Hardware Hacking Chronicles: IoT Hacking for Offence and Defence
- 1. HARDWARE HACKING CHRONICLES IOT HACKING FOR OFFENCE AND DEFENCE Fatih Ozavci Managing Consultant – Context Information Security
- 2. 2 Fatih Ozavci, Managing Consultant VoIP & phreaking Mobile applications and devices Network infrastructure CPE, hardware and IoT hacking Author of Viproy and VoIP Wars Public speaker and trainer Blackhat, Defcon, HITB, AusCert, Troopers May'16
- 3. 3 Subscriber services and IoT Hardware hacking chronicles Hacking broadband devices Hacking office devices Improving defense and offense May'16
- 4. May'16 Everything is connected Broadband services Smart modems IPTV equipment Office devices 3g/4g modems IP phones Keyboards & mouse Why should we evolve? 4
- 5. 5May'16
- 6. 6May'16 Broadband & 3G/4G IPTV/Satellite Broadcasting & VoD Home & Office Equipment
- 7. 7 Combining testing skills Design reviews do not show business logic issues Tech must be tested for various perspectives Traditional tests do not cover Devices’ firmware and hardware Management in a protected network Very limited days for testing May'16
- 8. 8 Testing methodology must be flexible Various devices – ARM vs MIPS, Phone vs Modem Various OSes – Android vs Linux vs VxWorks Testing must always focus on the device’s roles May'16
- 10. Configuration Edit & Re-Upload May'16 Secret Handshake to Enable Telnet Physical Interfaces 10
- 11. May'16 11
- 12. 12 Weaknesses are already known Configuration dump for credentials Editing the conf to enable a feature Vulnerabilities are public and easy Telnet authentication bypass Sagem: https://www.exploit-db.com/exploits/17670 Netgear: https://wiki.openwrt.org/toh/netgear/telnet.console E.g. admin password leak wget http://1.1.1.1/password.html -t 1 -q -O - | grep pwd May'16
- 13. Console Debugging TX, RX, GND, V May'16 Debugging On-Chip Debug TDI, TDO, TCK… Access to Flash Read/Write Data SCK, MOSI, MISO... 13
- 14. May'16 Bus Pirate Bus Blaster Shikra HydraBus Jtagulator GoodFet/GreatFet Logic Analyser SOIC8/16 Clips 14
- 15. May'16 15
- 16. May'16 16
- 17. May'16 17
- 18. May'16 18
- 19. 19 Usually 4 PINs TX, RX, GND, Voltage Provides device access Bootloader, console access Real-time debugging Access without a password May'16
- 20. Find the ground Find the voltage Set the target voltage Try to send/receive TX vs RX Various baud rates Analyse the output Jtagulator May'16 20
- 21. May'16 21
- 22. Debugging and logging Intercepting boot sequence Boot parameters CFE access Getting console access E.g. Netgear CG3100D May'16 22
- 23. May'16 23
- 24. May'16 Stop the boot process UART/Serial connection Possibilities Re-flash for OpenWRT Get information Credentials? Dump the firmware Eg. Sagemcom 3864v2 ADSL & NBN 24
- 25. May'16 25
- 26. 26 Debugging standard Everything depends on the vendor Device or system testing Daisy-chained JTAG TDI (Test Data In) TDO (Test Data Out) TCK (Test Clock) TMS (Test Mode Select) TRST (Test Reset) May'16
- 27. May'16 27
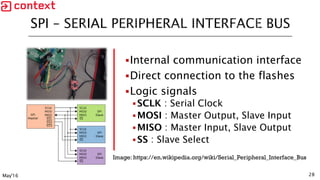
- 28. 28 Internal communication interface Direct connection to the flashes Logic signals SCLK : Serial Clock MOSI : Master Output, Slave Input MISO : Master Input, Slave Output SS : Slave Select May'16 Image: https://en.wikipedia.org/wiki/Serial_Peripheral_Interface_Bus
- 30. 30 Broadband, IPTV, Satellite… Devices are connected to the infrastructure managing by service provider in the consumer promises Relying on vendors for security Default configuration Legacy or unpatched software Management interfaces May'16
- 31. 31 Various vendors in a pool Device provisioning Software & configuration management Call centre connections Generic information in the wild Custom software (e.g OpenWRT) Bypassing controls is common BYOD on subscriber services May'16
- 32. Call Centre May'16 32 Service Provider ACS SIP Provisioning Pool BYOD TR-069 DOCSIS RADIUS
- 33. May'16 33 IPTV STB DVB STB VOD Streaming DRM WEB Services VOD, Licenses, Keys, Billing VOD, Licenses, Keys, Billing CLOUD SERVICE PROVIDER ACS BROADCAST RADIUS TR-069
- 34. May'16 34 Service Provider ACS SIP TR-069 / DOCSIS RADIUSVOIP (SIP + RTP) PSTN PSTN Service Provider MSAN/MGW Distributor VOIP (SIP + RTP) MANAGEMENT
- 35. May'16 35 3G Telecom Network 3G SIP IPSEC VPN RADIUS 3G 3G 3G Femtocell Pool Base Station TR-069
- 36. May'16 36 Debugging Gathering Information Attacking Server Service network Clients connected ACS TR-069 Modem ACS on Modem TCP/7676 ACS on Server TCP/443 ACS Connection Intercepted Modified Attacking ContentOriginal Content
- 37. 37 Dumping device memory X.509 certificates for IPSEC Auth PINs, passwords and config data Broadcasting and DRM keys Dump device firmware Reverse engineering, exploit dev Driving a consumer device Fake base station, billing bypass Altering VoD content, security bypass May'16
- 38. OFFICE DEVICES
- 39. 39 Backdoors on devices are common Open source, distribution, vendors… Expensive to replicate the attack Red teaming engagements Putting a Raspberry Pi in everything Collecting keyboard & mouse input Human factor pen-testing Sending backdoored devices May'16
- 40. 40 3G/4G Modems WiFi models with services and features USB models require drivers Internal storage and card reader Unauthorised access via services Firmware operations Dumping and reversing the firmware Backdooring the firmware Using their shelves for USB duckies May'16
- 41. 41 Keysweeper by SamyKamkar Arduino/Teensy based sniffer Sniffing Microsoft Wireless Keyboard Mousejack by Bastille Security RF keyboard & mouse receivers Force pairing vulnerability Force pairing a remote keyboard May'16
- 42. 42 Efficient for persistent access Raspberry Pi, Arduino Can fit in many devices Find a suitable device to backdoor Find a power source Find a network connection Solder and connect the pieces Broadcast the network connected Advanced implants take time May'16
- 43. May'16 43 RJ45 Connection Pins
- 44. May'16 44 Speaker Power Patch the Cat5 cable
- 46. 46 Enforcing vendors to Disable physical interfaces Use encryption and access keys Follow a security standard Network isolation for subscribers Tailored research for Vendor product vulnerabilities CPE management services Backdoor analysis May'16
- 47. 47 Devices are IN SCOPE Think different and combine skills Everything is a target Home automation, CCTV, phones… Testing service operator networks Test services through devices Extract information from devices Access and fuzz tests through devices May'16
- 48. 48 Focuses on all components Devices, infrastructure, software… Focuses on exploitable issues Combines various disciplines Embedded systems, mobile, network… Closes the gap between offense and defense May'16
- 49. 49 Context Information Security http://www.contextis.com AusCERT https://www.auscert.org.au IoT Security Wiki https://iotsecuritywiki.com May'16
- 50. QUESTIONS?
- 51. THANKS!