Hacking the Linux Kernel - An Introduction
0 likes88 views
Introduction to the Linux Kernel. Ever wondered how Linux is going? Ever wondered how to contribute to Linux? Now is your chance to get some hands-on information that will help shape your kernel engineer career.
1 of 17
Download to read offline















Recommended
Lt2013 uefisb.talk



Lt2013 uefisb.talkUdo Seidel 1) UEFI Secure Boot is a security feature of the UEFI specification that verifies bootloaders and operating systems are signed with approved cryptographic keys to ensure integrity.
2) Linux distributions have several options for working with UEFI Secure Boot, including using a setup mode, replacing the default cryptographic keys, or using a Microsoft-signed bootloader.
3) While UEFI Secure Boot initially posed challenges for Linux, projects are working to sign Linux bootloaders so they are verified by Secure Boot, enabling Linux to be installed on most new computers while maintaining security.
TSC Sponsored BoF: Can Linux and Automotive Functional Safety Mix ? Take 2: T...



TSC Sponsored BoF: Can Linux and Automotive Functional Safety Mix ? Take 2: T...Linaro Robin Randhawa presented on the potential for open source software in automotive functional safety domains. He discussed desirable attributes for a separation runtime including being open source, having a small trusted computing base, and supporting partitioning and virtualization. However, he noted additional non-technical requirements are needed like having ISO compliant development processes and a clearly accountable entity. Randhawa evaluated options like L4Re, seL4, and Xen and proposed forming a Linaro Automotive SIG to progress open source separation runtimes and help chart an strategy for open source in automotive.
Porting Tizen to open source hardware devices for beginners



Porting Tizen to open source hardware devices for beginnersLeon Anavi This document discusses porting Tizen to open-source hardware devices for beginners. It covers popular single-board computers (SBCs) like Raspberry Pi and devices using the Allwinner chipset. It then describes Tizen-sunxi, an open-source port of Tizen to Allwinner devices. Finally, it provides instructions on building a DIY Tizen tablet and laptop, including key components, and discusses the process of porting Tizen to new ARM devices by building the Linux kernel and bootloader, creating a Tizen platform image, and setting up Tizen on a microSD card.
Firewalls and Virtualization - pfSense Hangout June 2014



Firewalls and Virtualization - pfSense Hangout June 2014Netgate This document summarizes a hangout on firewalls and virtualization. It discusses types of virtualization, virtual networking options like bridged, NAT, and host-only, and considerations for virtualizing firewalls in production and for testing. Virtual networking is demonstrated for VirtualBox, VMware, ESX, and Hyper-V. While virtual firewalls can work well, having a physical firewall manage the virtualization environment is recommended. Performance and high availability considerations are also covered.
Embedded Recipes 2018 - Yoctoception: Containers in the embedded world - Jéré...



Embedded Recipes 2018 - Yoctoception: Containers in the embedded world - Jéré...Anne Nicolas Containerisation is a new player in the embedded world. Provisionning and rapid deployment doesn’t really make sense for embedded devices, but the extra security that container partitionning brings to the table is quickly becoming a “must have” for every embedded device.
However, the embedded world has its own constraints. Generic distributions like debian or Fedora are rarely used and tools like dockers can’t build software with custom build-chains the way Yocto or buildroot does it.
This talk will quickly review what are linux containers, why they are usefull in the embedde world, and then will study ways to generate container images using the yocto infrastructure and integrate them in another yocto image without breaking the package-based update system that Yocto provides.
Linux Introduction - Yousefpour - Rahnema College



Linux Introduction - Yousefpour - Rahnema CollegeMasoud Yousefpour The document provides an introduction and history of Linux. It discusses how Linux originated from the Unix operating system and the GNU project in the 1970s and 1980s. It then covers the development of Linux by Linus Torvalds in 1991. The document also summarizes key aspects of Linux including its kernel, popular distributions, command line interface, graphical user interface, common applications and uses, and its benefits for developers.
tizen-oshw-tds14sh



tizen-oshw-tds14shPhil www.rzr.online.fr Tizen:Common is a cross profile and cross architecture system that
aims to become the OS of everything. This presentation will discuss
its porting to open source hardware devices with ARM or Intel
processors and the stage of the open source project Tizen-sunxi. It
will provide guidelines for building Tizen:Common image from scratch
and booting it on x86 systems or ARM devices. Sunxi devices which
represent the family of ARM SoCs from the Chinese company Allwinner
Technology will be used to demonstrate how to build tizen by your own
and dual boot it on a tablet shipped with another OS. Allwinner chips
are preferred for low budget tablets and single board computers such
as open hardware OLinuXino, CubieBoard and Banana Pi. As of today
millions of Sunxi devices exist on the market and a large community of
open source developers support them but they are not the only ones to
hack on.
Philosophy of Open Source - SFO17-TR01



Philosophy of Open Source - SFO17-TR01Linaro The document discusses the history and philosophy of open source software. It begins by explaining that open source refers to the development methodology, not free software which is a social movement. The origins of open source date back to the 1960s when computer programmers shared source code. However, in the 1980s access to source code became restricted by vendors. This led to the rise of the free software movement and creation of the Free Software Foundation in 1985. In 1998, the Open Source Initiative was formed to promote open source principles to businesses. The document outlines the differences between the goals of OSI and FSF, and describes common open source licenses and development processes like forking.
Vpm



VpmGlobalLogic Ukraine This document discusses post-mortem debugging in embedded Linux systems. Post-mortem debugging involves analyzing system state data collected after a crash to investigate the cause. Key data includes RAM regions, CPU states, and peripheral states. Challenges include retrieving this data without modifying critical state information and analyzing it using tools that understand the OS and CPU architecture. Example tools discussed are Lauterbach TRACE32 and Red Hat Crash, which can analyze kernel crashes, IPC issues, deadlocks, and watchdog errors.
Linux 开源操作系统发展新趋势



Linux 开源操作系统发展新趋势Anthony Wong A guest lecture at National University of Defense Technology (NUDT) in 2016 to postgraduate students in China about emerging technologies in the Linux operating system.
Introduction to IoT.JS



