Identity Based Encryption
- 1. Introduction IBE Based on Quadratic Residues IBE Based on Pairing Scalar Multiplication Contributions Future Work Identity Based Encryption A Literature Survey Pratik Poddar Department of Computer Science and Engineering IIT Bombay November 21, 2009
- 2. Introduction IBE Based on Quadratic Residues IBE Based on Pairing Scalar Multiplication Contributions Future Work Contents 1 Introduction IBE Idea IBE Framework Applications of IBE 2 IBE Based on Quadratic Residues Quadratic Residues Jacobi Symbol Quadratic Residuosity Problem IBE Scheme Observations on Cock’s IBE 3 IBE Based on Pairing Bilinear Pairing Basic BF-IBE Scheme Weil Pairing Miller’s Algorithm 4 Scalar Multiplication 5 Contributions 6 Future Work
- 3. Introduction IBE Based on Quadratic Residues IBE Based on Pairing Scalar Multiplication Contributions Future Work IBE Idea Adi Shamir, Israel, 1984
- 4. Introduction IBE Based on Quadratic Residues IBE Based on Pairing Scalar Multiplication Contributions Future Work Need for IBE? Need for certificate management Certicate Management through PKI Problems with PKI 1 Authenticating the user (Issuance) 2 Certificate Revocation Lists (Revocation) The first IBE Schemes
- 5. Introduction IBE Based on Quadratic Residues IBE Based on Pairing Scalar Multiplication Contributions Future Work IBE Framework An IBE scheme E is specified by four randomized algorithms Setup: Returns params (system parameters) and master-key. params includes a description of a finite message and ciphertext space. The system parameters(params) would be known to everyone while the master-key is known only to the PKG Extract: Takes as input params, master-key and arbitrary ID, and returns d Encrypt: Takes as input params, ID and M ∈ M. It returns a ciphertext C ∈ C. Decrypt: Takes as input params, C ∈ C, and a private key d. It returns M ∈ M.
- 6. Introduction IBE Based on Quadratic Residues IBE Based on Pairing Scalar Multiplication Contributions Future Work Applications of IBE Revocation of Public Keys Delegation of decryption Keys Forward secure encryption Timed Cryptography
- 7. Introduction IBE Based on Quadratic Residues IBE Based on Pairing Scalar Multiplication Contributions Future Work Contents 1 Introduction IBE Idea IBE Framework Applications of IBE 2 IBE Based on Quadratic Residues Quadratic Residues Jacobi Symbol Quadratic Residuosity Problem IBE Scheme Observations on Cock’s IBE 3 IBE Based on Pairing Bilinear Pairing Basic BF-IBE Scheme Weil Pairing Miller’s Algorithm 4 Scalar Multiplication 5 Contributions 6 Future Work
- 8. Introduction IBE Based on Quadratic Residues IBE Based on Pairing Scalar Multiplication Contributions Future Work Definition of QR An integer q is called a quadratic residue modulo n if it is congruent to a perfect square (mod n) i.e., if there exists an integer x such that x2 ≡ q (mod n) Otherwise, q is called a quadratic non-residue (mod n). Notation: 0 if p divides a a = +1 if a is a quadratic residue modulo p and p does not divide a p −1 if a is a quadratic non-residue modulo p.
