How to encrypt and protect your moodle site for free with let's encrypt
Download as ODP, PDF0 likes3,457 views
Want to make your Moodle site more secure without using an expensive and complicated certificate? Find out how.
1 of 17
Downloaded 15 times
















Ad
Recommended
Menghidupkan Nurani dengan Berpikir Kritis



Menghidupkan Nurani dengan Berpikir KritisChaamid fajri Ayat Al-Imran (3): 190-191 memuat informasi tentang penciptaan alam semesta dan menantang pembacanya untuk merenungkan informasi tersebut dengan berpikir kritis. Berpikir kritis didefinisikan sebagai proses menganalisis dan mengevaluasi informasi dengan sikap reflektif untuk membimbing keyakinan dan tindakan. Manfaat berpikir kritis mencakup memahami hikmah ciptaan Allah, mengoptimalkan alam, mengambil
Negara Laos



Negara LaosxNet8 Dokumen tersebut merangkum informasi tentang Republik Demokratik Rakyat Laos, mulai dari sejarah, politik, geografi, ekonomi, budaya, dan media komunikasi. Laos awalnya dikuasai berbagai kerajaan sebelum akhirnya menjadi negara komunis setelah Revolusi Pathet Lao pada tahun 1975. Ekonomi Laos tumbuh pesat sejak melonggarkan kontrol ekonomi pada tahun 1986. Kebudayaan Laos dipengaru
MEMAHAMI KONFIGURASI EKSTENSI DAN DIAL-PLAN SERVER SOFTSWITCH.pptx



MEMAHAMI KONFIGURASI EKSTENSI DAN DIAL-PLAN SERVER SOFTSWITCH.pptxAnggariAyu1 Dokumen tersebut membahas tentang prosedur pengamatan kerja sistem telekomunikasi menggunakan VoIP. Secara ringkas, dokumen menjelaskan bahwa TCP digunakan untuk signaling, UDP digunakan untuk audio streaming karena lebih cepat, dan IP menyediakan alamat untuk identifikasi setiap komputer dalam pengiriman informasi.
15. perang bali tahun 1846 1849



15. perang bali tahun 1846 1849SMA Negeri 9 KERINCI Perang Bali tahun 1846-1849 terjadi akibat konflik antara kerajaan-kerajaan di Bali dengan pemerintah Hindia Belanda mengenai hak untuk menawan kapal-kapal yang terdampar. Perang berkecamuk di Buleleng dan disebut Perang Puputan karena prajurit melawan dengan semangat perang habis-habisan. Meskipun perlawanan sengit, pada akhirnya Belanda berhasil menundukkan Bali.
Ikhtiar dan tawakal agama



Ikhtiar dan tawakal agamaYuan Yuanita Tawakal berarti menyerahkan diri kepada Allah setelah berusaha secara maksimal. Tawakal dilakukan setelah usaha, bukan sebelum usaha. Beberapa dampak positif tawakal adalah mendapat kepuasan batin dan ketenangan jiwa. Ikhtiar berarti berusaha dengan menggunakan seluruh kemampuan. Beberapa perilaku ikhtiar adalah bekerja keras dan tidak mudah menyerah. Dampak positif ikhtiar adalah terhindar dari
Bab 2 Hidup Tenang dengan Kejujuran,.pptx



Bab 2 Hidup Tenang dengan Kejujuran,.pptxMuhammadNaziehIbadil Bab 2 membahas tentang hidup tenang dengan kejujuran, amanah, dan istiqamah. Kejujuran adalah kesesuaian antara perkataan dan perbuatan yang sebenarnya. Amanah berarti terpercaya dan menjaga tanggung jawab. Istiqamah berarti kukuh pada pendirian dan konsekuen dalam tindakan. Hidup dengan ketiga sifat ini memberikan banyak manfaat seperti mendapat kepercayaan, teman, ketentraman hidup, dan
Jaringan Komputer dan Internet Kelas 10



Jaringan Komputer dan Internet Kelas 10Farichah Riha Jaringan Komputer dan Internet - Informatika
SMA/MA Kelas X Semester Genap
PRESENTASI TEKNOLOGI INFORMASI DAN KOMUNIKASI



PRESENTASI TEKNOLOGI INFORMASI DAN KOMUNIKASIYoga Romdoni Berisi Materi tentang teknologi informasi dan komunikasi
Sabar, qonaah, ridho dan sabar



Sabar, qonaah, ridho dan sabarSandi Audy Dokumen tersebut membahas tentang tujuan pembelajaran dan pengertian dari sifat-sifat bersyukur, qanaah, rida, dan sabar menurut agama Islam. Siswa diharapkan dapat memahami definisi dan manfaat dari empat sifat tersebut, serta contoh perilaku dan dalil yang mendukungnya.
Buku produk cake dan kue indonesia kls xii



Buku produk cake dan kue indonesia kls xiiArdian Sufandi Buku Produk Cake untuk kelas XII Jurusan Tata Boga
Proposal jaringan komputer



