FEGTS IP training - TCP/IP Introduction
- 1. TCP/IP Introduction 智匯亞洲有限公司 Commverge Solutions, Taiwan FEGTS IP Training 2010/11/5, Taipei
- 2. Course Objects Introduce modern network and TCP/IP fundament
- 3. Course Scope Major scope 網路傳輸基礎介紹 常見網路設備介紹﹙一﹚ IP 介紹 ICMP/TCP/UDP 介紹 常見應用程式介紹 常見網路設備介紹﹙二﹚
- 4. Course Content Some course slides content comes from: Internetworking With TCP/IP Volume 1: Principles, Protocols, and Architecture, 5th Edition Douglas E. Comer; Prentice Hall Complete slide source: http://www.cs.purdue.edu/homes/dec/vol1/vol1_presentation.pdf
- 5. Course Schedule Review Test 5:30pm ~ 6:00pm TCP/IP Application 4:00pm ~ 5:30pm Break Protocol – ICMP, TCP and UDP 2:00pm ~ 3:50pm Lunch Break IP Network Introduction 11:00am ~ 12:50pm Break Modern Network Introduction 9:00am ~ 10:50am Agenda Time
- 6. About the Trainer Kae Hsu﹙ 許至凱﹚ Commverge Solutions – Taiwan [email_address] http:// tw.linkedin.com/in/kaehsu
- 7. 網路傳輸基礎介紹 常見網路傳輸介質 網路傳輸類別 傳輸協定 常見網路障礙分類
- 8. 如何傳遞訊號 ? 在通訊環境裡,資料最後還是會被轉換成 0 與 1 進行傳送 使用電流進行訊號交換;例如 用高電位 ( 5V or 0V ) 表示” 1” 用低電位 ( 0V or -5V ) 表示” 0” 使用光波進行訊號交換;例如 用”亮”表示” 1” 用”暗”表示” 0”
- 9. 常見網路傳輸介質 銅線 無遮罩雙絞線﹙ Unshielded Twisted Pair ﹚ Category 3 16Mhz, 10Base-T Category 4 20Mhz, 10Base-T Category 5 100Mhz, 100Base-TX Category 5e “ Enhanced” Cat5, 1000Base-T Category 6 250Mhz, 1000Base-TX 接頭 RJ-45 8P8C
- 10. 常見網路傳輸介質 UTP 收 / 送方向討論 在 Ethernet 家族, UTP 使用四對絞線中其中二對進行傳輸 一對為送端﹙ TX﹚ 一對為收端﹙ RX﹚ 設備連接時,必需一邊 TX 與他邊 RX 對接 RJ45 8P8C 兩種接線定義: TIA/EIA-568A 、 TIA/EIA-568B UTP 兩端 RJ45 腳位皆為 568A 或 568B 時,稱” straight” UTP 一端 RJ45 腳位為 568A ,另一端為 568B 時,稱” cross-over” 設備腳位配置可分成兩類: Host 端﹙含路由器﹚ - MDI Hub/Switch 端 - MDIX 同類設備連接時需使用” cross-over” wire ;異類則使用” straight” 較新的網路設備已可支援 MDI/MDIX 自動切換
- 11. 光通訊的掘起 使用銅線為介質所面臨的瓶頸 線材重、耗能 容量小 有效傳輸距離短 易被外界環境干擾 容易被鯊魚咬壞 XD 傳輸方式從電變成光 質輕,耗能少 容量大 有效傳輸距離長 不易受外界環境干擾 無電磁波問題
- 12. 常見光傳輸元件 光纖 多模光纖( Multi-mode Fiber , MMF ) 光纖直徑: 50/125μm 、 62.5/125μm 使用於 850nm 波長 傳送距離短( ~500m ) 單模光纖( Single-mode Fiber , SMF ) 光纖直徑: 9/125μm 使用於 1310nm , 1550nm 波長 傳送距離長( 10km~80km ) 光纖接頭 FC 、 SC 、 LC etc…
- 13. 常見光傳輸元件 光放大器 在電傳輸世界,可直接放大電流增加傳輸距離 光具獨立性,難以直接增強既有光源功率 需先將光轉成電,再轉成光後傳送 EDFA ( Erbium-Doped Fiber Amplifier ; 摻鉺光纖放大器) 利用 Er 3+ 離子電子躍遷放出相同波長光源達到放大小效果 “ 光通訊中最偉大發明之一” 傳輸距離 MMF SR : 300m~500m SMF LR : ~10km ER : ~40km ZR : ~80km
- 14. 網路傳輸類別 專線( Leased Line ) T1/E1 T1 : 1.544Mbps E1 : 2.048Mbps T3/E3 T3 : 44.736Mbps E3 : 34.368Mbps STM-X/OC-Y CWDM 、 DWDM
- 15. SONET/SDH rates 3.3333% 1327.10 39813.12 STM-256 OC-768 STS-768 3.3334% 331.78 9953.28 STM-64 OC-192 STS-192 3.3332% 82.94 2488.32 STM-16 OC-48 STS-48 3.3340% 20.74 622.08 STM-4 OC-12 STS-12 3.3308% 5.18 155.52 STM-1 OC-3 STS-3 3.3372% 1.73 51.84 STM-0 OC-1 STS-1 % Overhead Bandwidth Optical Optical Electrical Data rate (Mbps) SDH SONET
- 16. Wavelength-division multiplexing (WDM) Multiplex different wavelengths light into a single optical fiber Each wavelength light could carry 1 independent traffic Coarse WDM 8 λ multiplexed in a single optical fiber Dense WDM 32, 64 even 128 λ multiplexed in a single optical fiber Transponder Convert payload light to specific λ
- 17. Unchannelized, Channelized Use DS3 as the example Unchannelized T3 All slots composed to a single channel Non-multiplexed 44.736Mbps Channelized T3 All slots are independent Could be multiplexed into multiple DS0 or DS1 43.008Mbps With more overhead and bit stuffing
- 18. Ethernet Family Ethernet 10Mbps 10Base2, 10Base5, 10BaseT Fast Ethernet 100Mbps 100Base-TX, 100Base-FX Gigabit Ethernet 1Gbps 1000Base-SX/LX/ZX, 1000Base-T/TX 10Gigabit Ethernet 10Gbps 10GBase-SR/LR/ER/ZR, 10GBase-CX4/T Future technology 40Gbps 、 100Gbps
- 19. 傳輸協定 Layer 1 protocol T1 、 E1 、 T3 、 E3 、 SONET/SDH Layer 2 protocol HDLC 、 PPP 、 Frame-Relay 、 ATM 、 MPLS Layer 3+ protocol IPv4 、 IPv6 ICMPv4 、 ICMPv6 Layer 4 protocol TCP 、 UDP
- 20. 傳輸協定 Frame Relay 多用於早期 VPN 網路佈建協定( 1980~1990 ) 已被 MPLS 取代 ATM Fixed cell size – 53 bytes 48bytes for payload 5 bytes for header Fixed cell size designed for fast switching Overhead: 9.43% Good QoS mechanism for voice and data
- 21. 傳輸協定 Multiprotocol Label Switching (MPLS) Packet switching enhancement MPLS-TE ( Traffic Engineering ) Faster switching then Hop-by-Hop IP lookup VPN enhancement MPLS-VPN More features than legacy VPN technology QoS enhancement MPLS-QoS
