File handling in c
Download as PPT, PDF21 likes34,239 views
The document discusses files and file operations in C/C++. It defines a file as a collection of bytes stored on a secondary storage device. There are different types of files like text files, data files, program files, and directory files. It describes opening, reading, writing, appending, and closing files using functions like fopen(), fread(), fwrite(), fclose(), etc. It also discusses random and sequential file access and modifying file contents using functions like fseek(), fread(), fwrite().
1 of 34
Downloaded 1,775 times
























![#include<stdio.h>
void main()
{
FILE *fp;
char line[280];int ch, i=0;
fp=fopen(“a.dat”,”a”);
if(fp==NULL)
print(“Unable to open clear.c”);
else{
do{
do{
line[i++] = getchar();
}while(line[i-1]!=‘*’);
fputs(line, fp);//Writes string to the file
i=0;
printf(“nPress 1 to continue”);
scanf(“%d”,&ch);
}while(ch==1);
fclose(fp);
printf(“File is successfully created”);
}](https://image.slidesharecdn.com/filehandlinginc-130914023414-phpapp01/85/File-handling-in-c-25-320.jpg)


![#include<stdio.h>
struct stock
{
int itid, qty;
char n[100];
float rate;
}it;
void main()
{
FILE *fp; int ch; int r = 0;
fp = fopen(“item.c”, “r+”);
if(fp==NULL)
{
printf(“Unable to open item.c”);
}
}](https://image.slidesharecdn.com/filehandlinginc-130914023414-phpapp01/85/File-handling-in-c-28-320.jpg)





Ad
Recommended
File in C language



File in C languageManash Kumar Mondal A file is a collection of related data that a computer treats as a single unit. Files allow data to be stored permanently even when the computer is shut down. C uses the FILE structure to store attributes of a file. Files allow for flexible data storage and retrieval of large data volumes like experimental results. Key file operations in C include opening, reading, writing, and closing files. Functions like fopen(), fread(), fwrite(), fclose() perform these operations.
C Programming: Structure and Union



C Programming: Structure and UnionSelvaraj Seerangan The document discusses various user-defined data types in C programming including structures, unions, enumerated types, and type definitions. It provides details on declaring and defining structures and unions, accessing structure members, nested structures, arrays of structures, passing structures to functions, and bit fields. Enumerated types allow assigning names to integer values. Typedef allows abbreviating existing data type names. Structures and unions allow grouping related data as records while enumerated types and typedefs create new data types.
Functions in c language 



Functions in c language tanmaymodi4 what are functions in c
importance of function in c
uses of function in c
syantax of function in c
program of function in c
File Management in C



File Management in CPaurav Shah Contents:-
Introduction
What is a File?
High Level I/O Functions
Defining & Opening a File
Closing a File
The getc and putc Functions
The getw and putw Functions
The fprintf and fscanf Functions
Array in c



Array in cRavi Gelani The document discusses different types of arrays in C programming language. It defines an array as a fixed-size sequential collection of elements of the same data type. It describes one-dimensional, two-dimensional and multidimensional arrays. For one-dimensional arrays, it provides examples of declaration, initialization at compile-time and run-time. For two-dimensional arrays, it explains the memory layout and initialization syntax. It also lists some applications of arrays.
File handling in C



File handling in CKamal Acharya The document discusses file handling in C programming. It explains that console I/O functions use keyboard and monitor for input and output but the data is lost when the program terminates. Files provide a permanent way to store and access data. The document then describes different file handling functions like fopen(), fclose(), fgetc(), fputc(), fprintf(), fscanf() for reading from and writing to files. It also discusses opening files in different modes, reading and writing characters and strings to files, and using formatted I/O functions for files.
Structure in C



Structure in CKamal Acharya The document discusses various aspects of structures in C programming language. It defines a structure as a collection of variables of different data types grouped together under a single name. Structures allow grouping of related data and can be very useful for representing records. The key points discussed include:
- Defining structures using struct keyword and accessing members using dot operator.
- Declaring structure variables and initializing structure members.
- Using arrays of structures to store multiple records.
- Nested structures to group related members together.
- Pointers to structures for dynamic memory allocation.
- Passing structures, structure pointers and arrays of structures to functions.
Pointer in c



Pointer in clavanya marichamy Pointer is a variable that stores the address of another variable. Pointers in C are used to allocate memory dynamically at runtime and can point to data of any type such as int, float, char, etc. Pointers are declared with a * before the variable name and are initialized using the address operator &. Pointers can be used to pass arguments to functions by reference and can also point to elements within structures.
Function in C program



Function in C programNurul Zakiah Zamri Tan The document discusses functions in C programming. It defines functions as self-contained blocks of code that perform a specific task. Functions make a program more modular and easier to debug by dividing a large program into smaller, simpler tasks. Functions can take arguments as input and return values. Functions are called from within a program to execute their code.
structure and union



structure and unionstudent - A structure is a user-defined data type that groups logically related data items of different data types into a single unit. Structures allow related data to be accessed and managed together.
- Structures can contain nested structures as members. Nested structure members are accessed using two period operators (e.g. e1.doj.day).
- Structures can be passed to functions as parameters and returned from functions. Pointers to structures are declared and accessed using arrow (->) operator instead of period operator.
- A union shares the same memory space for multiple data types, allocating only enough space for its largest member. Unions allow different types to share the same memory location.
Basics of C programming



Basics of C programmingavikdhupar Introduction to C language. Compiled from different sources available online. Thanks to the original authors.
Functions in C



Functions in CKamal Acharya This document discusses different types of functions in C programming. It defines library functions, user-defined functions, and the key elements of functions like prototypes, arguments, parameters, return values. It categorizes functions based on whether they have arguments and return values. The document also explains how functions are called, either by value where changes are not reflected back or by reference where the original values are changed.
Programming in C Presentation upto FILE



Programming in C Presentation upto FILEDipta Saha Programming in C Presentation upto FILE
Facebook >> facebook.com/diptasaha.lpu.cse
Email >> [email protected]
Structures in c language



Structures in c languagetanmaymodi4 Structures in C allow the user to define a custom data type that combines different data types to represent a record. A structure is similar to an array but can contain heterogeneous data types, while an array only holds the same type. Structures are defined using the struct keyword followed by structure tags and member lists. Structure variables are declared like other variables and members can be accessed using the dot operator. Arrays of structures and nested structures are also supported.
Call by value