Introduction to IoT.JSSamsung Open Source Group This document discusses IoT.js, a lightweight version of Node.js designed for resource-constrained devices. It introduces JerryScript, a lightweight JavaScript engine developed by Samsung with a footprint of only 10KB that IoT.js runs on. The document outlines the goals and architecture of IoT.js, provides performance comparisons with other JavaScript engines, and demonstrates IoT.js running games like Tetris and Pong across devices with different capabilities. Future plans include further optimizations and adding more modules to expand IoT.js capabilities.
The ABC of Linux (Linux for Beginners)



The ABC of Linux (Linux for Beginners)plarsen67 This presentation introduces Linux for Computer Science students. It covers it's architecture and core components.
Kernel Recipes 2013 - Viewing real time ltt trace using gtkwave



Kernel Recipes 2013 - Viewing real time ltt trace using gtkwaveAnne Nicolas This presentation will explain how to use some ltt to be viewd in gtkwave, a graphical visualization tool, developped by the Parrot team.
It will also explain why this tool was developed, review some of the problems that have been analyzed using these traces. It will finally end up on the ongoing integration with LTTng 2.x.
Tizen platform-dev-tds14sh



Tizen platform-dev-tds14shPhil www.rzr.online.fr Since Tizen adopted "open governance model", a free and libre open
source GNU/Linux distribution known as "Tizen:Common" came to light.
Now anyone is able to install it on widely available machines (PC,
NUC, VM etc) and use the rolling release distro for any purpose, let's
go one step foreward and build software for it and make a basic bug
fix. This kick-start session aims to go directly to the pratical way
to use it or/and contribute to Tizen. Tizen development tools (git,
gbs, gerrit, jira...) will be presented live in real action, to give a
short overview on how the project is progressing on a daily basis.
Curious developers unfamiliar with platform development, can expect to
get the entry's keys and learn by example on how to work on tizen
platform and eventually share their wildest dreams.
Trojan linux



Trojan linuxBurak Duran Troy is a Linux distribution created in 2004 for Turkish users. It aims to provide a fast, reliable, and easy to use operating system. It has three versions - a foundation version for installing on hard disks, an employee version that runs from a CD, and an improved version still under development. Installing Troy is similar to other operating systems and involves partitioning the disk, then selecting the Linux section for installation. The installation process takes 10-30 minutes to complete depending on the system.
JerryScript on RIOT



JerryScript on RIOTSamsung Open Source Group JerryScript is a lightweight JavaScript engine optimized for microcontrollers and embedded devices. It has a small memory footprint of only 3KB and implements ECMAScript 5.1. JerryScript has been ported to run on the Internet of Things (IoT) operating system RIOT, allowing JavaScript code to easily be run on microcontrollers. A demo of JerryScript running a Tetris game on an STM32F4 board using an LED matrix was shown. Future work includes further optimizations and adding debugging support to JerryScript.
Git Money



Git MoneyTim N This document discusses techniques for finding and stealing source code from unprotected Git repositories, including cloning exposed repositories, exploiting path and file disclosures, recovering deleted files and credentials from commit logs, and using tools to conduct aggressive cloning attacks. It warns developers to secure access to Git configurations and repositories and not check in sensitive data, and cautions attackers to carefully inspect exposed repositories for hostnames, paths, files and credentials that could be abused.
A Science Project: Swift Serial Chat



A Science Project: Swift Serial Chatyeokm1 A talk I gave at iOS Dev Scout on 23 Nov 2016 about a desktop Swift chat app I wrote that uses the Serial Port. It uses the Swift Serial library which I also wrote.
Code for both library and the example app can be found here: https://github.com/yeokm1/SwiftSerial
Video of my talk can be found here: https://engineers.sg/v/1275
Testing Rest with Spring by Kostiantyn Baranov (Senior Software Engineer, Gl...



Testing Rest with Spring by Kostiantyn Baranov (Senior Software Engineer, Gl...GlobalLogic Ukraine - Why Spring Boot for REST?
- Why bother write tests?
- Spring Test Framework Overview
- Reviewing Test Results
Practically DROWNing



Practically DROWNingTim N This document discusses the DROWN attack in detail. It describes how the attack works by exploiting vulnerabilities in the SSLv2 protocol to decrypt TLS connections. Specifically, it uses a Bleichenbacher padding oracle attack and works by intercepting TLS handshake messages, transforming them, and sending them to an SSLv2 server to recover the premaster secret and decrypt traffic. The document provides information on the computational requirements, prevalence of vulnerable servers, variations of the attack that can decrypt more quickly, and recommendations for mitigation.
gnu و fsf پروژه های پیشنهادی 



gnu و fsf پروژه های پیشنهادی Shiraz LUG This document provides suggestions for how to help the GNU project and Free Software Foundation (FSF) through various activities like writing documentation, contributing to free software projects, spreading awareness of free software philosophy, encouraging use of GNU/Linux, supporting GNU development, and improving accessibility and internationalization of free software. It also lists specific free software projects that could benefit from help like Replicant mobile OS, GNU Social, Mastodon, decentralized web services, free drivers and firmware, real-time communication apps, accessibility tools, security tools, personal assistants, and moving popular GNU/Linux distributions to be fully free.
Opensource 是人生的好朋友 2016-07-21



Opensource 是人生的好朋友 2016-07-21CQD This presentation discusses open source software. It provides a brief history of open source including Unix in the 1970s, GNU in 1983, Linux in 1991, and Netscape in 1998. It describes features of open source like copyleft and various open source licenses. The presentation emphasizes that open source code does not guarantee good software - it is the skills of the programmers that determine quality - and contributing to open source benefits both the community and allows individuals to improve their skills.
Introduction to GNU/Linux



Introduction to GNU/LinuxMd Safiyat Reza This document provides an introduction to Linux. It explains that Linux is not an operating system by itself, but rather a kernel that is typically used with the GNU operating system. Linux originated from the need for an alternative to expensive UNIX systems and academically restricted MINIX. A 21-year old student named Linus Torvalds developed the initial Linux kernel for his new PC hardware and announced its development in an email in 1991. Today, Linux powers supercomputers, stock exchanges, bullet trains and more, with only 2% of its code originally written by Torvalds and the rest contributed by its vast developer community.
BKK16-209 Chromium with V4L2 playback - is it ready today?