Proposal jaringan komputerirwansyah budiman Proposal ini merangkum rencana pembuatan jaringan kantor untuk PT Putra Mutiara Bersama dengan menggunakan jaringan Local Area Network (LAN) dengan topologi tree untuk memudahkan berbagi data dan komunikasi. Rencana ini mencakup perancangan hardware dan software, penempatan perangkat, konfigurasi jaringan, serta biaya yang dibutuhkan.
Cara install apache, mysql, php, dan phpmyadmin pada freebsd 10



Cara install apache, mysql, php, dan phpmyadmin pada freebsd 10manafhsb Tulisan ini menjelaskan cara menginstal Apache, MySQL, PHP, dan phpMyAdmin di FreeBSD 10 untuk pengembangan web, termasuk menginstal masing-masing perangkat lunak, mengkonfigurasi, dan menguji menggunakan WordPress.
Peristiwa sekitar proklamasi dan proklamasi kemerdekaan



Peristiwa sekitar proklamasi dan proklamasi kemerdekaanGungun Misbah Gunawan Proklamasi Kemerdekaan Indonesia diumumkan pada tanggal 17 Agustus 1945 oleh Soekarno dan Mohammad Hatta di Jakarta, menyatakan kemerdekaan Indonesia dari penjajahan Jepang dan Belanda.
Persatuan dan kesatuan bangsa indonesia dari masa ke masa



Persatuan dan kesatuan bangsa indonesia dari masa ke masaafifahdhaniyah PERSATUAN DAN KESATUAN BANGSA INDONESIA DARI MASA KE MASA
Menjelaskan mengenai kemerdekaan dan sistem pemerintahan yang telah dilalui negara Indonesia pasca merdeka (revolusi - reformasi)
Makalah ubuntu server



Makalah ubuntu serverSumardin Setiawan Makalah ini membahas tentang Ubuntu Server dan cara menginstal serta mengkonfigurasinya. Tujuannya agar siswa SMK dapat dengan mudah membuat jaringan melalui sistem operasi Ubuntu Server. Secara singkat dijelaskan tentang definisi Ubuntu Server, perbedaan dengan desktop version, kelebihan dan kekurangannya, serta langkah-langkah dasar untuk menginstal Ubuntu Server.
Drupal and security - Advice for Site Builders and Coders



Drupal and security - Advice for Site Builders and CodersArunkumar Kupppuswamy The recent SA-CORE-2014-005 vulnerability has demonstrated that hackers have learnt how to take advantage of Drupal’s functionality to infect a site and go unnoticed. Site builders and site maintainers have a large role to play in preventing these kinds of disasters. Security doesn’t have to be a pain to implement and plan for.
The primary goal of this session is to give people a solid basis in the most common security issues so they can quickly identify those security issues. From there, we'll move into some other common pain-points of site builders like frequently made mistakes, modules to enhance security, and evaluating contributed module quality.
Overview of SSL: choose the option that's right for you



Overview of SSL: choose the option that's right for youCloudflare Keeping communication between your visitors and your website secure and confidential has never been more important. Data can be vulnerable to theft as it’s transferred to and from your website. One simple solution to this security threat is to encrypt your traffic with SSL (Secure Sockets Layer).
SSL encryption ensures the data transferred between your visitors and your site is safe from data theft, and having SSL enabled can also boost your Google search rankings.
CloudFlare has made it simple and easy to add SSL to your site: you don’t have to purchase a separate certificate or install anything. In this webinar CloudFlare’s solution engineer Peter Griffin explains the key features of SSL, and walks you through the simple process of getting SSL running on your site.
Ad
More Related Content
What's hot (20)
Jaringan Komputer dan Internet Kelas 10



Jaringan Komputer dan Internet Kelas 10Farichah Riha Jaringan Komputer dan Internet - Informatika
SMA/MA Kelas X Semester Genap
PRESENTASI TEKNOLOGI INFORMASI DAN KOMUNIKASI



PRESENTASI TEKNOLOGI INFORMASI DAN KOMUNIKASIYoga Romdoni Berisi Materi tentang teknologi informasi dan komunikasi
Sabar, qonaah, ridho dan sabar



Sabar, qonaah, ridho dan sabarSandi Audy Dokumen tersebut membahas tentang tujuan pembelajaran dan pengertian dari sifat-sifat bersyukur, qanaah, rida, dan sabar menurut agama Islam. Siswa diharapkan dapat memahami definisi dan manfaat dari empat sifat tersebut, serta contoh perilaku dan dalil yang mendukungnya.
Buku produk cake dan kue indonesia kls xii



Buku produk cake dan kue indonesia kls xiiArdian Sufandi Buku Produk Cake untuk kelas XII Jurusan Tata Boga
Proposal jaringan komputer