Call by valueDharani G The document discusses call by value and call by reference in functions. Call by value passes the actual value of an argument to the formal parameter, so any changes made to the formal parameter do not affect the actual argument. Call by reference passes the address of the actual argument, so changes to the formal parameter do directly modify the actual argument. An example program demonstrates call by value, where changing the formal parameter does not change the original variable.
Variables in C Programming



Variables in C Programmingprogramming9 This document discusses variables in C programming. It explains that variables are names that refer to memory locations where values can be stored and changed during program execution. It provides the syntax for declaring variables using different data types like int, float, double, and char. Rules for variable names are also outlined, such as starting with a letter or underscore and avoiding reserved words.
classes and objects in C++



classes and objects in C++HalaiHansaika Classes allow users to bundle data and functions together. A class defines data members and member functions. Data members store data within each object, while member functions implement behaviors. Classes support access specifiers like public and private to control access to members. Objects are instances of classes that allocate memory for data members. Member functions can access object data members and are called on objects using dot notation. Friend functions allow non-member functions to access private members of classes.
SPL 9 | Scope of Variables in C



SPL 9 | Scope of Variables in CMohammad Imam Hossain The document discusses scope of variables in programming languages. There are three scopes where variables can be declared: local within a function/block, global outside all functions, and as function parameters. Local variables are only accessible within their declaration block, while global variables can be accessed anywhere after declaration. The document provides examples demonstrating how variables with the same name in different scopes do not conflict, and how local variables take precedence over global variables of the same name.
MULTI THREADING IN JAVA



MULTI THREADING IN JAVAVINOTH R This document provides an overview of threads in Java, including:
- Threads allow for multitasking by executing multiple processes simultaneously. They are lightweight processes that exist within a process and share system resources.
- Threads can be created by extending the Thread class or implementing the Runnable interface. The run() method defines the code executed by the thread.
- Threads transition between states like new, runnable, running, blocked, and dead during their lifecycle. Methods like start(), sleep(), join(), etc. impact the thread states.
- Synchronization is used to control access to shared resources when multiple threads access methods and data outside their run() methods. This prevents issues like inconsistent data.
Strings in C



Strings in CKamal Acharya Strings are arrays of characters that are null-terminated. They can be manipulated using functions like strlen(), strcpy(), strcat(), and strcmp(). The document discusses initializing and reading strings, passing strings to functions, and using string handling functions to perform operations like copying, concatenating, comparing, and reversing strings. It also describes arrays of strings, which are 2D character arrays used to store multiple strings. Examples are provided to demonstrate reading and sorting arrays of strings.
Operators in java



Operators in javaThen Murugeshwari Operators in Java provide symbols that operate on arguments to produce results. The document discusses the different types of operators in Java including assignment, arithmetic, relational, logical, bitwise, and ternary operators. Examples are provided to demonstrate the usage of various operators like increment/decrement, arithmetic, relational, logical, bitwise, ternary, and instanceof operators in Java code.
Variables in C and C++ Language



Variables in C and C++ LanguageWay2itech This document discusses key concepts in C programming including variables, data types, constants, keywords, comments, and rules for writing C programs. It defines variables as containers for storing data in memory locations. It describes predefined data types like char, int, float, and double as well as derived and user-defined data types. It also covers identifiers, declarations, initialization, keywords, constants, comments, and general rules for writing C programs.
Pointers in c++



Pointers in c++Vineeta Garg Pointer is a variable that stores the memory address of another variable. It allows dynamic memory allocation and access of memory locations. There are three ways to pass arguments to functions in C++ - pass by value, pass by reference, and pass by pointer. Pass by value copies the value, pass by reference copies the address, and pass by pointer passes the address of the argument. Pointers can also point to arrays or strings to access elements. Arrays of pointers can store multiple strings. References are alternative names for existing variables and any changes made using the reference affect the original variable. Functions can return pointers or references.
Java program structure



Java program structureshalinikarunakaran1 The document discusses the structure of a Java program. A Java program contains classes, with one class containing a main method that acts as the starting point. Classes contain data members and methods that operate on the data. Methods contain declarations and executable statements. The structure also includes sections for documentation, package statements, import statements, interface statements, and class definitions, with the main method class being essential.
C++ Overview PPT



C++ Overview PPTThooyavan Venkatachalam C++ is an object-oriented programming language that was created as an extension of C programming language. It was created by Bjarne Stroustrup in 1979 at Bell Labs. Some key differences between C and C++ include C++ supporting object-oriented programming concepts like classes, inheritance and polymorphism, while C is a procedural language. Pointers and references are commonly used in C++ to pass arguments to functions by reference rather than by value. Arrays and functions are also important elements of C++ programs.
Basics of c++ Programming Language



Basics of c++ Programming LanguageAhmad Idrees The aim of this list of programming languages is to include all notable programming languages in existence, both those in current use and ... Note: This page does not list esoteric programming languages. .... Computer programming portal ...
File handling in c



File handling in caakanksha s File handling in C programming uses file streams as the means of communication between programs and data files. The input stream extracts data from files and supplies it to the program, while the output stream stores data from the program into files. To handle file input/output, header file fstream.h is included, which contains ifstream and ofstream classes. Common file operations include opening, reading, writing, and closing files using functions like fopen(), fgetc(), fputs(), fclose(), and checking for end-of-file conditions. Files can be opened in different modes like read, write, append depending on the operation to be performed.
Object Oriented Programming Using C++



Object Oriented Programming Using C++Muhammad Waqas This Powerpoint presentation covers following topics of C Plus Plus:
Features of OOP
Classes in C++
Objects & Creating the Objects
Constructors & Destructors
Friend Functions & Classes
Static data members & functions
Mesics lecture files in 'c'



Mesics lecture files in 'c'eShikshak The document discusses files and streams in C language. It explains that a file is a collection of bytes stored on a secondary storage device and has different types like data, text, program etc. It also describes streams as a series of bytes flowing between a program and file. The key functions for working with files and streams in C like fopen(), fclose(), fread(), fwrite() are explained along with their usage.
Presentation of file handling in C language



Presentation of file handling in C languageShruthi48 A file is a collection of bytes stored on a secondary storage device. There are different types of files like data files, text files, program files, and directory files. A file has a beginning and end, and its current position can be tracked using a marker. Files can be accessed sequentially for text or randomly for binary data. To perform operations on a file, it must first be opened by declaring a file pointer and bringing it into memory. Common file operations include reading, writing, modifying, and closing a file.
Ad
More Related Content
What's hot (20)
Function in C program