BKK16-209 Chromium with V4L2 playback - is it ready today?Linaro This BOF session will analyze architectural challenges migrating Chromium from the desktop to embedded devices. The impacts of different GPU libraries with their respective limitations will be discussed. We welcome audience participation in an open discussion on the V4L2 adaptation in Chromium.
Create IoT with Open Source Hardware, Tizen and HTML5



Create IoT with Open Source Hardware, Tizen and HTML5Leon Anavi Overview of Tizen, its profiles (including Tizen:Common and IVI), Crosswalk web runtime, SDK, installation and management of web apps (wgt) Tizen:Common and IVI. The presentation also includes information about open source hardware development boards with Intel and ARM SoC and instructions how to build Tizen for them using GBS or the Yocto project.
Have You Driven an SELinux Lately? - An Update on the SELinux Project - OLS ...



Have You Driven an SELinux Lately? - An Update on the SELinux Project - OLS ...James Morris "Have You Driven an SELinux Lately? - An Update on the SELinux Project"
This was given at OLS (Ottawa Linux Symposium) in 2008.
The paper from the talk may be found at
http://namei.org/ols-2008-selinux-paper.pdf.
Moscow virtualization meetup 2014: CRIU 1.0 What is next?



Moscow virtualization meetup 2014: CRIU 1.0 What is next?Andrey Vagin The document discusses CRIU, which allows checkpoint and restore of running Linux containers and processes. It aims to support full Linux containers and integrate with projects like OpenVZ, OpenMPI, Docker and LXC. CRIU is mostly written in C and maintained by a team of over 30 contributors. Key features include incremental dumping to deduplicate images, improved performance and stability, and plugins to handle unknown file types and external dependencies. It also includes an RPC library and self-dump capability for easy use across languages.
Linux- The open source system kernel



Linux- The open source system kernelPrasadKulkarni201 The document discusses the Linux operating system kernel. It begins with a brief history of Linux starting as a personal project by Linus Torvalds in 1991. Some key features of Linux mentioned are that it is free, most applications are free, and it has lower vulnerability to malware than other operating systems. The document also outlines several popular Linux distributions like Ubuntu, Linux Mint, SUSE, and Kali and notes their main purposes and users. Advantages of Ubuntu over other operating systems cited include being free, customizable, more secure, able to run without installing, and more resource-friendly. Basic system requirements for Ubuntu are also provided.
Embedded Linux on ARM



Embedded Linux on ARMEmertxe Information Technologies Pvt Ltd Linux has emerged as a number one choice for developing OS based Embedded Systems. Open Source development model, Customizability, Portability, Tool chain availability are some reasons for this success. This course gives a practical perspective of customizing, building and bringing up Linux Kernel on an ARM based target hardware. It combines various previous modules you have learned, by combing Linux administration, Hardware knowledge, Linux as OS, C/Computer programming areas. After bringing up Linux, you can port any of the existing applications into the target hardware.
Leveraging Android's Linux Heritage at AnDevCon3



Leveraging Android's Linux Heritage at AnDevCon3Opersys inc. This document discusses leveraging the Linux heritage in Android. It begins with an overview of Android concepts like components, intents, and manifest files. It then compares the overall architecture of a traditional Linux system to Android. Several roadblocks to integration are identified, such as differences in filesystem structure and IPC mechanisms. Potential approaches for coexistence are outlined, such as using a single filesystem or virtualization. Finally, ongoing work and unresolved challenges are acknowledged, such as implementing intents on Linux or running X applications within Android.
More Related Content
What's hot (20)
Vpm



VpmGlobalLogic Ukraine This document discusses post-mortem debugging in embedded Linux systems. Post-mortem debugging involves analyzing system state data collected after a crash to investigate the cause. Key data includes RAM regions, CPU states, and peripheral states. Challenges include retrieving this data without modifying critical state information and analyzing it using tools that understand the OS and CPU architecture. Example tools discussed are Lauterbach TRACE32 and Red Hat Crash, which can analyze kernel crashes, IPC issues, deadlocks, and watchdog errors.
Linux 开源操作系统发展新趋势



Linux 开源操作系统发展新趋势Anthony Wong A guest lecture at National University of Defense Technology (NUDT) in 2016 to postgraduate students in China about emerging technologies in the Linux operating system.
Introduction to IoT.JS



Introduction to IoT.JSSamsung Open Source Group This document discusses IoT.js, a lightweight version of Node.js designed for resource-constrained devices. It introduces JerryScript, a lightweight JavaScript engine developed by Samsung with a footprint of only 10KB that IoT.js runs on. The document outlines the goals and architecture of IoT.js, provides performance comparisons with other JavaScript engines, and demonstrates IoT.js running games like Tetris and Pong across devices with different capabilities. Future plans include further optimizations and adding more modules to expand IoT.js capabilities.
The ABC of Linux (Linux for Beginners)



The ABC of Linux (Linux for Beginners)plarsen67 This presentation introduces Linux for Computer Science students. It covers it's architecture and core components.
Kernel Recipes 2013 - Viewing real time ltt trace using gtkwave



Kernel Recipes 2013 - Viewing real time ltt trace using gtkwaveAnne Nicolas This presentation will explain how to use some ltt to be viewd in gtkwave, a graphical visualization tool, developped by the Parrot team.
It will also explain why this tool was developed, review some of the problems that have been analyzed using these traces. It will finally end up on the ongoing integration with LTTng 2.x.
Tizen platform-dev-tds14sh



Tizen platform-dev-tds14shPhil www.rzr.online.fr Since Tizen adopted "open governance model", a free and libre open
source GNU/Linux distribution known as "Tizen:Common" came to light.
Now anyone is able to install it on widely available machines (PC,
NUC, VM etc) and use the rolling release distro for any purpose, let's
go one step foreward and build software for it and make a basic bug
fix. This kick-start session aims to go directly to the pratical way
to use it or/and contribute to Tizen. Tizen development tools (git,
gbs, gerrit, jira...) will be presented live in real action, to give a
short overview on how the project is progressing on a daily basis.
Curious developers unfamiliar with platform development, can expect to
get the entry's keys and learn by example on how to work on tizen
platform and eventually share their wildest dreams.
Trojan linux