Proposal jaringan komputerirwansyah budiman Proposal ini merangkum rencana pembuatan jaringan kantor untuk PT Putra Mutiara Bersama dengan menggunakan jaringan Local Area Network (LAN) dengan topologi tree untuk memudahkan berbagi data dan komunikasi. Rencana ini mencakup perancangan hardware dan software, penempatan perangkat, konfigurasi jaringan, serta biaya yang dibutuhkan.
Cara install apache, mysql, php, dan phpmyadmin pada freebsd 10



Cara install apache, mysql, php, dan phpmyadmin pada freebsd 10manafhsb Tulisan ini menjelaskan cara menginstal Apache, MySQL, PHP, dan phpMyAdmin di FreeBSD 10 untuk pengembangan web, termasuk menginstal masing-masing perangkat lunak, mengkonfigurasi, dan menguji menggunakan WordPress.
Peristiwa sekitar proklamasi dan proklamasi kemerdekaan



Peristiwa sekitar proklamasi dan proklamasi kemerdekaanGungun Misbah Gunawan Proklamasi Kemerdekaan Indonesia diumumkan pada tanggal 17 Agustus 1945 oleh Soekarno dan Mohammad Hatta di Jakarta, menyatakan kemerdekaan Indonesia dari penjajahan Jepang dan Belanda.
Persatuan dan kesatuan bangsa indonesia dari masa ke masa



Persatuan dan kesatuan bangsa indonesia dari masa ke masaafifahdhaniyah PERSATUAN DAN KESATUAN BANGSA INDONESIA DARI MASA KE MASA
Menjelaskan mengenai kemerdekaan dan sistem pemerintahan yang telah dilalui negara Indonesia pasca merdeka (revolusi - reformasi)
Makalah ubuntu server



Makalah ubuntu serverSumardin Setiawan Makalah ini membahas tentang Ubuntu Server dan cara menginstal serta mengkonfigurasinya. Tujuannya agar siswa SMK dapat dengan mudah membuat jaringan melalui sistem operasi Ubuntu Server. Secara singkat dijelaskan tentang definisi Ubuntu Server, perbedaan dengan desktop version, kelebihan dan kekurangannya, serta langkah-langkah dasar untuk menginstal Ubuntu Server.
Similar to How to encrypt and protect your moodle site for free with let's encrypt (20)
Drupal and security - Advice for Site Builders and Coders



Drupal and security - Advice for Site Builders and CodersArunkumar Kupppuswamy The recent SA-CORE-2014-005 vulnerability has demonstrated that hackers have learnt how to take advantage of Drupal’s functionality to infect a site and go unnoticed. Site builders and site maintainers have a large role to play in preventing these kinds of disasters. Security doesn’t have to be a pain to implement and plan for.
The primary goal of this session is to give people a solid basis in the most common security issues so they can quickly identify those security issues. From there, we'll move into some other common pain-points of site builders like frequently made mistakes, modules to enhance security, and evaluating contributed module quality.
Overview of SSL: choose the option that's right for you



Overview of SSL: choose the option that's right for youCloudflare Keeping communication between your visitors and your website secure and confidential has never been more important. Data can be vulnerable to theft as it’s transferred to and from your website. One simple solution to this security threat is to encrypt your traffic with SSL (Secure Sockets Layer).
SSL encryption ensures the data transferred between your visitors and your site is safe from data theft, and having SSL enabled can also boost your Google search rankings.
CloudFlare has made it simple and easy to add SSL to your site: you don’t have to purchase a separate certificate or install anything. In this webinar CloudFlare’s solution engineer Peter Griffin explains the key features of SSL, and walks you through the simple process of getting SSL running on your site.
DNS hijacking



DNS hijackingMaarten Van Horenbeeck This document discusses DNS hijackings that have occurred from 2010 to 2013 in various countries and territories. It outlines the potential goals and impacts of such attacks, including defacement, theft of authentication tokens, and hosting of exploit kits or botnets. The document also describes some of the complexities in recovering from a hijacking and notes the top issues registries face are authorization schema vulnerabilities, SQL injection, and compromised registrar accounts. It provides recommendations for registries such as deploying a registry lock, emergency contact information, notification emails, and developing a security management framework.
Word press beirut 9th meetup march



Word press beirut 9th meetup marchFadi Nicolas Zahhar The document summarizes security best practices for WordPress websites. It includes:
1) Hardening security by changing file permissions, using random database names and passwords, securing wp-config.php, and forcing SSL logins.
2) Using plugins like Wordfence to add firewalls and malware scanning, and activity monitoring plugins to track user behavior.
3) Recommending regular backups, updates, and using trusted themes to maintain security over time.
Let's Encrypt!