Function in C programNurul Zakiah Zamri Tan The document discusses functions in C programming. It defines functions as self-contained blocks of code that perform a specific task. Functions make a program more modular and easier to debug by dividing a large program into smaller, simpler tasks. Functions can take arguments as input and return values. Functions are called from within a program to execute their code.
structure and union



structure and unionstudent - A structure is a user-defined data type that groups logically related data items of different data types into a single unit. Structures allow related data to be accessed and managed together.
- Structures can contain nested structures as members. Nested structure members are accessed using two period operators (e.g. e1.doj.day).
- Structures can be passed to functions as parameters and returned from functions. Pointers to structures are declared and accessed using arrow (->) operator instead of period operator.
- A union shares the same memory space for multiple data types, allocating only enough space for its largest member. Unions allow different types to share the same memory location.
Basics of C programming



Basics of C programmingavikdhupar Introduction to C language. Compiled from different sources available online. Thanks to the original authors.
Functions in C



Functions in CKamal Acharya This document discusses different types of functions in C programming. It defines library functions, user-defined functions, and the key elements of functions like prototypes, arguments, parameters, return values. It categorizes functions based on whether they have arguments and return values. The document also explains how functions are called, either by value where changes are not reflected back or by reference where the original values are changed.
Programming in C Presentation upto FILE



Programming in C Presentation upto FILEDipta Saha Programming in C Presentation upto FILE
Facebook >> facebook.com/diptasaha.lpu.cse
Email >> [email protected]
Structures in c language



Structures in c languagetanmaymodi4 Structures in C allow the user to define a custom data type that combines different data types to represent a record. A structure is similar to an array but can contain heterogeneous data types, while an array only holds the same type. Structures are defined using the struct keyword followed by structure tags and member lists. Structure variables are declared like other variables and members can be accessed using the dot operator. Arrays of structures and nested structures are also supported.
Call by value



Call by valueDharani G The document discusses call by value and call by reference in functions. Call by value passes the actual value of an argument to the formal parameter, so any changes made to the formal parameter do not affect the actual argument. Call by reference passes the address of the actual argument, so changes to the formal parameter do directly modify the actual argument. An example program demonstrates call by value, where changing the formal parameter does not change the original variable.
Variables in C Programming



Variables in C Programmingprogramming9 This document discusses variables in C programming. It explains that variables are names that refer to memory locations where values can be stored and changed during program execution. It provides the syntax for declaring variables using different data types like int, float, double, and char. Rules for variable names are also outlined, such as starting with a letter or underscore and avoiding reserved words.
classes and objects in C++



classes and objects in C++HalaiHansaika Classes allow users to bundle data and functions together. A class defines data members and member functions. Data members store data within each object, while member functions implement behaviors. Classes support access specifiers like public and private to control access to members. Objects are instances of classes that allocate memory for data members. Member functions can access object data members and are called on objects using dot notation. Friend functions allow non-member functions to access private members of classes.
SPL 9 | Scope of Variables in C



SPL 9 | Scope of Variables in CMohammad Imam Hossain The document discusses scope of variables in programming languages. There are three scopes where variables can be declared: local within a function/block, global outside all functions, and as function parameters. Local variables are only accessible within their declaration block, while global variables can be accessed anywhere after declaration. The document provides examples demonstrating how variables with the same name in different scopes do not conflict, and how local variables take precedence over global variables of the same name.
MULTI THREADING IN JAVA



MULTI THREADING IN JAVAVINOTH R This document provides an overview of threads in Java, including:
- Threads allow for multitasking by executing multiple processes simultaneously. They are lightweight processes that exist within a process and share system resources.
- Threads can be created by extending the Thread class or implementing the Runnable interface. The run() method defines the code executed by the thread.
- Threads transition between states like new, runnable, running, blocked, and dead during their lifecycle. Methods like start(), sleep(), join(), etc. impact the thread states.
- Synchronization is used to control access to shared resources when multiple threads access methods and data outside their run() methods. This prevents issues like inconsistent data.
Strings in C



Strings in CKamal Acharya Strings are arrays of characters that are null-terminated. They can be manipulated using functions like strlen(), strcpy(), strcat(), and strcmp(). The document discusses initializing and reading strings, passing strings to functions, and using string handling functions to perform operations like copying, concatenating, comparing, and reversing strings. It also describes arrays of strings, which are 2D character arrays used to store multiple strings. Examples are provided to demonstrate reading and sorting arrays of strings.
Operators in java



Operators in javaThen Murugeshwari Operators in Java provide symbols that operate on arguments to produce results. The document discusses the different types of operators in Java including assignment, arithmetic, relational, logical, bitwise, and ternary operators. Examples are provided to demonstrate the usage of various operators like increment/decrement, arithmetic, relational, logical, bitwise, ternary, and instanceof operators in Java code.
Variables in C and C++ Language



Variables in C and C++ LanguageWay2itech This document discusses key concepts in C programming including variables, data types, constants, keywords, comments, and rules for writing C programs. It defines variables as containers for storing data in memory locations. It describes predefined data types like char, int, float, and double as well as derived and user-defined data types. It also covers identifiers, declarations, initialization, keywords, constants, comments, and general rules for writing C programs.
Pointers in c++



Pointers in c++Vineeta Garg Pointer is a variable that stores the memory address of another variable. It allows dynamic memory allocation and access of memory locations. There are three ways to pass arguments to functions in C++ - pass by value, pass by reference, and pass by pointer. Pass by value copies the value, pass by reference copies the address, and pass by pointer passes the address of the argument. Pointers can also point to arrays or strings to access elements. Arrays of pointers can store multiple strings. References are alternative names for existing variables and any changes made using the reference affect the original variable. Functions can return pointers or references.
Java program structure



Java program structureshalinikarunakaran1 The document discusses the structure of a Java program. A Java program contains classes, with one class containing a main method that acts as the starting point. Classes contain data members and methods that operate on the data. Methods contain declarations and executable statements. The structure also includes sections for documentation, package statements, import statements, interface statements, and class definitions, with the main method class being essential.
C++ Overview PPT