- 9. Introduction IBE Based on Quadratic Residues IBE Based on Pairing Scalar Multiplication Contributions Future Work Properties of QR The number of quadratic residues (mod n) cannot exceed (n/2) + 1 (n even) or (n + 1)/2 (n odd) The multiplicative inverse of a residue is a residue, and the inverse of a non-residue is a non-residue The product of two non-residues is a residue and the product of a non-residue and a (non-zero) residue is a non-residue ab a a = p p p
- 10. Introduction IBE Based on Quadratic Residues IBE Based on Pairing Scalar Multiplication Contributions Future Work Definition of Jacobi Symbol For any integer a and any positive odd integer n, the Jacobi symbol is defined as the product of the Legendre symbols corresponding to the prime factors of n: α1 α2 αk a a a a α α α = ··· where n = p1 1 p2 2 · · · pk k n p1 p2 pk
- 11. Introduction IBE Based on Quadratic Residues IBE Based on Pairing Scalar Multiplication Contributions Future Work Properties of Jacobi Symbol a If n is (an odd) prime, then the Jacobi symbol is also a n Legendre symbol a b If a ≡ b (mod n) then = n n a 0 if gcd(a, n) = 1 = n ±1 if gcd(a, n) = 1 ab a b a2 = , so = 1 (or 0) n n n n a a a a = , so = 1 (or 0) mn m n n2
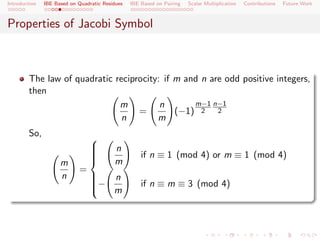
- 12. Introduction IBE Based on Quadratic Residues IBE Based on Pairing Scalar Multiplication Contributions Future Work Properties of Jacobi Symbol The law of quadratic reciprocity: if m and n are odd positive integers, then m n m−1 n−1 = (−1) 2 2 n m So, n if n ≡ 1 (mod 4) or m ≡ 1 (mod 4) m m = n n − if n ≡ m ≡ 3 (mod 4) m
- 13. Introduction IBE Based on Quadratic Residues IBE Based on Pairing Scalar Multiplication Contributions Future Work Quadratic Residuosity Problem a Like the Legendre symbol, if = −1 then a is a quadratic n non-residue (mod n) Like the Legendre symbol, if a is a quadratic residue (mod n), then a =1 n a Unlike the Legendre symbol, if = 1, then a may or may not be n a quadratic residue (mod n)
- 14. Introduction IBE Based on Quadratic Residues IBE Based on Pairing Scalar Multiplication Contributions Future Work Difficult Problem Calculating Jacobi symbol is easy QR Problem is difficult Easier than factorization Basis for Cock’s IBE and GM cryptosystem
- 15. Introduction IBE Based on Quadratic Residues IBE Based on Pairing Scalar Multiplication Contributions Future Work IBE Based on Quadratic Residues Clifford Cocks, Govt. Comm. HQ, UK, 2001
- 16. Introduction IBE Based on Quadratic Residues IBE Based on Pairing Scalar Multiplication Contributions Future Work Cock’s IBE Scheme Setup The PKG chooses: a public RSA-modulus n = pq, where p, q are primes such that p ≡ q ≡ 3 (mod 4) and are kept secret the message and the cipher space M = {−1, 1} , C = Zn a secure public hash function f : {0, 1}∗ → Zn
- 17. Introduction IBE Based on Quadratic Residues IBE Based on Pairing Scalar Multiplication Contributions Future Work Cock’s IBE Scheme Extract When user ID wants to obtain his private key, he contacts the PKG through a secure channel. The PKG a derives a with n = 1 by a determistic process from ID (e.g. multiple application of f on ID) n+5−p−q computes r = a 8 (mod n). This fulfils either r 2 = a (mod n) or r 2 = −a (mod n).a transmits r to the user (p−1)(q−1) a Calculations: r 2 = a.a 4 (mod p) which equals a if a is a quadratic residue modulo p and −a otherwise. Similarly for q. Since, n = 1, we get that r 2 = a or − a `a´ (mod n).
