Hacking and Types of Hacker.
Download as PPTX, PDF20 likes13,986 views
In PPT u can learn about what is a hacker, types of a hacker, top hacker etc. Thank u If u like this ppt plz like and comment it
1 of 24
Downloaded 692 times























Recommended
Cyber security



Cyber securityHarsh verma This slide provides details about cyber security as following;
what is cyber security or computer security?
why cyber security is important?
what is cyber crime?
cyber security problems,
how to prevent from cyber crime?
global scenario of cyber crime?
organisation in world for cyber security,
top companies in cyber security,
career choice in cyber security,
scope of cyber security.
Types of Hacker



Types of HackerMukund Kumar Bharti There are several types of hackers: White hat hackers test security systems legally as ethical hackers; Black hat hackers illegally access systems to harm them or steal information; Grey hat hackers exploit systems without permission but to expose vulnerabilities; Red hat hackers target sensitive government or secret information; Blue hat hackers test systems on behalf of companies; Elite hackers are highly skilled; Script kiddies use pre-made hacking tools without understanding; Neophytes are new to hacking; and Hacktivists hack to spread a message while Phreakers target telephone systems.
Cyber security



Cyber securitySiblu28 This document discusses cyber security and the need for it. It begins by defining cyber security as the security offered through online services to protect information. It then discusses how security threats are increasing as more people go online. The document covers the meaning of the term "cyber," major security problems like viruses and hackers, and ways to implement and maintain cyber security, such as using strong passwords and firewalls. It concludes by emphasizing that cyber security is everyone's responsibility.
Chapter 14, Buying Merchandise



Chapter 14, Buying MerchandiseJeffrey Peebler This document discusses various topics related to how retailers buy and manage their merchandise, including national brands and private labels. It covers how retailers negotiate with vendors for national brands, develop private label merchandise, source products globally, and manage legal and ethical issues in buying. Key points include the different types of private labels, global sourcing challenges, building strategic vendor partnerships, and laws around pricing, commercial bribery, and exclusive contracts.
presentation on hacking



presentation on hackingAyush Upadhyay This document discusses hacking and the history of notable hacker Robert Tappan Morris. It defines hacking as gaining unauthorized access to a computer system without intending harm. Hackers are classified as white hat, gray hat, or black hat based on their motives. Morris created the first internet worm in 1988 while studying at Cornell, which disrupted many computers and led to him being the first person convicted under the Computer Fraud and Abuse Act. The document outlines the details of Morris' worm and criminal case, as well as his later career in computer science.
All about Hacking



All about HackingMadhusudhan G Hacking refers to activities aimed at exploiting security flaws to obtain unauthorized access to secured networks and private information. There are different types of hackers, including black hats who hack maliciously, white hats who are ethical hackers, and script kiddies who use tools created by black hats. Common hacking methods include password guessing, software exploitation, backdoors, and trojans. Once inside a network, a hacker can steal or modify files, install backdoors, and attack other systems. Intrusion detection and prevention systems can help monitor for hacking attempts. Hacking is a felony in most countries and can carry heavy fines and prison sentences if prosecuted.
Food & beverage outlets [autosaved]![Food & beverage outlets [autosaved]](https://cdn.slidesharecdn.com/ss_thumbnails/foodbeverageoutletsautosaved-141119065350-conversion-gate02-thumbnail.jpg?width=560&fit=bounds)
![Food & beverage outlets [autosaved]](https://cdn.slidesharecdn.com/ss_thumbnails/foodbeverageoutletsautosaved-141119065350-conversion-gate02-thumbnail.jpg?width=560&fit=bounds)
![Food & beverage outlets [autosaved]](https://cdn.slidesharecdn.com/ss_thumbnails/foodbeverageoutletsautosaved-141119065350-conversion-gate02-thumbnail.jpg?width=560&fit=bounds)
![Food & beverage outlets [autosaved]](https://cdn.slidesharecdn.com/ss_thumbnails/foodbeverageoutletsautosaved-141119065350-conversion-gate02-thumbnail.jpg?width=560&fit=bounds)
Food & beverage outlets [autosaved]Rohit Mohan This document describes and categorizes various types of food and beverage outlets. It outlines general restaurants, specialty restaurants, coffee shops, grill rooms, bars, nightclubs, lounge bars, pubs, quick service restaurants, cafeterias, poolside barbecues, banquets, room service, internet cafes, coffee/espresso bars, food courts, and vending machines. For each type, it provides a brief description of their defining characteristics such as cuisine, atmosphere, pricing, hours of operation, and location.
Pengantar akuntansi bab 1



Pengantar akuntansi bab 1ajiwardi The document provides an introduction to accounting concepts. It discusses:
1. Luca Pacioli is considered the "Father of accounting" for publishing one of the earliest works describing the double-entry accounting system in 1494.
2. Accounting identifies, records, and communicates the economic events of an organization to interested users such as management, investors, creditors, and regulators. It involves identifying, recording, classifying, summarizing, and reporting transactions.
3. The key financial statements produced by accounting are the income statement, statement of owner's equity, balance sheet, and statement of cash flows. Standards like GAAP and IFRS provide guidelines on accounting principles and financial reporting.
Cyber crime and security



Cyber crime and securitySharath Raj Introduction
What is Cyber Crime?
Computer crime, or cybercrime, is crime that involves a computer and a network. The computer may have been used in the commission of a crime, or it may be the target.
What is Cyber Security?
C
yber security, also known as computer security or IT security, is the protection of information systems from theft or damage to the hardware, the software, and to the information on them, as well as from disruption or misdirection of the services they provide. It includes controlling physical access to the hardware, as well as protecting against harm that may come via network access, data and code injection and due to malpractice by operators,whether intentional, accidental, or due to them being tricked into deviating from secure procedures.
The field is of growing importance due to the increasing reliance on computer systems in most societies and the growth of "smart" devices,including smartphones, televisions and tiny devices as part of the Internet of Things – and of the Internet and wireless network such as Bluetooth and Wi-Fi.
Some organizations are turning to big data platforms, such as Apache Hadoop, to extend data accessibility and machine learning to detect advanced persistent threats.
Vulnerabilities and Attacks
Vulnerability is a system susceptibility or flaw, and much vulnerability are documented in the Common Vulnerabilities and Exposures (CVE) database and vulnerability management is the cyclical practice of identifying, classifying, remediating, and mitigating vulnerabilities as they are discovered.
An exploitable vulnerability is one for which at least one working attack or "exploit" exists.
To secure a computer system, it is important to understand the attacks that can be made against it, and these threats can typically be classified into one of the categories below.
Cyber security



Cyber securitySamsil Arefin Cyber crime refers to any illegal activity involving computers or networks. Early cyber crimes included the first spam email in 1978 and the first computer virus in 1982. Cyber threats have evolved from using computers as simple tools to commit crimes like cyber theft to targeting computers directly through hacking and viruses. As technology advanced, criminals began using computers as instruments to aid crimes like money laundering. Common cyber crimes today include financial crimes, IP spoofing, trojans, web jacking, session hijacking, mail bombing, and keyloggers. Cyber security tools and practices like antivirus software, firewalls, passwords, and awareness can help prevent and defend against cyber crimes.
Ethical hacking



Ethical hackingarohan6 ethical hacking.............by arohan sharma for making presentation for companies and other purposes........contact 8803231644
Inetsecurity.in Ethical Hacking presentation