C++ Overview PPTThooyavan Venkatachalam C++ is an object-oriented programming language that was created as an extension of C programming language. It was created by Bjarne Stroustrup in 1979 at Bell Labs. Some key differences between C and C++ include C++ supporting object-oriented programming concepts like classes, inheritance and polymorphism, while C is a procedural language. Pointers and references are commonly used in C++ to pass arguments to functions by reference rather than by value. Arrays and functions are also important elements of C++ programs.
Basics of c++ Programming Language



Basics of c++ Programming LanguageAhmad Idrees The aim of this list of programming languages is to include all notable programming languages in existence, both those in current use and ... Note: This page does not list esoteric programming languages. .... Computer programming portal ...
File handling in c



File handling in caakanksha s File handling in C programming uses file streams as the means of communication between programs and data files. The input stream extracts data from files and supplies it to the program, while the output stream stores data from the program into files. To handle file input/output, header file fstream.h is included, which contains ifstream and ofstream classes. Common file operations include opening, reading, writing, and closing files using functions like fopen(), fgetc(), fputs(), fclose(), and checking for end-of-file conditions. Files can be opened in different modes like read, write, append depending on the operation to be performed.
Object Oriented Programming Using C++



Object Oriented Programming Using C++Muhammad Waqas This Powerpoint presentation covers following topics of C Plus Plus:
Features of OOP
Classes in C++
Objects & Creating the Objects
Constructors & Destructors
Friend Functions & Classes
Static data members & functions
Similar to File handling in c (20)
Mesics lecture files in 'c'



Mesics lecture files in 'c'eShikshak The document discusses files and streams in C language. It explains that a file is a collection of bytes stored on a secondary storage device and has different types like data, text, program etc. It also describes streams as a series of bytes flowing between a program and file. The key functions for working with files and streams in C like fopen(), fclose(), fread(), fwrite() are explained along with their usage.
Presentation of file handling in C language



Presentation of file handling in C languageShruthi48 A file is a collection of bytes stored on a secondary storage device. There are different types of files like data files, text files, program files, and directory files. A file has a beginning and end, and its current position can be tracked using a marker. Files can be accessed sequentially for text or randomly for binary data. To perform operations on a file, it must first be opened by declaring a file pointer and bringing it into memory. Common file operations include reading, writing, modifying, and closing a file.
Unit-VI.pptx



Unit-VI.pptxMehul Desai Unit-VI discusses files in C programming. A file is a collection of related records stored permanently on secondary storage devices like hard disks. There are several file operations in C - opening a file using fopen(), reading the file using fgetc(), and closing it using fclose(). Different text modes like w, r, a, w+, a+ are used for opening files for write, read, append, write and read, append and read operations respectively. Programs are provided to demonstrate opening, writing, reading and closing files in various modes.
Programming C- File Handling , File Operation



Programming C- File Handling , File Operationsvkarthik86 Programming C- File Handling , File Operation
File handling in C hhsjsjshsjjsjsjs.pptx



File handling in C hhsjsjshsjjsjsjs.pptxarmaansohail9356 File handling in C allows storing program data in files that can be accessed later. There are two main file types: text files containing human-readable ASCII characters and binary files containing 0s and 1s in a non-human-readable format. Common file operations in C include creating, opening, writing, reading, moving within and closing files using functions like fopen(), fprintf(), fscanf(), fputc(), fgetc(), fclose(), and fseek(). A file pointer references an opened file and is required for read/write operations.
FILES IN C



FILES IN Cyndaravind fread() and fwrite() are functions used to read and write structured data from files. fread() reads an entire structure block from a file into memory. fwrite() writes an entire structure block from memory to a file. These functions allow efficient reading and writing of complex data types like structures and arrays from binary files.
Lecture 20 - File Handling



Lecture 20 - File HandlingMd. Imran Hossain Showrov C Programming Language is the most popular computer language and most used programming language till now. It is very simple and elegant language. This lecture series will give you basic concepts of structured programming language with C.
PPS PPT 2.pptx



PPS PPT 2.pptxSandeepbhuma1 File handling in C allows programs to permanently store and retrieve large amounts of data from files. Files must be opened before use and closed after to ensure data is properly written. Basic file operations include opening, reading, writing, and closing files. Functions like fopen open a file and return a file pointer. fread and fwrite can read and write arrays of data. An example shows merging two text files containing numbers into a single output file by comparing the numbers and writing the smaller value.
File handling-c



File handling-cCGC Technical campus,Mohali The document discusses file management in C. It defines a file as a collection of related data treated as a single unit by computers. C uses the FILE structure to store file attributes. The document outlines opening, reading, writing and closing files in C using functions like fopen(), fclose(), fread(), fwrite(), fseek(), ftell() and handling errors. It also discusses reading/writing characters using getc()/putc() and integers using getw()/putw() as well as formatted input/output with fscanf() and fprintf(). Random access to files using fseek() is also covered.
Unit 8



Unit 8Keerthi Mutyala 1) A file stores related data permanently on secondary storage like hard disks. It supports volatile main memory by storing data when the system shuts down.
2) A file name typically contains a primary name and optional extension separated by a period. File information like name and read/write position is stored in a file information table.
3) Standard input, output, and error streams (stdin, stdout, stderr) allow programs to read from and write to files and devices. Functions like fopen(), fclose(), fread(), fwrite() manage file access.
File management



File managementsumathiv9 File management functions in C allow programs to work with files. They provide functions to open, read, write, and close files. Some key functions include fopen() to open a file, fread() and fwrite() to read from and write to files, and fclose() to close a file. Files can be opened in different modes like read, write, append depending on whether the file needs to be read from or written to. Command line arguments allow passing of inputs to a program from the command line when it is launched.
COM1407: File Processing 



COM1407: File Processing Hemantha Kulathilake At the end of this lecture students should be able to;
Define the C standard functions for managing file input output.
Apply taught concepts for writing programs.
File handling



File handlingAns Ali File handling in C allows programs to read from and write to files. A file contains related data treated as a single unit that is stored in secondary storage. C uses the FILE structure to represent an opened file and track attributes. The basic file operations are opening a file with fopen, reading/writing with fread/fwrite, seeking position with fseek, getting position with ftell, and closing with fclose. Files can be opened in different modes like read, write, append to specify how the file will be used.
File Handling as 08032021 (1).ppt