- 22. 常見網路障礙分類 斷線 原因 實體電路或光纖損壞 設備故障 影響 無法連線 瞬斷 原因 光傳輸路由或光傳輸設備卡板切換 <50ms ,“理論上”不會有感覺 ISP 路由器進行路由收斂( routing convergency )過程中丟棄無法處理之封包 影響 掉包( packet loss )
- 23. 常見網路障礙分類 壅塞 原因 網路流量大於電路容量 影響 掉包 速度變慢、或忽快忽慢 連線速度慢( LAG ) 原因 瞬斷,壅塞造成的掉包 TCP 可進行遺失封包的重傳,瞬斷對客戶的影響多半是瞬斷後感覺連線變慢,不致於連線失敗;但仍與上層 application 行為有關 海纜路由 正常情況下,美東 ~150ms ,香港 ~22ms (皆為來回) 連線目標 loading 過大
- 24. 常見網路設備介紹﹙一﹚ 專線 CSU/DSU ( Channel Service Unit/Data Service Unit ) 做為 T1/E1/T3/E3 電路連接使用 路由器未內含 T1/E1/T3/E3 CSU/DSU 時,常以 V.35 or HSSI 介面連接外部 CSU/DSU DSLAM ( DSL access multiplexer ) 將許多 ADSL/VDSL 電路收攏處理 ATU-R ( ADSL Terminal Unit – Remote ) 用戶端 ADSL 設備 與 DSLAM 最大距離: 5.5km ( 1.5Mbps ) VTU-R ( VDSL Terminal Unit – Remote ) 用戶端 VDSL 設備 與 DSLAM 最大距離: 1500m ( 13Mbps ) 常與 FTTB 併用
- 25. 常見網路設備介紹﹙一﹚ Ethernet 過時的設備 Repeater 具放大電路訊號功能達到延申 Ethernet 目的 Hub 具 repeater 功能 將許多電腦連接在一起 Bridge 具 repeater 功能 可辨識 Ethernet 封包,區隔出 collision domain 仍無法區隔 broadcast domain Switch 可視為具 bridge 功能的 hub
- 26. IP 介紹 ARP IP 位址 IP 路由 IP 封包介紹
- 27. ARP IP 位址是一抽象化資料,無法直接用在資料傳遞 資料傳遞需藉由實體網路完成 ARP - Address Resolution Protocol 連結 IP 位址與下層網路實體位置 常用場合: Ethernet 環境
- 28. Ethernet 硬體位址 Ethernet 位址長度: 48bits 表示法: 16 進位表示法 16 進位: 0 ~ F Example 00:10:DB:98:7C:12 000d.ed8a.0961 4e-21-0d-7c-62-4f
- 29. ARP 運作 建立 IP 位址與硬體位址對映 Machine A broadcasts ARP request with B’s IP address All machines on local net receive broadcast Machine B replies with its physical address Machine A adds B’s address information to its table Machine A delivers packet directly to B 將結果存放在 ARP table 中 Table 有 cache 功能,不需要每次都要查 一般 Time-out 時間: 20 分鐘
- 30. Illustration Of ARP Request And Reply Messages
- 31. 使用 ARP 察看網路狀況 檢視電腦 ARP table “ arp –a” Example
- 32. 使用 ARP 察看網路狀況 檢視設備 ARP table “ show arp” Example
- 33. Internet Protocol Internet Protocol Internet 封包交換標準 IP address Internet 定址資訊 長度 IPv4 : 32bits IPv6 : 128bits 在 Internet 上,每台電腦應該都有獨一無二的 IP address 例外: Network behind NAT/PT DNS anycast
- 34. IP 位址分配與發放 目前最高 IP 管理單位為 IANA Internet Assigned Numbers Authority IP address & BGP AS number 管理 Domain names 管理 Protocol name & port number 註冊 其它 IP 管理與發放單位 Regional Internet Registry AfriNIC 、 APNIC 、 ARIN 、 LACNIC 、 RIPE NCC National Internet Registry TWNIC Local Internet Registry Internet Service Provider
- 35. IP Address Division Address divided into two parts Prefix (network ID) identifies network to which host attaches Suffix (host ID) identifies host on that network 如何區分 prefix & suffix? By “netmask” 長度與 IP address 一樣, 32bits IPv6 無 netmask 觀念 Netmask 由一串連續的 1 開始,結束於一串連續的 0 連續的” 1” 所佔的位元數,即為 prefix 長度 Example IP address : 10000000 00001010 00000010 00000011 Netmask : 11111111 11111111 11111111 00000000 Result : 10000000 00001010 00000010 00000011 prefix suffix
- 36. IP address 表示法 為了讀寫與記憶方便, IP 位址多半以十進位表示 A 32-bit number in binary 10000000 00001010 00000010 00000011 The same 32-bit number expressed in dotted decimal notation 128 . 10 . 2 . 3
- 37. IP address 表示法 VLSM - Variable Length Subnet Mask 以 IP address/Netmask pair 表示 IP 位址 目前絕大部份電腦與網路設備在設定 IP 位址時,皆是採 VLSM 型式設定 IP 位址 CIDR - Classless Inter-Domain Routing 以 IP address/N pair 表示 IP 位址 N 為 0~32 間的整數,表示 prefix 長度 Example IP address : 10000000 00001010 00000010 00000011 Netmask : 11111111 11111111 11111111 00000000 Result : VLSM : 128.10.2.3 , 255.255.255.0 CIDR : 128.10.2.3/24
- 38. VLSM 與 CIDR 對照
- 39. 特殊的 IP 位址 Network address Host field contains all 0 bits Limit broadcast Broadcast on local network 將封包傳送到本地網路上的所有電腦 路由器不會轉送該類封包 Network and host fields both contain all 1 bits Direct broadcast Broadcast on specific (possibly remote) network 將封包傳送到特定網路上的所有電腦 Host field contains all 1 bits 以上 IP address 都不能設定在電腦或網路設備上
- 40. 特殊的 IP 位址 All zero IP address 在電腦尚未拿到真正 IP 前做為本機 IP 位址使用 只能當做 source IP address 不能設定在實際電腦或網路設備上
- 41. 特殊的 IP 位址 Multicast address 32bit 表示法 111 XXXXX XXXXXXXX XXXXXXXX XXXXXXXX Formerly “Class D” IP address Multicast 位址分配資訊 http://www.iana.org/assignments/multicast-addresses Reversed address 32bit 表示法 1111 XXXX XXXXXXXX XXXXXXXX XXXXXXXX Formerly “Class E” IP address
- 42. 特殊的 IP 位址 無法在 Internet 上出現的 IP 位址 10.0.0.0/8 Private IP address , RFC1918 169.254.0.0/16 Link Local IP address , RFC5735 172.16.0.0/12 Private IP address , RFC1918 192.168.0.0/16 Private IP address , RFC1918 無法在網路上出現的 IP 位址 127.0.0.0/8 代表本機位址,常用的是 127.0.0.1 用於本機 IP 功能測試