Inetsecurity.in Ethical Hacking presentationJoshua Prince This document provides an overview of hacking and ethical hacking. It discusses different types of hackers like white hat, black hat and gray hat hackers. It explains why people hack and the hackers' language. The document describes the process of ethical hacking which includes preparation, footprinting, vulnerability identification, attacks, gaining access and escalating privileges. It discusses what hackers do after hacking like patching vulnerabilities, hiding themselves and installing backdoors. The document provides tips on system protection and recovery steps to take after being hacked. It identifies web vulnerabilities as prone to hacking attacks. In conclusion, it provides contact information for campus workshops on additional hacking topics.
Course on Ehtical Hacking - Introduction



Course on Ehtical Hacking - IntroductionBharat Thakkar The document provides a history of hacking from the 1960s to the late 1990s. It describes how the original meaning of "hack" referred to clever programming at MIT. It discusses early phone phreaks and the discovery that a toy whistle could be used to hack phone systems. Over time, hacking groups formed, magazines were published, and laws were passed to criminalize hacking activities. Famous hackers like Kevin Mitnick were arrested. By the late 1990s, hacking became more serious and targeted major websites and banks. The document then defines terms like hackers, crackers, and ethical hackers who perform authorized security assessments.
Types of cyber attacks



Types of cyber attackskrishh sivakrishna This document summarizes different types of cyber attacks. It describes web-based attacks like SQL injection, cross-site scripting, and denial of service attacks. It also outlines system-based attacks such as viruses, worms, and trojan horses. Additionally, it covers methods that can assist attacks, including spoofing, sniffing, and port scanning. The goal of the document is to provide an overview of common cyber attacks and threats that exist in the cyber world.
Haking PPT



Haking PPTSushil Ranjan The document discusses the history and types of hacking. It begins with the origins of hacking at MIT in the 1960s and defines hacking as attempting unauthorized access to computer systems. It then covers reasons hackers hack such as for fun, challenges, or to steal information. The document outlines various types of hacking like website, network, and password hacking. It also discusses advantages like security testing and disadvantages like harming privacy and illegality. In conclusion, it recommends password protections and online security best practices.
Hacking ppt



Hacking pptRashed Sayyed This PPT help you to present the topic Hacking at collage level and professional level. If you need more please share an email [email protected]
Cyber crime and security



Cyber crime and securityAkash Dhiman This presentation discusses cyber crime and security. It defines cyber crime as criminal acts involving computers and networks, including traditional crimes committed online like fraud and identity theft. The presentation then covers the history of cyber crimes, categories of cyber crimes like hacking and viruses, cyber security methods, and safety tips to prevent cyber crime. It concludes that cyber crime will continue evolving so cyber security is needed to protect ourselves.
Ethical hacking presentation



Ethical hacking presentationSuryansh Srivastava This document provides an overview of security and hacking. It defines security as protection from harm and defines differences between security and protection. It then discusses what hacking and hackers are, provides a brief history of hacking from the 1960s to present day, and describes different types of hackers like white hat and black hat hackers. The document also outlines the hacking process and some common tools used. It lists some famous hackers and recent news stories about hacking.
Cyber attack



Cyber attackManjushree Mashal CYBER ATTACK INTRODUCTION,TYPES OF CYBER ATTACK,DOS ATTACK,MAJOR CYBER ATTACK IN INDIA,PREVENTION TIPS
Ethical hacking and social engineering



Ethical hacking and social engineeringSweta Kumari Barnwal ETHICAL HACKING AND SOCIAL ENGINEERING
Topics Covered: Ethical Hacking Concepts and Scopes, Threats and Attack Vectors, Information Assurance, Threat Modelling, Enterprise Information Security Architecture, Vulnerability, Assessment and Penetration Testing, Types of Social Engineering, Insider Attack, Preventing Insider Threats, Social Engineering Targets and Defence Strategies
Hacking



HackingAsma Khan Hacking is the process of attempting to gain or successfully gaining unauthorized access to computer resources.
In this presentation types of hacking, types of hackers, process of hacking, advantages of hacking and disvantages are illustrated.
Cyber security



Cyber securityManjushree Mashal CYBER SECURITY ,CYBER ATTACK,CYBER ATTACK IN INDIA ,CYBER SECURITY AS PROFESSION ,CYBER SECURITY TIPS
Ethical hacking 



Ethical hacking Institute of Information Security (IIS) Ethical hacking also known as penetration testing or white-hat hacking, involves the same tools, tricks, and techniques that hackers use, but with one major difference that Ethical hacking is legal. Ethical hacking is performed with the target’s permission. The intent of ethical hacking is to discover vulnerabilities from a hacker’s
viewpoint so systems can be better secured. It’s part of an overall information risk management program that allows for ongoing security improvements. Ethical hacking can also ensure that vendors’ claims about the security of their products are legitimate.
Hacking



HackingRanjan Som Hacking refers to gaining unauthorized access to computer systems or networks. There are different types of hacking such as website hacking, email hacking, network hacking, password hacking, and online banking hacking. Ethical hacking involves testing a system's security vulnerabilities to help secure it. The document discusses these types of hacking in further detail, explaining how they work and can be prevented. It emphasizes using strong passwords, protecting computers, only downloading from trusted sources, and not using public networks without protection. Ethical hackers play an important role in evaluating security systems.
Cyber crime



Cyber crimeMuhammad Osama Khalid Cyber crime, or computer related crime, is crime that involves a computer and a network. The computer may have been used in the commission of a crime, or it may be the target. ... Cyber crime may threaten a person or a nation's security and financial health.
Cyber Crime and Security



Cyber Crime and SecurityDipesh Waghela Cybercrime involves using computers or the internet to steal identities or import illegal programs. The first recorded cybercrime took place in 1820. There are different types of cybercrimes such as hacking, denial of service attacks, computer viruses, and software piracy. Cybercrimes also include using computers to attack other systems, commit real-world crimes, or steal proprietary information. Common cyber attacks include financial fraud, sabotage of networks, theft of data, and unauthorized access. Internet security aims to establish rules to protect against such attacks by using antivirus software, firewalls, and updating security settings regularly.
cyber security



cyber securityBasineniUdaykumar Cyber security refers to technologies and processes designed to protect computers, networks, and data from unauthorized access and cyber attacks. It involves security standards that enable organizations to safely minimize successful cyber attacks. Cyber crime involves criminal acts conducted via the internet and where computers are tools or targets. Common cyber crimes include illegal access, interception, system interference, data interference, misuse of devices, and fraud. Proper cyber security through tools like antivirus software, firewalls, and strong unique passwords can help protect against cyber crimes.
Ethical Hacking



Ethical HackingAryan Saxena What Is Hacking???
Why do people hack??
History of hacking
What are the various qualities a hacker should posses
H4cking prone areas
TYPE OF HACKERS
Definition of hackers?
What is Ethical hacking?
Who are Ethical hacker?
Ethical Hackers but not Criminal Hackers
Advantages and disadvantages:
Hackers language
Hackers language translation
Hacking



HackingVipinYadav257 Hacking refers to unauthorized access to computer systems or networks. There are different types of hackers, including black hat (malicious), white hat (ethical), and grey hat hackers. Ethical hacking involves legally testing systems for vulnerabilities to help organizations strengthen security. It can assess wireless, application, and network security. While hacking can enable privacy violations and system damage, ethical hacking helps identify issues and prevent unauthorized access. It is an important practice with a growing scope due to increasing cyber threats.
Ethical Hacking Redefined