File Handling as 08032021 (1).pptRaja Ram Dutta This document discusses file handling in Python. File handling allows Python programs to read from and write data to disk files for permanent storage. The open() function is used to open a file and return a file object, which has methods like read(), write(), close() to interact with the file. Files can be opened in different modes like read, write, append. The read() method reads from the file while write() writes to it. Files must be closed using close() after processing to flush buffers and close the file properly.
Python Files I_O17.pdf



Python Files I_O17.pdfRashmiAngane1 This document discusses Python's built-in functions and methods for performing input/output operations (I/O) and manipulating files and directories. It covers printing to the screen, reading keyboard input, opening and closing files, reading and writing files, file positions, renaming and deleting files, and creating, removing, and changing directories.
Module 5 file cp



Module 5 file cpAmarjith C K 1. A file represents a sequence of bytes that can store data even if a program terminates. There are two types of files: text files containing plain text and binary files containing data in binary form (0s and 1s).
2. Common file operations include opening, closing, reading, and writing files. Functions like fopen(), fclose(), fgetc(), fputc(), fread(), and fwrite() are used to perform these operations.
3. Files allow permanent storage of data that can be accessed and transferred between computers. Programs demonstrate how to perform tasks like reading a file, copying file contents, finding the largest number in a file, and appending data to an existing file.
File Handling in C



File Handling in CVrushaliSolanke This document provides an overview of file handling in C programming, including:
1. Definitions of files, streams, and file opening modes. It describes text and binary files and the functions used to open, read, write, and close files.
2. Examples of using functions like fopen(), fclose(), fgetc(), fputs(), fscanf(), fprintf() to perform operations on files.
3. Descriptions of error handling and examples of checking for errors and using errno to identify issues.
Python file handlings



Python file handlings22261A1201ABDULMUQTA The document discusses Python's built-in functions and methods for reading, writing, and manipulating files and directories. It explains how to open and close files, read and write file contents, check file positions, rename and delete files, create and remove directories, and get the current working directory using functions like open(), close(), read(), write(), tell(), seek(), os.rename(), os.remove(), os.mkdir(), os.chdir(), and os.getcwd(). It also covers the different modes for opening files and lists attributes of file objects.
File handling3 (1).pdf uhgipughserigrfiogrehpiuhnfi;reuge



File handling3 (1).pdf uhgipughserigrfiogrehpiuhnfi;reugevsol7206 ginoegnareo;nbrawo;ignhwbouhnfo;gklnvsfoirughnifkirhgnbfklnirghisfbksior'bhjinsorkflbinejtrhobfknaehiorhnbfklraioen
Ad
More from David Livingston J (9)
Performing Addition and Subtraction on Integers



Performing Addition and Subtraction on IntegersDavid Livingston J This presentation introduces Integers as well as explains how to
perform Addition and Subtraction on Integers.
Introduction to Bluetooth technology



Introduction to Bluetooth technologyDavid Livingston J Bluetooth is a wireless technology developed in 1994 that allows electronic devices such as computers, phones, and other home appliances to connect without wires. It uses short-range radio transmissions to communicate and establish connections between devices within about 30 feet of each other. Bluetooth aims to eliminate cable clutter and enable easy data transfer and synchronization between devices. While it faces some security issues, Bluetooth's ability to connect devices wirelessly positions it to become widely adopted in homes and businesses.
Wireless LAN Technoloy



Wireless LAN TechnoloyDavid Livingston J The document discusses wireless local area networks (WLANs) and the IEEE 802.11 standard. It introduces various WLAN standards including 802.11b operating at 11 Mbps in the 2.4 GHz band, 802.11a operating at up to 54 Mbps in the 5 GHz band, and 802.11g which also operates at up to 54 Mbps in the 2.4 GHz band. It describes the differences between infrastructure-based WLAN networks that use an access point and ad-hoc networks without an access point. It provides details on the IEEE 802.11 standard including the use of carrier sense multiple access with collision avoidance for medium access. It also discusses some enhancements to
Past, Present and Future of Mobile Computing



Past, Present and Future of Mobile ComputingDavid Livingston J The document provides an overview of past, present, and future mobile computing technologies. It discusses early technologies like wireless LANs and cellular networks. Current technologies covered include Bluetooth, mobile IP, wireless ad hoc networks, and RFID. The future of mobile computing is also addressed, with continued advances in areas such as increased bandwidth and integration of computing into everyday objects expected.
Introduction & history of mobile computing



Introduction & history of mobile computingDavid Livingston J The document provides a history and overview of mobile computing. It discusses how mobile computing allows transmission of data, voice and video without a fixed physical link. It defines mobility and different types of mobile devices. The document then covers wireless communication technologies and contrasts wired vs wireless networks. It discusses advantages and disadvantages of wireless networks. The document traces the evolution of wireless technology from early radio experiments to the development of cellular networks and standards.
Frequently asked questions in c



Frequently asked questions in cDavid Livingston J This document contains frequently asked questions (FAQs) in C programming. It was developed by David Livingsto J from Coimbatore, India. His contact email and blogs are provided. The FAQs cover various C programming topics like arithmetic operators, relational operators, logical operators, decision making statements, looping statements, arrays, functions, recursion, and more. Each question is followed by a detailed answer explaining the relevant concept.
Frequently asked questions in c



Frequently asked questions in cDavid Livingston J This document contains frequently asked questions about C programming. It was developed by David Livingsto J from Coimbatore, India. His contact email is provided. The document contains 20 questions about various C programming concepts like operators, expressions, decision making statements, loops, functions, arrays, and more. Each question is followed by an answer that explains the concept in 1-2 paragraphs.
Structure of a C program



Structure of a C programDavid Livingston J This document provides an overview of the basic structure and components of a C program. It discusses the main parts including preprocessor directives like #include and #define, comments, data types, variables, statements, functions, and input/output functions like printf, scanf, getchar and putchar. It explains that a C program requires a main function and can declare global variables and functions. The document also covers format specifiers and escape sequences used with functions like printf.
Problem solving using Computer



Problem solving using ComputerDavid Livingston J The document discusses problem solving using computers. It explains that programming languages allow problems to be solved repeatedly by telling the computer the logic or algorithm to follow. An algorithm is a series of steps, like pseudocode or a flowchart, that represent the procedure for solving a problem. It then provides examples of algorithms for calculating the factorial of a number in different formats, including English steps, flowcharts, and pseudocode. Programming implements the algorithm by translating it line-by-line into source code.
Ad
Recently uploaded (20)
DevOpsDays Atlanta 2025 - Building 10x Development Organizations.pptx



DevOpsDays Atlanta 2025 - Building 10x Development Organizations.pptxJustin Reock Building 10x Organizations with Modern Productivity Metrics
10x developers may be a myth, but 10x organizations are very real, as proven by the influential study performed in the 1980s, ‘The Coding War Games.’
Right now, here in early 2025, we seem to be experiencing YAPP (Yet Another Productivity Philosophy), and that philosophy is converging on developer experience. It seems that with every new method we invent for the delivery of products, whether physical or virtual, we reinvent productivity philosophies to go alongside them.
But which of these approaches actually work? DORA? SPACE? DevEx? What should we invest in and create urgency behind today, so that we don’t find ourselves having the same discussion again in a decade?
Transcript: #StandardsGoals for 2025: Standards & certification roundup - Tec...



