Firewall in Perl by Chankey Pathak
Download as PPTX, PDF0 likes1,765 views
A software firewall inspects incoming and outgoing network packets to determine whether they should be allowed or blocked based on configured firewall rules. The document describes a training report on implementing a graphical user interface (GUI) version of iptables using Perl and the dialog tool. Key features of the SYS firewall implemented include authorizing users, limiting service access, filtering packets, network address translation (NAT), and masquerading. The GUI allows configuring and customizing firewall rules to block ping requests, drop all policies, and implement SNAT, masquerading, and DNAT.
1 of 25
Downloaded 28 times























Ad
Recommended
kali linix



kali linixMirza Baig This document provides an overview of the Kali Linux operating system. Kali Linux is a Linux distribution designed for penetration testing and security auditing. It includes over 600 security tools for tasks like penetration testing, forensics, and reverse engineering. Some key features of Kali Linux include tools for wireless attacks, a customized kernel, and strict security measures like disabled network services by default. The document discusses whether Kali Linux is suitable and provides advantages like helping find security vulnerabilities, and disadvantages like not functioning as a normal OS. Hardware requirements and legal warnings are also outlined.
kali linux 



kali linux Avinash Hanwate Kali Linux is an advanced Penetration Testing and Security Auditing Linux distribution (distro).
Named after a Hindu goddess.
It was designed to replace the BackTrack 6 Linux distro.
Developed by Mati Aharoni (muts), Devon Kearns (dookie) and, Raphaël Hertzog (bux) of Offensive Security.
UNIX > Linux > BackTrack > Kali.
kali linux



kali linuxDarshan Dalwadi Kali Linux is a Debian-derived Linux distribution designed for digital forensics and penetration testing. It contains over 300 security tools for tasks like wireless hacking, server exploitation, and web application testing. It is maintained by Offensive Security and provides a customizable, free, and open-source platform for security professionals and novices alike to conduct testing and research. Some key features include preinstalled security tools like nmap and Wireshark, support for multiple architectures and devices, and certification courses offered through Offensive Security.
Kali linux



Kali linuxAadhithyanPandian Kali Linux is a Debian-derived Linux distribution designed for digital forensics and penetration testing. It contains over 600 pre-installed penetration testing programs and is completely customizable with multilingual support. Kali Linux is focused on tools for network security assessments, penetration testing, and vulnerability assessments through programs like Nmap, Aircrack-ng, Nessus, and THC Hydra. The distribution is optimized for penetration testing and digital forensics and aims to provide industry standard tools for assessing network security.
Kali linux



Kali linuxfutaimbinlahej Kali Linux is a Debian-derived Linux distribution designed for digital forensics and penetration testing. It contains over 600 penetration testing tools, is free and open source, and adheres to Linux standards while supporting many wireless devices and customizing the kernel for injection. Kali Linux is maintained by Offensive Security and tailored for penetration testing professionals.
kali linux Presentaion



kali linux PresentaionDev Gandhi The document traces the origins and evolution of UNIX and Linux operating systems, culminating in the development of the Kali Linux operating system. It discusses how UNIX was developed at Bell Labs in the 1960s, and how Linux was later created by Linus Torvalds in the 1990s. It then focuses on the development of Kali Linux, which originated from the BackTrack Linux security and penetration testing distribution, and has become the premier operating system for penetration testing and security auditing.
Kali Linux



Kali LinuxShubham Agrawal Kali Linux is a Debian-derived Linux distribution designed for digital forensics and penetration testing. It contains over 600 security tools for tasks such as penetration testing, security research, computer forensics, and reverse engineering. Kali Linux is maintained by Offensive Security and led by core developer Mati Aharoni. It is based on BackTrack, an earlier Linux distro focused on hacking, and aims to provide a stable and secure platform for running security software.
Kali linux 



Kali linux Fa6ma_ This presentation is talking about Kali Linux and how we can use KALI LINUX. Kali Linux is an advanced Penetration Testing and Security Auditing Linux distribution (distro). It was designed to replace the BackTrack Linux distro. Linux is itself based off the UNIX kernel. Everyone was using it because its for free and its secure development environment.
Kali linux and some features [view in Full screen mode]![Kali linux and some features [view in Full screen mode]](https://cdn.slidesharecdn.com/ss_thumbnails/kali-171205224458-thumbnail.jpg?width=560&fit=bounds)
![Kali linux and some features [view in Full screen mode]](https://cdn.slidesharecdn.com/ss_thumbnails/kali-171205224458-thumbnail.jpg?width=560&fit=bounds)
![Kali linux and some features [view in Full screen mode]](https://cdn.slidesharecdn.com/ss_thumbnails/kali-171205224458-thumbnail.jpg?width=560&fit=bounds)
![Kali linux and some features [view in Full screen mode]](https://cdn.slidesharecdn.com/ss_thumbnails/kali-171205224458-thumbnail.jpg?width=560&fit=bounds)
Kali linux and some features [view in Full screen mode]abdou Bahassou This is a short presentation about Kali Linux and some of it's features , some reasons why i should use Linux in general and more ...
Kali linux



Kali linuxafraalfalasii Kali Linux is a Debian-derived Linux distribution designed for digital forensics and penetration testing. It is preinstalled with over 600 penetration testing programs and based on Debian Jessie. Kali Linux supports 32- and 64-bit images for x86 systems as well as ARM architectures like BeagleBoard and Samsung Chromebook. It has a dedicated project for porting to Android devices called Kali NetHunter, which enables wireless attacks and Bad USB attacks from Nexus devices.
CNIT 123: Ch 9: Embedded Operating Systems: The Hidden Threat



CNIT 123: Ch 9: Embedded Operating Systems: The Hidden ThreatSam Bowne This document discusses embedded operating systems and their vulnerabilities. It begins with an introduction to embedded OSs, what they are, and where they are used. It then describes several specific embedded OSs like Windows CE, VxWorks, and various Linux-based systems. It outlines some common vulnerabilities of embedded OSs like being unpatchable and having shared code with more widely used systems. Examples are given of attacks on embedded systems controlling infrastructure. The document concludes with best practices for securing embedded OSs like inventorying all systems, least privileges, encryption, and keeping systems up to date.
Kali linux summarised



Kali linux summarisedSanchit Srivastava Kali Linux is a Debian-based Linux distribution designed for digital forensics and penetration testing. It is maintained by Offensive Security and is a rewrite of their previous distribution, BackTrack. Kali Linux includes over 600 penetration testing tools and can run natively, from a live USB/CD, or in a virtual machine. It is specialized for penetration testing and forensics, unlike the more general purpose Ubuntu distribution. Common penetration testing tools included are nmap, Wireshark, John the Ripper, and Aircrack-ng for wireless assessments. Packet injection allows sending frames in monitor mode for wireless attacks like impersonation and deauthentication. The Alfa Network wireless adapter is often used for wireless hacks with its high
Kali linux