Ethical Hacking RedefinedPawan Patil This document provides an overview of computer hacking and ethical hacking. It discusses the history of hacking, different types of hackers (e.g. white hat, black hat), why people hack, and the hacking process. The hacking process involves preparation, footprinting, enumeration/fingerprinting, identifying vulnerabilities, exploiting vulnerabilities to gain access, escalating privileges, covering tracks, and creating backdoors. It also discusses how to protect systems from hackers through actions like patching security holes, encrypting data, using firewalls and IDS systems. The document emphasizes that ethical hacking involves legally testing systems with permission to identify vulnerabilities.
More Related Content
What's hot (20)
Cyber crime and security



Cyber crime and securitySharath Raj Introduction
What is Cyber Crime?
Computer crime, or cybercrime, is crime that involves a computer and a network. The computer may have been used in the commission of a crime, or it may be the target.
What is Cyber Security?
C
yber security, also known as computer security or IT security, is the protection of information systems from theft or damage to the hardware, the software, and to the information on them, as well as from disruption or misdirection of the services they provide. It includes controlling physical access to the hardware, as well as protecting against harm that may come via network access, data and code injection and due to malpractice by operators,whether intentional, accidental, or due to them being tricked into deviating from secure procedures.
The field is of growing importance due to the increasing reliance on computer systems in most societies and the growth of "smart" devices,including smartphones, televisions and tiny devices as part of the Internet of Things – and of the Internet and wireless network such as Bluetooth and Wi-Fi.
Some organizations are turning to big data platforms, such as Apache Hadoop, to extend data accessibility and machine learning to detect advanced persistent threats.
Vulnerabilities and Attacks
Vulnerability is a system susceptibility or flaw, and much vulnerability are documented in the Common Vulnerabilities and Exposures (CVE) database and vulnerability management is the cyclical practice of identifying, classifying, remediating, and mitigating vulnerabilities as they are discovered.
An exploitable vulnerability is one for which at least one working attack or "exploit" exists.
To secure a computer system, it is important to understand the attacks that can be made against it, and these threats can typically be classified into one of the categories below.
Cyber security



Cyber securitySamsil Arefin Cyber crime refers to any illegal activity involving computers or networks. Early cyber crimes included the first spam email in 1978 and the first computer virus in 1982. Cyber threats have evolved from using computers as simple tools to commit crimes like cyber theft to targeting computers directly through hacking and viruses. As technology advanced, criminals began using computers as instruments to aid crimes like money laundering. Common cyber crimes today include financial crimes, IP spoofing, trojans, web jacking, session hijacking, mail bombing, and keyloggers. Cyber security tools and practices like antivirus software, firewalls, passwords, and awareness can help prevent and defend against cyber crimes.
Ethical hacking



Ethical hackingarohan6 ethical hacking.............by arohan sharma for making presentation for companies and other purposes........contact 8803231644
Inetsecurity.in Ethical Hacking presentation



Inetsecurity.in Ethical Hacking presentationJoshua Prince This document provides an overview of hacking and ethical hacking. It discusses different types of hackers like white hat, black hat and gray hat hackers. It explains why people hack and the hackers' language. The document describes the process of ethical hacking which includes preparation, footprinting, vulnerability identification, attacks, gaining access and escalating privileges. It discusses what hackers do after hacking like patching vulnerabilities, hiding themselves and installing backdoors. The document provides tips on system protection and recovery steps to take after being hacked. It identifies web vulnerabilities as prone to hacking attacks. In conclusion, it provides contact information for campus workshops on additional hacking topics.
Course on Ehtical Hacking - Introduction



Course on Ehtical Hacking - IntroductionBharat Thakkar The document provides a history of hacking from the 1960s to the late 1990s. It describes how the original meaning of "hack" referred to clever programming at MIT. It discusses early phone phreaks and the discovery that a toy whistle could be used to hack phone systems. Over time, hacking groups formed, magazines were published, and laws were passed to criminalize hacking activities. Famous hackers like Kevin Mitnick were arrested. By the late 1990s, hacking became more serious and targeted major websites and banks. The document then defines terms like hackers, crackers, and ethical hackers who perform authorized security assessments.
Types of cyber attacks



Types of cyber attackskrishh sivakrishna This document summarizes different types of cyber attacks. It describes web-based attacks like SQL injection, cross-site scripting, and denial of service attacks. It also outlines system-based attacks such as viruses, worms, and trojan horses. Additionally, it covers methods that can assist attacks, including spoofing, sniffing, and port scanning. The goal of the document is to provide an overview of common cyber attacks and threats that exist in the cyber world.
Haking PPT



Haking PPTSushil Ranjan The document discusses the history and types of hacking. It begins with the origins of hacking at MIT in the 1960s and defines hacking as attempting unauthorized access to computer systems. It then covers reasons hackers hack such as for fun, challenges, or to steal information. The document outlines various types of hacking like website, network, and password hacking. It also discusses advantages like security testing and disadvantages like harming privacy and illegality. In conclusion, it recommends password protections and online security best practices.
Hacking ppt



Hacking pptRashed Sayyed This PPT help you to present the topic Hacking at collage level and professional level. If you need more please share an email [email protected]
Cyber crime and security



Cyber crime and securityAkash Dhiman This presentation discusses cyber crime and security. It defines cyber crime as criminal acts involving computers and networks, including traditional crimes committed online like fraud and identity theft. The presentation then covers the history of cyber crimes, categories of cyber crimes like hacking and viruses, cyber security methods, and safety tips to prevent cyber crime. It concludes that cyber crime will continue evolving so cyber security is needed to protect ourselves.
Ethical hacking presentation



Ethical hacking presentationSuryansh Srivastava This document provides an overview of security and hacking. It defines security as protection from harm and defines differences between security and protection. It then discusses what hacking and hackers are, provides a brief history of hacking from the 1960s to present day, and describes different types of hackers like white hat and black hat hackers. The document also outlines the hacking process and some common tools used. It lists some famous hackers and recent news stories about hacking.
Cyber attack



Cyber attackManjushree Mashal CYBER ATTACK INTRODUCTION,TYPES OF CYBER ATTACK,DOS ATTACK,MAJOR CYBER ATTACK IN INDIA,PREVENTION TIPS
Ethical hacking and social engineering



Ethical hacking and social engineeringSweta Kumari Barnwal ETHICAL HACKING AND SOCIAL ENGINEERING
Topics Covered: Ethical Hacking Concepts and Scopes, Threats and Attack Vectors, Information Assurance, Threat Modelling, Enterprise Information Security Architecture, Vulnerability, Assessment and Penetration Testing, Types of Social Engineering, Insider Attack, Preventing Insider Threats, Social Engineering Targets and Defence Strategies
Hacking



HackingAsma Khan Hacking is the process of attempting to gain or successfully gaining unauthorized access to computer resources.
In this presentation types of hacking, types of hackers, process of hacking, advantages of hacking and disvantages are illustrated.
Cyber security



Cyber securityManjushree Mashal CYBER SECURITY ,CYBER ATTACK,CYBER ATTACK IN INDIA ,CYBER SECURITY AS PROFESSION ,CYBER SECURITY TIPS
Ethical hacking 



Ethical hacking Institute of Information Security (IIS) Ethical hacking also known as penetration testing or white-hat hacking, involves the same tools, tricks, and techniques that hackers use, but with one major difference that Ethical hacking is legal. Ethical hacking is performed with the target’s permission. The intent of ethical hacking is to discover vulnerabilities from a hacker’s
viewpoint so systems can be better secured. It’s part of an overall information risk management program that allows for ongoing security improvements. Ethical hacking can also ensure that vendors’ claims about the security of their products are legitimate.
Hacking