Trojan linuxBurak Duran Troy is a Linux distribution created in 2004 for Turkish users. It aims to provide a fast, reliable, and easy to use operating system. It has three versions - a foundation version for installing on hard disks, an employee version that runs from a CD, and an improved version still under development. Installing Troy is similar to other operating systems and involves partitioning the disk, then selecting the Linux section for installation. The installation process takes 10-30 minutes to complete depending on the system.
JerryScript on RIOT



JerryScript on RIOTSamsung Open Source Group JerryScript is a lightweight JavaScript engine optimized for microcontrollers and embedded devices. It has a small memory footprint of only 3KB and implements ECMAScript 5.1. JerryScript has been ported to run on the Internet of Things (IoT) operating system RIOT, allowing JavaScript code to easily be run on microcontrollers. A demo of JerryScript running a Tetris game on an STM32F4 board using an LED matrix was shown. Future work includes further optimizations and adding debugging support to JerryScript.
Git Money



Git MoneyTim N This document discusses techniques for finding and stealing source code from unprotected Git repositories, including cloning exposed repositories, exploiting path and file disclosures, recovering deleted files and credentials from commit logs, and using tools to conduct aggressive cloning attacks. It warns developers to secure access to Git configurations and repositories and not check in sensitive data, and cautions attackers to carefully inspect exposed repositories for hostnames, paths, files and credentials that could be abused.
A Science Project: Swift Serial Chat



A Science Project: Swift Serial Chatyeokm1 A talk I gave at iOS Dev Scout on 23 Nov 2016 about a desktop Swift chat app I wrote that uses the Serial Port. It uses the Swift Serial library which I also wrote.
Code for both library and the example app can be found here: https://github.com/yeokm1/SwiftSerial
Video of my talk can be found here: https://engineers.sg/v/1275
Testing Rest with Spring by Kostiantyn Baranov (Senior Software Engineer, Gl...



Testing Rest with Spring by Kostiantyn Baranov (Senior Software Engineer, Gl...GlobalLogic Ukraine - Why Spring Boot for REST?
- Why bother write tests?
- Spring Test Framework Overview
- Reviewing Test Results
Practically DROWNing



Practically DROWNingTim N This document discusses the DROWN attack in detail. It describes how the attack works by exploiting vulnerabilities in the SSLv2 protocol to decrypt TLS connections. Specifically, it uses a Bleichenbacher padding oracle attack and works by intercepting TLS handshake messages, transforming them, and sending them to an SSLv2 server to recover the premaster secret and decrypt traffic. The document provides information on the computational requirements, prevalence of vulnerable servers, variations of the attack that can decrypt more quickly, and recommendations for mitigation.
gnu و fsf پروژه های پیشنهادی 



gnu و fsf پروژه های پیشنهادی Shiraz LUG This document provides suggestions for how to help the GNU project and Free Software Foundation (FSF) through various activities like writing documentation, contributing to free software projects, spreading awareness of free software philosophy, encouraging use of GNU/Linux, supporting GNU development, and improving accessibility and internationalization of free software. It also lists specific free software projects that could benefit from help like Replicant mobile OS, GNU Social, Mastodon, decentralized web services, free drivers and firmware, real-time communication apps, accessibility tools, security tools, personal assistants, and moving popular GNU/Linux distributions to be fully free.
Opensource 是人生的好朋友 2016-07-21



Opensource 是人生的好朋友 2016-07-21CQD This presentation discusses open source software. It provides a brief history of open source including Unix in the 1970s, GNU in 1983, Linux in 1991, and Netscape in 1998. It describes features of open source like copyleft and various open source licenses. The presentation emphasizes that open source code does not guarantee good software - it is the skills of the programmers that determine quality - and contributing to open source benefits both the community and allows individuals to improve their skills.
Introduction to GNU/Linux



Introduction to GNU/LinuxMd Safiyat Reza This document provides an introduction to Linux. It explains that Linux is not an operating system by itself, but rather a kernel that is typically used with the GNU operating system. Linux originated from the need for an alternative to expensive UNIX systems and academically restricted MINIX. A 21-year old student named Linus Torvalds developed the initial Linux kernel for his new PC hardware and announced its development in an email in 1991. Today, Linux powers supercomputers, stock exchanges, bullet trains and more, with only 2% of its code originally written by Torvalds and the rest contributed by its vast developer community.
BKK16-209 Chromium with V4L2 playback - is it ready today?



BKK16-209 Chromium with V4L2 playback - is it ready today?Linaro This BOF session will analyze architectural challenges migrating Chromium from the desktop to embedded devices. The impacts of different GPU libraries with their respective limitations will be discussed. We welcome audience participation in an open discussion on the V4L2 adaptation in Chromium.
Create IoT with Open Source Hardware, Tizen and HTML5



Create IoT with Open Source Hardware, Tizen and HTML5Leon Anavi Overview of Tizen, its profiles (including Tizen:Common and IVI), Crosswalk web runtime, SDK, installation and management of web apps (wgt) Tizen:Common and IVI. The presentation also includes information about open source hardware development boards with Intel and ARM SoC and instructions how to build Tizen for them using GBS or the Yocto project.
Have You Driven an SELinux Lately? - An Update on the SELinux Project - OLS ...



Have You Driven an SELinux Lately? - An Update on the SELinux Project - OLS ...James Morris "Have You Driven an SELinux Lately? - An Update on the SELinux Project"
This was given at OLS (Ottawa Linux Symposium) in 2008.
The paper from the talk may be found at
http://namei.org/ols-2008-selinux-paper.pdf.
Moscow virtualization meetup 2014: CRIU 1.0 What is next?



