg?width=560&fit=bounds)
![[Roundtable] Choreo - The AI-Native Internal Developer Platform as a Service](https://cdn.slidesharecdn.com/ss_thumbnails/choreo-deck-250328074645-511dded7-thumbnail.jpg?width=560&fit=bounds)
![[Roundtable] Choreo - The AI-Native Internal Developer Platform as a Service](https://cdn.slidesharecdn.com/ss_thumbnails/choreo-deck-250328074645-511dded7-thumbnail.jpg?width=560&fit=bounds)
![[Roundtable] Choreo - The AI-Native Internal Developer Platform as a Service](https://cdn.slidesharecdn.com/ss_thumbnails/choreo-deck-250328074645-511dded7-thumbnail.jpg?width=560&fit=bounds)
[Roundtable] Choreo - The AI-Native Internal Developer Platform as a ServiceWSO2 This deck explores Choreo - the AI-native internal developer platform as a service.
WSO2Con 2025 - Building AI Applications in the Enterprise (Part 1)



WSO2Con 2025 - Building AI Applications in the Enterprise (Part 1)WSO2 Building AI applications for the enterprise requires understanding key architectural patterns that enable powerful, scalable, and intelligent solutions. This session explores the core approaches to building AI-driven applications, including Generative AI, Retrieval-Augmented Generation (RAG), and AI Agents.
We’ll dive into how to build and integrate AI apps, discover and connect them with enterprise tools, and manage authentication and authorization securely. Additionally, we’ll cover best practices for deploying AI-powered applications and how an AI Gateway can help monitor, secure, and optimize interactions between AI models, agents, and enterprise systems.
WSO2Con 2025 - Building Secure Business Customer and Partner Experience (B2B)...



WSO2Con 2025 - Building Secure Business Customer and Partner Experience (B2B)...WSO2 Building modern B2B applications requires addressing complex identity and access management needs, from seamless onboarding to managing organizational hierarchies and user relationships. This session dives into the challenges of developing B2B apps and showcases how WSO2 B2B CIAM solutions can simplify and enhance these aspects.
We’ll explore key concepts such as organizational modeling, hierarchical structures, and organization onboarding strategies. You’ll learn how to design secure user login experiences, implement "Bring Your Own Identity Provider" (BYO IdP) functionality, and connect users seamlessly to their organizations.
The session will also provide a preview of WSO2 IAM roadmap for B2B applications, highlighting upcoming features designed to address evolving business challenges.
WSO2Con 2025 - Building Secure Customer Experience Apps



WSO2Con 2025 - Building Secure Customer Experience AppsWSO2 Creating exceptional customer experiences is essential in today’s digital-first world. This lab session explores building secure, personalized, and innovative customer experience apps using the WSO2 CIAM suite. We will dive into hands-on techniques for building customer experience apps using the Asgardeo SDKs, designing secure user sign-up, and login experiences using AI-driven features like Login Flow AI and Branding AI. We’ll also demonstrate how to apply MFA, passwordless, adaptive authentication, and protecting high-value APIs.
This session will include a sneak peek at the WSO2 IAM roadmap and how its evolving capabilities can empower you to stay ahead in the competitive landscape.
WSO2Con 2025 - AI-Driven API Design, Development, and Consumption with Enhanc...



WSO2Con 2025 - AI-Driven API Design, Development, and Consumption with Enhanc...WSO2 Most business operations, be it selling a product online, launching a marketing campaign, purchasing equipment, or hiring a person, may involve multiple business units, systems and external parties. Combining all such relevant entities into a single automated flow is crucial for smooth and efficient operations. Due to the large number of systems used in enterprises and the availability of many business operations, a typical organization would have to put an enormous effort into automating business operations. Therefore, simplifying the integration experience is a critical requirement for any organization. In this context, this session examines the use of the WSO2 Integrator for simplifying development of integration flows, by utilizing features such as low-code and pro-code development, AI-assisted development, data mapping, and built-in connectors.
WSO2Con 2025 - AI-Driven API Design, Development, and Consumption with Enhanc...