HackingRanjan Som Hacking refers to gaining unauthorized access to computer systems or networks. There are different types of hacking such as website hacking, email hacking, network hacking, password hacking, and online banking hacking. Ethical hacking involves testing a system's security vulnerabilities to help secure it. The document discusses these types of hacking in further detail, explaining how they work and can be prevented. It emphasizes using strong passwords, protecting computers, only downloading from trusted sources, and not using public networks without protection. Ethical hackers play an important role in evaluating security systems.
Cyber crime



Cyber crimeMuhammad Osama Khalid Cyber crime, or computer related crime, is crime that involves a computer and a network. The computer may have been used in the commission of a crime, or it may be the target. ... Cyber crime may threaten a person or a nation's security and financial health.
Cyber Crime and Security



Cyber Crime and SecurityDipesh Waghela Cybercrime involves using computers or the internet to steal identities or import illegal programs. The first recorded cybercrime took place in 1820. There are different types of cybercrimes such as hacking, denial of service attacks, computer viruses, and software piracy. Cybercrimes also include using computers to attack other systems, commit real-world crimes, or steal proprietary information. Common cyber attacks include financial fraud, sabotage of networks, theft of data, and unauthorized access. Internet security aims to establish rules to protect against such attacks by using antivirus software, firewalls, and updating security settings regularly.
cyber security



cyber securityBasineniUdaykumar Cyber security refers to technologies and processes designed to protect computers, networks, and data from unauthorized access and cyber attacks. It involves security standards that enable organizations to safely minimize successful cyber attacks. Cyber crime involves criminal acts conducted via the internet and where computers are tools or targets. Common cyber crimes include illegal access, interception, system interference, data interference, misuse of devices, and fraud. Proper cyber security through tools like antivirus software, firewalls, and strong unique passwords can help protect against cyber crimes.
Ethical Hacking



Ethical HackingAryan Saxena What Is Hacking???
Why do people hack??
History of hacking
What are the various qualities a hacker should posses
H4cking prone areas
TYPE OF HACKERS
Definition of hackers?
What is Ethical hacking?
Who are Ethical hacker?
Ethical Hackers but not Criminal Hackers
Advantages and disadvantages:
Hackers language
Hackers language translation
Similar to Hacking and Types of Hacker. (20)
Hacking



HackingVipinYadav257 Hacking refers to unauthorized access to computer systems or networks. There are different types of hackers, including black hat (malicious), white hat (ethical), and grey hat hackers. Ethical hacking involves legally testing systems for vulnerabilities to help organizations strengthen security. It can assess wireless, application, and network security. While hacking can enable privacy violations and system damage, ethical hacking helps identify issues and prevent unauthorized access. It is an important practice with a growing scope due to increasing cyber threats.
Ethical Hacking Redefined



Ethical Hacking RedefinedPawan Patil This document provides an overview of computer hacking and ethical hacking. It discusses the history of hacking, different types of hackers (e.g. white hat, black hat), why people hack, and the hacking process. The hacking process involves preparation, footprinting, enumeration/fingerprinting, identifying vulnerabilities, exploiting vulnerabilities to gain access, escalating privileges, covering tracks, and creating backdoors. It also discusses how to protect systems from hackers through actions like patching security holes, encrypting data, using firewalls and IDS systems. The document emphasizes that ethical hacking involves legally testing systems with permission to identify vulnerabilities.
Ethical Hacking



Ethical HackingLalit Kumar What is Hacking?
Hacking is accessing unauthorized data by any method
other than the direct method.
Hacking 



Hacking Harendra Singh In the computer security context, a hacker is someone who seeks and exploits weaknesses in a computer system or computer network.
News2 bytes



News2 bytesShreyasi Rao The document summarizes several cybersecurity news stories:
1. The "GhostDNS" botnet compromised over 100,000 routers in Brazil by guessing passwords or exploiting vulnerabilities to change the routers' DNS settings and hijack domains for phishing. It was highly automated and utilized diverse attack vectors.
2. Facebook disclosed a data breach from July-September 2018 that exposed information for 30 million users by exploiting vulnerabilities in the "View As" feature.
3. A WhatsApp vulnerability was found that could allow hackers to take over accounts by sending malformed video calls, and was patched by WhatsApp in September-October 2018.
4. The random number generator used for login cookies on Hacker News
How to be come a hacker slide for 2600 laos



How to be come a hacker slide for 2600 laosOuthai SAIOUDOM This document provides information on how to become a hacker and the skills required. It discusses that a hacker is a skilled computer expert who uses technical knowledge to overcome problems or break into systems. It outlines different types of hackers such as white hat, black hat, and grey hat hackers. It then describes the basic skills needed like computer skills, networking skills, Linux/Unix skills, virtualization skills, security concepts, web application skills, and forensics skills. More advanced skills discussed include cryptography, reverse engineering, problem solving, and persistence. The document provides resources for learning these skills to become an ethical hacker or work in cybersecurity.
Social engineering 



Social engineering Abdelhamid Limami This document discusses social engineering and its threats. Social engineering refers to manipulating people into performing actions or divulging confidential information. It is a significant threat because existing computer security technologies do not protect against human vulnerabilities. Common social engineering attacks include phishing emails, vishing phone calls, leaving infected USB drives in parking lots, and impersonating maintenance workers. The document demonstrates real examples of vishing attacks and provides tips for preventing social engineering, such as verifying identities of people requesting information. However, it notes that fully preventing social engineering attacks can be difficult due to human factors.
Ethical hacking



Ethical hackingRishabha Garg This document discusses computer security and ethical hacking. It covers various types of hacking like interruption and interception. It defines different types of hackers like white hat, black hat and gray hat hackers. It explains the process of ethical hacking which includes preparation, footprinting, vulnerability identification and exploitation. The document provides details on what hackers do after gaining access like covering tracks, creating backdoors. It suggests ways to protect systems like patching vulnerabilities, encrypting data, and setting up firewalls and intrusion detection systems. It advises actions to take after being hacked like restoring from backups.
Hacking- Ethical/ Non-ethical, Cyber Security.



Hacking- Ethical/ Non-ethical, Cyber Security.JasminJaman1 Hacking is the process of attempting to gain or successfully gaining , unauthorized access to computer resources.
Hacking refers to an array of activities which are done to intrude someone else’s personal information so as to use it for malicious , unwanted purposes. Cyber Security.
Bug Bounty Basics



Bug Bounty BasicsHackerOne Who is a hacker? What is a bug bounty program? How do you get started with bug bounties? How much should I pay hackers who find bugs in my website and apps?
All these questions and more are answered in our bug bounty basics booklet. Learn more about the market-leading bug bounty platform and how it is the ideal choice for continuous security testing at https://www.hackerone.com/product/bounty
Practical Experiences of hacking with Contextual Comms and BOTS, Sam Machin, ...