Let's Encrypt!Drew Fustini Secure Your Website with free SSL cert from Let's Encrypt!
(for 300 Seconds of Fame at lightning talk at Chicago hackerspace Pumping Station: One)
Our CloudFlare experience



Our CloudFlare experienceNick Malcolm This presentation discusses how to set up CloudFlare for a website to improve page speed and security. It explains why to use CloudFlare for DDoS protection and faster page loads. The presenter details how to sign up and configure CloudFlare, including SSL certificates and caching settings. Experience with CloudFlare showed improved response times and reduced content size, though GeoIP stopped working and a partner was blocked. Overall, CloudFlare provides free basic protection and performance benefits.
Keeping your Drupal site secure 2013



Keeping your Drupal site secure 2013scorlosquet This document discusses keeping Drupal sites secure. It recommends using HTTPS, SSH, strong passwords, and limiting permissions. Drupal 7 introduced stronger password hashing and login flood control. Modules can enhance security, and hosted options like Pantheon focus on security updates. Site maintainers should follow best practices, take backups, and sanitize shared backups. Drupal 8 introduces Twig templating to prevent PHP execution and filters uploaded images to the same site. References are provided for further security information.
Advanced nginx in mercari - How to handle over 1,200,000 HTTPS Reqs/Min



Advanced nginx in mercari - How to handle over 1,200,000 HTTPS Reqs/MinMasahiro Nagano Advanced nginx in mercari - How to handle over 1,200,000 HTTPS Reqs/Min
「nginx実践入門」出版記念!執筆者らが語る nginx Tech Talks
Digital certificates



Digital certificatesDouglasPickett Digital certificates encrypt communication between a user's browser and a website's server, protecting sensitive information. To use HTTPS with Joomla, only one setting needs changing, but proper digital certificates still must be installed on the web server. Certificates can be self-signed, from free services like Let's Encrypt, or verified certificates from a Certificate Authority. Manually installing Let's Encrypt certificates involves running their software to generate certificates, then creating specific files on the server to verify ownership before obtaining the certificates and installing them via the server's control panel.
Session,Cookies and Authentication



Session,Cookies and AuthenticationKnoldus Inc. In this session, you will learn about what are sessions, cookies, how we can implement authentication in nodejs. And will also see about the CSRF attacks.
10 server security hacks to secure your web servers



10 server security hacks to secure your web serversTemok IT Services When we consider how to secure our information systems against hacking, the things that come to mind are firewalls, encryption, and applying advanced software solutions. These technical solutions are often where the data security focus is both monetary and administrative. Keep your servers and everything up to date, safe and secure. Nowadays, every business has a web presence. But many network administrators and security managers don’t know about server security hacks.
https://www.temok.com/blog/server-security-hacks/
Secrets to a Hack-Proof Joomla Revealed



Secrets to a Hack-Proof Joomla RevealedSiteGround.com The recent spike of hack attempts on various Joomla sites has made it more urgent than ever to take actions and secure your Joomla in the best possible way. In this webinar the SiteGround Joomla Performance Guru Daniel Kanchev shows the best practices and shares insightful tricks how to protect your Joomla from getting hacked:
- Joomla administrator security settings
- Bullet-proof password tips
- Vulnerable extensions to avoid
- Web application firewall configurations
- Recommended server settings
- Intrusion detection and protection tools
- Disaster recovery plans
SPDY and What to Consider for HTTP/2.0



SPDY and What to Consider for HTTP/2.0Mike Belshe These slides were presented at the IETF HTTP-bis working group in Paris (March, 2012) as the group considered how to address HTTP/2.0.
A Safer’s Guide to Protecting Your Data with the FME Platform 



A Safer’s Guide to Protecting Your Data with the FME Platform Safe Software Join us for a webinar on FME Platform security, where we'll cover everything you need to know to protect your installation and keep your data safe. We'll start by introducing FME and its capabilities, then move on to discussing the importance of security in the context of this powerful data integration tool.
Next, we'll give you an overview of the security features built into FME, including authentication, encryption, database and web connection management. We'll also share suggestions for hardening your installation, as well as best practices for maintaining and monitoring your installations. Following this we’ll take a look at how Safe Software works with Security, Compliance, and Privacy and how you can be assured that FME meets your organization's requirements.
Finally, we'll have a Q&A session where you can ask any questions you have about FME Platform security. Whether you're new to FME or an experienced user, this webinar will give you the knowledge and tools you need to keep your installation secure. Don't miss it!
Learn to Add an SSL Certificate Boost Your Site's Security.pdf



Learn to Add an SSL Certificate Boost Your Site's Security.pdfReliqusConsulting
Enhance your website's security with Reliqus Consulting's simple guide on how to install an SSL certificate. Our step-by-step instructions make it easy for anyone to boost their site's protection. Learn the importance of SSL certificates and follow our user-friendly process to ensure a secure connection for your visitors. Safeguard sensitive data and build trust with your audience by implementing this crucial security measure.
iOS Application Security Testing



iOS Application Security TestingBlueinfy Solutions This document discusses insecure data storage on iOS devices. It provides details on how attackers can gain access to sensitive information stored by applications via insecure means such as weak WiFi passwords, jailbreaking, or physical theft. The types of sensitive information commonly found includes authentication credentials, financial data, personal information about the owner. It also lists specific locations within the file system where different types of application data, settings, logs and other information are stored.
The WordPress Hosting experience - Bought cheaply and paid dearly? - Jan Löf...