- 43. IP 位址操作 Major concept : 二進元運算;一切皆按 2 的冪次進行 網路分割 “ 除二”方式切分 注意 Prefix 長度 網路合併 找出最多重覆位元,即為新網路之 prefix 避開 host-id 為全 0 或全 1 者 All 0 in host-id: network All 1 in host-id: broadcast
- 44. IP 位址操作 Example A Write the following mask in slash notation (/n): 255.255.255.0 255.0.0.0 255.255.224.0 255.255.240.0 255.254.0.0
- 45. IP 位址操作 Example B In a class B subnet, we know the IP address of one of the hosts and the mask as given below: IP address: 125.134.112.66 Netmask: 255.255.224.0 What is the first address (network address)?
- 46. IP 位址操作 Example C Given four IP blocks: 192.168.0.0/23, 192.168.5.0/24, 192.168.12.0/25, 192.168.20.0/26. Please aggregate them to a new IP block with longest prefix-length.
- 47. IP 位址操作 Example D For IP block 20.0.0.0/8, the first address in a network (network address) is 20.0.0.0. What is the 220000th address?
- 48. IP 位址操作 Example E An organization is granted the block 16.0.0.0/18. The administrator wants to create 500 fixed-length subnets. Find the subnet mask Find the number of addresses in each subnet Find the first and the last address in the first subnet Find the first and the last address in the last subnet (subnet 500)
- 49. IP 位址操作 Example F An ISP is granted a block of address starting with 120.60.4.0/20. The ISP wants to distribute these blocks to 100 organizations with each organization receiving 8 addresses only. Design the subblocks and give the slash notation for each subblock. Find out how many addresses are still available after the allocations.
- 50. IP 路由 網路設備需透過 IP 路由資訊了解如何進行封包傳遞 網路設備獲得 IP 路由資訊的方式 Direct connect 該 IP network 直接介接在路由器上 Static route 手動設定路由器中的 IP 路由資訊 Dynamic route 路由器藉由路由協定互相交換 IP 路由資訊 RIP 、 OSPF 、 IS-IS 、 BGP 路由器中存放 IP 路由資訊的虛擬清單稱為 路由表 每筆路由皆含 prefix 與 netmask 資訊
- 51. IP 路由資訊 路由表中可含下列種類 IP 路由 Network-specific routes 表達特定網路 IP 路由資訊 Prefix 代表該特定網路 Suffix 全部為 0 Host-specific routes 表達特定主機 IP 路由資訊 Netmask 為 255.255.255.255 或 /32 Default route 表達路由器最後將參考的 IP 路由資訊 Host 多半只會設定 default route
- 52. 路由器如何選擇路由 ? 路由表中有許多 IP 路由資訊,路由器該如何選擇 ? 依路由表中 IP 路由資訊建立一二元”樹” 每筆路由都將會在該”樹”上被分配到一個位置 路由器對照 需被轉送的封包之 IP 位址 二元樹 二元樹上對映 IP 位址位元數最多者為最佳路由 此選擇 IP 路由原則稱 longest-prefix search or longest match
- 53. Longest-Prefix Matching 怎麼運作 ? 依路由表資訊建立” unique prefix list” 用最少位元區別出路由表中所有 IP 路由資訊 Example :一路由表中具七筆路由資訊 53.0.0.0/8 70.0.0.0/8 86.0.0.0/8 97.0.0.0/8 170.240.0.0/16 176.2.0.0/16 187.10.0.0/16
- 54. Longest-Prefix Matching 怎麼運作 ? 對照欲轉送封包 IP 位址與該二元樹得知結果 Example : 89.2.100.170 In 32bit : 0101 1001 00000010 01100100 10101010
- 55. 路由表長什麼樣子 ? Example : Cisco IOS
- 56. 路由表長什麼樣子 ? Example : Juniper Junos
- 57. 路由表長什麼樣子 ? Example : Linux
- 58. IP 封包 IP 封包攜帶資訊 IP 封包與其下層網路關聯
- 59. IP 封包資訊 – address Destination IP address IP 位址錯誤,無法傳送至正確目的 Source IP address IP 位址錯誤,無法返回至正確來源 IP 位址錯誤遭設備丟棄
- 60. IP 封包資訊 – fragmentation Fragmentation 各類網路介面其 MTU ( Maximum Transmission Unit )大小不一;換算至 IP 封包後 MTU 大小為 T1/E1 : 1500bytes T3/E3 : 4470bytes ATM : 4470bytes Fast Ethernet : 1500bytes Gigabit Ethernet : 1500bytes Jumbo frame support : 1518bytes ~ 9000bytes SONET/SDH : 4470bytes 封包自 MTU 大的網路介面往 MTU 小的網路介面移動時,就有可能發生問題
- 61. IP 封包資訊 – fragmentation 遇 MTU 較小網路時, IP 封包需要被切割 Performed by routers Divides datagram into several, smaller datagrams called fragments Fragment uses same header format as datagram Each fragment forwarded independently IP 封包重組 Ultimate destination puts fragments back together Key concept! Needed in a connectionless Internet Known as reassembly No need to reassemble subfragments first Timer used to ensure all fragments arrive Timer started when first fragment arrives If timer expires, entire datagram discarded
- 62. IP 封包資訊 – Time-to-Live TTL field of datagram header decremented at each hop (i.e., each router) If TTL reaches zero, datagram discarded Prevents datagrams from looping indefinitely (in case forwarding error introduces loop) IETF recommends initial value of 255 (max) Example
- 63. IP 封包轉送特色 IP uses best-effort delivery Makes an attempt to deliver Does not guarantee delivery In the Internet, routers become overrun or change routes, meaning that: Datagrams can be lost Datagrams can be duplicated Datagrams can arrive out of order or scrambled Motivation: allow IP to operate over the widest possible variety of physical networks