WSO2Con 2025 - AI-Driven API Design, Development, and Consumption with Enhanc...WSO2 As APIs continue to evolve, AI is transforming how they are designed, consumed, and governed. By integrating AI-driven capabilities, organizations can streamline workflows, enhance automation, and ensure compliance—making API management more intelligent, efficient, and adaptive.
This session explores how AI can be applied across the API lifecycle, from intelligent design recommendations to optimizing consumption patterns and enforcing governance policies. Through real-world examples, we will demonstrate how AI enhances API interactions, automates compliance, strengthens security, and integrates seamlessly with development workflows.
By the end of this session, attendees will gain valuable insights into leveraging AI for API management, balancing automation with governance, and building smarter, more secure API ecosystems. Whether you're an API developer, architect, or platform engineer, this session will provide practical strategies for the future of AI-enhanced API management.
WSO2Con 2025 - Unified Management of Ingress and Egress Across Multiple API G...



WSO2Con 2025 - Unified Management of Ingress and Egress Across Multiple API G...WSO2 In today’s multi-cloud, multi-gateway world, organizations struggle to apply consistent governance across all their APIs—both ingress APIs exposed to consumers and egress APIs calling external services like AI platforms and SaaS applications. This hands-on lab shows you how to solve that with a unified control plane that manages API gateways across environments, including Kubernetes, universal, immutable, and federated gateways (AWS, Solace).
You’ll see how a pluggable agent framework makes it easy to onboard any gateway supporting Kubernetes Gateway API, and how to enforce policies, observability, and analytics consistently across all your traffic—inbound and outbound. The lab will also dive deep into AI egress governance, showcasing features like model routing, prompt templating, semantic caching, and AI guardrails when connecting to OpenAI, Azure OpenAI, and Mistral.
If you’re looking for a future-proof way to manage all your APIs across diverse platforms, environments, and use cases—this is the session for you.
WSO2Con 2025 - How an Internal Developer Platform Lets Developers Focus on Code



WSO2Con 2025 - How an Internal Developer Platform Lets Developers Focus on CodeWSO2 Cloud-native development often involves setting up infrastructure, managing security, and integrating services—tasks that take time away from coding. An internal developer platform (IDP) streamlines these complexities, enabling developers to focus on building business logic.
This lab demonstrates how an IDP supports a hybrid development approach, where developers run some components locally while consuming cloud services seamlessly. Instead of manually configuring databases, authentication, or API gateways, they leverage platform capabilities for rapid iteration.
We’ll walk through a real-world scenario where a developer:
Onboards quickly with an architect-defined application structure.
Develops in a hybrid environment, consuming cloud APIs, databases, and AI services while iterating locally.
Uses Choreo-managed authentication without dealing with OAuth2 intricacies.
Discovers and reuses microservices and APIs instead of rebuilding them.
Debugs efficiently without deploying all dependencies locally.
Ensures security and compliance automatically, catching vulnerabilities early.
By the end, you’ll see how an IDP accelerates onboarding, enhances security, and simplifies cloud-native development—so developers can focus on building great applications instead of managing infrastructure.
WSO2Con 2025 - Architecting Cloud-Native Applications



WSO2Con 2025 - Architecting Cloud-Native ApplicationsWSO2 As enterprises modernise their technology stacks, designing platform-agnostic, scalable, and well-governed cloud-native architectures is essential for long-term success. This lab session will explore how to apply the platformless concept to build cloud-native applications that offer flexibility, portability, and resilience across diverse cloud environments.
Through guided discussions and real-world insights, we will examine key architectural patterns, including microservices, API gateways, and Kubernetes orchestration, while addressing critical aspects such as scalability, governance, and operational efficiency.
Join us to exchange ideas, refine best practices, and explore strategies for architecting cloud-native applications that are future-proof, scalable, and effectively governed.
Mastering Intelligent Digital Experiences with Platformless Modernization



Mastering Intelligent Digital Experiences with Platformless ModernizationWSO2 In today’s fast-evolving technological landscape, modernization isn’t just about upgrading systems—it’s about rethinking how organizations create value by delivering exceptional digital experiences. Platformless Modernization takes a revolutionary approach, focusing on outcomes rather than infrastructure, enabling businesses to remain agile, scalable, and competitive.
Tailored for IT leaders who are driving strategy, this slide deck explores how Platformless Modernization leverages cloud-native and AI-driven practices to simplify complexity, enhance adaptability, and accelerate value delivery. Through a blend of technical insights and strategic frameworks, you’ll gain actionable tools and methods to align modernization efforts with your organization’s business goals.
Key Takeaways:
Strategic Approaches: Understand how Platformless Modernization aligns IT strategy with business outcomes, ensuring every initiative drives measurable value.
Simplified Complexity: Learn how platformless approaches eliminate the overhead of managing infrastructure while enabling rapid solution delivery.
Cloud-Native and AI Practices: Explore patterns and tools that leverage cloud-native architectures and AI-driven intelligence to enhance scalability and adaptability.
Future-Proofing IT Investments: Discover how to build architectures designed to evolve with changing market dynamics and technology trends.
Agile Innovation: Gain insights into creating a culture and processes that foster continuous improvement and innovation in IT delivery.
Accelerate Enterprise Software Engineering with Platformless