The WordPress Hosting experience - Bought cheaply and paid dearly? - Jan Löf...Jan Löffler There are two main customer types in the world of WordPress: The greed-is-cool guy and the one who happily pays a premium for services that help to increase both performance and security of web projects and agility of workflows. What’s the difference between the two and who’s the one you want to go after? There are so many WordPress hosting offerings available and even we’re getting confused when trying to compare them all. So we asked experts to do it instead. In his talk Jan will not only share some of the results and introduce his vision of the best-in-class WordPress hosting. He’ll bring a surprise guest telling you how to make a WordPress user happy and let hosters stand out from the crowd. Becoming the most wanted WordPress hoster alive is easier than you think. Join in and be the first to hear about the latest product innovations from Plesk.
Html5 web storage



Html5 web storageMindfire Solutions HTML5 web storage, a better local storage than cookies. Learn how web pages can store data locally within the user's browser.
SharePoint On-Premises Nirvana



SharePoint On-Premises NirvanaJohn Calvert This document provides information about a SharePoint Saturday event in Ottawa on December 3rd, 2016. The event agenda includes topics on installing, configuring, and operating a SharePoint farm, both small and large. It also discusses SQL Server, IIS, and Windows Server configurations. Presenters will provide overviews of their experience with Microsoft technologies and SharePoint solutions. Attendees can learn about tools and resources for automating SharePoint deployment and management.
A Safer’s Guide to Protecting Your Data with the FME Platform



A Safer’s Guide to Protecting Your Data with the FME PlatformSafe Software Join us for a webinar on FME Platform security, where we'll cover everything you need to know to protect your installation and keep your data safe. We'll start by introducing FME and its capabilities, then move on to discussing the importance of security in the context of this powerful data integration tool.
Next, we'll give you an overview of the security features built into FME, including authentication, encryption, database and web connection management. We'll also share suggestions for hardening your installation, as well as best practices for maintaining and monitoring your installations. Following this we’ll take a look at how Safe Software works with Security, Compliance, and Privacy and how you can be assured that FME meets your organization's requirements.
Finally, we'll have a Q&A session where you can ask any questions you have about FME Platform security. Whether you're new to FME or an experienced user, this webinar will give you the knowledge and tools you need to keep your installation secure. Don't miss it!
Ad
More from moorejon (13)
Best new features in moodle 3.1



Best new features in moodle 3.1moorejon Moodle 3.1 includes several new features to improve performance, support competency-based education, and mobile learning. Key additions are PHP 7 support to boost speed, tools for defining and tracking individual learning plans, expanded mobile quiz and app capabilities, and easier course editing and publishing. The update also enhances forums, search, tagging, assignment grading and more.
Using moodle badges



Using moodle badgesmoorejon The document discusses using badges in Moodle. It defines badges as a way to demonstrate and acknowledge student achievements using the Mozilla Open Badges standard. Badges can be used at the site level or course level, and are manually assigned or earned through activity/resource completions. The document provides information on setting up criteria and requirements for badges, and how students can view and share badges they earn. It also discusses using badges and leaderboards to gamify the learning experience.
Using moodle outcomes and competencies



Using moodle outcomes and competenciesmoorejon - The document provides information on Moodle Outcomes and the new Competency Based Education (CBE) system in Moodle 3.1, comparing their features for defining and tracking learning objectives and competencies.
- Moodle Outcomes allows associating scales and activities with flat lists of outcomes, while CBE supports hierarchical competency frameworks, individual learning plans, and integrated workflows for competency demonstration.
- CBE has more fine-grained features for competency-based education, including tight course/activity integration and customization options, whereas Outcomes is more limited but integrated with Moodle's grading.
Git for Moodle Administrators



Git for Moodle Administratorsmoorejon This document provides information about using Git for Moodle administrators. It begins with the presenter's background and experience with Moodle. It then discusses what Git is, how Moodle uses Git for development and releases, and how to install and upgrade Moodle using Git. The document also covers adding plugins with Git and managing Git forks. It concludes by taking questions and providing contact information for further assistance.
Introduction to Moodle Development



Introduction to Moodle Developmentmoorejon This document provides an introduction to Moodle development. It outlines the necessary tools and steps to create a basic "Hello World" block, including using language files for localization, implementing capabilities, scheduled execution, and asking questions. The presenter provides background on their Moodle experience and the session objectives are to create a basic block, add configuration options, and display data based on a user's capabilities and scheduled execution. A number of development tools are also briefly outlined.
Extending Moodle Reporting



Extending Moodle Reportingmoorejon How to extend Moodle reporting to get more useful and actionable reporting, including site wide reports and better filtering.
Best practices in Moodle administration Monatana Moot 2014