Kali linuxHarsh Gor This document provides an overview of the Kali Linux operating system. It describes Kali Linux as a Debian-based distribution aimed at advanced penetration testing and security auditing. It contains hundreds of tools for tasks like penetration testing, forensics, and reverse engineering. Kali Linux is developed and maintained by Offensive Security and was created as a rebuild of BackTrack Linux, with its first version releasing in 2013. It highlights some of Kali Linux's core developers and features, such as over 600 preinstalled applications, support for multiple languages and wireless devices, and flexibility in running on physical/virtual machines or mobile devices.
[Wroclaw #8] IPMI appsec - an express train to hell![[Wroclaw #8] IPMI appsec - an express train to hell](https://cdn.slidesharecdn.com/ss_thumbnails/ipmi-180407090718-thumbnail.jpg?width=560&fit=bounds)
![[Wroclaw #8] IPMI appsec - an express train to hell](https://cdn.slidesharecdn.com/ss_thumbnails/ipmi-180407090718-thumbnail.jpg?width=560&fit=bounds)
![[Wroclaw #8] IPMI appsec - an express train to hell](https://cdn.slidesharecdn.com/ss_thumbnails/ipmi-180407090718-thumbnail.jpg?width=560&fit=bounds)
![[Wroclaw #8] IPMI appsec - an express train to hell](https://cdn.slidesharecdn.com/ss_thumbnails/ipmi-180407090718-thumbnail.jpg?width=560&fit=bounds)
[Wroclaw #8] IPMI appsec - an express train to hellOWASP This document discusses IPMI (Intelligence Platform Management Interface), which allows remote management of servers through an embedded system on the motherboard called BMC (Baseboard Management Controller). It notes that IPMI uses UDP port 623 and has vulnerabilities like default passwords and cipher zero authentication. The document demonstrates exploiting these to modify passwords, create users, and dump hashes. It recommends disconnecting IPMI from the internet or whitelisting IPs, keeping IPMI software updated, and implementing security best practices like unique administrator accounts and access control as countermeasures. In summary, it warns that IPMI provides full remote access invisible to the OS, like a "parasite inside" a computer that owners cannot fix or patch themselves.
Kalilinux



Kalilinuxhaha loser Kali Linux is a Debian-derived Linux distribution designed for penetration testing and digital forensics. It is maintained by Offensive Security and contains over 300 security and forensics tools. Kali Linux originated from previous penetration testing distributions like BackTrack, which it replaced in 2013. Some key features of Kali Linux include being preinstalled with tools like nmap, Wireshark, and John the Ripper, as well as supporting live booting, virtual machines, and ARM devices like Raspberry Pi.
CNIT 123: Ch 13: Network Protection Systems



CNIT 123: Ch 13: Network Protection SystemsSam Bowne Routers, firewalls, intrusion detection systems, honeypots, and other security devices can be used to protect networks. Routers direct network traffic using routing protocols and access lists. Firewalls control access to internal networks using packet filtering, stateful inspection, and application inspection. Intrusion detection systems monitor network traffic for suspicious activity and generate alerts. Honeypots are decoy systems used to attract and study hackers without exposing real systems to risk. These security devices provide layered defenses to enhance network protection.
Intel's Out of the Box Network Developers Ireland Meetup on March 29 2017 - ...



Intel's Out of the Box Network Developers Ireland Meetup on March 29 2017 - ...Haidee McMahon For details on Intel's Out of The Box Network Developers Ireland meetup, goto https://www.meetup.com/Out-of-the-Box-Network-Developers-Ireland/events/237726826/
Openet Talk : How vendors on-board solutions and define their attributes in the VNFD such as DPDK
By Aidan Molloy, Senior Director, NFV Strategy at Openet Accelerate
Bio: Aidan Molloy joined Openet in 2012, and currently serves as our Senior Director NFV Strategy in Openet Accelerate, a BU dedicated to NFV adoption since 2016. He is responsible for Openet Products in the NFV framework and more specifically MANO layer with Openet Weaver® as a G-VNFM. Prior to this, Mr Molloy has served in a number of roles for Openet, including, Product Management, Technical Sales Support and Operations. More information can be found at: http:/accelerate.openet.com/
07182013 Hacking Appliances: Ironic exploits in security products



07182013 Hacking Appliances: Ironic exploits in security productsNCC Group The document discusses security vulnerabilities found in various security appliance products. It describes easy password attacks, cross-site scripting vulnerabilities with session hijacking, lack of account lockouts, and other issues found across email/web filtering, firewall, and remote access appliances from vendors like Barracuda, Symantec, Trend Micro, Sophos, Citrix, and others. Many appliances were found to have command injection flaws allowing root access. Vendors' responses to reported vulnerabilities varied, with some issues getting addressed within months while others saw no fixes. The author advocates defense-in-depth practices and keeping appliances updated with vendor patches.
CNIT 123: 8: Desktop and Server OS Vulnerabilites



CNIT 123: 8: Desktop and Server OS VulnerabilitesSam Bowne Slides for a college course based on "Hands-On Ethical Hacking and Network Defense, Second Edition by Michael T. Simpson, Kent Backman, and James Corley -- ISBN: 1133935613
Teacher: Sam Bowne
Twitter: @sambowne
Website: https://samsclass.info/123/123_F16.shtml
Maemo 6 Platform Security



Maemo 6 Platform SecurityPeter Schneider 1) The document discusses platform security for the Maemo 6 operating system. It describes mechanisms like access control, hardware enablers, and integrity protection to secure the software platform.
2) Access control is based on a classical Unix multi-user model extended with application-level controls. Applications must declare needed resources in a manifest file.
3) Integrity protection validates executables against reference hashes stored securely to prevent offline attacks.
CNIT 125 Ch 5 Communication & Network Security (part 2 of 2)



CNIT 125 Ch 5 Communication & Network Security (part 2 of 2)Sam Bowne For a college course at Coastline Community College taught by Sam Bowne. Details at https://samsclass.info/125/125_F17.shtml
Based on: "CISSP Study Guide, Third Edition"; by Eric Conrad, Seth Misenar, Joshua Feldman; ISBN-10: 0128024372
Essential Layers of IBM i Security: IBM i Security Configuration



Essential Layers of IBM i Security: IBM i Security ConfigurationPrecisely Learn practical, sound practices for properly configuring security settings within the IBM i OS, keep the OS and PTFs up to date and user profile management considerations.
CNIT 123: Ch 6: Enumeration



