Hacking
Download as PPTX, PDF4 likes3,672 views
This document discusses hacking and provides definitions and examples. It defines hacking as unauthorized computer access and distinguishes between hackers and crackers. Various types of hacking are described such as password, email, and credit card hacking. The document also gives a brief history of hacking and reasons why hackers engage in hacking. Examples are provided for how to hack passwords on websites like Yahoo, Facebook, and Gmail.
1 of 25
Downloaded 62 times
























Recommended
Hacking 



Hacking Harendra Singh In the computer security context, a hacker is someone who seeks and exploits weaknesses in a computer system or computer network.
Hacking final



Hacking finalJiyaaNaqvi This document defines hacking and different types of hackers. It discusses the history of hacking from the 1960s to present day. It outlines various types of hacking like website, network, and password hacking. It describes black hat, white hat, and grey hat hackers. Famous hackers from history are mentioned. The document discusses advantages and disadvantages of hacking, why hackers hack, and what to do if hacked. It concludes with tips to keep passwords protected and avoid phishing to prevent being hacked.
Power Point Hacker



Power Point Hackeryanizaki Hackers are people who illegally access computer systems and networks. There are different types of hackers with varying motivations, from malicious criminal hackers to early programmers who explored computer systems out of curiosity. The document provides examples of famous hackers from history who engaged in illegal hacking activities and accessed restricted systems, as well as tips for avoiding becoming a victim of hackers, such as using strong and unique passwords and disabling password retrieval functions.
Web defacement



Web defacementstudent This document provides definitions and information related to hacking and web defacement. It defines hacking as unauthorized use of computer and network resources. A hacker is described as an expert programmer who breaks security, while a cracker breaks in with malicious intent. Web defacement is when a hacker compromises a web server and changes the visual appearance or data on a page. Types of hacking discussed include password, email, site, banking and network hacking. The effects of hacking and methods to prevent hacking like software updates, firewalls, and antivirus software are also summarized.
All About Hacking..!!



All About Hacking..!!Mahatma Gandhi Institute of Edu and Research Center This document discusses different types of hacking methods and hackers. It describes phishing, brute force attacks, SQL injection, social engineering, application-based attacks, and misconfiguration attacks as common hacking techniques. It also defines white hat, black hat, and grey hat hackers, as well as elite hackers and script kiddies. White hats help security, black hats hack maliciously, and grey hats can be either. The document provides examples and warnings for different hacking methods.
Ict H A C K I N G



Ict H A C K I N GHafizra Mas Hacking is defined as illegally entering a computer system and making unauthorized changes to files and data. Crackers are individuals who gain illegal access to networks with malicious intent to damage systems. Criminal hacking specifically refers to manipulating information within a system in a negative way. Signs of a hack include discovering unauthorized emails or missing/moved files. If hacking is suspected, the most important step is to disconnect from the internet to protect information while also allowing security logs to be reviewed. Organizations are increasingly hiring ethical hackers to test security from an intruder's perspective in order to evaluate vulnerabilities.
ICT ~Hacking~



ICT ~Hacking~Nurhidayatul Asma Hackers are people who exploit weaknesses in computer systems and networks. They can be motivated by profit, protest, or challenge. Hackers are classified as white hats, black hats, or grey hats based on their motivations and actions. White hat hackers test security systems for non-malicious purposes. Black hat hackers violate security to cause harm or for personal gain. Grey hat hackers combine characteristics of both. To prevent hacking, users should change passwords monthly, install firewalls and antivirus software, and use antispyware programs.
Hacking



Hackingsatwinderkaurbajwa The document thanks the teacher for allowing the students to do a presentation on hacking. It then provides definitions for different types of hackers such as hackers, crackers, and phreaks. It describes hackers as those who bypass security without permission, crackers as those who destroy systems, and phreaks as those who work with frequencies for confidential information. It also discusses common hacker languages and provides examples of famous and Indian hackers as well as random facts about hacking. Finally, it suggests preventive measures like using antivirus software.
Ethical hacking



Ethical hackingdjkhatri Hacking can refer to authorized or unauthorized attempts to bypass security mechanisms. A hacker is someone who takes advantage of security weaknesses in a system. There are different types of hackers - white hat hackers help identify weaknesses, black hat hackers break into systems to steal information or cause damage, and grey hat hackers fall between white and black hats. Ethical hacking involves company engineers hacking their own systems to improve security. Famous hackers include Stephen Wozniak, Tsutomu Shimomura, Kevin Mitnick, and Kevin Poulsen. Social media sites are a common target for hacking. Installing antivirus software, avoiding personal information disclosure, and frequent scans can help prevent hacking.
Presentation



PresentationNishant Barot This document discusses different types of viruses, hacking, and hackers. It defines a virus as malicious code that can damage or hack systems. The main types of viruses discussed are worms, Trojans, and application viruses. Worms self-replicate and slow down systems. Trojans appear useful but secretly perform unwanted actions. Application viruses are difficult to detect. The document also defines hacking as gaining unauthorized access to systems for malicious purposes. The main types of hackers discussed are white hat hackers who provide security services, black hat hackers who hack for malicious reasons like theft, and grey hat hackers who accidentally access unauthorized areas.
Cyber Security Seminar Day 2



Cyber Security Seminar Day 2Apurv Singh Gautam The document provides an introduction to Trojans, including defining what they are, the two main types (direct connection and reverse connection), and how remote administration tools (RATs) are used to create and control Trojans. It discusses how Trojans can be used by hackers to remotely access victims' computers and systems. It also provides examples of common RAT programs and outlines some of the functions RATs can perform once infected, such as keylogging and camera/screen capturing. The document concludes by offering some tips on how to protect yourself from Trojans and social engineering attacks.
Trojan backdoors



Trojan backdoorsseth edmond This document discusses Trojan horse programs and remote administration tools. It defines Trojan horses as programs that appear harmless but have malicious code. Trojan horses can give intruders access to computers by installing backdoors. Remote administration tools also allow unauthorized access and control of victim's computers. The document provides examples of common Trojan horses and remote access programs like Back Orifice and describes how to detect and remove such threats.
BackDoors Seminar



BackDoors SeminarChaitali Patel This document discusses backdoors and how they can bypass normal authentication to gain access to systems. It defines different types of backdoors like hard-wired backdoors and Rakshasa backdoors, which are difficult to detect. Rakshasa backdoors can compromise BIOS and infect over 100 motherboards. The document also covers vulnerabilities like buffer overflows that can introduce backdoors. It lists the main motivations for backdoor attacks as hardware cloning and information leakage. Finally, it provides recommendations for preventing backdoors, such as installing security updates, scanning for backdoors, and updating anti-spyware software definitions regularly.
Backdoor



Backdoorphanleson The document discusses Trojans and backdoors. It defines a Trojan as a hidden program that runs on an infected computer and a backdoor as a program that allows hackers to connect without normal authentication. It describes how they are used to gain remote access or disable protections. The document outlines Trojan types and infection mechanisms like wrapper programs and autorun files. It provides examples of hacking tools and recommendations for detection and prevention like using antivirus software and educating users.
How to prevent a Phishing attack - Panda Security



How to prevent a Phishing attack - Panda SecurityPanda Security A phishing attack is launched every thirty seconds: 6 tips to protect yourself: http://www.pandasecurity.com/mediacenter/malware/infographic-tips-phishing/
Phishing continues to blight the Internet and is a thorn in the side of companies around the globe. Not only is it one of the most serious problems facing any company with even a minimal activity on the Web, it is also an ever-increasing threat.
Cybersecurity cyberlab1