Best practices in Moodle administration Monatana Moot 2014moorejon Best Practices in Moodle Administration provides tips for optimizing Moodle performance and uptime. The presentation recommends establishing change management processes, using monitoring tools, automating user management, and following security best practices. It also demonstrates hands-on techniques for backups, debugging issues, and customizing themes.
JMeter performance and scalability in Moodle Montana Moot 2014



JMeter performance and scalability in Moodle Montana Moot 2014moorejon Using jMeter Moodle admins can help assess the capacity or potential capabilities of their Moodle site. With jMeter testing, admins can determine what kind of concurrency they should expect to be able to achieve with their current server configuration. This workshop would then tie into a one-hour session related to performance
Moodle performance and stress testing



Moodle performance and stress testingmoorejon Have you experienced a Moodle site failure during a critical time? Are you worried that your Moodle service won't be able to meet your needs at the busiest times? This session will cover a variety of methods to ensure optimal performance of Moodle under peak load. The session will address general resource guidelines for expected concurrency and help administrators determine the correct sizing of IT resources for an expected Moodle load. The session will also cover benchmarking techniques that can be used to measure the actual performance of your Moodle infrastructure.
Introduction To Elis



Introduction To Elismoorejon An Introduction to the Enterprise Learning Intelligence Suite for Moodle: Curriculum Management, Transcripts and Certifications, Enterprise Reporting (JasperSoft BI), Document Management (Alfresco), and Notifications.
Securing Your Moodle



Securing Your Moodlemoorejon 1) The document discusses various security measures for securing a Moodle installation including backing up data regularly, keeping software updated, using firewalls, monitoring server activity, and preparing for potential security breaches.
2) It recommends signing up for security mailing lists to stay updated on vulnerabilities and alerts, and configuring specific Moodle site security settings such as forcing login, using HTTPS, and restricting access.
3) The most secure configuration places the Moodle files and data folders outside of the web root with restricted permissions, uses SSL, and disables unnecessary services and access.
Best Practices In Moodle Administration



Best Practices In Moodle Administrationmoorejon The document provides an overview of best practices for Moodle administration based on a presentation. It includes tips on change management, performance tuning, backups, user management, issue tracking, security practices, and custom development. The presentation encourages automating processes, using change control boards, monitoring server performance, and testing custom modules and themes. It also demonstrates hands-on exercises for administrative tasks in Moodle.
Integrating Moodle With Enterprise Systems



Integrating Moodle With Enterprise Systemsmoorejon Integrating Moodle with external systems like LDAP, databases, and SSO providers can automate user authentication and enrollment, making administration easier for larger sites. Plugins exist that allow syncing user accounts, automatically creating and assigning courses, and enrolling students from external data sources. These plugins save time by handling processes like authentication, enrollment, and data synchronization externally rather than requiring manual setup and management in Moodle.
Ad
Recently uploaded (20)
Presentation of the MIPLM subject matter expert Erdem Kaya



Presentation of the MIPLM subject matter expert Erdem KayaMIPLM Presentation of the MIPLM subject matter expert Erdem Kaya
YSPH VMOC Special Report - Measles Outbreak Southwest US 4-30-2025.pptx



YSPH VMOC Special Report - Measles Outbreak Southwest US 4-30-2025.pptxYale School of Public Health - The Virtual Medical Operations Center (VMOC) A measles outbreak originating in West Texas has been linked to confirmed cases in New Mexico, with additional cases reported in Oklahoma and Kansas. The current case count is 795 from Texas, New Mexico, Oklahoma, and Kansas. 95 individuals have required hospitalization, and 3 deaths, 2 children in Texas and one adult in New Mexico. These fatalities mark the first measles-related deaths in the United States since 2015 and the first pediatric measles death since 2003.
The YSPH Virtual Medical Operations Center Briefs (VMOC) were created as a service-learning project by faculty and graduate students at the Yale School of Public Health in response to the 2010 Haiti Earthquake. Each year, the VMOC Briefs are produced by students enrolled in Environmental Health Science Course 581 - Public Health Emergencies: Disaster Planning and Response. These briefs compile diverse information sources – including status reports, maps, news articles, and web content– into a single, easily digestible document that can be widely shared and used interactively. Key features of this report include:
- Comprehensive Overview: Provides situation updates, maps, relevant news, and web resources.
- Accessibility: Designed for easy reading, wide distribution, and interactive use.
- Collaboration: The “unlocked" format enables other responders to share, copy, and adapt seamlessly. The students learn by doing, quickly discovering how and where to find critical information and presenting it in an easily understood manner.
Handling Multiple Choice Responses: Fortune Effiong.pptx