CNIT 123: Ch 6: EnumerationSam Bowne This document discusses enumeration, which is the process of extracting information about network resources and user accounts. It provides examples of tools used to enumerate different operating systems, including NBTscan for Microsoft OS, null sessions, NetBIOS tools like nbtstat and net view, and Windows tools in Backtrack like Smb4K, DumpSec, and Hyena. For NetWare, it discusses tools like Novell Client. For UNIX systems it discusses the finger utility and using Nessus. It includes screenshots of enumerating devices with these various tools.
How we breach small and medium enterprises (SMEs)



How we breach small and medium enterprises (SMEs)NCC Group This document summarizes common techniques used to breach small and medium enterprises. It discusses how networks are typically assessed through discovery, vulnerability assessment, exploitation, and post-exploitation. It then outlines several weaknesses that are commonly leveraged, including lack of security patches, default credentials, excessive network footprint, lack of network segregation, exceptions in configurations, and failure to implement whitelisting over blacklisting. Specific scenarios are provided for each to illustrate how access can be gained and privilege escalated within a network. The document stresses the importance of security fundamentals like patching, access control, and network segmentation.
Palo alto outline course | Mostafa El Lathy



Palo alto outline course | Mostafa El LathyMostafa El Lathy This document provides an overview of a 150-video, 25-hour Palo Alto Networks NGFW advanced training course covering PAN-OS versions 8.0 and 8.1. The course contains 20 modules that cover topics such as networking, security policies, objects, User-ID, authentication, URL filtering, application control, certificates, threat prevention, WildFire, high availability, advanced networking, and VPN. It is designed to prepare students for the PCNSA and PCNSE certification exams but does not cover Panorama, cloud platforms, IPv6, or dynamic routing protocols.
Intoto Linley Tech Utm Architecture Presentation



Intoto Linley Tech Utm Architecture Presentationsaddepalli Presentation on different architectures to implement UTM in Multicore chips - Presentation made in Linley conference in Sanjose
Mastering checkpoint-1-basic-installation



Mastering checkpoint-1-basic-installationnetworkershome The document provides an overview of Check Point's Gaia operating system. Some key points:
- Gaia is Check Point's next generation operating system that combines the best of their SecurePlatform and IPSO operating systems.
- It supports all Check Point security appliances and products, including Software Blades, Gateways, and Security Management.
- Features include support for IPv4/IPv6, high connection capacity, load sharing, high availability, dynamic routing, easy CLI, and role-based administration.
- Gaia allows for simple upgrades from IPSO and SecurePlatform and includes automated software updates for Check Point products.
NCS: NEtwork Control System Hands-on Labs 



NCS: NEtwork Control System Hands-on Labs Cisco Canada Jason Yen, Solution Architect and Ashok Sadasivan, Solution Architect, discusses NCS: Network control systems at Cisco Connect Toronto 2015.
Database Firewall with Snort



Database Firewall with SnortNarudom Roongsiriwong, CISSP Database firewall is a useful tool that monitor databases to identify and protect against database specific attacks that mostly seek to access sensitive information stored in the databases. However the commercial database firewalls are expensive and needs specific product knowledge, while the opensource database firewalls are designed for specific opensource database servers.
In order to fulfill the need of inexpensive database firewall, Snort - an opensource IDS/IPS - is possible to achieve the goal in some scenarios with familiar rule writing. The paper will explain the limitation of Snort as a database firewall, constraints in commercial database statement and some example implementation.
Security defined routing_cybergamut_v1_1



Security defined routing_cybergamut_v1_1Joel W. King http://cybergamut.com/2014/09/technical-tuesday-28-october-2014-software-defined-networking-by-joel-king-of-world-wide-technology/
Ad
More Related Content
What's hot (20)
Kali linux and some features [view in Full screen mode]![Kali linux and some features [view in Full screen mode]](https://cdn.slidesharecdn.com/ss_thumbnails/kali-171205224458-thumbnail.jpg?width=560&fit=bounds)
![Kali linux and some features [view in Full screen mode]](https://cdn.slidesharecdn.com/ss_thumbnails/kali-171205224458-thumbnail.jpg?width=560&fit=bounds)
![Kali linux and some features [view in Full screen mode]](https://cdn.slidesharecdn.com/ss_thumbnails/kali-171205224458-thumbnail.jpg?width=560&fit=bounds)
![Kali linux and some features [view in Full screen mode]](https://cdn.slidesharecdn.com/ss_thumbnails/kali-171205224458-thumbnail.jpg?width=560&fit=bounds)
Kali linux and some features [view in Full screen mode]abdou Bahassou This is a short presentation about Kali Linux and some of it's features , some reasons why i should use Linux in general and more ...
Kali linux



Kali linuxafraalfalasii Kali Linux is a Debian-derived Linux distribution designed for digital forensics and penetration testing. It is preinstalled with over 600 penetration testing programs and based on Debian Jessie. Kali Linux supports 32- and 64-bit images for x86 systems as well as ARM architectures like BeagleBoard and Samsung Chromebook. It has a dedicated project for porting to Android devices called Kali NetHunter, which enables wireless attacks and Bad USB attacks from Nexus devices.
CNIT 123: Ch 9: Embedded Operating Systems: The Hidden Threat



CNIT 123: Ch 9: Embedded Operating Systems: The Hidden ThreatSam Bowne This document discusses embedded operating systems and their vulnerabilities. It begins with an introduction to embedded OSs, what they are, and where they are used. It then describes several specific embedded OSs like Windows CE, VxWorks, and various Linux-based systems. It outlines some common vulnerabilities of embedded OSs like being unpatchable and having shared code with more widely used systems. Examples are given of attacks on embedded systems controlling infrastructure. The document concludes with best practices for securing embedded OSs like inventorying all systems, least privileges, encryption, and keeping systems up to date.
Kali linux summarised



Kali linux summarisedSanchit Srivastava Kali Linux is a Debian-based Linux distribution designed for digital forensics and penetration testing. It is maintained by Offensive Security and is a rewrite of their previous distribution, BackTrack. Kali Linux includes over 600 penetration testing tools and can run natively, from a live USB/CD, or in a virtual machine. It is specialized for penetration testing and forensics, unlike the more general purpose Ubuntu distribution. Common penetration testing tools included are nmap, Wireshark, John the Ripper, and Aircrack-ng for wireless assessments. Packet injection allows sending frames in monitor mode for wireless attacks like impersonation and deauthentication. The Alfa Network wireless adapter is often used for wireless hacks with its high
Kali linux