Moscow virtualization meetup 2014: CRIU 1.0 What is next?Andrey Vagin The document discusses CRIU, which allows checkpoint and restore of running Linux containers and processes. It aims to support full Linux containers and integrate with projects like OpenVZ, OpenMPI, Docker and LXC. CRIU is mostly written in C and maintained by a team of over 30 contributors. Key features include incremental dumping to deduplicate images, improved performance and stability, and plugins to handle unknown file types and external dependencies. It also includes an RPC library and self-dump capability for easy use across languages.
Linux- The open source system kernel



Linux- The open source system kernelPrasadKulkarni201 The document discusses the Linux operating system kernel. It begins with a brief history of Linux starting as a personal project by Linus Torvalds in 1991. Some key features of Linux mentioned are that it is free, most applications are free, and it has lower vulnerability to malware than other operating systems. The document also outlines several popular Linux distributions like Ubuntu, Linux Mint, SUSE, and Kali and notes their main purposes and users. Advantages of Ubuntu over other operating systems cited include being free, customizable, more secure, able to run without installing, and more resource-friendly. Basic system requirements for Ubuntu are also provided.
Similar to Hacking the Linux Kernel - An Introduction (20)
Embedded Linux on ARM



Embedded Linux on ARMEmertxe Information Technologies Pvt Ltd Linux has emerged as a number one choice for developing OS based Embedded Systems. Open Source development model, Customizability, Portability, Tool chain availability are some reasons for this success. This course gives a practical perspective of customizing, building and bringing up Linux Kernel on an ARM based target hardware. It combines various previous modules you have learned, by combing Linux administration, Hardware knowledge, Linux as OS, C/Computer programming areas. After bringing up Linux, you can port any of the existing applications into the target hardware.
Leveraging Android's Linux Heritage at AnDevCon3



Leveraging Android's Linux Heritage at AnDevCon3Opersys inc. This document discusses leveraging the Linux heritage in Android. It begins with an overview of Android concepts like components, intents, and manifest files. It then compares the overall architecture of a traditional Linux system to Android. Several roadblocks to integration are identified, such as differences in filesystem structure and IPC mechanisms. Potential approaches for coexistence are outlined, such as using a single filesystem or virtualization. Finally, ongoing work and unresolved challenges are acknowledged, such as implementing intents on Linux or running X applications within Android.
BUD17-TR02: Upstreaming 101 



BUD17-TR02: Upstreaming 101 Linaro "Session ID: BUD17-TR02
Session Name: Upstreaming 101 - BUD17-TR02
Speaker:
Track:
★ Session Summary ★
Introduction to the mechanics and norms of upstreaming
---------------------------------------------------
★ Resources ★
Event Page: http://connect.linaro.org/resource/bud17/bud17-tr02/
Presentation: https://www.slideshare.net/linaroorg/bud17tr02-upstreaming-101
Video: https://youtu.be/S-zoQNNn-Q0
---------------------------------------------------
★ Event Details ★
Linaro Connect Budapest 2017 (BUD17)
6-10 March 2017
Corinthia Hotel, Budapest,
Erzsébet krt. 43-49,
1073 Hungary
---------------------------------------------------
Keyword: Upstreaming, 101
http://www.linaro.org
http://connect.linaro.org
---------------------------------------------------
Follow us on Social Media
https://www.facebook.com/LinaroOrg
https://twitter.com/linaroorg
https://www.youtube.com/user/linaroorg?sub_confirmation=1
https://www.linkedin.com/company/1026961"
Upstreaming 101 - SFO17-TR02



Upstreaming 101 - SFO17-TR02Linaro Session ID: SFO17-TR02
Session Name: Upstreaming 101
- SFO17-TR02
Speaker: Daniel Lezcano
Track:
★ Session Summary ★
Introduction to the mechanics and norms of upstreaming
---------------------------------------------------
★ Resources ★
Event Page: http://connect.linaro.org/resource/sfo17/sfo17-tr02/
Presentation:
Video:
---------------------------------------------------
★ Event Details ★
Linaro Connect San Francisco 2017 (SFO17)
25-29 September 2017
Hyatt Regency San Francisco Airport
---------------------------------------------------
Keyword:
http://www.linaro.org
http://connect.linaro.org
---------------------------------------------------
Follow us on Social Media
https://www.facebook.com/LinaroOrg
https://twitter.com/linaroorg
https://www.youtube.com/user/linaroorg?sub_confirmation=1
https://www.linkedin.com/company/1026961
Leveraging Android's Linux Heritage



Leveraging Android's Linux HeritageOpersys inc. This document discusses leveraging Android's Linux heritage by exploring ways for Linux and Android to coexist and interact. It outlines some of the key differences between the Android and Linux stacks that pose roadblocks, such as the filesystem, C library, IPC mechanisms, and display management. Potential approaches for coexistence discussed include using a single filesystem, chroot jails, virtualization, and bridges between components like intents and DBus. The document concludes with demos of running BusyBox in Android and a client-server app communicating via sockets between the different stacks.
Introduction to Gnu/Linux



Introduction to Gnu/LinuxRanjith Siji This document provides an overview of the GNU/Linux operating system. It discusses the history of GNU and Linux, including the founding of the GNU project by Richard Stallman in 1983 to create a free Unix-like operating system. It then describes how Linux, developed by Linus Torvalds in 1991, combined with GNU tools to form the GNU/Linux operating system. The document outlines key concepts of free software and open source as well as technical and economic advantages of GNU/Linux over proprietary operating systems.
Iot development from prototype to production



Iot development from prototype to productionMender.io This is my talk on IOT connected device development. Topics include hardware, system software, application software, patching/updating, and other design considerations.
Intro to linux 



Intro to linux Islam Nabil TIEC
refrences
iti (shrief mousa slides ) mr . google , udacity , free-electron website عكاشيات محمد عكاتشه
واسف ان نسيت مرجع
Leveraging Android's Linux Heritage at ELC-E 2011



Leveraging Android's Linux Heritage at ELC-E 2011Opersys inc. "Leveraging Android's Linux Heritage" presentation by Karim Yaghmour at the Embedded Linux Conference Europe 2011.
The RULE project: efficient computing for all GNU/Linux users



The RULE project: efficient computing for all GNU/Linux usersMarco Fioretti The RULE (Run Up to date Linux Everywhere, http://rule.zona-m.net) was an attempt to fight the waste of computer equipment with properly chosen Free Software. Since some of those needs are still valid today, here is how I presented RULE at the Rome Linux Day 2004.
Embedded Linux from Scratch to Yocto