Cybersecurity cyberlab1rayborg This document provides an overview of hacking, including its history and common techniques. It begins with early "phone freaks" who experimented with hacking phone systems using blue boxes and Captain Crunch whistles. It then outlines the stages of a typical penetration test: reconnaissance, scanning/enumeration, gaining access, privilege escalation, maintaining access covertly, and covering tracks. Common hacking methods like password cracking, man-in-the-middle attacks, Trojans, and keyloggers are also summarized. The document concludes by noting that nothing is truly secure and that risk is a balance of attack cost and information value.
Introduction to trojans and backdoors



Introduction to trojans and backdoorsjibinmanjooran This document provides an introduction to trojans and backdoors, including what they are, how they work, common types of trojans, and methods of detecting trojan activity. Trojans and backdoors allow hackers to send and receive data through open ports to gain control of systems. Common trojan types include remote access trojans, data sending trojans, and trojans that disable security software. Netstat and Wireshark can be used to monitor network activity and detect trojans. Wrappers and defacing applications help disguise trojans by changing file icons or combining with other programs.
Trojans and backdoors



Trojans and backdoorsGaurav Dalvi This document discusses Trojans, backdoors, and other malware. It begins by explaining the origin of the term "Trojan" from the story of the Trojan horse in Greek mythology. It then defines Trojans and different types like destructive, denial of service, and remote access Trojans. The document also covers how systems can become infected, techniques for detecting and hiding malware like Trojans and backdoors, and discusses the historical Back Orifice 2000 backdoor as a case study. It concludes with recommendations for protecting against malware.
14 tips to increase cybersecurity awareness



14 tips to increase cybersecurity awarenessMichel Bitter We used this presentation within our company to increase the cybersecurity awareness of our employees. These 14 tips should help everybody to protect themselves against the most obvious cyber attacks.
Web security



Web securitySubhash Basistha The presentation discussed web security issues including client-side, server-side, and data transmission risks and proposed SSL as a solution to encrypt data exchange between clients and servers, providing authentication, integrity, and confidentiality of data. It described the SSL architecture and protocols for encrypting records, negotiating keys during handshake, and alerting of errors. The presentation also covered the SET protocol for secure online payment transactions.
Cyber Security - All Over World



Cyber Security - All Over WorldBhawani Singh Chouhan *According to the Quick Heal Annual Threat Report 2019, the metropolitans of Mumbai, Delhi, Bengaluru and Kolkata are the most attacked cities in India, in terms of online attacks.*
So guys in this Power Point Presentation I explained Most Common Cyber Attacks,viruses,Malware,Password Cracking Technique,Major Security Problems,Cyber Security Companies In India And Also Most Important Safety Tips.
Thank You.
Hacker word that describes person who have special skills in the field of com...



Hacker word that describes person who have special skills in the field of com...Mahmoud Saeed Hackers are people with specialized computer and information security skills. Some hackers test systems to improve security ("white hat"), while others hack illegally for personal gain ("black hat"). Companies hire white hat hackers to find security vulnerabilities. In 2014, hackers believed to be supported by North Korea attacked Sony Pictures in retaliation for a film depicting the assassination of Kim Jong-un. This caused Sony to cancel the film's release. The hack involved stealing terabytes of data and leaving threatening messages. Another hacking group called Lizard Squad claimed credit for attacks on Microsoft and Sony gaming networks around Christmas to demonstrate security weaknesses.
Hacking



Hackingzubair112233 This document discusses hacking and provides information on various types of hackers. It defines hacking as attempting unauthorized access to computer resources and notes hackers seek weaknesses in systems. The document outlines different types of hacking like website and online banking hacking. It also describes the history of hacking and different types of hackers, including black hat, gray hat, and white hat hackers. Lastly, it provides advice on what to do if a system is hacked, such as shutting it down and restoring from backups.
Keyloggers



Keyloggersnovacharter Key loggers are programs or hardware devices that record every keystroke on a computer. They can be used legitimately to monitor employee productivity but are also used illegally to steal sensitive information like passwords, usernames, credit card numbers, and personal details. Key loggers come in both hardware and software forms. Hardware key loggers are small devices that physically attach to keyboards while software key loggers can be installed remotely or hidden in viruses and malware. Common prevention methods include using up-to-date antivirus software, firewalls, automatic form fillers, alternative keyboard layouts, and on-screen keyboards. It is important to be aware of what is installed on your computer and keep security software updated.
Detection of running backdoors



Detection of running backdoorsmridulahuja This document discusses backdoor Trojans and how they can bypass authentication to gain unauthorized access to a computer system. Backdoor Trojans are classified as viruses that create a backdoor to access a specific system. They do not spread to other files. Common backdoors take the form of installed programs or subvert the system through a rootkit. Backdoors can enable harmful actions like crashing the computer, data theft, keylogging, and linking the computer to a botnet. Popular backdoor Trojans mentioned include Netbus, Subseven, Back Orifice, Beast, and Zeus. Detecting backdoors is challenging as they can modify object code rather than just source code. Analysis of running processes and any open
Understanding Keylogger



Understanding KeyloggerPhannarith Ou, G-CISO This document discusses keyloggers, which are programs or devices that record every keystroke typed on a computer. It describes how keyloggers can be used by companies to monitor employees, parents to track children's online activity, and partners to spy on each other's computer use. However, keyloggers also pose privacy and security risks if used by hackers to steal personal information like passwords, credit card numbers, and more. The document then focuses on the KeyGhost hardware keylogger and how to protect against keyloggers by using up-to-date antivirus software, one-time passwords, keylogging detection systems, and virtual keyboards.
Hackers



HackersMahmoud Saeed This slide about hackers and about technology do it will help everyone to understand what does hackers do !
Ethi mini1 - ethical hacking



Ethi mini1 - ethical hackingBeing Uniq Sonu The document discusses different types of hackers and hacking techniques. It describes script kiddies, professional criminals, virus writers and their motives. It then explains various web application hacks like file query, SQL injection, and cross-site scripting. The document also discusses ethical hacking and how organizations use ethical hackers to evaluate security vulnerabilities by attempting to break into systems. Ethical hackers possess strong programming and networking skills along with knowledge of operating systems, hardware, protocols and project management. Their evaluations seek to determine what an attacker can access and how they may go undetected.
Defcamp 2013 - Does it pay to be a blackhat hacker



Defcamp 2013 - Does it pay to be a blackhat hackerDefCamp The document discusses different types of hackers - white hat, grey hat, and black hat. A white hat hacker conducts ethical hacking and security testing, while a black hat hacker violates security for personal gain or maliciousness. The document uses a real Apache PHP vulnerability as an example to show how a black hat hacker could potentially exploit it at large scale to infect millions of servers and earn millions setting up a powerful botnet to perform DDoS attacks and other illicit activities for profit, though this scenario is more science fiction. While financially lucrative, being a black hat hacker risks legal consequences like jail time.
how to prevent system from hacking...by sarika



how to prevent system from hacking...by sarikaSarika Dyne Hacking involves modifying systems to accomplish goals beyond their original purpose. A hacker consistently engages in hacking and sees it as a lifestyle. There are black hat, white hat, and grey hat hackers. Ethical hacking tests resources for good and helps secure systems, which is important as cyber crimes have risen globally. Hacking can provide security for banks and help catch thieves, but ethical hackers must be trustworthy and professionals are expensive to hire. Systems can be protected using firewalls and antivirus software.
More Related Content
What's hot (18)
Ethical hacking



Ethical hackingdjkhatri Hacking can refer to authorized or unauthorized attempts to bypass security mechanisms. A hacker is someone who takes advantage of security weaknesses in a system. There are different types of hackers - white hat hackers help identify weaknesses, black hat hackers break into systems to steal information or cause damage, and grey hat hackers fall between white and black hats. Ethical hacking involves company engineers hacking their own systems to improve security. Famous hackers include Stephen Wozniak, Tsutomu Shimomura, Kevin Mitnick, and Kevin Poulsen. Social media sites are a common target for hacking. Installing antivirus software, avoiding personal information disclosure, and frequent scans can help prevent hacking.
Presentation