Kali linuxHarsh Gor This document provides an overview of the Kali Linux operating system. It describes Kali Linux as a Debian-based distribution aimed at advanced penetration testing and security auditing. It contains hundreds of tools for tasks like penetration testing, forensics, and reverse engineering. Kali Linux is developed and maintained by Offensive Security and was created as a rebuild of BackTrack Linux, with its first version releasing in 2013. It highlights some of Kali Linux's core developers and features, such as over 600 preinstalled applications, support for multiple languages and wireless devices, and flexibility in running on physical/virtual machines or mobile devices.
[Wroclaw #8] IPMI appsec - an express train to hell![[Wroclaw #8] IPMI appsec - an express train to hell](https://cdn.slidesharecdn.com/ss_thumbnails/ipmi-180407090718-thumbnail.jpg?width=560&fit=bounds)
![[Wroclaw #8] IPMI appsec - an express train to hell](https://cdn.slidesharecdn.com/ss_thumbnails/ipmi-180407090718-thumbnail.jpg?width=560&fit=bounds)
![[Wroclaw #8] IPMI appsec - an express train to hell](https://cdn.slidesharecdn.com/ss_thumbnails/ipmi-180407090718-thumbnail.jpg?width=560&fit=bounds)
![[Wroclaw #8] IPMI appsec - an express train to hell](https://cdn.slidesharecdn.com/ss_thumbnails/ipmi-180407090718-thumbnail.jpg?width=560&fit=bounds)
[Wroclaw #8] IPMI appsec - an express train to hellOWASP This document discusses IPMI (Intelligence Platform Management Interface), which allows remote management of servers through an embedded system on the motherboard called BMC (Baseboard Management Controller). It notes that IPMI uses UDP port 623 and has vulnerabilities like default passwords and cipher zero authentication. The document demonstrates exploiting these to modify passwords, create users, and dump hashes. It recommends disconnecting IPMI from the internet or whitelisting IPs, keeping IPMI software updated, and implementing security best practices like unique administrator accounts and access control as countermeasures. In summary, it warns that IPMI provides full remote access invisible to the OS, like a "parasite inside" a computer that owners cannot fix or patch themselves.
Kalilinux



Kalilinuxhaha loser Kali Linux is a Debian-derived Linux distribution designed for penetration testing and digital forensics. It is maintained by Offensive Security and contains over 300 security and forensics tools. Kali Linux originated from previous penetration testing distributions like BackTrack, which it replaced in 2013. Some key features of Kali Linux include being preinstalled with tools like nmap, Wireshark, and John the Ripper, as well as supporting live booting, virtual machines, and ARM devices like Raspberry Pi.
CNIT 123: Ch 13: Network Protection Systems



CNIT 123: Ch 13: Network Protection SystemsSam Bowne Routers, firewalls, intrusion detection systems, honeypots, and other security devices can be used to protect networks. Routers direct network traffic using routing protocols and access lists. Firewalls control access to internal networks using packet filtering, stateful inspection, and application inspection. Intrusion detection systems monitor network traffic for suspicious activity and generate alerts. Honeypots are decoy systems used to attract and study hackers without exposing real systems to risk. These security devices provide layered defenses to enhance network protection.
Intel's Out of the Box Network Developers Ireland Meetup on March 29 2017 - ...



Intel's Out of the Box Network Developers Ireland Meetup on March 29 2017 - ...Haidee McMahon For details on Intel's Out of The Box Network Developers Ireland meetup, goto https://www.meetup.com/Out-of-the-Box-Network-Developers-Ireland/events/237726826/
Openet Talk : How vendors on-board solutions and define their attributes in the VNFD such as DPDK
By Aidan Molloy, Senior Director, NFV Strategy at Openet Accelerate
Bio: Aidan Molloy joined Openet in 2012, and currently serves as our Senior Director NFV Strategy in Openet Accelerate, a BU dedicated to NFV adoption since 2016. He is responsible for Openet Products in the NFV framework and more specifically MANO layer with Openet Weaver® as a G-VNFM. Prior to this, Mr Molloy has served in a number of roles for Openet, including, Product Management, Technical Sales Support and Operations. More information can be found at: http:/accelerate.openet.com/
07182013 Hacking Appliances: Ironic exploits in security products



07182013 Hacking Appliances: Ironic exploits in security productsNCC Group The document discusses security vulnerabilities found in various security appliance products. It describes easy password attacks, cross-site scripting vulnerabilities with session hijacking, lack of account lockouts, and other issues found across email/web filtering, firewall, and remote access appliances from vendors like Barracuda, Symantec, Trend Micro, Sophos, Citrix, and others. Many appliances were found to have command injection flaws allowing root access. Vendors' responses to reported vulnerabilities varied, with some issues getting addressed within months while others saw no fixes. The author advocates defense-in-depth practices and keeping appliances updated with vendor patches.
CNIT 123: 8: Desktop and Server OS Vulnerabilites



CNIT 123: 8: Desktop and Server OS VulnerabilitesSam Bowne Slides for a college course based on "Hands-On Ethical Hacking and Network Defense, Second Edition by Michael T. Simpson, Kent Backman, and James Corley -- ISBN: 1133935613
Teacher: Sam Bowne
Twitter: @sambowne
Website: https://samsclass.info/123/123_F16.shtml
Maemo 6 Platform Security



Maemo 6 Platform SecurityPeter Schneider 1) The document discusses platform security for the Maemo 6 operating system. It describes mechanisms like access control, hardware enablers, and integrity protection to secure the software platform.
2) Access control is based on a classical Unix multi-user model extended with application-level controls. Applications must declare needed resources in a manifest file.
3) Integrity protection validates executables against reference hashes stored securely to prevent offline attacks.
CNIT 125 Ch 5 Communication & Network Security (part 2 of 2)



CNIT 125 Ch 5 Communication & Network Security (part 2 of 2)Sam Bowne For a college course at Coastline Community College taught by Sam Bowne. Details at https://samsclass.info/125/125_F17.shtml
Based on: "CISSP Study Guide, Third Edition"; by Eric Conrad, Seth Misenar, Joshua Feldman; ISBN-10: 0128024372
Essential Layers of IBM i Security: IBM i Security Configuration



Essential Layers of IBM i Security: IBM i Security ConfigurationPrecisely Learn practical, sound practices for properly configuring security settings within the IBM i OS, keep the OS and PTFs up to date and user profile management considerations.
CNIT 123: Ch 6: Enumeration



CNIT 123: Ch 6: EnumerationSam Bowne This document discusses enumeration, which is the process of extracting information about network resources and user accounts. It provides examples of tools used to enumerate different operating systems, including NBTscan for Microsoft OS, null sessions, NetBIOS tools like nbtstat and net view, and Windows tools in Backtrack like Smb4K, DumpSec, and Hyena. For NetWare, it discusses tools like Novell Client. For UNIX systems it discusses the finger utility and using Nessus. It includes screenshots of enumerating devices with these various tools.
How we breach small and medium enterprises (SMEs)



How we breach small and medium enterprises (SMEs)NCC Group This document summarizes common techniques used to breach small and medium enterprises. It discusses how networks are typically assessed through discovery, vulnerability assessment, exploitation, and post-exploitation. It then outlines several weaknesses that are commonly leveraged, including lack of security patches, default credentials, excessive network footprint, lack of network segregation, exceptions in configurations, and failure to implement whitelisting over blacklisting. Specific scenarios are provided for each to illustrate how access can be gained and privilege escalated within a network. The document stresses the importance of security fundamentals like patching, access control, and network segmentation.
Palo alto outline course | Mostafa El Lathy