Embedded Linux from Scratch to YoctoSherif Mousa Embedded Linux is the use of the Linux kernel and operating system components adapted for embedded systems with limited resources. Building an embedded Linux system involves compiling the cross-compiler toolchain, bootloader, Linux kernel, root filesystem, busybox commands, and startup scripts. This can be done from scratch or using automated build tools like Buildroot or Yocto Project, which simplify and standardize the process of building a custom embedded Linux image.
Android for Embedded Linux Developers



Android for Embedded Linux DevelopersOpersys inc. The default applications on an embedded Linux system include many common command line utilities from BusyBox, such as cat, cp, grep, ls, mkdir, more, mv, ping, ps, rm, top, and vi. BusyBox provides minimal versions of many common UNIX commands in a single executable to reduce the size of the system. Other default applications may include services like bootchartd, crond, and syslogd.
Part 1 of 'Introduction to Linux for bioinformatics': Introduction



Part 1 of 'Introduction to Linux for bioinformatics': IntroductionJoachim Jacob This is part 1 of the training session 'Introduction to Linux for bioinformatics'. We explain in very general terms what Linux is and stands for, and how we can get access to it. Interested in following this training session? Please contact me at http://www.jakonix.be/contact.html
IoT: Contrasting Yocto/Buildroot to binary OSes



IoT: Contrasting Yocto/Buildroot to binary OSesMender.io Drew Moseley gave a presentation comparing the workflows of using binary operating systems versus build systems like Yocto Project and Buildroot for embedded and IoT development. He outlined the steps in a typical development workflow and discussed the advantages and disadvantages of each approach. He also touched on security best practices, the potential uses of containers in embedded/IoT, and concluded with recommendations to define applications early, use a reproducible build system, consider OTA updates, monitor containers, and contact Mender for additional information and resources.
Thinking inside the box (shared)



Thinking inside the box (shared)Joe Brockmeier "In the beginning there was RPM, and it was good." Certainly, Linux packaging has solved many of the problems involved in shipping software, from creation to consumption and maintenance. As software development and deployment have evolved, however, new pain points have cropped up that have not been solved by traditional packaging tools.
Are containers the answer? They may be able to solve many of the current problems, but they also introduce a new set of issues and ignore important lessons from the evolution of distribution-level packaging.
Is Android the New Embedded Linux? at AnDevCon V



Is Android the New Embedded Linux? at AnDevCon VOpersys inc. The document discusses whether Android is becoming the new embedded Linux. It begins by outlining reasons for the question, such as Android being based on Linux, being used in embedded applications, and enjoying strong support from chip manufacturers. It then reviews the history of embedded Linux and the origins and licensing of Android. Key challenges for using Android in embedded applications are identified as documentation, customization limitations, long build times, and dependency on Google. Headless use without a graphical interface is also discussed as an option.
embedded-linux-120203.pdf



embedded-linux-120203.pdftwtester The document provides an overview of the structure and content of an embedded Linux training course. It discusses the following:
1. The course will cover embedded Linux system architecture, building an embedded Linux system with minimal dependencies, hands-on experience developing embedded Linux systems, and taking advantage of open source development models.
2. The course consists of lectures and exercises and covers topics like booting custom kernels, flash and root filesystems, debugging, real-time, and networking.
3. Recommended hardware for exercises includes Motorola and TQ Components boards with PowerPC processors, RAM, flash storage, and I/O capabilities.
Is Android the New Embedded Linux? at AnDevCon VI



Is Android the New Embedded Linux? at AnDevCon VIOpersys inc. This document discusses whether Android is becoming the new embedded Linux. It begins by outlining the similarities between Android and embedded Linux, as Android is based on Linux and often used in embedded systems. It then reviews the history and rise of embedded Linux. The document examines the origins and development of Android at Google. Key differences between embedded Linux and Android are identified, such as Android having standardized developer tools and APIs. Challenges for using Android in embedded systems are presented, like limited documentation and customization options. The talk concludes by considering future trends, like Google's Nexus Q using Android headlessly.
Hillel kobrovski Linux security overview for ciso



Hillel kobrovski Linux security overview for cisoHillel Kobrovski Linux is an open source operating system kernel that is used widely in servers, desktops, embedded devices, and more. Some key points about Linux include:
- Linux started as a hobby project by Linus Torvalds in 1991 and is now widely used due to its flexibility and wide range of applications. It is often bundled with tools from the GNU project to form a complete open source operating system.
- There are many Linux distributions that package the Linux kernel along with other software, with examples including Red Hat, Ubuntu, Debian, and SUSE. Distributions are tailored for different use cases like desktop, server, or embedded systems.
- Linux is open source, allowing anyone to modify the source code
More from Levente Kurusa (6)
Linux Kernel - Bevezetes



Linux Kernel - BevezetesLevente Kurusa I did this talk for the Free Software Conference in Szeged, 2013.
English version also available soon. (should have been uploaded by now)
Introduction to Linux Kernel Development



Introduction to Linux Kernel DevelopmentLevente Kurusa This document provides an introduction to Linux kernel development. It discusses the basics of the kernel including its responsibilities and types. It covers the process of building the kernel using Kconfig and Makefiles. It also describes the kernel API and common data structures used for threading, modules, and devices. Finally, it discusses best practices for patching the kernel including code style checks and signing off on changes.
Linux Kernel - Let's Contribute!



Linux Kernel - Let's Contribute!Levente Kurusa Slides of the talk I did at LinuxWochen Wien 2014.
This talk will give you a quick introduction to Linux kernel development. During the talk we will explore some options of contribution, including random configurations, stable-testing, RC-testing and actual coding! By the end of the talk we will post a basic patch to the developers as well.
How is the Fedora Kernel different?



How is the Fedora Kernel different?Levente Kurusa The Fedora kernel includes extra patches for ACPI device quirks, disabling SecureBoot, and DRM fixes. It uses SLUB for memory allocation and has kernel preemption set to voluntary. The default CPU frequency governor is ONDEMAND and the kernel config process has been criticized as tedious. In summary, the Fedora kernel includes some extra patches and has different configuration options than other distributions like OpenSUSE, Ubuntu, and Arch Linux.
Linux Desktop: When is our year?