Accelerate Enterprise Software Engineering with PlatformlessWSO2 Key takeaways:
Challenges of building platforms and the benefits of platformless.
Key principles of platformless, including API-first, cloud-native middleware, platform engineering, and developer experience.
How Choreo enables the platformless experience.
How key concepts like application architecture, domain-driven design, zero trust, and cell-based architecture are inherently a part of Choreo.
Demo of an end-to-end app built and deployed on Choreo.
WSO2Con2024 - WSO2's IAM Vision: Identity-Led Digital Transformation



WSO2Con2024 - WSO2's IAM Vision: Identity-Led Digital TransformationWSO2 WSO2Con2024 - WSO2's IAM Vision: Identity-Led Digital Transformation
architecting-ai-in-the-enterprise-apis-and-applications.pdf



architecting-ai-in-the-enterprise-apis-and-applications.pdfWSO2 Architecting AI in the Enterprise: APIs and Applications
Driving Innovation: Scania's API Revolution with WSO2



Driving Innovation: Scania's API Revolution with WSO2WSO2 Driving Innovation: Scania's API Revolution with WSO2
Less Is More: Utilizing Ballerina to Architect a Cloud Data Platform



Less Is More: Utilizing Ballerina to Architect a Cloud Data PlatformWSO2 At its core, the challenge of managing Human Resources data is an integration challenge: estimates range from 2-3 HR systems in use at a typical SMB, up to a few dozen systems implemented amongst enterprise HR departments, and these systems seldom integrate seamlessly between themselves. Providing a multi-tenant, cloud-native solution to integrate these hundreds of HR-related systems, normalize their disparate data models and then render that consolidated information for stakeholder decision making has been a substantial undertaking, but one significantly eased by leveraging Ballerina. In this session, we’ll cover:
The overall software architecture for VHR’s Cloud Data Platform
Critical decision points leading to adoption of Ballerina for the CDP
Ballerina’s role in multiple evolutionary steps to the current architecture
Roadmap for the CDP architecture and plans for Ballerina
WSO2’s partnership in bringing continual success for the CD
Modernizing Legacy Systems Using Ballerina



Modernizing Legacy Systems Using BallerinaWSO2 The integration landscape is changing rapidly with the introduction of technologies like GraphQL, gRPC, stream processing, iPaaS, and platformless. However, not all existing applications and industries can keep up with these new technologies. Certain industries, like manufacturing, logistics, and finance, still rely on well-established EDI-based message formats. Some applications use XML or CSV with file-based communications, while others have strict on premises deployment requirements. This talk focuses on how Ballerina's built-in integration capabilities can bridge the gap between "old" and "new" technologies, modernizing enterprise applications without disrupting business operations.
WSO2CON 2024 - Unlocking the Identity: Embracing CIAM 2.0 for a Competitive A...



WSO2CON 2024 - Unlocking the Identity: Embracing CIAM 2.0 for a Competitive A...WSO2 WSO2CON 2024 - Unlocking the Identity: Embracing CIAM 2.0 for a Competitive Advantage
Recently uploaded (20)
TrsLabs - Fintech Product & Business Consulting



TrsLabs - Fintech Product & Business ConsultingTrs Labs Hybrid Growth Mandate Model with TrsLabs
Strategic Investments, Inorganic Growth, Business Model Pivoting are critical activities that business don't do/change everyday. In cases like this, it may benefit your business to choose a temporary external consultant.
An unbiased plan driven by clearcut deliverables, market dynamics and without the influence of your internal office equations empower business leaders to make right choices.
Getting things done within a budget within a timeframe is key to Growing Business - No matter whether you are a start-up or a big company
Talk to us & Unlock the competitive advantage
Vaibhav Gupta BAML: AI work flows without Hallucinations