Handling Multiple Choice Responses: Fortune Effiong.pptxAuthorAIDNationalRes INTRO TO STATISTICS
INTRO TO SPSS INTERFACE
CLEANING MULTIPLE CHOICE RESPONSE DATA WITH EXCEL
ANALYZING MULTIPLE CHOICE RESPONSE DATA
INTERPRETATION
Q & A SESSION
PRACTICAL HANDS-ON ACTIVITY
Exploring-Substances-Acidic-Basic-and-Neutral.pdf



Exploring-Substances-Acidic-Basic-and-Neutral.pdfSandeep Swamy Exploring Substances:
Acidic, Basic, and
Neutral
Welcome to the fascinating world of acids and bases! Join siblings Ashwin and
Keerthi as they explore the colorful world of substances at their school's
National Science Day fair. Their adventure begins with a mysterious white paper
that reveals hidden messages when sprayed with a special liquid.
In this presentation, we'll discover how different substances can be classified as
acidic, basic, or neutral. We'll explore natural indicators like litmus, red rose
extract, and turmeric that help us identify these substances through color
changes. We'll also learn about neutralization reactions and their applications in
our daily lives.
by sandeep swamy
pulse ppt.pptx Types of pulse , characteristics of pulse , Alteration of pulse



pulse ppt.pptx Types of pulse , characteristics of pulse , Alteration of pulsesushreesangita003 what is pulse ?
Purpose
physiology and Regulation of pulse
Characteristics of pulse
factors affecting pulse
Sites of pulse
Alteration of pulse
for BSC Nursing 1st semester
for Gnm Nursing 1st year
Students .
vitalsign
The ever evoilving world of science /7th class science curiosity /samyans aca...



The ever evoilving world of science /7th class science curiosity /samyans aca...Sandeep Swamy The Ever-Evolving World of
Science
Welcome to Grade 7 Science4not just a textbook with facts, but an invitation to
question, experiment, and explore the beautiful world we live in. From tiny cells
inside a leaf to the movement of celestial bodies, from household materials to
underground water flows, this journey will challenge your thinking and expand
your knowledge.
Notice something special about this book? The page numbers follow the playful
flight of a butterfly and a soaring paper plane! Just as these objects take flight,
learning soars when curiosity leads the way. Simple observations, like paper
planes, have inspired scientific explorations throughout history.
Niamh Lucey, Mary Dunne. Health Sciences Libraries Group (LAI). Lighting the ...



Niamh Lucey, Mary Dunne. Health Sciences Libraries Group (LAI). Lighting the ...Library Association of Ireland
UNIT 3 NATIONAL HEALTH PROGRAMMEE. SOCIAL AND PREVENTIVE PHARMACY



UNIT 3 NATIONAL HEALTH PROGRAMMEE. SOCIAL AND PREVENTIVE PHARMACYDR.PRISCILLA MARY J NATIONAL HEALTH PROGRAMMEE
Unit 6_Introduction_Phishing_Password Cracking.pdf



Unit 6_Introduction_Phishing_Password Cracking.pdfKanchanPatil34 Initial stages of attacks, Phishing, Password Cracking, guidelines to prevent password attacks, Strong password, weak password,
Marie Boran Special Collections Librarian Hardiman Library, University of Gal...



Marie Boran Special Collections Librarian Hardiman Library, University of Gal...Library Association of Ireland Phoenix – A Collaborative Renewal of Children’s and Young People’s Services Clare Doyle - Cork City Libraries
To study the nervous system of insect.pptx



To study the nervous system of insect.pptxArshad Shaikh The *nervous system of insects* is a complex network of nerve cells (neurons) and supporting cells that process and transmit information. Here's an overview:
Structure
1. *Brain*: The insect brain is a complex structure that processes sensory information, controls behavior, and integrates information.
2. *Ventral nerve cord*: A chain of ganglia (nerve clusters) that runs along the insect's body, controlling movement and sensory processing.
3. *Peripheral nervous system*: Nerves that connect the central nervous system to sensory organs and muscles.
Functions
1. *Sensory processing*: Insects can detect and respond to various stimuli, such as light, sound, touch, taste, and smell.
2. *Motor control*: The nervous system controls movement, including walking, flying, and feeding.
3. *Behavioral responThe *nervous system of insects* is a complex network of nerve cells (neurons) and supporting cells that process and transmit information. Here's an overview:
Structure
1. *Brain*: The insect brain is a complex structure that processes sensory information, controls behavior, and integrates information.
2. *Ventral nerve cord*: A chain of ganglia (nerve clusters) that runs along the insect's body, controlling movement and sensory processing.
3. *Peripheral nervous system*: Nerves that connect the central nervous system to sensory organs and muscles.
Functions
1. *Sensory processing*: Insects can detect and respond to various stimuli, such as light, sound, touch, taste, and smell.
2. *Motor control*: The nervous system controls movement, including walking, flying, and feeding.
3. *Behavioral responses*: Insects can exhibit complex behaviors, such as mating, foraging, and social interactions.
Characteristics
1. *Decentralized*: Insect nervous systems have some autonomy in different body parts.
2. *Specialized*: Different parts of the nervous system are specialized for specific functions.
3. *Efficient*: Insect nervous systems are highly efficient, allowing for rapid processing and response to stimuli.
The insect nervous system is a remarkable example of evolutionary adaptation, enabling insects to thrive in diverse environments.
The insect nervous system is a remarkable example of evolutionary adaptation, enabling insects to thrive
How to Manage Opening & Closing Controls in Odoo 17 POS