Linux Desktop: When is our year?Levente Kurusa Presented at SCALE 13x in Los Angeles, CA on February 21, 2015
We will start with some information about the current Desktop market, the status of the Linux Desktop and its different environments. First, we will list some problems I found and discuss each of them, one-by-one, while showing points where they are related to eachother. These problems vary in nature from community problems to diversity problems while including the problem of the enterprise overriding the needs of the desktop. While some of these problems are not that important, when there are multiples of them, they are problems. The community must work together to solve these problems and make sure that the people who aren't tech-savvy can use a Linux distribution and we must ensure that they enjoy it.
Let's write a Debugger!



Let's write a Debugger!Levente Kurusa A short, introductory talk to the world of debuggers. During the talk, we write a simple debugger application in Rust.
Video at: https://www.youtube.com/watch?v=qS51kIHWARM
Recently uploaded (20)
Lidar for Autonomous Driving, LiDAR Mapping for Driverless Cars.pptx



Lidar for Autonomous Driving, LiDAR Mapping for Driverless Cars.pptxRishavKumar530754 LiDAR-Based System for Autonomous Cars
Autonomous Driving with LiDAR Tech
LiDAR Integration in Self-Driving Cars
Self-Driving Vehicles Using LiDAR
LiDAR Mapping for Driverless Cars
ADVXAI IN MALWARE ANALYSIS FRAMEWORK: BALANCING EXPLAINABILITY WITH SECURITY



ADVXAI IN MALWARE ANALYSIS FRAMEWORK: BALANCING EXPLAINABILITY WITH SECURITYijscai With the increased use of Artificial Intelligence (AI) in malware analysis there is also an increased need to
understand the decisions models make when identifying malicious artifacts. Explainable AI (XAI) becomes
the answer to interpreting the decision-making process that AI malware analysis models use to determine
malicious benign samples to gain trust that in a production environment, the system is able to catch
malware. With any cyber innovation brings a new set of challenges and literature soon came out about XAI
as a new attack vector. Adversarial XAI (AdvXAI) is a relatively new concept but with AI applications in
many sectors, it is crucial to quickly respond to the attack surface that it creates. This paper seeks to
conceptualize a theoretical framework focused on addressing AdvXAI in malware analysis in an effort to
balance explainability with security. Following this framework, designing a machine with an AI malware
detection and analysis model will ensure that it can effectively analyze malware, explain how it came to its
decision, and be built securely to avoid adversarial attacks and manipulations. The framework focuses on
choosing malware datasets to train the model, choosing the AI model, choosing an XAI technique,
implementing AdvXAI defensive measures, and continually evaluating the model. This framework will
significantly contribute to automated malware detection and XAI efforts allowing for secure systems that
are resilient to adversarial attacks.
"Boiler Feed Pump (BFP): Working, Applications, Advantages, and Limitations E...



"Boiler Feed Pump (BFP): Working, Applications, Advantages, and Limitations E...Infopitaara A Boiler Feed Pump (BFP) is a critical component in thermal power plants. It supplies high-pressure water (feedwater) to the boiler, ensuring continuous steam generation.
⚙️ How a Boiler Feed Pump Works
Water Collection:
Feedwater is collected from the deaerator or feedwater tank.
Pressurization:
The pump increases water pressure using multiple impellers/stages in centrifugal types.
Discharge to Boiler:
Pressurized water is then supplied to the boiler drum or economizer section, depending on design.
🌀 Types of Boiler Feed Pumps
Centrifugal Pumps (most common):
Multistage for higher pressure.
Used in large thermal power stations.
Positive Displacement Pumps (less common):
For smaller or specific applications.
Precise flow control but less efficient for large volumes.
🛠️ Key Operations and Controls
Recirculation Line: Protects the pump from overheating at low flow.
Throttle Valve: Regulates flow based on boiler demand.
Control System: Often automated via DCS/PLC for variable load conditions.
Sealing & Cooling Systems: Prevent leakage and maintain pump health.
⚠️ Common BFP Issues
Cavitation due to low NPSH (Net Positive Suction Head).
Seal or bearing failure.
Overheating from improper flow or recirculation.
Process Parameter Optimization for Minimizing Springback in Cold Drawing Proc...



Process Parameter Optimization for Minimizing Springback in Cold Drawing Proc...Journal of Soft Computing in Civil Engineering In tube drawing process, a tube is pulled out through a die and a plug to reduce its diameter and thickness as per the requirement. Dimensional accuracy of cold drawn tubes plays a vital role in the further quality of end products and controlling rejection in manufacturing processes of these end products. Springback phenomenon is the elastic strain recovery after removal of forming loads, causes geometrical inaccuracies in drawn tubes. Further, this leads to difficulty in achieving close dimensional tolerances. In the present work springback of EN 8 D tube material is studied for various cold drawing parameters. The process parameters in this work include die semi-angle, land width and drawing speed. The experimentation is done using Taguchi’s L36 orthogonal array, and then optimization is done in data analysis software Minitab 17. The results of ANOVA shows that 15 degrees die semi-angle,5 mm land width and 6 m/min drawing speed yields least springback. Furthermore, optimization algorithms named Particle Swarm Optimization (PSO), Simulated Annealing (SA) and Genetic Algorithm (GA) are applied which shows that 15 degrees die semi-angle, 10 mm land width and 8 m/min drawing speed results in minimal springback with almost 10.5 % improvement. Finally, the results of experimentation are validated with Finite Element Analysis technique using ANSYS.
RICS Membership-(The Royal Institution of Chartered Surveyors).pdf



RICS Membership-(The Royal Institution of Chartered Surveyors).pdfMohamedAbdelkader115 Glad to be one of only 14 members inside Kuwait to hold this credential.
Please check the members inside kuwait from this link:
https://www.rics.org/networking/find-a-member.html?firstname=&lastname=&town=&country=Kuwait&member_grade=(AssocRICS)&expert_witness=&accrediation=&page=1
Raish Khanji GTU 8th sem Internship Report.pdf