- 18. Introduction IBE Based on Quadratic Residues IBE Based on Pairing Scalar Multiplication Contributions Future Work Cock’s IBE Scheme Encrypt To encrypt a bit (coded as {1, −1}) m ∈ M for ID, the user t chooses random t with m = n computes c1 = t + at −1 (mod n) and c2 = t − at −1 (mod n) sends s = (c1 , c2 ) to the usera a Note that here we are assuming that the encrypting entity does not know whether ID has the square root r of a or −a
- 19. Introduction IBE Based on Quadratic Residues IBE Based on Pairing Scalar Multiplication Contributions Future Work Cock’s IBE Scheme Decrypt To decrypt a ciphertext s = (c1 , c2 ) for user ID, he t chooses random t with m = n computes α = c1 + 2r if r 2 = a or α = c2 + 2r otherwise, and α computes m = n
- 20. Introduction IBE Based on Quadratic Residues IBE Based on Pairing Scalar Multiplication Contributions Future Work Some Observations Vulnerable to Adaptive Chosen Ciphertext Attack Solution: add redundancy Message-expansion: 2 log n
- 21. Introduction IBE Based on Quadratic Residues IBE Based on Pairing Scalar Multiplication Contributions Future Work Contents 1 Introduction IBE Idea IBE Framework Applications of IBE 2 IBE Based on Quadratic Residues Quadratic Residues Jacobi Symbol Quadratic Residuosity Problem IBE Scheme Observations on Cock’s IBE 3 IBE Based on Pairing Bilinear Pairing Basic BF-IBE Scheme Weil Pairing Miller’s Algorithm 4 Scalar Multiplication 5 Contributions 6 Future Work
- 22. Introduction IBE Based on Quadratic Residues IBE Based on Pairing Scalar Multiplication Contributions Future Work Bilinear Pairing Two groups G1 and G2 , both of prime order q. Admissible bilinear map is defined by e : G1 × G1 → G2 iff: ˆ Bilinear: e (aP, bQ) = e (P, Q)ab for all P, Q ∈ G1 and all a, b ∈ Z. ˆ ˆ Non-degenerate: Does not map all pairs of G1 × G1 to the identity in G2 Computable: An efficient polynomial time algorithm exists to calculate e (P, Q) for any given P, Q ∈ G1 . ˆ
- 23. Introduction IBE Based on Quadratic Residues IBE Based on Pairing Scalar Multiplication Contributions Future Work “Other” uses of pairings Tri-partite diffie hellman protocol MOV Reduction
- 24. Introduction IBE Based on Quadratic Residues IBE Based on Pairing Scalar Multiplication Contributions Future Work Basic BF-IBE Scheme Dan Boneh (Stanford), Matt Franklin (UC Davis), 2001
- 25. Introduction IBE Based on Quadratic Residues IBE Based on Pairing Scalar Multiplication Contributions Future Work Basic BF-IBE Scheme Setup PKG generates a prime q and two groups G1 and G2 of order q An admissible bilinear map e : G1 × G1 → G2 ˆ A random generator P ∈ G1 , a random s ∈ Z∗ and set Ppub = sP q Two cryptographic hash functions H1 : {0, 1}∗ → G∗ and 1 H2 : G2 → {0, 1}n for some n Details are: Message space is M = {0, 1}n . Ciphertext space is C = G∗ × {0, 1}n 1 The master-key is s ∈ Z∗ and the params are q (q, G1 , G2 , e , n, P, Ppub , H1 , H2 ) ˆ
- 26. Introduction IBE Based on Quadratic Residues IBE Based on Pairing Scalar Multiplication Contributions Future Work Basic BF-IBE Scheme Extract For a given string ID ∈ {0, 1}∗ , the algorithm computes QID = H1 (ID) ∈ G∗ , and sets the private key dID to be sQID where S is 1 the master-key
- 27. Introduction IBE Based on Quadratic Residues IBE Based on Pairing Scalar Multiplication Contributions Future Work Basic BF-IBE Scheme Encrypt To encrypt M ∈ M under the public key ID, first compute QID = H1 (ID) ∈ G∗ , choose a random number r ∈ Z∗ and set the 1 q ciphertext to be (rP, M ⊕ H2 (gID )) where gID = e (QID , Ppub ) ∈ G∗ r ˆ 2
- 28. Introduction IBE Based on Quadratic Residues IBE Based on Pairing Scalar Multiplication Contributions Future Work Basic BF-IBE Scheme Decrypt Assume that C = (U, V ) ∈ C is a ciphertext encrypted using the public key ID. To decrypt C using the private key dID ∈ G∗ , compute 1 M = V ⊕ H2 (ˆ(dID , U)) e
- 29. Introduction IBE Based on Quadratic Residues IBE Based on Pairing Scalar Multiplication Contributions Future Work Weil Pairing Existence of bilinear mapping: Weil pairing popular Needs degenerate Distortion helps
- 30. Introduction IBE Based on Quadratic Residues IBE Based on Pairing Scalar Multiplication Contributions Future Work Definitions - Lots of Definitions Divisor Provides a representation to indicate which points are zeroes or poles and their orders for a rational function over the elliptic curve Formal sum of points on elliptic curve group E , i.e. D = P∈E nP (P) where nP specifies the zero/pole property of point P and its order