- 64. ICMP/TCP/UDP 介紹 通訊協定分層 ICMP - ERROR AND CONTROL MESSAGES TCP - RELIABLE STREAM TRANSPORT SERVICE UDP - USER DATAGRAM PROTOCOL
- 65. 通訊協定分層 Motivation For Layering Communication is difficult to understand Many subproblems Hardware failure Network congestion Packet delay or loss Data corruption Data duplication or inverted arrivals How to solve? Divide the problem into pieces Solve subproblems separately Combine into integrated whole Result is layered protocols
- 66. Protocol Layering Concept Separates protocol functionality Each layer solves one part of the communication problem Intended primarily for protocol designers Set of layers is called a protocol stack
- 67. 實際分層情況
- 68. Examples Of Layering Two models exist ISO 7-layer reference model for Open System Interconnection (OSI) Predates TCP/IP Does not include an Internet layer Prescriptive (designed before protocols) Internet 5-layer reference model Designed for TCP/IP Descriptive (designed along with actual protocols)
- 69. ISO 7-Layer Reference Model
- 70. TCP/IP 5-Layer Reference Model
- 71. TCP/IP Layer Layer 1 - physical hardware Defines electrical signals used in communication (e.g. voltages on wires between two computers) Uninteresting except to electrical engineers Layer 2 - Network Interface Defines communication between computer and network hardware Isolates details of hardware (MAC) addressing Example protocol: ARP Code is usually in the operating system
- 72. TCP/IP Layer 3: Internet Layer 3 - Internet Protocol is IP Machine to machine communication Defines best-effort, connectionless datagram delivery service for the Internet Code is usually in the operating system Layer 4 – Transport Provides end-to-end connection from application program to application program Often handles reliability, flow control Protocols are TCP and UDP Code is usually in the operating system Layer 5 – Application Implemented by application programs Built on top of transport layer
- 73. The Layering Principle Software implementing layer n at the destination receives exactly the message sent by software implementing layer n at the source.
- 74. Illustration Of Layering In An Internet
- 75. Handling Multiple Protocols Per Layer Sender places field in header to say which protocol used at each layer Receiver uses field to determine which protocol at next layer receives the packet Known as multiplexing and demultiplexing
- 76. Example Of Demultiplexing Performed By IP
- 77. Example Of Demultiplexing Performed By TCP TCP is part of operating system Transfer to application program must cross operating system boundary
- 78. ERROR AND CONTROL MESSAGES – ICMP Errors In Packet Switching Networks Causes include Temporary or permanent disconnection Hardware failures Router overrun Routing loops Need mechanisms to detect and correct Error Detection And Reporting Mechanisms IP header checksum to detect transmission errors Error reporting mechanism to distinguish between events such as lost datagrams and incorrect addresses Higher level protocols (i.e., TCP) must handle all other problems
- 79. Error Reporting Mechanism Named Internet Control Message Protocol (ICMP) Required and integral part of IP Used primarily by routers to report delivery or routing problems to original source Also includes informational (nonerror) functionality Uses IP to carry control messages Only reports problems to original source ICMP purpose The Internet Control Message Protocol allows a router to send error or control messages to the source of a datagram, typically a host. ICMP provides communication between the Internet Protocol software on one machine and the Internet Protocol software on another.
- 80. Error Reporting Vs. Error Correction ICMP does not Provide interaction between a router and the source of trouble Maintain state information (each packet is handled independently) Consequence When a datagram causes an error, ICMP can only report the error condition back to the original source of the datagram; the source must relate the error to an individual application program or take other action to correct the problem.