Vaibhav Gupta BAML: AI work flows without Hallucinationsjohn409870 Shipping Agents
Vaibhav Gupta
Cofounder @ Boundary
in/vaigup
boundaryml/baml
Imagine if every API call you made
failed only 5% of the time
boundaryml/baml
Imagine if every LLM call you made
failed only 5% of the time
boundaryml/baml
Imagine if every LLM call you made
failed only 5% of the time
boundaryml/baml
Fault tolerant systems are hard
but now everything must be
fault tolerant
boundaryml/baml
We need to change how we
think about these systems
Aaron Villalpando
Cofounder @ Boundary
Boundary
Combinator
boundaryml/baml
We used to write websites like this:
boundaryml/baml
But now we do this:
boundaryml/baml
Problems web dev had:
boundaryml/baml
Problems web dev had:
Strings. Strings everywhere.
boundaryml/baml
Problems web dev had:
Strings. Strings everywhere.
State management was impossible.
boundaryml/baml
Problems web dev had:
Strings. Strings everywhere.
State management was impossible.
Dynamic components? forget about it.
boundaryml/baml
Problems web dev had:
Strings. Strings everywhere.
State management was impossible.
Dynamic components? forget about it.
Reuse components? Good luck.
boundaryml/baml
Problems web dev had:
Strings. Strings everywhere.
State management was impossible.
Dynamic components? forget about it.
Reuse components? Good luck.
Iteration loops took minutes.
boundaryml/baml
Problems web dev had:
Strings. Strings everywhere.
State management was impossible.
Dynamic components? forget about it.
Reuse components? Good luck.
Iteration loops took minutes.
Low engineering rigor
boundaryml/baml
React added engineering rigor
boundaryml/baml
The syntax we use changes how we
think about problems
boundaryml/baml
We used to write agents like this:
boundaryml/baml
Problems agents have:
boundaryml/baml
Problems agents have:
Strings. Strings everywhere.
Context management is impossible.
Changing one thing breaks another.
New models come out all the time.
Iteration loops take minutes.
boundaryml/baml
Problems agents have:
Strings. Strings everywhere.
Context management is impossible.
Changing one thing breaks another.
New models come out all the time.
Iteration loops take minutes.
Low engineering rigor
boundaryml/baml
Agents need
the expressiveness of English,
but the structure of code
F*** You, Show Me The Prompt.
boundaryml/baml
<show don’t tell>
Less prompting +
More engineering
=
Reliability +
Maintainability
BAML
Sam
Greg Antonio
Chris
turned down
openai to join
ex-founder, one
of the earliest
BAML users
MIT PhD
20+ years in
compilers
made his own
database, 400k+
youtube views
Vaibhav Gupta
in/vaigup
[email protected]
boundaryml/baml
Thank you!
Technology Trends in 2025: AI and Big Data Analytics



Technology Trends in 2025: AI and Big Data AnalyticsInData Labs At InData Labs, we have been keeping an ear to the ground, looking out for AI-enabled digital transformation trends coming our way in 2025. Our report will provide a look into the technology landscape of the future, including:
-Artificial Intelligence Market Overview
-Strategies for AI Adoption in 2025
-Anticipated drivers of AI adoption and transformative technologies
-Benefits of AI and Big data for your business
-Tips on how to prepare your business for innovation
-AI and data privacy: Strategies for securing data privacy in AI models, etc.
Download your free copy nowand implement the key findings to improve your business.
Transcript: #StandardsGoals for 2025: Standards & certification roundup - Tec...



Transcript: #StandardsGoals for 2025: Standards & certification roundup - Tec...BookNet Canada Book industry standards are evolving rapidly. In the first part of this session, we’ll share an overview of key developments from 2024 and the early months of 2025. Then, BookNet’s resident standards expert, Tom Richardson, and CEO, Lauren Stewart, have a forward-looking conversation about what’s next.
Link to recording, presentation slides, and accompanying resource: https://bnctechforum.ca/sessions/standardsgoals-for-2025-standards-certification-roundup/
Presented by BookNet Canada on May 6, 2025 with support from the Department of Canadian Heritage.
Rusty Waters: Elevating Lakehouses Beyond Spark



Rusty Waters: Elevating Lakehouses Beyond Sparkcarlyakerly1 Spark is a powerhouse for large datasets, but when it comes to smaller data workloads, its overhead can sometimes slow things down. What if you could achieve high performance and efficiency without the need for Spark?
At S&P Global Commodity Insights, having a complete view of global energy and commodities markets enables customers to make data-driven decisions with confidence and create long-term, sustainable value. 🌍
Explore delta-rs + CDC and how these open-source innovations power lightweight, high-performance data applications beyond Spark! 🚀
UiPath Community Berlin: Orchestrator API, Swagger, and Test Manager API