PresentationNishant Barot This document discusses different types of viruses, hacking, and hackers. It defines a virus as malicious code that can damage or hack systems. The main types of viruses discussed are worms, Trojans, and application viruses. Worms self-replicate and slow down systems. Trojans appear useful but secretly perform unwanted actions. Application viruses are difficult to detect. The document also defines hacking as gaining unauthorized access to systems for malicious purposes. The main types of hackers discussed are white hat hackers who provide security services, black hat hackers who hack for malicious reasons like theft, and grey hat hackers who accidentally access unauthorized areas.
Cyber Security Seminar Day 2



Cyber Security Seminar Day 2Apurv Singh Gautam The document provides an introduction to Trojans, including defining what they are, the two main types (direct connection and reverse connection), and how remote administration tools (RATs) are used to create and control Trojans. It discusses how Trojans can be used by hackers to remotely access victims' computers and systems. It also provides examples of common RAT programs and outlines some of the functions RATs can perform once infected, such as keylogging and camera/screen capturing. The document concludes by offering some tips on how to protect yourself from Trojans and social engineering attacks.
Trojan backdoors



Trojan backdoorsseth edmond This document discusses Trojan horse programs and remote administration tools. It defines Trojan horses as programs that appear harmless but have malicious code. Trojan horses can give intruders access to computers by installing backdoors. Remote administration tools also allow unauthorized access and control of victim's computers. The document provides examples of common Trojan horses and remote access programs like Back Orifice and describes how to detect and remove such threats.
BackDoors Seminar



BackDoors SeminarChaitali Patel This document discusses backdoors and how they can bypass normal authentication to gain access to systems. It defines different types of backdoors like hard-wired backdoors and Rakshasa backdoors, which are difficult to detect. Rakshasa backdoors can compromise BIOS and infect over 100 motherboards. The document also covers vulnerabilities like buffer overflows that can introduce backdoors. It lists the main motivations for backdoor attacks as hardware cloning and information leakage. Finally, it provides recommendations for preventing backdoors, such as installing security updates, scanning for backdoors, and updating anti-spyware software definitions regularly.
Backdoor



Backdoorphanleson The document discusses Trojans and backdoors. It defines a Trojan as a hidden program that runs on an infected computer and a backdoor as a program that allows hackers to connect without normal authentication. It describes how they are used to gain remote access or disable protections. The document outlines Trojan types and infection mechanisms like wrapper programs and autorun files. It provides examples of hacking tools and recommendations for detection and prevention like using antivirus software and educating users.
How to prevent a Phishing attack - Panda Security



How to prevent a Phishing attack - Panda SecurityPanda Security A phishing attack is launched every thirty seconds: 6 tips to protect yourself: http://www.pandasecurity.com/mediacenter/malware/infographic-tips-phishing/
Phishing continues to blight the Internet and is a thorn in the side of companies around the globe. Not only is it one of the most serious problems facing any company with even a minimal activity on the Web, it is also an ever-increasing threat.
Cybersecurity cyberlab1



Cybersecurity cyberlab1rayborg This document provides an overview of hacking, including its history and common techniques. It begins with early "phone freaks" who experimented with hacking phone systems using blue boxes and Captain Crunch whistles. It then outlines the stages of a typical penetration test: reconnaissance, scanning/enumeration, gaining access, privilege escalation, maintaining access covertly, and covering tracks. Common hacking methods like password cracking, man-in-the-middle attacks, Trojans, and keyloggers are also summarized. The document concludes by noting that nothing is truly secure and that risk is a balance of attack cost and information value.
Introduction to trojans and backdoors



Introduction to trojans and backdoorsjibinmanjooran This document provides an introduction to trojans and backdoors, including what they are, how they work, common types of trojans, and methods of detecting trojan activity. Trojans and backdoors allow hackers to send and receive data through open ports to gain control of systems. Common trojan types include remote access trojans, data sending trojans, and trojans that disable security software. Netstat and Wireshark can be used to monitor network activity and detect trojans. Wrappers and defacing applications help disguise trojans by changing file icons or combining with other programs.
Trojans and backdoors



Trojans and backdoorsGaurav Dalvi This document discusses Trojans, backdoors, and other malware. It begins by explaining the origin of the term "Trojan" from the story of the Trojan horse in Greek mythology. It then defines Trojans and different types like destructive, denial of service, and remote access Trojans. The document also covers how systems can become infected, techniques for detecting and hiding malware like Trojans and backdoors, and discusses the historical Back Orifice 2000 backdoor as a case study. It concludes with recommendations for protecting against malware.
14 tips to increase cybersecurity awareness



14 tips to increase cybersecurity awarenessMichel Bitter We used this presentation within our company to increase the cybersecurity awareness of our employees. These 14 tips should help everybody to protect themselves against the most obvious cyber attacks.
Web security



Web securitySubhash Basistha The presentation discussed web security issues including client-side, server-side, and data transmission risks and proposed SSL as a solution to encrypt data exchange between clients and servers, providing authentication, integrity, and confidentiality of data. It described the SSL architecture and protocols for encrypting records, negotiating keys during handshake, and alerting of errors. The presentation also covered the SET protocol for secure online payment transactions.
Cyber Security - All Over World



Cyber Security - All Over WorldBhawani Singh Chouhan *According to the Quick Heal Annual Threat Report 2019, the metropolitans of Mumbai, Delhi, Bengaluru and Kolkata are the most attacked cities in India, in terms of online attacks.*
So guys in this Power Point Presentation I explained Most Common Cyber Attacks,viruses,Malware,Password Cracking Technique,Major Security Problems,Cyber Security Companies In India And Also Most Important Safety Tips.
Thank You.
Hacker word that describes person who have special skills in the field of com...



Hacker word that describes person who have special skills in the field of com...Mahmoud Saeed Hackers are people with specialized computer and information security skills. Some hackers test systems to improve security ("white hat"), while others hack illegally for personal gain ("black hat"). Companies hire white hat hackers to find security vulnerabilities. In 2014, hackers believed to be supported by North Korea attacked Sony Pictures in retaliation for a film depicting the assassination of Kim Jong-un. This caused Sony to cancel the film's release. The hack involved stealing terabytes of data and leaving threatening messages. Another hacking group called Lizard Squad claimed credit for attacks on Microsoft and Sony gaming networks around Christmas to demonstrate security weaknesses.
Hacking



Hackingzubair112233 This document discusses hacking and provides information on various types of hackers. It defines hacking as attempting unauthorized access to computer resources and notes hackers seek weaknesses in systems. The document outlines different types of hacking like website and online banking hacking. It also describes the history of hacking and different types of hackers, including black hat, gray hat, and white hat hackers. Lastly, it provides advice on what to do if a system is hacked, such as shutting it down and restoring from backups.
Keyloggers



Keyloggersnovacharter Key loggers are programs or hardware devices that record every keystroke on a computer. They can be used legitimately to monitor employee productivity but are also used illegally to steal sensitive information like passwords, usernames, credit card numbers, and personal details. Key loggers come in both hardware and software forms. Hardware key loggers are small devices that physically attach to keyboards while software key loggers can be installed remotely or hidden in viruses and malware. Common prevention methods include using up-to-date antivirus software, firewalls, automatic form fillers, alternative keyboard layouts, and on-screen keyboards. It is important to be aware of what is installed on your computer and keep security software updated.
Detection of running backdoors