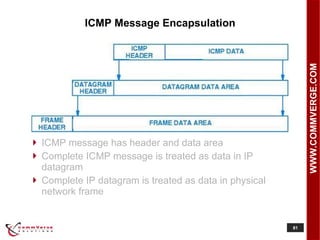
- 81. ICMP Message Encapsulation ICMP message has header and data area Complete ICMP message is treated as data in IP datagram Complete IP datagram is treated as data in physical network frame
- 82. ICMP Message Format Multiple message types Each message has its own format Messages Begin with 1-octet TYPE field that identifies which of the basic ICMP message types follows Some messages have a 1-octet CODE field that further classifies the message Example TYPE specifies destination unreachable CODE specifies whether host or network was unreachable
- 84. Example ICMP Message (ICMP Echo Request/Reply) Sent by ping program Used to test reachability
- 85. Example ICMP Message (Destination Unreachable) Used to report that datagram could not be delivered Code specifies details
- 86. Example ICMP Message (Destination Unreachable)
- 87. Example ICMP Message (Time Exceeded) At least one fragment failed to arrive, or TTL field in IP header reached zero
- 88. RELIABLE STREAM TRANSPORT SERVICE - TCP Transmission Control Protocol (TCP) Major transport service in the TCP/IP suite Used for most Internet applications (esp. World Wide Web) Around 95% of all bytes and around 85-95% of all packets on the Internet are transmitted using TCP. – Eggert, et. al. CCR
- 89. TCP Characteristics Stream orientation Buffered transfer Full duplex connection Machine could send and receive simultaneously Reliability Positive Acknowledgement with Retransmission (PAR) Receiver sends acknowledgement when data arrives Sender starts timer whenever transmitting Sender retransmits if timer expires before acknowledgement arrives
- 90. Illustration Of Acknowledgements Time moves from top to bottom in the diagram
- 91. Illustration Of Recovery After Packet Loss
- 92. Sliding Window The Problem With Simplistic PAR A simple positive acknowledgement protocol wastes a substantial amount of network bandwidth because it must delay sending a new packet until it receives an acknowledgement for the previous packet. Problem is especially severe if network has long latency Sliding Window Allow multiple packets to be outstanding at any time Still require acknowledgements and retransmission Example source : http://www.it.uu.se/edu/course/homepage/datakom/civinght04/schema/ sliding_window . pps
- 93. Sliding window - Sender side Cumulative Acknowledgments Not sent Sent, no ACK ACK:ed Free Sending buffer at the sender: Old data sent that has already been ACK:ed (Could as well be marked as free space) New data sent to transport layer by application, but not yet sent Free buffer space where application can write new data to be sent
- 94. Sliding window - Sender side Cumulative Acknowledgments Not sent Sent, no ACK ACK:ed Free Sending buffer at the sender: Data that has been sent, but not ACK:ed Also called the Sending window This is the sliding window (yes, it slides!) This data can not be sent yet, as the sliding window in this example has a maximum size of 10
- 95. Sliding window - Sender side Cumulative Acknowledgments Not sent Sent, no ACK ACK:ed Free Sending buffer at the sender: ACTION : An ACK of the oldest sent packet arrives The window slides so that the left border is in line with the oldest outstanding ACK The unsent segments that fit within the window are sent
- 96. Sliding window - Sender side Cumulative Acknowledgments Not sent Sent, no ACK ACK:ed Free Sending buffer at the sender: The data is placed in free buffer slots ACTION : The application has more data to send
- 97. Sliding window - Sender side Cumulative Acknowledgments Not sent Sent, no ACK ACK:ed Free Sending buffer at the sender: Older sent but un-ACK:ed segments are now considered to be ACK:ed ACTION : An ACK arrives in the middle of the window The window slides and unsent segments within the window are sent The window shrinks by one segment as there is no more than 9 segments outstanding
- 98. Sliding window - Sender side Cumulative Acknowledgments Not sent Sent, no ACK ACK:ed Free Sending buffer at the sender: The data is placed in free buffer slots ACTION : The application has more data to send As the window is currently 9 segments wide, it can grow by one segment The new data that fits within the window is sent
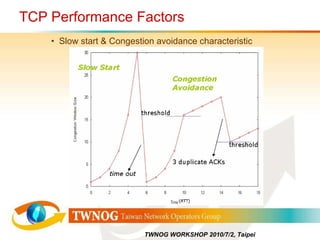
- 99. Sliding window - Sender side Cumulative Acknowledgments Not sent Sent, no ACK ACK:ed Free Sending buffer at the sender: The ACK is silently ignored ACTION : An ACK of already ACK:ed segments arrives
- 100. Layering Of The Three Major Protocols
- 101. TCP Ports, Connections, And Endpoints Endpoint of communication is application program TCP uses protocol port number to identify application TCP connection between two endpoints identified by four items Sender’s IP address Sender’s protocol port number Receiver’s IP address Receiver’s protocol port number Because TCP identifies a connection by a pair of endpoints, a given TCP port number can be shared by multiple connections on the same machine.