UiPath Community Berlin: Orchestrator API, Swagger, and Test Manager APIUiPathCommunity Join this UiPath Community Berlin meetup to explore the Orchestrator API, Swagger interface, and the Test Manager API. Learn how to leverage these tools to streamline automation, enhance testing, and integrate more efficiently with UiPath. Perfect for developers, testers, and automation enthusiasts!
📕 Agenda
Welcome & Introductions
Orchestrator API Overview
Exploring the Swagger Interface
Test Manager API Highlights
Streamlining Automation & Testing with APIs (Demo)
Q&A and Open Discussion
Perfect for developers, testers, and automation enthusiasts!
👉 Join our UiPath Community Berlin chapter: https://community.uipath.com/berlin/
This session streamed live on April 29, 2025, 18:00 CET.
Check out all our upcoming UiPath Community sessions at https://community.uipath.com/events/.
Role of Data Annotation Services in AI-Powered Manufacturing



Role of Data Annotation Services in AI-Powered ManufacturingAndrew Leo From predictive maintenance to robotic automation, AI is driving the future of manufacturing. But without high-quality annotated data, even the smartest models fall short.
Discover how data annotation services are powering accuracy, safety, and efficiency in AI-driven manufacturing systems.
Precision in data labeling = Precision on the production floor.
#StandardsGoals for 2025: Standards & certification roundup - Tech Forum 2025



#StandardsGoals for 2025: Standards & certification roundup - Tech Forum 2025BookNet Canada Book industry standards are evolving rapidly. In the first part of this session, we’ll share an overview of key developments from 2024 and the early months of 2025. Then, BookNet’s resident standards expert, Tom Richardson, and CEO, Lauren Stewart, have a forward-looking conversation about what’s next.
Link to recording, transcript, and accompanying resource: https://bnctechforum.ca/sessions/standardsgoals-for-2025-standards-certification-roundup/
Presented by BookNet Canada on May 6, 2025 with support from the Department of Canadian Heritage.
The Evolution of Meme Coins A New Era for Digital Currency ppt.pdf



The Evolution of Meme Coins A New Era for Digital Currency ppt.pdfAbi john Analyze the growth of meme coins from mere online jokes to potential assets in the digital economy. Explore the community, culture, and utility as they elevate themselves to a new era in cryptocurrency.
Into The Box Conference Keynote Day 1 (ITB2025)



Into The Box Conference Keynote Day 1 (ITB2025)Ortus Solutions, Corp This is the keynote of the Into the Box conference, highlighting the release of the BoxLang JVM language, its key enhancements, and its vision for the future.
Semantic Cultivators : The Critical Future Role to Enable AI



Semantic Cultivators : The Critical Future Role to Enable AIartmondano By 2026, AI agents will consume 10x more enterprise data than humans, but with none of the contextual understanding that prevents catastrophic misinterpretations.
Dev Dives: Automate and orchestrate your processes with UiPath Maestro



Dev Dives: Automate and orchestrate your processes with UiPath MaestroUiPathCommunity This session is designed to equip developers with the skills needed to build mission-critical, end-to-end processes that seamlessly orchestrate agents, people, and robots.
📕 Here's what you can expect:
- Modeling: Build end-to-end processes using BPMN.
- Implementing: Integrate agentic tasks, RPA, APIs, and advanced decisioning into processes.
- Operating: Control process instances with rewind, replay, pause, and stop functions.
- Monitoring: Use dashboards and embedded analytics for real-time insights into process instances.
This webinar is a must-attend for developers looking to enhance their agentic automation skills and orchestrate robust, mission-critical processes.
👨🏫 Speaker:
Andrei Vintila, Principal Product Manager @UiPath
This session streamed live on April 29, 2025, 16:00 CET.
Check out all our upcoming Dev Dives sessions at https://community.uipath.com/dev-dives-automation-developer-2025/.
AI and Data Privacy in 2025: Global Trends



AI and Data Privacy in 2025: Global TrendsInData Labs In this infographic, we explore how businesses can implement effective governance frameworks to address AI data privacy. Understanding it is crucial for developing effective strategies that ensure compliance, safeguard customer trust, and leverage AI responsibly. Equip yourself with insights that can drive informed decision-making and position your organization for success in the future of data privacy.
This infographic contains:
-AI and data privacy: Key findings
-Statistics on AI data privacy in the today’s world
-Tips on how to overcome data privacy challenges
-Benefits of AI data security investments.
Keep up-to-date on how AI is reshaping privacy standards and what this entails for both individuals and organizations.
Massive Power Outage Hits Spain, Portugal, and France: Causes, Impact, and On...