Palo alto outline course | Mostafa El LathyMostafa El Lathy This document provides an overview of a 150-video, 25-hour Palo Alto Networks NGFW advanced training course covering PAN-OS versions 8.0 and 8.1. The course contains 20 modules that cover topics such as networking, security policies, objects, User-ID, authentication, URL filtering, application control, certificates, threat prevention, WildFire, high availability, advanced networking, and VPN. It is designed to prepare students for the PCNSA and PCNSE certification exams but does not cover Panorama, cloud platforms, IPv6, or dynamic routing protocols.
Intoto Linley Tech Utm Architecture Presentation



Intoto Linley Tech Utm Architecture Presentationsaddepalli Presentation on different architectures to implement UTM in Multicore chips - Presentation made in Linley conference in Sanjose
Mastering checkpoint-1-basic-installation



Mastering checkpoint-1-basic-installationnetworkershome The document provides an overview of Check Point's Gaia operating system. Some key points:
- Gaia is Check Point's next generation operating system that combines the best of their SecurePlatform and IPSO operating systems.
- It supports all Check Point security appliances and products, including Software Blades, Gateways, and Security Management.
- Features include support for IPv4/IPv6, high connection capacity, load sharing, high availability, dynamic routing, easy CLI, and role-based administration.
- Gaia allows for simple upgrades from IPSO and SecurePlatform and includes automated software updates for Check Point products.
NCS: NEtwork Control System Hands-on Labs 



NCS: NEtwork Control System Hands-on Labs Cisco Canada Jason Yen, Solution Architect and Ashok Sadasivan, Solution Architect, discusses NCS: Network control systems at Cisco Connect Toronto 2015.
Similar to Firewall in Perl by Chankey Pathak (20)
Database Firewall with Snort



Database Firewall with SnortNarudom Roongsiriwong, CISSP Database firewall is a useful tool that monitor databases to identify and protect against database specific attacks that mostly seek to access sensitive information stored in the databases. However the commercial database firewalls are expensive and needs specific product knowledge, while the opensource database firewalls are designed for specific opensource database servers.
In order to fulfill the need of inexpensive database firewall, Snort - an opensource IDS/IPS - is possible to achieve the goal in some scenarios with familiar rule writing. The paper will explain the limitation of Snort as a database firewall, constraints in commercial database statement and some example implementation.
Security defined routing_cybergamut_v1_1



Security defined routing_cybergamut_v1_1Joel W. King http://cybergamut.com/2014/09/technical-tuesday-28-october-2014-software-defined-networking-by-joel-king-of-world-wide-technology/
TTL Alfresco Product Security and Best Practices 2017



TTL Alfresco Product Security and Best Practices 2017Toni de la Fuente Slide deck used during Tech Talk Live #110 in October 2017. Phil Meadows and myself discussed about Alfresco products security and I went through Alfresco CS security best practices.
Chapter 7 security tools i



Chapter 7 security tools iSyaiful Ahdan This document provides a summary of the top 18 security tools as voted on by over 3,000 respondents to a survey conducted by Insecure.org. The top tools included Nmap, Nessus, Wireshark, Snort, Netcat, Metasploit Framework, and others. For each tool, a brief 1-2 sentence description of its functionality is provided. The document shows that while many new tools have emerged, some older standards like tcpdump, SSH, and John the Ripper remain very popular.
OpenVINO introduction



OpenVINO introductionYury Gorbachev The document discusses OpenVINOTM, an Intel toolkit that provides high performance computer vision and deep learning inference capabilities. It allows building applications that leverage OpenCV, deep learning models, and heterogeneous execution across CPU, GPU, FPGA and VPU hardware. Key benefits include portable deployment across platforms with a minimal footprint, optimized performance on Intel hardware, and pre-trained models for common tasks like object detection. The toolkit includes libraries, tools for model optimization, and samples to help developers build and deploy high performance computer vision and deep learning applications.
RIoT (Raiding Internet of Things) by Jacob Holcomb



RIoT (Raiding Internet of Things) by Jacob HolcombPriyanka Aash The recorded version of 'Best Of The World Webcast Series' [Webinar] where Jacob Holcomb speaks on 'RIoT (Raiding Internet of Things)' is available on CISOPlatform.
Best Of The World Webcast Series are webinars where breakthrough/original security researchers showcase their study, to offer the CISO/security experts the best insights in information security.
For more signup(it's free): www.cisoplatform.com
4.1-cnse-study-guide.pdf



4.1-cnse-study-guide.pdfssuser88346b This document provides an overview and study guide for the Palo Alto Networks CNSE 4.1 certification exam. It includes general advice for preparing for the exam, lists the major exam topics, and provides descriptions of Palo Alto Networks appliances, interface types, application identification, and other key networking and security concepts covered on the exam. Additional support documents are referenced throughout for further reading.
Infosecurity.be 2019: What are relevant open source security tools you should...



Infosecurity.be 2019: What are relevant open source security tools you should...B.A. Quick talk by Marc Vael and yours truly about the treasure trove of open source security tools that are available to us all.
Metasploitation part-1 (murtuja)



Metasploitation part-1 (murtuja)ClubHack This document provides an overview of metasploitation and using the Metasploit framework. It discusses basics like vulnerabilities, exploits, payloads and encoders. It then covers using the msfconsole interface, exploit modules, auxiliary modules like scanners, databases integration, automation, client-side exploits, payload generation, backdooring files, Linux backdoors, Meterpreter, pivoting, and post-exploitation techniques. The document includes several screenshots and links resources for further information.
Powering up on power shell avengercon - 2018



Powering up on power shell avengercon - 2018Fernando Tomlinson, CISSP, MBA This document provides information about a PowerShell presentation titled "Powering up on PowerShell". It includes the wireless network credentials to access the demo environment, a link to demo files, an agenda for the presentation topics, and a brief biography of the presenter. Some of the topics to be covered in the presentation include moving around the file system and registry, hashing, data storage techniques, custom event logging, WinRM logging, port scanning, and achieving persistence through PowerShell profiles.
Developer Day 2014 - 7 - andrew mitchell - legato



Developer Day 2014 - 7 - andrew mitchell - legatoThibault Cantegrel The document discusses Legato, an open source embedded Linux platform for machine-to-machine (M2M) devices from Sierra Wireless. It notes that existing Linux distributions are complex to set up and maintain for M2M use cases. Legato aims to simplify M2M development with solutions that are ready-to-run, ready-to-build, and ready-to-connect. It provides an integrated and validated Linux distribution, application framework, and development tools to accelerate the creation of M2M applications. Legato uses a sandboxed approach to isolate and secure multiple applications running on a device.
Orion NTA Customer Training