- 31. Introduction IBE Based on Quadratic Residues IBE Based on Pairing Scalar Multiplication Contributions Future Work Definitions - Lots of Definitions Group of divisors The group of divisors on E (Div (E )) forms an abelian group If D1 = P∈E nP (P) and D2 = P∈E mP (P), then D1 + D2 = P∈E (nP + mP )(P) Define supp(D) = {P ∈ E | nP = 0} (support of divisor) and deg (D) = P∈E nP (degree of divisor)
- 32. Introduction IBE Based on Quadratic Residues IBE Based on Pairing Scalar Multiplication Contributions Future Work Definitions - Lots of Definitions Divisor of functions The evaluation of f on a point P = (xP , yP ) is f (P) = f (xP , yP ) The evaluation of f on a divisor D = P∈E nP (P) is f (D) = P∈supp(D) f (P)nP
- 33. Introduction IBE Based on Quadratic Residues IBE Based on Pairing Scalar Multiplication Contributions Future Work Definitions - Lots of Definitions Principal Divisor A divisor is principal iff D = div (f ) for some rational function f The principal divisor D is characterized by P∈E nP P = O and P∈E nP = 0 If a divisor is such that the two equalities hold, the divisor is principal
- 34. Introduction IBE Based on Quadratic Residues IBE Based on Pairing Scalar Multiplication Contributions Future Work Definitions - Lots of Definitions Equivalent Divisor Two divisors D1 , D2 of degree 0 are said to be equivalent (denoted by D1 ∼ D2 ), if D1 − D2 is principal For any zero degree divisor D = R∈E nR (R), there is a unique point P = R∈E nR R ∈ E such that D ∼ (P) − (O)
- 35. Introduction IBE Based on Quadratic Residues IBE Based on Pairing Scalar Multiplication Contributions Future Work Definitions - Lots of Definitions Adding two divisors Let f1 , f2 be such that D1 = div (f1 ) and D2 = div (f2 ) div (f1 f2 ) = D1 + D2 and div (f1 /f2 ) = D1 − D2 Let D1 = (P1 ) − (O) + div (f1 ) and D2 = (P2 ) − (O) + div (f2 ). Also, let P1 + P2 = P3 , hP1 ,P2 (x, y ) = ay + bx + c be the straight line passing through P1 and P2 and hP3 (x, y ) = x + d be the vertical line passing through P3 . Then we have div (hP1 ,P2 ) = (P1 ) + (P2 ) + (−P3 ) − 3(O) div (hP3 ) = (P3 ) + (−P3 ) − 2((O)) D1 + D2 = (P1 ) + (P2 ) − 2(O) + div (f1 f2 ) f1 f2 hP1 ,P2 which simplifies to (P3 ) − (O) + div ( ) hP3
- 36. Introduction IBE Based on Quadratic Residues IBE Based on Pairing Scalar Multiplication Contributions Future Work Definitions - Lots of Definitions Weil Pairing Elliptic curve E over a finite field K . E [m] = {P | mP = O, P ∈ E } (m prime to char (K )) Weil pairing is e : E [m] × E [m] → Z Given P, Q ∈ E [m], DP = (P) − (O) and DQ = (Q) − (O) Randomly choose T and U and define DP as (P + T ) − (T ) and DQ as (Q + U) − (U). Now, DP ∼ (P) − (O) and DQ ∼ (Q) − (O). div (fP ) = mP and div (fQ ) = mQ. The Weil Pairing is defined as fP (DQ ) e(P, Q) = fQ (DP )
- 37. Introduction IBE Based on Quadratic Residues IBE Based on Pairing Scalar Multiplication Contributions Future Work Miller’s Algorithm Miller’s Algorithm Given two points P, Q ∈ E [n], compute e(P, Q) fP (DQ ) fP (Q + R2 )fQ (R1 ) e(P, Q) = = fQ (DP ) fP (R2 )fQ (P + R1 ) Suffices to evaluate fP at DQ . Db = b(P + R1 ) − b(R1 ) − (bP) + (O), is a principal divisor. So there exists fb such that Db = Div (fb ). Db = Div (fb ) = b(P + R1 ) − b(R1 ) − (bP) + (O) Note that (fP ) = (fn ), so fP (DQ ) = fn (DQ ). Evaluate fn (DQ ) Given fα (DQ ), fβ (DQ ), αP, βP and (α + β)P, a constant time algorithm to calculate fα+β (DQ ) Let hαP,βP (x, y ) = ay + bx + c be the line passing through αP and βP, and h(α+β) (x, y ) = x + d be the line passing through (α + β)P. Then we have div (hαP,βP ) = (αP) + (βP) + ((−α − β)P) − 3(O) div (h(α+β)P ) = ((α + β)P) + ((−α − β)P) − 2(O)
- 38. Introduction IBE Based on Quadratic Residues IBE Based on Pairing Scalar Multiplication Contributions Future Work Miller’s Algorithm Miller’s Algorithm By definition, we have Dα = α(P + R1 ) − α(R1 ) − (αP) + (O) Dβ = β(P + R1 ) − β(R1 ) − (βP) + (O) Dα+β = (α + β)(P + R1 ) − (α + β)(R1 ) − ((α + β)P) + (O) So, Dα+β − Dα − Dβ = (αP) + (βP) − ((α + β)P) − (O) So, Dα+β − Dα − Dβ = div (hαP,βP ) − div (h(α+β)P ) So, hαP,βP (DQ ) fα+β (DQ ) = fα (DQ ).fβ (DQ ). h(α+β)P (DQ ) Denote this algorithm by D.