Transcript: #StandardsGoals for 2025: Standards & certification roundup - Tec...BookNet Canada Book industry standards are evolving rapidly. In the first part of this session, we’ll share an overview of key developments from 2024 and the early months of 2025. Then, BookNet’s resident standards expert, Tom Richardson, and CEO, Lauren Stewart, have a forward-looking conversation about what’s next.
Link to recording, presentation slides, and accompanying resource: https://bnctechforum.ca/sessions/standardsgoals-for-2025-standards-certification-roundup/
Presented by BookNet Canada on May 6, 2025 with support from the Department of Canadian Heritage.
Noah Loul Shares 5 Steps to Implement AI Agents for Maximum Business Efficien...



Noah Loul Shares 5 Steps to Implement AI Agents for Maximum Business Efficien...Noah Loul Artificial intelligence is changing how businesses operate. Companies are using AI agents to automate tasks, reduce time spent on repetitive work, and focus more on high-value activities. Noah Loul, an AI strategist and entrepreneur, has helped dozens of companies streamline their operations using smart automation. He believes AI agents aren't just tools—they're workers that take on repeatable tasks so your human team can focus on what matters. If you want to reduce time waste and increase output, AI agents are the next move.
Mobile App Development Company in Saudi Arabia



Mobile App Development Company in Saudi ArabiaSteve Jonas EmizenTech is a globally recognized software development company, proudly serving businesses since 2013. With over 11+ years of industry experience and a team of 200+ skilled professionals, we have successfully delivered 1200+ projects across various sectors. As a leading Mobile App Development Company In Saudi Arabia we offer end-to-end solutions for iOS, Android, and cross-platform applications. Our apps are known for their user-friendly interfaces, scalability, high performance, and strong security features. We tailor each mobile application to meet the unique needs of different industries, ensuring a seamless user experience. EmizenTech is committed to turning your vision into a powerful digital product that drives growth, innovation, and long-term success in the competitive mobile landscape of Saudi Arabia.
Big Data Analytics Quick Research Guide by Arthur Morgan



Big Data Analytics Quick Research Guide by Arthur MorganArthur Morgan This is a Quick Research Guide (QRG).
QRGs include the following:
- A brief, high-level overview of the QRG topic.
- A milestone timeline for the QRG topic.
- Links to various free online resource materials to provide a deeper dive into the QRG topic.
- Conclusion and a recommendation for at least two books available in the SJPL system on the QRG topic.
QRGs planned for the series:
- Artificial Intelligence QRG
- Quantum Computing QRG
- Big Data Analytics QRG
- Spacecraft Guidance, Navigation & Control QRG (coming 2026)
- UK Home Computing & The Birth of ARM QRG (coming 2027)
Any questions or comments?
- Please contact Arthur Morgan at [email protected].
100% human made.
Linux Support for SMARC: How Toradex Empowers Embedded Developers



Linux Support for SMARC: How Toradex Empowers Embedded DevelopersToradex Toradex brings robust Linux support to SMARC (Smart Mobility Architecture), ensuring high performance and long-term reliability for embedded applications. Here’s how:
• Optimized Torizon OS & Yocto Support – Toradex provides Torizon OS, a Debian-based easy-to-use platform, and Yocto BSPs for customized Linux images on SMARC modules.
• Seamless Integration with i.MX 8M Plus and i.MX 95 – Toradex SMARC solutions leverage NXP’s i.MX 8 M Plus and i.MX 95 SoCs, delivering power efficiency and AI-ready performance.
• Secure and Reliable – With Secure Boot, over-the-air (OTA) updates, and LTS kernel support, Toradex ensures industrial-grade security and longevity.
• Containerized Workflows for AI & IoT – Support for Docker, ROS, and real-time Linux enables scalable AI, ML, and IoT applications.
• Strong Ecosystem & Developer Support – Toradex offers comprehensive documentation, developer tools, and dedicated support, accelerating time-to-market.
With Toradex’s Linux support for SMARC, developers get a scalable, secure, and high-performance solution for industrial, medical, and AI-driven applications.
Do you have a specific project or application in mind where you're considering SMARC? We can help with Free Compatibility Check and help you with quick time-to-market
For more information: https://www.toradex.com/computer-on-modules/smarc-arm-family
#StandardsGoals for 2025: Standards & certification roundup - Tech Forum 2025



#StandardsGoals for 2025: Standards & certification roundup - Tech Forum 2025BookNet Canada Book industry standards are evolving rapidly. In the first part of this session, we’ll share an overview of key developments from 2024 and the early months of 2025. Then, BookNet’s resident standards expert, Tom Richardson, and CEO, Lauren Stewart, have a forward-looking conversation about what’s next.
Link to recording, transcript, and accompanying resource: https://bnctechforum.ca/sessions/standardsgoals-for-2025-standards-certification-roundup/
Presented by BookNet Canada on May 6, 2025 with support from the Department of Canadian Heritage.
AI and Data Privacy in 2025: Global Trends



AI and Data Privacy in 2025: Global TrendsInData Labs In this infographic, we explore how businesses can implement effective governance frameworks to address AI data privacy. Understanding it is crucial for developing effective strategies that ensure compliance, safeguard customer trust, and leverage AI responsibly. Equip yourself with insights that can drive informed decision-making and position your organization for success in the future of data privacy.
This infographic contains:
-AI and data privacy: Key findings
-Statistics on AI data privacy in the today’s world
-Tips on how to overcome data privacy challenges
-Benefits of AI data security investments.
Keep up-to-date on how AI is reshaping privacy standards and what this entails for both individuals and organizations.
Generative Artificial Intelligence (GenAI) in Business