Orion NTA Customer TrainingSolarWinds For more information on NTA, visit: http://www.solarwinds.com/products/network-traffic-analyzer/info.aspx
Watch this webcast: http://www.solarwinds.com/resources/videos/video-tutorial-netflow-training-part-i.html
This video tutorial covers NetFlow best practices for planning and deployment and is Part 1 of the NetFlow training series.
Intro ch 07_a



Intro ch 07_aQuaid-e-Awam University of Engineering Science and Technology Nawabshah Sindh Pakistan This document discusses operating systems and their core functions. It describes different types of operating systems including real-time, single-user/single-tasking, single-user/multitasking, and multi-user/multitasking. The key functions of operating systems are providing a user interface, running programs, managing hardware devices, and organizing file storage. Graphical user interfaces and command line interfaces are discussed. Utilities that enhance operating systems like backup software, anti-virus software, firewalls, and intrusion detection are also outlined.
Network Securities.pptx



Network Securities.pptxatharkaleem2 The document discusses root password breaks, network security, containers, and intrusion detection systems. It describes how to change the root password when booted into advanced options on Ubuntu. It also explains network security concepts like firewalls, iptables rules, and traffic types. Popular open-source intrusion detection systems (IDS) like Ossec and Snort are covered, along with their features and how to deploy them in containers for learning.
Quantum-grizzly-packet-filtering



Quantum-grizzly-packet-filteringAkihiro Motoki This document proposes improvements to OpenStack's packet filtering features by introducing more flexible and fine-grained packet filtering policies. It suggests implementing (1) a new packet filtering policy API, (2) the ability to bind policies to quantum ports or "port groups", and (3) a driver model to support multiple filtering implementations like iptables or SDN controllers. This would allow enforcing dynamic, tenant-specific security policies beyond just security groups.
Kali presentation



Kali presentationZain Ul abadin kali operating system LINUX UNIX MAC Window presentation ubanto MAC KAli features compare of kali and unix in hindi easy present ppt slideshare tolls hacking penetration ethical hacking KALI top ten feature best hacking tool
Devicemgmt



Devicemgmtxyxz The document discusses Linux on network switches. It provides an overview of using Linux kernel on Cisco switches, including running Linux utilities and tools for interface management, troubleshooting, and network namespaces for VRF capabilities. It also introduces the GuestShell feature, which allows running open source packages and applications in a secure Linux container on the switch.
CCNA_Security_02.ppt



CCNA_Security_02.pptveracru1 This document provides an overview of a lesson on securing network devices. The lesson objectives include describing how to configure secure router administration access, SSH, privilege levels, and role-based CLI access. It discusses concepts like router hardening, administrative access configuration, and network monitoring techniques. Specific configuration examples are provided for setting passwords, virtual login security, and SSH. The document also summarizes using SDM to configure the SSH daemon and assigning administrative roles through privilege levels and role-based CLI access.
Security tools



Security toolsGreater Noida Institute Of Technology This document summarizes several security analysis tools, including CACLS for modifying access control lists in Windows, NSLOOKUP for resolving domain names to IP addresses, Traceroute/tracert for tracing the network path between hosts, Ping for checking network connectivity, and WS-Ping which combines tools like Ping, Traceroute, network scanning, and information gathering. It also discusses SATAN and Nessus, which are vulnerability scanners that detect potential security issues by analyzing network configurations and services without exploiting any vulnerabilities.
Ad
Recently uploaded (20)
Manifest Pre-Seed Update | A Humanoid OEM Deeptech In France



Manifest Pre-Seed Update | A Humanoid OEM Deeptech In Francechb3 The latest updates on Manifest's pre-seed stage progress.
The Evolution of Meme Coins A New Era for Digital Currency ppt.pdf



The Evolution of Meme Coins A New Era for Digital Currency ppt.pdfAbi john Analyze the growth of meme coins from mere online jokes to potential assets in the digital economy. Explore the community, culture, and utility as they elevate themselves to a new era in cryptocurrency.
Enhancing ICU Intelligence: How Our Functional Testing Enabled a Healthcare I...



Enhancing ICU Intelligence: How Our Functional Testing Enabled a Healthcare I...Impelsys Inc. Impelsys provided a robust testing solution, leveraging a risk-based and requirement-mapped approach to validate ICU Connect and CritiXpert. A well-defined test suite was developed to assess data communication, clinical data collection, transformation, and visualization across integrated devices.
Technology Trends in 2025: AI and Big Data Analytics



Technology Trends in 2025: AI and Big Data AnalyticsInData Labs At InData Labs, we have been keeping an ear to the ground, looking out for AI-enabled digital transformation trends coming our way in 2025. Our report will provide a look into the technology landscape of the future, including:
-Artificial Intelligence Market Overview
-Strategies for AI Adoption in 2025
-Anticipated drivers of AI adoption and transformative technologies
-Benefits of AI and Big data for your business
-Tips on how to prepare your business for innovation
-AI and data privacy: Strategies for securing data privacy in AI models, etc.
Download your free copy nowand implement the key findings to improve your business.
Andrew Marnell: Transforming Business Strategy Through Data-Driven Insights



Andrew Marnell: Transforming Business Strategy Through Data-Driven InsightsAndrew Marnell With expertise in data architecture, performance tracking, and revenue forecasting, Andrew Marnell plays a vital role in aligning business strategies with data insights. Andrew Marnell’s ability to lead cross-functional teams ensures businesses achieve sustainable growth and operational excellence.
Quantum Computing Quick Research Guide by Arthur Morgan



Quantum Computing Quick Research Guide by Arthur MorganArthur Morgan This is a Quick Research Guide (QRG).
QRGs include the following:
- A brief, high-level overview of the QRG topic.
- A milestone timeline for the QRG topic.
- Links to various free online resource materials to provide a deeper dive into the QRG topic.
- Conclusion and a recommendation for at least two books available in the SJPL system on the QRG topic.
QRGs planned for the series:
- Artificial Intelligence QRG
- Quantum Computing QRG
- Big Data Analytics QRG
- Spacecraft Guidance, Navigation & Control QRG (coming 2026)
- UK Home Computing & The Birth of ARM QRG (coming 2027)
Any questions or comments?
- Please contact Arthur Morgan at [email protected].
100% human made.
UiPath Community Berlin: Orchestrator API, Swagger, and Test Manager API