Practical Experiences of hacking with Contextual Comms and BOTS, Sam Machin, ...Alan Quayle Practical Experiences of hacking with Contextual Comms and BOTS, Sam Machin, Developer Relations, Nexmo, a Vonage Company and TADHack Winner
Presented at TADSummit 2016, 15-16 Nov, Lisbon in Stream 4, Contextual Comms, Conversational CRM, BOTs, reviews the practical impact of the changes happening to communications. Messaging and IP Communications as a Platform providers are diversifying the options for communications, and how businesses communicate with their customers. We are only at the early stages of this change, however, multi-channel communications, session management, automation (BOTs) and real-time analytics are delivering business results today. Attendees can learn from leading implementers where to focus efforts, and not get taken-in my the weak-minded marketing BS plaguing in this space.
Attacks on the cyber world



Attacks on the cyber worldNikhil Tripathi This presentation give you a brief idea about some of the popuplar attacks like phishing, sniffing, session hijacking, DNS poisoning
Ethical hacking for fun and profit



Ethical hacking for fun and profitFlorent Batard Describe the ethical hacking, why it's fun to learn and a land of possibility to make business with it
Hacking intro



Hacking introMilind Mishra This document provides an introduction to hacking, including definitions and types of hackers. It discusses the concept of security and common causes of security failures like ignorance. It outlines different types of attacks like DoS, PoD, DDoS, SYN Flood and SQL injection. SQL injection is discussed as a currently prevalent attack method due to increased database use and novice programmers. Trojan attacks and how they allow remote access are described. The document concludes by listing basic hacking skills, the importance of hiding one's identity when hacking, and providing examples of some famous hackers throughout history.
Bar Camp 11 Oct09 Hacking



Bar Camp 11 Oct09 HackingBarcamp Kerala This document discusses hacking and provides an overview of ethical hacking. It begins by defining what a hacker is, noting that historically it referred to an enthusiastic computer hobbyist rather than a criminal. It discusses the evolution of hacking and open source culture. It then discusses ethical hacking and penetration testing, noting it involves authorized attempts to breach systems to test security. It provides an example case study of a large hadron collider being hacked. It also discusses the importance of security given the rise in internet users and potential for attacks on critical networks.
Ethical hacking



Ethical hackingSourabh Goyal This document discusses hacking and ethical hacking. It provides an overview of hackers and different types of hackers such as black hat, white hat, and grey hat hackers. The history of hacking is explored beginning in the 1960s and the evolution of hacking with the rise of computers and the internet. The hacking process and techniques/tools used are addressed as well as advantages and disadvantages of ethical hacking. Different types of hackers like script kiddies are defined. Precautions against hacking and some famous hackers are also mentioned. The document provides references for further information.
Introduction to ethical hacking



Introduction to ethical hackingankit sarode Introduction to ethical hacking.
what is hacking
what types of hackers
difference between hackers and crackers
history of hacking
types of hackers.
INTERNSHIPREVIEW-ISHAQ (1) [Recovered].pptx![INTERNSHIPREVIEW-ISHAQ (1) [Recovered].pptx](https://cdn.slidesharecdn.com/ss_thumbnails/internshipreview-ishaq1recovered-230109133242-4ce6a92f-thumbnail.jpg?width=560&fit=bounds)
![INTERNSHIPREVIEW-ISHAQ (1) [Recovered].pptx](https://cdn.slidesharecdn.com/ss_thumbnails/internshipreview-ishaq1recovered-230109133242-4ce6a92f-thumbnail.jpg?width=560&fit=bounds)
![INTERNSHIPREVIEW-ISHAQ (1) [Recovered].pptx](https://cdn.slidesharecdn.com/ss_thumbnails/internshipreview-ishaq1recovered-230109133242-4ce6a92f-thumbnail.jpg?width=560&fit=bounds)
![INTERNSHIPREVIEW-ISHAQ (1) [Recovered].pptx](https://cdn.slidesharecdn.com/ss_thumbnails/internshipreview-ishaq1recovered-230109133242-4ce6a92f-thumbnail.jpg?width=560&fit=bounds)
INTERNSHIPREVIEW-ISHAQ (1) [Recovered].pptxSuhailShaik16 The document is an internship report that includes:
- Details about the internship organization and the internship period.
- An overview of ethical hacking and the internship project involving identifying vulnerabilities.
- A description of tasks completed including Portswigger labs, detecting vulnerabilities on a banking website, and executing a payload on a vulnerable website.
- Results from ethical hacking quizzes and a generated vulnerability report using OWASP-ZAP.
- Conclusions about gaining technical security knowledge around hacking techniques and prevention.
Cyber crime &_info_security



Cyber crime &_info_securityEr Mahendra Yadav cyber crime & information security is most famous in the world..day by day increase cyber crime in internet world. that see. the detail about of cyber security.
The Secret Of Hacking Trial Pages



The Secret Of Hacking Trial Pagesleoimpact The document introduces hacking and provides context. It defines hacking as unauthorized access to computer systems and networks to bypass security. It discusses the need for ethical hacking to test one's own security. The document gives a brief history of hacking and lists some of the most famous hackers. It also provides an overview of the real hacking process and how to find the latest exploits.
More from Coder Tech (9)
HTML (Basic to Advance)



HTML (Basic to Advance)Coder Tech HTML was originally developed to define the structure of scientific documents and is now widely used to format web pages. It is important for students and professionals to learn HTML to create websites, become a web designer, understand how websites work, and learn other languages like JavaScript. HTML uses tags like <html>, <head>, <body>, <p>, and <h1> to define headings, paragraphs and other elements. Attributes provide additional information about elements, and core attributes like id, title, class and style can be used on most elements. Formatting tags like <b>, <i> and <strong> change the appearance of text. Comments starting with <!-- and ending with --> allow adding notes to code.
PHP Course (Basic to Advance)



PHP Course (Basic to Advance)Coder Tech PHP is a programming language used for web development that allows developers to create dynamic content. It is embedded within HTML and is commonly used with databases like MySQL. PHP code is executed on the server side, and the results are sent to the browser as plain HTML, JavaScript, or other code. Some key points about PHP include that it is free, open source, and can be easily integrated with popular databases. It also supports a variety of protocols and has a simple syntax that allows for powerful functions like system calls and form handling.
Kotlin- Basic to Advance 



Kotlin- Basic to Advance Coder Tech In this PDF you can learn about Kotlin Basic as well as Intermediate part. As also you can develop the android apps and publish in a google play store.
Hardware Authentication



Hardware AuthenticationCoder Tech Hello, Guys, My name is Punit Pandey and i am pursuing an MCA and I am also a security expert for securing a network and computer. So, that i am gonna publish some PPT for understanding how to create a layer for security.
In this section, you can learn the introduction of the hardware authentication in a technology.
And it will be covering all the Hardware security-related things I think it is a very helpful for your learning process and easy to understand how to the hardware work.
Android (Types, Feature,Application etc..)



Android (Types, Feature,Application etc..)Coder Tech In this PPT u can learn feature, types, application etc. for android...
And I'm sure that you can easily understand about android.
Thank u
Firewall and Types of firewall



Firewall and Types of firewallCoder Tech In this PPT you can learn a firewall and types which help you a lot and you can able to understand. So, that you must read at once I sure that you are understand
Thank you!!!
I
Structure of shared memory space



Structure of shared memory spaceCoder Tech This document discusses different ways to structure shared memory space in a distributed shared memory (DSM) system. It describes three common types: no structuring, where shared memory is a linear array of words; structuring by data type, where memory is organized as objects or variables; and structuring as a database, where memory is ordered like a tuple space database. The document provides details on each type, including advantages like flexibility of page size for no structuring and matching access granularity to object size for structuring by data type.
Mother board (Part's of Motherboard)



Mother board (Part's of Motherboard)Coder Tech This document provides information about motherboards. It begins with an introduction explaining that a motherboard is the primary circuit board in a computer that connects the CPU, memory, drives, and other peripherals. It then discusses motherboard form factors like ATX and microATX. The document outlines the key components of a motherboard like the chipset, CPU socket, memory slots, expansion slots, and BIOS. It also explains the roles of the northbridge and southbridge chips. In the end, it provides some tips for selecting a suitable motherboard.
Barcode & qr code