- 39. Introduction IBE Based on Quadratic Residues IBE Based on Pairing Scalar Multiplication Contributions Future Work Miller’s Algorithm Miller’s Algorithm D(fα (DQ ), fβ (DQ ), αP, βP, (α + β)P) = fα+β (DQ ) Now one can compute the fP (DQ ) = fn (DQ ) using the standard doubling procedure. Let bi s represent binary representation of n such that n = m bi 2i . i=0 Init: Set Z = O, V = f0 (DQ ) = 1 and k = 0 Iterate: For i = m to 0 by −1, do: If bi = 1 then V = D(V , f1 (DQ ), Z , P, Z + P), set Z = Z + P, and set k =k +1 If i > 0 set V = D(V , V , Z , Z , 2Z ), set Z = 2Z , and set k = 2k. Observe that at the end of each iteration, we have Z = kP and V = fk (DQ ) Output: After m iterations, we have k = n and so, V = fn (DQ )
- 40. Introduction IBE Based on Quadratic Residues IBE Based on Pairing Scalar Multiplication Contributions Future Work Scalar Multiplication: Motivation and Algorithms Algorithms Binary Method NAF Method Montgomery’s Ladder Eisentr¨ger, Lauter and Montogomery Method a
- 41. Introduction IBE Based on Quadratic Residues IBE Based on Pairing Scalar Multiplication Contributions Future Work Contributions Contributions We tried to explore if it was possible to improve scalar multiplication of elliptic curves. The conclusions made were: Since in Weil pairing computation, the central authority decides the value of n and its not a secret, the value of n should be chosen to be of low hamming weight, thus greatly improving the Weil pairing computation. Exploring other encoding schemes of k might help. For example, representing n as a sum of fibonacci numbers (or any such sequence) can be of immense help as doubling operation in elliptic curves is costlier than addition of two unequal points. So, if n can be represented as the sum of fibonacci numbers with low corresponding hamming weight, one can improve the algorithm to compute Weil pairing.
- 42. Introduction IBE Based on Quadratic Residues IBE Based on Pairing Scalar Multiplication Contributions Future Work Future Work Reading Details of Boneh Frankline IBE Scheme, Distortions to induce non-degeneracy Hierarchical Identity Based Encryption MOV Reduction, Supersingular curves, Choice of curves in BF-IBE 133 page-report Martin Gagn´ Master’s thesis e A forward-secure public-key encryption scheme Ideas to be explored Scalar Multiplication for special numbers n Choosing BDH parameters in BF-IBE Scheme
- 43. Introduction IBE Based on Quadratic Residues IBE Based on Pairing Scalar Multiplication Contributions Future Work References D. Boneh, M Franklin “Identity Based Encryption from the Weil Pairing” SIAM J. of Computing, 2003. Clifford Cocks “An Identity Based Encryption Scheme Based on Quadratic Residues” Cryptography and Coding, LNCS, 2001. A. Shamir “Identity-Based Cryptosystems and Signature Schemes” Proceedings of Crypto, 1984. R. Rivest, A. Shamir, D. Wagner “Time-lock Puzzles and Timed-release Crypto” Technical Report No. MIT/LCS/TR-684, 1996. Antoine Joux, Kim Nguyen “Separating Decision Diffie-Hellman from Computational Diffie-Hellman in Cryptographic Groups” J. Cryptology, 2003. A. Menezes, T. Okamoto, and S. Vanstone, “Reducing elliptic curve logarithms in a finite field” IEEE Trans. Inf. Theory, 1993.