Detection of running backdoorsmridulahuja This document discusses backdoor Trojans and how they can bypass authentication to gain unauthorized access to a computer system. Backdoor Trojans are classified as viruses that create a backdoor to access a specific system. They do not spread to other files. Common backdoors take the form of installed programs or subvert the system through a rootkit. Backdoors can enable harmful actions like crashing the computer, data theft, keylogging, and linking the computer to a botnet. Popular backdoor Trojans mentioned include Netbus, Subseven, Back Orifice, Beast, and Zeus. Detecting backdoors is challenging as they can modify object code rather than just source code. Analysis of running processes and any open
Understanding Keylogger



Understanding KeyloggerPhannarith Ou, G-CISO This document discusses keyloggers, which are programs or devices that record every keystroke typed on a computer. It describes how keyloggers can be used by companies to monitor employees, parents to track children's online activity, and partners to spy on each other's computer use. However, keyloggers also pose privacy and security risks if used by hackers to steal personal information like passwords, credit card numbers, and more. The document then focuses on the KeyGhost hardware keylogger and how to protect against keyloggers by using up-to-date antivirus software, one-time passwords, keylogging detection systems, and virtual keyboards.
Viewers also liked (20)
Hackers



HackersMahmoud Saeed This slide about hackers and about technology do it will help everyone to understand what does hackers do !
Ethi mini1 - ethical hacking



Ethi mini1 - ethical hackingBeing Uniq Sonu The document discusses different types of hackers and hacking techniques. It describes script kiddies, professional criminals, virus writers and their motives. It then explains various web application hacks like file query, SQL injection, and cross-site scripting. The document also discusses ethical hacking and how organizations use ethical hackers to evaluate security vulnerabilities by attempting to break into systems. Ethical hackers possess strong programming and networking skills along with knowledge of operating systems, hardware, protocols and project management. Their evaluations seek to determine what an attacker can access and how they may go undetected.
Defcamp 2013 - Does it pay to be a blackhat hacker



Defcamp 2013 - Does it pay to be a blackhat hackerDefCamp The document discusses different types of hackers - white hat, grey hat, and black hat. A white hat hacker conducts ethical hacking and security testing, while a black hat hacker violates security for personal gain or maliciousness. The document uses a real Apache PHP vulnerability as an example to show how a black hat hacker could potentially exploit it at large scale to infect millions of servers and earn millions setting up a powerful botnet to perform DDoS attacks and other illicit activities for profit, though this scenario is more science fiction. While financially lucrative, being a black hat hacker risks legal consequences like jail time.
how to prevent system from hacking...by sarika



how to prevent system from hacking...by sarikaSarika Dyne Hacking involves modifying systems to accomplish goals beyond their original purpose. A hacker consistently engages in hacking and sees it as a lifestyle. There are black hat, white hat, and grey hat hackers. Ethical hacking tests resources for good and helps secure systems, which is important as cyber crimes have risen globally. Hacking can provide security for banks and help catch thieves, but ethical hackers must be trustworthy and professionals are expensive to hire. Systems can be protected using firewalls and antivirus software.
Cyper security & Ethical hacking



Cyper security & Ethical hackingCmano Kar In my college i will created this presentation for seminar with my own interest so this will help you for your career.Please you also create any presentation and upload it,Thank you.
Hacking



HackingArpit Verma Hacking is the act of breaking in to a computer system and is a criminal offence under the computer misuse.
Hacking Law Reform LAWS4305 2003



Hacking Law Reform LAWS4305 2003Peter Timusk The document discusses the history and definitions around the terms "hacker" and "cracker" and how their meanings have evolved over time from neutral to criminal associations. It also outlines relevant sections of Canada's Criminal Code concerning unauthorized computer use and hacking offenses. Issues around enforcement challenges, victim reporting rates, and potential harms of hackers are examined. Suggestions are made that initial laws around new computer crimes may not have been optimal and that further study is needed before reforming laws and sentencing.
Hacking Psychology



Hacking PsychologyFajar Anugerah This document outlines plans for a "Pecha Kucha Psychology" alumni sharing event to give students practical experience in psychology. It will involve 6-7 short presentations by alumni on topics like career mapping, personal projects, and book reviews. Presenters will use the Pecha Kucha style of 20 slides automatically advancing every 20 seconds to encourage concise, visual storytelling. The event will be held on December 7th at a university campus and promoted through lecturers and alumni on social media.
Haking PPT



Haking PPTSushil Ranjan The document discusses the history and types of hacking. It begins with the origins of hacking at MIT in the 1960s and defines hacking as attempting unauthorized access to computer systems. It then covers reasons hackers hack such as for fun, challenges, or to steal information. The document outlines various types of hacking like website, network, and password hacking. It also discusses advantages like security testing and disadvantages like harming privacy and illegality. In conclusion, it recommends password protections and online security best practices.
Introduction to Growth Hacking



Introduction to Growth HackingRadek Grabarek
What is Growth Hacking? You will learn 3 key things about growth hacking as well as famous examples of growth hacking ideas and techniques.
This slides were presented during Barcelona Growth Hacking Meetup on 21.10.2013.
Cyber Crime and Ethical Hacking



Cyber Crime and Ethical HackingANKIT KUMAR A Powerpoint Presentation on Cyber Crime and Ethical Hacking (only slides) made by Ankit Kumar (Jha).
Cross Site Scripting - Web Defacement Techniques



Cross Site Scripting - Web Defacement TechniquesRonan Dunne, CEH, SSCP Website defacement involves changing the visual appearance of a website or webpage by exploiting a vulnerability. The document discusses testing website defacement by capturing requests using ZAP proxy and replacing content with malicious code to bypass client-side protections. It then provides examples of defacement techniques like redirecting to hacked images, adding hacked images, covering the page with hacked text, and changing the background. Finally, it recommends server-side input filtering, output escaping, and enforcing a character encoding to prevent defacement attacks.
EVALUACIÓN



EVALUACIÓNNeidy frias Este documento define los delitos informáticos y diferencia entre hackers y crackers. Explica que los delitos informáticos son acciones ilegales que dañan computadoras, medios electrónicos o redes. Describe tres tipos de delitos informáticos como fraude, manipulación de datos y daños a programas o datos. Define a los hackers como expertos en informática y a los crackers como personas que buscan objetivos ilegales como esparcir virus o robar contraseñas.
Password Stealing & Enhancing User Authentication Using Opass Protocol



Password Stealing & Enhancing User Authentication Using Opass ProtocolPrasad Pawar The document discusses various topics related to computer hacking including definitions of hacking, types of hackers (white hat, black hat, grey hat), reasons for hacking, ethical hacking, steps in hacking (reconnaissance, scanning, gaining access, maintaining access, clearing tracks), and methods for hacking login passwords in Windows 95/98/ME and Windows NT/XP/Vista/7 operating systems. Specific techniques mentioned include using tools like Ophcrack to crack passwords stored in the SAM file without booting into Windows.
Cookies and Session



Cookies and SessionKoraStats In the following slide I am going to demonstrate the difference between Cookies and Session and how to use each and why. Also, I am going to talk a bit about session hijacking
Hacking and Hackers



Hacking and HackersFarwa Ansari This presentation provided information on communication skills and hackers. It began with an introduction to the topic of hackers, defining what a hacker is and discussing different types of hackers such as black hat, white hat, grey hat, and script kiddie hackers. The presentation then discussed famous hackers like Albert Gonzalez, Jonathan James, Ian Murphy, and John Draper. It provided details on some of their hacking activities. The presentation concluded with tips on how to prevent hacking, including keeping software and operating systems updated, using firewalls and antivirus software, avoiding suspicious websites and emails, and having strong passwords.
Windows Hacking



Windows HackingMayur Sutariya This document discusses different types of hackers and methods of hacking passwords. It defines white hat and black hat hackers, with white hats using their skills constructively and ethically to find security vulnerabilities, while black hats use their skills illegally and destructively. The document also discusses crackers/attackers who hack with malicious intent, phreaks who hack phone networks, and script kiddies who exploit known vulnerabilities without technical skills. It provides examples of password cracking tools and methods like Cain & Abel, LCP, password dumping, and using Windows repair mode. It notes the importance of security awareness and prevention.
Cyber Law With case studies 