Massive Power Outage Hits Spain, Portugal, and France: Causes, Impact, and On...Aqusag Technologies In late April 2025, a significant portion of Europe, particularly Spain, Portugal, and parts of southern France, experienced widespread, rolling power outages that continue to affect millions of residents, businesses, and infrastructure systems.
Procurement Insights Cost To Value Guide.pptx



Procurement Insights Cost To Value Guide.pptxJon Hansen Procurement Insights integrated Historic Procurement Industry Archives, serves as a powerful complement — not a competitor — to other procurement industry firms. It fills critical gaps in depth, agility, and contextual insight that most traditional analyst and association models overlook.
Learn more about this value- driven proprietary service offering here.
Cybersecurity Identity and Access Solutions using Azure AD



Cybersecurity Identity and Access Solutions using Azure ADVICTOR MAESTRE RAMIREZ Cybersecurity Identity and Access Solutions using Azure AD
Manifest Pre-Seed Update | A Humanoid OEM Deeptech In France



Manifest Pre-Seed Update | A Humanoid OEM Deeptech In Francechb3 The latest updates on Manifest's pre-seed stage progress.
Special Meetup Edition - TDX Bengaluru Meetup #52.pptx



Special Meetup Edition - TDX Bengaluru Meetup #52.pptxshyamraj55 We’re bringing the TDX energy to our community with 2 power-packed sessions:
🛠️ Workshop: MuleSoft for Agentforce
Explore the new version of our hands-on workshop featuring the latest Topic Center and API Catalog updates.
📄 Talk: Power Up Document Processing
Dive into smart automation with MuleSoft IDP, NLP, and Einstein AI for intelligent document workflows.
Extended Security with WSO2 API Management Platform
- 1. WSO2 Uvindra Dias Jayasinha Extended Security with WSO2 API Management Platform 30th April, 2015
- 2. ** About the Presenter Uvindra joined WSO2 in November 2013. He is a Senior Software Engineer in the WSO2 API Manager Team. He has a background in Telecom Billing Systems and Financial Trading systems, including High Performance Software development
- 3. ** Agenda ● Best practices when requesting OAuth 2.0 Access Tokens ● Adding SAML based Single Sign On (SSO) capabilities to API management and leveraging SAML2 Bearer Tokens to request OAuth 2.0 Access Tokens ● Federated identity: How to use a third-party identity provider with API Manager ● Enforcing fine-grained entitlement policies at the API management layer ● Accessing API user's attributes to make decisions
- 4. ** APIs and Security Exposing Services as APIs means we need to address how those APIs are going to be secured ● Primarily protecting APIs via API Access Tokens ● But also so much more than that…... ❏ Forced to deal with different kinds of users and applications ❏ One size does not fit all when it comes to security
- 5. ** OAuth 2.0 - The Cornerstone OAuth definition from the OAuth 2.0 IETF specification - "The OAuth 2.0 authorization framework enables a third-party application to obtain limited access to an HTTP service, either on behalf of a resource owner by orchestrating an approval interaction between the resource owner and the HTTP service, or by allowing the third-party application to obtain access on its own behalf." [1] [1] http://tools.ietf.org/html/rfc6749
- 6. ** OAuth 2.0 - Grant Types Depending on the trustworthiness of the application that is trying to access the API, oauth provides different methods that can be used for granting access ● Authorization Code ● Password(Resource Owner Credentials) ● Client Credentials ● Implicit
- 7. ** Understanding the actors involved Resource owner The Person who owns the data or has rights to the data that will be exposed by the Service via an API Resource Server The server that hosts the actual Service/API that exposes the data Application Considered as the ‘client’ in OAuth circles. The one requesting access to the API Auth Server Grants access to the Application after authenticating it with the Resource Owner
- 8. ** Key OAuth concepts Client ID A unique string representing an Application registered with the Auth Server Client Secret A secret password that is used by the Auth Server to authenticate if the Application is an authorized Application Access Token A key provided by the Auth Server to the Application which allows access to a given API for a limited amount of time. After the time expires the key will be considered invalid Refresh Token A secondary key that can be used by the Application to request a new Access Token from the Auth Server