- 102. TCP Segment Format
- 103. TCP Retransmission Designed for Internet environment Delays on one connection vary over time Delays vary widely between connections Fixed value for timeout will fail Waiting too long introduces unnecessary delay Not waiting long enough wastes network bandwidth with unnecessary retransmission Retransmission strategy must be adaptive Adaptive Retransmission TCP keeps estimate of round-trip time (RTT) on each connection Round-trip estimate derived from observed delay between sending segment and receiving acknowledgement Timeout for retransmission based on current round-trip estimate
- 104. Adaptive Retransmission Issue Difficulties With Adaptive Retransmission The problem is knowing when to retransmit Segments or ACKs can be lost or delayed, making roundtrip estimation difficult or inaccurate Round-trip times vary over several orders of magnitude between different connections Traffic is bursty, so round-trip times fluctuate wildly on a single connection Load imposed by a single connection can congest routers or networks Retransmission can cause congestion Because an internet contains diverse network hardware technologies, there may be little or no control for intranetwork congestion
- 105. Solution: Smoothing Adaptive retransmission schemes keep a statistically smoothed round-trip estimate Smoothing keeps running average from fluctuating wildly, and keeps TCP from overreacting to change Difficulty: choice of smoothing scheme
- 106. Flow Control And Congestion Control Flow Control Receiver advertises window that specifies how many additional bytes it can accept Window size of zero means sender must not send normal data (ACKs and urgent data allowed) Congestion Control Slow start Congestion avoidance Fast retransmit Fast recovery Example source : [TWNOG] 網路與 TCP 效能關聯探討 http://opm.twnic.net.tw/14th/1-twnogworkshop.pdf
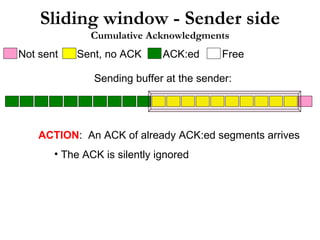
- 107. TCP Performance Factors Flow control Window Size Adjustment “ Receiver window size filed” in TCP header
- 108. TCP Performance Factors Congestion Control Flow control 讓接收端控制進入之流量,避免 buffer overflow 情況發生 藉由 AdvertisedWindow 調整發送端 window size 無法反應網路連線狀況 無法避免所經網路是否有類似 buffer overflow 情況發生 為能偵測可能的網路壅塞, TCP 使用 Congestion control 。 藉由 CongestionWindow (cwnd) 來進行調整 Congestion control 主要含四種方式 (RFC5681) : Slow start Congestion avoidance Fast retransmit Fast recovery
- 109. TCP Performance Factors Slow start TCP connection 剛建立時,使用小的 window size 。等到收到 ACK 後再慢慢增加。 cwnd 初始值為 1 旨在偵測網路頻寬狀況 每收到 1 個 ACK 則 cwnd+1 如此一來,每經過一個 round-trip time (RTT) , cwnd 的值則變成上一次 RTT 的兩倍 指數成長 為避免 cwnd 增加太快,俟 cwnd 超過” slow start threshold, ssthresh” 後,每一 RTT 只增加 1 線性成長
- 110. TCP Performance Factors Congestion avoidance 在此階段 : cwnd > ssthresh cwnd + 1 for each RTT 當有 packet loss 發生時,則 : ssthresh -> cwnd/2 cwnd -> 1 packet retransmission 一旦 packet loss 發生時, TCP Performance 將受到嚴重影響。
- 111. TCP Performance Factors Slow start & Congestion avoidance characteristic
- 112. TCP Connection Details Connections started reliably, and terminated gracefully Connection established with a 3-way handshake Connection terminated with 4-way handshake
- 113. TCP Finite State Machine
- 114. TCP State – real case Command :” netstat –na”
- 115. USER DATAGRAM PROTOCOL (UDP) User Datagram Protocol Transport-layer protocol (Layer 4) Connectionless service: provides application programs with ability to send and receive messages Allows multiple, application programs on a single machine to communicate concurrently Same best-effort semantics as IP Message can be delayed, lost, or duplicated Messages can arrive out of order Application accepts full responsibility for errors
- 116. Port Numbers In A UDP Message SOURCE PORT identifies application on original source computer DESTINATION PORT identifies application on ultimate destination computer Note: IP addresses of source and destination do not appear explicitly in header
- 117. Position Of UDP In Protocol Stack UDP lies between applications and IP
- 118. UDP Encapsulation
- 119. Demultiplexing Based On UDP Protocol Port Number
- 120. Assignment Of UDP Port Numbers Small numbers reserved for specific services Called well-known ports Same interpretation throughout the Internet Used by server software Large numbers not reserved Available to arbitrary application program Used by client software More later in the course Internetworking
- 121. Examples Of Assigned UDP Port Numbers
- 122. 常見應用程式介紹 名稱解析 遠端登入 檔案傳輸與存取 電子郵件 全球資訊網 網路管理
- 123. Client-Server Interaction Client Invoked by user Forms connection to remote server Passes keystrokes from user’s keyboard to server and displays output from server on user’s screen Server Accepts connection over the network Passes incoming characters to OS as if they were typed on a local keyboard Sends output over connection to client
- 124. 名稱解析 IP 位址不容易記憶 使用”名字”來替主機取名 電腦仍需要靠 IP 位址來運作 DNS - Domain Name Service DNS 查詢( UDP , port 53 ) DNS Zone Transfer ( TCP , port 53 )
- 125. 遠端登入 文字介面( CLI ) telnet ( TCP , port 23 ) rlogin ( TCP , port 513 ) rsh ( TCP , port 514 ) ssh ( TCP , port 22 ) 圖形介面( GUI ) Virtual Network Computing (VNC) Remote Desktop Protocol (RDP)
- 127. 檔案傳輸與存取 Always a popular application Two basic paradigms Whole-file copying Piecewise file access Whole-file copying FTP ( TCP , port 20 、 21 ) Secured version : SSL-FTP 、 sftp 、 scp TFTP ( UDP , port 69 ) Code is much smaller Piecewise file access NFS ( TCP , port 2049 ) Protocol for file access, not copying Developed by Sun Microsystems, now part of TCP/IP standards Transparent (application cannot tell that file is remote)
- 128. NFS Implementation
- 129. 電子郵件 Among most widely used Internet services Protocols for email : Simple Mail Transfer Protocol (SMTP , TCP:25) Post Office Protocol version 3 (POP3 , TCP:110) Internet Message Access Protocol (IMAP , TCP:143) Protocol 使用位置 Mail client 連線至 email server 進行寄信動作 SMTP Mail client 連線至 email server 進行收信動作 POP3 、 IMAP Email server 間彼此傳遞信件 SMTP
- 130. Example Of SMTP S: 220 Beta.GOV Simple Mail Transfer Service Ready C: HELO Alpha.EDU S: 250 Beta.GOV C: MAIL FROM:<[email protected]> S: 250 OK C: RCPT TO:<[email protected]> S: 250 OK C: RCPT TO:<[email protected]> S: 550 No such user here C: RCPT TO:<[email protected]> S: 250 OK C: DATA S: 354 Start mail input; end with <CR><LF>.<CR><LF> C: ...sends body of mail message... C: ...continues for as many lines as message contains C: <CR><LF>.<CR><LF> S: 250 OK C: QUIT S: 221 Beta.GOV Service closing transmission channel
- 131. Multipurpose Internet Mail Extensions (MIME) Permits nontextual data to be sent in email Graphics image Voice or video clip Sender Encodes binary item into printable characters Places in email message for transfer Receiver Receives email message containing encoded item Decodes message to extract original binary value
- 132. Example Of Mixed / Multipart Message
- 133. 全球資訊網 Distributed hypermedia paradigm Major service on the Internet
- 134. Web Page Identifier Known as Uniform Resource Locator (URL) Encodes Access protocol to use Domain name of server Protocol port number (optional) Path through server’s file system (optional) Parameters (optional) Query (optional) Format http: // hostname [: port] / path [; parameters] [? query]
- 135. Web Standards Separate standards for Representation HyperText Markup Language (HTML) Document contains text plus embedded links HTML gives guidelines for display, not details Consequence: two browsers may choose to display same document differently Transfer Used between browser and web server Protocol is HyperText Transfer Protocol (HTTP) Runs over TCP
- 136. HTTP Operation Browser sends requests to which server replies Typical request: GET used to fetch document Example GET http://www.cs.purdue.edu/people/comer/ HTTP/1.1 Relative URL also permitted GET /people/comer/ HTTP/1.1
- 137. 網路管理 Early network systems used two approaches Separate, parallel management network Link-level management commands TCP/IP pioneered running management protocols at the application layer Motivation: provide internet-wide capability instead of single network capability In a TCP/IP internet, a manager needs to examine and control routers and other network devices. Because such devices attach to arbitrary networks, protocols for internet management operate at the application level and communicate using TCP/IP transport-level protocols.