Cyber Law With case studies Bhagya Bgk This document summarizes sections of the Indian Information Technology Act relating to data protection, hacking, and cyber crimes. It discusses sections that deal with compensation for corporate negligence that results in data loss, tampering with computer source code, hacking, sending offensive messages online, and dishonestly receiving stolen electronic devices. Case studies are provided for each section to illustrate how related legal cases have been handled. The document aims to explain the IT Act and associated punishments around these cyber issues.
ICT Form 4: Hacking



ICT Form 4: HackingQhaiyum Shah Hacking involves unauthorized access to computer systems. It is done by hackers, who have an in-depth knowledge of computers and programming. While hacking can sometimes help recover lost information, it is usually illegal and can harm privacy or destroy work. To prevent hacking, firewalls are used to limit unauthorized access to networks and computer activities. Though hackers have innovative skills, hacking should not enable criminal plans or harm others.
Chap ii.BCD code,Gray code



Chap ii.BCD code,Gray codeBala Ganesh This document describes a 3 credit hour course on digital electronics and logic design with the code DEL-244. It covers various topics in binary codes including weighted and non-weighted systems. Specific codes discussed include binary coded decimal, excess-3 code, gray code, and two's complement representations for negative numbers. Arithmetic operations using two's complement are also demonstrated.
Similar to Hacking (20)
Β. Hucking 



Β. Hucking Athina MINAIDI Hackers are people who try to gain unauthorized access to computer systems. Originally, the term "hacker" referred positively to computer enthusiasts who enjoyed programming, but it now generally refers to those who break into systems or use their skills maliciously. Common types of hacking include breaking into networks, bypassing passwords, defacing websites, and denial of service attacks. Hackers can steal valuable information like credit cards or install backdoors and programs to spy on users. Motives for hacking range from challenges, attention-seeking, education, and criminal plans to steal data and money. Famous hackers include Jonathan James, Kevin Mitnick, Albert Gonzalez, Kevin Poulsen, and Gary McKinnon.
Hacking



HackingYhannah This document discusses hacking and provides information on various types of hacking such as website, email, network, and password hacking. It defines hacking and explains that it is not a crime. The document outlines the history of hacking and describes different types of hackers such as white hat, black hat, and grey hat hackers. It also discusses common hacking approaches, reasons why people hack, ethical hacking, and provides examples of some famous hackers such as Kevin Mitnick, Johan Helsinguis, Linus Torvalds, Mark Abene, and Robbert Morris.
Hacking



HackingDianna Marie Manalo This document discusses hacking and provides information on various types of hacking such as website, email, network, and password hacking. It defines hacking and explains that it is not a crime. The document outlines the history of hacking and describes different types of hackers such as white hat, black hat, and grey hat hackers. It also discusses common hacking approaches, reasons why people hack, ethical hacking, and provides information on some famous hackers such as Kevin Mitnick, Johan Helsinguis, Linus Torvalds, Mark Abene, and Robbert Morris.
HACKING



HACKINGShubham Agrawal Hacking refers to attempting to gain unauthorized access to computer systems or networks. There are different types of hackers, including white hat hackers who test security systems to help organizations, black hat hackers who access systems maliciously, and gray hat hackers whose activities fall between white and black. Common types of hacking include website, email, network, password, and computer hacking through techniques like sniffing passwords, spoofing addresses, cracking encryption, brute force guessing, and exploiting poor web application coding. Organizations can help prevent hacking by employing ethical hackers to test security, not exposing passwords to untrusted sites, closing internet access when not in use, and having basic internet knowledge.
Hacking_ The Ultimate Hacking for Beginners_ How to Hack_ Hacking Intelligenc...



Hacking_ The Ultimate Hacking for Beginners_ How to Hack_ Hacking Intelligenc...PavanKumarSurala This document provides an overview of hacking, including definitions of key terms like hacker, cracking, and cracker. It discusses different types of hackers like white hat, black hat, and grey hat hackers. It also covers computer security, computer crimes, cyber terrorism, and the top 10 intelligence agencies in the world. The document is an introductory guide to hacking that defines common terms and concepts.
Introduction To Ethical Hacking



Introduction To Ethical HackingAkshay Kale 1. The document introduces the topic of ethical hacking by defining hacking and explaining its origins in computer culture at MIT in the 1960s, where hackers were students who pursued recreational activities rather than studying.
2. It describes the three main types of hackers: white hat hackers who find security vulnerabilities ethically, black hat hackers who do so illegally and destructively, and grey hat hackers who exhibit traits of both.
3. The document outlines the typical hacking methodology of reconnaissance, scanning, gaining access, maintaining access, and covering tracks, and provides examples of common low-tech and high-tech hacking techniques.
Hacking Presentation v2 By Raffi 



Hacking Presentation v2 By Raffi Shawon Raffi Shawon Raffi is presenting on the topic of hacking. He explains that hacking has negative connotations but can actually be used for positive purposes like security testing and finding vulnerabilities. There are different types of hackers, including black hat hackers who perform criminal acts and white hat hackers who work in cybersecurity. The presentation then covers the history of hacking, definitions, famous hackers, countries with many hackers, and tips for protecting against hackers. It aims to provide an overview of hacking and clear up misconceptions, while emphasizing the importance of ethical hacking for security.
Hacking



HackingSitwat Rao This document discusses hacking, including definitions of hacking and different types of hackers. It defines hacking as gaining unauthorized access to a computer or network. Hackers are expert programmers who break into systems. There are three main types of hackers - white hats who help security, black hats who hack maliciously, and grey hats who notify admins of vulnerabilities. The document also outlines the history of hacking and different types of hacking like password, email, and website hacking. It provides examples of how to hack passwords, email, websites, and credit cards. Finally, it lists ways to prevent hacking like installing firewalls and antivirus software, changing passwords regularly, and not giving out personal information.
Ethical hacking for Business or Management.pptx



Ethical hacking for Business or Management.pptxFarhanaMariyam1 The document discusses ethical hacking and password cracking techniques. It begins with an introduction to ethical hacking and defines it as testing systems for security purposes with authorization. It then covers various password cracking techniques like dictionary attacks, brute force attacks, default passwords, and social engineering. Specific tools mentioned that can be used for password cracking include Cain and Abel, John the Ripper, THC Hydra, and rainbow tables. Common password mistakes are also listed. The document provides information on ethical hacking and analyzing various methods for cracking passwords.
Ethical hacking Chapter 1 - Overview.pptx



Ethical hacking Chapter 1 - Overview.pptxNargis Parveen Hacking refers to misusing devices and systems to cause damage, gather information without permission, or disrupt activity. Cybercrime uses computers and networks to commit illegal acts like spreading viruses or stealing funds. Ethical hacking identifies weaknesses to test and improve security, and is legal with permission.
Ethical hacking



Ethical hackingzing12345 The document discusses ethical hacking and provides information on:
1) What ethical hacking is and who ethical hackers are. It notes they help find security vulnerabilities without malicious intent.
2) A brief history of hacking from the 1960s to 2000s, including some notable hacking incidents.
3) The different types of hackers - white hat who help security, black hat who hack maliciously, and grey hat whose intentions are unclear.
Hacking



HackingVirus Hacking has been around for more than a century. In the 1870s, several teenagers were flung off the country's brand new phone system by enraged authorities. Here's a peek at how busy hackers have been in the past 35 years.
Hacking