Barcode & qr codeCoder Tech The document discusses barcode technology and QR codes. It defines a barcode as a predefined format of dark and white spaces that can contain specific information to allow real-time data collection. There are two main types of barcodes: linear and 2D barcodes. QR codes are a type of 2D barcode that can store more information and be read quickly by camera devices. Barcodes and QR codes provide benefits like cost efficiency, accuracy, and linking digital and physical items, but have disadvantages like requiring coding of data and system reliance.
Recently uploaded (20)
How to manage Multiple Warehouses for multiple floors in odoo point of sale



How to manage Multiple Warehouses for multiple floors in odoo point of saleCeline George The need for multiple warehouses and effective inventory management is crucial for companies aiming to optimize their operations, enhance customer satisfaction, and maintain a competitive edge.
Presentation of the MIPLM subject matter expert Erdem Kaya



Presentation of the MIPLM subject matter expert Erdem KayaMIPLM Presentation of the MIPLM subject matter expert Erdem Kaya
How to Customize Your Financial Reports & Tax Reports With Odoo 17 Accounting



How to Customize Your Financial Reports & Tax Reports With Odoo 17 AccountingCeline George The Accounting module in Odoo 17 is a complete tool designed to manage all financial aspects of a business. Odoo offers a comprehensive set of tools for generating financial and tax reports, which are crucial for managing a company's finances and ensuring compliance with tax regulations.
Michelle Rumley & Mairéad Mooney, Boole Library, University College Cork. Tra...



Michelle Rumley & Mairéad Mooney, Boole Library, University College Cork. Tra...Library Association of Ireland
K12 Tableau Tuesday - Algebra Equity and Access in Atlanta Public Schools



K12 Tableau Tuesday - Algebra Equity and Access in Atlanta Public Schoolsdogden2 Algebra 1 is often described as a “gateway” class, a pivotal moment that can shape the rest of a student’s K–12 education. Early access is key: successfully completing Algebra 1 in middle school allows students to complete advanced math and science coursework in high school, which research shows lead to higher wages and lower rates of unemployment in adulthood.
Learn how The Atlanta Public Schools is using their data to create a more equitable enrollment in middle school Algebra classes.
YSPH VMOC Special Report - Measles Outbreak Southwest US 4-30-2025.pptx



YSPH VMOC Special Report - Measles Outbreak Southwest US 4-30-2025.pptxYale School of Public Health - The Virtual Medical Operations Center (VMOC) A measles outbreak originating in West Texas has been linked to confirmed cases in New Mexico, with additional cases reported in Oklahoma and Kansas. The current case count is 795 from Texas, New Mexico, Oklahoma, and Kansas. 95 individuals have required hospitalization, and 3 deaths, 2 children in Texas and one adult in New Mexico. These fatalities mark the first measles-related deaths in the United States since 2015 and the first pediatric measles death since 2003.
The YSPH Virtual Medical Operations Center Briefs (VMOC) were created as a service-learning project by faculty and graduate students at the Yale School of Public Health in response to the 2010 Haiti Earthquake. Each year, the VMOC Briefs are produced by students enrolled in Environmental Health Science Course 581 - Public Health Emergencies: Disaster Planning and Response. These briefs compile diverse information sources – including status reports, maps, news articles, and web content– into a single, easily digestible document that can be widely shared and used interactively. Key features of this report include:
- Comprehensive Overview: Provides situation updates, maps, relevant news, and web resources.
- Accessibility: Designed for easy reading, wide distribution, and interactive use.
- Collaboration: The “unlocked" format enables other responders to share, copy, and adapt seamlessly. The students learn by doing, quickly discovering how and where to find critical information and presenting it in an easily understood manner.
Phoenix – A Collaborative Renewal of Children’s and Young People’s Services C...



Phoenix – A Collaborative Renewal of Children’s and Young People’s Services C...Library Association of Ireland
One Hot encoding a revolution in Machine learning



One Hot encoding a revolution in Machine learningmomer9505 A brief introduction to ONE HOT encoding a way to communicate with machines
Studying Drama: Definition, types and elements



Studying Drama: Definition, types and elementsAbdelFattahAdel2 Studying Drama: Definition, types and elements
Niamh Lucey, Mary Dunne. Health Sciences Libraries Group (LAI). Lighting the ...



Niamh Lucey, Mary Dunne. Health Sciences Libraries Group (LAI). Lighting the ...Library Association of Ireland
Metamorphosis: Life's Transformative Journey



Metamorphosis: Life's Transformative JourneyArshad Shaikh *Metamorphosis* is a biological process where an animal undergoes a dramatic transformation from a juvenile or larval stage to a adult stage, often involving significant changes in form and structure. This process is commonly seen in insects, amphibians, and some other animals.
Exploring-Substances-Acidic-Basic-and-Neutral.pdf



Exploring-Substances-Acidic-Basic-and-Neutral.pdfSandeep Swamy Exploring Substances:
Acidic, Basic, and
Neutral
Welcome to the fascinating world of acids and bases! Join siblings Ashwin and
Keerthi as they explore the colorful world of substances at their school's
National Science Day fair. Their adventure begins with a mysterious white paper
that reveals hidden messages when sprayed with a special liquid.
In this presentation, we'll discover how different substances can be classified as
acidic, basic, or neutral. We'll explore natural indicators like litmus, red rose
extract, and turmeric that help us identify these substances through color
changes. We'll also learn about neutralization reactions and their applications in
our daily lives.
by sandeep swamy
Open Access: Revamping Library Learning Resources.



Open Access: Revamping Library Learning Resources.Rishi Bankim Chandra Evening College, Naihati, North 24 Parganas, West Bengal, India Dr. Santosh Kumar Tunga discussed an overview of the availability and the use of Open Educational Resources (OER) and its related various issues for various stakeholders in higher educational Institutions. Dr. Tunga described the concept of open access initiatives, open learning resources, creative commons licensing attribution, and copyright. Dr. Tunga also explained the various types of OER, INFLIBNET & NMEICT initiatives in India and the role of academic librarians regarding the use of OER.
Introduction to Vibe Coding and Vibe Engineering



Introduction to Vibe Coding and Vibe EngineeringDamian T. Gordon Introduction to Vibe Coding and Vibe Engineering
Geography Sem II Unit 1C Correlation of Geography with other school subjects



Geography Sem II Unit 1C Correlation of Geography with other school subjectsProfDrShaikhImran The correlation of school subjects refers to the interconnectedness and mutual reinforcement between different academic disciplines. This concept highlights how knowledge and skills in one subject can support, enhance, or overlap with learning in another. Recognizing these correlations helps in creating a more holistic and meaningful educational experience.
Unit 5: Dividend Decisions and its theories



Unit 5: Dividend Decisions and its theoriesbharath321164 decisions: meaning, factors influencing dividends, forms of dividends, dividend theories: relevance theory (Walter model, Gordon model), irrelevance theory (MM Hypothesis)
The ever evoilving world of science /7th class science curiosity /samyans aca...



The ever evoilving world of science /7th class science curiosity /samyans aca...Sandeep Swamy The Ever-Evolving World of
Science
Welcome to Grade 7 Science4not just a textbook with facts, but an invitation to
question, experiment, and explore the beautiful world we live in. From tiny cells
inside a leaf to the movement of celestial bodies, from household materials to
underground water flows, this journey will challenge your thinking and expand
your knowledge.
Notice something special about this book? The page numbers follow the playful
flight of a butterfly and a soaring paper plane! Just as these objects take flight,
learning soars when curiosity leads the way. Simple observations, like paper
planes, have inspired scientific explorations throughout history.
Envenomation---Clinical Toxicology. pptx



Envenomation---Clinical Toxicology. pptxrekhapositivity Envenomation is the process by which venom is injected by the bite or sting of a venomous animal such as a snake, scorpion, spider, or insect. Arthropod bite is nothing but a sharp bite or sting by ants, fruit flies, bees, beetles, moths, or hornets. Though not a serious condition, arthropod bite can be extremely painful, with redness and mild to severe swelling around the site of the bite
Michelle Rumley & Mairéad Mooney, Boole Library, University College Cork. Tra...