How to Manage Opening & Closing Controls in Odoo 17 POSCeline George In Odoo 17 Point of Sale, the opening and closing controls are key for cash management. At the start of a shift, cashiers log in and enter the starting cash amount, marking the beginning of financial tracking. Throughout the shift, every transaction is recorded, creating an audit trail.
To study Digestive system of insect.pptx



To study Digestive system of insect.pptxArshad Shaikh Education is one thing no one can take away from you.”
Ultimate VMware 2V0-11.25 Exam Dumps for Exam Success



Ultimate VMware 2V0-11.25 Exam Dumps for Exam SuccessMark Soia Boost your chances of passing the 2V0-11.25 exam with CertsExpert reliable exam dumps. Prepare effectively and ace the VMware certification on your first try
Quality dumps. Trusted results. — Visit CertsExpert Now: https://www.certsexpert.com/2V0-11.25-pdf-questions.html
Odoo Inventory Rules and Routes v17 - Odoo Slides



Odoo Inventory Rules and Routes v17 - Odoo SlidesCeline George Odoo's inventory management system is highly flexible and powerful, allowing businesses to efficiently manage their stock operations through the use of Rules and Routes.
World war-1(Causes & impacts at a glance) PPT by Simanchala Sarab(BABed,sem-4...



World war-1(Causes & impacts at a glance) PPT by Simanchala Sarab(BABed,sem-4...larencebapu132 This is short and accurate description of World war-1 (1914-18)
It can give you the perfect factual conceptual clarity on the great war
Regards Simanchala Sarab
Student of BABed(ITEP, Secondary stage)in History at Guru Nanak Dev University Amritsar Punjab 🙏🙏
Phoenix – A Collaborative Renewal of Children’s and Young People’s Services C...



Phoenix – A Collaborative Renewal of Children’s and Young People’s Services C...Library Association of Ireland
YSPH VMOC Special Report - Measles Outbreak Southwest US 4-30-2025.pptx



YSPH VMOC Special Report - Measles Outbreak Southwest US 4-30-2025.pptxYale School of Public Health - The Virtual Medical Operations Center (VMOC)
Niamh Lucey, Mary Dunne. Health Sciences Libraries Group (LAI). Lighting the ...



Niamh Lucey, Mary Dunne. Health Sciences Libraries Group (LAI). Lighting the ...Library Association of Ireland
Marie Boran Special Collections Librarian Hardiman Library, University of Gal...



Marie Boran Special Collections Librarian Hardiman Library, University of Gal...Library Association of Ireland
Phoenix – A Collaborative Renewal of Children’s and Young People’s Services C...



Phoenix – A Collaborative Renewal of Children’s and Young People’s Services C...Library Association of Ireland
How to encrypt and protect your moodle site for free with let's encrypt
- 1. How To Encrypt and Protect your Moodle Site for Free Jonathan Moore ● http://elearningconsultancy.com ● [email protected] ● Twitter: @moorejon ● Skype: moorejon07
- 2. What is Let's Encrypt? ● A new certificate authority ● Offering free Secure Sockets Layer / Transport Layer Security (SSL / TSL) certificates ● Automate process to simplify installation
- 3. What you need ● A domain you control ● Admin access to server hosting the domain ● Some comfort with command line ● Desire to improve your site's security
- 4. Why encrypt? ● Protect user's login credentials ● Protect confidential information stored on your site ● Help improve the internet's herd immunity ● Browser makers gradually making this the default for 'safe' access indicators ● More difficult for ISPs / carriers interfere with usability of your site
- 5. Warning! ● Do you have a good backup ● This can damage your configuration files
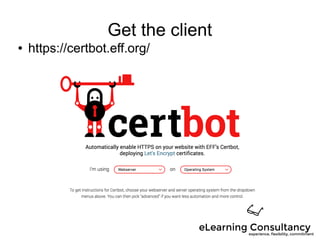
- 6. Get the client ● https://certbot.eff.org/
- 7. Installation
- 8. Usage
- 9. Renewals
- 10. Moodle Setup ● Site Administration → Security → HTTP Security
- 11. To Fully Encrypted Site ● Edit config.php – Change $CFG->wwwroot ● From http:// ● To https://
- 12. Re-write old URLs on Existing Sites ● http://my_domain/moodle31/admin/tool/replace/
- 13. Compatibility ● Works with most current browsers ● Will improve over time
- 17. Test it ● Early days for Let's Encrypt ● Try first on staging or pilot site