Generative Artificial Intelligence (GenAI) in BusinessDr. Tathagat Varma My talk for the Indian School of Business (ISB) Emerging Leaders Program Cohort 9. In this talk, I discussed key issues around adoption of GenAI in business - benefits, opportunities and limitations. I also discussed how my research on Theory of Cognitive Chasms helps address some of these issues
Special Meetup Edition - TDX Bengaluru Meetup #52.pptx



Special Meetup Edition - TDX Bengaluru Meetup #52.pptxshyamraj55 We’re bringing the TDX energy to our community with 2 power-packed sessions:
🛠️ Workshop: MuleSoft for Agentforce
Explore the new version of our hands-on workshop featuring the latest Topic Center and API Catalog updates.
📄 Talk: Power Up Document Processing
Dive into smart automation with MuleSoft IDP, NLP, and Einstein AI for intelligent document workflows.
AI EngineHost Review: Revolutionary USA Datacenter-Based Hosting with NVIDIA ...



AI EngineHost Review: Revolutionary USA Datacenter-Based Hosting with NVIDIA ...SOFTTECHHUB I started my online journey with several hosting services before stumbling upon Ai EngineHost. At first, the idea of paying one fee and getting lifetime access seemed too good to pass up. The platform is built on reliable US-based servers, ensuring your projects run at high speeds and remain safe. Let me take you step by step through its benefits and features as I explain why this hosting solution is a perfect fit for digital entrepreneurs.
tecnologias de las primeras civilizaciones.pdf



tecnologias de las primeras civilizaciones.pdffjgm517 descaripcion detallada del avance de las tecnologias en mesopotamia, egipto, roma y grecia.
Complete Guide to Advanced Logistics Management Software in Riyadh.pdf



Complete Guide to Advanced Logistics Management Software in Riyadh.pdfSoftware Company Explore the benefits and features of advanced logistics management software for businesses in Riyadh. This guide delves into the latest technologies, from real-time tracking and route optimization to warehouse management and inventory control, helping businesses streamline their logistics operations and reduce costs. Learn how implementing the right software solution can enhance efficiency, improve customer satisfaction, and provide a competitive edge in the growing logistics sector of Riyadh.
Dev Dives: Automate and orchestrate your processes with UiPath Maestro



Dev Dives: Automate and orchestrate your processes with UiPath MaestroUiPathCommunity This session is designed to equip developers with the skills needed to build mission-critical, end-to-end processes that seamlessly orchestrate agents, people, and robots.
📕 Here's what you can expect:
- Modeling: Build end-to-end processes using BPMN.
- Implementing: Integrate agentic tasks, RPA, APIs, and advanced decisioning into processes.
- Operating: Control process instances with rewind, replay, pause, and stop functions.
- Monitoring: Use dashboards and embedded analytics for real-time insights into process instances.
This webinar is a must-attend for developers looking to enhance their agentic automation skills and orchestrate robust, mission-critical processes.
👨🏫 Speaker:
Andrei Vintila, Principal Product Manager @UiPath
This session streamed live on April 29, 2025, 16:00 CET.
Check out all our upcoming Dev Dives sessions at https://community.uipath.com/dev-dives-automation-developer-2025/.
Manifest Pre-Seed Update | A Humanoid OEM Deeptech In France



Manifest Pre-Seed Update | A Humanoid OEM Deeptech In Francechb3 The latest updates on Manifest's pre-seed stage progress.
IEDM 2024 Tutorial2_Advances in CMOS Technologies and Future Directions for C...



IEDM 2024 Tutorial2_Advances in CMOS Technologies and Future Directions for C...organizerofv IEDM 2024 Tutorial2
Increasing Retail Store Efficiency How can Planograms Save Time and Money.pptx



Increasing Retail Store Efficiency How can Planograms Save Time and Money.pptxAnoop Ashok In today's fast-paced retail environment, efficiency is key. Every minute counts, and every penny matters. One tool that can significantly boost your store's efficiency is a well-executed planogram. These visual merchandising blueprints not only enhance store layouts but also save time and money in the process.
Linux Professional Institute LPIC-1 Exam.pdf



Linux Professional Institute LPIC-1 Exam.pdfRHCSA Guru Introduction to LPIC-1 Exam - overview, exam details, price and job opportunities
Build Your Own Copilot & Agents For Devs



