Hyper Island - 2012
- 1. EVIL DATA MINING FOR FUN AND PROFIT!
- 2. Contents ● Web Scraping ● Quick and Dirty SQL Injections ● iPhones, WiFi and Evil Twins ● Hacking Neighbours ● Port scanning on Steroids
- 3. Introduction ● Fredrik Nordberg Almroth (@Almroot) Head application engineer and co-founder @ detectify.com IT-security guy Hacked Google. Twice. ● Johan Edholm (@norrskal) Server administrator and co-founder @ detectify.com Worked with IT security analytics and anti-scraping Studied system and network management in Linux
- 4. What is Detectify? Detectify is an automated vulnerability scanner.
- 5. ● You sign up using beta code.
- 6. ● You press start! ● Detectify emulates a hacking attack.
- 7. ● You get a report regarding your vulnerabilities.
- 8. ● Detectify is currently in closed beta! ● You may try it for free using the beta code: HyperMine ● http://detectify.com/ ● We love feedback! :)
- 9. What is data mining? ● Data mining is mostly associated with statistics and machine learning. ● ...or discovery of patterns (intelligence) in large datasets... ● No fancy algorithms! Just real life examples.
- 10. Web scraping ● Grab content from websites ● Host somewhere else ● Study the data ● Sell the data
- 11. Web scraping ● Manual copy-paste
- 12. Web scraping
- 14. Web scraping ● Bad scrapers ○ Downloadable or online tools ○ Homemade scripts ○ HTTP rewriters
- 15. Web scraping ● Homemade scripts ○ Made for one site/purpose ○ No hacking ○ May be against ToS ○ Probably legal
- 16. Web scraping ● Sosseblaskan.se ○ Copy of aftonbladet (rewrite) ○ A joke ○ Not ads for aftonbladet ○ Not phishing ○ Illegal
- 17. SQL ● Structured Query Language ● Used to talk with databases. MySQL, PostgreSQL, etc...
- 18. How it's used ● Websites use databases to maintain data. ● The SQL queries often contain user-data. ● You search on a website for a few keywords. ● The odds of it being done by some SQL dialect is huge.
- 19. What could possibly go wrong? ● User supplied data may alter the SQL query. ● Example: SELECT title FROM blog WHERE title = '$search_keywords'; ● If the searched data contain a quote, the SQL query will break. ● Attackers may gain other data than just the "blog title". ● Usernames, passwords, emails, credit-cards...
- 20. SQL Injections
- 21. ● Devastating attack. ● Worst part. It's really common. ● Remember Sony last year?
- 22. ● Victims 2012. ○ eHarmony ○ last.fm ○ Yahoo! ○ Android Forums ○ Billabong ○ Formspring ○ nVidia ○ Gamigo ○ ...List goes on...
- 23. ● Thousands of sites attacked daily. ● Incredibly easy to get going. ● Loads of guides and tools on the internet. ● Devastating for the vulnerable organizations.
- 24. LIVE DEMO! (This is the time we'll stand here and struggle with the equipment.)
- 25. Fun with WLAN ● Create an evil twin ● Jasager
- 26. Evil twin ● You connect to eg. "espresso house free" ● iPhone will save and remember that network ● When you come back it will automatically connect
- 27. Evil twin ● Someone creates a network called "espresso house free" ● Your phone will automatically connect
- 28. What if the attacker don't know which networks you've been connected to?
- 30. Jasager
- 31. Fun with WLAN ● Works on everything ○ Windows, linux, Mac, Android, iPhone etc ● Can be monitored ○ See which networks you are looking for and in which order
- 33. IT-Security @ Home ● Devices on local networks. ○ Routers ○ Printers ○ Heat Pumps ○ Laptops ○ PC's ○ Tablets ○ Cellphones ○ XBOX'es ○ ...etc...
- 34. Telecom operator ComHem provide "Tre-hål-i-väggen"
- 35. ● Routers may act as switches ● IP Forwarding ● You can see your neighbours devices
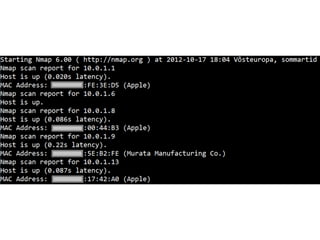
- 37. ● Portscan! ● A port scanner finds open services on IP- addresses. ● nmap
- 39. ● Find vulnerability or ● Weak (default) password or ● No password! Protip: http://www.routerpasswords.com/
- 40. GAME OVER
- 41. Conclusion You can with ease gain access to your neighbours data.
- 42. Speaking of portscanning... ● Spring 2010, the "spoon" project. ● Got interested in packet crafting. ● 3000 packets/second
- 43. ● Sweden got 25.000.000 allocated IPv4-addresses. ● ...Results in a timeframe of 2 hours and 20 min to scan. ● Resolve all servers on a given port in a Sweden. ● Could of course be applied to any country.
- 44. ● Early 2011, "spoon2". ● 30000 packets/second. Ten times as fast! ● From 2½ hour, to approximate 15 minutes. ● Same result.
- 45. ● Imagine a company. Like ACME Corp. ● 10 servers running "spoon2". ● Get a fresh map of Sweden every 90 second. ● 100 servers, every 9'th second second.
- 46. ● ACME Corp got potential to become a global "pingdom". ● Results in large scale data mining. ● Would require loads of clever algorithms and infrastructure to maintain it all though.
- 47. shodanhq.com ● The firm shodanhq already crawls countries for open services. ● Identified ~438.000 web servers in Sweden alone. ● Mostly devices found on local networks. (routers / printers). ● No security. Loads of vulnerable devices.
- 48. ● Eavesdrop your neighbour? No problem. ● Why bother? ● Can be applied to a whole country.
- 49. Summary ● Web Scraping ● Quick and Dirty SQL Injections ● iPhones, WiFi and Evil Twins ● Hacking Neighbours ● Port scanning on Steroids
- 50. Q&A Hack the planet! http://detectify.com/
- 51. References ● http://www.theta44.org/karma/aawns.pdf ● http://timtux.net/posts/10-Vad-delar-du-ut-IT-skerhet-i-hemmet ● http://krebsonsecurity.com/2010/06/wi-fi-street-smarts-iphone-edition/ ● http://nmap.org/6/ ● http://www.ietf.org/rfc/rfc793.txt ● http://www.ietf.org/rfc/rfc791.txt ● http://www.ietf.org/rfc/rfc1323.txt ● http://www.zdnet.com/sql-injection-attacks-up-69-7000001742/