Ad
iCode Security Architecture Framework
- 1. Security Verified Security Architecture Framework Mohamed Ridha Chebbi, CISSP iCode InfoSec – CEO & Head of PS [email protected] © 2012 iCode information security All rights reserved
- 2. Agenda Security Verified Introduction Approach to Develop Security Architecture Information Security Concepts Security Architecture Levels & Viewpoints Technical Viewpoint Information Viewpoint Business Viewpoint Security Architecture Framework iCode Professional Services © 2012 iCode information security All rights reserved
- 3. Introduction Security Verified There are a Number of Approaches to Develop a Security Architecture Like : 1. As a DOMAIN in the TECHNICAL ARCHITECTURE 2. As TOTALLY SEPARATE Security Architecture ViewPoint Security is Pervasive across all of Architecture impacting : - Business - Information - and Technology © 2012 iCode information security All rights reserved
- 4. Approach to Develop Security Architecture Security Verified Architecture Information Security : . Data Security Architecture Requirements Solutions & Business . Data Classification Security . Application Security Architecture Standard Architecture Security : Technology . Business Security Requirements . Security Organization Security : . Security Policy . Technology Framework Security . Process Security Requirements . Security Principles . Security Patterns . Security Services . Security Bricks © 2012 iCode information security All rights reserved
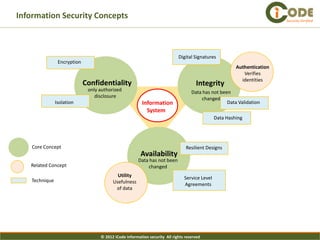
- 5. Information Security Concepts Security Verified Digital Signatures Encryption Authentication Verifies identities Confidentiality Integrity only authorized Data has not been disclosure changed Isolation Information Data Validation System Data Hashing Core Concept Resilient Designs Availability Data has not been Related Concept changed Utility Service Level Technique Usefulness Agreements of data © 2012 iCode information security All rights reserved
- 6. iCode Security Architecture Framework Security Verified Vision Security Services Framework Design Principles Requirement Templates Business Information Technical Viewpoint Viewpoint Viewpoint © 2012 iCode information security All rights reserved
- 7. Technical Viewpoint Security Verified Vision Security Services Framework .Trust Levels .Conceptual Technology Models Design Principles .Logical Technology Models .Trust Models Requirement Templates . Technical Reference Models .Security Infrastructure Architecture .Security Services Architecture .Application Security Architecture Technical Viewpoint © 2012 iCode information security All rights reserved
- 8. Information Viewpoint Security Verified Vision Security Services Framework . Policy Framework . Information Classification Framework Design Principles . Security Information Flow Models . SLA Model Requirement Templates . Security Information Architecture . Information Classification Register . SLA’s Information Viewpoint © 2012 iCode information security All rights reserved
- 9. Business Viewpoint Security Verified Vision Security Services Framework .Process Models .Roles & Responsibi- lities Models Design Principles .Organization Models Requirement Templates .Organizational Architecture Business Viewpoint © 2012 iCode information security All rights reserved
- 10. Global Security Architecture Framework Security Verified Vision Security Services Framework .Process . Policy .Trust Levels Models Framework .Roles & . Information .Conceptual Responsibi- Classification Technology lities Models Framework Models Design Principles . Security Information .Logical Technology .Organization Flow Models Models Models . SLA Model .Trust Models Requirement Templates .Organizational . Security Information Architecture . Technical Reference Models .Security Infrastructure Architecture . Information Classification Register Architecture . SLA’s .Security Services Architecture .Application Security Architecture Business Information Technical Viewpoint Viewpoint Viewpoint © 2012 iCode information security All rights reserved
- 11. iCode Professional Services for Tunisiana Security Verified © 2012 iCode information security All rights reserved
- 12. Security Verified Thanks Mohamed Ridha Chebbi, CISSP iCode InfoSec – CEO & Head of PS [email protected] © 2012 iCode information security All rights reserved
































































![[Chaco] Soluciones de Seguridad – Nicolás Pérez, Giux](https://cdn.slidesharecdn.com/ss_thumbnails/8-120705112239-phpapp02-thumbnail.jpg?width=560&fit=bounds)








![Software Plus Services Customer Deck[1]](https://cdn.slidesharecdn.com/ss_thumbnails/softwareplusservicescustomerdeck1-090611093802-phpapp02-thumbnail.jpg?width=560&fit=bounds)