- 44. Introduction IBE Based on Quadratic Residues IBE Based on Pairing Scalar Multiplication Contributions Future Work References Antoine Joux, “The Weil and Tate Pairings as Building Blocks for Public Key Cryptosystems”, ANTS, 2002. Martin Gagn´ “Identity-Based Encryption: a Survey” CryptoBytes 2003. e A. Shamir “How to share a secret” Communications of the ACM, 1979. Antoine Joux, “A One Round Protocol for Tripartite Diffie-Hellman” J. Cryptology, 2004. K. Eisentr¨ger, K. Lauter, P. L. Montgomery, “Improved Weil and Tate pairings a for elliptic and hyperelliptic curves”, Algorithmic Number Theory, 6th International Symposium, ANTS-VI Proceedings, 2004 Jing-Shyang Hwu, Rong-Jaye Chen, Yi-Bing Lin, “An efficient identity-based cryptosystem for end-to-end mobile security Export”, IEEE Transactions on In Wireless Communications, 2006.
- 45. Introduction IBE Based on Quadratic Residues IBE Based on Pairing Scalar Multiplication Contributions Future Work References William Stallings “Cryptography and Network Security (4th Edition)” Prentice Hall, 2005. Victor Shoup. “A Computational Introduction to Number Theory and Algebra.” Cambridge University Press 2005 CRC. A. Menezes, P. van Oorschot, and S. Vanstone. “Handbook of Applied Cryptography.” CRC. 1996. Cohen, H “Number Theory: Volume II: Analytic and Modern Tools (Graduate Texts in Mathematics)” Springer, 1 edition, 2007. Hankerson, Menezes, Vanstone, “Guide to Elliptic Curve Cryptography”, Springer, 2004.



































![Introduction IBE Based on Quadratic Residues IBE Based on Pairing Scalar Multiplication Contributions Future Work
Definitions - Lots of Definitions
Weil Pairing
Elliptic curve E over a finite field K . E [m] = {P | mP = O, P ∈ E }
(m prime to char (K ))
Weil pairing is e : E [m] × E [m] → Z
Given P, Q ∈ E [m], DP = (P) − (O) and DQ = (Q) − (O)
Randomly choose T and U and define DP as (P + T ) − (T ) and DQ
as (Q + U) − (U). Now, DP ∼ (P) − (O) and DQ ∼ (Q) − (O).
div (fP ) = mP and div (fQ ) = mQ.
The Weil Pairing is defined as
fP (DQ )
e(P, Q) =
fQ (DP )](https://image.slidesharecdn.com/btp-091203014542-phpapp01/85/Identity-Based-Encryption-36-320.jpg)
![Introduction IBE Based on Quadratic Residues IBE Based on Pairing Scalar Multiplication Contributions Future Work
Miller’s Algorithm
Miller’s Algorithm
Given two points P, Q ∈ E [n], compute e(P, Q)
fP (DQ ) fP (Q + R2 )fQ (R1 )
e(P, Q) = =
fQ (DP ) fP (R2 )fQ (P + R1 )
Suffices to evaluate fP at DQ .
Db = b(P + R1 ) − b(R1 ) − (bP) + (O), is a principal divisor. So there exists fb such that
Db = Div (fb ).
Db = Div (fb ) = b(P + R1 ) − b(R1 ) − (bP) + (O)
Note that (fP ) = (fn ), so fP (DQ ) = fn (DQ ). Evaluate fn (DQ )
Given fα (DQ ), fβ (DQ ), αP, βP and (α + β)P, a constant time algorithm to calculate
fα+β (DQ )
Let hαP,βP (x, y ) = ay + bx + c be the line passing through αP and βP, and
h(α+β) (x, y ) = x + d be the line passing through (α + β)P. Then we have
div (hαP,βP ) = (αP) + (βP) + ((−α − β)P) − 3(O)
div (h(α+β)P ) = ((α + β)P) + ((−α − β)P) − 2(O)](https://image.slidesharecdn.com/btp-091203014542-phpapp01/85/Identity-Based-Encryption-37-320.jpg)