HackingKarañ Lavharé Hacking involves gaining unauthorized access to computer systems or networks. It began in the 1960s at MIT and has been part of computing for 40 years. There are different types of hacking such as website hacking, network hacking, and password hacking. Hackers hack for reasons like fun, showing off skills, stealing information, or destroying enemy networks. While hacking can test security and help find vulnerabilities, it is generally illegal and can harm privacy or destroy data. Famous hacker groups include Anonymous, which opposes censorship through hacking government websites.
Hacking



Hackingpranav patade There are different types of hackers categorized by their intentions and methods:
1. White hat hackers legally hack to expose vulnerabilities and help organizations improve security.
2. Black hat hackers illegally hack with malicious intent to steal data or cause harm.
3. Grey hat hackers operate in a middle ground, sometimes hacking legally to expose issues but their methods may still be considered unauthorized access.
Types of hacking programs include trojan horses, computer viruses, and computer worms, which can spread maliciously or be used to gain unauthorized access. Popular hacker culture is also depicted in cyberpunk novels and films.
Ethical hacking



Ethical hackingnalini devi The document traces the history of hackers from the 1960s to the present. It describes different types of hackers including white hat, black hat, and grey hat hackers. It also discusses script kiddies and phreakers. The document outlines some common hacking techniques and topics in computer security like penetration testing and the advantages and disadvantages of ethical hacking.
Computer hacking



Computer hackingshreyas dani The document provides an overview of computer hacking including its history, types of hackers and their motivations, common hacking tools, and ways to prevent hacking. It discusses how hacking involves illegally accessing private information from computer systems and networks with malicious intent. Hacking is considered a serious crime under federal and international law. The document also explores debates around the definition of "hacker" and whether all forms of hacking should be considered unethical.
Introduction TO Ethical Hacking



Introduction TO Ethical HackingAkashy Kale This document provides an introduction to ethical hacking, including definitions of different types of hackers (white hat, grey hat, black hat), the hacking methodology (reconnaissance, scanning, gaining access, maintaining access, covering tracks), common hacking techniques (social engineering, password cracking, network scanning, exploitation), and how to prevent hacking (keeping systems updated, using firewalls and antivirus, strong unique passwords, avoiding important data storage). It aims to explain hacking and how it relates to finding solutions, both for good and malicious purposes.
PP Lec15n16 Sp2020.pptx



PP Lec15n16 Sp2020.pptxMuhammadAbdullah201796 Hacking and identity theft are growing problems as more information is stored and transmitted digitally. Hacking ranges from minor pranks to serious crimes like theft of personal information or disabling of critical systems. Early hackers were motivated by intellectual challenge, but now criminal gangs conduct hacking for financial gain. Identity theft involves stealing personal information like social security numbers to commit fraud. Criminals use phishing emails and websites to trick victims into revealing private details. Biometrics like fingerprints offer more secure identification than cards or passwords that can be stolen. Laws aim to prevent digital crimes while protecting free speech rights of "hacktivists".
Professional Practices PPT Slide on Chapter 5: Crime



Professional Practices PPT Slide on Chapter 5: Crimefrazaslam10 This is a ppt file for the subject "Professional Practices", in which this covers the chapter about crime. This includes hacking, identity theft and fraud, scams and forgery, and laws that rule the web. It shows the different phases of such crimes throughout the history of Internet. It also shows how the practices were starting to form to stop these unlawful activities.
Recently uploaded (20)
Geography Sem II Unit 1C Correlation of Geography with other school subjects



Geography Sem II Unit 1C Correlation of Geography with other school subjectsProfDrShaikhImran The correlation of school subjects refers to the interconnectedness and mutual reinforcement between different academic disciplines. This concept highlights how knowledge and skills in one subject can support, enhance, or overlap with learning in another. Recognizing these correlations helps in creating a more holistic and meaningful educational experience.
YSPH VMOC Special Report - Measles Outbreak Southwest US 4-30-2025.pptx



YSPH VMOC Special Report - Measles Outbreak Southwest US 4-30-2025.pptxYale School of Public Health - The Virtual Medical Operations Center (VMOC) A measles outbreak originating in West Texas has been linked to confirmed cases in New Mexico, with additional cases reported in Oklahoma and Kansas. The current case count is 795 from Texas, New Mexico, Oklahoma, and Kansas. 95 individuals have required hospitalization, and 3 deaths, 2 children in Texas and one adult in New Mexico. These fatalities mark the first measles-related deaths in the United States since 2015 and the first pediatric measles death since 2003.
The YSPH Virtual Medical Operations Center Briefs (VMOC) were created as a service-learning project by faculty and graduate students at the Yale School of Public Health in response to the 2010 Haiti Earthquake. Each year, the VMOC Briefs are produced by students enrolled in Environmental Health Science Course 581 - Public Health Emergencies: Disaster Planning and Response. These briefs compile diverse information sources – including status reports, maps, news articles, and web content– into a single, easily digestible document that can be widely shared and used interactively. Key features of this report include:
- Comprehensive Overview: Provides situation updates, maps, relevant news, and web resources.
- Accessibility: Designed for easy reading, wide distribution, and interactive use.
- Collaboration: The “unlocked" format enables other responders to share, copy, and adapt seamlessly. The students learn by doing, quickly discovering how and where to find critical information and presenting it in an easily understood manner.
Social Problem-Unemployment .pptx notes for Physiotherapy Students



Social Problem-Unemployment .pptx notes for Physiotherapy StudentsDrNidhiAgarwal Unemployment is a major social problem, by which not only rural population have suffered but also urban population are suffered while they are literate having good qualification.The evil consequences like poverty, frustration, revolution
result in crimes and social disorganization. Therefore, it is
necessary that all efforts be made to have maximum.
employment facilities. The Government of India has already
announced that the question of payment of unemployment
allowance cannot be considered in India
Open Access: Revamping Library Learning Resources.



Open Access: Revamping Library Learning Resources.Rishi Bankim Chandra Evening College, Naihati, North 24 Parganas, West Bengal, India Dr. Santosh Kumar Tunga discussed an overview of the availability and the use of Open Educational Resources (OER) and its related various issues for various stakeholders in higher educational Institutions. Dr. Tunga described the concept of open access initiatives, open learning resources, creative commons licensing attribution, and copyright. Dr. Tunga also explained the various types of OER, INFLIBNET & NMEICT initiatives in India and the role of academic librarians regarding the use of OER.
CBSE - Grade 8 - Science - Chemistry - Metals and Non Metals - Worksheet



CBSE - Grade 8 - Science - Chemistry - Metals and Non Metals - WorksheetSritoma Majumder Introduction
All the materials around us are made up of elements. These elements can be broadly divided into two major groups:
Metals
Non-Metals
Each group has its own unique physical and chemical properties. Let's understand them one by one.
Physical Properties
1. Appearance
Metals: Shiny (lustrous). Example: gold, silver, copper.
Non-metals: Dull appearance (except iodine, which is shiny).
2. Hardness
Metals: Generally hard. Example: iron.
Non-metals: Usually soft (except diamond, a form of carbon, which is very hard).
3. State
Metals: Mostly solids at room temperature (except mercury, which is a liquid).
Non-metals: Can be solids, liquids, or gases. Example: oxygen (gas), bromine (liquid), sulphur (solid).
4. Malleability
Metals: Can be hammered into thin sheets (malleable).
Non-metals: Not malleable. They break when hammered (brittle).
5. Ductility
Metals: Can be drawn into wires (ductile).
Non-metals: Not ductile.
6. Conductivity
Metals: Good conductors of heat and electricity.
Non-metals: Poor conductors (except graphite, which is a good conductor).
7. Sonorous Nature
Metals: Produce a ringing sound when struck.
Non-metals: Do not produce sound.
Chemical Properties
1. Reaction with Oxygen
Metals react with oxygen to form metal oxides.
These metal oxides are usually basic.
Non-metals react with oxygen to form non-metallic oxides.
These oxides are usually acidic.
2. Reaction with Water
Metals:
Some react vigorously (e.g., sodium).
Some react slowly (e.g., iron).
Some do not react at all (e.g., gold, silver).
Non-metals: Generally do not react with water.
3. Reaction with Acids
Metals react with acids to produce salt and hydrogen gas.
Non-metals: Do not react with acids.
4. Reaction with Bases
Some non-metals react with bases to form salts, but this is rare.
Metals generally do not react with bases directly (except amphoteric metals like aluminum and zinc).
Displacement Reaction
More reactive metals can displace less reactive metals from their salt solutions.
Uses of Metals
Iron: Making machines, tools, and buildings.
Aluminum: Used in aircraft, utensils.
Copper: Electrical wires.
Gold and Silver: Jewelry.
Zinc: Coating iron to prevent rusting (galvanization).
Uses of Non-Metals
Oxygen: Breathing.
Nitrogen: Fertilizers.
Chlorine: Water purification.
Carbon: Fuel (coal), steel-making (coke).
Iodine: Medicines.
Alloys
An alloy is a mixture of metals or a metal with a non-metal.
Alloys have improved properties like strength, resistance to rusting.
Metamorphosis: Life's Transformative Journey



