【HITCON FreeTalk 2021 - From fakespy to Guerilla: Understanding Android malware crime gangs】
- 1. TLP:WHITE From FakeSpy to Guerilla Understanding Android Malware Crime Gangs Fyodor Yarochkin (with help of Paul Pajeres, Vladimir Kropotov, Ecular Xu, Zhengyu Dong) Trend Micro Research
- 2. Copyright 2021 Trend Micro Inc. 2 TLP:WHITE Introduction
- 3. Copyright 2021 Trend Micro Inc. 3 TLP:WHITE Why Mobile phones are targets? • Mobile often phones ~= ATM cards with Antennas • Telecom carriers ~= Banking Institutions • Less regulated, more connected, easier to break, compromise and remotely control
- 4. Copyright 2021 Trend Micro Inc. 4 TLP:WHITE Reasons for Android Phones being targetd 1. Money theft 2. Cyber espionage 3. Data breaches 4. Ransomware (targeted) 5. Crypto currencies
- 5. Copyright 2019 Trend Micro Inc. 5 TLP:WHITE Geographical specifics • Many online IDs are bound to a phone in China • Mobile Phones allow balance transfers in a number of countries including china, india • Verified phone numbers in some countries allow caller impersonation
- 6. Copyright 2021 Trend Micro Inc. 6 TLP:WHITE Criminals interest in android platforms? • Money (banking) • Virtual currencies • Access to other apps and accounts in bulk • Access to phone numbers
- 7. Copyright 2021 Trend Micro Inc. 7 TLP:WHITE Numbers are valuable commodity
- 8. Copyright 2021 Trend Micro Inc. 8 TLP:WHITE Lets take a look at some examples • Fakespy • Anubis • Guerilla
- 9. Copyright 2021 Trend Micro Inc. 9 TLP:WHITE A good illustration what hackers want from a phone • Mail • Storage • Finance • Online accounts • Crypto currencies
- 10. Copyright 2021 Trend Micro Inc. 10 TLP:WHITE Fakespy
- 11. Copyright 2021 Trend Micro Inc. 11 TLP:WHITE How It Works SMS with malicious link Poses as courier service, Chrome update, others. Prompt to install malicious iOS profile to configure Wifi, email accounts, etc Prompts to install malicious Android app Display Apple phishing or illegal Casino site Monitor device activity like SMS, device info, router, mobile transactions Connect to SNS account Decrypt content and reveal real C2 server Send and receive information Spread SMS to contacts
- 12. Copyright 2021 Trend Micro Inc. 12 TLP:WHITE Lifecycle of Fakespy Apps Oct 2017 Dec 2017 Jun 2018 Korean banks (NH Capital, KB Kookmin, Nonghyup Bank) Apr 2019 Oct 2019 2,000+ fake apps up to Nov Label: 日本郵便 Aug 2019 5,400+ fake apps up to Nov Label: DHL Paket 4 fake apps Label: Die Post Jul 2019 1,400+ fake apps up to Nov Label: 智能宅急 便 Started Feb 2016 around 800+ fake apps until Aug 2019 1200+ fake apps in Sep 2019 to Nov Label: CJ 대한통운 Sep 2019 20,000+ fake apps since 2015 Label: Chrome 600+ fake apps since 2017 Label: Facebook 21,600+ fake apps since 2017 Label: 佐川急便 Xloader started Jun 2018 Fakespy started Dec 2017 70+ fake apps Oct & Nov 2019 Label: ヤマト運輸 50+ fake apps Mar to Sep 2019 Label: SEX kr porn 2 fake app MyDocomo 800+ fake apps Mar to Oct 2019 Label: Anshin Scan
- 13. Copyright 2019 Trend Micro Inc. 13 TLP:WHITE Use of social networks as covert channel
- 14. Copyright 2021 Trend Micro Inc. 14 TLP:WHITE Fakespy • Fakespy does not target banks but • collects contact information, intercepts SMS • and propagates via SMS. Common lures are • Japan Post, Sagawa Express and Chrome
- 15. Copyright 2021 Trend Micro Inc. 15 TLP:WHITE Fakespy derrivatives • FakeOps: targets europe (appeared during Covid) • Xloader: banks in Japan
- 16. Copyright 2021 Trend Micro Inc. 16 TLP:WHITE Fakespy vs Xloader 0 50,000 100,000 150,000 200,000 250,000 300,000 350,000 Jan-19 Feb-19 Mar-19 Apr-19 May-19 Jun-19 Jul-19 Aug-19 Sep-19 Oct-19 Nov-19 Dec-19 Jan-20 Feb-20 Mar-20 Apr-20 May-20 Jun-20 Jul-20 Aug-20 FakeSpy Xloader
- 17. Copyright 2021 Trend Micro Inc. 17 TLP:WHITE Victims and Infrastrcture • Asia: Korea, Japan, Singapore • Some countries in Europe • Infrastructure: geographically diverse
- 18. Copyright 2021 Trend Micro Inc. 18 TLP:WHITE Anubis
- 19. Copyright 2019 Trend Micro Inc. 19 TLP:WHITE What is Anubis?!
- 20. Copyright 2019 Trend Micro Inc. 20 TLP:WHITE Anubis backend
- 21. Copyright 2019 Trend Micro Inc. 21 TLP:WHITE Anubis communications
- 22. Copyright 2019 Trend Micro Inc. 22 TLP:WHITE Objective of Anubis actions: $$$ MONEY!
- 23. Copyright 2019 Trend Micro Inc. 23 TLP:WHITE
- 24. Copyright 2021 Trend Micro Inc. 24 TLP:WHITE Guerilla
- 25. Copyright 2019 Trend Micro Inc. 25 TLP:WHITE
- 26. Copyright 2019 Trend Micro Inc. 26 TLP:WHITE
- 27. Copyright 2019 Trend Micro Inc. 27 TLP:WHITE Guerilla app testing lifecycle
- 28. Copyright 2019 Trend Micro Inc. 28 TLP:WHITE Debugging statements in some modules
- 29. Copyright 2019 Trend Micro Inc. 29 TLP:WHITE Lots of other functionality
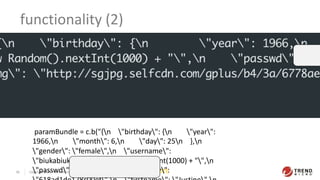
- 30. Copyright 2019 Trend Micro Inc. 30 TLP:WHITE functionality (2) paramBundle = c.b("{n "birthday": {n "year": 1966,n "month": 6,n "day": 25n },n "gender": "female",n "username": "biukabiuka88" + new Random().nextInt(1000) + "",n "passwd": "d0b22405db",n "key":
- 31. Copyright 2019 Trend Micro Inc. 31 TLP:WHITE Many victims, globally
- 32. Copyright 2019 Trend Micro Inc. 32 TLP:WHITE ConclusionJ Trust your phone? Verify your phone? Protect phone?
- 33. Copyright 2019 Trend Micro Inc. 33 TLP:WHITE Protect your phone :p my phone – my bastion J Questions? ;-) Iphone J
- 34. Copyright 2021 Trend Micro Inc. 34 TLP:WHITE Thank You! QUESTIONS => [email protected]