UiPath Community Berlin: Orchestrator API, Swagger, and Test Manager APIUiPathCommunity Join this UiPath Community Berlin meetup to explore the Orchestrator API, Swagger interface, and the Test Manager API. Learn how to leverage these tools to streamline automation, enhance testing, and integrate more efficiently with UiPath. Perfect for developers, testers, and automation enthusiasts!
📕 Agenda
Welcome & Introductions
Orchestrator API Overview
Exploring the Swagger Interface
Test Manager API Highlights
Streamlining Automation & Testing with APIs (Demo)
Q&A and Open Discussion
Perfect for developers, testers, and automation enthusiasts!
👉 Join our UiPath Community Berlin chapter: https://community.uipath.com/berlin/
This session streamed live on April 29, 2025, 18:00 CET.
Check out all our upcoming UiPath Community sessions at https://community.uipath.com/events/.
How analogue intelligence complements AI



How analogue intelligence complements AIPaul Rowe
Artificial Intelligence is providing benefits in many areas of work within the heritage sector, from image analysis, to ideas generation, and new research tools. However, it is more critical than ever for people, with analogue intelligence, to ensure the integrity and ethical use of AI. Including real people can improve the use of AI by identifying potential biases, cross-checking results, refining workflows, and providing contextual relevance to AI-driven results.
News about the impact of AI often paints a rosy picture. In practice, there are many potential pitfalls. This presentation discusses these issues and looks at the role of analogue intelligence and analogue interfaces in providing the best results to our audiences. How do we deal with factually incorrect results? How do we get content generated that better reflects the diversity of our communities? What roles are there for physical, in-person experiences in the digital world?
AI Changes Everything – Talk at Cardiff Metropolitan University, 29th April 2...



AI Changes Everything – Talk at Cardiff Metropolitan University, 29th April 2...Alan Dix Talk at the final event of Data Fusion Dynamics: A Collaborative UK-Saudi Initiative in Cybersecurity and Artificial Intelligence funded by the British Council UK-Saudi Challenge Fund 2024, Cardiff Metropolitan University, 29th April 2025
https://alandix.com/academic/talks/CMet2025-AI-Changes-Everything/
Is AI just another technology, or does it fundamentally change the way we live and think?
Every technology has a direct impact with micro-ethical consequences, some good, some bad. However more profound are the ways in which some technologies reshape the very fabric of society with macro-ethical impacts. The invention of the stirrup revolutionised mounted combat, but as a side effect gave rise to the feudal system, which still shapes politics today. The internal combustion engine offers personal freedom and creates pollution, but has also transformed the nature of urban planning and international trade. When we look at AI the micro-ethical issues, such as bias, are most obvious, but the macro-ethical challenges may be greater.
At a micro-ethical level AI has the potential to deepen social, ethnic and gender bias, issues I have warned about since the early 1990s! It is also being used increasingly on the battlefield. However, it also offers amazing opportunities in health and educations, as the recent Nobel prizes for the developers of AlphaFold illustrate. More radically, the need to encode ethics acts as a mirror to surface essential ethical problems and conflicts.
At the macro-ethical level, by the early 2000s digital technology had already begun to undermine sovereignty (e.g. gambling), market economics (through network effects and emergent monopolies), and the very meaning of money. Modern AI is the child of big data, big computation and ultimately big business, intensifying the inherent tendency of digital technology to concentrate power. AI is already unravelling the fundamentals of the social, political and economic world around us, but this is a world that needs radical reimagining to overcome the global environmental and human challenges that confront us. Our challenge is whether to let the threads fall as they may, or to use them to weave a better future.
Generative Artificial Intelligence (GenAI) in Business



Generative Artificial Intelligence (GenAI) in BusinessDr. Tathagat Varma My talk for the Indian School of Business (ISB) Emerging Leaders Program Cohort 9. In this talk, I discussed key issues around adoption of GenAI in business - benefits, opportunities and limitations. I also discussed how my research on Theory of Cognitive Chasms helps address some of these issues
Linux Support for SMARC: How Toradex Empowers Embedded Developers



Linux Support for SMARC: How Toradex Empowers Embedded DevelopersToradex Toradex brings robust Linux support to SMARC (Smart Mobility Architecture), ensuring high performance and long-term reliability for embedded applications. Here’s how:
• Optimized Torizon OS & Yocto Support – Toradex provides Torizon OS, a Debian-based easy-to-use platform, and Yocto BSPs for customized Linux images on SMARC modules.
• Seamless Integration with i.MX 8M Plus and i.MX 95 – Toradex SMARC solutions leverage NXP’s i.MX 8 M Plus and i.MX 95 SoCs, delivering power efficiency and AI-ready performance.
• Secure and Reliable – With Secure Boot, over-the-air (OTA) updates, and LTS kernel support, Toradex ensures industrial-grade security and longevity.
• Containerized Workflows for AI & IoT – Support for Docker, ROS, and real-time Linux enables scalable AI, ML, and IoT applications.
• Strong Ecosystem & Developer Support – Toradex offers comprehensive documentation, developer tools, and dedicated support, accelerating time-to-market.
With Toradex’s Linux support for SMARC, developers get a scalable, secure, and high-performance solution for industrial, medical, and AI-driven applications.
Do you have a specific project or application in mind where you're considering SMARC? We can help with Free Compatibility Check and help you with quick time-to-market
For more information: https://www.toradex.com/computer-on-modules/smarc-arm-family
Increasing Retail Store Efficiency How can Planograms Save Time and Money.pptx



Increasing Retail Store Efficiency How can Planograms Save Time and Money.pptxAnoop Ashok In today's fast-paced retail environment, efficiency is key. Every minute counts, and every penny matters. One tool that can significantly boost your store's efficiency is a well-executed planogram. These visual merchandising blueprints not only enhance store layouts but also save time and money in the process.
Drupalcamp Finland – Measuring Front-end Energy Consumption



Drupalcamp Finland – Measuring Front-end Energy ConsumptionExove How to measure web front-end energy consumption using Firefox Profiler. Presented in DrupalCamp Finland on April 25th, 2025.
Cyber Awareness overview for 2025 month of security



Cyber Awareness overview for 2025 month of securityriccardosl1 Cyber awareness training educates employees on risk associated with internet and malicious emails
Complete Guide to Advanced Logistics Management Software in Riyadh.pdf



Complete Guide to Advanced Logistics Management Software in Riyadh.pdfSoftware Company Explore the benefits and features of advanced logistics management software for businesses in Riyadh. This guide delves into the latest technologies, from real-time tracking and route optimization to warehouse management and inventory control, helping businesses streamline their logistics operations and reduce costs. Learn how implementing the right software solution can enhance efficiency, improve customer satisfaction, and provide a competitive edge in the growing logistics sector of Riyadh.
Transcript: #StandardsGoals for 2025: Standards & certification roundup - Tec...