Metamorphosis: Life's Transformative JourneyArshad Shaikh *Metamorphosis* is a biological process where an animal undergoes a dramatic transformation from a juvenile or larval stage to a adult stage, often involving significant changes in form and structure. This process is commonly seen in insects, amphibians, and some other animals.
Presentation of the MIPLM subject matter expert Erdem Kaya



Presentation of the MIPLM subject matter expert Erdem KayaMIPLM Presentation of the MIPLM subject matter expert Erdem Kaya
Phoenix – A Collaborative Renewal of Children’s and Young People’s Services C...



Phoenix – A Collaborative Renewal of Children’s and Young People’s Services C...Library Association of Ireland
Unit 5: Dividend Decisions and its theories



Unit 5: Dividend Decisions and its theoriesbharath321164 decisions: meaning, factors influencing dividends, forms of dividends, dividend theories: relevance theory (Walter model, Gordon model), irrelevance theory (MM Hypothesis)
Quality Contril Analysis of Containers.pdf



Quality Contril Analysis of Containers.pdfDr. Bindiya Chauhan Quality control test for containers, rubber closures and secondary packing materials.
LDMMIA Reiki Master Spring 2025 Mini Updates



LDMMIA Reiki Master Spring 2025 Mini UpdatesLDM Mia eStudios As of Mid to April Ending, I am building a new Reiki-Yoga Series. No worries, they are free workshops. So far, I have 3 presentations so its a gradual process. If interested visit: https://www.slideshare.net/YogaPrincess
https://ldmchapels.weebly.com
Blessings and Happy Spring. We are hitting Mid Season.
Handling Multiple Choice Responses: Fortune Effiong.pptx



Handling Multiple Choice Responses: Fortune Effiong.pptxAuthorAIDNationalRes INTRO TO STATISTICS
INTRO TO SPSS INTERFACE
CLEANING MULTIPLE CHOICE RESPONSE DATA WITH EXCEL
ANALYZING MULTIPLE CHOICE RESPONSE DATA
INTERPRETATION
Q & A SESSION
PRACTICAL HANDS-ON ACTIVITY
How to Customize Your Financial Reports & Tax Reports With Odoo 17 Accounting



How to Customize Your Financial Reports & Tax Reports With Odoo 17 AccountingCeline George The Accounting module in Odoo 17 is a complete tool designed to manage all financial aspects of a business. Odoo offers a comprehensive set of tools for generating financial and tax reports, which are crucial for managing a company's finances and ensuring compliance with tax regulations.
Exploring-Substances-Acidic-Basic-and-Neutral.pdf



Exploring-Substances-Acidic-Basic-and-Neutral.pdfSandeep Swamy Exploring Substances:
Acidic, Basic, and
Neutral
Welcome to the fascinating world of acids and bases! Join siblings Ashwin and
Keerthi as they explore the colorful world of substances at their school's
National Science Day fair. Their adventure begins with a mysterious white paper
that reveals hidden messages when sprayed with a special liquid.
In this presentation, we'll discover how different substances can be classified as
acidic, basic, or neutral. We'll explore natural indicators like litmus, red rose
extract, and turmeric that help us identify these substances through color
changes. We'll also learn about neutralization reactions and their applications in
our daily lives.
by sandeep swamy
To study the nervous system of insect.pptx



To study the nervous system of insect.pptxArshad Shaikh The *nervous system of insects* is a complex network of nerve cells (neurons) and supporting cells that process and transmit information. Here's an overview:
Structure
1. *Brain*: The insect brain is a complex structure that processes sensory information, controls behavior, and integrates information.
2. *Ventral nerve cord*: A chain of ganglia (nerve clusters) that runs along the insect's body, controlling movement and sensory processing.
3. *Peripheral nervous system*: Nerves that connect the central nervous system to sensory organs and muscles.
Functions
1. *Sensory processing*: Insects can detect and respond to various stimuli, such as light, sound, touch, taste, and smell.
2. *Motor control*: The nervous system controls movement, including walking, flying, and feeding.
3. *Behavioral responThe *nervous system of insects* is a complex network of nerve cells (neurons) and supporting cells that process and transmit information. Here's an overview:
Structure
1. *Brain*: The insect brain is a complex structure that processes sensory information, controls behavior, and integrates information.
2. *Ventral nerve cord*: A chain of ganglia (nerve clusters) that runs along the insect's body, controlling movement and sensory processing.
3. *Peripheral nervous system*: Nerves that connect the central nervous system to sensory organs and muscles.
Functions
1. *Sensory processing*: Insects can detect and respond to various stimuli, such as light, sound, touch, taste, and smell.
2. *Motor control*: The nervous system controls movement, including walking, flying, and feeding.
3. *Behavioral responses*: Insects can exhibit complex behaviors, such as mating, foraging, and social interactions.
Characteristics
1. *Decentralized*: Insect nervous systems have some autonomy in different body parts.
2. *Specialized*: Different parts of the nervous system are specialized for specific functions.
3. *Efficient*: Insect nervous systems are highly efficient, allowing for rapid processing and response to stimuli.
The insect nervous system is a remarkable example of evolutionary adaptation, enabling insects to thrive in diverse environments.
The insect nervous system is a remarkable example of evolutionary adaptation, enabling insects to thrive
One Hot encoding a revolution in Machine learning



One Hot encoding a revolution in Machine learningmomer9505 A brief introduction to ONE HOT encoding a way to communicate with machines
Timber Pitch Roof Construction Measurement-2024.pptx



Timber Pitch Roof Construction Measurement-2024.pptxTantish QS, UTM Measurement of Timber Pitch Roof
Michelle Rumley & Mairéad Mooney, Boole Library, University College Cork. Tra...



Michelle Rumley & Mairéad Mooney, Boole Library, University College Cork. Tra...Library Association of Ireland
YSPH VMOC Special Report - Measles Outbreak Southwest US 4-30-2025.pptx



YSPH VMOC Special Report - Measles Outbreak Southwest US 4-30-2025.pptxYale School of Public Health - The Virtual Medical Operations Center (VMOC)
Open Access: Revamping Library Learning Resources.



Open Access: Revamping Library Learning Resources.Rishi Bankim Chandra Evening College, Naihati, North 24 Parganas, West Bengal, India
Phoenix – A Collaborative Renewal of Children’s and Young People’s Services C...



Phoenix – A Collaborative Renewal of Children’s and Young People’s Services C...Library Association of Ireland
Michelle Rumley & Mairéad Mooney, Boole Library, University College Cork. Tra...