- 138. Architecture Model
- 139. Terminology Agent Runs on arbitrary system (e.g., a router) Responds to manager’s requests Management software Runs on manager’s workstation Sends requests to agents as directed by the manager
- 140. Simple Network Management Protocol (SNMP) Specifies communication between manager’s workstation and managed entity Uses fetch-store paradigm 常見版本 SNMPv1 SNMPv2c SNMPv3
- 141. Application Troubleshooting Network troubleshooting Ping 偵測目標是否可到達 Ping 不到原因 目標不存在或沒有開機 目標網路斷線 ICMP 封包遭防火牆丟棄 Traceroute 偵測封包至目標 IP 地址”去向”路由 “ 返回路由”無法藉由 traceroute 探詢 Ping 可有限度的探詢返回路由 Traceroute 不到原因 Traceroute 所使用封包( UDP 、 ICMP )遭防火牆丟棄 調整 traceroute 所使用封包來規避 firewall 攔截 MPLS-TE Tunnel 可設定不回應 TTL 變化
- 142. Application Troubleshooting TCP troubleshooting 偵測目標主機 TCP 狀況: 確認 TCP 3-way handshaking 成功 若 3-way handshaking 都無法完成自然不可能成功連線 利用基本 application protocol 指令測試目標主機狀況 SMTP POP3 HTTP
- 144. 常見網路設備介紹﹙二﹚ 路由器 Layer 3 device 主要以 destination IP address 為轉送依據 網路防火牆 Layer 4 device 可 IP 與 TCP/UDP 資訊進行過濾依據 應用程式防火牆 Layer 7 device 可察看應用程式協定如 HTTP 、 FTP 再進行過濾
- 145. 常見網路設備介紹﹙二﹚ 交換器 L3 switch L4 switch L7 switch Proxy/Cache 應用程式加速器
- 146. Reference TCP/IP TCP-IP.Illustrated,.Volume.1 W. Richard Stevens; Addison-Wesley Professional
- 147. 課堂練習與課後測驗解答
- 148. 課堂練習 Example A Write the following mask in slash notation (/n): 255.255.255.0 255.0.0.0 255.255.224.0 255.255.240.0 255.254.0.0 Answer /24 /8 /19 /20 /15
- 149. 課堂練習 Example B In a class B subnet, we know the IP address of one of the hosts and the mask as given below: IP address: 125.134.112.66 Netmask: 255.255.224.0 What is the first address (network address)? Answer IP= 01111101 10000110 011 10000 01000010 Netmask= 11111111 11111111 111 00000 00000000 IP Prefix= 01111101 10000110 011 Network= 01111101 10000110 01100000 00000000 = 125.134.96.0
- 150. 課堂練習 Example C Given four IP blocks: 192.168.0.0/23, 192.168.5.0/24, 192.168.12.0/25, 192.168.20.0/26. Please aggregate them to a new IP block with longest prefix-length. Answer 192.168.0.0/23= 11000000 10101000 0000000 0 00000000 192.168.5.0/24= 11000000 10101000 00000101 00000000 192.168.12.0/25= 11000000 10101000 00001100 0 0000000 192.168.20.0/26= 11000000 10101000 00010100 00 000000 longest prefix= 11000000 10101000 000 New prefix= 192.168.0.0/19
- 151. 課堂練習 Example D For IP block 20.0.0.0/8, the first address in a network (network address) is 20.0.0.0. What is the 220000th address? Answer 20.0.0.0/8= 00010100 00000000 00000000 00000000 1st= 00010100 00000000 00000000 00000000 =0 in decimal 2nd= 00010100 00000000 00000000 00000001 =1 3rd= 00010100 00000000 00000000 00000010 =2 4th= 00010100 00000000 00000000 00000011 =3 … 220000th= 00010100 ???????? ???????? ???????? =219999 219999 in binary = 131072+65536+16384+4096+2048+512+256+64+16+8+4+2+1 = 2 17 +2 16 +2 14 +2 12 +2 11 +2 9 +2 8 +2 6 +2 4 +2 3 +2 2 +2 1 +2 0 = 110101101101011111 220000th= 00010100 00000011 01011011 01011111 20.3.91.95
- 152. 課堂練習 Example E An organization is granted the block 16.0.0.0/18. The administrator wants to create 500 fixed-length subnets. Find the subnet mask Find the number of addresses in each subnet Find the first and the last address in the first subnet Find the first and the last address in the last subnet (subnet 500) Answer Divide the block into 512 equal-length subnets 16.0.0.0/18= 00010000 00000000 00 000000 00000000 16.0.0.0/18 divide in 2= 00010000 00000000 00 ?00000 00000000 16.0.0.0/18 divide in 512= 00010000 00000000 00 ?????? ???00000 New subnet mask= 11111111 11111111 11111111 11100000= 255.255.255.224 Number of addresses in each subnet = 2 6 = 32 First subnet= 00010000 00000000 00000000 000 00000= 16.0.0.0 Last address in first subnet= 00010000 00000000 00000000 000 11111= 16.0.0.31 500th subnet= 00010000 00000000 00111110 011 00000= 16.0.62.96 Last address in 500 th subnet= 00010000 00000000 00111110 011 11111= 16.0.62.127