Raish Khanji GTU 8th sem Internship Report.pdfRaishKhanji This report details the practical experiences gained during an internship at Indo German Tool
Room, Ahmedabad. The internship provided hands-on training in various manufacturing technologies, encompassing both conventional and advanced techniques. Significant emphasis was placed on machining processes, including operation and fundamental
understanding of lathe and milling machines. Furthermore, the internship incorporated
modern welding technology, notably through the application of an Augmented Reality (AR)
simulator, offering a safe and effective environment for skill development. Exposure to
industrial automation was achieved through practical exercises in Programmable Logic Controllers (PLCs) using Siemens TIA software and direct operation of industrial robots
utilizing teach pendants. The principles and practical aspects of Computer Numerical Control
(CNC) technology were also explored. Complementing these manufacturing processes, the
internship included extensive application of SolidWorks software for design and modeling tasks. This comprehensive practical training has provided a foundational understanding of
key aspects of modern manufacturing and design, enhancing the technical proficiency and readiness for future engineering endeavors.
Compiler Design_Lexical Analysis phase.pptx



Compiler Design_Lexical Analysis phase.pptxRushaliDeshmukh2 The role of the lexical analyzer
Specification of tokens
Finite state machines
From a regular expressions to an NFA
Convert NFA to DFA
Transforming grammars and regular expressions
Transforming automata to grammars
Language for specifying lexical analyzers
railway wheels, descaling after reheating and before forging



railway wheels, descaling after reheating and before forgingJavad Kadkhodapour railway wheels, descaling after reheating and before forging
Level 1-Safety.pptx Presentation of Electrical Safety



Level 1-Safety.pptx Presentation of Electrical SafetyJoseAlbertoCariasDel Level 1-Safety.pptx Presentation of Electrical Safety
Data Structures_Searching and Sorting.pptx



Data Structures_Searching and Sorting.pptxRushaliDeshmukh2 Sorting Order and Stability in Sorting.
Concept of Internal and External Sorting.
Bubble Sort,
Insertion Sort,
Selection Sort,
Quick Sort and
Merge Sort,
Radix Sort, and
Shell Sort,
External Sorting, Time complexity analysis of Sorting Algorithms.
Avnet Silica's PCIM 2025 Highlights Flyer



Avnet Silica's PCIM 2025 Highlights FlyerWillDavies22 See what you can expect to find on Avnet Silica's stand at PCIM 2025.
Degree_of_Automation.pdf for Instrumentation and industrial specialist



Degree_of_Automation.pdf for Instrumentation and industrial specialistshreyabhosale19 degree of Automation for industrial and Instrumentation learners.
Artificial Intelligence (AI) basics.pptx



Artificial Intelligence (AI) basics.pptxaditichinar its all about Artificial Intelligence(Ai) and Machine Learning and not on advanced level you can study before the exam or can check for some information on Ai for project
Process Parameter Optimization for Minimizing Springback in Cold Drawing Proc...



Process Parameter Optimization for Minimizing Springback in Cold Drawing Proc...Journal of Soft Computing in Civil Engineering
Hacking the Linux Kernel - An Introduction
- 1. Hacking the LINUX KERNEL Introduction Kurusa Levente <[email protected]> Free Software Conference Szeged, Szent-Györgyi Albert Agóra, 2013. november 29. 15:00
- 2. A little bit of history... ● Development began in 1991 on behalf of Linus Torvalds ● UNIX clone ● Originally not meant to be portable
- 3. What is a kernel and what is it for? ● The core of the operating system ● Responsibilities: ● Initialize the system for usage ● Minimal protection of data ● Help development of software by abstractions.
- 4. What type of a kernel is Linux? ● Monolithic ● Modular ● Free software!
- 5. Root of the kernel directory
- 6. Development statistics ● Since 2005, more than 10000 developers from 1000 companies ● Every 70 days a new release, this number was 80 days in 2012. ● Approx. 10000 modifications each release ● Every hour 7.14 modifications, this was 6.9 in 2012
- 7. Code statistics ● Approx. 44000 files ● Approx 18M lines of code ● Languages: – 96.08% ANSI-C – 3.63 % Assembly – 0.10 % Perl
- 8. Where is Linux mostly used? ● Android devices (1.3M each day) ● Smart TVs (700.000 daily) ● Financial transactions (80%) ● Supercomputers (98%) És: ● The cloud (Google, Facebook, Amazon) ● Defence system ● Nuclear submarines ● Trains, airports, and more!
- 9. Contribution ● This is the biggest collab project! ● The hackers have already found the easy but useful way. ● 'scripts/checkpatch.pl' ● With this script you can find common codestyle issues in the code
- 10. Staging drivers ● Drivers of small startups (mostly) ● Full of codestyle errors ● Checkpatch.pl finds these and identifies them ● The volunteering developer corrects them! (patching) ● And they have contributed to the success of Linux! :-)
- 11. Patch creation I. ● git clone git://git.kernel.org/pub/scm/linux/kernel/git/next/linux- next.git ● 'drivers/staging' exploration ● Select a file from this folder ● 'scripts/checkpatch.pl -f <file location>
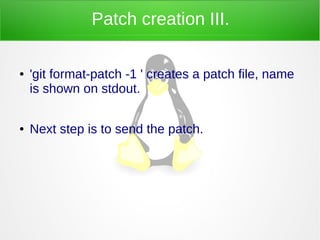
- 12. Patch creation II. ● 'git commit -a' saves the changes
- 13. Patch creation III. ● 'git format-patch -1 ' creates a patch file, name is shown on stdout. ● Next step is to send the patch.
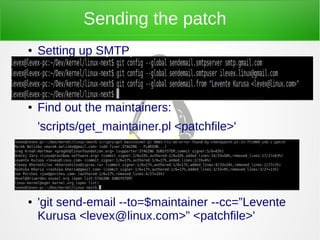
- 14. Sending the patch ● Setting up SMTP ● ● ● Find out the maintainers: 'scripts/get_maintainer.pl <patchfile>' ● ● ● 'git send-email --to=$maintainer --cc=”Levente Kurusa <[email protected]>” <patchfile>'
- 15. We are done! :-)
- 16. Postscript ● Hopefully when you go home, you create a patch like this! :-) ● After that, welcome to the group of Kernel Hackers!
- 17. Thank you for your attention! ● Kernel panic – not syncing: Reached end of presentation.