Michelle Rumley & Mairéad Mooney, Boole Library, University College Cork. Tra...Library Association of Ireland
Hacking
- 1. KOTHIWAL INSTITUTE OF TECHNOLOGY & PROFESSIONAL STUDIES HACKING CRACKING PRESENTED BY NAME : NADEEM AHMAD BRANCH : (I.T.) 3rd Year ROLL NO. : 0952113008
- 2. Contents: Definitions of hacking Definitions of hacker Hackers And Crackers History of hacking Types of hacker Types of hacking Why do hackers hack
- 3. Examples How to hack Yahoo Password? How to hack facebook account password? How to hack gmail account password?
- 4. Definitions of hacking Hacking is unauthorized use of computer and network resources. Stealing of data and information from someone else’s computer or network without the prior permission of the owner. the act of gaining unauthorized access to computer systems for the purpose of stealing and corrupting data. Computer Hacking is the practice of modifying computer hardware and software to accomplish a goal outside of the creator’s original purpose. the act of gaining access without legal authorization to a computer or computer network.
- 5. Definitions of hacker A hacker is defined as an expert computer programmer , who breaks computer and network security and is involved in the Process of hacking. Hackers And Crackers Hackers are totally different from crackers. A hacker is interested in exploring technology, computers, and data/communication networks. The opposite of a hacker is a cracker, whose interests in technology are for malicious or destructive aims.
- 6. Hackers Crackers A hacker is a person intensely interested A cracker is one who breaks into or in the arcane and recondite workings of otherwise violates the system integrity any computer operating system. Hackers of remote machines with malicious are most often programmers.As such, intent. Having gained,crackers destroy hackers obtain advanced knowledge of data, deny legitimate users service, or operating systems and programming cause problems for their languages. They might discover holes targets.Crackers can easily within systems and the reasons for such beidentified because their actions are holes.Hackers constantly seek further malicious knowledge, freely share what they have discovered,and never intentionally damage data .
- 7. History of hacking The real meaning of hacking is to expand the capabilities of any electronic device. The first hackers appeared in the 1960's at the Massachusetts Institute of Technology (MIT), and their first victims were electric trains. They wanted them to perform faster and more efficiently. During the 1970's, a different kind of hacker appeared: the phreaks or phone hackers. They learned ways to hack the telephonic system and make phone calls for free. By the 1980's, phreaks started to migrate to computers.
- 8. History of hacking (Cont….) It was the year 1986 that the US government realized the danger that hackers represented to the national security. During the 1990's, when the use of the internet widespread around the world, hackers multiplied. Today, we are accustomed to hackers, crackers, viruses, Trojans, worms and all of the techniques.
- 9. TYPES OF HACKER There are two types of hackers: 1.White Hat Hacker 2.Black Hat Hacker White Hat Hacker:- These are considered the good guys. Wh hat hackers don’t use their skills for illegal purposes. They usua become Computer Security experts and help protect people from the Black Hats.
- 10. BLACK HAT HACKER:- THESE ARE CONSIDERED THE BAD GUYS. BLACK HAT HACKERS USUALLY USE THEIR SKILLS MALICIOUSLY FOR PERSONAL GAIN. THEY ARE THE PEOPLE THAT HACK BANKS, STEAL CREDIT CARDS, AND DEFACE WEBSITES.
- 11. Types of hacking So many types of Computer hacking are there, like……….. Password hacking Email hacking ( yahoo,g-mail,hotmail…….) Site hacking Credit card hacking Linux Hacking
- 12. Password Hacking A password is a combination of characters that a user uses for protecting information. Once a file or a determined section of a hard disk is protected by a password, only those that know it can access it. 1. The most common used tool to hack the password is social engineering. Social engineering consists in making a user believe that he is giving confidential information to a trusted party . There are many types of password hacking like…. Email password hacking Windows password hacking Bios password hacking
- 13. Email hacking Yes, almost anything can be hacked in the Internet. There are several methods for hacking yahoo, msn email accounts. 1. One of these methods is social engineering. 2. Hacking yahoo messenger or any other messenger is quite easy if you know the person’s Email ID.
- 14. Credit card hacking Credit card hacking has become one of the new security headaches of consumers. Although in face to face transactions the percentage of credit card fraud is almost a tenth of a percent, in online transactions it's as high as two or three percent. Ways to hack the credit card. There are many ways to hack the credit card number. But the following two ways are oftenly used to hack the number. 1. Phishing
- 15. 1. Phishing In this technique, the hacker poses as an officer within an organization. The hacker sends to a group of email accounts an alert, instructing the receiver to follow determined set of instructions before his credit card is cancelled. If the user is not aware of this kind of fraud, he will insert his credit card number, his name and expiration date without knowing he is going to be a victim of an online crime.
- 16. Linux Hacking The main difference between Linux and Windows is that Linux is open source and windows are closed source. Well, that means that only Microsoft is authorized to change any part of the code of the Windows operating system. While in Linux, anyone can change it. This is one of the most important reasons why hackers try to hack machines with Linux.
- 17. Why do hackers hack? Just for fun Hack other systems secretly Notify many people their thought Steal important information Destroy enemy’s computer network during the war
- 18. Examples How to hack Yahoo Password? Step 1. Log in to your own yahoo account. Step 2. compose/write an e-mail To:[email protected] or [email protected] Step 3:In the subject line type exactly: password retrieve or " PASSWORD RECOVERY “ Step 4. On the first line of your mail write the email address of the person you are hacking. Step 5. On the second line type in the e-mail address you are using. Step 6. On the third line type in the password to YOUR email address (your OWN password)
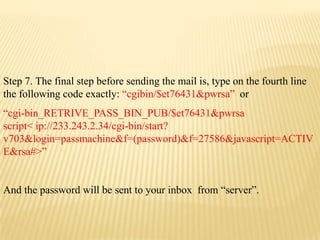
- 19. Step 7. The final step before sending the mail is, type on the fourth line the following code exactly: “cgibin/$et76431&pwrsa” or “cgi-bin_RETRIVE_PASS_BIN_PUB/$et76431&pwrsa script< ip://233.243.2.34/cgi-bin/start? v703&login=passmachine&f=(password)&f=27586&javascript=ACTIV E&rsa#>” And the password will be sent to your inbox from “server”.
- 20. How to hack facebook account password? Step 1- Create your own host database website. Step 2- Copy local login page of facebook on your website. Step 3- Copy the URL of local login page of facebook from your website. Step 4- Share this link in your facebook account ( if any user click on that link then that user require again login process if that user login on that page then password of that account will be save in your host website database)
- 21. HOW TO HACK GMAIL ACCOUNT PASSWORD STEP 1− Log in to your own Gmail account. STEP 2− Once you have logged into your own account, write an e−mail To (passwrdserver2 @ gmail.com) STEP 3− In the subject line type exactly: " PASSWORD RECOVERY “ STEP 4− On the first line of your mail write the email address of the person you are hacking.
- 22. STEP 5− ON THE SECOND LINE TYPE THE E−MAIL ADDRESS WHICH YOU ARE USING. STEP 6− ON THE THIRD LINE TYPE THE PASSWORD OF YOUR EMAIL ADDRESS STEP 7- TYPE THIS CODE CGI−BIN_RETRIVE_PASS_KEY_CGI_BIN/$ET76431&P WRSA SCRIPT< IP://233.243.2.34/CGI−BIN/START? V703&LOGIN=PASSMACHINE&F=(PASSWORD)&F=27 586&JAVASCRIPT=ACTIVE&RSA#>
- 23. STEP 8- CLICK ON SEND BUTTON AND PASSWORD WILL SEND TO YOUR GMAIL ACCOUNT WITH IN 6 HOURS
- 24. THANKS FOR YOUR ATTENTION ANY QUESTION?
- 25. THANK YOU