- 153. 課堂練習 Example F An ISP is granted a block of address starting with 120.60.4.0/20. The ISP wants to distribute these blocks to 100 organizations with each organization receiving 8 addresses only. Design the subblocks and give the slash notation for each subblock. Find out how many addresses are still available after the allocations. Answer Complete subnet comes from 120.60.0.0 to 120.60.15.255 120.60.4.0/20= 01111000 00111100 0000 0100 00000000 Only 8 addresses is assigned: only 3 bites for host ID Possible assigned subnets: 01111000 00111100 0000 01?? ?????000 1st subnet = 01111000 00111100 00000100 00000 000 = 120.60.4.0/29 2nd subnet = 01111000 00111100 00000100 00001 000 = 120.64.4.8/29 3rd subnet = 01111000 00111100 00000100 00010 000 = 120.64.16.0/29 … .. 100 th subnet = 01111000 00111100 00000111 00011 000 = 120.60.7.24/29 Available address comes from: 01111000 00111100 00000111 00100000 to: 01111000 00111100 00001111 11111111 Available address = 2272 addresses
- 154. 課後測驗 Review 1 Choose components are DEDICATED for optical transmission? (Choose THREE best answers)(10 points) DWDM transponder EDFA Multimode fiber Router Switch Answer: A, B, C
- 155. 課後測驗 Review 2 Which IP addresses could be configured on a computer? (Choose TWO best answers)(10 points) 10.24.130.5/15 139.175.3.255/22 172.29.2.255/23 192.168.1.32/27 192.168.100.127/25 Answer: A, C
- 156. 課後測驗 Review 3 For IP block 69.0.0.0: Does it belong class A, B or C in CLASSFUL IP scheme? ______(4 points) What is the CIDR notation if the prefix-length is 16bits? ____________(4 points) Follow “B.” above, what are the 4 networks if we divide this network into four equal pieces (CIDR notation)? ________________, (2 points) ________________, (2 points) ________________, (2 points) ________________, (2 points) What’s the sub-network’s netmask? ________________ (4 points) Answer: Class A 69.0.0.0/16 69.0.0.0/18, 69.0.64.0/18, 69.0.128.0/18, 69.0.192.0/18 255.255.192.0
- 157. 課後測驗 Review 4 Which network address are invalid on Internet? (Choose FOUR best answers)(10 points) 10.1.10.100 127.5.63.254 172.32.64.1 169.254.82.45 193.168.256.29 Answer: A, B, D, E
- 158. 課後測驗 Review 5 Choose options related Time-to-Live field in IP header? (Choose TWO best answers)(10 points) Network Time Synchronization Ping Remove packets when routing loop happened Traceroute Transmission health check Answer: C, D
- 159. 課後測驗 Review 6 Choose features related TCP? (Choose THREE best answers)(10 points) Connectionless Flow Duplex Flow Control Reliability SYN packet carry receiver sliding window size information Answer: B, C, D
- 160. 課後測驗 Review 7 Choose options about identifying a TCP flow? (Choose THREE best answers)(10 points) MAC address Protocol type Source/Destination IP address Source/Destination TCP port TCP flag(s) Answer: B, C, D
- 161. 課後測驗 Review 8 Which TCP feature cause Denied-of-Service attack? (Choose ONE best answer)(5 points) Four-way handshaking Re-transmission Sliding Window Slow Start Three-way handshaking Answer: E
- 162. 課後測驗 Review 9 Which protocol provide similar function with RARP (Reverse ARP) and substitute it later? (Choose ONE best answer)(5 points) ARP DHCP DNS GARP SNMP Answer: B
- 163. 課後測驗 Review 10 Choose protocols belong TCP application? (Choose THREE best answer)(10 points) HTTP SMTP SNMP SSH TFTP Answer: A, B, D






![About the Trainer Kae Hsu﹙ 許至凱﹚ Commverge Solutions – Taiwan [email_address] http:// tw.linkedin.com/in/kaehsu](https://image.slidesharecdn.com/fegtsiptraining-tcpipintroduction20101105-101112024512-phpapp01/85/FEGTS-IP-training-TCP-IP-Introduction-6-320.jpg)

































































































![Flow Control And Congestion Control Flow Control Receiver advertises window that specifies how many additional bytes it can accept Window size of zero means sender must not send normal data (ACKs and urgent data allowed) Congestion Control Slow start Congestion avoidance Fast retransmit Fast recovery Example source : [TWNOG] 網路與 TCP 效能關聯探討 http://opm.twnic.net.tw/14th/1-twnogworkshop.pdf](https://image.slidesharecdn.com/fegtsiptraining-tcpipintroduction20101105-101112024512-phpapp01/85/FEGTS-IP-training-TCP-IP-Introduction-106-320.jpg)


























![Web Page Identifier Known as Uniform Resource Locator (URL) Encodes Access protocol to use Domain name of server Protocol port number (optional) Path through server’s file system (optional) Parameters (optional) Query (optional) Format http: // hostname [: port] / path [; parameters] [? query]](https://image.slidesharecdn.com/fegtsiptraining-tcpipintroduction20101105-101112024512-phpapp01/85/FEGTS-IP-training-TCP-IP-Introduction-134-320.jpg)




