Michelle Rumley & Mairéad Mooney, Boole Library, University College Cork. Tra...Library Association of Ireland
YSPH VMOC Special Report - Measles Outbreak Southwest US 4-30-2025.pptx



YSPH VMOC Special Report - Measles Outbreak Southwest US 4-30-2025.pptxYale School of Public Health - The Virtual Medical Operations Center (VMOC)
Phoenix – A Collaborative Renewal of Children’s and Young People’s Services C...



Phoenix – A Collaborative Renewal of Children’s and Young People’s Services C...Library Association of Ireland
Niamh Lucey, Mary Dunne. Health Sciences Libraries Group (LAI). Lighting the ...



Niamh Lucey, Mary Dunne. Health Sciences Libraries Group (LAI). Lighting the ...Library Association of Ireland
Open Access: Revamping Library Learning Resources.



Open Access: Revamping Library Learning Resources.Rishi Bankim Chandra Evening College, Naihati, North 24 Parganas, West Bengal, India
Hacking and Types of Hacker.
- 1. HACKING
- 2. HISTORY OF HACKING: • THE FIRST HACKER WAS APPEARED IN 1960’S AT THE MASSACHUSETTS INSTITUTE OF TECHNOLOGY(MIT) • DURING THE 1970’S, A DIFFERENT KIND OF HACKER APPEARED: PHONE PHREAKER OR PHONE HACKER
- 3. WHAT IS HACKING: • IN COMPUTING, A HACKER IS ANY SKILLED COMPUTER EXPERT THAT USES THEIR TECHNICAL KNOWLEDGE TO OVERCOME A PROBLEM. WHILE "HACKER" CAN REFER TO ANY COMPUTER PROGRAMMER, THE TERM HAS BECOME ASSOCIATED IN POPULAR CULTURE WITH A "SECURITY HACKER", SOMEONE WHO, WITH THEIR TECHNICAL KNOWLEDGE, USES BUGS OR EXPLOITS TO BREAK INTO COMPUTER SYSTEMS.
- 4. TYPES OF HACKER: Hacker Ethical Hacker (White hat) Cracker (Black hat) Grey hat (Both)
- 5. Ethical Hacker (White hat): A hacker who gains access to systems with a view to fix the identified weaknesses. They may also perform penetration Testing and vulnerability assessments. Cracker (Black hat): A hacker who gains unauthorized access to computer systems for personal gain. The intent is usually to steal corporate data, violate privacy rights, transfer funds from bank accounts etc. Grey hat: A hacker who is in between ethical and black hat hackers. He/she breaks into computer systems without authority with a view to identify weaknesses and reveal them to the system owner.
- 6. HACKING TECHNIQUES: 1. KEYLOGGER 2. DENIAL OF SERVICE (DOSDDOS) 3. WATERHOLE ATTACKS 4. FAKE WAP 5. EAVESDROPPING (PASSIVE ATTACKS) 6. PHISHING 7. VIRUS, TROJEN ETC. 8. CLICKJACKING ATTACKS 9. COOKIE THEFT 10. BAIT AND SWITCH
- 7. KEYLOGGER: • KEYLOGGER IS A SIMPLE SOFTWARE THAT RECORDS THE KEY SEQUENCE AND STROKES OF YOUR KEYBOARD INTO A LOG FILE ON YOUR MACHINE. THESE LOG FILES MIGHT EVEN CONTAIN YOUR PERSONAL EMAIL IDS AND PASSWORDS. • KEYLOGGER IS ONE OF THE MAIN REASONS WHY ONLINE BANKING SITES GIVE YOU AN OPTION TO USE THEIR VIRTUAL KEYBOARDS.
- 8. DENIAL OF SERVICE ATTACK: • A DENIAL OF SERVICE ATTACK IS A HACKING TECHNIQUE TO TAKE DOWN A SITE OR SERVER BY FLOODING THAT SITE OR SERVER WITH A LOT OF TRAFFIC THAT THE SERVER IS UNABLE TO PROCESS ALL THE REQUESTS IN THE REAL TIME AND FINALLY CRASHES DOWN. • FOR DDOS ATTACKS, HACKERS OFTEN DEPLOY BOTNETS OR ZOMBIE COMPUTERS WHICH HAVE GOT THE ONLY WORK TO FLOOD YOUR SYSTEM WITH REQUEST PACKETS.
- 9. WATERHOLE ATTACKS: • IF YOU ARE A BIG FAN OF DISCOVERY OR NATIONAL GEOGRAPHIC CHANNELS, YOU COULD RELATE EASILY WITH THE WATERHOLE ATTACKS. TO POISON A PLACE, IN THIS CASE, THE HACKER HITS THE MOST ACCESSIBLE PHYSICAL POINT OF THE VICTIM. • FOR EXAMPLE, IF THE SOURCE OF A RIVER IS POISONED, IT WILL HIT THE ENTIRE STRETCH OF ANIMALS DURING SUMMER. IN THE SAME WAY, HACKERS TARGET THE MOST ACCESSED PHYSICAL LOCATION TO ATTACK THE VICTIM. THAT POINT COULD BE A COFFEE SHOP, A CAFETERIA ETC. • ONCE HACKERS ARE AWARE OF YOUR TIMINGS, THEY MIGHT CREATE A FAKE WI-FI ACCESS POINT AND MODIFY YOUR MOST VISITED WEBSITE TO REDIRECT THEM TO YOU TO GET YOUR PERSONAL INFORMATION.
- 10. FAKE WAP: • EVEN JUST FOR FUN, A HACKER CAN USE SOFTWARE TO FAKE A WIRELESS ACCESS POINT. THIS WAP CONNECTS TO THE OFFICIAL PUBLIC PLACE WAP. ONCE YOU GET CONNECTED THE FAKE WAP, A HACKER CAN ACCESS YOUR DATA, JUST LIKE IN THE ABOVE CASE. • EX: • TOOL: WI-FI PUMPKIN
- 11. EAVESDROPPING (PASSIVE ATTACKS): • UNLIKE OTHER ATTACKS WHICH ARE ACTIVE IN NATURE, USING A PASSIVE ATTACK, A HACKER JUST MONITORS THE COMPUTER SYSTEMS AND NETWORKS TO GAIN SOME UNWANTED INFORMATION. • THE MOTIVE BEHIND EAVESDROPPING IS NOT TO HARM THE SYSTEM BUT TO GET SOME INFORMATION WITHOUT BEING IDENTIFIED.
- 12. PHISHING: • PHISHING IS A HACKING TECHNIQUE USING WHICH A HACKER REPLICATES THE MOST-ACCESSED SITES AND TRAPS THE VICTIM BY SENDING THAT SPOOFED LINK. • ONCE THE VICTIM TRIES TO LOGIN OR ENTER SOME DATA, THE HACKER GETS THAT PRIVATE INFORMATION OF THE TARGET VICTIM USING THE TROJAN RUNNING ON THE FAKE SITE.