Build Your Own Copilot & Agents For DevsBrian McKeiver May 2nd, 2025 talk at StirTrek 2025 Conference.
File handling in c
- 1. Developed by www.futureforyou.net & www.eshikshak.co.in
- 2. A collection of data or information that are stored on a computer known as file A file is a collection of bytes stored on a secondary storage device. There are four different types of file Data files Text files Program files Directory files Different types of file store different types of information
- 3. A file has a beginning and an end. We need a marker to mark the current position of the file from the beginning (in terms of bytes) while reading and write operation, takes place on a file. Initially the marker is at the beginning of the file. We can move the marker to any other position in the file. The new current position can be specified as an offset from the beginning the file.
- 4. A stream refers to the flow of data (in bytes) from one place to another (from program to file or vice-versa). There are two types of streams Text Stream ▪ It consists of sequence of characters ▪ Each line of characters in the stream may be terminated by a newline character. ▪ Text streams are used for textual data, which has a consistent appearance from one environment to another or from one machine to another
- 5. Binary Stream ▪ It is a series of bytes. ▪ Binary streams are primarily used for non-textual data, which is required to keep exact contents of the file.
- 7. A text file can be a stream of characters that a computer can process sequentially. It is processed only in forward direction. It is opened for one kind of operation (reading, writing, or appending) at any give time. We can read only one character at a time from a text file.
- 8. A binary file is a file consisting of collection of bytes. A binary file is also referred to as a character stream
- 11. A file is identified by its name. This name is divided into two parts File Name ▪ It consists of alphabets and digits. ▪ Special characters are also supported, but it depends on the operating system we use. Extension ▪ It describes the file type
- 12. Before opening a file, we need to declare a file pointer. A file pointer is a pointer variable of type FILE, which is defined in the “stdio.h” header file. A file pointer has the complete information about file being opened and processed such as: Name of file, mode it is opened in, starting buffer address, a character pointer that points to the character being read.
- 13. To perform any operation (read or write) on a file, the file must be brought into memory from the storage device (hard disk). This process of bringing the copy of the file from disk (secondary storage) to memory (main storage) is called opening the file.
- 14. Mode Meaning r Open a text file for reading only. If the file doesn’t exist, it returns null. w Opens a file for writing only. If file exists, than all the contents of that file are destroyed and new fresh blank file is copied on the disk and memory with same name If file dosen’t exists, a new blank file is created and opened for writing. Returns NULL if it is unable to open the file a Appends to the existing text file Adds data at the end of the file. If file doesn’t exists then a new file is created. Returns NULL if it is unable to open the file. rb Open a binary file for reading wb Open a binary file for reading ab Append to a binary file r+ Open a text file for read/write w+ Opens the existing text file or Creates a text file for read/write
- 15. Mode Meaning a+ Append or create a text file for read/write r+b Open a binary file for read/write w+b Create a binary file for read/write a+b Append a binary file for read/write
- 16. fopen() function, like all the other file-system functions, uses the head file stdio.h The name of the file to be opened is pointed to by fname The string given as the second parameter - for mode, determines how the file should be accessed (r-read, w-write a-append).
- 17. FILE *fp; if(fp = fopen(“myfile”,”r”)) == NULL) { printf(“Error opening a file”); exit(1); }
- 18. To read contents from an existing file, we need to open that file in read mode that means “r” mode Algorithm to read data from a file: 1. Open the file in read mode 2. Read data from the file 3. Write the data into an output device 4. Repeat steps 3 and 4 untill the end of file occurs 5. Stop procedure
- 19. #include<stdio.h> void main() { FILE *fp; char ch; fp=fopen(“clear.c”,”r”); if(fp==NULL) print(“Unable to open clear.c”); else { do { ch = getc(fp); putchar(ch); }while(ch!=EOF); fclose(fp); } }
- 20. Generally, a file contains a large amount of data. In a large file, it is difficult to detect the end of file while reading. In order to mark the end of a text file, a special character EOF is stored at the end.
- 21. To close a file and dis-associate it with a stream (file pointer), use fclose() function. fclose() returns 0 if the file is closed successfully The fcloseall() closes all the files opened previously.
- 22. #include<stdio.h> void main() { FILE *fp; char ch; fp=fopen(“clear.c”,”r”); if(fp==NULL) print(“Unable to open clear.c”); else { do { ch = getc(fp);// gets the character from file putchar(ch); }while(ch!=EOF); fclose(fp); } }
- 23. We can add contents to an existing file whenever required. Perform the following steps to append an existing file: 1. Declare a file pointer 2. Open the file in append mode 3. Read data from the keyboard 4. Write it into the file 5. Repeat steps 3 and 4 according to until the user gives input 6. Stop the process
- 24. char *fgets(char *str, int n, FILE *fptr); This function reads a character from the file stream pointed by fptr and stores it in the character array ‘str’ until a new line character (n) is read or end of file (EOF) is reached or n-1 characters have been read. fputs(const char *str, FILE *fptr); This function writes data to the stream pointed to by fptr, the content of the string stored in ‘str’
- 25. #include<stdio.h> void main() { FILE *fp; char line[280];int ch, i=0; fp=fopen(“a.dat”,”a”); if(fp==NULL) print(“Unable to open clear.c”); else{ do{ do{ line[i++] = getchar(); }while(line[i-1]!=‘*’); fputs(line, fp);//Writes string to the file i=0; printf(“nPress 1 to continue”); scanf(“%d”,&ch); }while(ch==1); fclose(fp); printf(“File is successfully created”); }
- 26. A file can be accessed in two ways: Serial access Random access Generally all the text files are considered to be sequential files because lines of text (also called records) are stored in a file The beginning of each record in a sequential file is unpredictable Whereas, in random access files, all the records are in same length.
- 27. To modify the content of a file, open the file with read and write mode (“r+” or “w+” or “a+”) Generally “r+” mode is used for both reading and writing operation. The procedure is as follows: 1. Initialize a pointer variable 2. Open the file in read and write mode 3. Read data from file and Print it 4. Move the file pointer to the place where we have the data to be modified and re-write the new data in that place. 5. Repeat steps 3 and 4 till the end of file reaches. 6. Stop the Process
- 28. #include<stdio.h> struct stock { int itid, qty; char n[100]; float rate; }it; void main() { FILE *fp; int ch; int r = 0; fp = fopen(“item.c”, “r+”); if(fp==NULL) { printf(“Unable to open item.c”); } }
- 29. else{ do{ fread(&it, sizeof(it),1,fp); printf(“n%d %s %d %f”, it.itid, it.n, it.qty, it.rate); printf(“n Press 1 to change it?”); scanf(“%d”,&ch); if(ch==1) { printf(“n Enter Itemid ItemName Quantity & Price”); scanf(“%d%s%d%f”, &it.itid, it.n, &it.qty, &it.rate); fseek(fp, r*sizeof(it), 0); fwrite(&it, sizeof(it),1,fp); }r++; }while(!feof(fp)); fclose(fp); } }
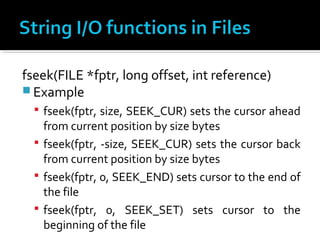
- 30. fseek(FILE *fptr, long offset, int reference) Moves the pointer from one record to another. The first argument is the file pointer The second argument tells the compiler how many bytes (offset) the pointer should be moved from a particular position. The third argument is the reference from where the pointer should be moved n bytes (specified in the offset).
- 31. fseek(FILE *fptr, long offset, int reference) The third argument is the reference from where the pointer should be moved n bytes as specified in the offset. SEEK_END moves the pointer from the end marker SEEK_CUR moves the pointer from the current position SEEK_SET moves the pointer from the beginning of the file
- 32. fseek(FILE *fptr, long offset, int reference) Example fseek(fptr, size, SEEK_CUR) sets the cursor ahead from current position by size bytes fseek(fptr, -size, SEEK_CUR) sets the cursor back from current position by size bytes fseek(fptr, 0, SEEK_END) sets cursor to the end of the file fseek(fptr, 0, SEEK_SET) sets cursor to the beginning of the file