- 9. ** Authorization Code Grant Type Category of Application - 3rd Party untrusted Locality of Application - Resides remotely from the Resource Owner ● Resource Owner gets involved initially to decide if the Auth Server should grant API access to the Application ● ‘Auth Code’ is returned by Auth Server to the Application which uses it to request Access + Refresh Tokens from the Auth Server ● The Application may store the Access + Refresh Tokens and reuse them to access the API, no longer needing intervention from the Resource Owner ● Considered the most secure grant type
- 10. ** Implicit Grant Type Category of Application - 3rd Party untrusted Locality of Application - Resides locally to the Resource Owner(eg: Web browser, Mobile device) ● A simplified version of the Authorization Code grant type with the elimination of the Auth Code issuing step ● Since Resource Owner is present in proximity to App there is nothing to be gained by issuing an Auth Code ● Once Resource Owner approves App, Auth Server provides Access Token directly to App ● Access Token validity periods should be relatively short, no Refresh Token is issued ● App should rely on the Resource Owner to get involved again to get a new Access Token
- 11. ** Password Grant Type Category of Application - 3rd Party trusted ● Since the App is trusted the Resource Owner is able to share their own username and password directly with the App ● By providing their credentials to the App, the Resource Owner is delegating authority to the App to authenticate itself with the Auth Server and get Access + Refresh Tokens
- 12. ** Client Credentials Grant Type Category of Application - Resource Owners App ● Since the App belongs to the Resource Owner there is no need to authenticate the App via the Resource Owners credentials or require that the Resource Owner get involved to help the Auth Server decide if access should be granted ● All that is required by the Auth Server is to identify if the App requesting the Access Token is in fact the Resource Owners App ● The App only needs to provide the Client ID and Client Secret to the Auth Server to get the Access Token
- 13. ** Single Sign On ● The WSO2 API Management platform can be configured to support SAML 2.0 based SSO ● Security Assertion Markup Language 2.0 - XML-based protocol that uses security tokens containing assertions to pass information about a principal (usually an end user) between a SAML authority, that is, an identity provider, and a SAML consumer, that is, a service provider ● SAML is a widely established means of identity federation in enterprises.
- 14. ** Advantage of SAML based SSO ● Provides convenience when working with multiple store/publisher web applications ● Reduces password fatigue ● Able to exchange the SAML token issued by the Identity Provider for an OAuth 2.0 access token, avoiding the need to explicitly be authenticated by an Auth 2.0 Auth Server. This is an advantage for enterprises that already have an existing SAML identity provider
- 15. ** Federated Identity ● Demo Scenario - Using Facebook as a Federated identity provider to act as a Auth Server to obtain a API Access Token
- 16. ** Fine-grained entitlement policies ● API Manager supports Auth 2.0 scopes to restrict access to API resources based on user roles ● But when more fine grained entitlement policies are required XACML policies can be used ● XACML stands for "eXtensible Access Control Markup Language", which defines a declarative access control policy language implemented in XML and a processing model describing how to evaluate access requests according to the rules defined in policies.
- 17. ** Accessing API users attributes to make decisions ● Its often useful for the API hosting service to make decisions based on information associated with the user who initiated the API invocation such as, ○ Username of end user ○ The organization the end user is associated with ○ The email of the end user ○ The gender of the end user
- 18. ** Passing Claims via JWT ● Claim - user attribute that is mapped to the underlying user store ● Claim dialect - A set of predefined claims ● API Manager can be configured to pass a Claim Dialect via a JSON Web Token[1] to the back end API along with the API invocation [1] http://openid.net/specs/draft-jones-json-web-token-07.html#anchor3
- 19. ** Resources ● [Article] OAuth2 Grant Types and Need For Implicit Grant for JavaScript and Mobile Applications http://wso2.com/library/articles/2014/12/article- oauth2-grant-types-and-need-for-implicit-grant-for-javascript-mobile-applications/ ● What is the purpose of the implicit grant authorization type in OAuth 2? http://stackoverflow.com/questions/7522831/what-is-the-purpose-of-the-implicit-grant-authorization-type-in-oauth-2 ● Enforcing fine grained entitlement policies With XACML http://xacmlinfo.org/2014/10/24/authorization-for-apis-with-xacml-and-oauth-2-0/
- 20. Contact us !