Transcript: #StandardsGoals for 2025: Standards & certification roundup - Tec...BookNet Canada Book industry standards are evolving rapidly. In the first part of this session, we’ll share an overview of key developments from 2024 and the early months of 2025. Then, BookNet’s resident standards expert, Tom Richardson, and CEO, Lauren Stewart, have a forward-looking conversation about what’s next.
Link to recording, presentation slides, and accompanying resource: https://bnctechforum.ca/sessions/standardsgoals-for-2025-standards-certification-roundup/
Presented by BookNet Canada on May 6, 2025 with support from the Department of Canadian Heritage.
HCL Nomad Web – Best Practices und Verwaltung von Multiuser-Umgebungen



HCL Nomad Web – Best Practices und Verwaltung von Multiuser-Umgebungenpanagenda Webinar Recording: https://www.panagenda.com/webinars/hcl-nomad-web-best-practices-und-verwaltung-von-multiuser-umgebungen/
HCL Nomad Web wird als die nächste Generation des HCL Notes-Clients gefeiert und bietet zahlreiche Vorteile, wie die Beseitigung des Bedarfs an Paketierung, Verteilung und Installation. Nomad Web-Client-Updates werden “automatisch” im Hintergrund installiert, was den administrativen Aufwand im Vergleich zu traditionellen HCL Notes-Clients erheblich reduziert. Allerdings stellt die Fehlerbehebung in Nomad Web im Vergleich zum Notes-Client einzigartige Herausforderungen dar.
Begleiten Sie Christoph und Marc, während sie demonstrieren, wie der Fehlerbehebungsprozess in HCL Nomad Web vereinfacht werden kann, um eine reibungslose und effiziente Benutzererfahrung zu gewährleisten.
In diesem Webinar werden wir effektive Strategien zur Diagnose und Lösung häufiger Probleme in HCL Nomad Web untersuchen, einschließlich
- Zugriff auf die Konsole
- Auffinden und Interpretieren von Protokolldateien
- Zugriff auf den Datenordner im Cache des Browsers (unter Verwendung von OPFS)
- Verständnis der Unterschiede zwischen Einzel- und Mehrbenutzerszenarien
- Nutzung der Client Clocking-Funktion
Mobile App Development Company in Saudi Arabia



Mobile App Development Company in Saudi ArabiaSteve Jonas EmizenTech is a globally recognized software development company, proudly serving businesses since 2013. With over 11+ years of industry experience and a team of 200+ skilled professionals, we have successfully delivered 1200+ projects across various sectors. As a leading Mobile App Development Company In Saudi Arabia we offer end-to-end solutions for iOS, Android, and cross-platform applications. Our apps are known for their user-friendly interfaces, scalability, high performance, and strong security features. We tailor each mobile application to meet the unique needs of different industries, ensuring a seamless user experience. EmizenTech is committed to turning your vision into a powerful digital product that drives growth, innovation, and long-term success in the competitive mobile landscape of Saudi Arabia.
Splunk Security Update | Public Sector Summit Germany 2025



Splunk Security Update | Public Sector Summit Germany 2025Splunk Splunk Security Update
Sprecher: Marcel Tanuatmadja
Ad
Firewall in Perl by Chankey Pathak
- 1. TRAINING REPORT ON SYS - FIREWALL Secure Your System A handy tool for System-Administrators Chandra Prakash Pathak 08EMTCS032 Computer Science Maharishi Arvind Institute of Engineering and Technology, Jaipur http://technostall.com
- 2. Company Profile- Linux World • The best awarded Red Hat partner in India. • The company has been contributing a great deal to Linux Server & Networking industry by fulfilling its need for trained manpower in the field of Linux support, Networking, System Integration & Programming.
- 3. GREEN-HORNE PROJECT (An open source operating system) Module: SYS Firewall
- 4. What is a Firewall? A firewall is hardware, software, or a combination of both that is used to prevent unauthorized programs or Internet users from accessing a private network and/or a single computer.
- 5. How does a software firewall work? • Inspects each individual “packet” of data as it arrives at either side of the firewall • Inbound to or outbound from your computer • Determines whether it should be allowed to pass through or if it should be blocked
- 6. Firewall Rules • Allow – traffic that flows automatically because it has been deemed as “safe” (Ex. Meeting Maker, Eudora, etc.) • Block – traffic that is blocked because it has been deemed dangerous to your computer • Ask – asks the user whether or not the traffic is allowed to pass through
- 7. What a personal firewall can do • Stop hackers from accessing your computer • Protects your personal information • Blocks “pop up” ads and certain cookies • Determines which programs can access the Internet
- 8. What a SYS firewall can do • Authorizing users • Limiting access for the services • Filtering the packets • NATing • Masquerading
- 9. Requirements • Linux Kernel 2.4.x or higher • iptables • Perl 5.6 or higher • dialog
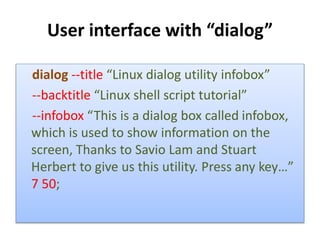
- 10. User interface with “dialog” dialog --title “Linux dialog utility infobox” --backtitle “Linux shell script tutorial” --infobox “This is a dialog box called infobox, which is used to show information on the screen, Thanks to Savio Lam and Stuart Herbert to give us this utility. Press any key…” 7 50;
- 12. Implementing iptables • Using Perl and dialog I build a GUI version of the iptables. Perl – For coding purpose dialog – For Graphical User Interface
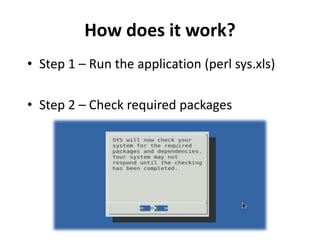
- 13. How does it work? • Step 1 – Run the application (perl sys.xls) • Step 2 – Check required packages
- 14. • Step 3 – Authenticate User (password)
- 15. • Step 4 – Main Interface
- 16. • Step 5 – Customize rules
- 17. Dropping all policies • iptables -P INPUT DROP • iptables -P OUTPUT DROP • iptables -P FORWARD DROP
- 18. Block Ping iptables -A INPUT -p icmp --icmp-type echo-request -j DROP iptables -A OUTPUT -p icmp --icmp-type echo-reply -j DROP
- 19. A dynamic approach # iptables -A INPUT -m state --state ESTABLISHED,RELATED -j ACCEPT # iptables -P INPUT DROP # iptables -A INPUT -m state --state ESTABLISHED,RELATED -j ACCEPT
- 20. SNAT • For static connections. • iptables -t nat -A POSTROUTING -o eth0 -j SNAT --to-source <SERVER'S_EXTERNAL_IP>
- 22. Masquerade • For dynamic connections. • iptables -t nat -A POSTROUTING -o ppp0 -j MASQUERADE
- 23. DNAT • iptables -t nat -A PREROUTING -i ppp0 -p tcp -- dport 80 -j DNAT --to-destination 192.168.1.24:80
- 24. Extra services • Saving rules • Logging • Exit