- 13. VIRUS OR TROJANS ETC. : • VIRUS OR TROJANS ARE MALICIOUS SOFTWARE PROGRAMS WHICH GET INSTALLED INTO THE VICTIM’S SYSTEM AND KEEPS SENDING THE VICTIMS DATA TO THE HACKER.
- 14. CLICKJACKING: • CLICKJACKING IS ALSO KNOWN BY A DIFFERENT NAME, UI REDRESS. IN THIS ATTACK, THE HACKER HIDES THE ACTUAL UI WHERE THE VICTIM IS SUPPOSED TO CLICK. • IN ANOTHER WORD, THE ATTACKER HIJACKS THE CLICKS OF THE VICTIM THAT AREN’T MEANT FOR THE EXACT PAGE, BUT FOR A PAGE WHERE THE HACKER WANTS YOU TO BE.
- 15. COOKIE THEFT: • THE COOKIES OF A BROWSER KEEP OUR PERSONAL DATA SUCH AS BROWSING HISTORY, USERNAME, AND PASSWORDS FOR DIFFERENT SITES THAT WE ACCESS. ONCE THE HACKER GETS THE ACCESS TO YOUR COOKIE, HE CAN EVEN AUTHENTICATE HIMSELF AS YOU ON A BROWSER.
- 16. BAIT AND SWITCH: • USING BAIT AND SWITCH HACKING TECHNIQUE, THE HACKER RUNS A MALICIOUS PROGRAM WHICH THE USER BELIEVES TO BE AUTHENTIC. THIS WAY, AFTER INSTALLING THE MALICIOUS PROGRAM ON YOUR COMPUTER, THE HACKER GETS UNPRIVILEGED ACCESS TO YOUR COMPUTER.
- 17. HACKING LANGUAGE: 1. WEB HACKING: SINCE MOST OF THE TECH IS BUILD AROUND WORLD WIDE WEB, IT IS IMPORTANT TO LEARN WEB HACKING TO BE A GOOD HACKER. LET’S SAY YOU ARE INTERESTED IN HACKING WEB APPS AND/OR WEBSITES THEN YOU WILL NEED TO LEARN WEB CODING. WEBSITES USE MOSTLY HTML, PHP AND JAVASCRIPT SO IT IS IMPORTANT TO LEARN THESE THREE. • HTML: ONE OF THE EASIEST AND WIDELY USED STATIC MARKUP WEB LANGUAGE PRESENT IN EACH AND EVERY WEBSITE YOU SEE IN YOUR BROWSER. IT’S RECOMMENDED TO LEARN HTML BECAUSE IT HELPS UNDERSTANDING WEB ACTIONS, RESPONSE, AND LOGIC. • JAVASCRIPT: JS IS A CLIENT-SIDE WEB PROGRAMMING MOSTLY USED IN WEB SITES FOR BETTER USER INTERFACE AND QUICK RESPONSE. IF YOU ARE INTERESTED IN A HACKING CAREER YOU NEED TO LEARN JAVASCRIPT BECAUSE IT HELPS TO UNDERSTAND CLIENT-SIDE MECHANISM WHICH IS ESSENTIAL FOR FINDING CLIENT-SIDE FLAWS.
- 18. CONT.…. • PHP: A DYNAMIC SERVER-SIDE LANGUAGE WHICH IS RESPONSIBLE FOR MANAGING WEB-APPS AND DATABASE. PHP IS CONSIDERED ONE OF THE MOST ESSENTIAL LANGUAGE BECAUSE IT CONTROLS EVERYTHING ON SITE AND SERVER, LIKE A CAPTAIN OF A SHIP. IT IS ADVISED TO LEARN PHP NICELY. • SQL: SQL IS RESPONSIBLE FOR STORING AND MANAGING SENSITIVE AND CONFIDENTIAL DATA SUCH AS USER CREDENTIALS, BANK AND PERSONAL INFORMATION ABOUT THE WEBSITE VISITORS. BLACK HAT HACKERS MOSTLY TARGET SQL DATABASE AND STEAL INFORMATION WHICH IS LATER SOLD ON UNDERGROUND DARK WEB FORUM. IF YOU WANT TO BE GOOD SECURITY RESEARCHER, YOU SHOULD LEARN SQL SO THAT YOU CAN FIND FLAWS IN A WEBSITE AND REPORT THEM.
- 19. CONT... 2. EXPLOIT WRITING AFTER WEB HACKING, ANOTHER MOST IMPORTANT FEATURE OF HACKING IS EXPLOITS. YOU CAN CRACK A PARTICULAR SOFTWARE BY WRITING A EXPLOIT. BUT TO WRITE A EXPLOIT YOU NEED TO LEARN EITHER PYTHON OR RUBY. • PYTHON: IT IS SAID THAT A SECURITY RESEARCHER OR HACKER SHOULD KNOW PYTHON BECAUSE IT THE CORE LANGUAGE FOR CREATING EXPLOITS AND TOOLS. SECURITY EXPERTS AND EVEN PRO HACKERS SUGGEST THAT MASTER PYTHON IS THE BEST WAY TO LEARN HACKING. PYTHON OFFERS WIDER FLEXIBILITY AND YOU CAN CREATE EXPLOITS ONLY IF YOU ARE GOOD IN PYTHON. • RUBY: RUBY IS A SIMPLE YET COMPLICATED OBJECT-ORIENTED LANGUAGE. RUBY IS VERY USEFUL WHEN IT COMES TO EXPLOIT WRITING. IT IS USED FOR METERPRETER SCRIPTING BY HACKERS. THE MOST FAMOUS HACKER TOOL, METASPLOIT FRAMEWORK IS PROGRAMMED IN RUBY. THOUGH RUBY MAY NOT BE AS VERSATILE AS PYTHON, KNOWLEDGE OF RUBY IS MUST IN UNDERSTANDING EXPLOITS.
- 20. CONT.… • REVERSE ENGINEERING: • REVERSE ENGINEERING, THE PROCESS OF TAKING A SOFTWARE PROGRAM’S BINARY CODE AND RECREATING IT SO AS TO TRACE IT BACK TO THE ORIGINAL SOURCE CODE. IF YOU KNOW REVERSE ENGINEERING YOU CAN FIND FLAWS AND BUGS EASILY. IF YOU WANT TO LEARN REVERSE ENGINEERING YOU NEED TO KNOW C, C++ AND JAVA. THE PROCESS OF CONVERTING THE CODE WRITTEN IN HIGH LEVEL LANGUAGE INTO A LOW LEVEL LANGUAGE WITHOUT CHANGING THE ORIGINAL PROGRAM IS KNOWN AS REVERSE ENGINEERING.
- 21. HOW TO TRANSLATE THE HACKERS’ LANGUAGE 1 -> I OR L 3 -> E 4 -> A 7 -> T 9 -> G 0 -> O $ -> S | -> I OR L || -> N |/| -> M S -> Z Z -> S F -> PH PH -> F X -> CK CK -> X
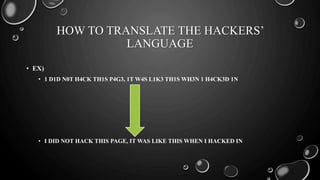
- 22. HOW TO TRANSLATE THE HACKERS’ LANGUAGE • EX) • 1 D1D N0T H4CK TH1S P4G3, 1T W4S L1K3 TH1S WH3N 1 H4CK3D 1N • I DID NOT HACK THIS PAGE, IT WAS LIKE THIS WHEN I HACKED IN
- 23. TOP 10 ETHICAL HACKER: 1) RAHUL TYAGI 2) PRANAV MISTRY 3) ANKIT FADIA 4) KOUSHIK DUTTA 5) VIVEK RAMACHANDRAN 6) TRISHNEET ARORA 7) SUNNY VAGHELA 8) BENILD JOSEPH 9) FALGUN RATHOD 10) JAYANT KRISHNAMURTHY


